CSE 4095 Digital Signatures and Hashing 8 1






















- Slides: 33

CSE 4095 Digital Signatures and Hashing 8 -1

Outline v v v Will introduce Diffie-Hellman based encryption Digital Signatures (using ideas from Diffie. Hellman) Hash Functions 8 -2

Diffie-Hellman Key Exchange v First published public-key algorithm § “New Directions in Cryptography, ” 1976 v. A number of commercial products employ this key exchange technique v Purpose: key establishment v Effectiveness: depends on the difficulty of computing discrete logarithms § Given gx mod p hard to determine x 8 -3

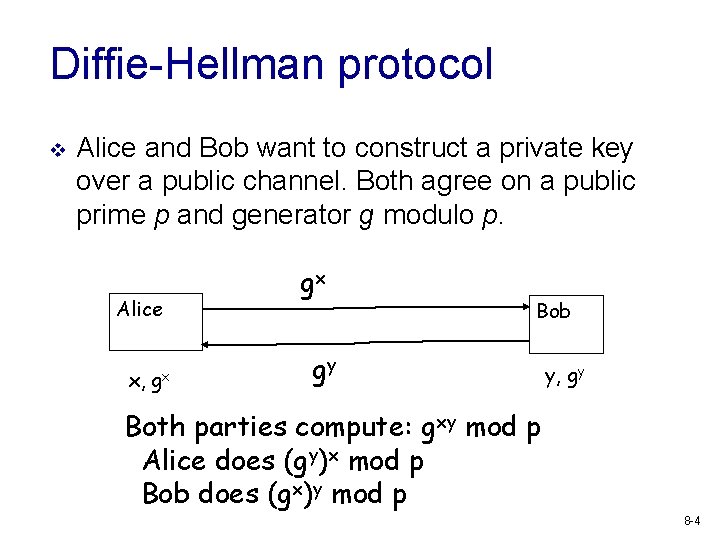
Diffie-Hellman protocol v Alice and Bob want to construct a private key over a public channel. Both agree on a public prime p and generator g modulo p. Alice x, gx gx Bob gy y, gy Both parties compute: gxy mod p Alice does (gy)x mod p Bob does (gx)y mod p 8 -4

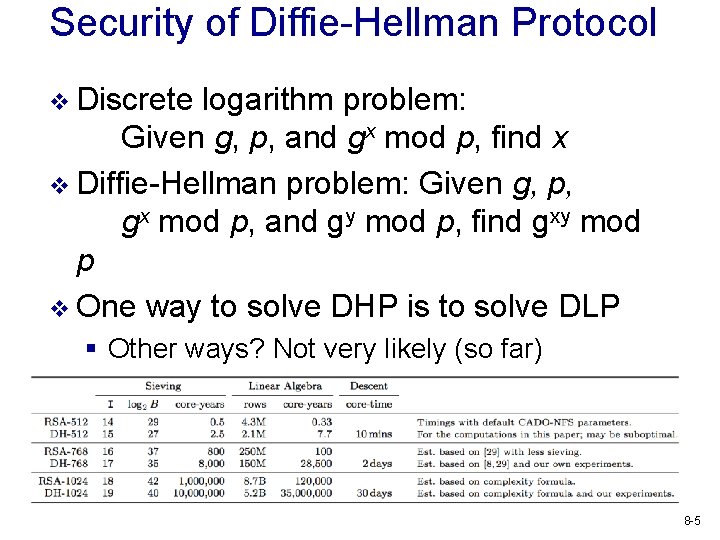
Security of Diffie-Hellman Protocol v Discrete logarithm problem: Given g, p, and gx mod p, find x v Diffie-Hellman problem: Given g, p, gx mod p, and gy mod p, find gxy mod p v One way to solve DHP is to solve DLP § Other ways? Not very likely (so far) v Solving DLP seems to be hard for large p 8 -5

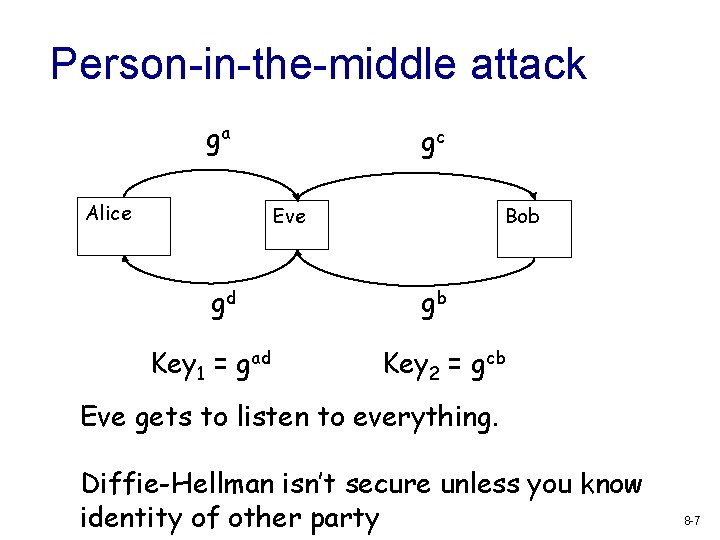
Person-in-the-middle attack ga Alice gc Eve gd Key 1 = gad Bob gb Key 2 = gcb Eve gets to listen to everything. Diffie-Hellman isn’t secure unless you know identity of other party 8 -7

El. Gamal v Invented in 1984 § T. Elgamal, “A public key cryptosystem and a signature scheme based on discrete logarithms”, Proc. of Crypto, 1984 v Used in digital signature standard (DSS), S/MIME email standard 8 -9

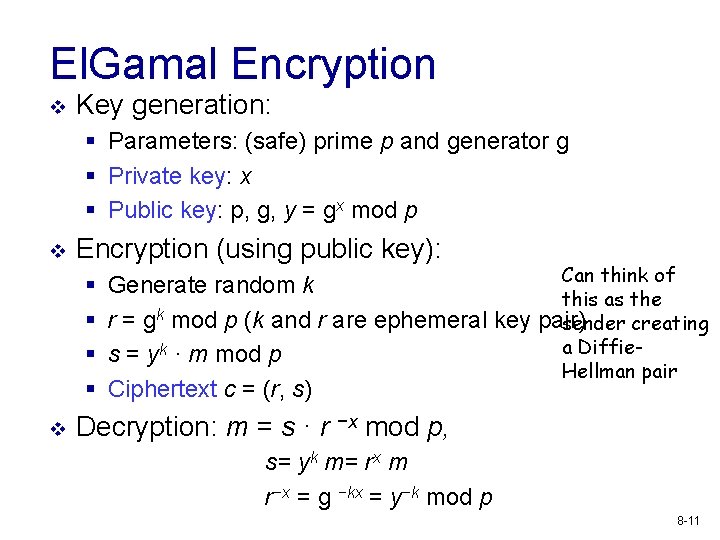
El. Gamal Encryption v Key generation: § Parameters: (safe) prime p and generator g § Private key: x § Public key: p, g, y = gx mod p v Encryption (using public key): § § v Can think of Generate random k this as the r = gk mod p (k and r are ephemeral key pair) sender creating a Diffies = yk · m mod p Hellman pair Ciphertext c = (r, s) Decryption: m = s · r −x mod p, s= yk m= rx m r−x = g −kx = y−k mod p 8 -11

El. Gamal example v Key generation: § p=19, g=10 § Private key: x=5 § Public key: p, g, y = 10 5 mod 19=3 v Encryption (using public key) message m=17: § § v Generate random k, suppose k=6 r = gk mod p =106 mod 19=11 s = yk · m mod p =36 *17 mod 19 = 7*17 mod 19=5 Ciphertext c = (11, 5) Decryption: § m = s · r−x mod p = 5*(115 mod 19)-1 mod 19=5*7 -1 mod 19 =5*11 mod 19=17 8 -12

About El. Gamal v Security relies on the discrete log problem and not on factoring § Find private key using public key § Discover one time key k v v Ciphertext twice as long as the plaintext Secure random number generator required for k § Non-deterministic encryption: the same plaintext will always result in different ciphertexts 8 -13

Digital Signatures v v In a public key encryption we were providing confidentiality, hiding a message from an observer The goal of a digital signature is primarily to provide integrity, be sure that no one has altered a message Alice’s sk signing K A key plaintext signing plaintext, algorithm signature Alice’s vk verification Akey plaintext, verification plaintext signature algorithm 8 -14

Exercise: Signature security v Consider possible security goals and adversary powers for a signature scheme (similar to our exercise for encryption) 8 -15

Signature Security v Possible goals: § Recover key § Create new signature for same message § Create signature for random message § Create signature for chosen message Known as chosen message unforgeability under chosen message attack (EU-CMA) v Possible capabilities: § See public key § See a single signature § See multiple signatures for random messages § See multiple signatures for chosen messages § See signatures for adaptively chosen messages 8 -16

Constructing Digital Signatures v v v Possible to create a digital signature from the factoring and discrete logarithm assumptions Don’t assume that swapping encryption and decryption will give you a digital signature algorithm Often requires use of a cryptographic hash function (later this class) 8 -17

Diffie-Hellman based Signature Signing Input m, secret key sk. A=x (random value) v Sample random value k v Compute r = gk mod p v Compute s = (H(m) - sk. A*r)/k mod p v Output (r, s) Verification: Input m, r, s, pk. A =gx v Check if g. H(m) = pk. Ar*rs mod p =gxr*gks = gxr*gk(H(m) - sk. A*r)/k= = gxr*g(H(m) - x*r)=g. H(m) 8 -18

Current trends in asymmetric crypto v v v v Both RSA and Diffie-Hellman are showing their 40 year age Cryptanalytic attacks are getting better Increasing key size frequently is difficult (for usability reasons) Quantum computers can efficiently break both schemes Still primary mechanisms on the internet Timing and side-channels are major problems Researchers are designing new systems that are resistant to quantum computer attacks 8 -19

Hash Functions v v Used to compress length of data Many different applications that require different properties Denoted H: {0, 1}*-> {0, 1}256 (may have different length output 80, 128, 512) Should be easy to compute 8 -20

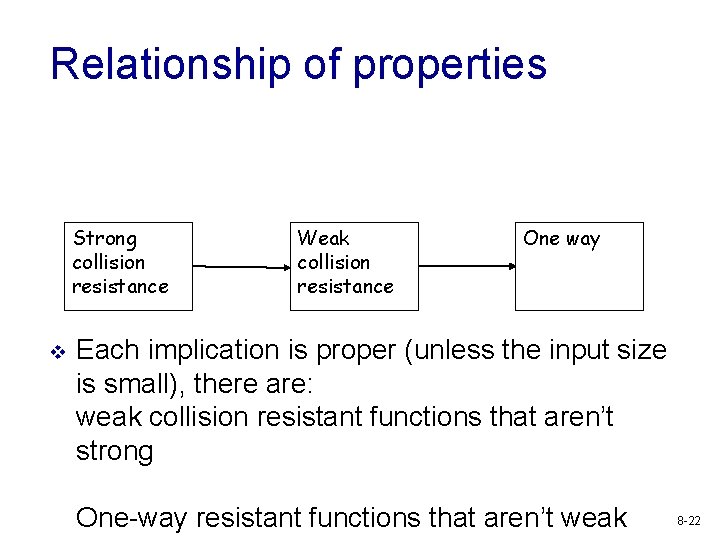
Definitions of security v Also known as message digest v Preimage resistant (one-way property): given H(m), but not m, it is find an m. Second preimage resistant (weak collision resistant): Given m 1, it is difficult to find m 2 s. t. H(m 2)=H(m 1). (Strong) Collision resistant: Computationally infeasible to find m 1, m 2, s. t. H(m 1)=H(m 2) v v 8 -21

Relationship of properties Strong collision resistance v Weak collision resistance One way Each implication is proper (unless the input size is small), there are: weak collision resistant functions that aren’t strong One-way resistant functions that aren’t weak 8 -22

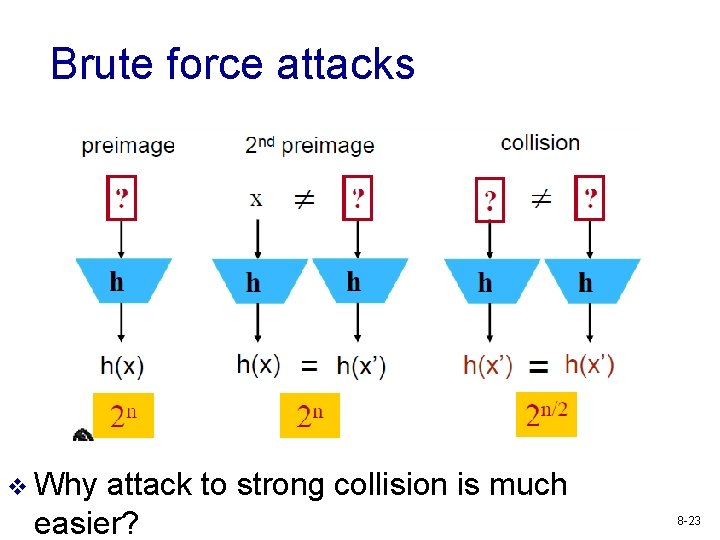
Brute force attacks v Why attack to strong collision is much easier? 8 -23

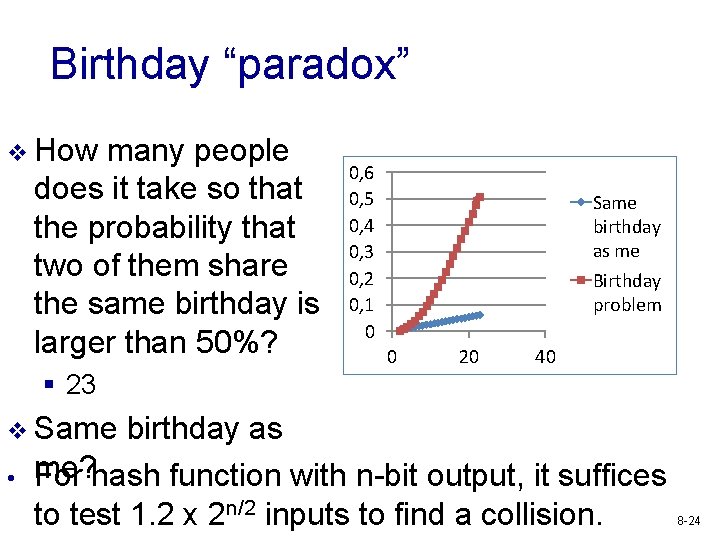
Birthday “paradox” v How many people does it take so that the probability that two of them share the same birthday is larger than 50%? 0, 6 0, 5 0, 4 0, 3 0, 2 0, 1 0 Same birthday as me Birthday problem 0 20 40 § 23 v Same • birthday as me? For hash function with n-bit output, it suffices to test 1. 2 x 2 n/2 inputs to find a collision. 8 -24

Length of hash function output v Due to birthday attack, the length of hash outputs in general should double the key length of block ciphers § SHA-256, SHA-384, SHA-512 to match the new key lengths (128, 192, 256) in AES 8 -25

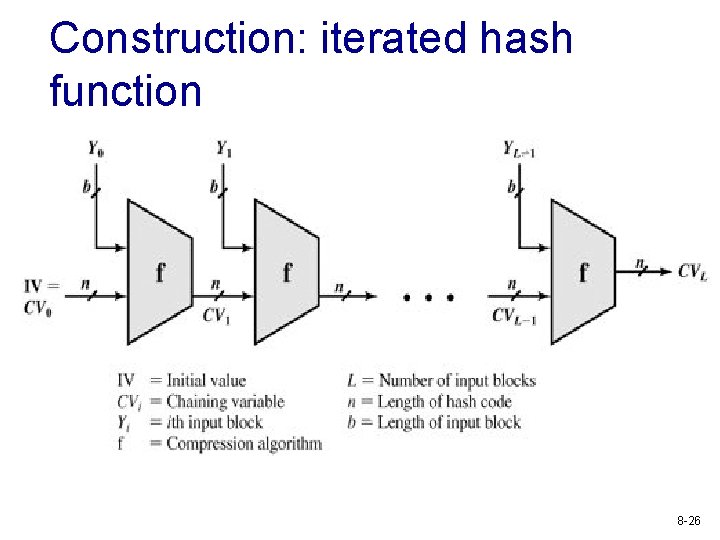
Construction: iterated hash function 8 -26

Iterated hash function v v Partition message into L fixed-size b-bit blocks Compression function f: take two inputs § Chaining variable (n bits) from previous step § b-bit block, b > n (compression) § Can be constructed from block ciphers, must be collision resistant v Motivation § If the compression function is collision resistant, then so is the iterated hash function § Designing secure hash function reduces to designing collision-resistant compression function that takes fixed-size input 8 -27

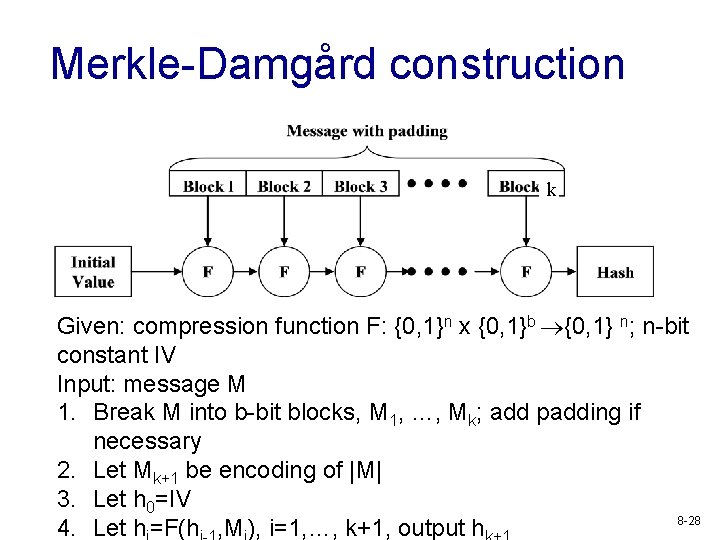
Merkle-Damgård construction k Given: compression function F: {0, 1}n x {0, 1}b {0, 1} n; n-bit constant IV Input: message M 1. Break M into b-bit blocks, M 1, …, Mk; add padding if necessary 2. Let Mk+1 be encoding of |M| 3. Let h 0=IV 8 -28 4. Let h =F(h , M ), i=1, …, k+1, output h

Commonly used hash functions v MD 5 v SHA family § SHA-0, SHA-1, SHA-2, and v SHA-3 (different construction paradigm) v Whirlpool v Tiger v RIPEMD-128, 160, 256, 320 § Improved version of RIPEMD 8 -29

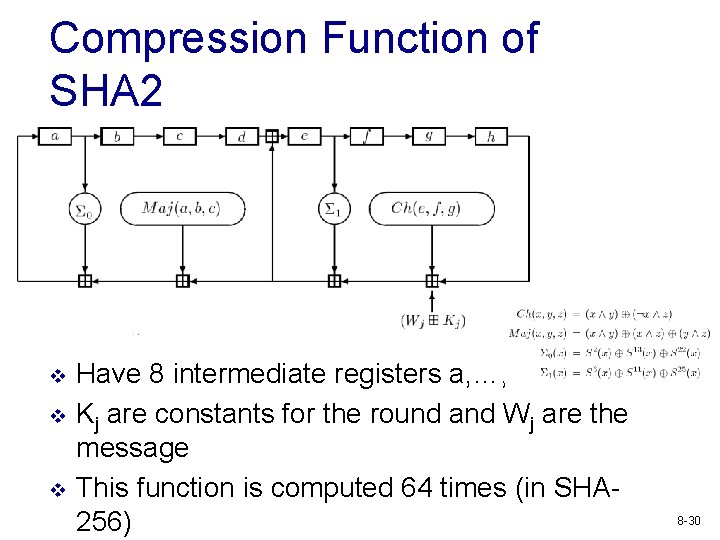
Compression Function of SHA 2 v v v Have 8 intermediate registers a, …, h Kj are constants for the round and Wj are the message This function is computed 64 times (in SHA 256) 8 -30

Attacks: MD 5 v MD 4: 128 bits, 1990. Broken v MD 5: 128 bits, 1992. Wide Usage. v Flaw found in 1996, collision attacks in 2004 v Current best attacks: Xie-Feng (2009) in 220 v Preimage attacks : still hard ~ 2123. 4 (Sasaki-Aoki) 8 -31

Attack: the SHA Family v SHA-0: v made a standard by NIST in 1993 § based on Merkle-Damgard design. 160 bits § In 1998 collisions against SHA-0 were demonstrated in 261 steps SHA-1: US standard [NIST, FIPS PUB 180 -1] § 160 -bit message digest § Collisions were found in 269 steps Wang, Yin, Yu, Crypto 2005 § NIST requires federal agencies to move to SHA-2 after 2010 § SHA-1 was considered broken 8 -32

SHA-2 v SHA-224, SHA-256, SHA-384, SHA-512 § Outputs 224, 256, 384, and 512 bits, respectively § No real security concerns, yet v Similar design principle as SHA-1 (and MD 5) 8 -33

SHA-3 v v v 2007: Request for submissions of new hash functions 2008: Submissions deadline. Received 64 entries. Announced first-round selections of 51 candidates 2009: First SHA-3 candidate conference in Feb. Announced 14 Second Round Candidates in July 2010: After one year public review of the algorithms, the second SHA-3 candidate conference was held in Aug. Announced 5 thirdround candidates in Dec 2011: Public comment for final round 8 -34

Applications of hash functions v Password hashing v Many other applications § Message Integrity § § Digital signature Pseudo-random string generation/key derivation Commitment … v Message authentication codes (MAC) can be built out of hash functions provide “symmetric” signatures 8 -35

Review of crypto functionality v Symmetric Encryption: provides confidentiality in the setting where two parties share a cryptographic key § Needs to be construction from block cipher, mode of operation matters v v Message authentication code: provides integrity in the setting where two parties share a cryptographic key Public-key encryption: provides confidentiality where receiver’s identity is public Digital signature: provides integrity when sender’s identity is public Hash function: provides fixed length representation of data, hard to find collisions or preimages 8 -36