Cyber Situation Awareness from a Cyber Security Perspective

Cyber Situation Awareness from a Cyber Security Perspective Sushil Jajodia, Massimiliano Albanese George Mason University Peng Liu Pennsylvania State University Doug Reeves, Peng Ning, Christopher Healey North Carolina State University V. S. Subrahmanian University of Maryland ARO-MURI on Cyber-Situation Awareness Review Meeting Phoenix AZ, 2013
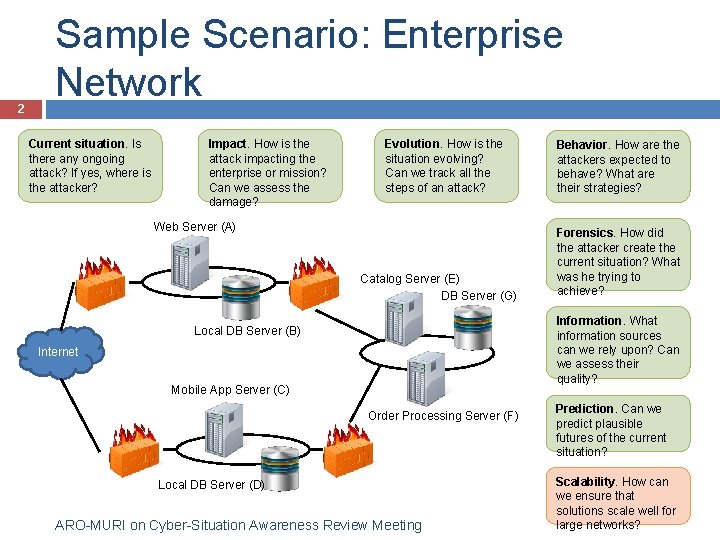
2 Sample Scenario: Enterprise Network Current situation. Is there any ongoing attack? If yes, where is the attacker? Impact. How is the attack impacting the enterprise or mission? Can we assess the damage? Evolution. How is the situation evolving? Can we track all the steps of an attack? Web Server (A) Catalog Server (E) DB Server (G) Behavior. How are the attackers expected to behave? What are their strategies? Forensics. How did the attacker create the current situation? What was he trying to achieve? Information. What information sources can we rely upon? Can we assess their quality? Local DB Server (B) Internet Mobile App Server (C) Order Processing Server (F) Local DB Server (D) ARO-MURI on Cyber-Situation Awareness Review Meeting Prediction. Can we predict plausible futures of the current situation? Scalability. How can we ensure that solutions scale well for large networks?

Desired CSA Capabilities 3 Aspects of cyber situational awareness that need to be addressed in order to answers all the previous questions 1. Be aware of current situation 2. Be aware of the impact of the attack 3. Integration of knowledge of the attacker’s behavior into the attack model Be aware of why and how the current situation is caused 6. Real-time tracking of attacks Be aware of adversary behavior 5. Damage assessment Be aware of how situations evolve 4. Identification of past and ongoing attacks Forensics Be aware of quality of information Information sources, data integration, quality measures 7. Assess plausible futures of Meeting the current ARO-MURI on Cyber-Situation Awareness Review situations
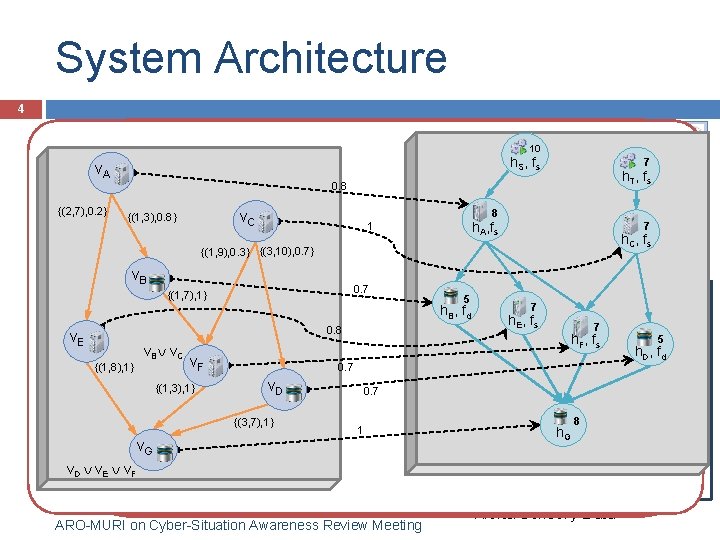
System Architecture 4 Vulnerability Databases 10 h. G v. A Scenario Analysis &7 h. S, fs Unexplained Activities h. Heavy Visualization T, fs Iron 0. 8 CVE NVD {(2, 7), 0. 2} {(1, 3), 0. 8} fd Local DB Server (D) OSVD v. C Mobile App {(3, 10), 0. 7} {(1, 9), 0. 3} 0. 7 Topological Server (C) h v B Vulnerability B {(1, 7), 1} Cauldro Switchwal Analysis n v. E {(1, 8), 1} l v. B v. C v. F {(1, 3), 1} fs fs. Analys 1 h. A fd Network Hardening 7 h. C, fs Graph DB h. FServer (G) h. D Index & Data Processing 0. 7 Structures 5 and Indexing 7 Order Processing 0. 8 Server (F) f 0. 3 s v. D h. E t Model Adversarial 8 modeling h. A, fs 1 1 0. 7 Stochastic h. B, fd Attack Models 0. 7 fs h. E, fs 7 h. F, fs h. D, fd Situation h. C Knowledge Reference Model No information about the impact on 8 {(3, 7), 1} 1 h G missions of different courses of Generalized Dependency v. G fs f Dependency actions Analysis s NSDMine v. D v. E v. F Graphs r Mobile Order Tracking Online Shopping Monitored Network ARO-MURI on Cyber-Situation Awareness Review Meeting 5 Alerts/Sensory Data
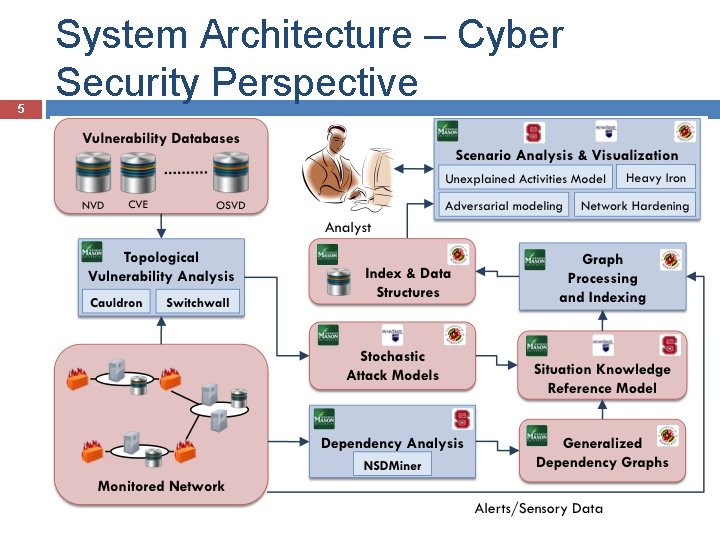
5 System Architecture – Cyber Security Perspective
- Slides: 5