Cybercrime How it Really Happens New Trends How

Cybercrime: How it Really Happens, New Trends, & How to Protect You & Your Company September 11, 2019 Southwest Ohio Association for Financial Professionals (SWOAFP) Classification: Internal Use

Darrin Steinmann Director & Vice President Fifth Third Bank Corporate Investigations darrin. steinmann@53. com Kevin Carpenter Director, Risk Consulting Services RSM US LLP kevin. carpenter@rsmus. com Classification: Internal Use

What is Cybercrime? In the most broad sense cybercrime, or computer related crime, is crime that involves the internet, a computer system or computer technology. The computer may have been used in the commission of a crime, or it may be the target. Source: https: //en. wikipedia. org/wiki/Cybercrime Classification: Internal Use 2

The Cost of Cybercrime costs are unprecedented Organized criminals are exceptionally wellfunded; the cost of cybercrime is expected to reach $2 trillion this year @ $22 Million Year per 90, 909 NFL Quarterbacks 48, 000 miles cost $499 B in 2016 dollars Could replicate 4 x over with cyber losses Source: http: //www. gartner. com/newsroom/id/2828722; https: //www. forbes. com/sites/stevemorgan/2016/01/17/cyber-crime-costs-projected-to-reach-2 -trillion-by-2019/#47 a 242633 a 91 Photo: sportingnews. com Classification: Internal Use By SPUI - National Atlas, Public Domain, https: //commons. wikimedia. org/w/index. php? curid=945257 3

Who is Behind Cybercrime? What are Their Motivations? Org Crime/Fraudsters Theft Hacktivists Nation-States Disruption Destruction Classification: Internal Use 4

Social Media: A Fraudster’s Dream 33% of Web users are attacked by cyber criminals through social networks You have a 69% chance of falling victim to cyber crime in your lifetime 3. 5 new threats pop up every second (that’s 12, 600 per hour) Source: Fraudwatch International Classification: Internal Use 5

Threats on Social Media • Criminals LOVE social media • They share information and sell services to one another • Facebook offers the ability to see friends (and friends of friends) depending on privacy settings • Very easy to create fake accounts Source: Barracuda Labs Social Networking Analysis Classification: Internal Use 6

The Stakes Have Never Been Higher Anatomy of an Attack Classification: Internal Use 7
Issues You Face Online Identity Theft Threats are More Sophisticated Regulations Classification: Internal Use Education 8

Classification: Internal Use 9

Identity Fraud Reached an All-time High in 2017… …. and Continued in 2018 16. 7 MILLION # of identity fraud victims in the U. S. 35% For the first time ever, SSNs (35%) were compromised more than credit card numbers (30%) in breaches $16. 8 Amount stolen from U. S. consumers due to identity fraud BILLION 8% Image: https: //commons. wikimedia. org/wiki/File: Fingerprint_picture. svg Business Wire - Identity Fraud Hits All Time High With 16. 7 Million U. S. Victims in 2017, According to New Javelin Strategy & Research Study: https: //www. businesswire. com/news/home/20180206005363/en/Identity-Fraud-Hits-Time-High-16. 7 -Million Classification: Internal Use 10

2017 Cybersecurity Timeline Yahoo! reveals breach impacted all 3 billion of its users Not. Petya ransomware attack emerges globally; total losses could exceed $1 B Apache Struts remote code execution vulnerability reported JAN FEB MAR APR MAY Wanna. Cry $600 billion lost to cybercrime globally in 2017 ransomware worm first struck; most notably forcing some UK hospitals to shut down. JUN JUL Honda motor plant shutdown due to Wanna. Cry Sources: 2017 Year in Review: Cyber-Security Faces Challenges Old and New: http: //www. eweek. com/security/2017 year-in-review-cyber-security-faces-challenges-old-and-new Uber Hid 2016 Breach, Paying Hackers to Delete Stolen Data: https: //www. nytimes. com/2017/11/21/technology/uberhack. html Classification: Internal Use Equifax credit bureau announces data breach impacting 143 million consumers; Apache Struts is cause AUG SEP Blueborne Bluetooth vulnerabilities first disclosed; exposed nearly all operating systems to risk Uber disclosed 2016 breach and payment to hackers to delete stolen data OCT NOV DEC KRACK Wi. Fi vulnerabilities disclosed; enables attackers to bypass WPA 2 Wi. Fi security Lesson learned: The importance of timely patching Have I Been Pwned? https: //haveibeenpwned. com/ 11

Classification: Internal Use 12

Business Email Compromise (BEC) The Art of Deception Compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds. – A business is asked to wire funds for invoice payment to an alternate, fraudulent account – Email accounts of high-level business executives are compromised – An employee of a business has their email hacked Classification: Internal Use 13
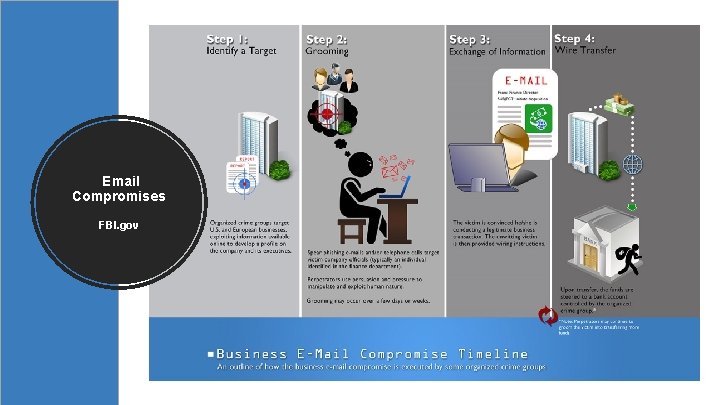
Email Compromises FBI. gov Classification: Internal Use 14

Business Email Compromise (BEC) The Art of Deception 17% increase in BEC attacks last year 13 Average number of people targeted in an organization; (Attacks are typically low in volume, but more people are being targeted across more units and more identities are being spoofed) 1/3 rd of BEC messages contain the word “payment” in the subject line; (Most attacks are designed with wire transfer fraud in mind) 11% of all email fraud attacks use ‘fake email chain’ messages, to give a realistic experience and appear more credible Classification: Internal Use 15
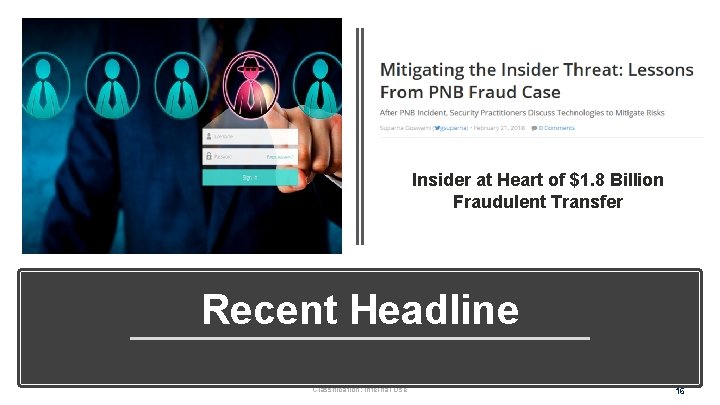
Insider at Heart of $1. 8 Billion Fraudulent Transfer Recent Headline Classification: Internal Use 16
Internal Fraud • Typical organizations lose 5% of revenues each year to internal fraud • The higher the perpetrator’s level of authority, the greater fraud losses tend to be Ø Separation of Duties • Most fraud attempts go undetected for an average Ø Reconciliation Functions of 18 months • 87% of occupational fraudsters have never been charged or convicted of a fraud-related offense Ø Analyze Resumes • Organizations with hotlines are much more likely to catch fraud by a tip Ø Establish referral process Classification: Internal Use 17

Finance Director 16 Month Embezzlement 20 Yr. Employee No Prior Issues Detected by Bank Internal On-Line Banking Scam November 2018 Classification: Internal Use 18 This Photo by Unknown Author is licensed under CC BY-SA

Classification: Internal Use 19

5 Security Things You Must Do 1. Know what’s on your network 2. Configure what’s on your network 3. Patch what’s on your network 4. Protect your administrative accounts 5. Train your employees Classification: Internal Use 20

1. Know what’s on your network If you don’t know what you have, how do you know if you need to patch it? Did you know it was here? Classification: Internal Use 21
2. Configure what’s on your network Apply consistent security settings across your network Classification: Internal Use 22
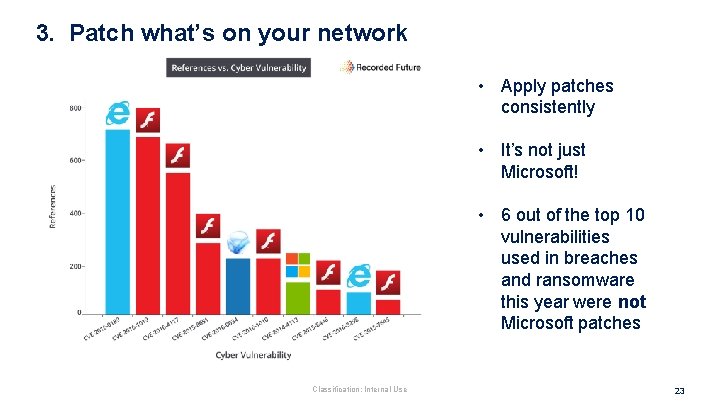
3. Patch what’s on your network • Apply patches consistently • It’s not just Microsoft! • 6 out of the top 10 vulnerabilities used in breaches and ransomware this year were not Microsoft patches Classification: Internal Use 23
4. Protect your administrative accounts • IT People: Do not use an administrative account for everyday activities • Consider implementing two factor authentication Classification: Internal Use 24
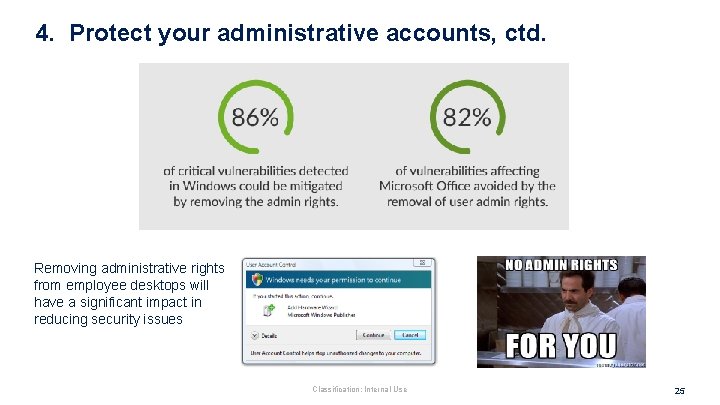
4. Protect your administrative accounts, ctd. Removing administrative rights from employee desktops will have a significant impact in reducing security issues Classification: Internal Use 25
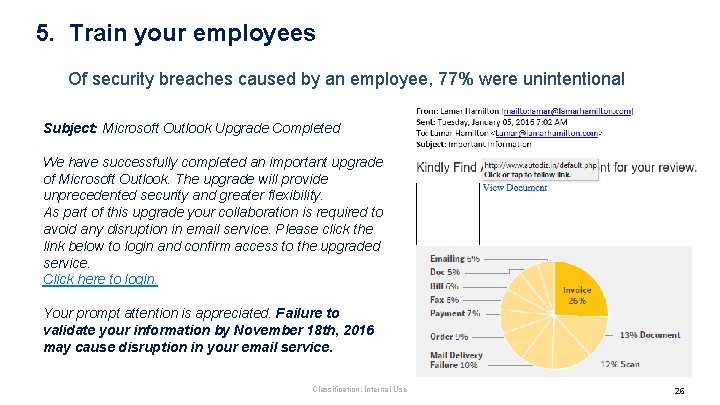
5. Train your employees Of security breaches caused by an employee, 77% were unintentional Subject: Microsoft Outlook Upgrade Completed We have successfully completed an important upgrade of Microsoft Outlook. The upgrade will provide unprecedented security and greater flexibility. As part of this upgrade your collaboration is required to avoid any disruption in email service. Please click the link below to login and confirm access to the upgraded service. Click here to login. Your prompt attention is appreciated. Failure to validate your information by November 18 th, 2016 may cause disruption in your email service. Classification: Internal Use 26

Best Practices Summary • • • Dual control Up to date patches / anti-virus software Strong authentication practices, dual factor Unique passwords for each site / system Do not click on links / attachments from unknown senders Red flags training and overall employee education Secure websites Set privacy controls on social media sites Consider cyber Insurance Do not access confidential sites via public networks Limit access authority, delete former employees, limit the ability to move money Utilize tools (people and tech) to monitor for suspect transactions Classification: Internal Use 27

Cyber Security is a Shared Responsibility We’re all in this together! Classification: Internal Use 28

So…. will you tell me your password? Jimmy Kimmel Cybersecurity Classification: Internal Use 29

Questions? Thank you. Classification: Internal Use 30
- Slides: 31