CSL Workshop 4 Wireless Hacking by Max Farrell

CSL Workshop 4 Wireless Hacking by Max Farrell

Wireless Protocols: WEP (Wireless Equivalent Protocol) WEP was in use widely from 1999 to 2005 as the default standard. WEP has multiple insecurities including passive traffic capture, weak stream cipher encryption, and no packet checking and was retired officially in 2004 by the Wi-Fi Alliance. http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html WEP is still in use today on many consumer WAPs distributed by ISPs.

Wireless Protocols: WPA (Wi-Fi Protected Access) WPA was the immediate successor to WEP. WPA employs packet checking in the form of TKIP (Temporal Key Integrity Protocol). WPA also employs 256 -bit keys which WEP did not even employ at the time of WPAs creation. * WPA did however have flaws which came from being the successor of WEP. In order for WPA to be widely available it needed to be provided as an upgrade to systems using WEP, this led to the [crippling] of TKIP.

Wireless Protocols: WPA 2 (Wi-Fi Protected Access 2) WPA 2 is the successor to WPA 2 employs many of the same techniques as WPA, however the protocols in use have mostly changed. WPA 2 uses only AES encryption while WEP and WPA device manufacturers could choose which encryption algorithms they would use. WPA 2 also replaced TKIP with CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol).
WPS (Wi-Fi Protected Setup) WPS is the primary security vulnerability associated with modern WAPs. WPS is meant to make connecting to Wi-Fi easier as you don’t have to enter a pre-shared key (WPA/2 PSK). Instead there are two options: pressing a button or entering a pin. The greatest concern come from the latter. WPS requires an 8 -digit pin. This pin is checked 4 digits at a time, making a brute force attack simple.
Aircrack-ng For this workshop we will be using the Aircrack-ng suite. This suite consists of tools to assess Wi-Fi security. The tools we will be using from this suite are: airmon-ng: Enables monitor mode on WLAN adapters. airodump-ng: Packet capturing utility, allows us to monitor traffic to and from WAPs (Wireless Access Points) aireplay-ng: Frame injection utility, allows to deauthenticate users so they must reauthenticate aircrack-ng: Handshake cracking utility, allows us to decrypt authentication handshakes

Putting adapter in monitor mode
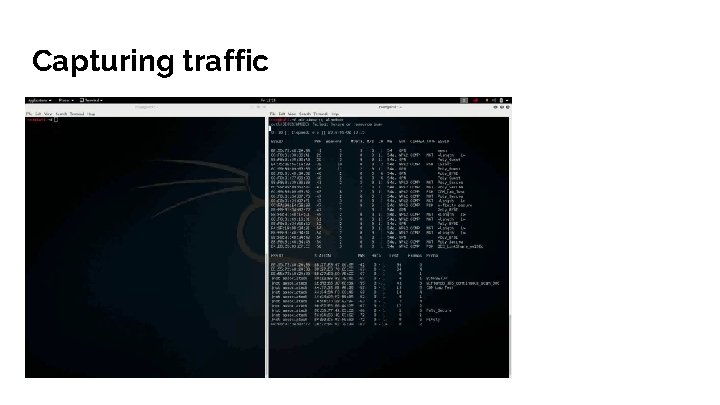
Capturing traffic
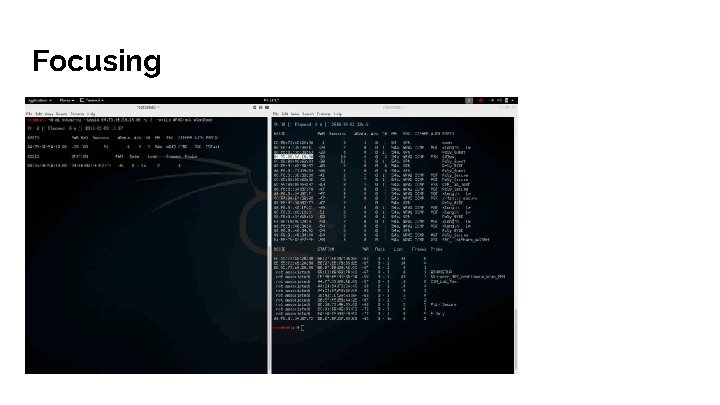
Focusing
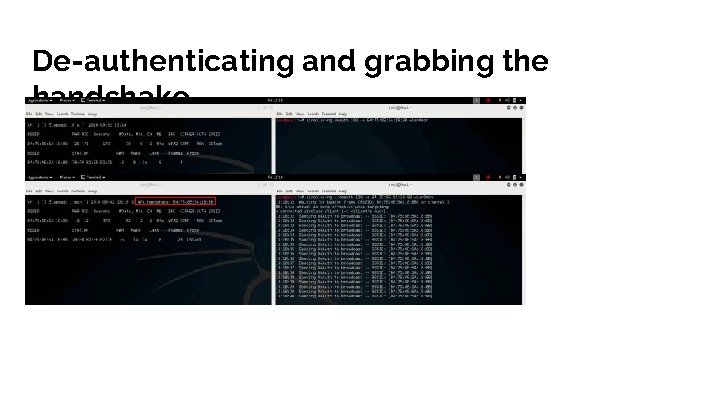
De-authenticating and grabbing the handshake
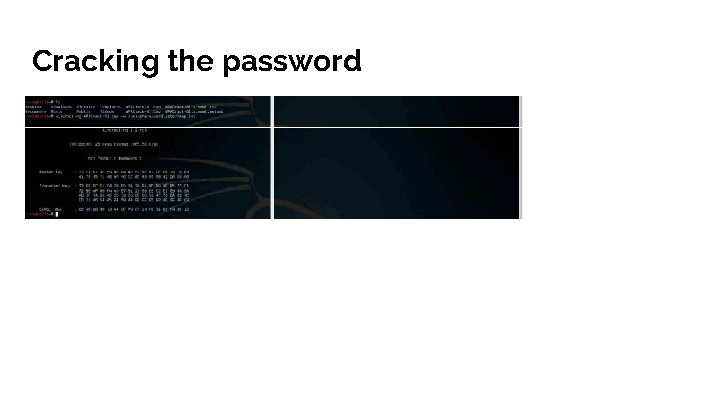
Cracking the password
Network enumeration Now that you’re in the network see what you can find. Anything Evil? (Remember the Network Enumeration and Script Injection workshops)
Best Practices Set strong, randomly generated passwords. https: //lastpass. com/generatepassword. php Do not physically write down the password. If the password used is too long to remember have a managed password safe such as Lastpass or Password Safe. Make sure WPA 2 -PSK is enabled and WPS is disabled.
- Slides: 13