CSC 532 TERM PAPER SECURITY AS NONFUNCTIONAL REQUIREMENT








- Slides: 13

CSC 532 TERM PAPER SECURITY AS NON-FUNCTIONAL REQUIREMENT IN SOFTWARE ENGINEERING PUNIT S VORA

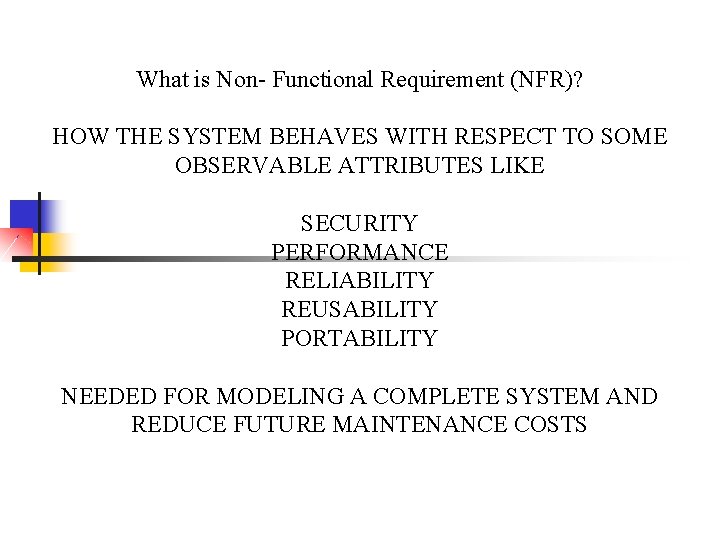
What is Non- Functional Requirement (NFR)? HOW THE SYSTEM BEHAVES WITH RESPECT TO SOME OBSERVABLE ATTRIBUTES LIKE SECURITY PERFORMANCE RELIABILITY REUSABILITY PORTABILITY NEEDED FOR MODELING A COMPLETE SYSTEM AND REDUCE FUTURE MAINTENANCE COSTS

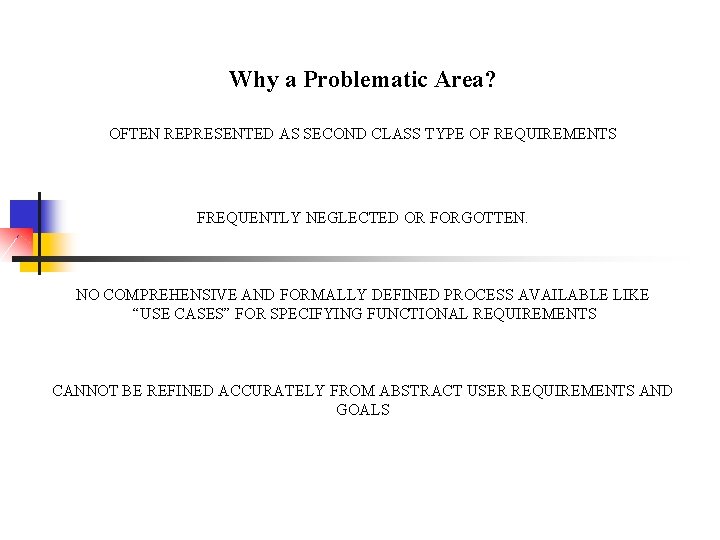
Why a Problematic Area? OFTEN REPRESENTED AS SECOND CLASS TYPE OF REQUIREMENTS FREQUENTLY NEGLECTED OR FORGOTTEN. NO COMPREHENSIVE AND FORMALLY DEFINED PROCESS AVAILABLE LIKE “USE CASES” FOR SPECIFYING FUNCTIONAL REQUIREMENTS CANNOT BE REFINED ACCURATELY FROM ABSTRACT USER REQUIREMENTS AND GOALS

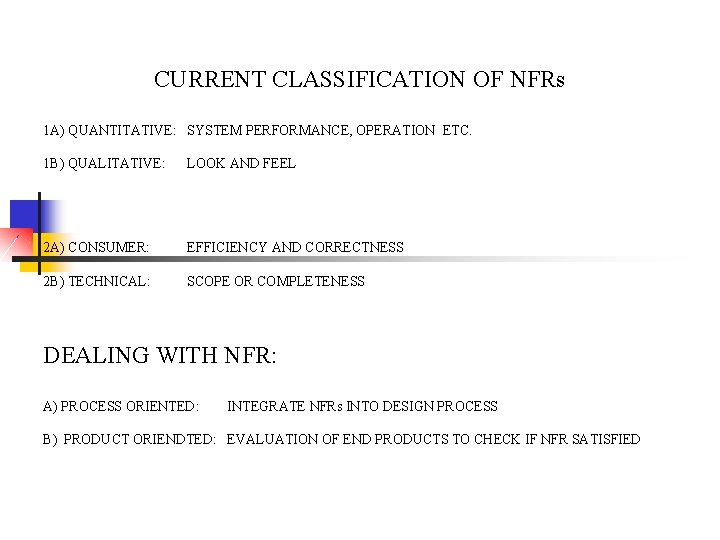
CURRENT CLASSIFICATION OF NFRs 1 A) QUANTITATIVE: SYSTEM PERFORMANCE, OPERATION ETC. 1 B) QUALITATIVE: LOOK AND FEEL 2 A) CONSUMER: EFFICIENCY AND CORRECTNESS 2 B) TECHNICAL: SCOPE OR COMPLETENESS DEALING WITH NFR: A) PROCESS ORIENTED: INTEGRATE NFRs INTO DESIGN PROCESS B) PRODUCT ORIENDTED: EVALUATION OF END PRODUCTS TO CHECK IF NFR SATISFIED

PROPOSED APPROACHES FOR NFR CAPTURE AND MODELLING: 1) Goal Graph Method: Includes non-functional requirement goals (security, performance etc. ), satisficing goals (category of design decisions that may be adopted in order to satisfy one or more NFRs) and argumentation goals (formal or informal claims that provide support of counter evidence for a goal or goal refinement). 2) Performance Case: which are modeled like use cases (contains identifying information, description of action steps and links to other related information). 3) Abuse cases: A family of complete transactions between one or more actors and system that result in harm to the system or the process. It also includes a description of the range of security privileges that may be abused. 4) UMLsec: An extension to UML to specifically incorporate the security part of the NFRs. The extension is given in form of a UML profile using the standard UML extension mechanisms.

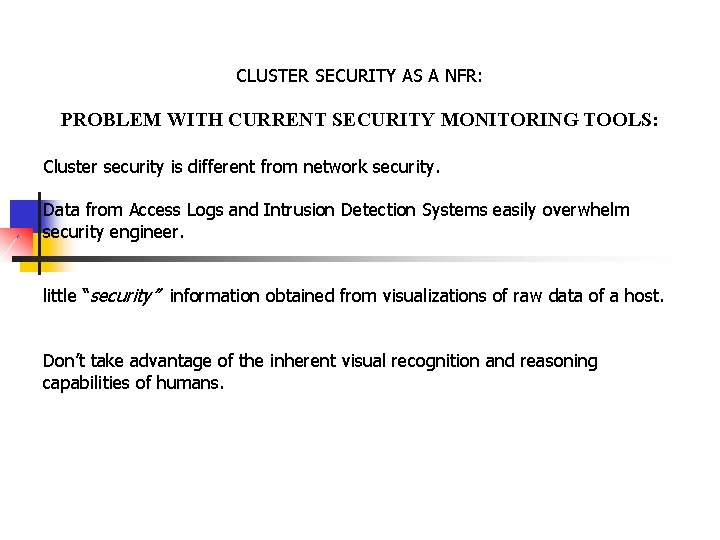
CLUSTER SECURITY AS A NFR: PROBLEM WITH CURRENT SECURITY MONITORING TOOLS: Cluster security is different from network security. Data from Access Logs and Intrusion Detection Systems easily overwhelm security engineer. little “security” information obtained from visualizations of raw data of a host. Don’t take advantage of the inherent visual recognition and reasoning capabilities of humans.

NVision. CC (CC = Cluster Computing) : A SECURITY MONITORING TOOL FOR CLUSTER COMPUTING developed by NCSA (National Center for Supercomputing Applications at UIUC) Emphasizes Situational Awareness & Visual Reasoning Visual Information Seeking Mantra (“Overview first, zoom and filter, then details on-demand”) Easily comprehensible visual interface on single screen. Alerts point to nodes where potential security breach observed.

NVision. CC: contd. implemented as an interface plug-in extension of Clumon, a cluster performance monitoring tool developed at NCSA Depends on the data collection and logging facilities of Clumon It currently includes : Process Monitor Module : tracks processes on each node Port Scanner Module : scans each node for open network ports File Integrity Module : validates identity of disk files, particularly files that hackers frequently try to alter

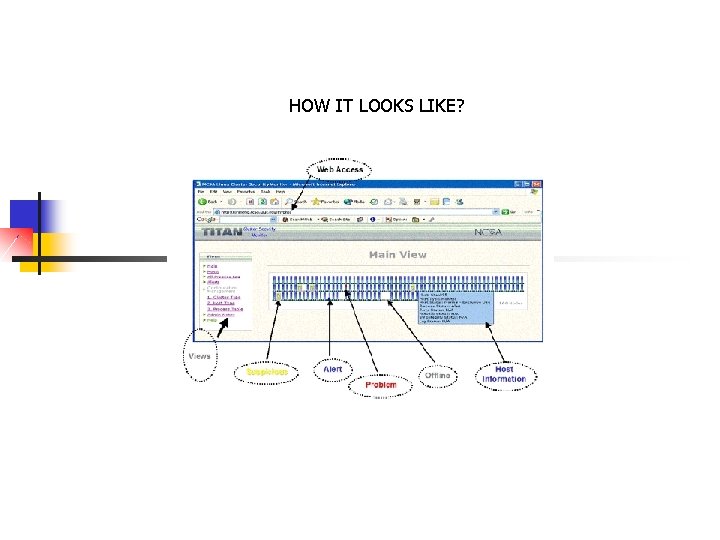
Basic Visualization design elements of NVision. CC : • All nodes of cluster shown on one screen: adjacent in space. • Overview of entire cluster with drill down to areas of interest and raw data details on demand at the individual node level. • Different levels of security status: critical, bad, suspicious, and normal. • Process Alert View: provides decision-making assistance by consolidating alerts from all nodes into a prioritized list. • Host Level View

HOW IT LOOKS LIKE?

Advantages of NVision. CC, Why is it good? Tailored specifically for Cluster security. Is near real-time, thus security status can be continuously monitored. Allows easy visualization with ‘deeper’ views for the select host/node among the cluster.

CONCLUSION essential to develop methods that allow the treatment of non-functional requirement in tandem with the functional requirements Cluster security is a critical non-functional requirement that has to be addressed differently from network security NVision. CC is designed effectively to monitor security on large size clusters

THANKYOU!! QUESTIONS? ?