CSC 482582 Computer Security CrossSite Security CSC 482582











- Slides: 20

CSC 482/582: Computer Security Cross-Site Security CSC 482/582: Computer Security

Topics 1. Java. Script and Same Origin Policy 2. Cross-Site Scripting (XSS) 3. Protecting Against XSS CSC 482/582: Computer Security

Java. Script in the Browser • Common web scripting language. • Standardized as ECMAScript (currently version 5). • Runs in browser via a Just-In-Time (JIT) compiler. • Can be included in a web page via • Inline <script> blocks. • Remote scripts via <script src=“…> • javascript: URLs in HTML params and CSS. • CSS expression(…) syntax • Event handlers (onload, onclick, onerror, …) • Timers (set. Timeout, set. Interval) • eval(…) calls from within Java. Script. CSC 482/582: Computer Security Slide #3

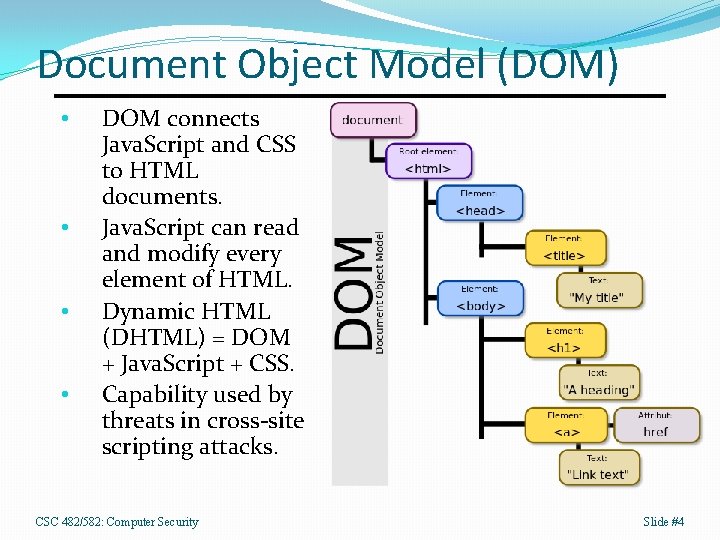
Document Object Model (DOM) • • DOM connects Java. Script and CSS to HTML documents. Java. Script can read and modify every element of HTML. Dynamic HTML (DHTML) = DOM + Java. Script + CSS. Capability used by threats in cross-site scripting attacks. CSC 482/582: Computer Security Slide #4

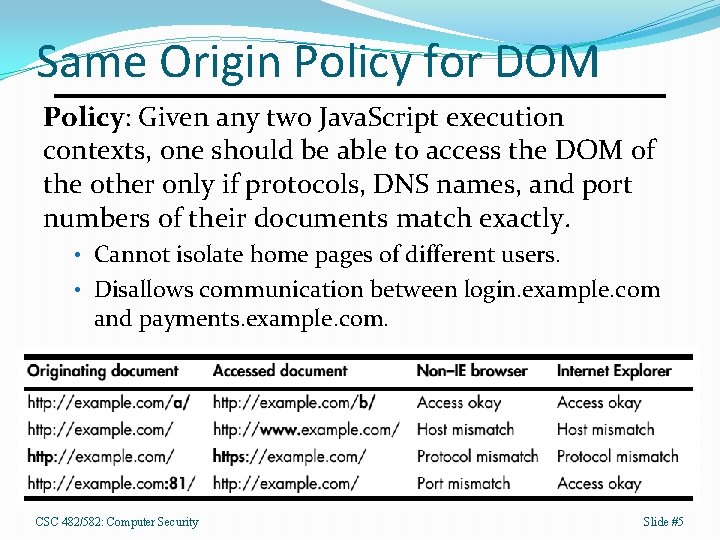
Same Origin Policy for DOM Policy: Given any two Java. Script execution contexts, one should be able to access the DOM of the other only if protocols, DNS names, and port numbers of their documents match exactly. • Cannot isolate home pages of different users. • Disallows communication between login. example. com and payments. example. com. CSC 482/582: Computer Security Slide #5

Cross-Site Scripting (XSS) • Attacker causes a legitimate web server to send user executable content (Javascript, Flash Active. Script) of attacker’s choosing. • Impact of XSS • Account hijacking. • Browser hijacking (malware hosting. ) • Information leakage (stored form values, etc. ) • Virtual defacement. CSC 482/582: Computer Security

XSS Examples • My. Space worm (October 2005) • When someone viewed Samy’s profile: • Set him as friend of viewer. • Incorporated code in viewer’s profile. • Paypal (2006) • XSS redirect used to steal money from Paypal users in a phishing scam. • Imgur/8 chan worm (September 2015) • Imgur vulnerability + 8 chan copied XSS string from HTML 5 storage into web page • Allowed persistent XSS using local storage. CSC 482/582: Computer Security

XSS Key Steps 1. 2. 3. 4. Attacker sends code to web application. Legitimate user accesses web app. Web app sends attacker code to user. User’s browser executes code. CSC 482/582: Computer Security

Why does XSS Work? • Same-Origin Policy • Browser only allows Javascript from site X to access cookies and other data from site X. • Attacker needs to make attack come from site X. • Vulnerable Server Program • Any program that returns user input without filtering out dangerous code. CSC 482/582: Computer Security

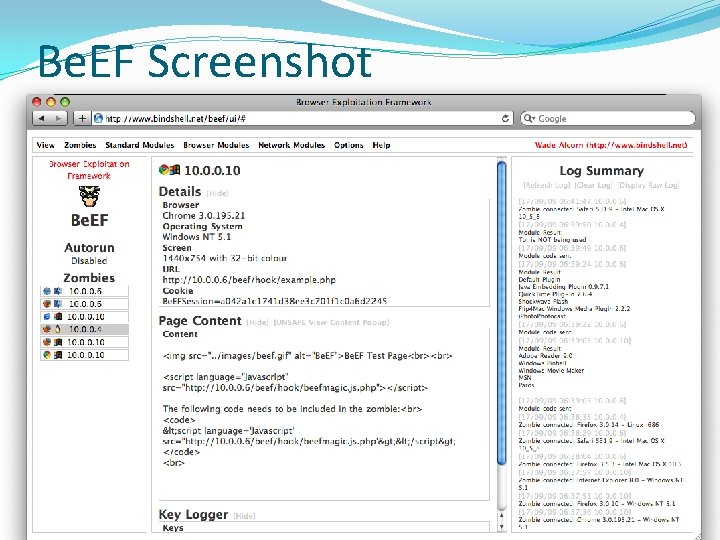
Browser Exploitation Framework Be. EF hooks browsers via XSS exploit Can use as stored or reflected XSS. Hooked browsers are bots controlled by Be. EF. Exploitation modules run on hooked browsers to View browsing history. Identify authenticated sessions. Phishing and other social engineering attacks. Port scans of network browser is running on. Reverse proxy into network browser is running on. Use Metasploit. CSC 482/582: Computer Security

Be. EF Screenshot CSC 482/582: Computer Security

Mitigating XSS Can't we just filter out all dangerous HTML tags and stop the attacker from running Java. Script code? CSC 482/582: Computer Security

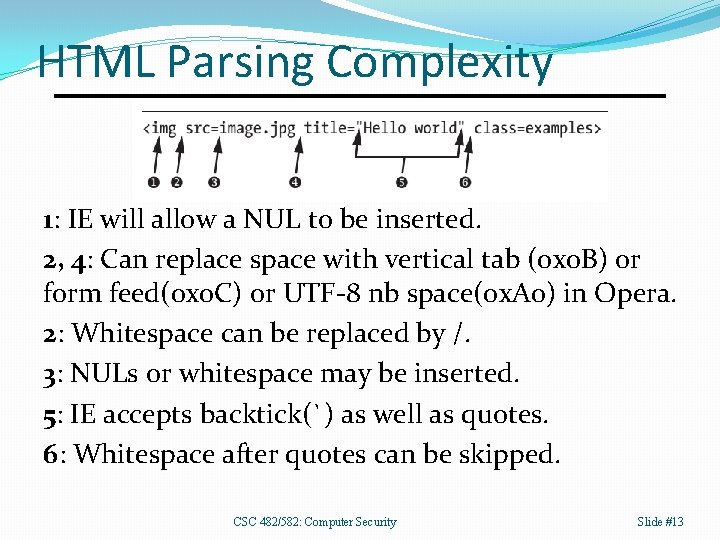
HTML Parsing Complexity 1: IE will allow a NUL to be inserted. 2, 4: Can replace space with vertical tab (0 x 0 B) or form feed(0 x 0 C) or UTF-8 nb space(0 x. A 0) in Opera. 2: Whitespace can be replaced by /. 3: NULs or whitespace may be inserted. 5: IE accepts backtick(`) as well as quotes. 6: Whitespace after quotes can be skipped. CSC 482/582: Computer Security Slide #13

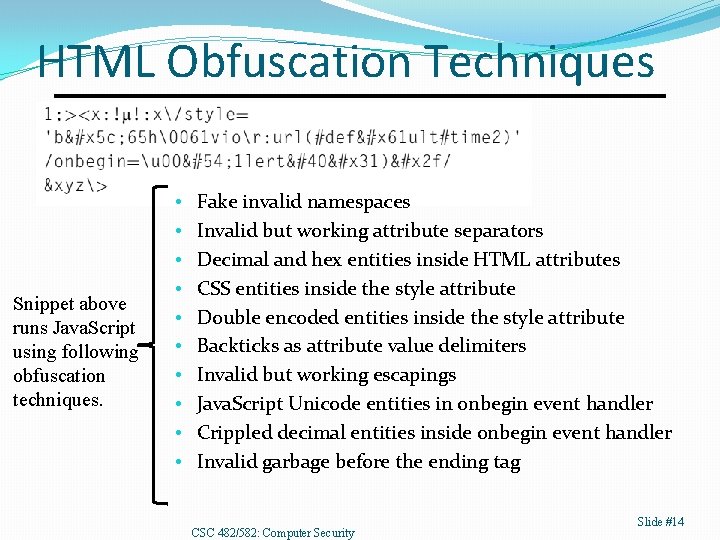
HTML Obfuscation Techniques Snippet above runs Java. Script using following obfuscation techniques. • • • Fake invalid namespaces Invalid but working attribute separators Decimal and hex entities inside HTML attributes CSS entities inside the style attribute Double encoded entities inside the style attribute Backticks as attribute value delimiters Invalid but working escapings Java. Script Unicode entities in onbegin event handler Crippled decimal entities inside onbegin event handler Invalid garbage before the ending tag CSC 482/582: Computer Security Slide #14

What about output encoding? If we can't filter our input, could we just replace all the angle brackets in our output with HTML entities, so they don't get treated as HTML tags? CSC 482/582: Computer Security Slide #15

Web Browser Context Model CSC 482/582: Computer Security Slide #16

Java. Script Security Issues Each <script> block is processed individually in the order encountered on page. • Syntax error won’t stop later <script>s from running. • All scripts can set variables in global namespace. • Scripts can replace built-in classes and functions. Nested script inclusion requires nested encoding <div onclick=“set. Timeout(‘do_stuff(’user_string’)’, 1)”> 1. HTML parser extracts onclick and puts in DOM. 2. When button clicked, timeout is set. 3. When timeout triggered, inside script executed. To be secure, double-encode user_string with JS backslashes, then encode with HTML entities. CSC 482/582: Computer Security Slide #18

What can we do about XSS? 1. Use a security encoding library like • Microsoft Anti-XSS (now built into. NET) • OWASP Java Encoder • Ruby on Rails has built-in XSS protection 2. Configure a Content Security Policy on your web server. CSC 482/582: Computer Security Slide #19

Content Security Policy Server provides Content-Security-Policy header which • Disables inline Java. Script. • Disables dynamic code evaluation. • Permits JS inclusion only from a white list of sources. Prevents XSS if • Application architected to not directly include any Java. Script via <script> tags or included in other tags. • CSP configuration is not too permissive. See https: //developer. mozilla. org/en. US/docs/Web/HTTP/CSP for more details. CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. Brian Chess and Jacob West, Secure Programming with Static Analysis, Addison-Wesley, 2007. Daswani et. al. , Foundations of Security, Apress, 2007. Seth Fogie et. al. , XSS Attacks: Cross-Site Scripting Exploits and Defense, Syngress, 2007. Michael Howard, David Le. Blanc, and John Viega, 19 Deadly Sins of Software Security, Mc. Graw-Hill Osborne, 2005. Nathan, http: //www. neohaxor. org/2008/12/01/csrf-vulns-onlocal-network-devices/, 2008. PCI Security Standards Council, PCI DSS Requirements and Security Assessment Procedures, v 1. 2, 2008. Stuttart and Pinto, The Web Application Hacker’s Handbook, 2 nd ed, Wiley, 2011. Michal Zalewski, The Tangled Web: A Guide to Securing Modern Web Applications, No Starch Press, 2012. CSC 482/582: Computer Security