Cyber Security Issues in Saudi Arabia Challenges and

Cyber Security Issues in Saudi Arabia: Challenges and Solutions Presented by: Dr, Latifa Saad Alzahrani, An Assistant Professor in the department of Management Information Systems, Taif University : Taif, Saudi Arabia

Research Background • Cyber security has risen to become a national concern • The security and privacy of cyber and cyber-physical systems is increasingly considered a major issue in many industries • Many users are still not knowledgeable about the threats that exist online;

Research Background Most countries are creating cyber security frameworks in order to protect their online services and increase awareness of cyber security. For example, 1 - US 2 - United Kingdom 3 - Australia and Canada

Research Aim The aim of this paper is to investigate and analyze the levels of cyber security awareness (CSA) among higher education students in a business college in Saudi Arabia. It also aims to examine students' knowledge and their attitude towards the following major security issues related to cyber security: cyber risk, cyber security, cyber awareness and cyber trust.
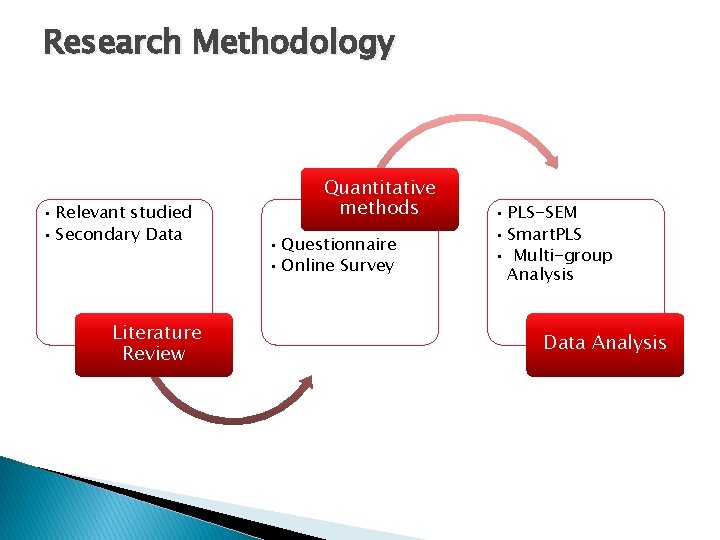
Research Methodology • Relevant studied • Secondary Data Literature Review Quantitative methods • Questionnaire • Online Survey • PLS-SEM • Smart. PLS • Multi-group Analysis Data Analysis

Literature Review • Cyber security has been defined as “the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance, and technologies that could be used for protecting the cyber environment and organization and user’s assets” (Solms & Niekerk, 2013). • Kim (2018) defines cyber security as technologies and processes constructed to protect computers, computer hardware, software, networks, and data from unauthorized access, vulnerabilities supplied through the Internet by cyber criminals, terrorist groups, and hackers.
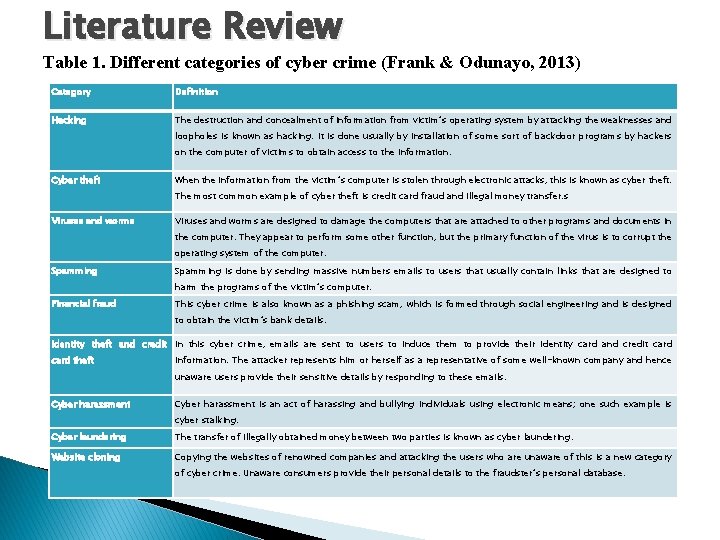
Literature Review Table 1. Different categories of cyber crime (Frank & Odunayo, 2013) Category Definition Hacking The destruction and concealment of information from victim’s operating system by attacking the weaknesses and loopholes is known as hacking. It is done usually by installation of some sort of backdoor programs by hackers on the computer of victims to obtain access to the information. Cyber theft When the information from the victim’s computer is stolen through electronic attacks, this is known as cyber theft. The most common example of cyber theft is credit card fraud and illegal money transfer. s Viruses and worms are designed to damage the computers that are attached to other programs and documents in the computer. They appear to perform some other function, but the primary function of the virus is to corrupt the operating system of the computer. Spamming is done by sending massive numbers emails to users that usually contain links that are designed to harm the programs of the victim’s computer. Financial fraud This cyber crime is also known as a phishing scam, which is formed through social engineering and is designed to obtain the victim’s bank details. Identity theft and credit In this cyber crime, emails are sent to users to induce them to provide their identity card and credit card theft information. The attacker represents him or herself as a representative of some well-known company and hence unaware users provide their sensitive details by responding to these emails. Cyber harassment is an act of harassing and bullying individuals using electronic means; one such example is cyber stalking. Cyber laundering The transfer of illegally obtained money between two parties is known as cyber laundering. Website cloning Copying the websites of renowned companies and attacking the users who are unaware of this is a new category of cyber crime. Unaware consumers provide their personal details to the fraudster’s personal database.

Literature Review • it is crucial to secure financial information that can affect personal financial status. Therefore, there is a vital need for Internet users to understand how to protect themselves from online fraud and identity theft • even though technology has done many things to protect end -users’ information systems, it is argued by security experts that technology alone cannot protect these systems effectively.

Literature Review The reasons behind such a larger number of attacks are a lack of CSA among the general public of Saudi Arabia. Culture also plays a major part in reducing such cyber crime, and the culture of Saudi Arabia is highly censored, patriarchal, and of a tribal nature. A research survey by Alzahrani and Alomar (2016) has revealed that information security awareness is very low and there is a higher level of risk related to cyber space in Saudi Arabia.

Literature Review Because the issue of cyber security is an important topic in Saudi Vision 2030, this study was conducted in Saudi Arabia. Cyber security in Saudi Arabia still faces many challenges that need to be addressed.
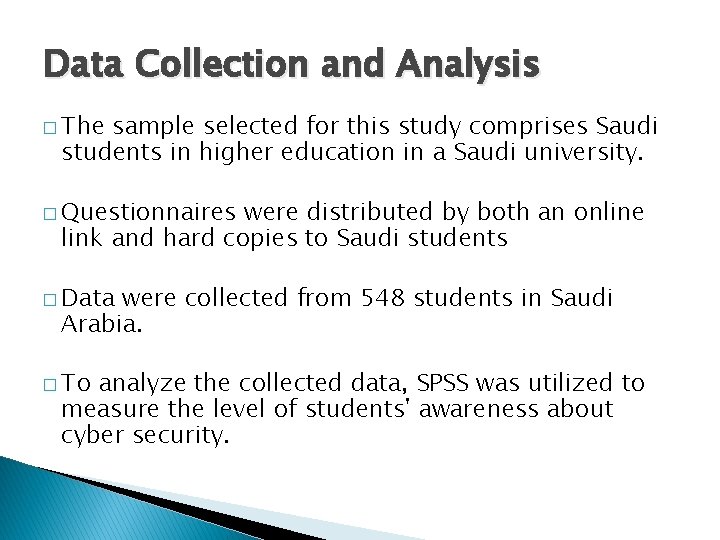
Data Collection and Analysis � The sample selected for this study comprises Saudi students in higher education in a Saudi university. � Questionnaires were distributed by both an online link and hard copies to Saudi students � Data were collected from 548 students in Saudi Arabia. � To analyze the collected data, SPSS was utilized to measure the level of students' awareness about cyber security.

Research Findings • 1 - General Information about Cyber Security • The results in Table 2 show that 82. 5% of students do not know what cyber security means. Table 2. Results for "Do you know what cyber security means? " Valid Frequency Percent (%) Valid (%) Cumulative (%) 96 17. 5 No 452 82. 5 100. 0 Total 548 100. 0 Yes

Research Findings • 1 - General Information about Cyber Security • The results in Table 3 also show that 97. 4% of students are not attending any training or educational programs Table 3. Results for "Are you attending any security training or education programs? " Valid Percent (%) Valid (%) Cumulative (%) 14 2. 6 No 534 97. 4 100. 0 Total 548 100. 0 Yes Frequency
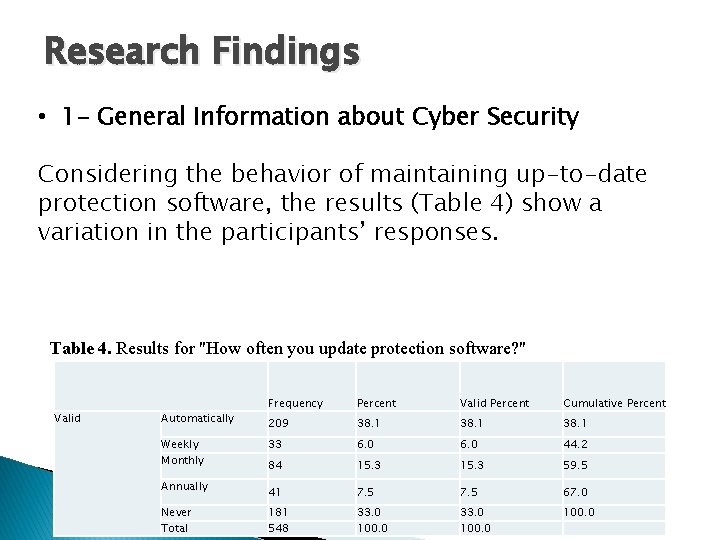
Research Findings • 1 - General Information about Cyber Security Considering the behavior of maintaining up-to-date protection software, the results (Table 4) show a variation in the participants’ responses. Table 4. Results for "How often you update protection software? " Valid Frequency Percent Valid Percent Cumulative Percent 209 38. 1 Weekly Monthly 33 6. 0 44. 2 84 15. 3 59. 5 Annually 41 7. 5 67. 0 Never Total 181 548 33. 0 100. 0 Automatically

Research Findings 2 - Multiple Response Analysis A multiple response analyses was utilized to answer the question, "What types of protection software you use? " As shown in Table 5, 43. 6% of respondents do not have any idea what protection software they are using for protection. Table 5. Results for "What types of protection software you use? " Responses N Percent (%) Percent Cases (%) 229 36. 6 42. 1 Firewall 72 11. 5 13. 2 Anti-spam 12 1. 9 2. 2 Anti-spyware 40 6. 4 7. 4 I don't know 273 43. 6 50. 2 626 100. 0 115. 1 Anti-virus Total a. Dichotomy group tabulated at value 1. of

Research Findings 3 - Factor Analysis Table 6 presents the rotated component matrix, which presents the four groups (components) along with their items. As shown in Table 6, cyber risk has six items and cyber security has four items. Both cyber trust and cyber awareness have three items.
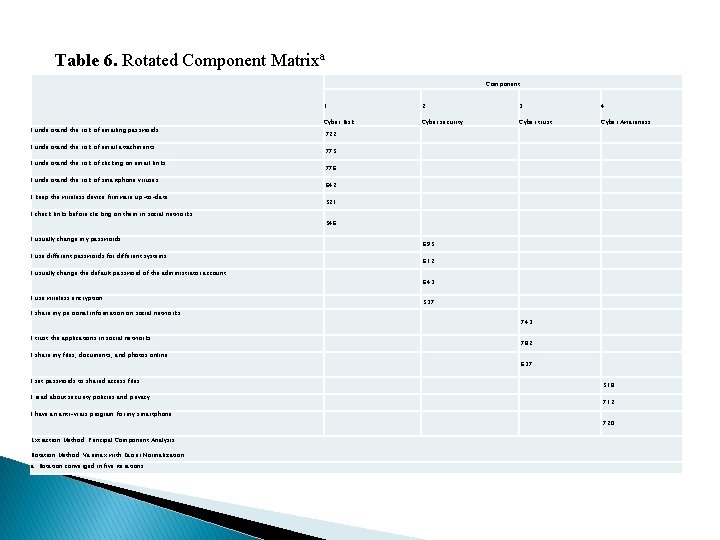
Table 6. Rotated Component Matrixa Component I understand the risk of emailing passwords. I understand the risk of email attachments. I understand the risk of clicking on email links. I understand the risk of smartphone viruses. I keep the wireless device firmware up-to-date. I check links before clicking on them in social networks I usually change my passwords. I use different passwords for different systems. I usually change the default password of the administrator account. I use wireless encryption. I share my personal information on social networks. I trust the applications in social networks. I share my files, documents, and photos online. I set passwords to shared access files. I read about security policies and privacy. I have an anti-virus program for my smartphone. Extraction Method: Principal Component Analysis. Rotation Method: Varimax with Kaiser Normalization. a. Rotation converged in five iterations. 1 2 3 4 Cyber Risk Cyber security Cyber trust Cyber Awareness . 722. 775. 776. 642. 521. 546. 695. 612. 643. 537. 743. 782. 637. 518. 712. 720
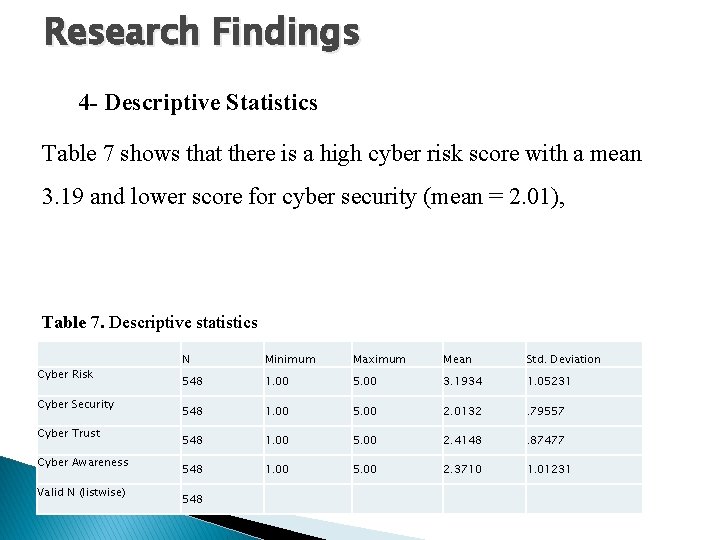
Research Findings 4 - Descriptive Statistics Table 7 shows that there is a high cyber risk score with a mean 3. 19 and lower score for cyber security (mean = 2. 01), Table 7. Descriptive statistics Cyber Risk Cyber Security Cyber Trust Cyber Awareness Valid N (listwise) N Minimum Maximum Mean Std. Deviation 548 1. 00 5. 00 3. 1934 1. 05231 548 1. 00 5. 00 2. 0132 . 79557 548 1. 00 5. 00 2. 4148 . 87477 548 1. 00 5. 00 2. 3710 1. 01231 548

Research Conclusion �The purpose of the current study was to investigate and highlight the cyber security issues and threats in Saudi Arabia. �The most obvious finding to emerge from this study is that there is a lack of awareness of basic cyber security among Saudi students. The second significant finding is that, with respect to training and awareness, the score was surprisingly low (92% of respondents have never had any type of cyber security training). . �

Research Conclusion � The results of this study suggest that Saudi universities should educate their students about anticybercrime law and the significant information security awareness problems found in this study. �

Research Limitations • Context on Saudi Arabia • Methodology • Data Analysis Tool

References Abawajy J. User preference of cyber security awareness delivery methods. Behav Inf Technol 2012; 33: 237– 248. doi: 10. 1080/0144929 x. 2012. 708787. Adams M, Makramalla M. Cybersecurity skills training: An attacker-centric gamified approach. Technol Innovation Manag Rev 2015; 5: 5– 14. Alarifi A, Tootell H, Hyland P. A study of information security awareness and practices in Saudi Arabia. In: 2 nd Int Conf Commun Inf Technol (ICCIT): Digital Inf Manag. Saudi Arabia: IEEE; 2012. p. 6– 12. Alzahrani A, Alomar K. Information security issues and threats in Saudi Arabia: A research survey. Int J Comput Sci Issues 2016; 13: 129– 135. . Atkinson S, Furnell S, Phippen A. Securing the next generation: Enhancing e-safety awareness among young people. Comput Fraud Secur 2009; 7: 13– 19. doi: 10. 1016/s 1361 -3723(09)70088 -0 Eichensehr K. Public-private cybersecurity. Tex L Rev 2017; 95: 467. Elnaim BME. Cyber crime in Kingdom of Saudi Arabia: The threat today and the expected future, Inf. Knowl Manag 2013; 3: 14– 19. Farn K, Lin S, Fung A. A study on information security management system evaluation—assets, threat and vulnerability. Comput Stand Interfaces 2004; 26: 501– 513. doi: 10. 1016/j. csi. 2004. 03. 012 Frank I, Odunayo E. Approach to cyber security issues in Nigeria: Challenges and solution. Int J Cognit Res Sci Eng Educ 2013; 1. Kim L. Cybersecurity matters. Nurs Manag 2018; 49: 16– 22

Any Questions
- Slides: 23