CTOC COUNTERING TRANSNATIONAL ORGANIZED CRIME DIGITAL FORENSICS AND
















- Slides: 20

CTOC COUNTERING TRANSNATIONAL ORGANIZED CRIME DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

COMPETENCIES ACHIEVED Following this module, participants will have: ü Knowledge of the importance of communications exploitation in wildlife crime investigations ü Knowledge of the considerations involved in obtaining, preserving and analyzing digital evidence collected from mobile devices DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

INTRODUCTION • Digital forensics is a branch of forensic science involving the recovery and investigation of material found in digital devices • An increasing number of criminals are using technology and conducting activities online • Law enforcement officers must understand the importance of collecting and exploiting digital/online evidence DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

TYPES OF DIGITAL FORENSICS • Computer Forensics: laptops, personal computers, hard drives, USB thumb drives • Network Forensics: network equipment, servers, LAN networks • Mobile Phone Forensics: landlines, mobile phones, smartphones, GPS tracking devices • Internet of Things (Io. T) Forensics: drones, connected physical devices, home automation appliances and wearable devices • Multimedia Forensics: audio, images, video, gaming • Cloud Forensics: cloud services, hosting services DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

DIGITAL FORENSICS • Digital forensics techniques are used to search, preserve and analyze information on computer systems and communication devices. o With intent that evidence obtained can then be used to support court cases • Digital forensics uses many of the same techniques as those used in crime scene investigations o Some, however, are unique to digital investigations DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

DIGITAL FORENSICS Why digital forensics is important to investigators: • Every criminal involved in wildlife trafficking has a cell phone from low-level couriers and transportation facilitators to wholesalers, retailers, or kingpins • Wildlife trafficking cannot occur without criminals operating along a supply chain communicating and leaving a digital record of their activities • Exploitation of digital evidence helps identify those involved and link them to each other and to the criminal activity DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

DIGITAL FORENSICS CHALLENGES • Done wrong - you risk destroying vital evidence or having forensic evidence ruled inadmissible in a court • Lack of physical evidence makes crimes harder to prosecute, you may need to educate the court • Large amounts of storage space required for digital evidence (up to 10 terabytes) making collection and preservation difficult • Rapid technological changes require constant upgrades or changes DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

DIGITAL FORENSIC TOOLS DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

MOBILE PHONE FORENSICS “the science of recovering digital evidence from a mobile phone under forensically sound conditions using accepted methods” DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

MOBILE DEVICE FORENSICS • Mobile devices are now part of daily life, and are used to facilitate criminal activity • Mobile devices generally belong to only one individual • Rapid technological progress and constant upgrades makes extracting information from mobile devices challenging • It is extremely difficult to develop a single process or tool to address all possibilities an examiner may face DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

MOBILE FORENSICS • It is the responsibility of the responding or seizing officer to collect and preserve digital evidence • Secure the scene and obtain legal authority to seize the evidence before collecting devices • Mobile devices should be seized following same evidence collection procedures as any other piece of evidence DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

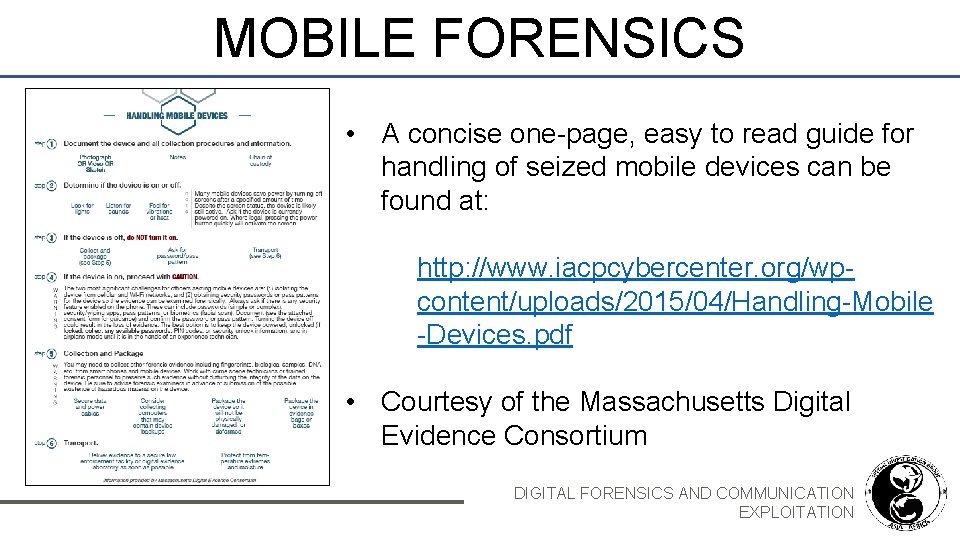
MOBILE FORENSICS • A concise one-page, easy to read guide for handling of seized mobile devices can be found at: http: //www. iacpcybercenter. org/wpcontent/uploads/2015/04/Handling-Mobile -Devices. pdf • Courtesy of the Massachusetts Digital Evidence Consortium DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

MOBILE DEVICE FORENSIC PROCESSING Key challenges to extract and analyze data from a mobile include: • Increasing functionality and growing data storage, mobile devices have become pocket size computers • Password protection and encryption • The National Institute for Standards and Technology (NIST) and the Scientific Group on Digital Evidence (SWGDE) outline the benefits and challenges mobile forensics present to law enforcement NIST: Guidelines on Mobile Device Forensics SWGDE: Best Practices for Mobile Phone Forensics DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

COMPLICATIONS DURING MOBILE PHONE FORENSICS • Turn phone off or leave it on? Charging and continued communication • File system sometimes in volatile memory • Wide variety of cables and connectors • Short product cycles for new devices • Diverse operating systems • Hibernation behavior • Battery powered • Compact size DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

POPULAR FORENSIC TOOLS DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

PARTS OF A MOBILE PHONE DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

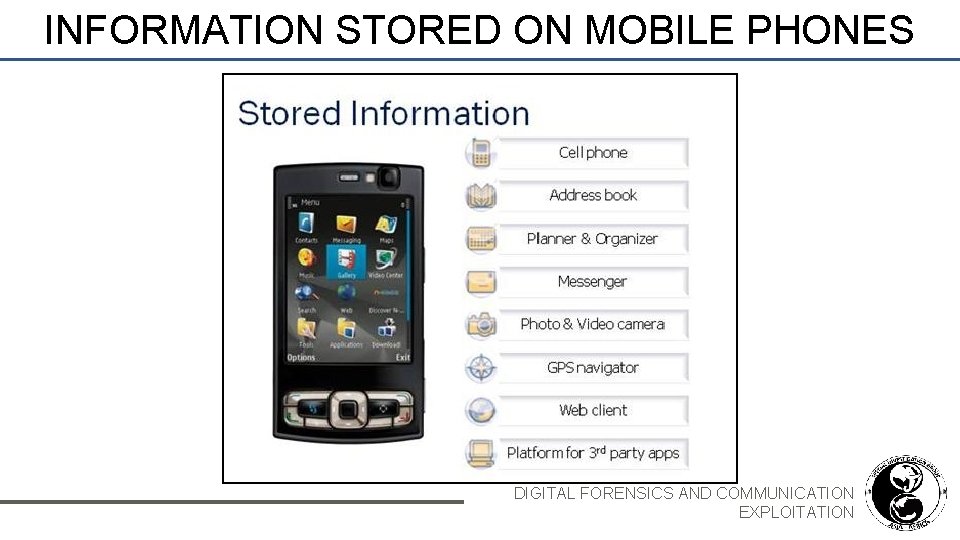
INFORMATION STORED ON MOBILE PHONES DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

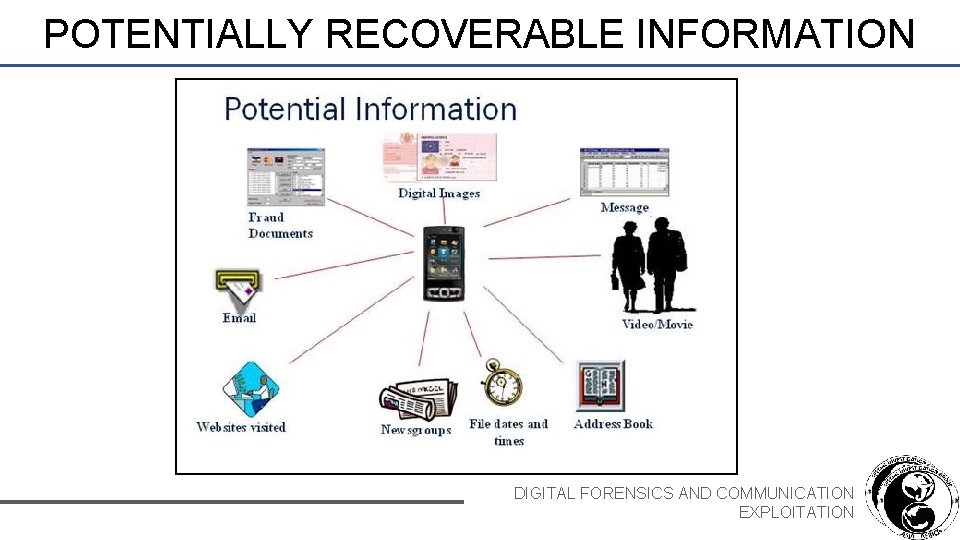
POTENTIALLY RECOVERABLE INFORMATION DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

CALL DETAIL RECORDS • Call Detail Records (CDRs) which are maintained by service providers, capture all activity on a mobile device made by a subscriber • e. g. incoming and outgoing messages and calls • CDRs normally identify the cellular tower that services calls which can tell you the location of the subscriber when the call was made • CDR’s generally require legal process to be obtained DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION

QUESTIONS? COMMENTS? CONCERNS? Photo: R 4 robin via Wikimedia Commons/ CC BY-SA 4. 0 DIGITAL FORENSICS AND COMMUNICATION EXPLOITATION
 Transnational crime and the developing world
Transnational crime and the developing world Transnational crime examples
Transnational crime examples War making and state making as organized crime
War making and state making as organized crime Grande barrio central okc
Grande barrio central okc Organized crime osrs
Organized crime osrs Hungarian organized crime
Hungarian organized crime Forensic duplication
Forensic duplication Gillware digital forensics
Gillware digital forensics Computer forensics denver
Computer forensics denver Example of an expert witness digital forensics report
Example of an expert witness digital forensics report The phases of investigation
The phases of investigation Forensics
Forensics Multidomestic strategy
Multidomestic strategy Transnational vs multinational
Transnational vs multinational First mnc in the world
First mnc in the world Multidomestic corporation
Multidomestic corporation Multinational vs transnational
Multinational vs transnational Transnational strategy vs global strategy
Transnational strategy vs global strategy First mnc in world
First mnc in world Disney + strategy
Disney + strategy Distributing service
Distributing service