Cyber Security of Power System Operation and Control

Cyber Security of Power System Operation and Control Chen-Ching Liu School of Electrical, Electronic and Mechanical Engineering University College Dublin National University of Ireland, Ireland Seminar at IEEE PES France, Aug 2009

Overview of Cyber Security Issues § § § Evolution of SCADA Systems SCADA System Security CIP 002 -009 and Other Standards Highlights of SCADA Security Incidents Enhancing Cyber Security of SCADA Systems
Evolution of SCADA Systems Evolved through generations § Monolithic § Distributed § Networked
Monolithic § First developed system centered in mainframe (allin-one role) § Stand alone § Communication protocols to RTUs are proprietary § Redundancy and connectivity depend on features of a vendor
Distributed § Implemented using Local Area Network (LAN) technology § Distribute computational burden to a number of computers via LAN § Servers include communication, application, user interface, database § Redundancy between servers provide failover capability § Limitation of hardware and software provided by vendors

Networked § Close to distributed framework § More open system environment § Standardized protocols such as DNP 3. 0 i, IEC 61850, Modbus, RS-232, etc. § Implementation of WAN communication § Cost-effective as hardware and software become PCbased § Use of standardized WAN communication cause cyber security problems

Critical Cyber Assets § Critical Cyber Assets in Power infrastructure Ø Energy Management System (EMS) in Control Center Ø Distribution Management System (DMS) Ø Process Control System (Power Plants) Ø Substation Automation System (SAS)

Cyber Systems in Power Infrastructure
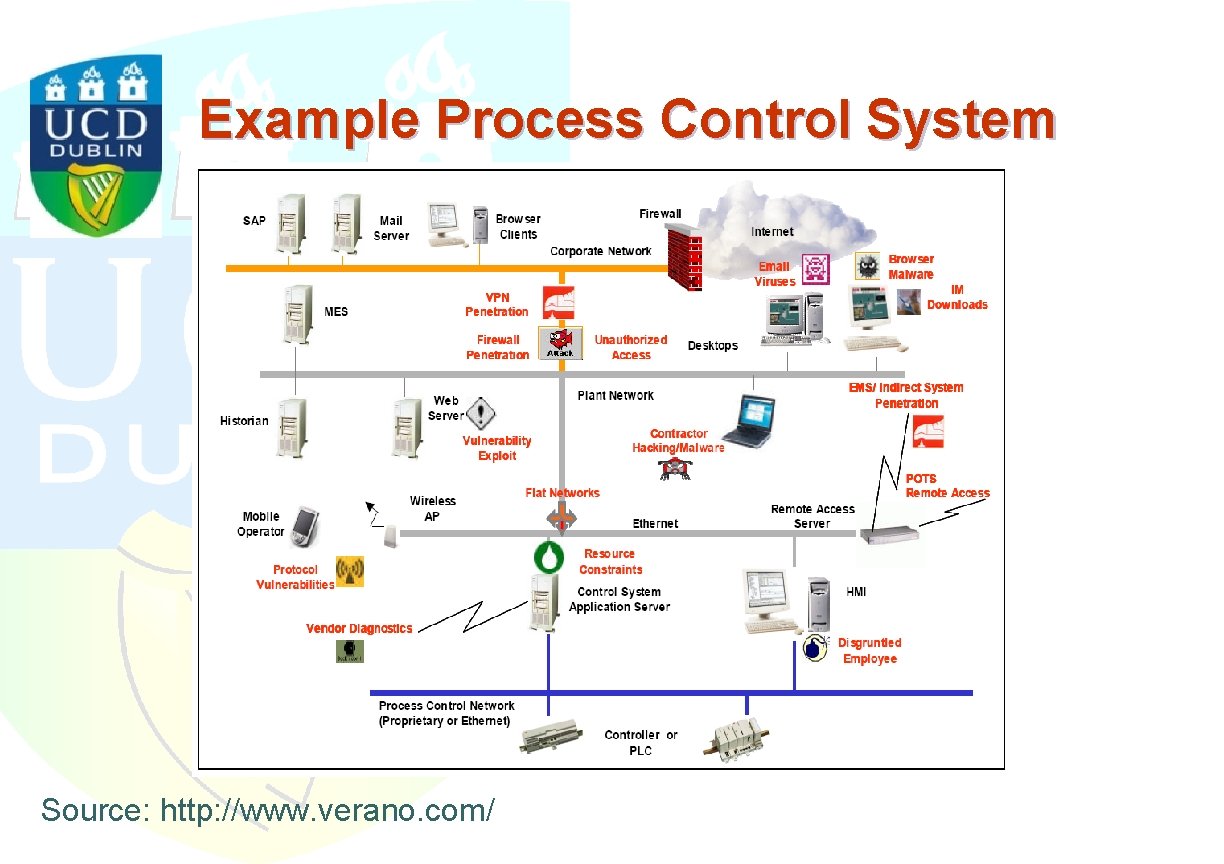
Example Process Control System Source: http: //www. verano. com/

Highlights of SCADA Attack Incidents § § § § § 1994: Salt River Project, an electricity and water provider in Phoenix, was compromised 1997: A teenager shuts down the air-traffic control room of a local MA airport 1997: The US Do. D asks NSA to test safety of power supply going to US military bases 1999: Russian hackers took control of a pipeline for 24 hours 2000: Disgruntled Australian employee hacks wastewater SCADA system 45 times and dumps 264, 000 gallons of sewage in the city’s parks and rivers 2001: California ISO hacked by a software exploit in Solaris, for 17 days 2002: Captured laptops reveal critical data to hack the US power grid 2003: Slammer worm crashes Davis-Besse nuclear power plant, OH, for 5 hours 2003: Slammer worm penetrates a major SCADA network through a VPN connection

Escalating Cyber Security Factors § Adoption of standardized technologies with known vulnerabilities § Connectivity of control systems to other networks § Constraints on use of existing security technologies and practices § Insecure remote connections § Widespread availability of technical information about control systems
Scenarios of Vulnerabilities § Remote access to control network and gain SCADA control to cause damage, particularly, to take control of remote devices in Ø Control Center Ø Substation SCADA Ø Process Control System Ø Distribution Automation
Access Points in Control Networks § § § Virtual Private Network (VPN) Dial-up Networks Wireless Networks Any Remote Logon Programs Backdoor Access - Trojan Horse (on Unknown Service Ports)

Scenario 1 § Penetration to PCS and sabotage the internal instrumental controls in power plants § Use this node as the stepping stone intruding into control center via VPN § Attacks on both PCS and Control Center Ø Mass manipulation of open commands of circuit breakers at each substation Ø Determine backup control centers and wipe out databases Ø Create permanent faults at power plant that may overload the power system
Scenario 1

Scenario 2 § Penetration into any substation through dial-up connection using social engineering approach § Use this node as the stepping stone to intruding into control center via VPN § Attack on control center § Mass manipulation of open commands of breakers at each substation from a control center as well as local databases § Determine backup control centers and wipe out databases
Scenario 3 § Penetration to web-based SCADA service providers and execute possible attacks § Web-based SCADA features Ø SCADA, EMS, Load forecasting, Trouble Call Management, Load Management § Enhanced authentication using security token § Attack on control area of SCADA Ø Send open commands to breakers at each substation from web-based SCADA

Intrusion Tools § § War Dialing Scanning Traffic Sniffing Password Cracking
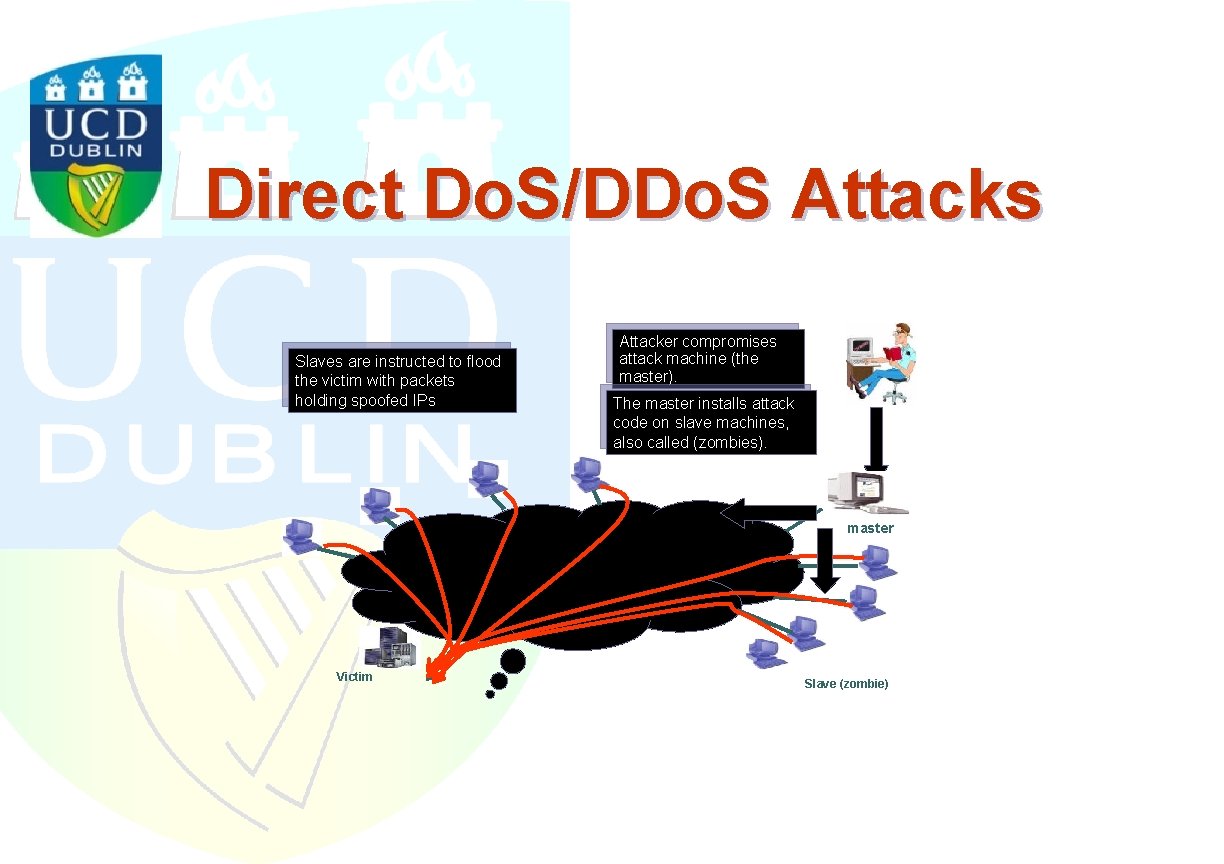
Direct Do. S/DDo. S Attacks Slaves are instructed to flood the victim with packets holding spoofed IPs Attacker compromises attack machine (the master). The master installs attack code on slave machines, also called (zombies). master Victim Slave (zombie)

Cyber Security Standards for SCADA (NERC CIP 002 -009 Compliance) § CIP 001 stresses on physical security § Provides general guidance about what to comply, alert, train personnel § Identifies physical and cyber parameters, and critical cyber asset § Security management controls (auditing) § Personnel training § Does not provide guidance to system vulnerability assessment based on what is implemented
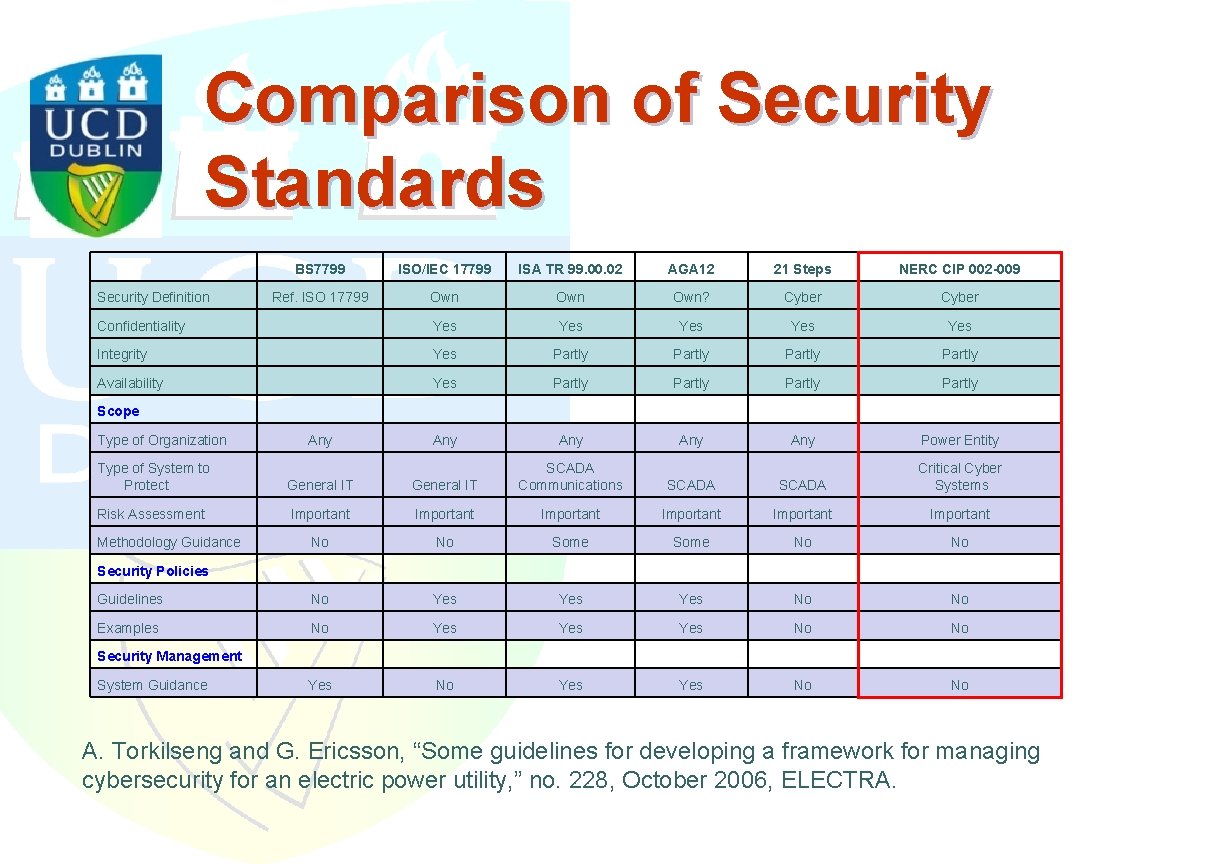
Comparison of Security Standards BS 7799 ISO/IEC 17799 ISA TR 99. 00. 02 AGA 12 21 Steps NERC CIP 002 -009 Ref. ISO 17799 Own Own? Cyber Confidentiality Yes Yes Yes Integrity Yes Partly Availability Yes Partly Any Any Power Entity SCADA Critical Cyber Systems Security Definition Scope Type of Organization Any Type of System to Protect General IT SCADA Communications Risk Assessment Important Important No No Some No No Guidelines No Yes Yes No No Examples No Yes Yes No No Methodology Guidance Security Policies Security Management System Guidance A. Torkilseng and G. Ericsson, “Some guidelines for developing a framework for managing cybersecurity for an electric power utility, ” no. 228, October 2006, ELECTRA.

Security Risk Management § Risk Assessment Ø Input: Identify risk, determine possible damages, quantify impact of potential threats, balance between economic impact of risk and cost of risk mitigation Ø Output: report that describes threats and vulnerability

Security Risk Management (Cont. ) § Risk Mitigation Ø Systematic methodology to prioritize, evaluate, and implement countermeasures by risk assessment process Ø Monitoring: Last phase of risk management process after actual effectiveness of implemented countermeasure evaluated

Preventing an Attack? § Start enhancing the protection scheme on every level Ø Enforce enhancement policies to Internet, Intranet, and computer access Ø Protocol encryption within computers in the control center and privileges to RTU Ø Improve redundancy of computers within control centers Ø Enhance high reliability and redundancy of the network with contingency analysis
Power Infrastructure Protection § To build transmission lines with underground (expensive alternatives) to have less exposure outside § Multi-site control centers with the same role of authentication to SCADA system § Enforce “multiple authentication policy” from multiple sites to close or open the break remotely § Incorporate bio-verification system in SCADA system § Increase security in significant generators in the network to avoid cascading events

Vulnerability Assessment § Methodology of Vulnerability Assessment Ø System Vulnerability Ø Scenario Vulnerability Ø Access Point Vulnerability Ø Quantitative Analysis Ø Impact Factor Evaluation
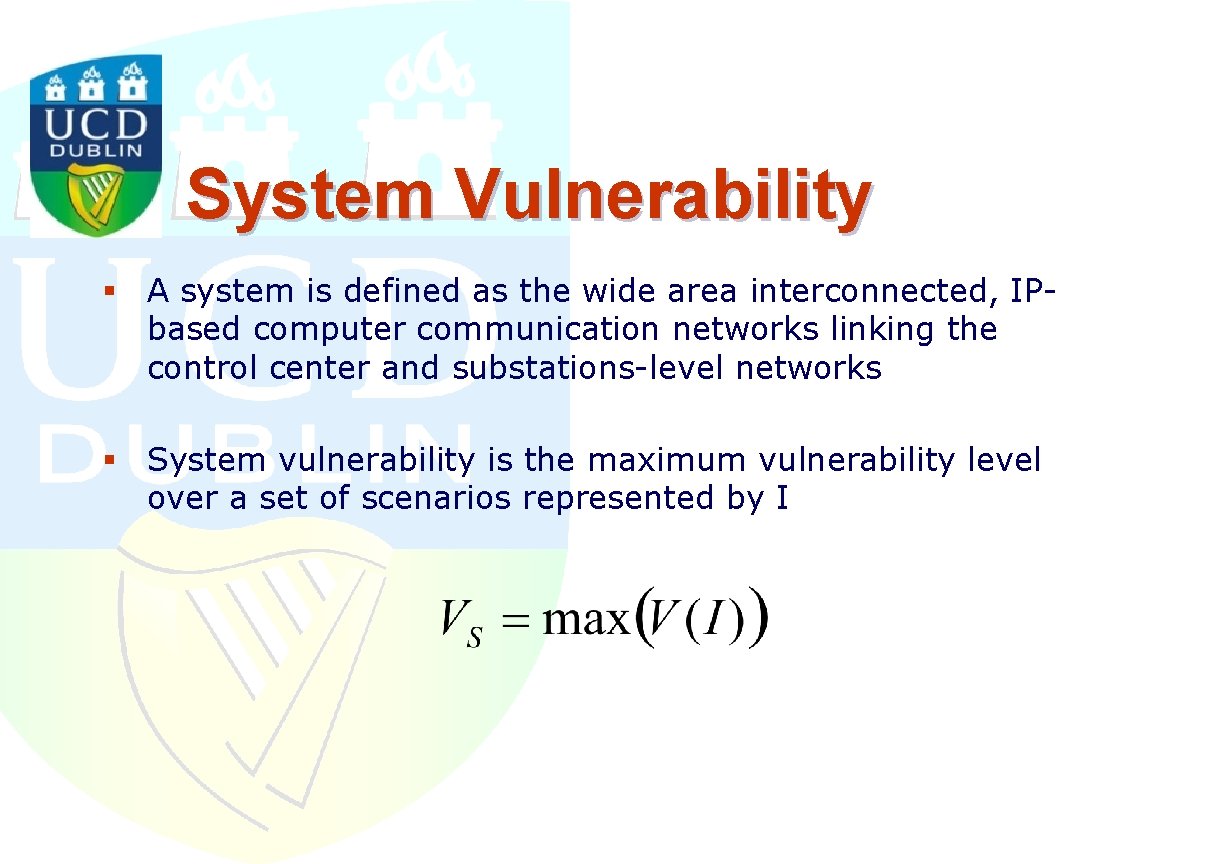
System Vulnerability § A system is defined as the wide area interconnected, IPbased computer communication networks linking the control center and substations-level networks § System vulnerability is the maximum vulnerability level over a set of scenarios represented by I
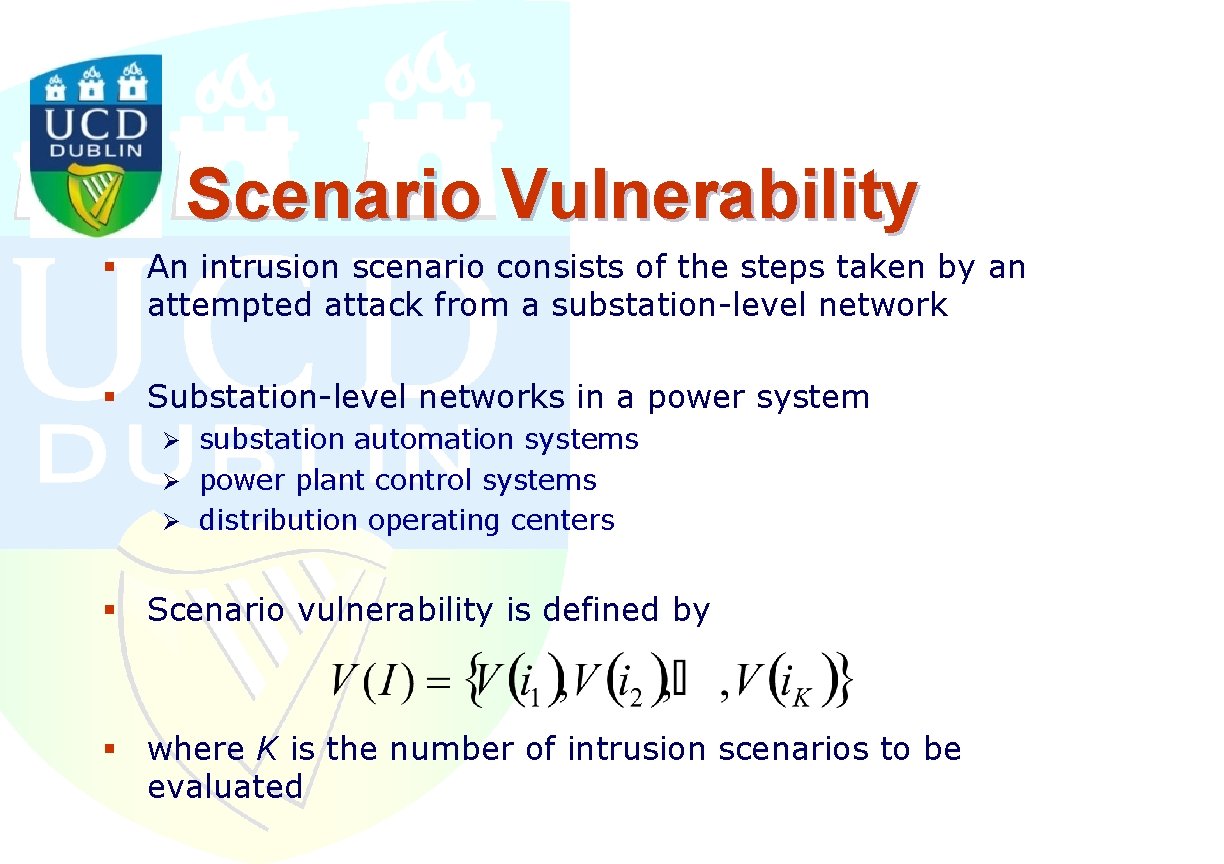
Scenario Vulnerability § An intrusion scenario consists of the steps taken by an attempted attack from a substation-level network § Substation-level networks in a power system Ø substation automation systems Ø power plant control systems Ø distribution operating centers § Scenario vulnerability is defined by § where K is the number of intrusion scenarios to be evaluated

Access Point Vulnerability § Access point provides the port services to establish a connection for an intruder to penetrate SCADA computer systems § Vulnerability of a scenario i, V(i), through an access point is evaluated to determine its potential damage § Scenario vulnerability - weighted sum of the potential damages over the set S. where is the steady state probability that a SCADA system is attacked through a specific access point j, which is linked to the SCADA system. The damage factor, , represents the level of damage on a power system when a substation is removed

Generalized Stochastic Petri Net (GSPN) § Intrusion and cyber-net are modeled by a GSPN model § GSPN consists of two different transition classes: immediate and timed transitions. § States of the stochastic process are the status of intrusions to a network that are inferred from the abnormal activities § Cyber-net is a composite model Ø Firewall model Ø Password model § These include malicious packets flowing through Ø Pre-defined firewall rules Ø Failed logon password
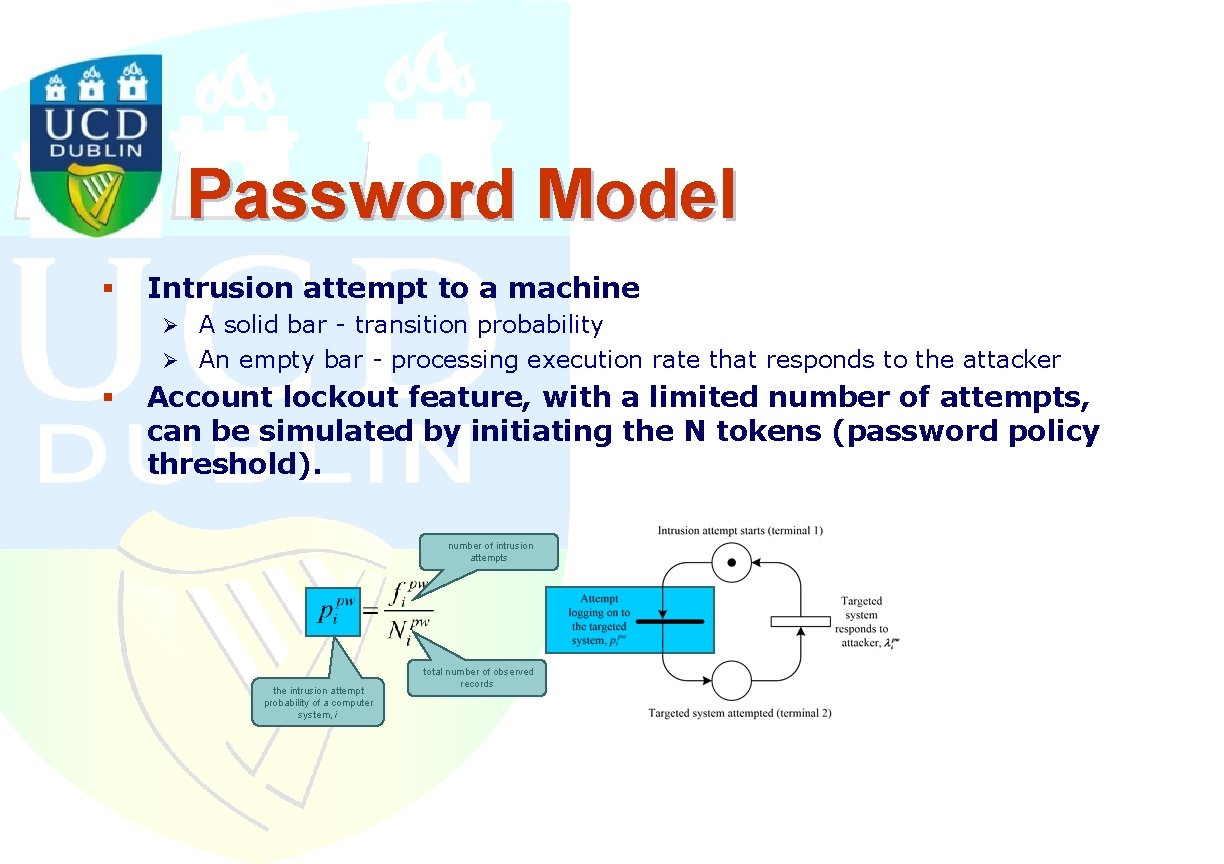
Password Model § Intrusion attempt to a machine Ø A solid bar - transition probability Ø An empty bar - processing execution rate that responds to the attacker § Account lockout feature, with a limited number of attempts, can be simulated by initiating the N tokens (password policy threshold). number of intrusion attempts the intrusion attempt probability of a computer system, i total number of observed records
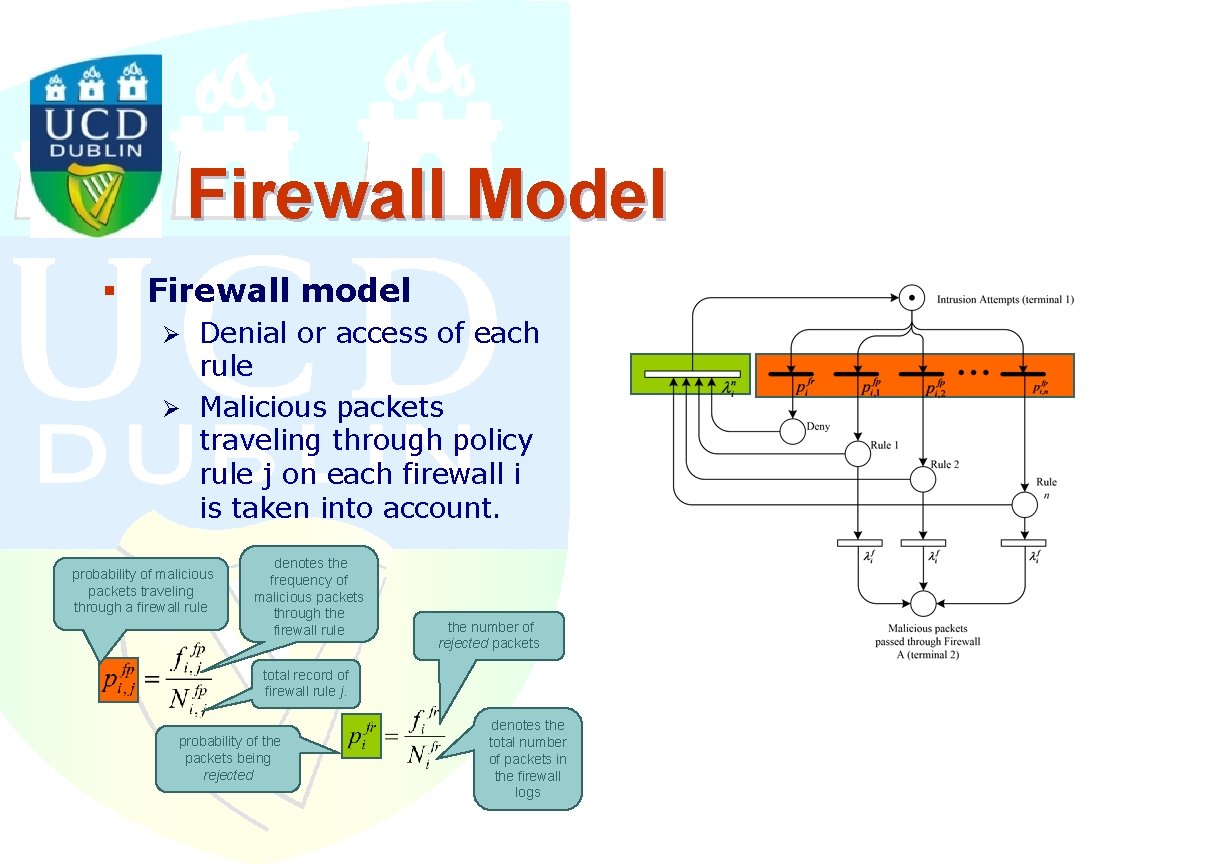
Firewall Model § Firewall model Ø Denial or access of each rule Ø Malicious packets traveling through policy rule j on each firewall i is taken into account. probability of malicious packets traveling through a firewall rule denotes the frequency of malicious packets through the firewall rule the number of rejected packets total record of firewall rule j. probability of the packets being rejected denotes the total number of packets in the firewall logs
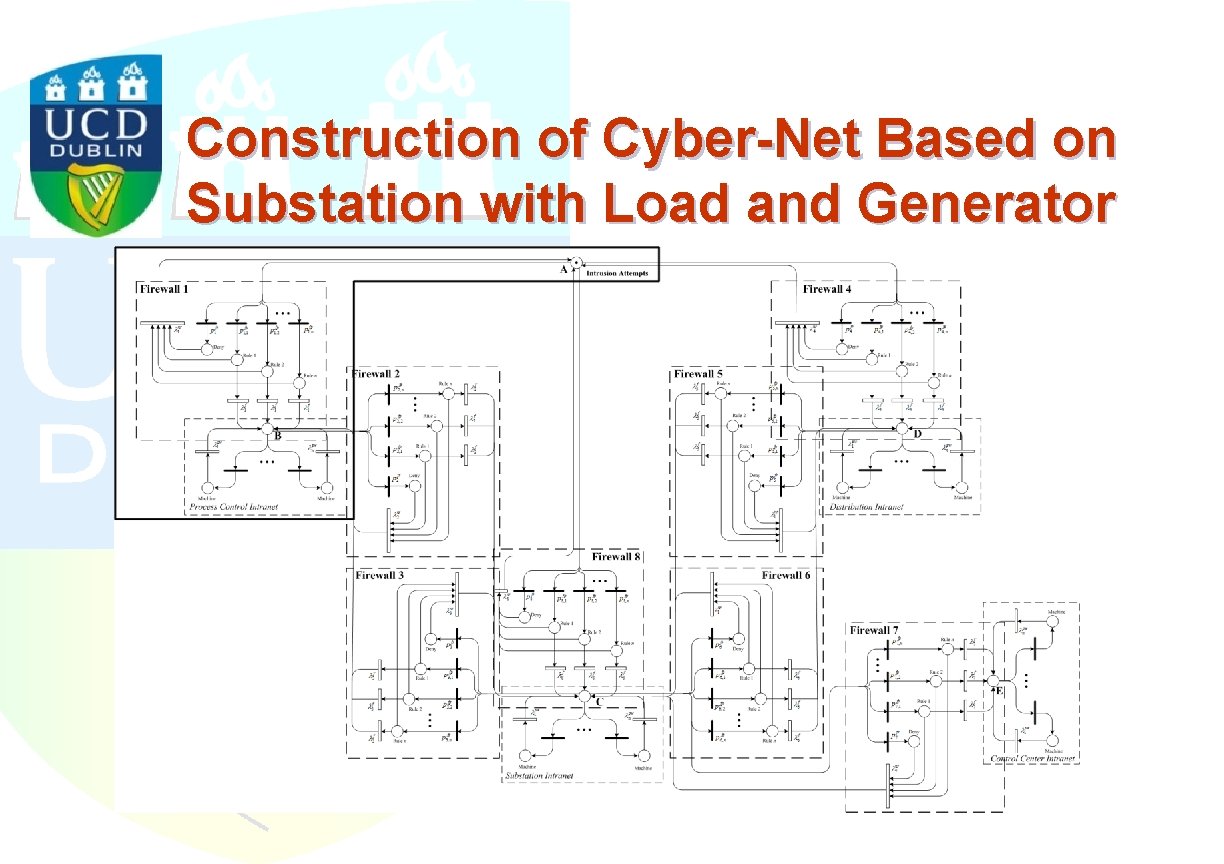
Construction of Cyber-Net Based on Substation with Load and Generator
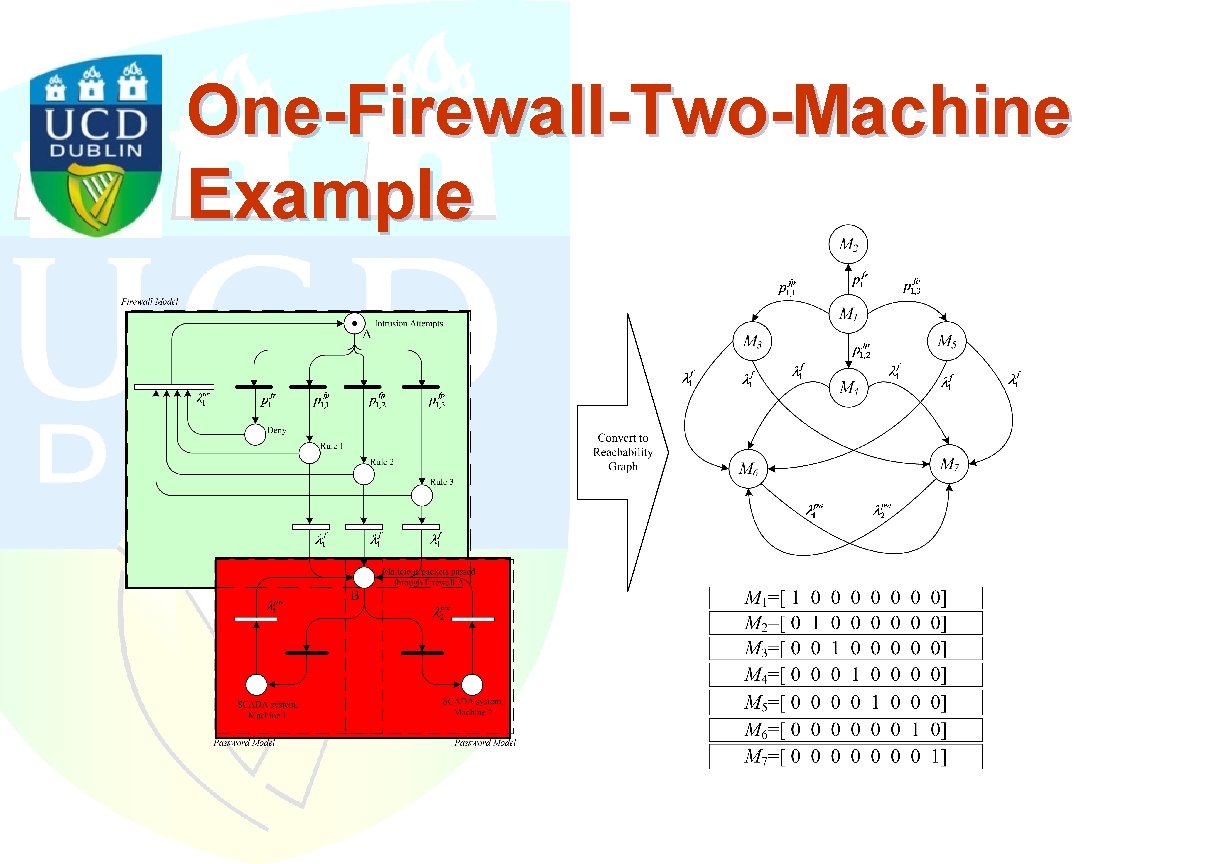
One-Firewall-Two-Machine Example
![Quantitative Analysis of Cyber-Net Suppose the probabilities are Pfp=[. 0095324. 0181514. 0019415], and packet Quantitative Analysis of Cyber-Net Suppose the probabilities are Pfp=[. 0095324. 0181514. 0019415], and packet](http://slidetodoc.com/presentation_image_h2/1651ffefe4059f139c199fa8b509ff76/image-35.jpg)
Quantitative Analysis of Cyber-Net Suppose the probabilities are Pfp=[. 0095324. 0181514. 0019415], and packet rejection Pfr=[. 71457]. An estimated 10% failed logons are assumed for both machines. The rates are assumed to be and M 1, M 3, M 4, and M 5 are induced by immediate transitions M 2, M 6, and M 7 are induced by timed transitions
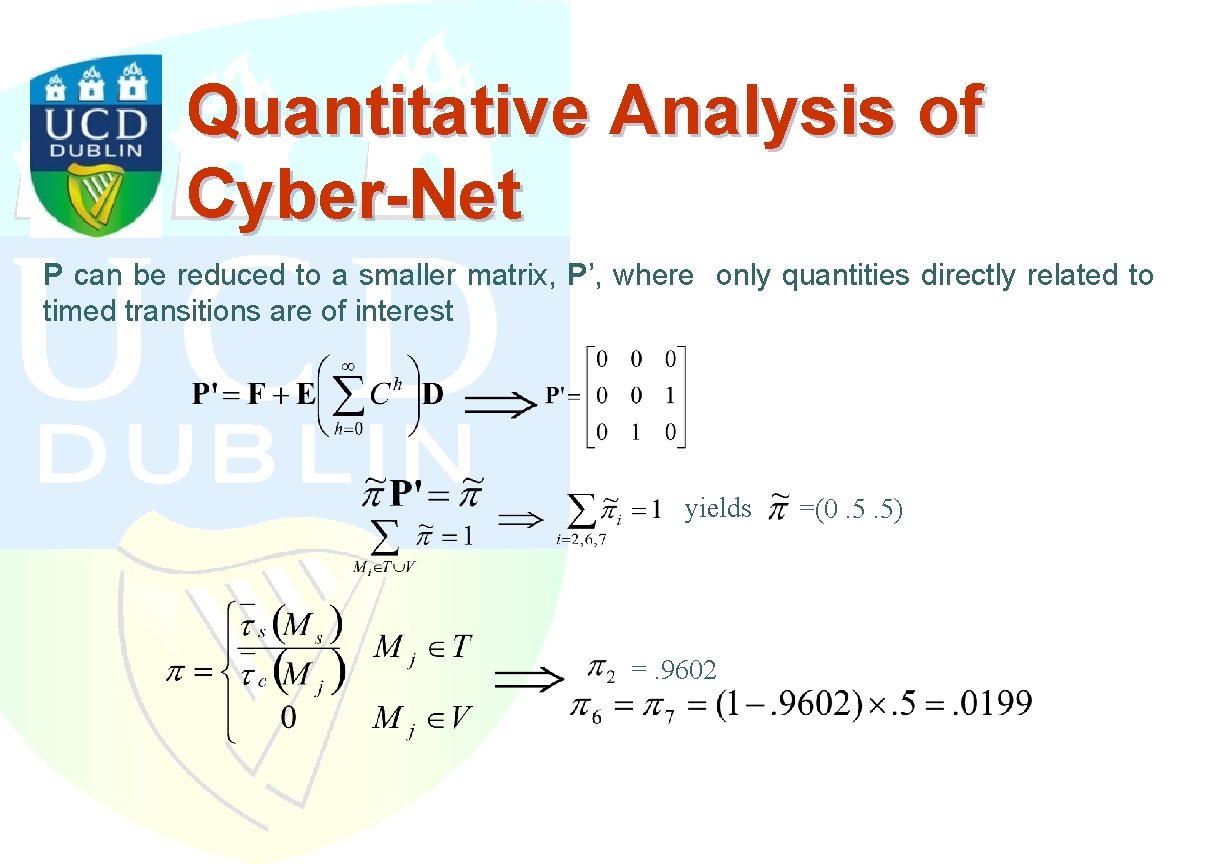
Quantitative Analysis of Cyber-Net P can be reduced to a smaller matrix, P’, where only quantities directly related to timed transitions are of interest yields =. 9602 =(0. 5. 5)
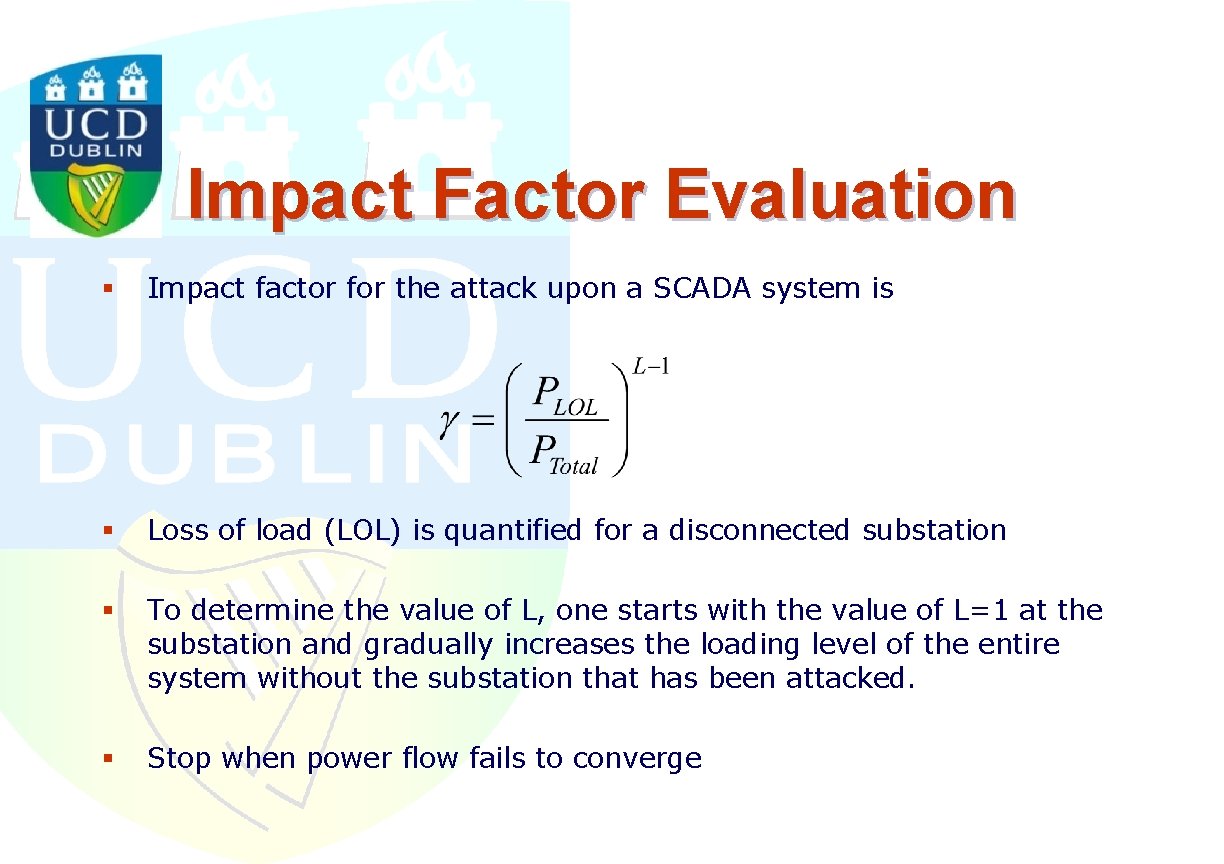
Impact Factor Evaluation § Impact factor for the attack upon a SCADA system is § Loss of load (LOL) is quantified for a disconnected substation § To determine the value of L, one starts with the value of L=1 at the substation and gradually increases the loading level of the entire system without the substation that has been attacked. § Stop when power flow fails to converge
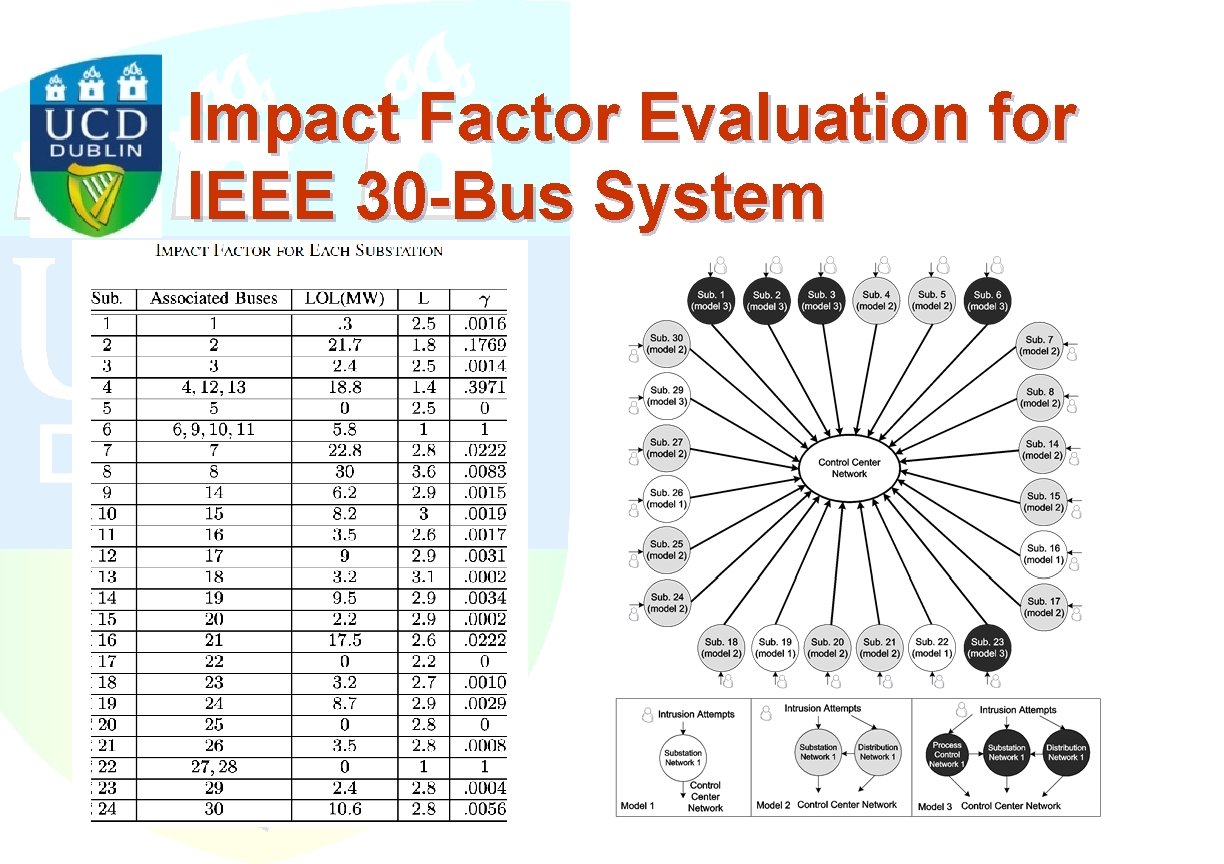
Impact Factor Evaluation for IEEE 30 -Bus System
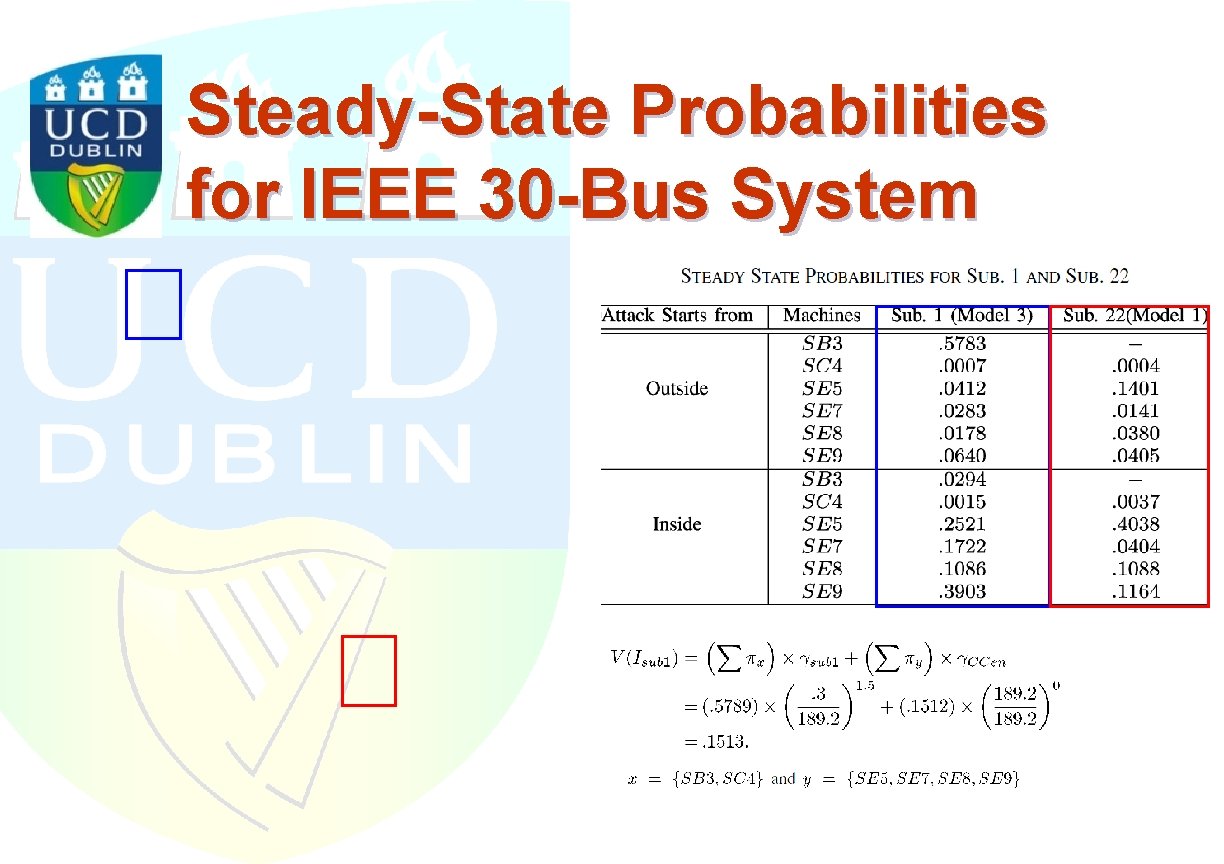
Steady-State Probabilities for IEEE 30 -Bus System

Cyber Security Monitoring and Mitigation

Major Power-Cyber Research Institutions § § ERSE, Milan, Italy TCIP from University of Illinois US National Laboratories. . .

Conclusions § SCADA cyber security enhancements § Anomaly detection and vulnerability analysis against cyber attacks § Evaluation of cyber security on test beds § Awareness and cyber security education

Conclusions § SCADA cyber security enhancements § Anomaly detection and vulnerability analysis against cyber attacks § Evaluation of cyber security on test beds § Awareness and cyber security education

Further Information § § § Chee-Wooi Ten, Chen-Ching Liu, and Manimaran Govindarasu, “Vulnerability Assessment of Cybersecurity for SCADA Systems, " IEEE Transactions on Power Systems, vol. 23, no. 4, pp. 1836 -1846, Nov. 2008. Chee-Wooi Ten, Chen-Ching Liu, and Manimaran Govindarasu, “Anomaly Extraction and Correlations for Power Infrastructure Cyber Systems, ” Proc. e. Networks Cyberengineering Workshop, October 12 -15, 2008, Singapore. Chee-Wooi Ten, Chen-Ching Liu, and Manimaran Govindarasu, “Cyber. Vulnerability of Power Grid Monitoring and Control Systems, ” Proc. 4 th Cyber Security and Information Intelligence Research (CSIIR) Workshop, May 1214, 2008, Oak Ridge, Tennessee, USA. Chee-Wooi Ten, Manimaran Govindarasu, and Chen-Ching Liu, “Cybersecurity for Electric Power Control and Automation Systems, ” Proc. e. Networks Cyberengineering Workshop, IEEE-SMC 2007, Montreal, Canada. Chee-Wooi Ten, Chen-Ching Liu, and Manimaran Govindarasu, “Vulnerability Assessment of Cybersecurity for SCADA Systems Using Attack Trees, ” Proc. IEEE PES General Meeting 2007, Tampa, Florida.
- Slides: 44