Cyber SystemCentric Approach To Cyber Security and CIP

Cyber System-Centric Approach To Cyber Security and CIP Morgan King Senior Compliance Auditor – Cyber Security WECC Reliability and Security Workshop San Diego CA – October 23 – 24, 2018 W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

2 Did We Get CIP v 5 Right? 1. We got CIP v 5 so right 2. System-centric approach never fully realized 3. Need all perspectives in identifying and resolving the issues 4. Making CIP more manageable, auditable, secure, and resilient W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
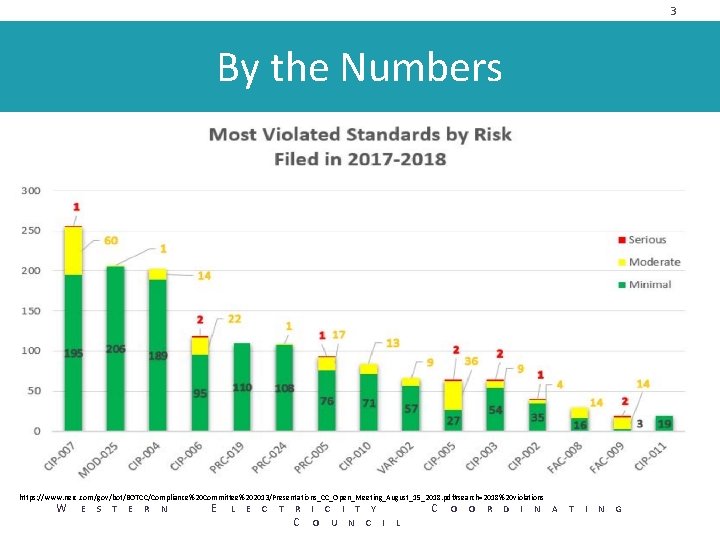
3 By the Numbers https: //www. nerc. com/gov/bot/BOTCC/Compliance%20 Committee%202013/Presentations_CC_Open_Meeting_August_15_2018. pdf#search=2018%20 violations W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
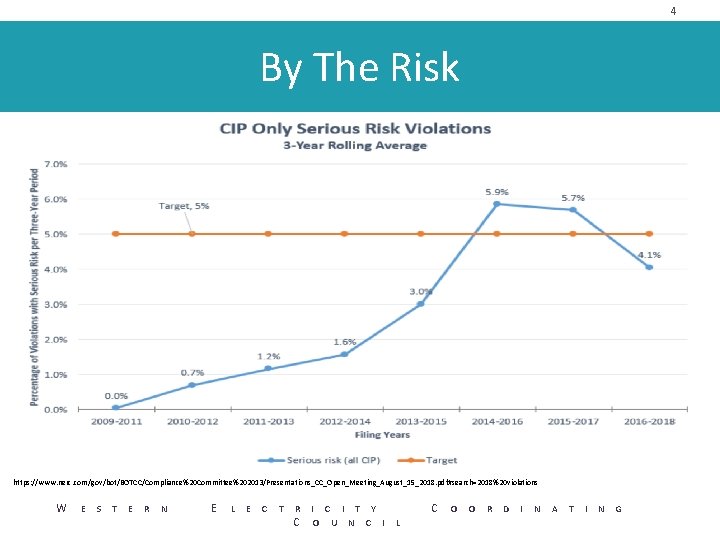
4 By The Risk https: //www. nerc. com/gov/bot/BOTCC/Compliance%20 Committee%202013/Presentations_CC_Open_Meeting_August_15_2018. pdf#search=2018%20 violations W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
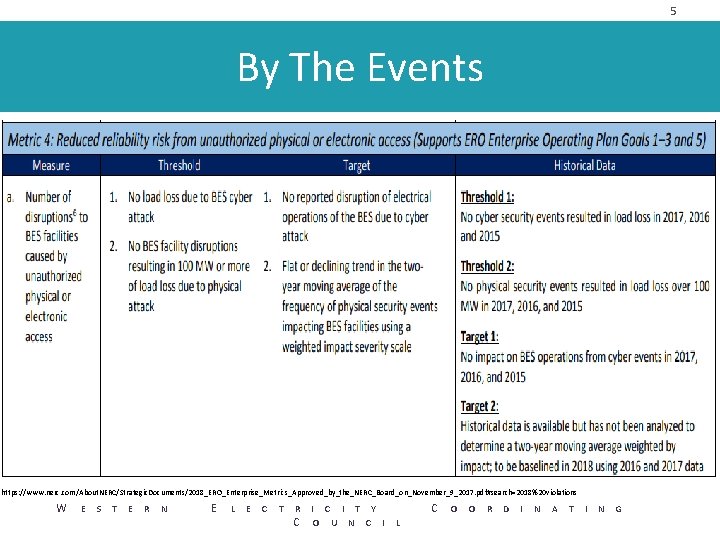
5 By The Events https: //www. nerc. com/About. NERC/Strategic. Documents/2018_ERO_Enterprise_Metrics_Approved_by_the_NERC_Board_on_November_9_2017. pdf#search=2018%20 violations W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
6 Two Aspects in CIP • CIP is a PROGRAM and its elements. – CIP-002, CIP-003, CIP-004, CIP-006, CIP-008, CIP 009, CIP-011, CIP-014 • CIP has TECHNICAL architecture requirements. – CIP-005, CIP-007, CIP-010 W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
7 Paradigm Shift https: //www. biggreendoor. com/wp-content/uploads/znvn 774 tlxdrpv 3 lzqhu. png W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

8 Device-Centric • CIP v 3 Critical Cyber Assets • CIP v 5 original concept was to be a paradigm shift from device-centric to a system-centric approach. – Cyber Asset • Programmable electronic device – BES Cyber Asset – BES Cyber System • Per BES Cyber System / Cyber Asset Capability W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

9 Device-Centric Approach W Baseline BES Cyber System Cyber Asset E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
10 System-Centric • Consider that cyber technology in support of reliability is not just a piece of hardware or software, or a communication circuit, but a system intimately associated with the reliability functions it supports. • One of the fundamental differences between Versions 4 and 5 of the CIP Cyber Security Standards is the shift from identifying Critical Cyber Assets to identifying BES Cyber Systems. W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

11 System-Centric Approach BES Cyber System Baselines For Like Device Types BES Cyber System W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
12 What If…? • We retire some definitions • We modify existing or create new definitions concerning devices and networking to include virtualization concepts • We create additional technical requirements for securing today’s version of virtualization technology? • We change requirements to security-objective-based Technology agnositic Nonprescriptive Backward compatible Future Proof technology agnostic – – W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
13 CIP Modifications Drafting Team • SDT has worked for over a year on designing virtualization-specific language and requirements – Electronic Security Zone – to logically isolate systems on shared infrastructure – Centralized Management System – to address the risk of virtualization management systems; “fewer, bigger buttons” • Issues – Very complex – Today’s technology and products – Continues to evolve W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

14 CIP SDT White Paper https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_Virtualization_Outreach_Webinar_Slides_06292018. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

15 CIP Modifications Drafting Team • Definitions Proposed for Retirement – BES Cyber Asset – Protected Cyber Asset – Electronic Security Perimeter – Electronic Access Point – Electronic Access Control or Monitoring Systems W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
16 More Change Upon Us • Cyber Asset only applicable to (TCA, Removable Media) • BES Cyber System • Protected Cyber System • Electronic Access Control System • Electronic Access Monitoring Systems • External Routable Connectivity with new objective-based isolation model • Interactive Remote Access to address IP-serial conversion scenarios W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
17 Nonprescriptive • CIP-007 -6 R 3 Part 3. 1 – “Deploy method(s) to deter, detect, or prevent malicious code. ” • CIP-007 -6 R 3 Guidance – “Due to the wide range of equipment comprising the BES Cyber Systems and the wide variety of vulnerability and capability of that equipment to malware as well as the constantly evolving threat and resultant tools and controls, it is not practical within the standard to prescribe how malware is to be addressed on each Cyber Asset. Rather, the Responsible Entity determines on a BES Cyber System basis which Cyber Assets have susceptibility to malware intrusions and documents their plans and processes for addressing those risks and provides evidence that they follow those plans and processes. ” W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
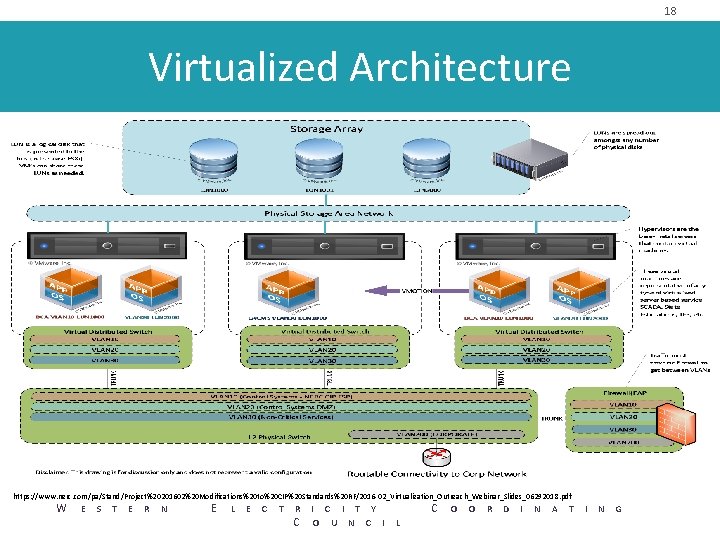
18 Virtualized Architecture https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_Virtualization_Outreach_Webinar_Slides_06292018. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
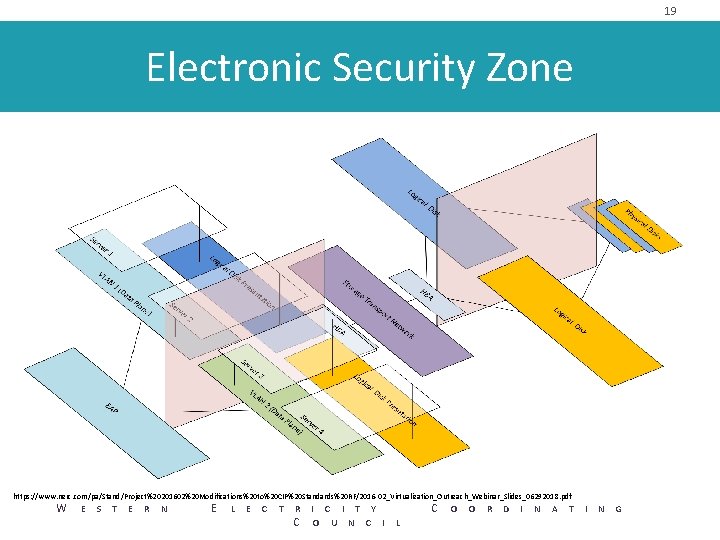
19 Electronic Security Zone https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_Virtualization_Outreach_Webinar_Slides_06292018. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
20 CIP Modifications Drafting Team • Is a containerized application a BCA? Or is it just an application? • An entities Electronic Access Point is now a policy-based “firewall, ” dynamically placed in front of workloads. Access control is now beyond a layer 3 routable protocol level. How does an entity demonstrate compliance with CIP-005? • Is SAN part of the same BES Cyber Asset as the virtual machine, is a SAN its own BES Cyber Asset, or is it just a BES Cyber System Information repository since it alone does not perform any BES functions? W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
21 System-Centric Approach • Make “BES Cyber System” the foundational object. • Requirements apply at the system level. – Implement on system as a whole – Implement on components that make sense – Allows for dynamic components W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

22 Current CIP-005 -5 R 1, R 2 W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
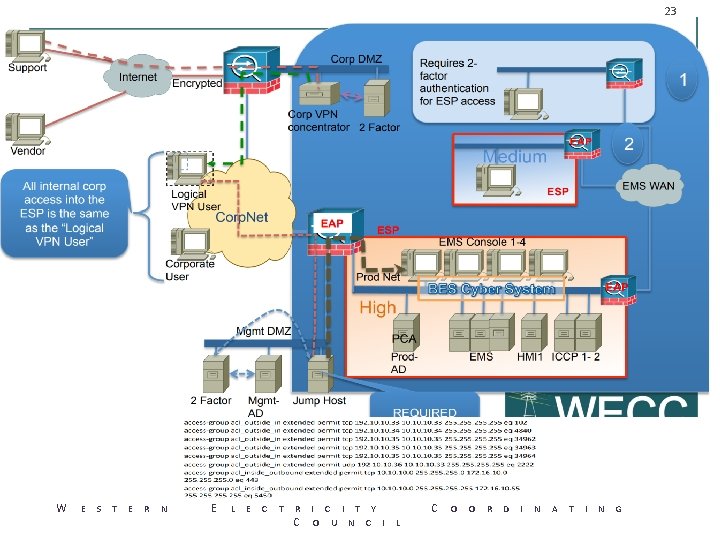
23 W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
24 Logical Isolation Zone / External Routable Connectivity • Logical Isolation Zone – One or more cyber systems isolated by logical controls that only allow known and controlled communications to or from those systems. • External Routable Connectivity – Inbound and outbound communication to a logically isolated BES Cyber system initiated from a system that is outside of the Logical Isolation Zone. W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
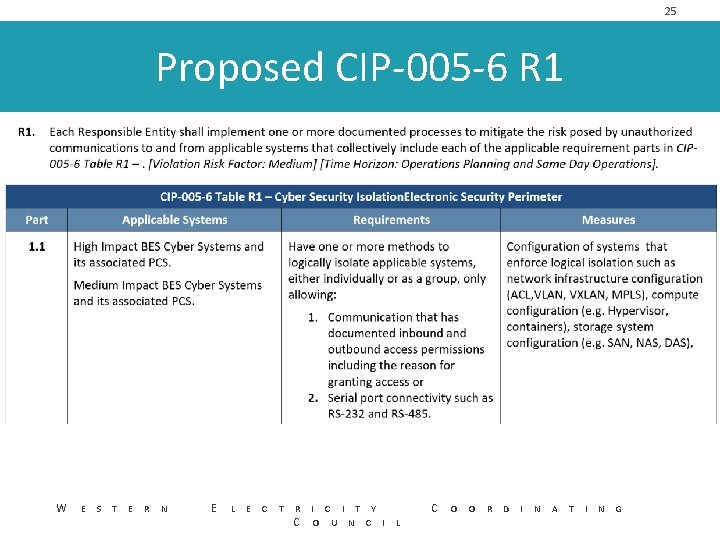
25 Proposed CIP-005 -6 R 1 ` W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
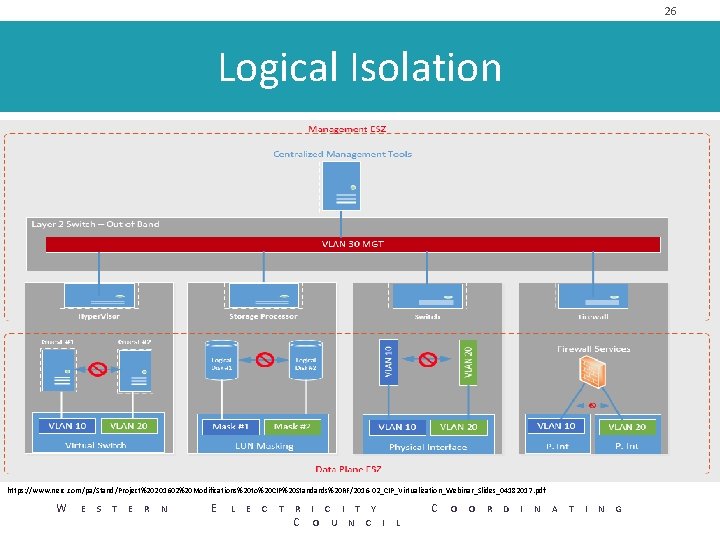
26 Logical Isolation https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_CIP_Virtualization_Webinar_Slides_04182017. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
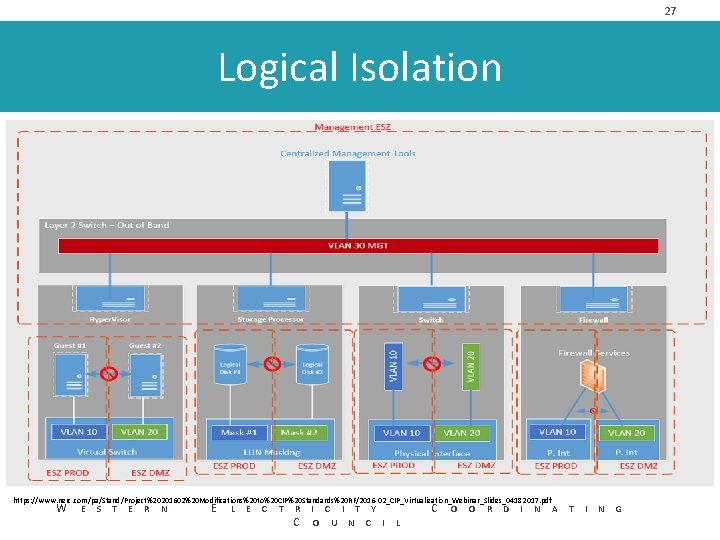
27 Logical Isolation https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_CIP_Virtualization_Webinar_Slides_04182017. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
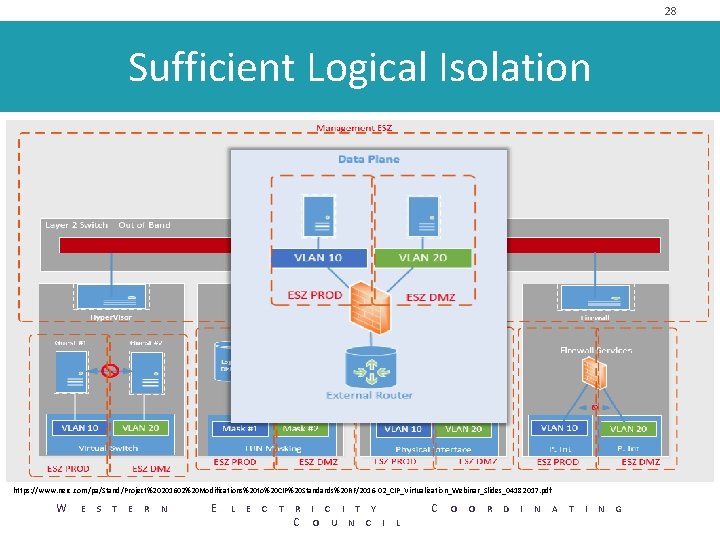
28 Sufficient Logical Isolation https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_CIP_Virtualization_Webinar_Slides_04182017. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
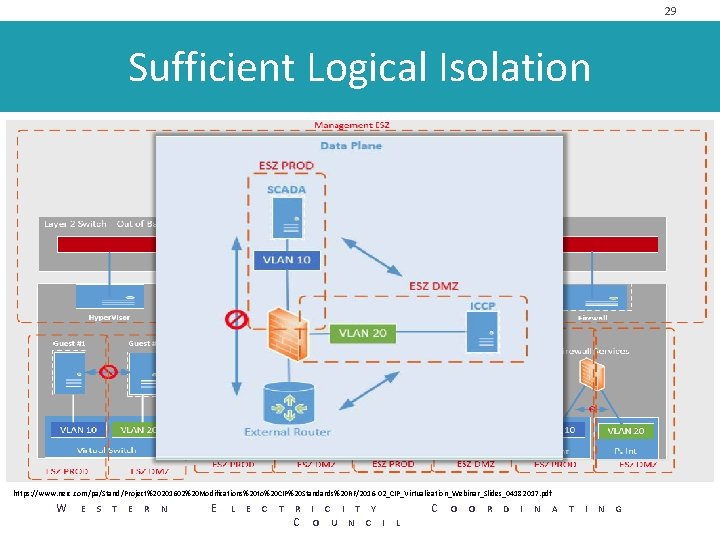
29 Sufficient Logical Isolation https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_CIP_Virtualization_Webinar_Slides_04182017. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
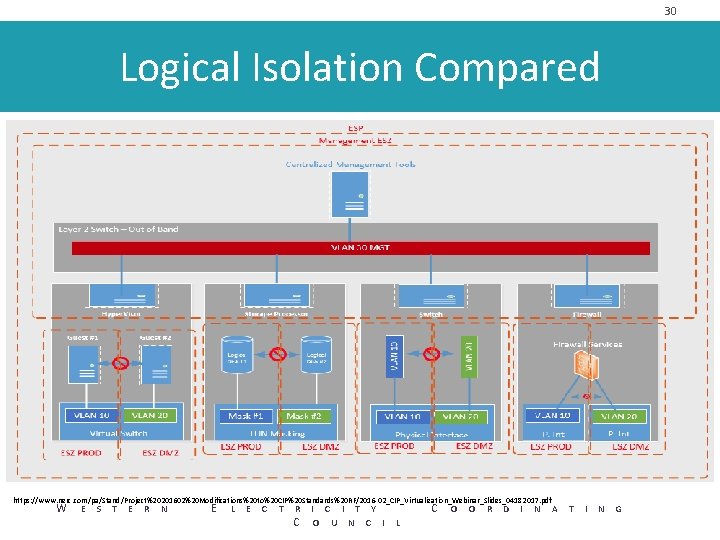
30 Logical Isolation Compared https: //www. nerc. com/pa/Stand/Project%20201602%20 Modifications%20 to%20 CIP%20 Standards%20 RF/2016 -02_CIP_Virtualization_Webinar_Slides_04182017. pdf W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
31 NERC CIPC/CIWG Cloud Project Implications of Cloud Services for CIP Assets Underlay / Overlay Certifications Meeting security objectives for applicable systems • • W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
32 CIWG Cloud Project Tabletop Participants Tri-State SMUD APS MISO AES Ameren? KCP&L? • • W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

33 Service Provider Participants Coal. Fire AWS IBM Service. Now Microsoft Fed. RAMP PMO? • • • W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
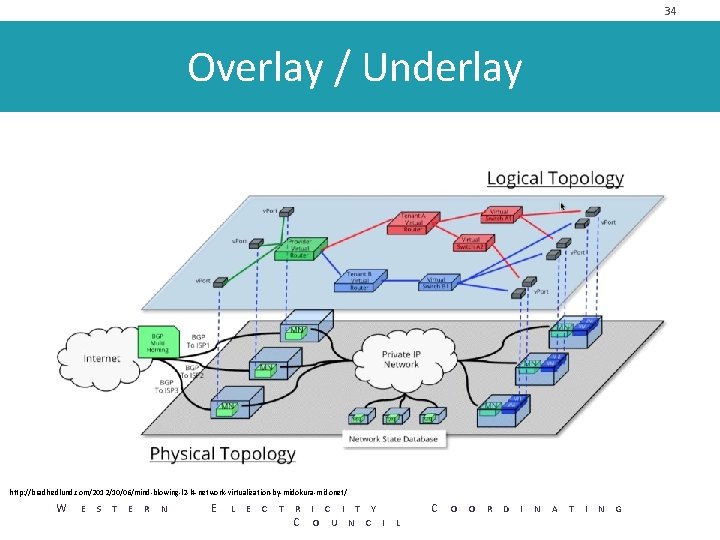
34 Overlay / Underlay http: //bradhedlund. com/2012/10/06/mind-blowing-l 2 -l 4 -network-virtualization-by-midokura-midonet/ W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
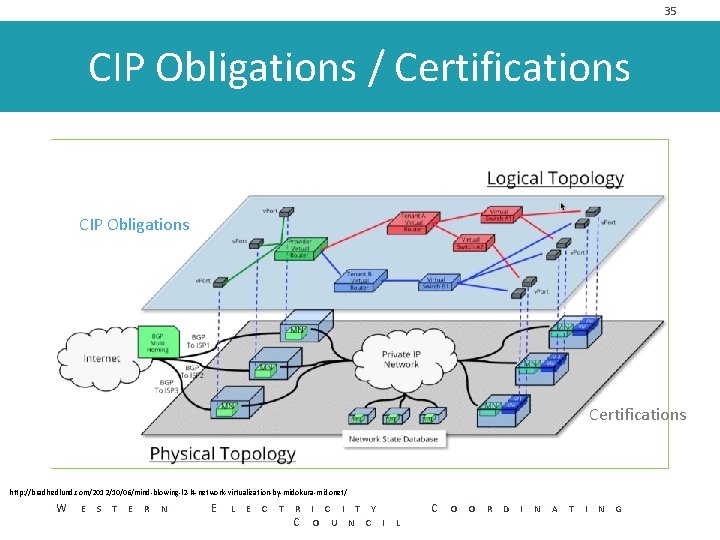
35 CIP Obligations / Certifications CIP Obligations Certifications http: //bradhedlund. com/2012/10/06/mind-blowing-l 2 -l 4 -network-virtualization-by-midokura-midonet/ W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
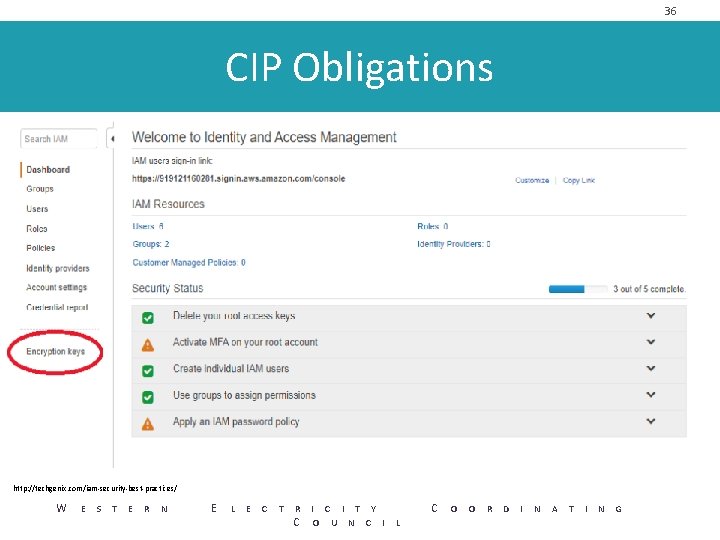
36 CIP Obligations http: //techgenix. com/iam-security-best-practices/ W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
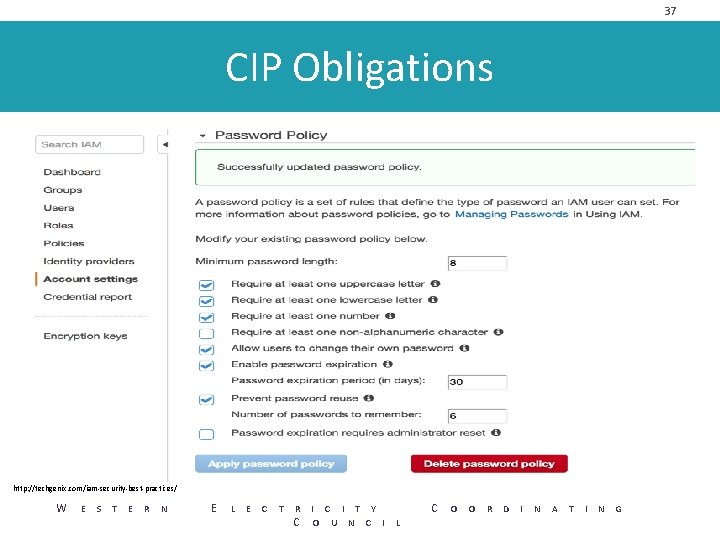
37 CIP Obligations http: //techgenix. com/iam-security-best-practices/ W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
38 Potential Gaps • Should there be a notification to utilities when CIP standard are violated? • Service provider audit report not shared with others • Ensuring the security plan and actual implementation are adequate W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
39 Concerns • Compliance risks for utilities when vendors don’t perform • How to address changes to CIP standards with service providers? • Mapping to the CMEP – How will this be audited and PNCs addressed? – Mitigating violations that impact CIP Compliance W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

40 Review 1. CIP v 5 continues to evolve 2. System-centric approach closer to being fully developed 3. Need all perspectives in identifying and resolving the issues 4. Ensuring CIP is more manageable, auditable, secure, and resilient W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G

41 Next Steps • Post for informal comment period October 29, 2018. • Seeking Standards Committee (SC) authorization to post March 2019. • Initial posting March 2019 (if authorized to post by SC). • November 1, 2018 Virtualization Webinar. W E S T E R N E L E C T R I C I T Y C O U N C I L C O O R D I N A T I N G
- Slides: 41