Cyber Security Framework for States and Cities COCON

Cyber Security Framework for States and Cities COCON International Cyber Security and Policing Conference Aug 19 th 2016 Rama Vedashree (rama@dsci. in) Data Security Council of India 1 A NASSCOM® Initiative
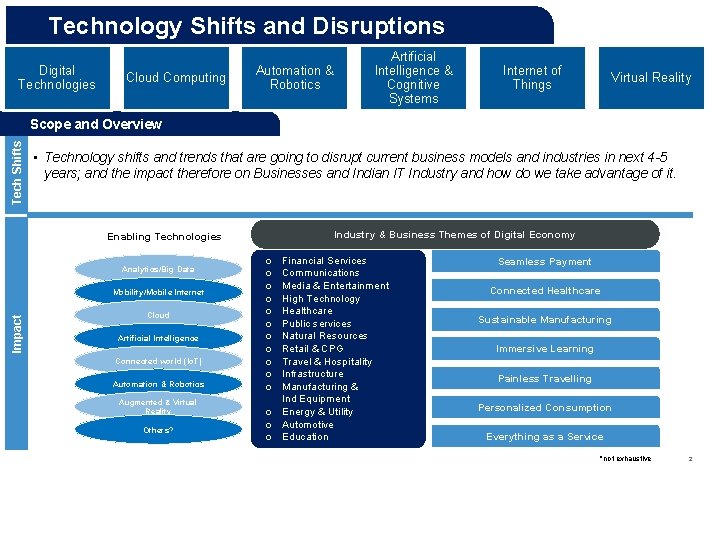
Technology Shifts and Disruptions Digital Technologies Cloud Computing Automation & Robotics Artificial Intelligence & Cognitive Systems Internet of Things Virtual Reality Tech Shifts Scope and Overview • Technology shifts and trends that are going to disrupt current business models and industries in next 4 -5 years; and the impact therefore on Businesses and Indian IT Industry and how do we take advantage of it. Industry & Business Themes of Digital Economy Enabling Technologies Analytics/Big Data Impact Mobility/Mobile Internet Cloud Artificial Intelligence Connected world (Io. T) Automation & Robotics Augmented & Virtual Reality Others? Financial Services Communications Media & Entertainment High Technology Healthcare Public services Natural Resources Retail & CPG Travel & Hospitality Infrastructure Manufacturing & Ind Equipment o Energy & Utility o Automotive o Education o o o Seamless Payment Connected Healthcare Sustainable Manufacturing Immersive Learning Painless Travelling Personalized Consumption Everything as a Service *not exhaustive 2
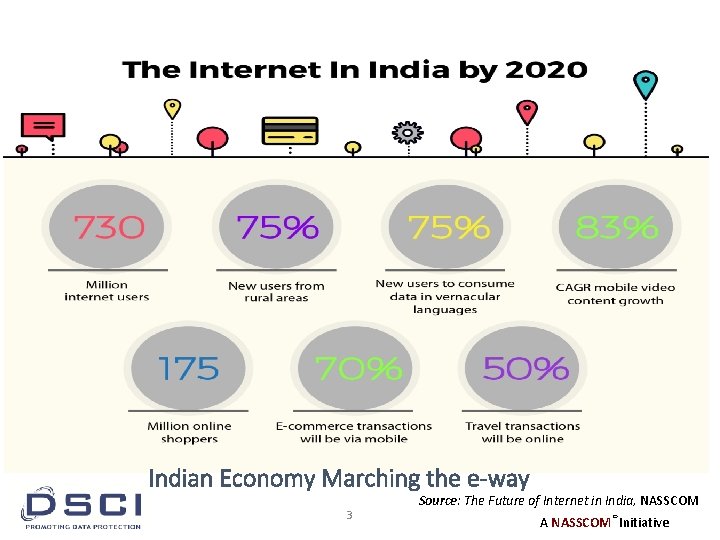
Indian Economy Marching the e-way 3 Source: The Future of Internet in India, NASSCOM A NASSCOM® Initiative
Smart Cities A NASSCOM® Initiative
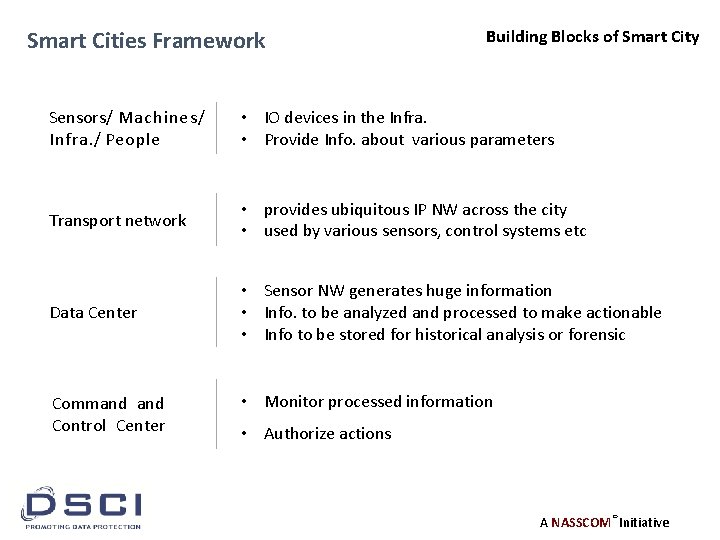
Smart Cities Framework Building Blocks of Smart City Sensors/ Machines/ Infra. / People • IO devices in the Infra. • Provide Info. about various parameters Transport network • provides ubiquitous IP NW across the city • used by various sensors, control systems etc Data Center • Sensor NW generates huge information • Info. to be analyzed and processed to make actionable • Info to be stored for historical analysis or forensic Command Control Center • Monitor processed information • Authorize actions A NASSCOM® Initiative
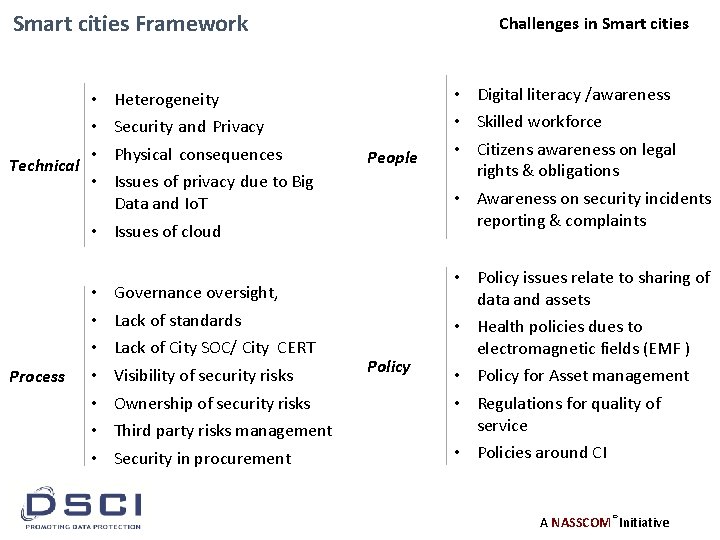
Smart cities Framework • • • Technical • Challenges in Smart cities People • Digital literacy /awareness • Skilled workforce • Citizens awareness on legal rights & obligations • Awareness on security incidents reporting & complaints Policy • Policy issues relate to sharing of data and assets • Health policies dues to electromagnetic fields (EMF ) • Policy for Asset management • Regulations for quality of service • Policies around CI Heterogeneity Security and Privacy Physical consequences Issues of privacy due to Big Data and Io. T • Issues of cloud Process • • Governance oversight, Lack of standards Lack of City SOC/ City CERT Visibility of security risks Ownership of security risks Third party risks management Security in procurement A NASSCOM® Initiative

Smart cities Framework Recommendations 1. Public, Private and People Partnership • To ensure Cyber security and Privacy, Safety, Reliability, and Resiliency at an inception stage, a “ 4 P” (Public, Private and People Partnership) ecosystem approach would need to be followed. 2. Creating synergies between various systems - Interoperability • Data from multiple sensors providing different perspectives to the same problem • For more insights and reducing the overall costs interoperability is to be maintained 3. Integration of Smart City Infrastructure Management System across multiple cities / state • There would be a need to share application information for city services between two cities which may be running on different platforms • It requires that data structures / models need to be standardized for all utilities / services for which information needs to be shared across platforms. A NASSCOM® Initiative

Smart cities Framework Recommendations 4. Chief Security Office • The smart city should have a designated Chief Security Officer (CSO) responsible for the converged security of cyber assets, physical assets and people. 5. Incident Management • Threat to the security of the ICT systems and digital information in a smart city should be detected, analyzed and dealt with using threat intelligence services 6. City Command Control Operation • A hub where the converged (physical and cyber) processed information is being monitored on a 24 x 7 basis and actions being authorized based upon the information received. A NASSCOM® Initiative

Smart cities Framework Cyber Security Protections Securing the Infrastructure • Infra of smart city carries information about the city health e. g. traffic, security information, parking information, along with citizen centric data which might be confidential in nature e. g. energy utilization, video feeds around specific areas etc. • Hence it is very important that the infrastructure used for the system be highly secure. Transport Layer Security • Securing the physical assets, and ensuring that no unauthorized tapping of the fiber/ power line infrastructure • All information flowing on the network can be encrypted to ensure that there is no snooping on the wire leading to loss of confidential data • Devices at each endpoint of the line to be authenticated using passwords and the encryption keys Operational Technology Security/ Sensor Network Security • Sensors deployed to send information to the control systems need to be authenticated before they can start to send any information. A NASSCOM® Initiative

Smart cities Framework Cyber Security Protections Data Center Security • Security breach into the Data Center would lead to loss of data or data being manipulated • A defense in depth approach needs to be taken for the DC to secure each and every layer and entry point into the DC. Securing the Processes • Operational technology and information technology processes have to overlap to ensure that the right operational controls are implemented at the information technology layer. Application Security • Applications should be developed using a Secure SDLC approach, and goes through a security assessment to conform compliance to the security policies of the CISO • Infrastructure should be deployed for the pilot of the services in a secure manner Backup, archiving and recovery • Strategy for data backup, archival and recovery and its governance should be defined • Data retention duration should be carefully considered Domain Name System • Clear naming scheme for each of the connected objects is very important and number of devices connected in smart city NW is of very large magnitude A NASSCOM® Initiative

Recommendations on Cybersecurity Framework for States P-P-P Model for Cybersecurity • State Cybersecurity Framework shall be envisaged in P-P-P model • Government shall partner with the private sector and the academia to strengthen cybersecurity posture of the state Information Security Policy and Practices • IS policies & practices shall be mandated at govt. functionaries & its service providers • Security Audit adhering to international standards applicable for all govt. websites, applications before hosting and publishing • Govt. to ensure ISPs operating in the state shall deploy cybersecurity plans in line with State cybersecurity policy State Computer Emergency Response Team • Establishment of the State CERT to operate in conjunction I-CERT and coordinate with NCIIPC • Cybersecurity drills shall be carried out under the supervision of I-CERT Identity Theft and Security Incident Prevention • State cybersecurity framework to support strategy and implementation mechanisms to prevent digital impersonation and identity theft and the security incidents A NASSCOM® Initiative
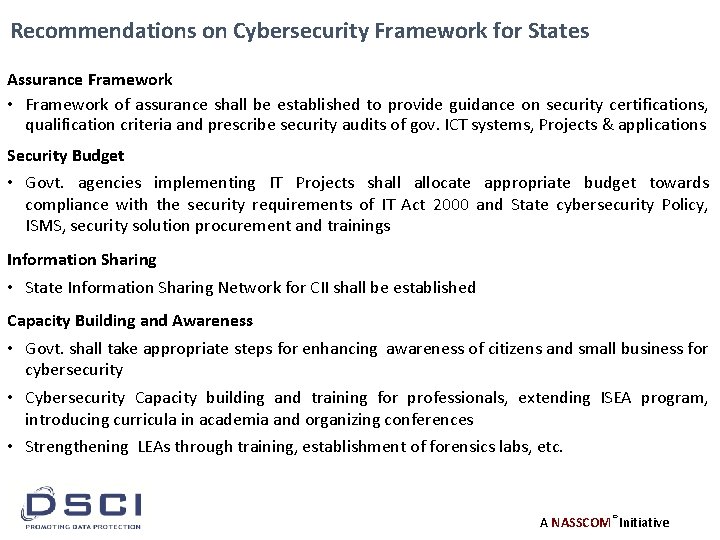
Recommendations on Cybersecurity Framework for States Assurance Framework • Framework of assurance shall be established to provide guidance on security certifications, qualification criteria and prescribe security audits of gov. ICT systems, Projects & applications Security Budget • Govt. agencies implementing IT Projects shall allocate appropriate budget towards compliance with the security requirements of IT Act 2000 and State cybersecurity Policy, ISMS, security solution procurement and trainings Information Sharing • State Information Sharing Network for CII shall be established Capacity Building and Awareness • Govt. shall take appropriate steps for enhancing awareness of citizens and small business for cybersecurity • Cybersecurity Capacity building and training for professionals, extending ISEA program, introducing curricula in academia and organizing conferences • Strengthening LEAs through training, establishment of forensics labs, etc. A NASSCOM® Initiative
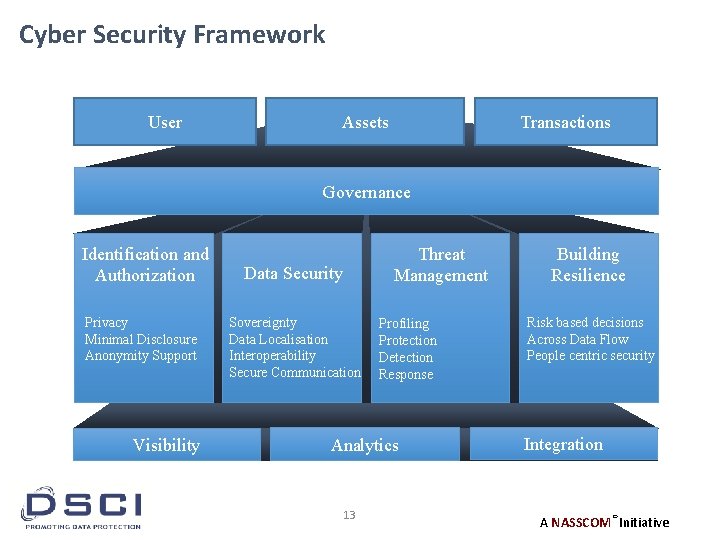
Cyber Security Framework User Assets Transactions Governance Identification and Authorization Privacy Minimal Disclosure Anonymity Support Visibility Threat Management Data Security Sovereignty Data Localisation Interoperability Secure Communication Profiling Protection Detection Response Analytics 13 Building Resilience Risk based decisions Across Data Flow People centric security Integration A NASSCOM® Initiative
Thank You 14 A NASSCOM® Initiative
- Slides: 14