CSE 5392 Sensor Network Security Course Introduction CSE



















- Slides: 27

CSE 5392 Sensor Network Security Course Introduction CSE 5392 By Dr. Donggang Liu 1

About Instructor • Dr. Donggang Liu, assistant professor, CSE department – http: //ranger. uta. edu/~dliu – dliu@cse. uta. edu – Tel: (817) 272 -0741 – Office: 330 NH – Office hours: Tuesday&Thursday 5: 00 PM-6: 00 PM CSE 5392 By Dr. Donggang Liu 2

About TA • TBD • Office hours: – TBD CSE 5392 By Dr. Donggang Liu 3

Course Objectives • Understanding of fundamental concepts, principles, and mechanisms in sensor network security • Prepare students for graduate research in sensor network security – Advanced topics: key management, security services, etc – Recently published research papers CSE 5392 By Dr. Donggang Liu 4

Course Outcomes • Basic – Explain known security problems in sensor networks – Explain how security mechanisms work for sensor networks – Distinguish difference between security problems in sensor networks and those in wired networks. • Advanced – Identify and analyze new security problems in sensor networks – Develop mechanisms to solve security problems in sensor networks. – Design simulations to evaluate and analyze the performance of algorithms in sensor networks CSE 5392 By Dr. Donggang Liu 5

Course Style • By instructor – Sensor network basics – Cryptography and security basics – Sensor network security • By students – Read research papers on sensor network security – Write reviews – Give in-class presentations (15~20 minutes) CSE 5392 By Dr. Donggang Liu 6

Prerequisites • Required – Computer network – Operating system • Necessary for great success – Technical writing skills – Hardworking CSE 5392 By Dr. Donggang Liu 7

Textbooks and Papers • No textbooks • Reference books – Handbook of Applied Cryptography by Alfred J. Menezes, Paul C. Van Oorschot, Scott A. Vanstone (http: //www. cacr. math. uwaterloo. ca/hac/) – Cryptography and Network Security: Principles and Practice by William Stallings. – Practical Cryptography by Niels Ferguson, Bruce Schneier • Papers and Slides – Links in the course syllabus CSE 5392 By Dr. Donggang Liu 8

Projects • Group – 2~3 students – Working alone must be justified – Roles can be negotiated inside the group • Topics – Should be relevant to the class – Each group can come up with one – The instructor can also give topics (check website) CSE 5392 By Dr. Donggang Liu 9

Projects (Cont’d) • Survey paper • Surveys a particular field on sensor network security • Summarizes the trend in this field • A proposal (due on 6/10) and a final paper (due on 1/12) • Research paper • Identify original research problems • A research paper with original technical contribution • A proposal (due on 6/10) and a final paper (due on 1/12) • Start thinking about your team and topic NOW CSE 5392 By Dr. Donggang Liu 10

On-line resource • Course website – http: //ranger. uta. edu/~dliu/cse 5392 -sns. htm – For course materials, e. g. , papers, homework, project assignment. – Check frequently for updates CSE 5392 By Dr. Donggang Liu 11

Grading • Paper review – 20% • Participation – 10% • Project – 40% • Class presentation – 30% + 10% extra CSE 5392 By Dr. Donggang Liu 12

Course Policies • Assignment (paper review) and project deadlines will be firm. • Late assignments will be accepted with a 10% reduction in grade for each day they are late by. • All assignments must be turned in before the start of class on the due date CSE 5392 By Dr. Donggang Liu 13

Academic Integrity • The university, college, and department policies against academic dishonesty will be strictly enforced. – http: //www. uta. edu/studentaffairs/judicialaffairs CSE 5392 By Dr. Donggang Liu 14

Course Topics • Cryptography and security basics • Sensor network basics • Useful security tools – One way hash chain – Merkle hash tree • Security in Sensor Networks – – – Key management Broadcast authentication Secure localization Secure data aggregation Intrusion detection Privacy CSE 5392 By Dr. Donggang Liu 15

CSE 5392 Sensor Network Security Basic Security Concepts CSE 5392 By Dr. Donggang Liu 16

Cryptography and Security • Cryptography – Study of fundamental algorithms to protect data – Encryption/decryption, hash, digital signature, etc. • Security – Study of protocols to protect a system – Usually build upon cryptographic techniques CSE 5392 By Dr. Donggang Liu 17

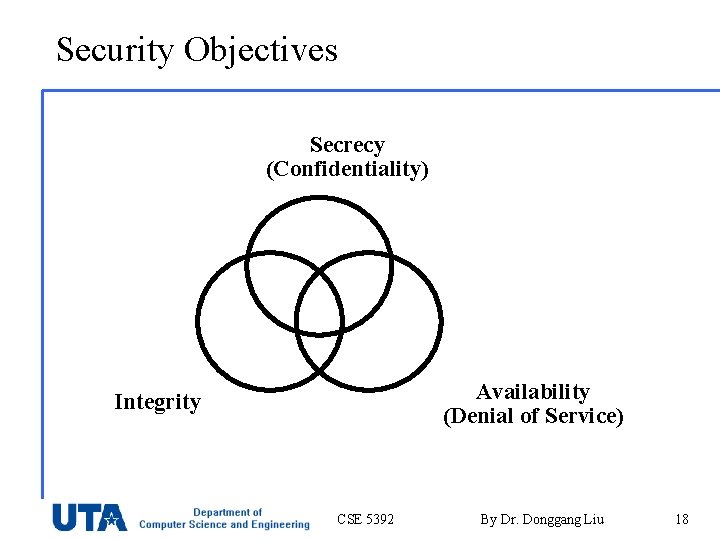
Security Objectives Secrecy (Confidentiality) Availability (Denial of Service) Integrity CSE 5392 By Dr. Donggang Liu 18

Secrecy (Confidentiality) • Prevent/detect/deter improper disclosure of information • Examples: – An employee should not come to know the salary of his manager – The target coordinates of a missile should not be improperly disclosed CSE 5392 By Dr. Donggang Liu 19

Integrity • Prevent/detect/deter improper modification of information • Examples: – An employee should not be able to modify the employee's own salary – The target coordinates of a missile should not be improperly modified CSE 5392 By Dr. Donggang Liu 20

Availability (Denial of Service) • Prevent/detect/deter improper denial of access to services provided by the system • Examples: – Paychecks should be printed on time as stipulated by law – When the proper command is issued the missile should fire CSE 5392 By Dr. Donggang Liu 21

Other Security Objectives • Non-repudiation – Prevent an entity from denying the previous commitments or actions • Securing computing resources: – Prevent/detect/deter improper use of computing resources • Hardware Resources • Software resources • Data resources • Anonymity – Prevent the disclosure of the identify of an entity to others CSE 5392 By Dr. Donggang Liu 22

Achieving Security • Security policy — What? • Security mechanism — How? • Security assurance — How well? CSE 5392 By Dr. Donggang Liu 23

Security Policy • The set of rules that regulate how an organization manages, protects, and distributes sensitive information. • Convert organization requirements to security policy that a computer system can understand – Interact with human being – Check and remove conflict rules CSE 5392 By Dr. Donggang Liu 24

Security Mechanism • Prevention — Access control • Detection — Auditing and intrusion detection • Tolerance — Practicality Good prevention and detection both require good authentication as a foundation CSE 5392 By Dr. Donggang Liu 25

Security Mechanisms • Security mechanisms implement functions that help prevent, detect, and respond to security attacks • Prevention is more fundamental, but sometimes detection is the only option, e. g. , – Accountability inproper use of authorized privileges • Security functions are typically made available to users as a set of security services through APIs or integrated interfaces – Security services: confidentiality, authentication, integrity, non-repudiation, access control, monitor & response • Cryptography underlies (almost) all security mechanisms CSE 5392 By Dr. Donggang Liu 26

Security Assurance • How well your security mechanisms guarantee your security policy • Everyone wants high assurance • High assurance implies high cost – May not be possible • Trade-off is needed. CSE 5392 By Dr. Donggang Liu 27