CYBER CRIME Cybercrime also called computer crime the

CYBER CRIME

Cybercrime, also called computer crime, the use of a computer as an instrument to further illegal ends, such as committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy. Cybercrime, especially through the Internet, has grown in importance as the computer has become central to commerce, entertainment, and government. Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most, but not all, cybercrime is committed by cybercriminals or hackers who want to make money. Cybercrime is carried out by individuals or organizations. Some cybercriminals are organized, use advanced techniques and are highly technically skilled. Others are novice hackers. Rarely, cybercrime aims to damage computers for reasons other than profit. These could be political or personal.

Types of cybercrime Email and internet fraud. Identity fraud (where personal information is stolen and used). Theft of financial or card payment data. Theft and sale of corporate data. Cyber-extortion (demanding money to prevent a threatened attack). Ransomware attacks (a type of cyber-extortion). Crypto-jacking (where hackers mine cryptocurrency using resources they do not own). Cyberespionage (where hackers access government or company data).

Classification of Cyber Crimes Cyber crimes have been classified on the basis of the nature and purpose of the offence and have been broadly grouped into three categories depending upon the target of the crime. It may be against person, property or Government. Against person – hate messages, cyber/online stalking, cyber defamation, and transmission of illicit content. Against property – trespass, vandalism, transmission of harmful programmes and unauthorised possession of computerised information. Against Government – Hacking the websites, cyber terrorism.

David L. Carter has classified cyber crimes into three categories – 1. Where computer is the target of the crime 2. Where computer facilitates the commission of crime 3. Where computer is incidental to the crime
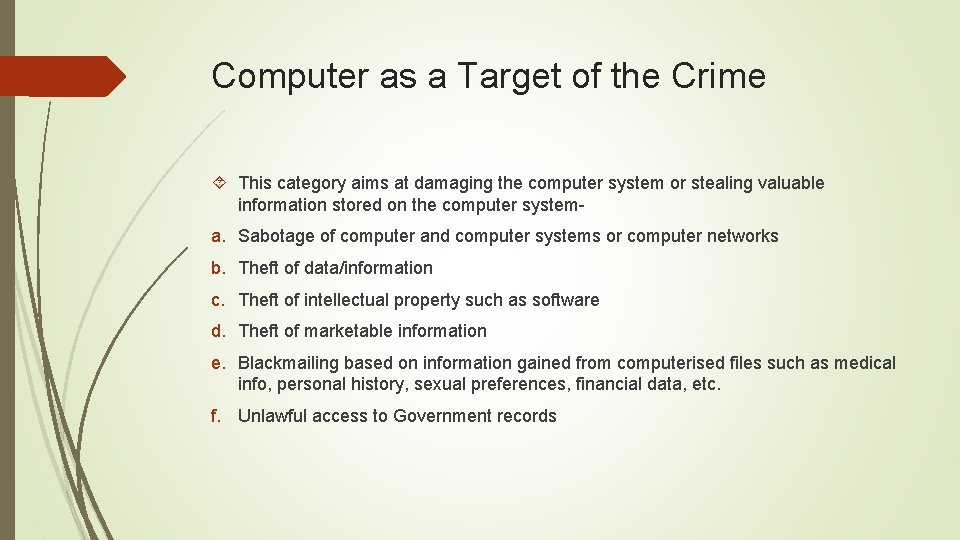
Computer as a Target of the Crime This category aims at damaging the computer system or stealing valuable information stored on the computer systema. Sabotage of computer and computer systems or computer networks b. Theft of data/information c. Theft of intellectual property such as software d. Theft of marketable information e. Blackmailing based on information gained from computerised files such as medical info, personal history, sexual preferences, financial data, etc. f. Unlawful access to Government records

Computer as an instrument of crime The cyber crimes falling under this category uses a computer as a medium for the commission of crime. The computer programmes are manipulated to defraud others – 1. Fraudulent use of ATM cards and accounts 2. Credit card frauds 3. Frauds involving electronic fund transfer 4. Frauds involving stock transfer 5. Frauds related to e-commerce 6. Telecommunication frauds

Computer as incidental to the crime The diverse application and use of the Internet made it incidental to the crimes that may be classified as – A. Internet crime B. Web based crime

Internet crime It includes that group of crimes that make the criminal use of the Internet Infrastructures. These maybe – i. Hacking i. e. theft of information, passwords, credit card numbers ii. Launch of malicious programmes iii. Espionage iv. Spamming
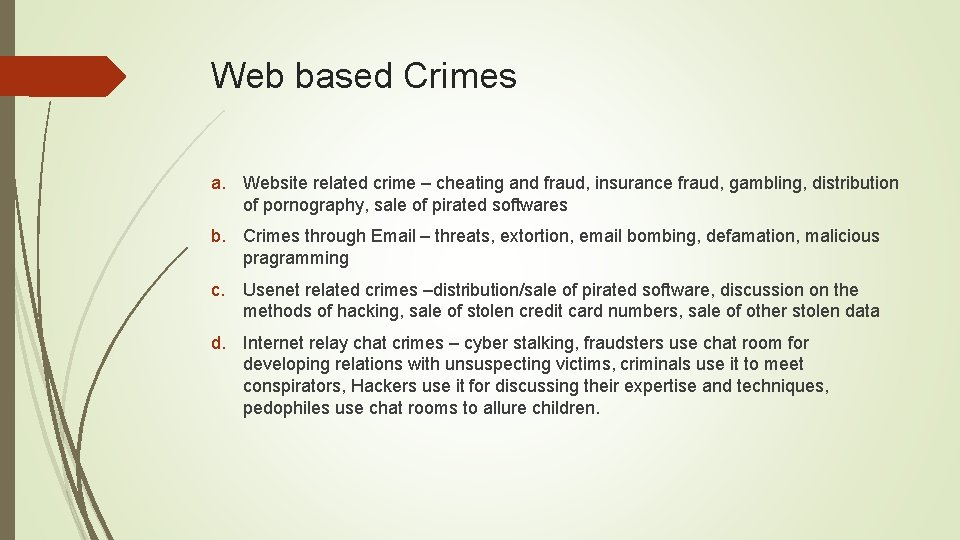
Web based Crimes a. Website related crime – cheating and fraud, insurance fraud, gambling, distribution of pornography, sale of pirated softwares b. Crimes through Email – threats, extortion, email bombing, defamation, malicious pragramming c. Usenet related crimes –distribution/sale of pirated software, discussion on the methods of hacking, sale of stolen credit card numbers, sale of other stolen data d. Internet relay chat crimes – cyber stalking, fraudsters use chat room for developing relations with unsuspecting victims, criminals use it to meet conspirators, Hackers use it for discussing their expertise and techniques, pedophiles use chat rooms to allure children.
- Slides: 10