CSE 503 Design Charette Mattias Engblom Robert Franzn

CSE 503 – Design Charette Mattias Engblom Robert Franzén Johan Hesselberg Raphael Hoffman Ramy Shahin

Presentation Overview Introduction n Design overview n Models n

Introduction Chosen area – Security n Known security techniques n What we decided to implement n ¨ Privacy ¨ Integrity ¨ Authentication
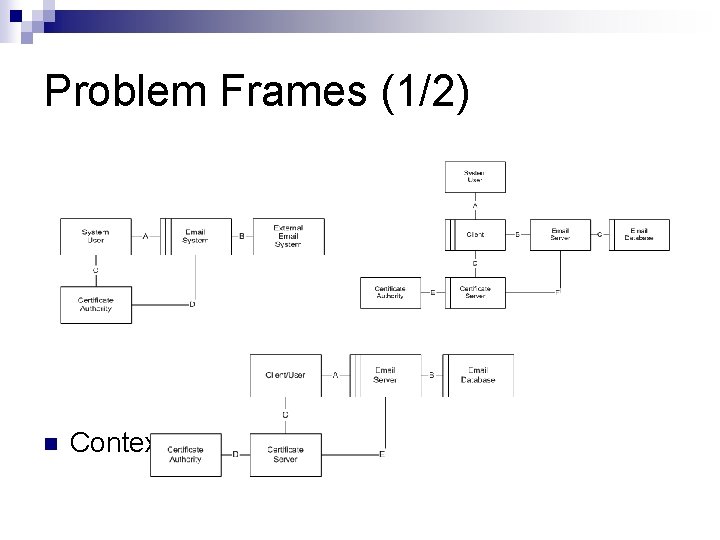
Problem Frames (1/2) n Context Diagrams

Problem Frames (2/2) n Usefulness of Problem Frames ¨ Shared Phenomena ¨ Idea of system participants ¨ Derive requirements ¨ Being able to focus on specific parts
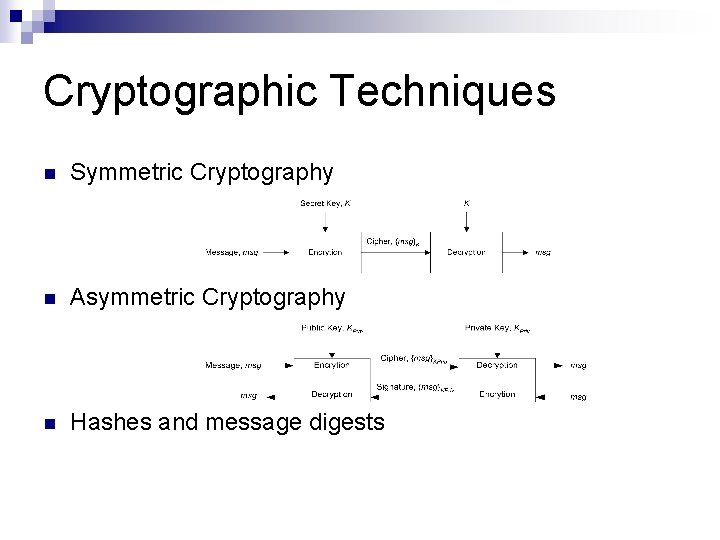
Cryptographic Techniques n Symmetric Cryptography n Asymmetric Cryptography n Hashes and message digests
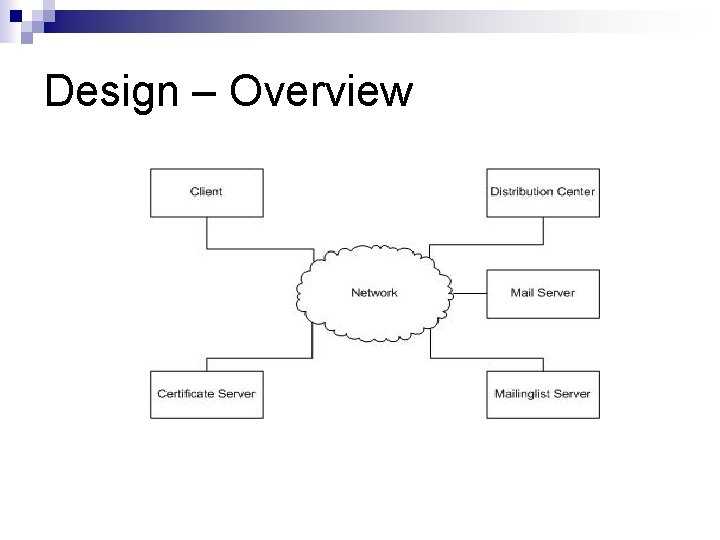
Design – Overview
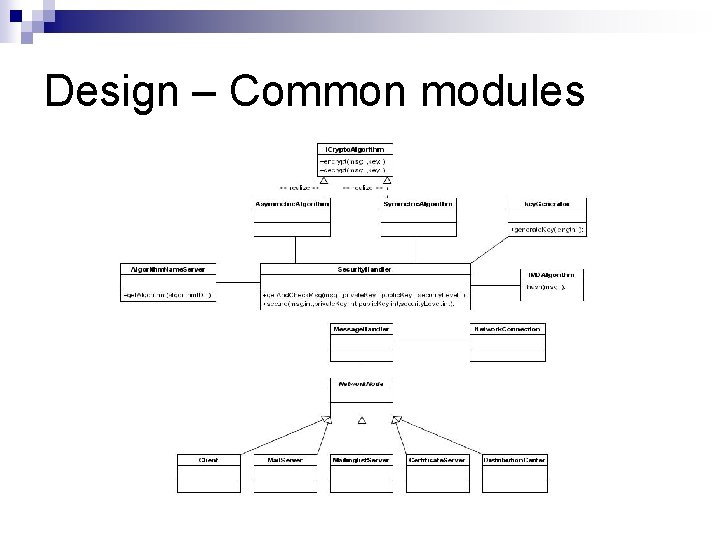
Design – Common modules
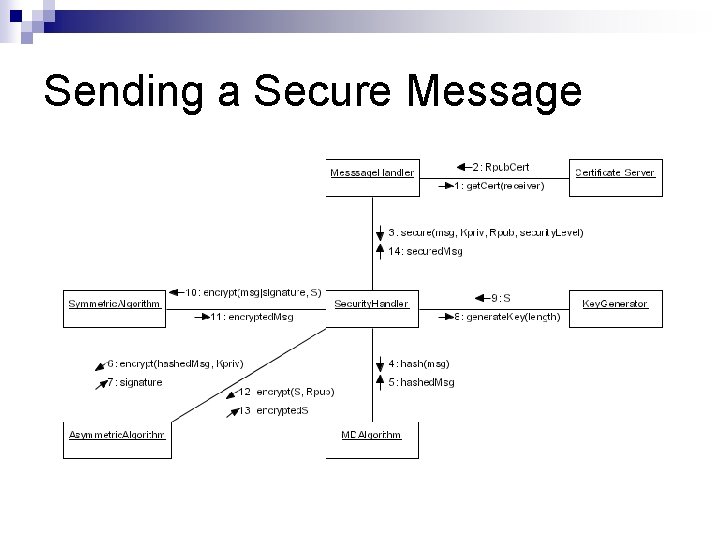
Sending a Secure Message
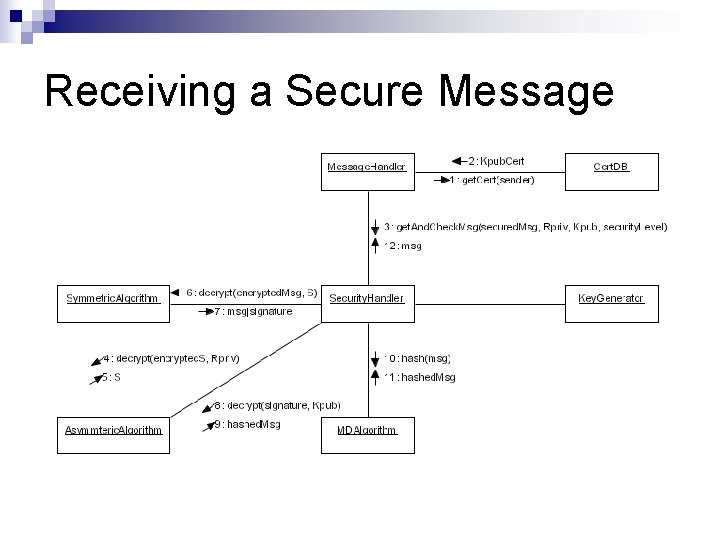
Receiving a Secure Message
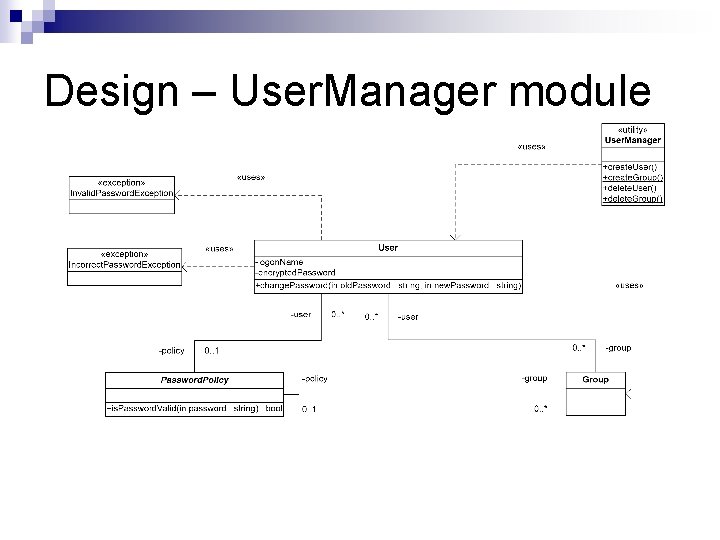
Design – User. Manager module

Models Privacy and Authentication in Communication with Mail Server (SRP Protocol) n Privacy and Authentication in Email Communication n Secure Distribution Centers n Spin Alloy
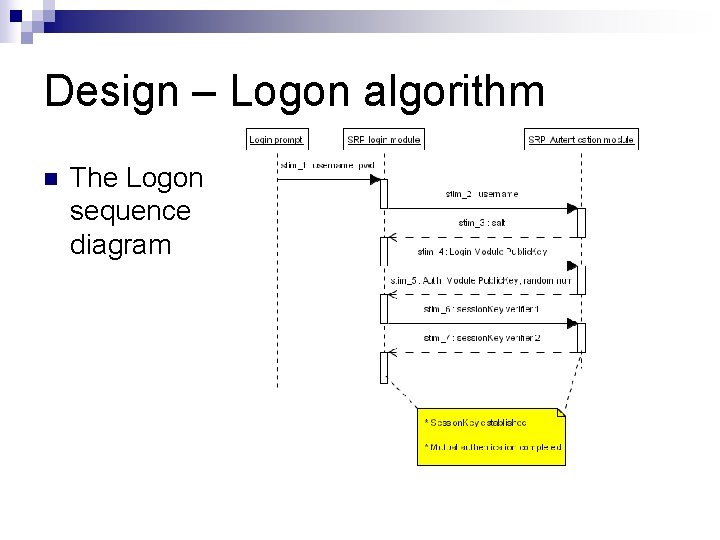
Design – Logon algorithm n The Logon sequence diagram
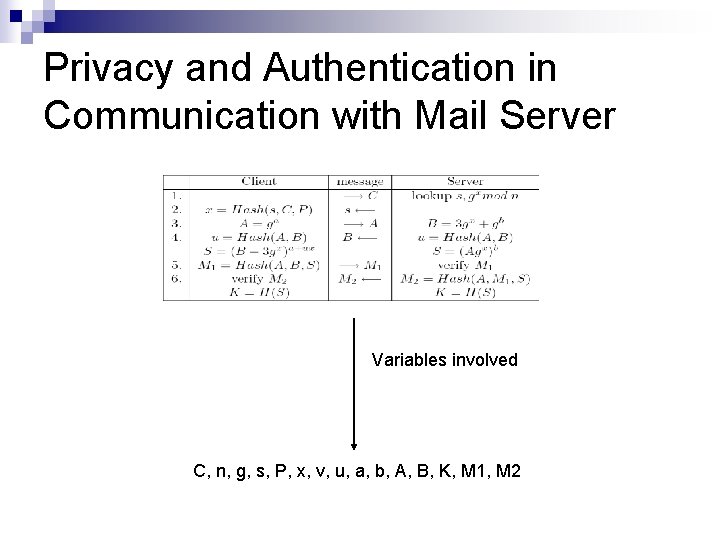
Privacy and Authentication in Communication with Mail Server Variables involved C, n, g, s, P, x, v, u, a, b, A, B, K, M 1, M 2
Privacy and Authentication in Communication with Mail Server Client Server Intruder
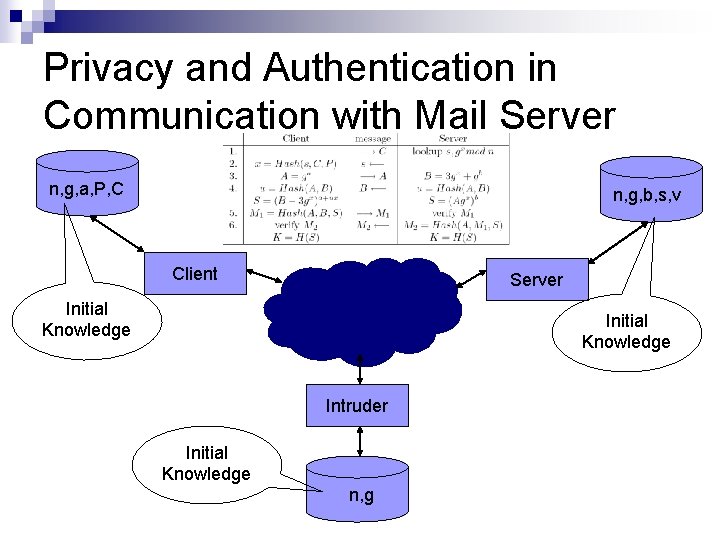
Privacy and Authentication in Communication with Mail Server n, g, a, P, C n, g, b, s, v Client Server Initial Knowledge Intruder Initial Knowledge n, g
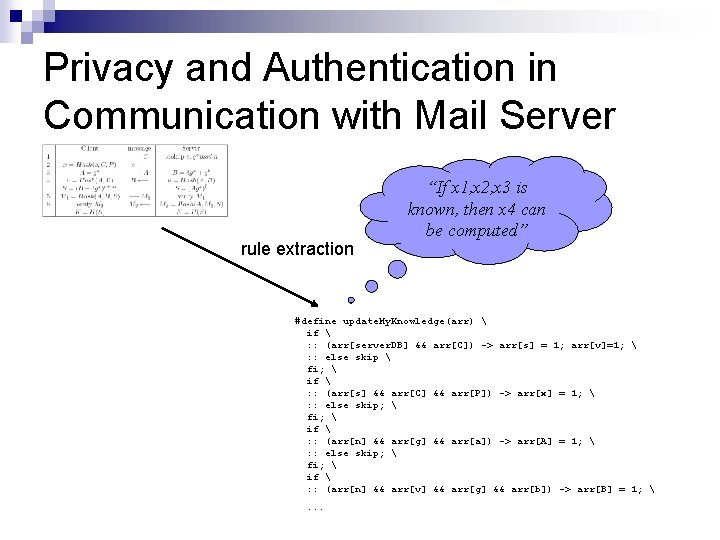
Privacy and Authentication in Communication with Mail Server rule extraction “If x 1, x 2, x 3 is known, then x 4 can be computed” #define update. My. Knowledge(arr) if : : (arr[server. DB] && arr[C]) -> arr[s] = 1; arr[v]=1; : : else skip fi; if : : (arr[s] && arr[C] && arr[P]) -> arr[x] = 1; : : else skip; fi; if : : (arr[n] && arr[g] && arr[a]) -> arr[A] = 1; : : else skip; fi; if : : (arr[n] && arr[v] && arr[g] && arr[b]) -> arr[B] = 1; . . .
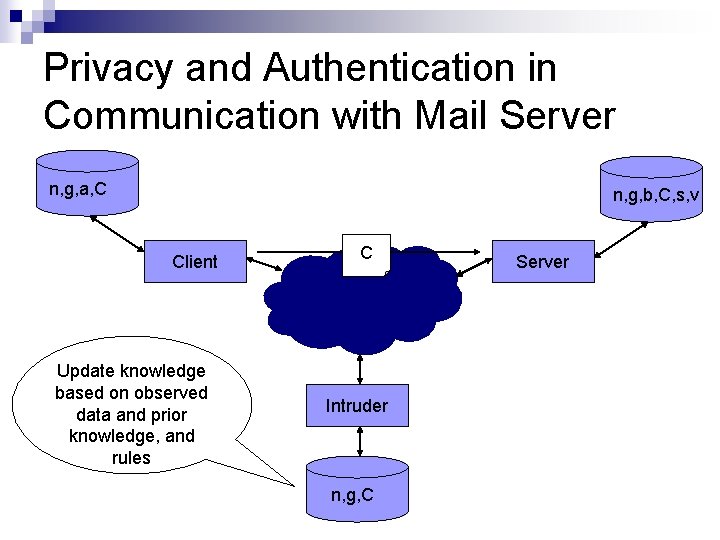
Privacy and Authentication in Communication with Mail Server n, g, a, C n, g, b, C, s, v Client Update knowledge based on observed data and prior knowledge, and rules C Intruder n, g, C Server

Privacy and Authentication in Communication with Mail Server Intruder proctype Intruder(mtype self; mtype party) { mtype msg; /* initialize knowledge of Intruder*/ knowledge. Of. Intruder[g] = 1; knowledge. Of. Intruder[n] = 1; /* do : : : : : : : : send random messages can only send that information it knows */ knowledge. Of. Intruder[C] -> net ! self, party, C; knowledge. Of. Intruder[n] -> net ! self, party, n; knowledge. Of. Intruder[g] -> net ! self, party, g; knowledge. Of. Intruder[s] -> net ! self, party, s; knowledge. Of. Intruder[P] -> net ! self, party, P; knowledge. Of. Intruder[x] -> net ! self, party, x; knowledge. Of. Intruder[v] -> net ! self, party, v; knowledge. Of. Intruder[a] -> net ! self, party, a; knowledge. Of. Intruder[b] -> net ! self, party, b; knowledge. Of. Intruder[A] -> net ! self, party, A; knowledge. Of. Intruder[B] -> net ! self, party, B; knowledge. Of. Intruder[K] -> net ! self, party, K; knowledge. Of. Intruder[M 1] -> net ! self, party, M 1; knowledge. Of. Intruder[M 2] -> net ! self, party, M 2; /* if intruder doesn't know, it can send junk */ net ! self, party, junk; : : net ? eval(party), eval(self), msg -> knowledge. Of. Intruder[msg] = 1; update. My. Knowledge(knowledge. Of. Intruder); od learn new values }

Privacy and Authentication in Communication with Mail Server Modeled and verified three scenarios 1. Intruder cannot learn session key based on prior knowledge, observed data and rules 2. Intruder cannot impersonate the server 3. Intruder cannot impersonate the client Assumptions Rules are complete, etc.

Q&A
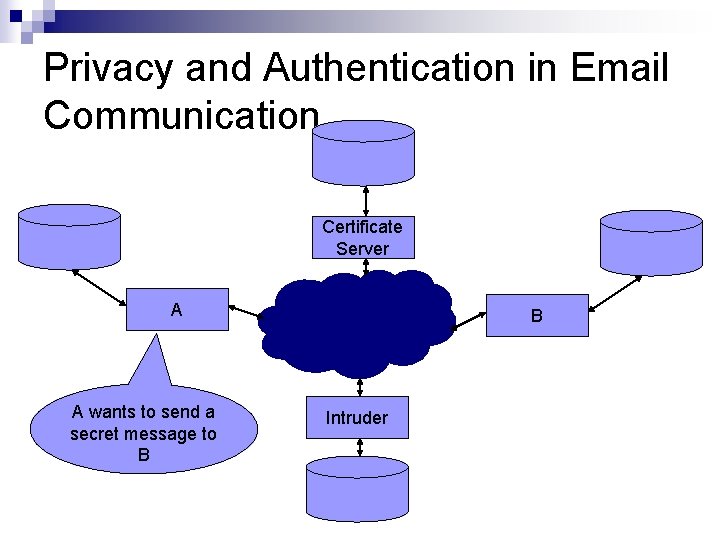
Privacy and Authentication in Email Communication Certificate Server A A wants to send a secret message to B B Intruder
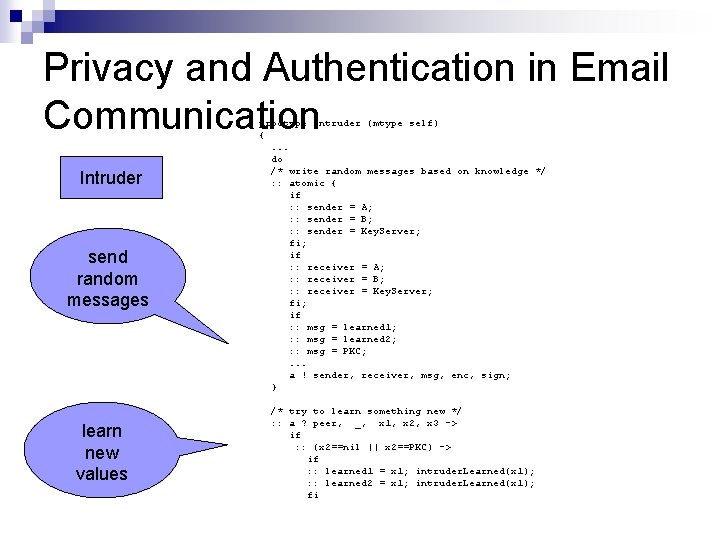
Privacy and Authentication in Email Communication Intruder send random messages learn new values proctype Intruder (mtype self) {. . . do /* write random messages based on knowledge */ : : atomic { if : : sender = A; : : sender = B; : : sender = Key. Server; fi; if : : receiver = A; : : receiver = B; : : receiver = Key. Server; fi; if : : msg = learned 1; : : msg = learned 2; : : msg = PKC; . . . a ! sender, receiver, msg, enc, sign; } /* try to learn something new */ : : a ? peer, _, x 1, x 2, x 3 -> if : : (x 2==nil || x 2==PKC) -> if : : learned 1 = x 1; intruder. Learned(x 1); : : learned 2 = x 1; intruder. Learned(x 1); fi
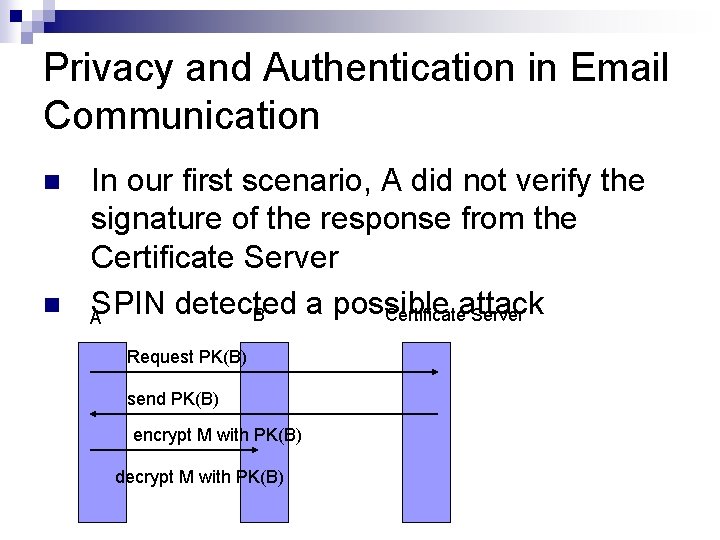
Privacy and Authentication in Email Communication n n In our first scenario, A did not verify the signature of the response from the Certificate Server SPIN detected a possible B Certificateattack Server A Request PK(B) send PK(B) encrypt M with PK(B) decrypt M with PK(B)
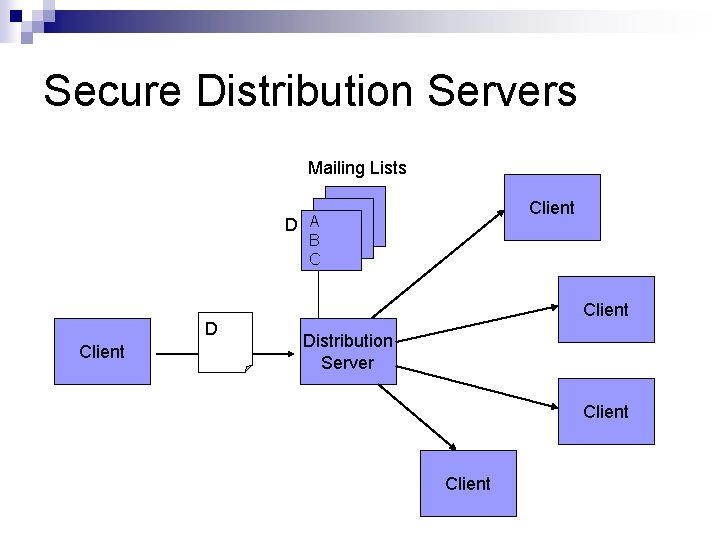
Secure Distribution Servers Mailing Lists Client D A B C D Client Distribution Server Client
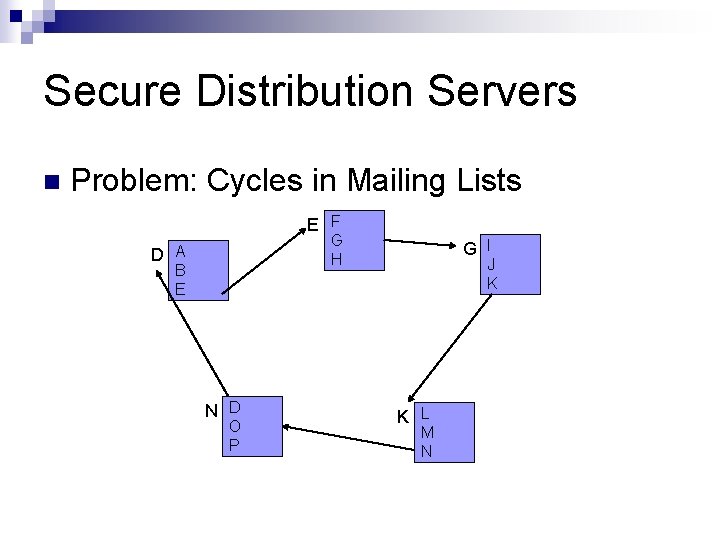
Secure Distribution Servers n Problem: Cycles in Mailing Lists E F G H D A B E N D O P G I J K K L M N

Secure Distribution Servers Solution: Introduce a TTL (Time to live) field inside an email message, that is decremented each time the message reaches a distribution server n We modeled our system in Alloy and showed that with the above extension no infinite cycles are possible anymore. n
- Slides: 27