Cyber Attacks CLIENT AND SERVER SIDE Introduction With

Cyber Attacks CLIENT AND SERVER SIDE

Introduction With advent of Business-to-Business (B 2 B) and Business-to. Consumer (B 2 C) interaction, it is has become a necessity that information must be exchanged in a secure and accurate way. Most of the web application contains security vulnerabilities which enables attacker to exploit them and launch attack. As a result of attack confidentiality, integrity and availability of information are lost.
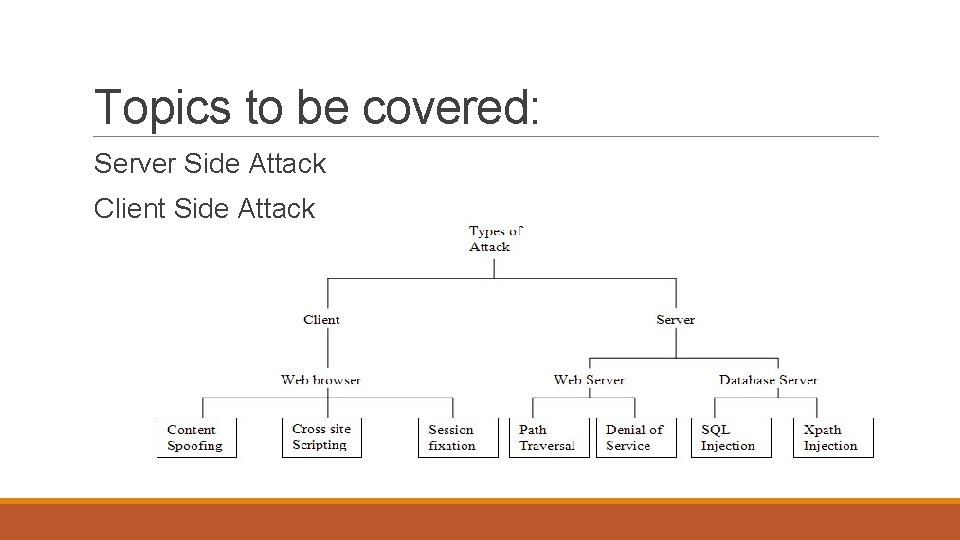
Topics to be covered: Server Side Attack Client Side Attack

Need for securing web applications 1. Rapid increase in attack 2. Cost of attack

What is Server Side Attack? ? The Server-Side Includes attack allows the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary codes remotely. It can be exploited through manipulation of SSI in use in the application or force its use through user input fields. There are further 2 types of attacks broadly classified as : 1. Web Server 2. Database Server

Web Server side attack target web server for downloading or viewing files like scripts, configuration files without proper authorization. They use path traversal attack to achieve this file disclosure. Other form of web server attack like denial of service attack prevents legitimate user from using service by flooding web server with messages. Due to heavy traffic and limited capacity the web server's resource are exhausted and is unable to process request of legitimate user.
Database Server side attack like SQL injection and Xpath injection target database server to retrieve information without proper authentication and authorization. Both these attack are possible when application uses user input to dynamically generate query without sanitizing them
Server Side Attacks Web Server: Database Server: 1. Path Traversal Attack 1. SQL Injections 2. Denial of Service(DOS) 2. XPath

Path traversal attack Web servers generally allow access to a specific portion of the Web server's file system called the "Web document root" directory. In path traversal attack, attacker accesses files and directories that are outside web document directory. They do this by using special character sequences in URL input parameter like. . / which allows to access parent folder of a subfolder.
Example In some cases web application loads text from static file to render web page. Like URL below uses home variable to load index page. http: //webpage/update. cgi? home=index. htm The attacker can change URL parameter to replace index. htm with update. cgi to get source code of script update. cgi. http: //webpage/update. cgi? home=update. cgi

What can be done to prevent it ? To prevent attacker from executing operating system commands, Web root directories and virtual directories must be kept in non-system partition, since it is not possible to traverse across drives. If system is installed on C: drive , web site and content must be moved to E: drive, and virtual directory should point to the new drive.

Denial of Service Denial of service attack aims to prevent legitimate users from using a service. This is usually done by consuming all of a resource used to provide the service like CPU, operating system memory etc. Attacker may launch attack by bombarding website with numerous messages. If the attack is carried out by thousands of machines, than it is called distributed denial of service attack.

Example A web server takes a certain amount of time to serve web page requests, which limits the maximum number of requests which can be handled by web server in a finite amount of time. If it is assumed that a web server can process 1000 requests per second to retrieve file and serve home page, than at most 1000 customer's request can be processed concurrently. Normally the web server receives 50 -70 requests per second. If attacker controls 10, 000 machines and makes them send request every 10 second, than web server will receive 1000 request per second which when combined with normal traffic makes total request 1050 -1070 request which exceeds the maximum capacity that web server can handle. The web server is not able to handle legitimate requests because of saturation.

What can be done to prevent it ? 1. Attacks can be prevented by identifying software bug or error in application design and patching up with latest patches. 2. Reverse turing test can be employed to make sure that a there is a human user at other end of connection. 3. Sources should be validated to verify the user’s identity before granting service request.

Code Injection In this kind of attack, attacker manipulates input parameters to inject malicious code which executes at server side to perform operations violating security of data. SQL injection and Xpath injection are two different kinds of attack under this category targeting database. Xpath injection is more severe, since the attacker is able access to all information, unlike SQL injection where the administrator can restrict user from accessing all information. Xpath as same syntax , unlike SQL where, different vendors have different syntaxes.
SQL Injection In SQL injection attacker provides user input which becomes part of SQL query. Dynamically generated query when executed on database server without proper check could let attacker retrieve authorized information without proper authentication and authorization.
Example: Consider a website which requires user to provide login name and password to access account information. The user name and password is used to generate SQL statement. Therefore, if a user submits login and password as “abc” and “xyz, ” the servlet dynamically builds the query: SELECT info FROM users WHERE login=’abc’ AND pass=’xyz’ If attacker enters “’ OR 1=1 --” and “”, instead of “abc” and “xyz”, the resulting query is: SELECT info FROM users WHERE login=’’ OR 1=1 --’ AND pass=’’
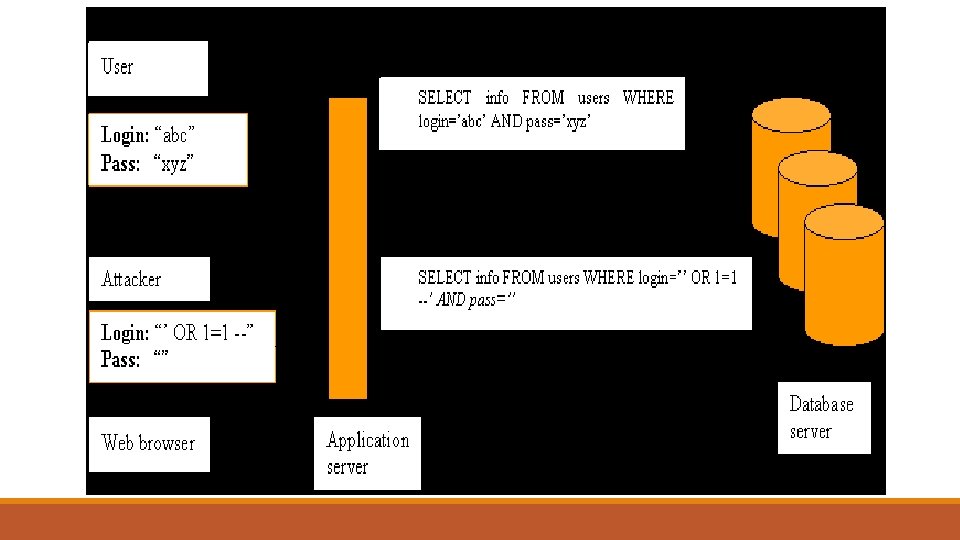

The single quote before OR keyword neutralizes opening quote. Presence of the “OR 1=1” clause after WHERE clause turns this conditional into a tautology. The characters “--” denotes the beginning of a comment, so everything after them is ignored. Hence the password condition is disabled by attacker. As a result, the database would return information about all users

What can be done to prevent it ? 1. Validating all string input for SQL keywords and escape all single quotes 2. Restricting access to standard database functions and procedures 3. Restricting access to custom database stored procedures
Xpath injection XPath is used to query XML database is represented using an XML document and XPath query is similar to an SQL query. XPath queries are used for search requests, for login processing, for data retrieval, and other lightweight database tasks. XPath injection takes place in web site, which constructs XPath from User input.

Example: Consider a XML document with three elements: User name, password and checking account number. The XPath expression to retrieve account number requires user to give user name and password : string(//user[name/text()='abc' and password/text()='abc']/account/text()) If the attacker enters following string in username field: ' or 1=1 or ' '=' , the Xpath expression would be: string(//user[name/text()='' or 1=1 or ' '=' ' and password/text()='xyz']/account/text()) Since 1=1 is a tautology, the attacker can login as first user listed in XML document.

Dangers involved in Xpath injection is even more severe than SQL injection. 1. XPath allows one to query all items of the database, unlike SQL DBMS in which user might restrict to some tables using access control. 2. Since XPath is a standard language compared to SQL, it is much easier to launch attack.

What can be done to prevent it ? Defending against XPath Injection is essentially similar to defending against SQL injection 1. Disallowing the single and double quote characters. This can be done either in the application itself, or in a third party product (e. g. application firewall. ) 2. Testing application susceptibility to XPath Injection can be easily performed by injecting a single quote or a double quote, and inspecting the response. If an error has occurred, then it’s likely that an XPath Injection is possible.

Content Spoofing In this type of attack malicious hackers would create fake website with look similar to original one to make user believe that the site is legitimate. They would create fake website for banks such as Citibank, online organization such as Pay. Pal and e. Bay. Attacker would than send specially crafted links through email, instant messages to user. The messages may look quite authentic, having corporate logos and formats similar to the ones used by legitimate messages. Typically they would ask for verification of certain information such as account numbers and passwords. These links would make user believe that the content is coming from trusted website, but in fact they would be from external source.
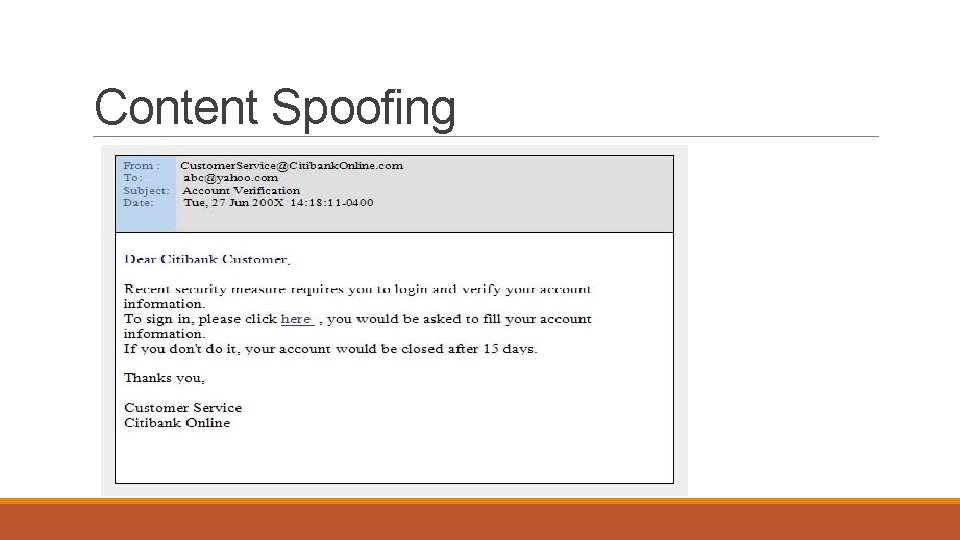
Content Spoofing
Cross Site Scripting In cross-site scripting (XSS) malicious code is executed in user’s browsers which are usually written in VBScript, Active. X, java etc. The code is echoed by web site to user’s browser. The code is placed in web site by attacker using message boards, bulletins etc. When these pages are viewed by user, the script present in messages is executed at user end. These scripts may read, modify or transmit data accessible by client’s browser.
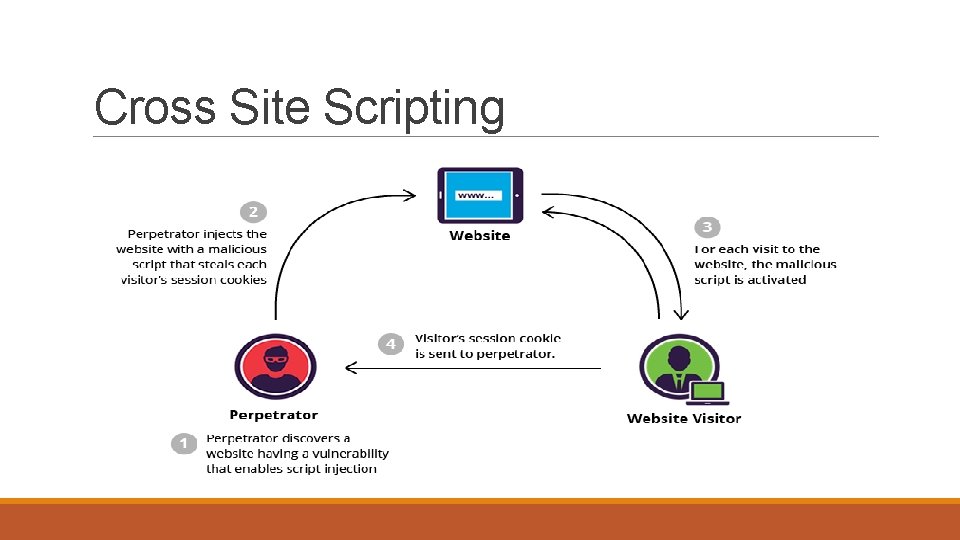
Cross Site Scripting

Session Fixation HTTP was designed purely for document exchange. It is incapable of session management. It does not provide any way for web server to maintain states for user's subsequent requests. To perform session management web server generates session identifier which is sent to user's browser. In each subsequent request web browser sends this session identifier (sessionid) back to web server. Session ID thus can be used to identify users. In session fixation attack, attacker fixes the Session ID of victim. Since the session ID, which is used by the victim, is fixed by attacker, attacker is able to access account of the victim by using same session ID to connect to his account without any authentication. Session fixation allows attacker to get access to the application with same privileges of the user whose session he steals.

Session Fixation The session fixation attack is normally a three step process : Session set-up The attacker connects to website to obtain session ID, which would be introduced in user's browser. Session fixation The attacker introduces the session value obtained in last step into the users browser by making him click on a URL containing session ID which is obtained in last step (The URL link can be sent by attacker to victim). When the user clicks on URL sent by attacker, his session ID is fixed to the session ID value contained in URL.
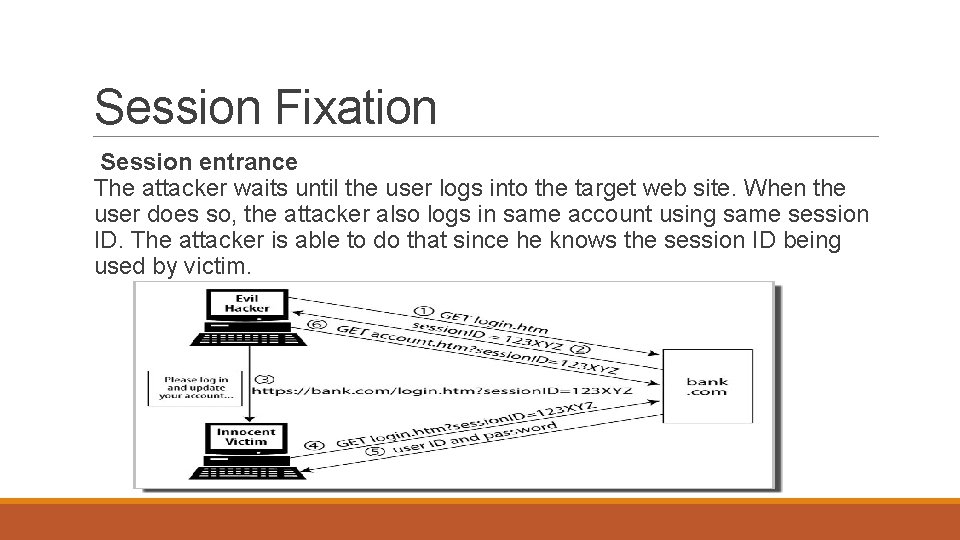
Session Fixation Session entrance The attacker waits until the user logs into the target web site. When the user does so, the attacker also logs in same account using same session ID. The attacker is able to do that since he knows the session ID being used by victim.
Thank You : )
- Slides: 32