Cyber Attacks and Cryptography Overview Security Objectives l

Cyber Attacks and Cryptography Overview

Security Objectives l Confidentiality l Integrity How can we define these concepts wrt. the Internet? l Availability l Authentication l Non-repudiation Internet Security - Farkas 2

Types of Attacks (1) § Interruption – an asset is destroyed, unavailable or § § unusable (availability) Interception – unauthorized party gains access to an asset (confidentiality) Modification – unauthorized party tampers with asset (integrity) Fabrication – unauthorized party inserts counterfeit object into the system (authenticity) Denial – person denies taking an action (authenticity) Internet Security - Farkas 3

Types of Attacks (2) § Passive attacks: § Eavesdropping § Monitoring § Active attacks: § Masquerade – one entity pretends to be a different entity § Replay – passive capture of information and its § § retransmission Modification of messages – legitimate message is altered Denial of service – prevents normal use of resources Internet Security - Farkas 4
Protection l Protection at storage – Inactive (e. g. , databases storage, file system) – During processing (e. g. , DBMS access, application access) l Protection during transmission – Level of protection (e. g. , content vs. header info) – Aim of protection (e. g. , confidentiality, integrity, privacy, etc. ) Internet Security - Farkas 5

Basic Defense Mechanisms Usable security! l Identification and Authentication l Authorization l Cryptography l Hardware, software security – Tampering avoidance – Information leakage prevention – Input validation l Network-protection: communication, firewall, IDS, etc. Internet Security - Farkas 6

Attacks Against Communication Channels Internet Security - Farkas 7

Insecure communications Confidential Insecure channel Recipient Sender Encryption: confidential communication Internet Security - Farkas 8

Encryption Does it support? l Confidentiality l Integrity l Availability l Authentication (pair-wise, third party) l Non-repudiation Internet Security - Farkas 9

Terminology § Plaintext (cleartext): a message in its original § § § form Ciphertext (cyphertext): an encrypted message Encryption: transformation of a message to hide its meaning Cipher: cryptographic algorithm. A mathematical function used for encryption (encryption algorithm) and decryption (decryption algorithm). Internet Security - Farkas 10
Terminology §Decryption: recovering meaning from ciphertext §Cryptography: art and science of keeping messages secure §Cryptanalysis: art and science of breaking ciphertext §Cryptology: study of both cryptography and cryptanalysis Internet Security - Farkas 11

CONTINUE FROM 08/29 Internet Security - Farkas 12
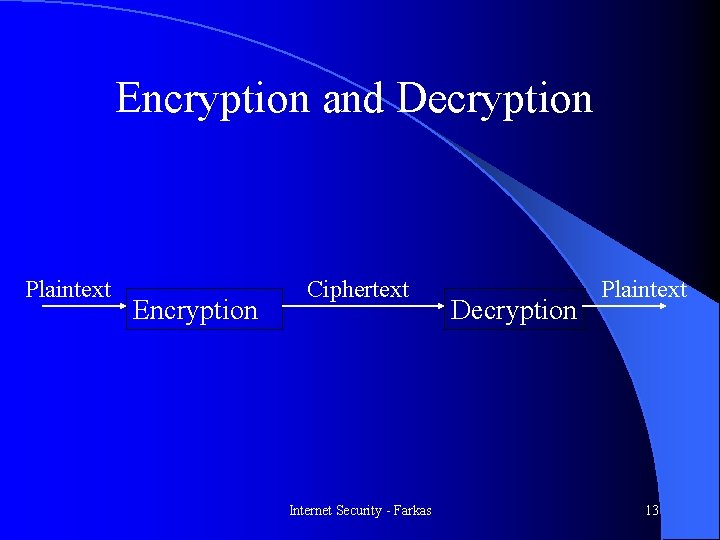
Encryption and Decryption Plaintext Encryption Ciphertext Internet Security - Farkas Decryption Plaintext 13
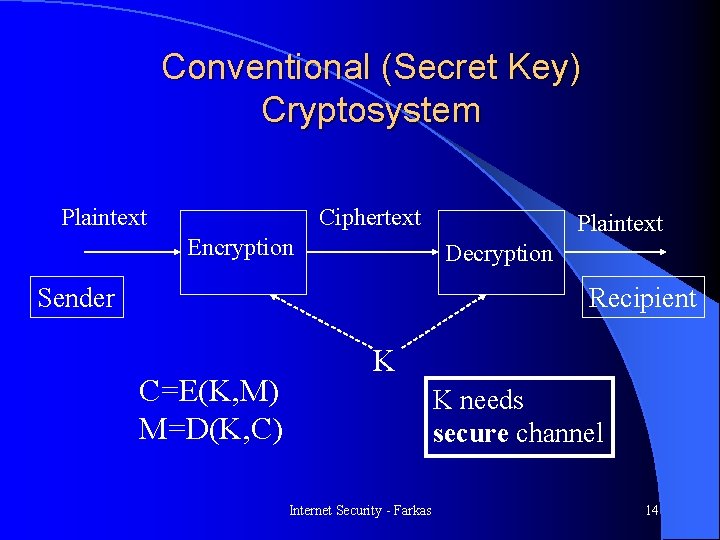
Conventional (Secret Key) Cryptosystem Plaintext Ciphertext Encryption Plaintext Decryption Sender Recipient C=E(K, M) M=D(K, C) K K needs secure channel Internet Security - Farkas 14
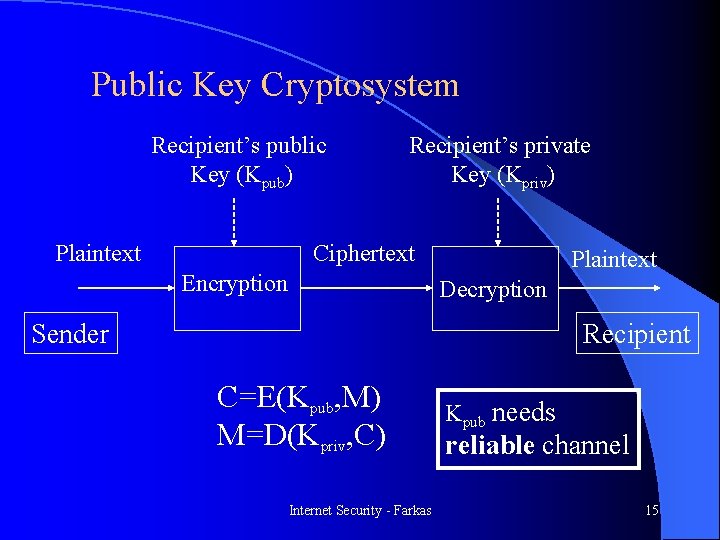
Public Key Cryptosystem Recipient’s public Key (Kpub) Plaintext Recipient’s private Key (Kpriv) Ciphertext Encryption Plaintext Decryption Sender Recipient C=E(Kpub, M) M=D(Kpriv, C) Internet Security - Farkas Kpub needs reliable channel 15

Summary: Secret-Key Encryption Single, secret key l Key distribution problem of secret key systems – Establish key before communication – Need n(n-1)/2 keys with n different parties l Do NOT provide electronic signatures l Faster than public-key encryption l Internet Security - Farkas 16

Summary: Public Key Encryption l Supports confidentiality and authentication l Need reliable channel for key distribution l 2 n keys for n users (public, private pairs) l Digital certificate l PKI Internet Security - Farkas 17
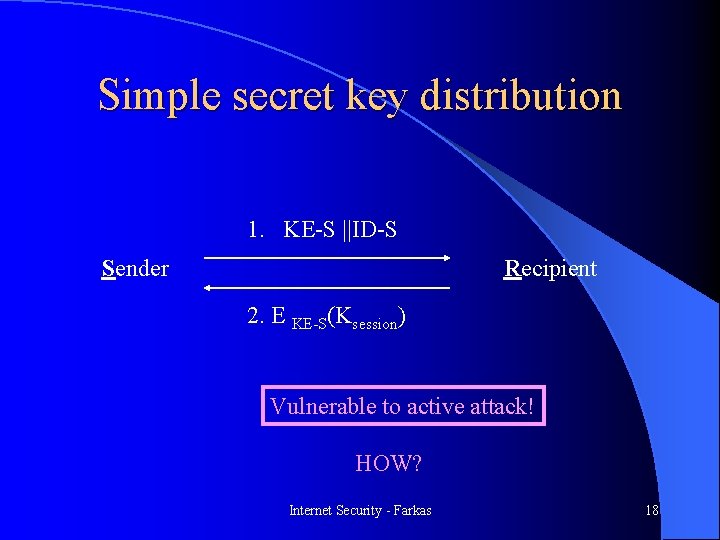
Simple secret key distribution 1. KE-S ||ID-S Sender Recipient 2. E KE-S(Ksession) Vulnerable to active attack! HOW? Internet Security - Farkas 18
![With confidentiality and authentication 1. E KE-R[N 1||ID-S] Sender 2. E KE-S[N 1||N 2] With confidentiality and authentication 1. E KE-R[N 1||ID-S] Sender 2. E KE-S[N 1||N 2]](http://slidetodoc.com/presentation_image_h2/59c9c2459e37cd6ce533f4aae82afdd1/image-19.jpg)
With confidentiality and authentication 1. E KE-R[N 1||ID-S] Sender 2. E KE-S[N 1||N 2] Recipient 3. E KE-R[N 2 -1] 4. E KE-R E KD-S(Ksession) Internet Security - Farkas What are the basic requirements for this protocol to be correct? 19
WHAT IS A PROTOCOL? Internet Security - Farkas 20
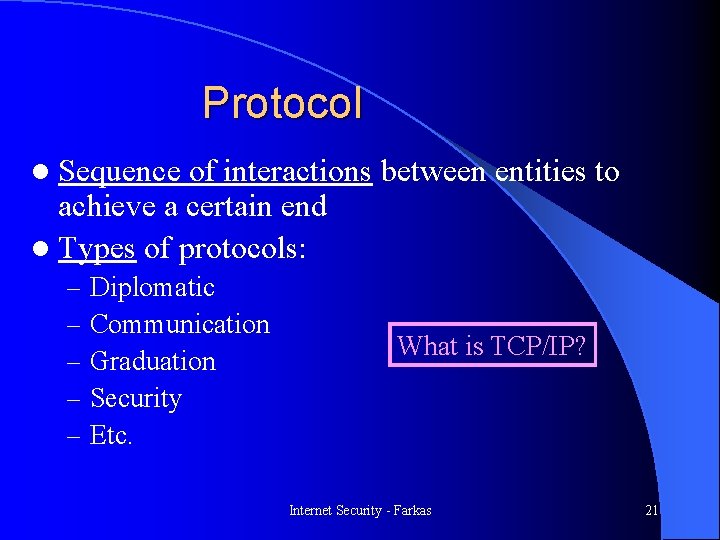
Protocol l Sequence of interactions between entities to achieve a certain end l Types of protocols: – – – Diplomatic Communication Graduation Security Etc. What is TCP/IP? Internet Security - Farkas 21

Reading Assignment Recommended Reading: P. Y. A. Ryan, S. A. Schneider, M. H. Goldsmith, G. Lowe and A. W. Roscoe, The Modelling and Analysis of Security Protocols: the CSP Approach, Section 0. Introduction, pages: 1 – 37, http: //www. computing. surrey. ac. uk/personal/st/S. Sc hneider/books/MASP. pdf Internet Security - Farkas 22

Security Protocols l Cryptographic protocols l Services: secrecy, integrity, authentication, key exchange, non-repudiation, etc. l Components: communicating parties (nodes), trusted third party, encryption algorithms, hash functions, timestamps, nonce, etc. Internet Security - Farkas 23

Security Properties – Secrecy l Non-interference: Intruder should not be able to deduce anything about the legitimate users’ activities l Message confidentiality: intruder cannot derive the plaintext of messages passed between two legitimate nodes Internet Security - Farkas 24

Security Properties – Authentication of Origin l Verify – Who sent the message? – Who sent the message to whom and how many times? Internet Security - Farkas 25

Security Properties – Entity Authentication l Similar to authentication of origin but has timeliness l Repeated form of origin authentication Internet Security - Farkas 26

Security Properties – Integrity l Data cannot be corrupted l Content of output messages match the content of the input message Internet Security - Farkas 27

Security Properties – Authenticated Key-Exchange I’m calling from your utilities company. We need your SSN, billing address, and … Internet Security - Farkas l Share a secret key with another person and know for sure who this other person is 28
Security Properties – Nonrepudiation l Legitimate participants l Against possible cheating l Signature-type mechanism Internet Security - Farkas 29

Security Properties – Fairness l Legitimate participants l Prevents one of the participants to gain advantage over another by halting the protocol part-way through Internet Security - Farkas 30

Security Properties – Anonymity l Over some sets of events l Shuffling the events will not change an observer’s view l Occurrence of events? l Accountability Internet Security - Farkas 31

Security Properties – Availability l To be able to achieve the goals Internet Security - Farkas 32

More Examples of Crypto protocols Read on your own Internet Security - Farkas 33

Diffie-Hellman Key Exchange Proposed in 1976 l First public key algorithm l Allows group of users to agree on secret key over insecure channel l Cannot be used to encrypt and decrypt messages l Internet Security - Farkas 34

Diffie-Hellman Key Exchange Protocol for A and B want to agree on shared secret key: l A and B agree on two large numbers n and g, such that 1<g<n l A chooses random x and computes X=gx mod n and sends X to B l B chooses random y and computes Y=gy mod n and sends Y l A computes k= Yx mod n l B computer k’= Xy mod n l Note: k =k’= gyx mod n Internet Security - Farkas 35

Diffie-Hellman Key Exchange Requires no prior communication between A and B l Security depends on difficulty of computing x given X=gx mod n l Choices for g and n are critical: both n and (n-1)/2 should be prime, n should be large l Susceptible to intruder in the middle attack (active intruder) l Internet Security - Farkas 36
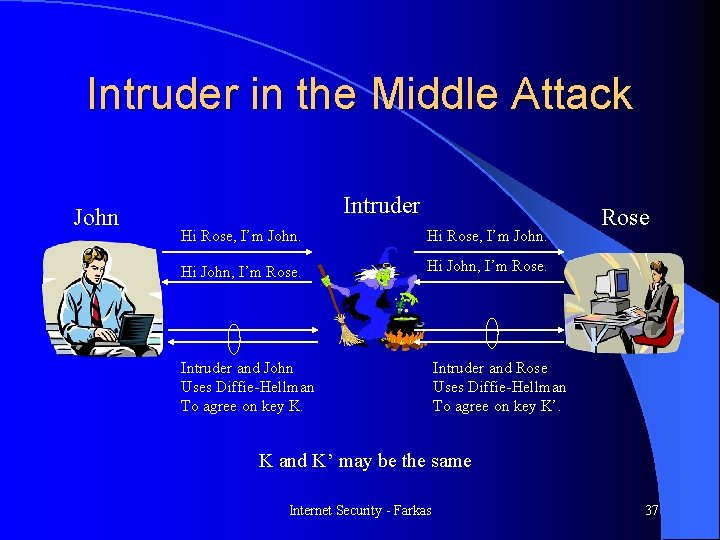
Intruder in the Middle Attack John Intruder Hi Rose, I’m John. Hi John, I’m Rose. Intruder and John Uses Diffie-Hellman To agree on key K. Rose Intruder and Rose Uses Diffie-Hellman To agree on key K’. K and K’ may be the same Internet Security - Farkas 37

Asymmetric-Key Exchange l Without server – Broadcasting – Publicly available directory l With server – Public key distribution center – Certificates Internet Security - Farkas 38
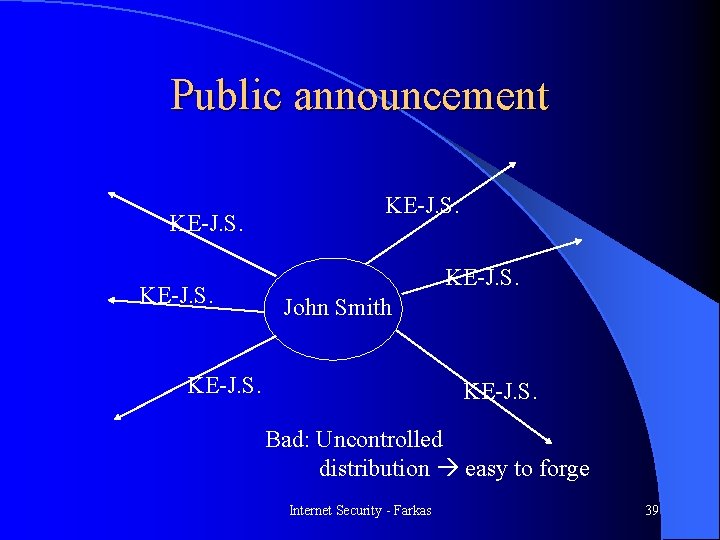
Public announcement KE-J. S. John Smith KE-J. S. Bad: Uncontrolled distribution easy to forge Internet Security - Farkas 39
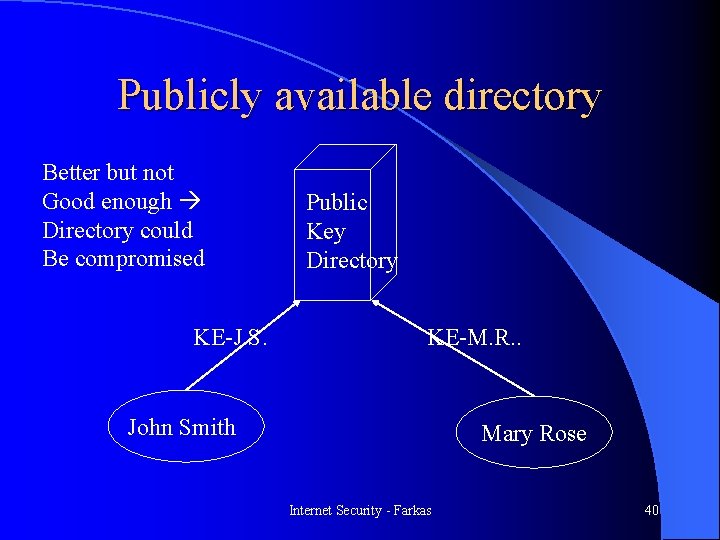
Publicly available directory Better but not Good enough Directory could Be compromised KE-J. S. Public Key Directory KE-M. R. . John Smith Mary Rose Internet Security - Farkas 40
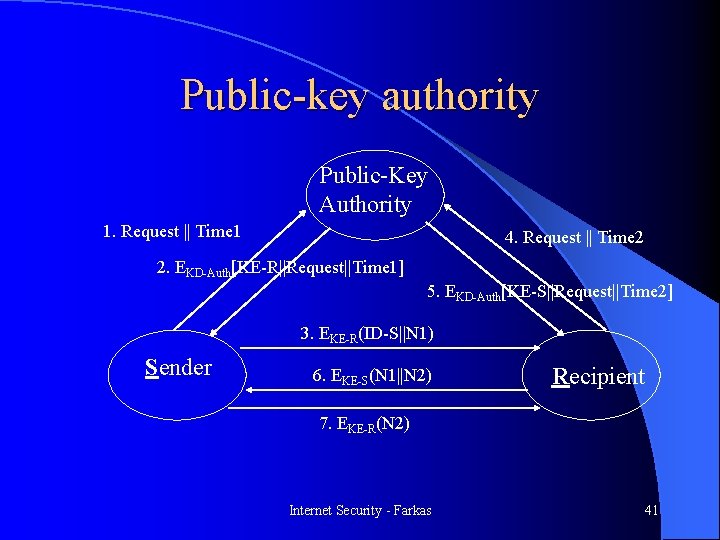
Public-key authority Public-Key Authority 1. Request || Time 1 4. Request || Time 2 2. EKD-Auth[KE-R||Request||Time 1] 5. EKD-Auth[KE-S||Request||Time 2] 3. EKE-R(ID-S||N 1) Sender 6. EKE-S(N 1||N 2) Recipient 7. EKE-R(N 2) Internet Security - Farkas 41
![Public-key certificates Certificate Authority KE-S C-S=EKD-CAuth[Time 1, ID-S, KE-S] KE-R CR=EKD-CAuth[Time 2, ID-R, KE-R] Public-key certificates Certificate Authority KE-S C-S=EKD-CAuth[Time 1, ID-S, KE-S] KE-R CR=EKD-CAuth[Time 2, ID-R, KE-R]](http://slidetodoc.com/presentation_image_h2/59c9c2459e37cd6ce533f4aae82afdd1/image-42.jpg)
Public-key certificates Certificate Authority KE-S C-S=EKD-CAuth[Time 1, ID-S, KE-S] KE-R CR=EKD-CAuth[Time 2, ID-R, KE-R] 1. C-S Sender 2. C-R Internet Security - Farkas Recipient 42

Certificates l Guarantees the validity of the information l Establishing trust l Public key and user identity are bound together, then signed by someone trusted l Need: digital signature Internet Security - Farkas 43

Digital Signature l Need the same effect as a real signature – Un-forgeable – Authentic – Non-alterable – Not reusable Internet Security - Farkas 44

Digital signature l Direct digital signature: public-key cryptography based l Arbitrated digital signature: – Conventional encryption: Arbiter sees message l Arbiter does not see message l – Public-key based l Arbiter does not see message Internet Security - Farkas 45
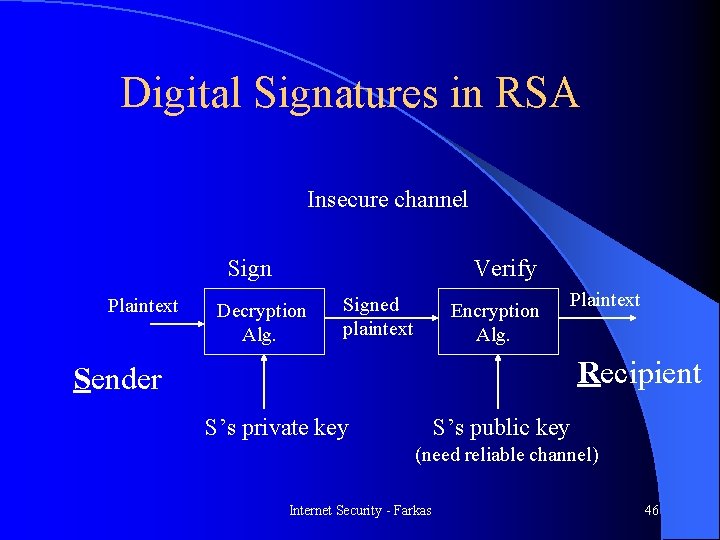
Digital Signatures in RSA Insecure channel Sign Plaintext Verify Decryption Alg. Signed plaintext Encryption Alg. Plaintext Recipient Sender S’s private key S’s public key (need reliable channel) Internet Security - Farkas 46

Non-repudiation l Requires notarized signature, involving a third party l Large system: hierarchies of notarization Internet Security - Farkas 47

NEXT CLASS TCP/IP OVERVIEW Internet Security - Farkas 48
- Slides: 48