CWSP Guide to Wireless Security Chapter 5 Wireless








































- Slides: 44

CWSP Guide to Wireless Security Chapter 5 Wireless Security Models CWSP Guide to Wireless Security

Objectives • Explain the advantages of WPA and WPA 2 • Explain the technologies that are part of the personal security model • List the features of the transitional security model • Define the enterprise security model CWSP Guide to Wireless Security 2

Wireless Security Solutions • WEP suffers from serious weakness • “Band-aid” solutions – WEP 2 and Dynamic WEP • Better solutions – IEEE 802. 11 i – Wi-Fi Protected Access (WPA) – Wi-Fi Protected Access 2 (WPA 2) CWSP Guide to Wireless Security 3

IEEE 802. 11 i • Addresses the two weaknesses of wireless networks: encryption and authentication • Encryption – Replaces the RC 4 stream cipher algorithm with a block cipher • Manipulates an entire block of text at one time – 802. 11 i uses the Advanced Encryption Standard (AES) • Designed to be an encryption technique that is secure from attacks CWSP Guide to Wireless Security 4

IEEE 802. 11 i (continued) CWSP Guide to Wireless Security 5

IEEE 802. 11 i (continued) • Authentication and key management – Accomplished by the IEEE 802. 1 x standard • Implements port security • Blocks all traffic on a port-by-port basis – Until the client is authenticated using credentials stored on an authentication server • Key-caching – Stores information from a device on the network – If a user roams away and later returns • She does not need to re-enter all of the credentials CWSP Guide to Wireless Security 6

IEEE 802. 11 i (continued) CWSP Guide to Wireless Security 7

IEEE 802. 11 i (continued) • Pre-authentication – Allows a device to become authenticated to an AP • Before moving into range of the AP – Device sends a pre-authentication packet to the AP the user is currently associated with • And the packet is then routed to a remote AP or APs – Allows for faster roaming between access points CWSP Guide to Wireless Security 8

Wi-Fi Protected Access (WPA) • Subset of 802. 11 i and addresses both encryption and authentication • Temporal Key Integrity Protocol (TKIP) – TKIP keys are known as per-packet keys – TKIP dynamically generates a new key for each packet that is created – Prevent collisions • Which was one of the primary weaknesses of WEP • Authentication server can use 802. 1 x to produce a unique master key for that user session CWSP Guide to Wireless Security 9

Wi-Fi Protected Access (WPA) (continued) • TKIP distributes the key to wireless devices and AP – Setting up an automated key hierarchy and management system • WPA replaces the Cyclic Redundancy Check (CRC) with the Message Integrity Check (MIC) – Designed to prevent an attacker from capturing, altering, and resending data packets – Provides a strong mathematical function – Clients are de-authenticated and new associations are prevented for one minute if an MIC error occurs • Optional feature CWSP Guide to Wireless Security 10

Wi-Fi Protected Access (WPA) (continued) CWSP Guide to Wireless Security 11

Wi-Fi Protected Access (WPA) (continued) • WPA authentication – Accomplished by using either IEEE 802. 1 x or preshared key (PSK) technology • PSK authentication uses a passphrase to generate the encryption key – Passphrase must be entered on each access point and wireless device in advance – Serves as the seed for mathematically generating the encryption keys • WPA was designed to address WEP vulnerabilities with minimum inconvenience CWSP Guide to Wireless Security 12

Wi-Fi Protected Access 2 (WPA 2) • Second generation of WPA security • Based on the final IEEE 802. 11 i standard • Uses the Advanced Encryption Standard (AES) for data encryption • Supports IEEE 802. 1 x authentication or PSK technology • WPA 2 allows both AES and TKIP clients to operate in the same WLAN CWSP Guide to Wireless Security 13

Wi-Fi Protected Access 2 (WPA 2) (continued) CWSP Guide to Wireless Security 14

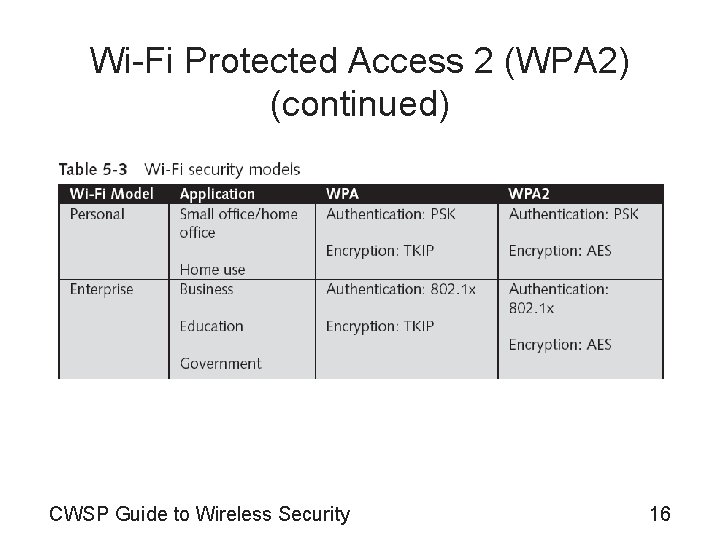
Wi-Fi Protected Access 2 (WPA 2) (continued) • Wi-Fi Alliance wireless security models based on WPA and WPA 2 – – WPA—Personal Security WPA—Enterprise Security WPA 2—Personal Security WPA 2—Enterprise Security • Transitional security model – Used as a “bridge” solution in situations where WPA or WPA 2 security is not available – Intended as a temporary fix CWSP Guide to Wireless Security 15

Wi-Fi Protected Access 2 (WPA 2) (continued) CWSP Guide to Wireless Security 16

Transitional Security Model • Should only be implemented as a temporary solution CWSP Guide to Wireless Security 17

Authentication • Shared key authentication – Should be used instead of open system authentication – Uses WEP keys for authentication – Based on a challenge-response scheme • SSID beaconing – Should be turned off – May prevent a “casual” unauthorized user or novice attacker from capturing the SSID • And entering the network – Use a hard-to-guess SSID in a WLAN CWSP Guide to Wireless Security 18

Authentication (continued) • MAC address filtering limitations – Managing a large number of MAC addresses is difficult – Does not provide an easy means to temporarily allow a guest user to access the network – WLANs initially exchange MAC addresses in cleartext – A MAC address can be “spoofed” or substituted • DHCP restrictions – DHCP “leases” IP addresses to clients to use while they are connected to the network CWSP Guide to Wireless Security 19

Authentication (continued) CWSP Guide to Wireless Security 20

Authentication (continued) CWSP Guide to Wireless Security 21

WEP Encryption • Should be turned on – If no other options are available for encryption • The longest WEP key available should be used for added security – Most vendors have the option of a 128 -bit WEP key • There is evidence that WEP passphrase generators may create predictable keys CWSP Guide to Wireless Security 22

WEP Encryption (continued) CWSP Guide to Wireless Security 23

Personal Security Model • Designed for single users or small office/home office (SOHO) settings – Generally 10 or fewer wireless devices • Intended for settings in which an authentication server is unavailable • Divided into two parts, WPA and WPA 2 – WPA 2 should always be used instead of WPA CWSP Guide to Wireless Security 24

WPA Personal Security • PSK authentication – Purchasing, installing, and managing an authentication server is costly • May require special technical skills – PSK functions • Used to authenticate the user • Plays a role in encryption – PSK vulnerabilities • Key management • Passphrases CWSP Guide to Wireless Security 25

WPA Personal Security (continued) CWSP Guide to Wireless Security 26

WPA Personal Security (continued) CWSP Guide to Wireless Security 27

WPA Personal Security (continued) • PSK authentication (continued) – PSK key management weakness • Distribution and sharing of PSK keys is performed manually • PSK only uses a single key • Changing the PSK key requires reconfiguring the key on every wireless device and all APs • To allow a guest user to have access to a PSKWLAN, the key must be given to that guest – PSK passphrase • 64 -bit hexadecimal number CWSP Guide to Wireless Security 28

WPA Personal Security (continued) • PSK authentication (continued) – PSK passphrases of fewer than 20 characters can be subject to offline dictionary attacks – Linksys’ Secure. Easy. Setup (SES) • Software and hardware interface • Creates and distributes a strong PSK key • TKIP encryption – TKIP is designed to fit into existing WEP procedure – Wireless device has two keys • 128 -bit encryption key called the temporal key and a 64 bit MIC CWSP Guide to Wireless Security 29

WPA Personal Security (continued) CWSP Guide to Wireless Security 30

WPA Personal Security (continued) • TKIP encryption (continued) – TKIP components • MIC • IV sequence • TKIP key mixing CWSP Guide to Wireless Security 31

WPA 2 Personal Security • PSK authentication – PSK keys are automatically changed (called rekeying) • And authenticated between devices after a specified period – Known as the rekey interval • AES-CCMP encryption – AES is used in WPA 2 for data encryption – AES-CCMP is the encryption protocol in the 802. 11 i standard • CCMP is based upon the Counter Mode with CBC-MAC (CCM) CWSP Guide to Wireless Security 32

WPA 2 Personal Security (continued) • AES-CCMP encryption (continued) – CCM provides data privacy – CBC-MAC provides data integrity and authentication – AES algorithm processes blocks of 128 bits • Length of the cipher keys and number of rounds can vary – It is recommended that AES encryption and decryption be performed in hardware CWSP Guide to Wireless Security 33

WPA 2 Personal Security (continued) CWSP Guide to Wireless Security 34

Enterprise Security Model • Most robust level of security • Designed for medium to large-sized organizations • Intended for settings in which an authentication server is available • Divided into two parts, WPA and WPA 2 CWSP Guide to Wireless Security 35

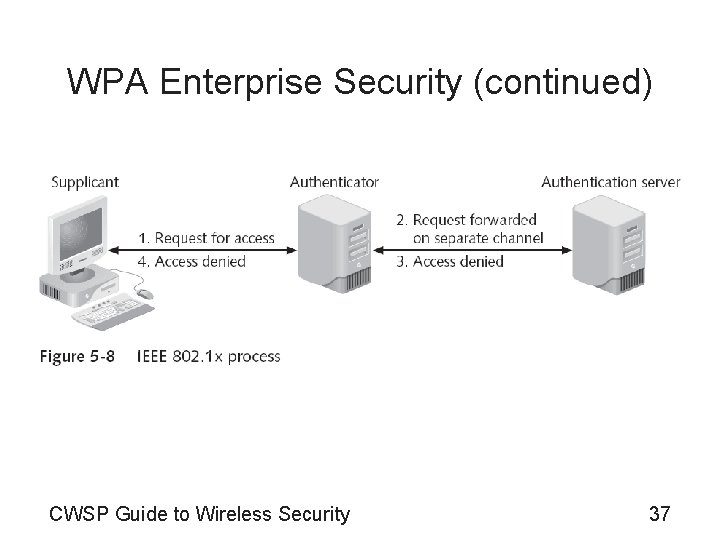
WPA Enterprise Security • IEEE 802. 1 x authentication – Provides an authentication framework for all IEEE 802 based LANs – Elements • Supplicant • Authenticator • Authentication server – IEEE 802. 1 x supplicant • Software that implements the IEEE 802. 1 x framework • May be included in the client operating system or WNIC CWSP Guide to Wireless Security 36

WPA Enterprise Security (continued) CWSP Guide to Wireless Security 37

WPA Enterprise Security (continued) • IEEE 802. 1 x authentication (continued) – Authentication server • Stores the list of the names and credentials of authorized users to verify their authenticity • Typically a Remote Authentication Dial-In User Service (RADIUS) server is used – Allows a company to maintain user profiles in a central database that all remote servers can share • Other options – Structured Query Language (SQL) – Lightweight Directory Access Protocol (LDAP) – Microsoft Active Directory CWSP Guide to Wireless Security 38

WPA Enterprise Security (continued) • TKIP encryption – Should be considered an interim WPA enterprise security solution – A more robust encryption protocol is AES-CCMP CWSP Guide to Wireless Security 39

WPA 2 Enterprise Security • IEEE 802. 1 x authentication – Disadvantage • High cost involved with purchasing, installing, and maintaining an authentication server • AES-CCMP encryption – A 128 -bit key length is used – AES encryption includes four stages that make up one round • Each round is iterated 10 times CWSP Guide to Wireless Security 40

WPA 2 Enterprise Security (continued) CWSP Guide to Wireless Security 41

WPA 2 Enterprise Security (continued) • Robust Secure Network (RSN) – Uses dynamic negotiation of authentication and encryption algorithms • Between access points and wireless devices – RSNs evolve as vulnerabilities are exposed or improved security is introduced CWSP Guide to Wireless Security 42

Summary • Additional security solutions – IEEE 802. 11 i – Wi-Fi Protected Access (WPA) – Wi-Fi Protected Access Version 2 (WPA 2) • IEEE 802. 11 i standard provided a more solid wireless security model – Uses AES and IEEE 802. 1 x port security • WPA is a subset of 802. 11 i and addresses both encryption and authentication – Uses Temporal Key Integrity Protocol (TKIP) and a Message Integrity Check (MIC) CWSP Guide to Wireless Security 43

Summary (continued) • The transitional security model should be implemented only as a temporary solution • The personal security model is designed for single users or small office home office (SOHO) • The enterprise security model is designed for medium to large-sized organizations CWSP Guide to Wireless Security 44