CS 6910 Pervasive Computing Spring 2007 Section 6
















- Slides: 64

CS 6910 – Pervasive Computing Spring 2007 Section 6 (Ch. 6): Multiple Radio Access Prof. Leszek Lilien Department of Computer Science Western Michigan University Slides based on publisher’s slides for 1 st and 2 nd edition of: Introduction to Wireless and Mobile Systems by Agrawal & Zeng © 2003, 2006, Dharma P. Agrawal and Qing-An Zeng. All rights reserved. Some original slides were modified by L. Lilien, who strived to make such modifications clearly visible. Some slides were added by L. Lilien, and are © 2006 -2007 by Leszek T. Lilien. Requests to use L. Lilien’s slides for non-profit purposes will be gladly granted upon a written request. 1

Chapter 6 Multiple Radio Access Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 2

Outline n n n n Introduction Contention Protocols ALOHA Slotted ALOHA CSMA (Carrier Sense Multiple Access) CSMA/CD (CSMA with Collision Detection) CSMA/CA (CSMA with Collision Avoidance) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 3

6. 1. Introduction n Recall n Large # of traffic channels on each BS n n n Bec. control channels shared by many MSs for short periods n nli o )c r wa r Fo do d( e ers v Re n pli ar rse e v ch n h c l o r el n an t n co k) lin n w do ( d rw Fo MS (u l tro k w Bec. traffic channels used by 1 MS exclusively for call duration Small # of control channels on each BS el n an h a tr k) lin p (u cc i f f a tr k) c ffi n an ch Re el el n an BS Too expensive/inefficient to assign control channnel for call duration MSs compete for these few shared control channels n For call setup, etc. Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 4

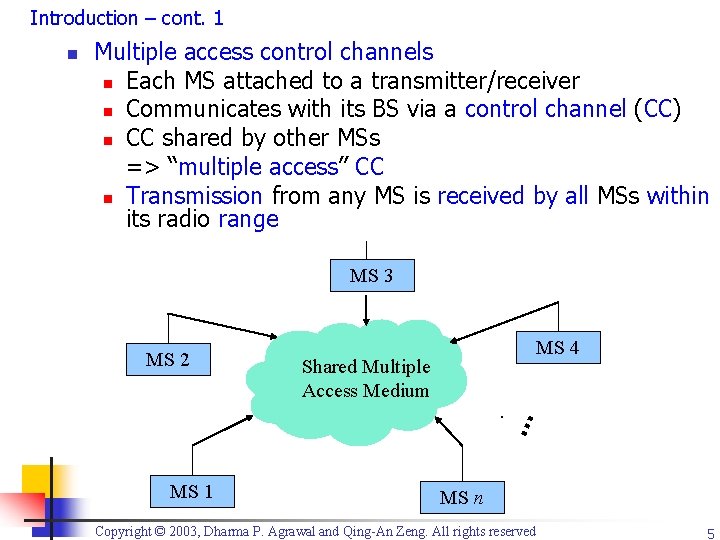
Introduction – cont. 1 Multiple access control channels n Each MS attached to a transmitter/receiver n Communicates with its BS via a control channel (CC) n CC shared by other MSs => “multiple access” CC n Transmission from any MS is received by all MSs within its radio range MS 3 MS 4 Shared Multiple Access Medium … MS 2 … n MS 1 MS n Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 5

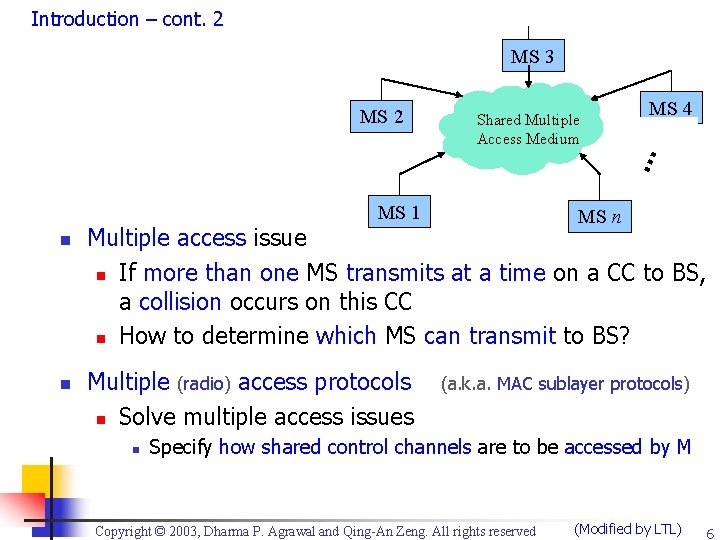
Introduction – cont. 2 MS 3 Shared Multiple Access Medium MS 1 n n MS 4 …… MS 2 MS n Multiple access issue n If more than one MS transmits at a time on a CC to BS, a collision occurs on this CC n How to determine which MS can transmit to BS? Multiple (radio) access protocols n Solve multiple access issues n (a. k. a. MAC sublayer protocols) Specify how shared control channels are to be accessed by M Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 6

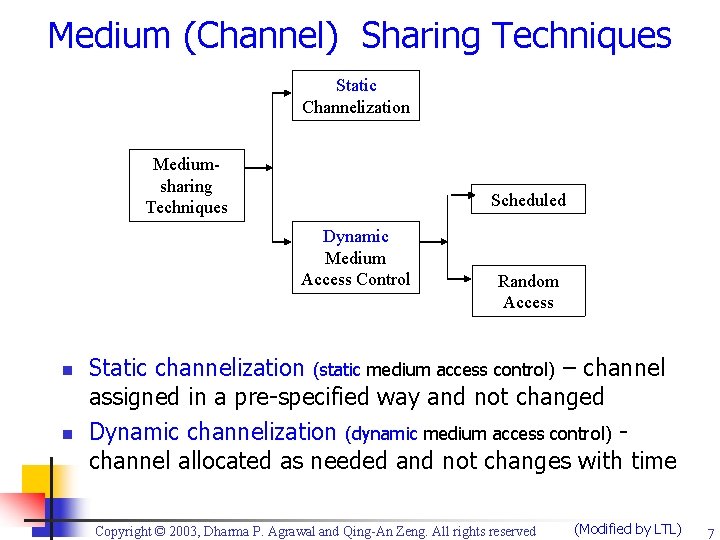
Medium (Channel) Sharing Techniques Static Channelization Mediumsharing Techniques Scheduled Dynamic Medium Access Control n n Random Access Static channelization (static medium access control) – channel assigned in a pre-specified way and not changed Dynamic channelization (dynamic medium access control) channel allocated as needed and not changes with time Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 7

6. 2. Multiple (Radio) Access Protocols = MAC Sublayer Protocols n Recall ISO Open Systems Interconnection Reference Model for networks n Communication subnetwork = 3 lowest layers of OSI n Network layer (NET) n Data link layer (DLL) n Physical layer (PHY) Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 8

6. 2. Multiple (Radio) Access Protocols = MAC Sublayer Protocols – cont. 1 n Comm subnet in wired LANs, MANs, PRNs, PANs LAN = local area network / MAN = metropolitan area network PAN = personal area network / PRN = paceket radio network n n Classic (wire!): point-to-point full-duplex channels Comm subnet in wireless systems n Broadcast half-duplex channels n n n Can emulate point-to-point xmission in wireless systems n n Broadcast over airwaves - not point-to-point Radio transmission goes from xmitter to rcvr - not full-duplex In order to use solutions (e. g. , protocols) from wired netwroks over wireless Note: broadcast possible in some wired net topologies n E. g. bus, ring, . . . Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 9

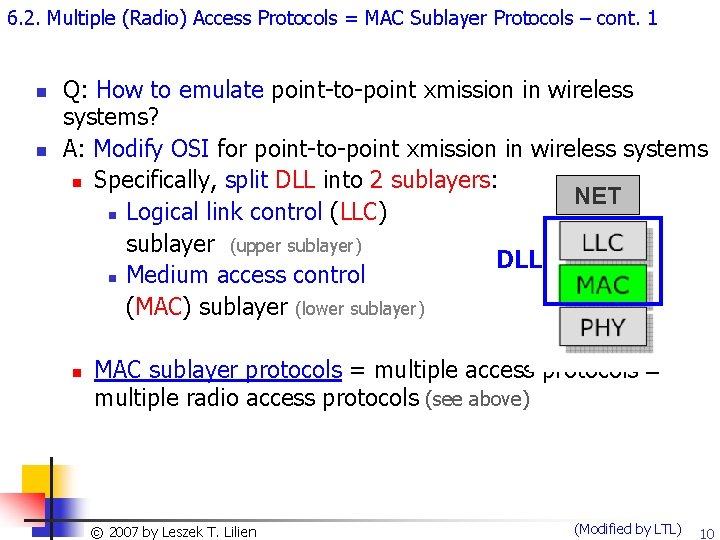
6. 2. Multiple (Radio) Access Protocols = MAC Sublayer Protocols – cont. 1 n n Q: How to emulate point-to-point xmission in wireless systems? A: Modify OSI for point-to-point xmission in wireless systems n Specifically, split DLL into 2 sublayers: NET n Logical link control (LLC) sublayer (upper sublayer) DLL n Medium access control (MAC) sublayer (lower sublayer) n MAC sublayer protocols = multiple access protocols = multiple radio access protocols (see above) Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 10

Types of Multiple Access Protocols n Types of multiple access protocols (cf. next slide): n Contention-based protocols - resolve a collision after it occurs n n Execute a collision resolution protocol after each collision Collision-free protocols collision never occurs n (a. k. a. conflict free p. ) - ensure that a E. g. , a bit-map protocol and binary countdown protocol Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 11

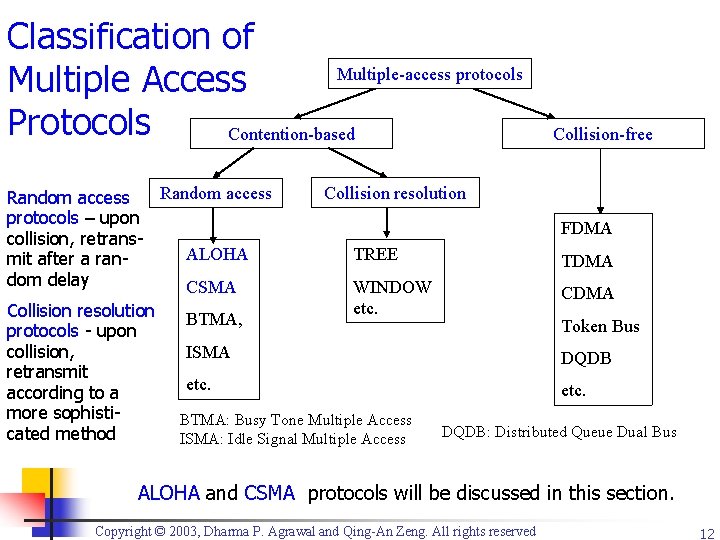
Classification of Multiple-access protocols Multiple Access Protocols Contention-based Collision-free Collision resolution Random access protocols – upon FDMA collision, retrans. TREE ALOHA mit after a ran. TDMA dom delay WINDOW CSMA CDMA etc. Collision resolution BTMA, Token Bus protocols - upon ISMA collision, DQDB retransmit etc. according to a more sophisti. BTMA: Busy Tone Multiple Access DQDB: Distributed Queue Dual Bus cated method ISMA: Idle Signal Multiple Access ALOHA and CSMA protocols will be discussed in this section. Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 12

6. 3. Contention-Based Protocols n Major categories of contention-based protocols 1) ALOHA (a. k. a. Pure ALOHA) 2) Slotted ALOHA 3) CSMA (Carrier Sense Multiple Access). . . discussed in turn below. . . Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 13

6. 3. 1. ALOHA (a. k. a. Pure ALOHA) n Developed in the 1970 s for a packet radio network by University of Hawaii n n To interconnect islands’ campuses / Single-hop network Principles: n Sender S may xmit a packet at any time (hoping no collision will occur) n S finds out whether transmission was successful or experienced a collision by listening for an ACK broadcast from the destination station n n Successful if an ACK arrrives within a time-out period T If no ACK within T, S assumes that there was a collision n => packet was lost after colliding with pckt of another station If there was a collision, S retransmits after some random time Analogy: 2 people entering a doorway simultaneously n n n Collision can occur Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 14

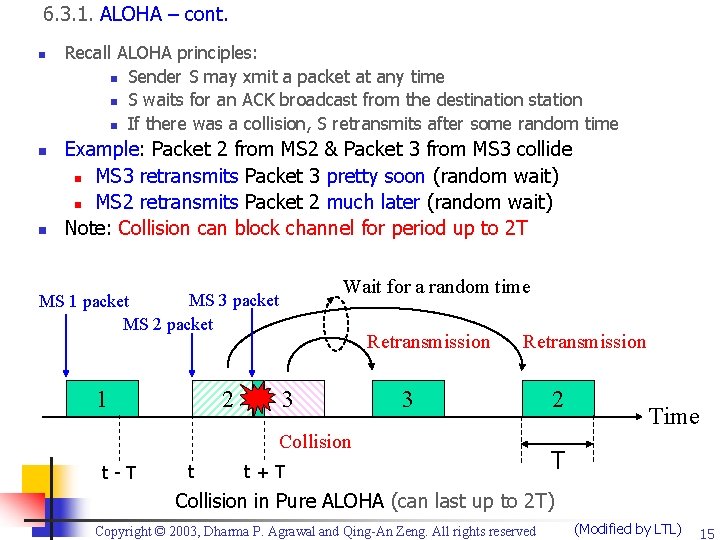
6. 3. 1. ALOHA – cont. n n n Recall ALOHA principles: n Sender S may xmit a packet at any time n S waits for an ACK broadcast from the destination station n If there was a collision, S retransmits after some random time Example: Packet 2 from MS 2 & Packet 3 from MS 3 collide n MS 3 retransmits Packet 3 pretty soon (random wait) n MS 2 retransmits Packet 2 much later (random wait) Note: Collision can block channel for period up to 2 T Wait for a random time MS 3 packet MS 1 packet MS 2 packet 1 2 Retransmission 3 Collision t-T t t+T 2 Time T Collision in Pure ALOHA (can last up to 2 T) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 15

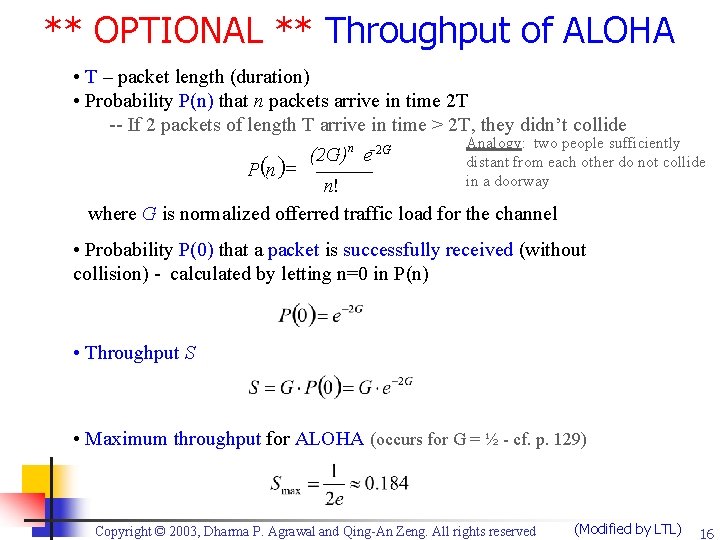
** OPTIONAL ** Throughput of ALOHA • T – packet length (duration) • Probability P(n) that n packets arrive in time 2 T -- If 2 packets of length T arrive in time > 2 T, they didn’t collide Analogy: two people sufficiently n -2 G (2 G) e distant from each other do not collide ( ) = Pn in a doorway n! where G is normalized offerred traffic load for the channel • Probability P(0) that a packet is successfully received (without collision) - calculated by letting n=0 in P(n) • Throughput S • Maximum throughput for ALOHA (occurs for G = ½ - cf. p. 129) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 16

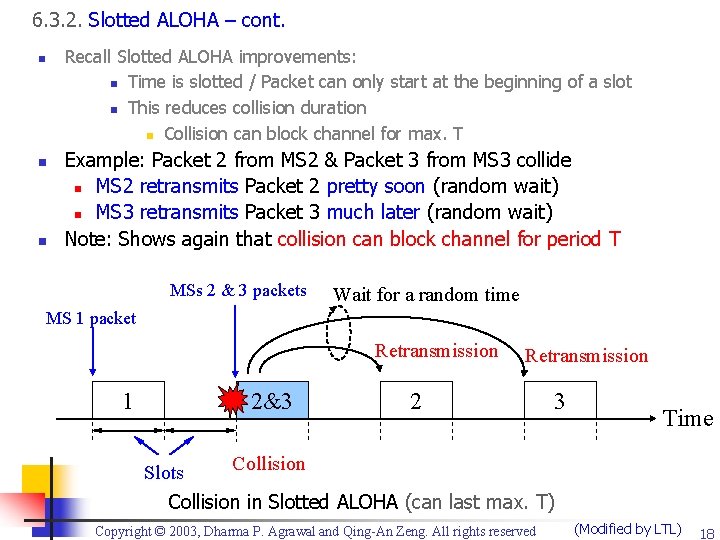
6. 3. 2. Slotted ALOHA n Improvements over Pure ALOHA: n Time is slotted n n n Slot length = packet length (duration) = T Packet transmission can start only at the beginning of a slot This reduces collision duration n n Pure ALOHA: If Packet 1 is almost finished when it collides with just-starting Packet 2, collision can lasts for nearly T+T = 2 T (details: Slide +2) Slotted ALOHA: 2 Packets can collide only when both are just starting => collision can last at most T (details: Slide +4) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 17

6. 3. 2. Slotted ALOHA – cont. n n n Recall Slotted ALOHA improvements: n Time is slotted / Packet can only start at the beginning of a slot n This reduces collision duration n Collision can block channel for max. T Example: Packet 2 from MS 2 & Packet 3 from MS 3 collide n MS 2 retransmits Packet 2 pretty soon (random wait) n MS 3 retransmits Packet 3 much later (random wait) Note: Shows again that collision can block channel for period T MSs 2 & 3 packets Wait for a random time MS 1 packet Retransmission 1 2&3 Slots Retransmission 2 3 Time Collision in Slotted ALOHA (can last max. T) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 18

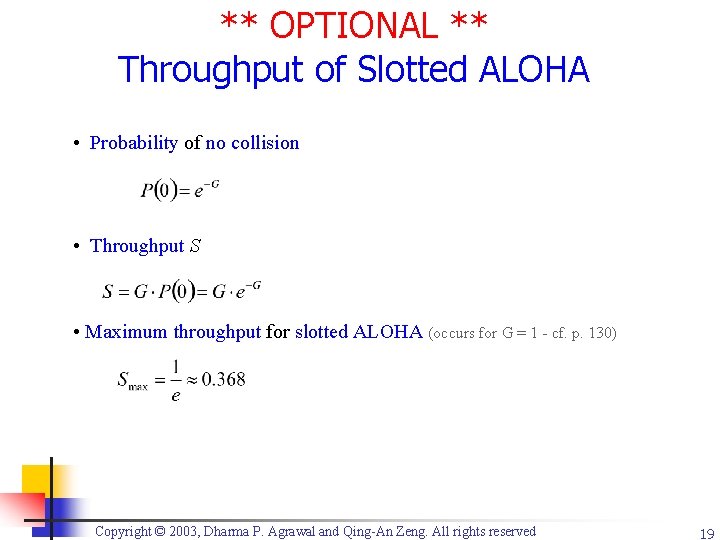
** OPTIONAL ** Throughput of Slotted ALOHA • Probability of no collision • Throughput S • Maximum throughput for slotted ALOHA (occurs for G = 1 - cf. p. 130) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 19

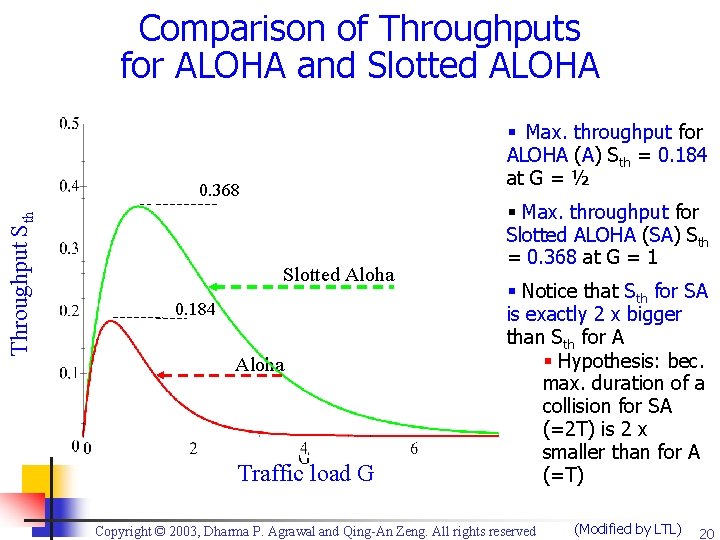
Comparison of Throughputs for ALOHA and Slotted ALOHA § Max. throughput for ALOHA (A) Sth = 0. 184 at G = ½ Throughput Sth 0. 368 Slotted Aloha 0. 184 Aloha Traffic load G § Max. throughput for Slotted ALOHA (SA) Sth = 0. 368 at G = 1 § Notice that Sth for SA is exactly 2 x bigger than Sth for A § Hypothesis: bec. max. duration of a collision for SA (=2 T) is 2 x smaller than for A (=T) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 20

6. 3. 2 -B. CSMA (Carrier Sense Multiple Access) Group of Protocols n n n Max. throughputs for Pure & Slotted ALOHA are 0. 184 & 0. 368 CSMA protocols give better throughput than both Aloha protocols n By avoiding collisions Basic improvement in all CSMA protocols over ALOHA protocols: Listen to the channel (“sense” for the presence of the “carrier”) before transmitting a packet n Don’t transmit if channel busy n n Avoids some collisions - but not all See Fig - next slide Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 21

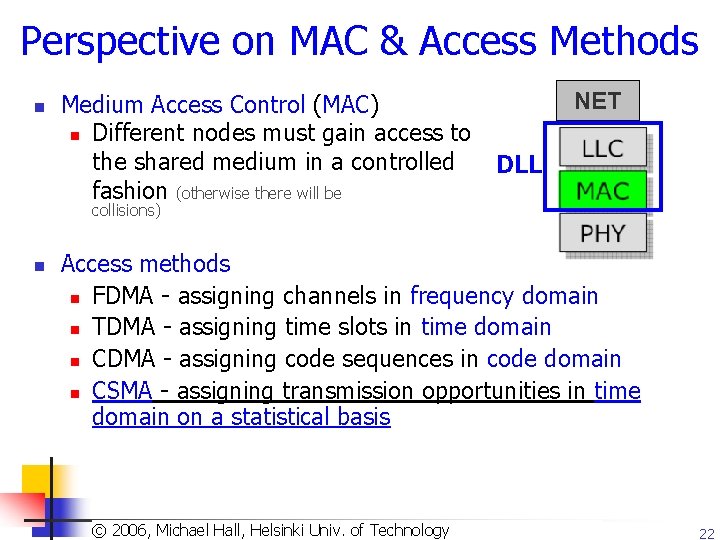
Perspective on MAC & Access Methods n Medium Access Control (MAC) n Different nodes must gain access to the shared medium in a controlled fashion (otherwise there will be NET DLL collisions) n Access methods n FDMA - assigning channels in frequency domain n TDMA - assigning time slots in time domain n CDMA - assigning code sequences in code domain n CSMA - assigning transmission opportunities in time domain on a statistical basis Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology 22

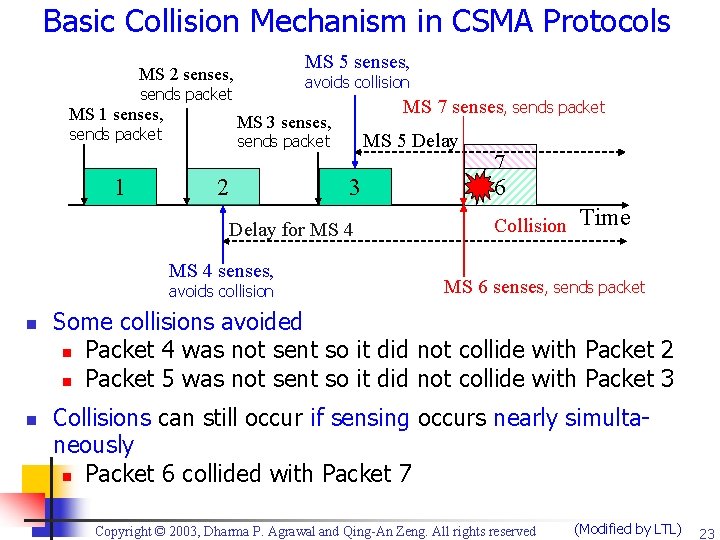
Basic Collision Mechanism in CSMA Protocols MS 5 senses, MS 2 senses, avoids collision sends packet MS 1 senses, MS 3 senses, sends packet 1 MS 7 senses, sends packet MS 5 Delay sends packet 2 3 Delay for MS 4 senses, avoids collision n n 7 6 Collision Time MS 6 senses, sends packet Some collisions avoided n Packet 4 was not sent so it did not collide with Packet 2 n Packet 5 was not sent so it did not collide with Packet 3 Collisions can still occur if sensing occurs nearly simultaneously n Packet 6 collided with Packet 7 Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 23

Types of CSMA Protocols 1) Basic CSMA, often just CSMA (Carrier Sense Multiple Access) 2) CSMA/CD (CSMA with Collision Detection) 3) CSMA/CA (CSMA with Collision Avoidance) Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 24

6. 3. 3 (Basic) CSMA Protocol n (Basic) CSMA improvement over ALOHAs: Sender S starts transmission only if no transmission is ongoing Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 25

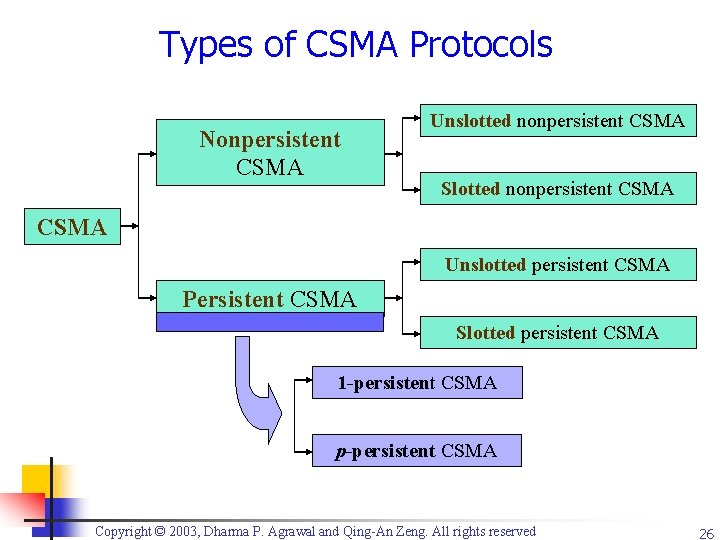
Types of CSMA Protocols Nonpersistent CSMA Unslotted nonpersistent CSMA Slotted nonpersistent CSMA Unslotted persistent CSMA Persistent CSMA Slotted persistent CSMA 1 -persistent CSMA p-persistent CSMA Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 26

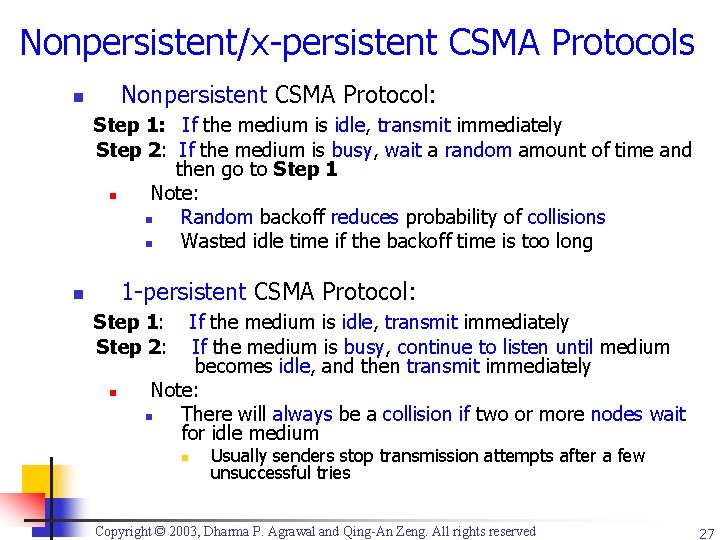
Nonpersistent/x-persistent CSMA Protocols Nonpersistent CSMA Protocol: n Step 1: If the medium is idle, transmit immediately Step 2: If the medium is busy, wait a random amount of time and then go to Step 1 n Note: n Random backoff reduces probability of collisions n Wasted idle time if the backoff time is too long 1 -persistent CSMA Protocol: n Step 1: Step 2: n If the medium is idle, transmit immediately If the medium is busy, continue to listen until medium becomes idle, and then transmit immediately Note: n There will always be a collision if two or more nodes wait for idle medium n Usually senders stop transmission attempts after a few unsuccessful tries Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 27

Nonpersistent/x-persistent CSMA Protocols – cont. n p-persistent CSMA Protocol: Slotted time required. Step 1: If the medium is idle, transmit with probability p, or delay till next time slot with probability (1 -p) Step 2: If transmission was delayed by one time slot, go to Step 1 Step 3: If the medium is busy, continue to listen until medium becomes idle, then go to Step 1 n Note: n P-persistent CSMA is a good tradeoff between nonpersistent and 1 -persistent CSMA Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 28

How to Select Probability p ? n n Assume: N - # nodes that can be active at a time (i. e. , ready to send a packet) => Np - the expected number of nodes that will attempt to transmit once the medium becomes idle Np ≥ 1 => a collision is expected to occur => to avoid collisions, network must make sure that Np < 1 Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 29

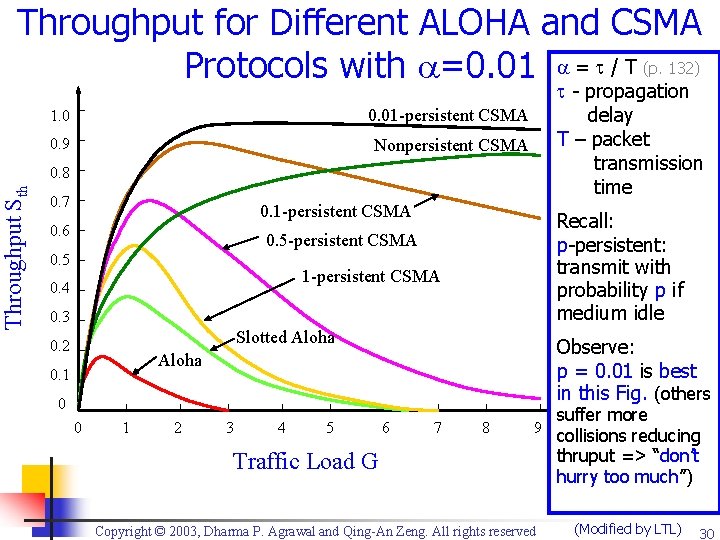
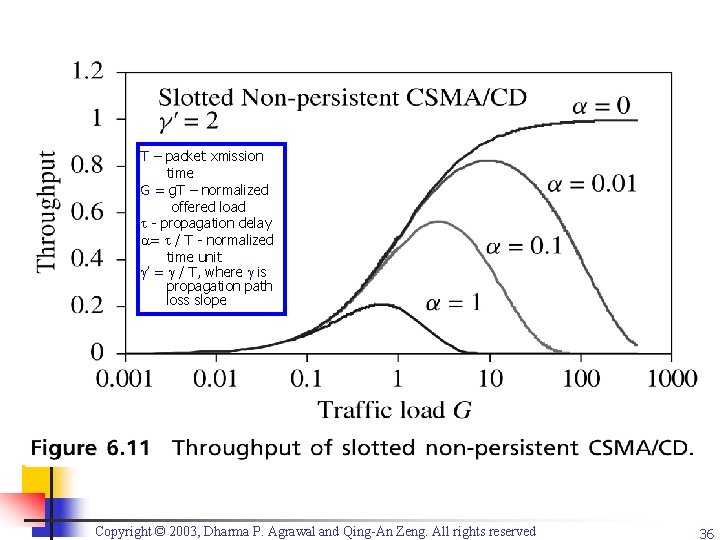
Throughput Sth Throughput for Different ALOHA and CSMA Protocols with =0. 01 = / T (p. 132) 1. 0 0. 01 -persistent CSMA 0. 9 Nonpersistent CSMA - propagation delay T – packet transmission time 0. 8 0. 7 0. 1 -persistent CSMA 0. 6 Recall: p-persistent: transmit with probability p if medium idle 0. 5 -persistent CSMA 0. 5 1 -persistent CSMA 0. 4 0. 3 Slotted Aloha 0. 2 Observe: p = 0. 01 is best in this Fig. (others Aloha 0. 1 0 0 1 2 3 4 5 6 7 8 9 Traffic Load G Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved suffer more collisions reducing thruput => “don’t hurry too much”) (Modified by LTL) 30

6. 3. 4. CSMA/CD (CSMA with Collision Detection) n n n In Basic CSMA: If 2 terminals begin sending packets at the same time, each will transmit its complete packet n Even if collision is taking place Problem: Wasting medium for an entire packet duration Solution principle (main CSMA/CD idea): Backoff immediately after a collision Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved Modified by LTL 31

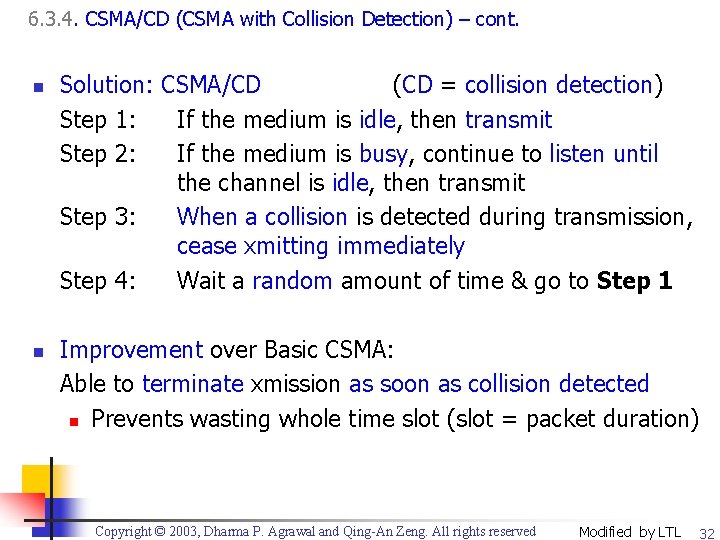
6. 3. 4. CSMA/CD (CSMA with Collision Detection) – cont. n n Solution: CSMA/CD (CD = collision detection) Step 1: If the medium is idle, then transmit Step 2: If the medium is busy, continue to listen until the channel is idle, then transmit Step 3: When a collision is detected during transmission, cease xmitting immediately Step 4: Wait a random amount of time & go to Step 1 Improvement over Basic CSMA: Able to terminate xmission as soon as collision detected n Prevents wasting whole time slot (slot = packet duration) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved Modified by LTL 32

Use of Jamming Signal in CSMA/CD n Collision Mechanisms in CSMA/CD 1) Without a jamming signal 2) With a jamming signal Jamming signal facilitates collision detection by other terminals Note: Different timing assumptions in the textbook (pp. 135 -136) Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 33

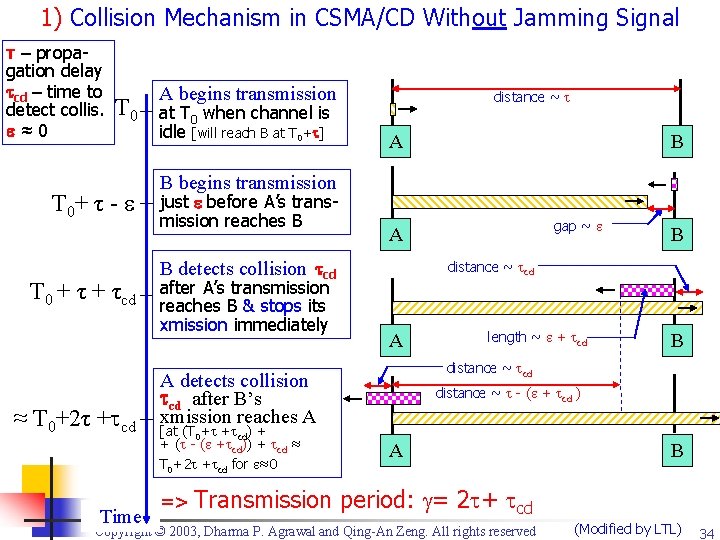
1) Collision Mechanism in CSMA/CD Without Jamming Signal τ – propagation delay cd – time to detect collis. ≈0 T 0+ τ - T 0 + τcd ≈ T 0+2τ + cd Time A begins transmission at T 0 when channel is idle [will reach B at T 0+ ] distance ~ A B B begins transmission just before A’s transmission reaches B B detects collision cd after A’s transmission reaches B & stops its xmission immediately => Transmission B distance ~ cd A length ~ + cd B distance ~ cd A detects collision cd after B’s xmission reaches A [at (T 0+ + cd) + + ( - ( + cd)) + cd ≈ T 0+2 + cd for ≈0 gap ~ A distance ~ - ( + cd ) A B period: = 2 + cd Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 34

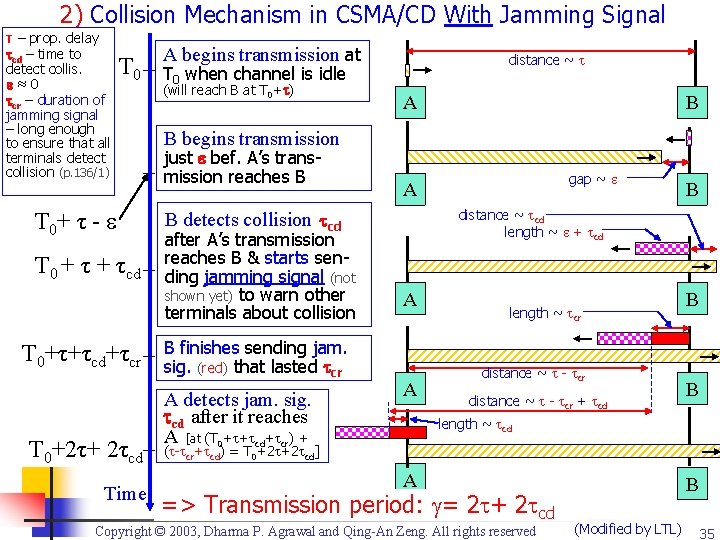
2) Collision Mechanism in CSMA/CD With Jamming Signal τ – prop. delay cd – time to detect collis. ≈0 cr – duration of jamming signal – long enough to ensure that all terminals detect collision (p. 136/1) T 0+ τ - T 0 + τcd T 0+τ+τcd+τcr T 0+2τ+ 2τcd Time A begins transmission at distance ~ T 0 when channel is idle (will reach B at T 0+ ) A B B begins transmission just bef. A’s transmission reaches B B finishes sending jam. sig. (red) that lasted cr A detects jam. sig. cd after it reaches A [at (T 0+ + cd+ cr) + B distance ~ cd length ~ + cd B detects collision cd after A’s transmission reaches B & starts sending jamming signal (not shown yet) to warn other terminals about collision gap ~ A A A length ~ cr distance ~ - cr + cd B B length ~ cd ( - cr+ cd) = T 0+2 +2 cd] A => Transmission period: = 2 + 2 cd Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved B (Modified by LTL) 35

T – packet xmission time G = g. T – normalized offered load - propagation delay = / T - normalized time unit ’ = / T, where is propagation path loss slope Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 36

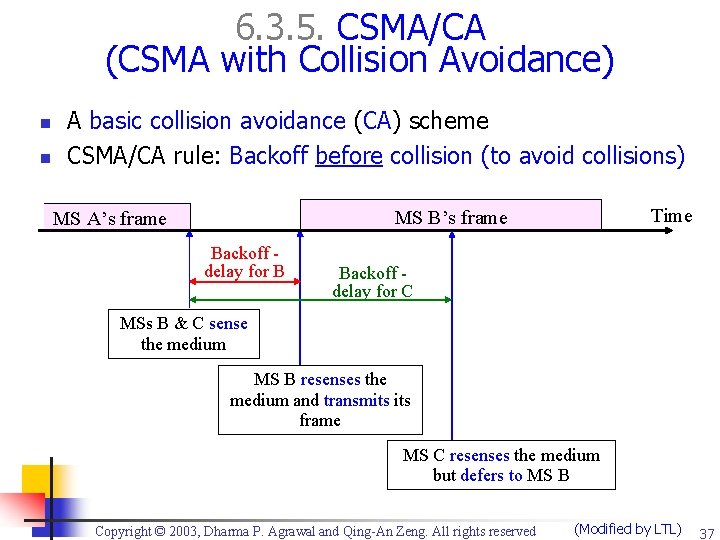
6. 3. 5. CSMA/CA (CSMA with Collision Avoidance) n n A basic collision avoidance (CA) scheme CSMA/CA rule: Backoff before collision (to avoid collisions) Time MS B’s frame MS A’s frame Backoff delay for B Backoff delay for C MSs B & C sense the medium MS B resenses the medium and transmits frame MS C resenses the medium but defers to MS B Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 37

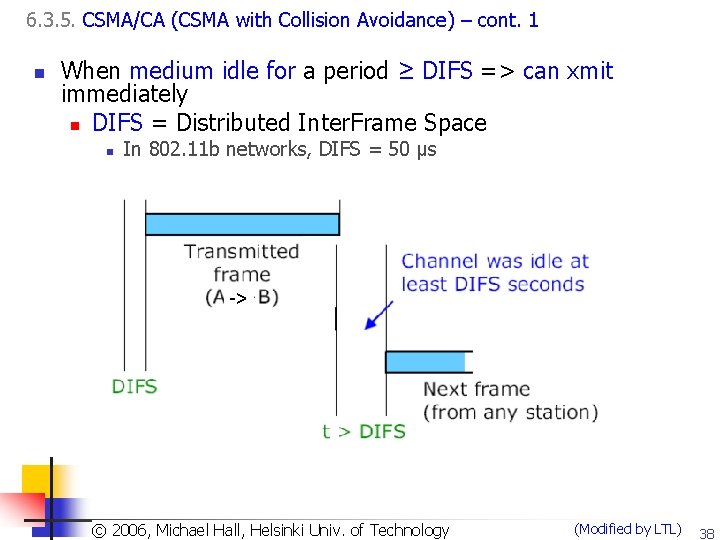
6. 3. 5. CSMA/CA (CSMA with Collision Avoidance) – cont. 1 n When medium idle for a period ≥ DIFS => can xmit immediately n DIFS = Distributed Inter. Frame Space n In 802. 11 b networks, DIFS = 50 μs -> DIFS Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology (Modified by LTL) 38

Types of CSMA/CA n Types of CSMA/CA 1) Basic CSMA/CA 2) CSMA/CA with ACK 3) CSMA/CA with RTS and CTS . . . discussed in turn. . . Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 39

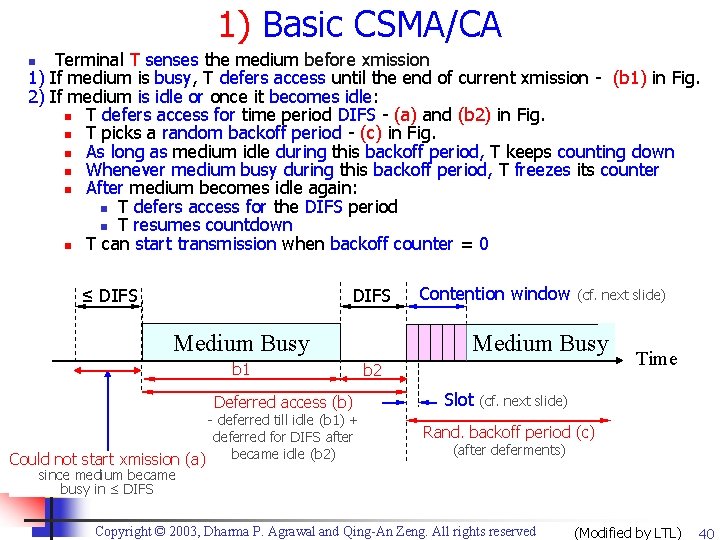
1) Basic CSMA/CA Terminal T senses the medium before xmission 1) If medium is busy, T defers access until the end of current xmission - (b 1) in Fig. 2) If medium is idle or once it becomes idle: n T defers access for time period DIFS - (a) and (b 2) in Fig. n T picks a random backoff period - (c) in Fig. n As long as medium idle during this backoff period, T keeps counting down n Whenever medium busy during this backoff period, T freezes its counter n After medium becomes idle again: n T defers access for the DIFS period n T resumes countdown n T can start transmission when backoff counter = 0 n DIFS ≤ DIFS Medium Busy b 1 Deferred access (b) - deferred till idle (b 1) + deferred for DIFS after became idle (b 2) Could not start xmission (a) since medium became busy in ≤ DIFS Contention window (cf. next slide) Medium Busy b 2 Slot Time (cf. next slide) Rand. backoff period (c) (after deferments) Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 40

1) Basic CSMA/CA – cont. 1 All except red text repeated (in larger font) Terminal T senses the medium before xmission 1) If medium is busy, T defers access until the end of current xmission 2) If medium is idle or once it becomes idle: n T defers access for time period DIFS n T picks a random backoff period n n n As long as medium idle during this backoff period, T keeps counting down = decreases its backoff counter n n n I. e. , count down as long as medium idle, stop countdown when medium busy again Whenever medium busy during this backoff period, T freezes its counter After medium becomes idle again: n n n Backoff counter - initialized with the value of backoff period T defers access for the DIFS period T resumes countdown T can start transmission when backoff counter = 0 Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 41

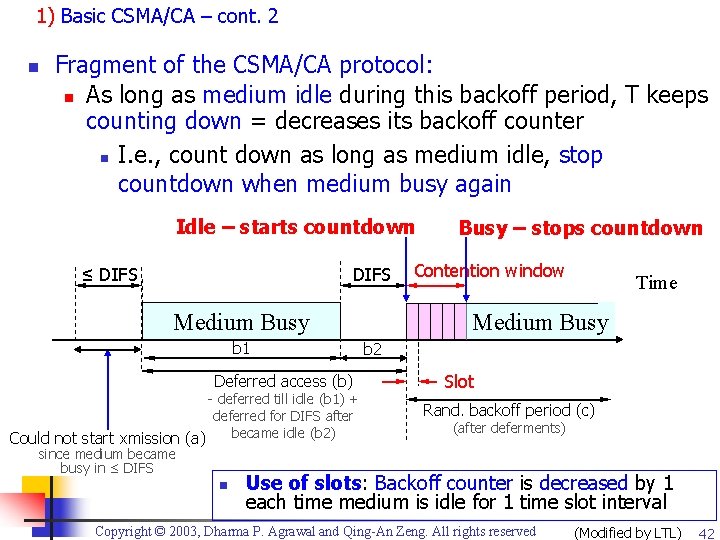
1) Basic CSMA/CA – cont. 2 n Fragment of the CSMA/CA protocol: n As long as medium idle during this backoff period, T keeps counting down = decreases its backoff counter n I. e. , count down as long as medium idle, stop countdown when medium busy again Idle – starts countdown DIFS ≤ DIFS Deferred access (b) - deferred till idle (b 1) + deferred for DIFS after became idle (b 2) Could not start xmission (a) since medium became busy in ≤ DIFS n Contention window Time Medium Busy b 1 Busy – stops countdown b 2 Slot Rand. backoff period (c) (after deferments) Use of slots: Backoff counter is decreased by 1 each time medium is idle for 1 time slot interval Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 42

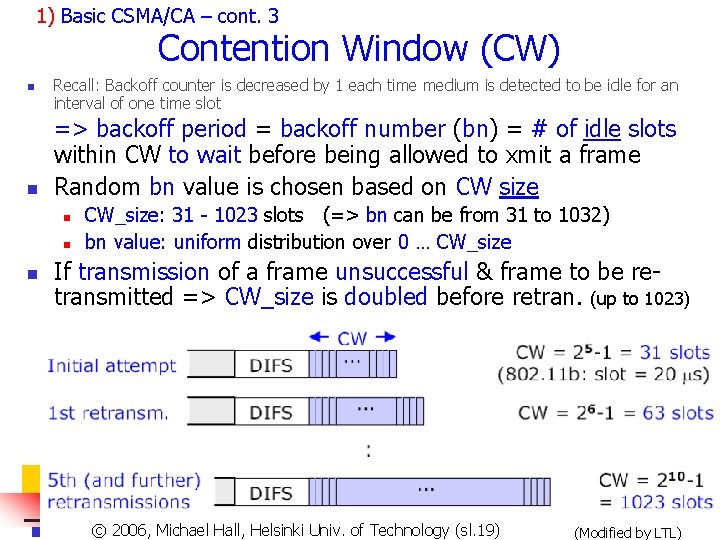
1) Basic CSMA/CA – cont. 3 Contention Window (CW) n n Recall: Backoff counter is decreased by 1 each time medium is detected to be idle for an interval of one time slot => backoff period = backoff number (bn) = # of idle slots within CW to wait before being allowed to xmit a frame Random bn value is chosen based on CW size n n n CW_size: 31 - 1023 slots (=> bn can be from 31 to 1032) bn value: uniform distribution over 0 … CW_size If transmission of a frame unsuccessful & frame to be retransmitted => CW_size is doubled before retran. (up to 1023) Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 19) © 2007 by© Leszek T. Hall, Lilien. Helsinki (Modified by LTL) 43

1) Basic CSMA/CA – cont. 4 Selection of Random Backoff Value n n Recall: If transmission of a frame unsuccessful & frame allowed to be retransmitted => => before each retransm. CW_size is doubled (up to 1023) => Pr{ bn value is larger } is higher Since it is unlikely that several stations will choose the same value of bn, collisions are avoided Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 20) © 2007 by© Leszek T. Hall, Lilien. Helsinki (Modified by LTL) 44

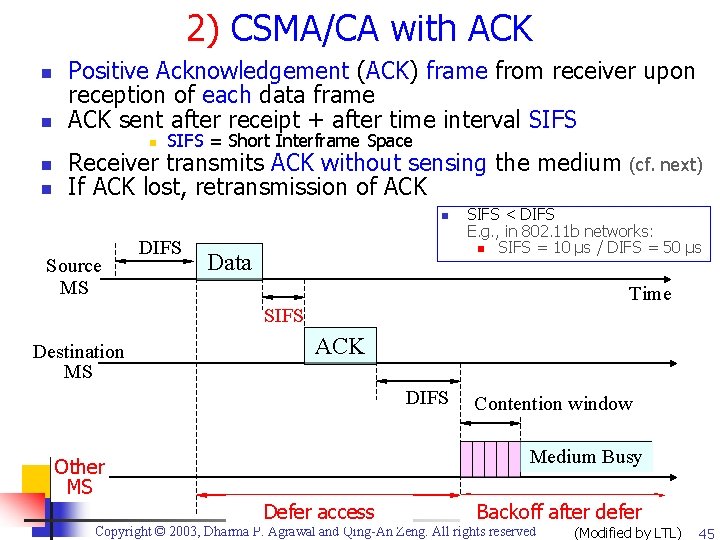
2) CSMA/CA with ACK n n Positive Acknowledgement (ACK) frame from receiver upon reception of each data frame ACK sent after receipt + after time interval SIFS n n n SIFS = Short Interframe Space Receiver transmits ACK without sensing the medium If ACK lost, retransmission of ACK n Source MS DIFS Data SIFS < DIFS E. g. , in 802. 11 b networks: n SIFS = 10 μs / DIFS = 50 μs Time SIFS Destination MS (cf. next) ACK DIFS Contention window Medium Busy Other MS Defer access Backoff after defer Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved (Modified by LTL) 45

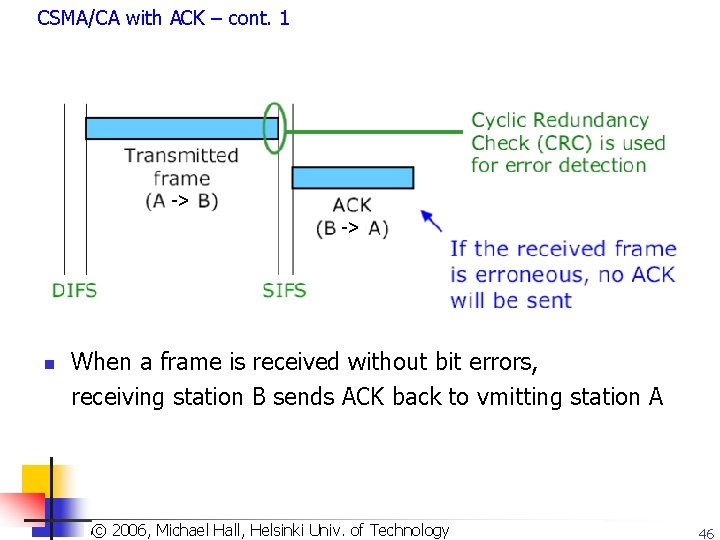
CSMA/CA with ACK – cont. 1 -> -> n When a frame is received without bit errors, receiving station B sends ACK back to vmitting station A Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology © 2007 by© Leszek T. Hall, Lilien. Helsinki 46

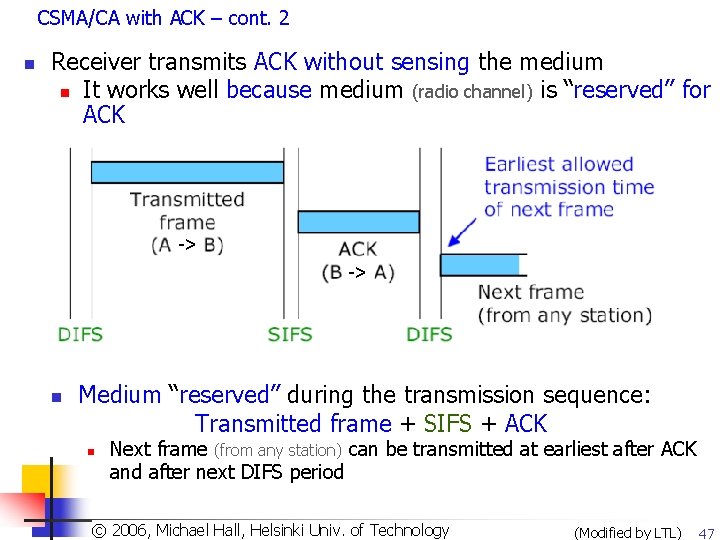
CSMA/CA with ACK – cont. 2 n Receiver transmits ACK without sensing the medium n It works well because medium (radio channel) is “reserved” for ACK -> -> n Medium “reserved” during the transmission sequence: Transmitted frame + SIFS + ACK n Next frame (from any station) can be transmitted at earliest after ACK and after next DIFS period Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology (Modified by LTL) 47

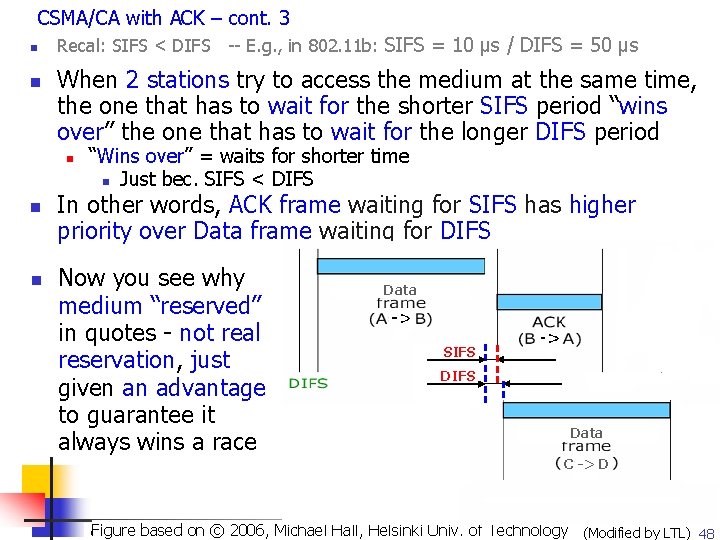
CSMA/CA with ACK – cont. 3 n n Recal: SIFS < DIFS -- E. g. , in 802. 11 b: SIFS = 10 μs / DIFS = 50 μs When 2 stations try to access the medium at the same time, the one that has to wait for the shorter SIFS period “wins over” the one that has to wait for the longer DIFS period n n n “Wins over” = waits for shorter time n Just bec. SIFS < DIFS In other words, ACK frame waiting for SIFS has higher priority over Data frame waiting for DIFS Now you see why medium “reserved” in quotes - not real reservation, just given an advantage to guarantee it always wins a race Data SIFS Data C -> D Copyright 2003, P. Agrawal and Qing-An Zeng. Univ. All rights reserved Figure on. Dharma ©Lilien 2006, Michael Hall, Helsinki of Technology © 2007 based by©Leszek T. (Modified by LTL) 48

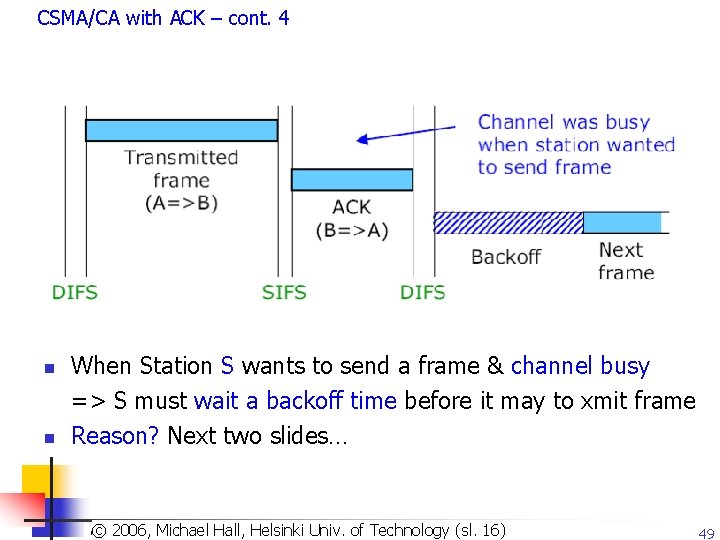
CSMA/CA with ACK – cont. 4 n n When Station S wants to send a frame & channel busy => S must wait a backoff time before it may to xmit frame Reason? Next two slides… Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 16) © 2007 by© Leszek T. Hall, Lilien. Helsinki 49

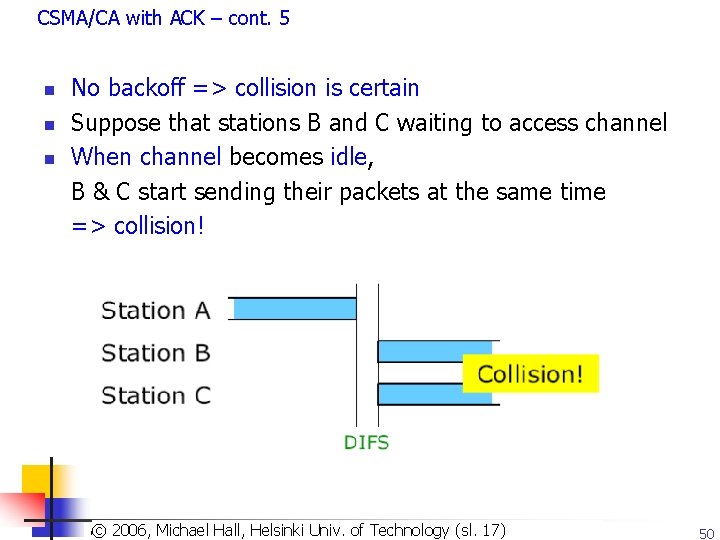
CSMA/CA with ACK – cont. 5 n n n No backoff => collision is certain Suppose that stations B and C waiting to access channel When channel becomes idle, B & C start sending their packets at the same time => collision! Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 17) © 2007 by© Leszek T. Hall, Lilien. Helsinki 50

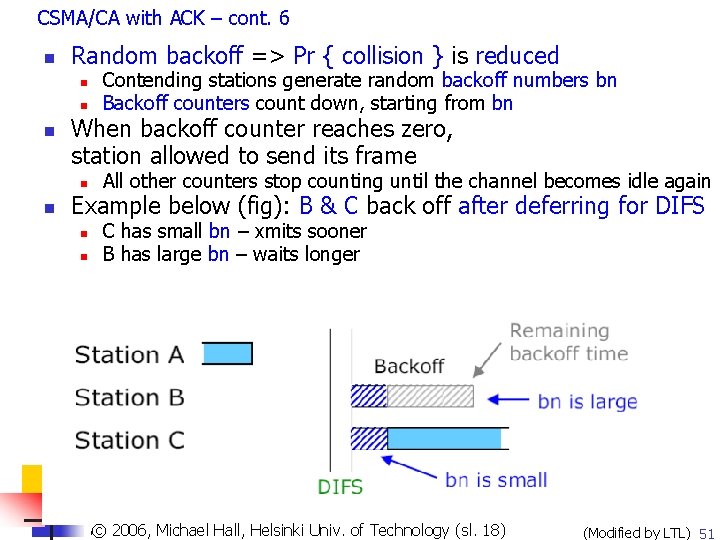
CSMA/CA with ACK – cont. 6 n Random backoff => Pr { collision } is reduced n n n When backoff counter reaches zero, station allowed to send its frame n n Contending stations generate random backoff numbers bn Backoff counters count down, starting from bn All other counters stop counting until the channel becomes idle again Example below (fig): B & C back off after deferring for DIFS n n C has small bn – xmits sooner B has large bn – waits longer Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 18) © 2007 by© Leszek T. Hall, Lilien. Helsinki (Modified by LTL) 51

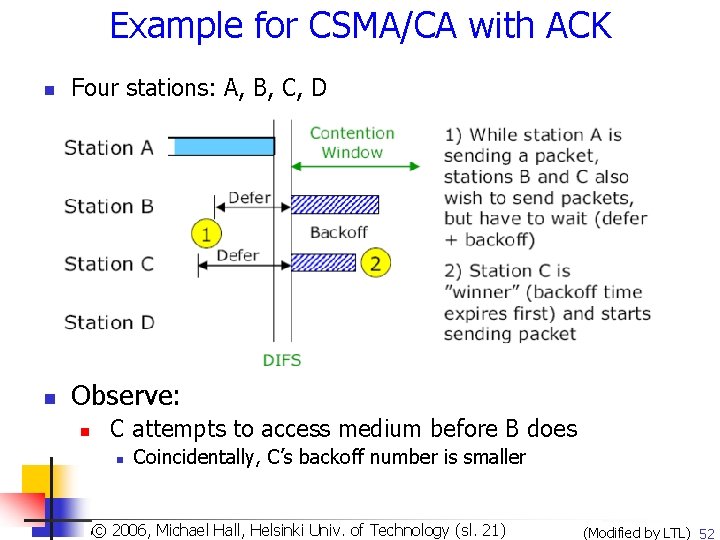
Example for CSMA/CA with ACK n Four stations: A, B, C, D n Observe: n C attempts to access medium before B does n Coincidentally, C’s backoff number is smaller Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, Michael of Technology (sl. 21) © 2007 by© Leszek T. Hall, Lilien. Helsinki (Modified by LTL) 52

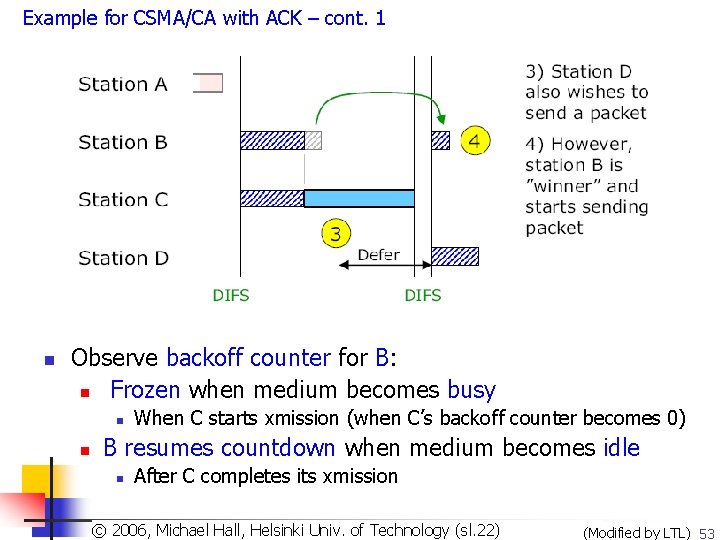
Example for CSMA/CA with ACK – cont. 1 n Observe backoff counter for B: n Frozen when medium becomes busy n n When C starts xmission (when C’s backoff counter becomes 0) B resumes countdown when medium becomes idle n After C completes its xmission Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology (sl. 22) (Modified by LTL) 53

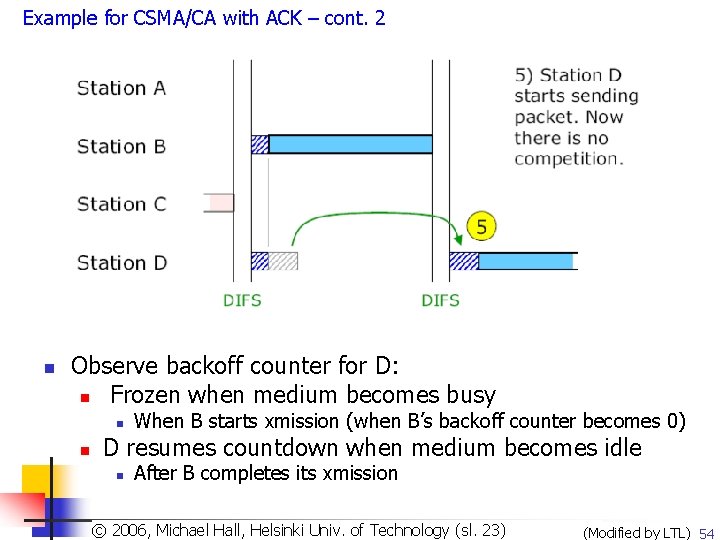
Example for CSMA/CA with ACK – cont. 2 n Observe backoff counter for D: n Frozen when medium becomes busy n n When B starts xmission (when B’s backoff counter becomes 0) D resumes countdown when medium becomes idle n After B completes its xmission Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology (sl. 23) (Modified by LTL) 54

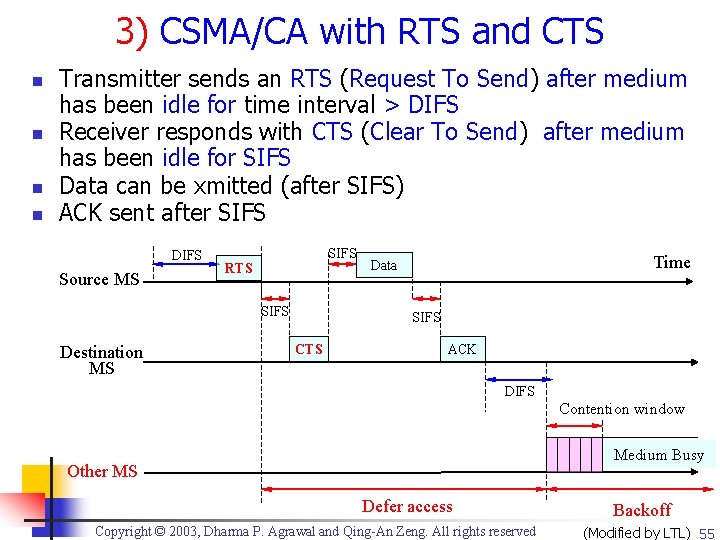
3) CSMA/CA with RTS and CTS n n Transmitter sends an RTS (Request To Send) after medium has been idle for time interval > DIFS Receiver responds with CTS (Clear To Send) after medium has been idle for SIFS Data can be xmitted (after SIFS) ACK sent after SIFS DIFS Source MS SIFS RTS SIFS Destination MS Time Data SIFS CTS ACK DIFS Contention window Medium Busy Other MS Defer access Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved Backoff (Modified by LTL) 55

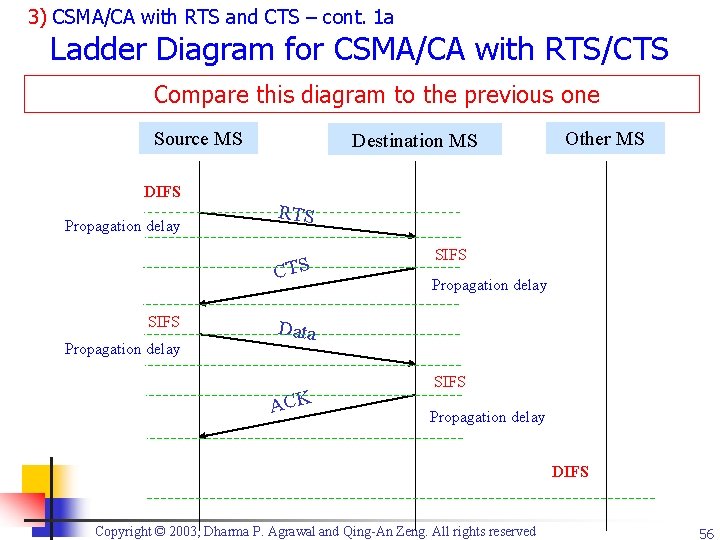
3) CSMA/CA with RTS and CTS – cont. 1 a Ladder Diagram for CSMA/CA with RTS/CTS Compare this diagram to the previous one Source MS DIFS Propagation delay Destination MS RTS CTS SIFS Propagation delay Other MS SIFS Propagation delay Data ACK SIFS Propagation delay DIFS Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 56

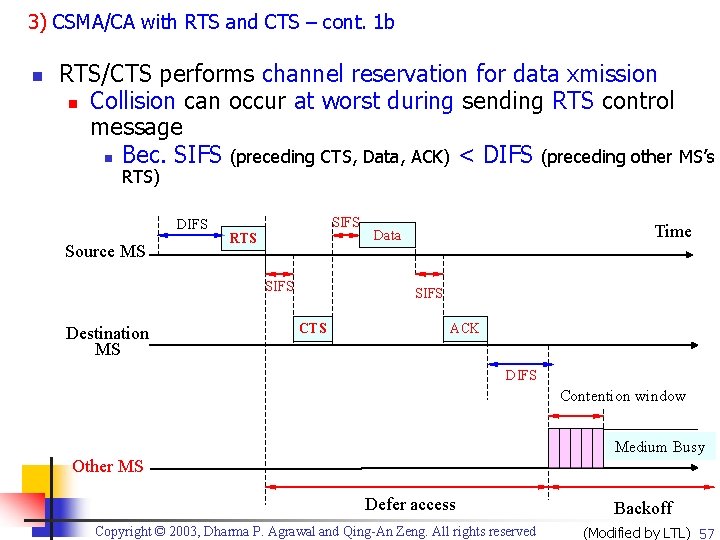
3) CSMA/CA with RTS and CTS – cont. 1 b n RTS/CTS performs channel reservation for data xmission n Collision can occur at worst during sending RTS control message n Bec. SIFS (preceding CTS, Data, ACK) < DIFS (preceding other MS’s RTS) DIFS Source MS SIFS RTS SIFS Destination MS Time Data SIFS CTS ACK DIFS Contention window Medium Busy Other MS Defer access Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved Backoff (Modified by LTL) 57

3) CSMA/CA with RTS/CTS – cont. 1 c n n n RTS = Request To Send / CTS = Clear To Send RTS/CTS scheme - used as a countermeasure against the “hidden node” problem Hidden node problem n WS 1 & WS 2 can hear AP but not each other n => If WS 1 sends a packet, WS 2 does notice this (and vice versa) => collision! Copyright 2003, Dharma P. Agrawal. Univ. and Qing-An Zeng. All rights reserved © 2006, © Michael Hall, Helsinki of Technology (sl. 25) 58

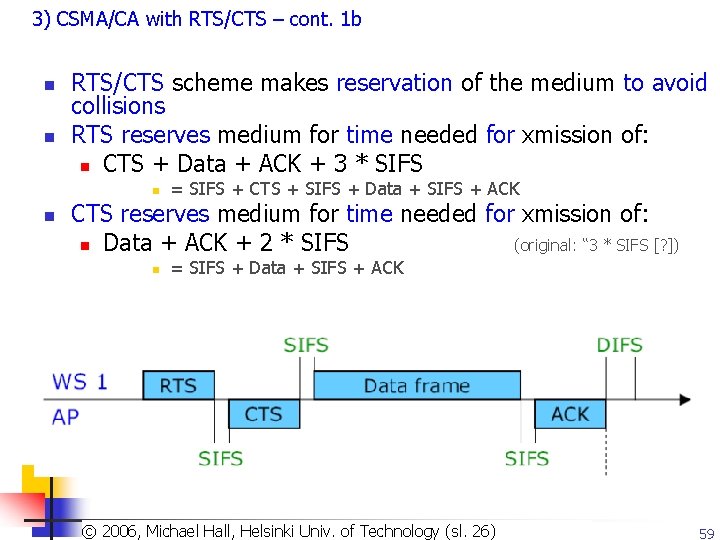
3) CSMA/CA with RTS/CTS – cont. 1 b n n RTS/CTS scheme makes reservation of the medium to avoid collisions RTS reserves medium for time needed for xmission of: n CTS + Data + ACK + 3 * SIFS n n = SIFS + CTS + SIFS + Data + SIFS + ACK CTS reserves medium for time needed for xmission of: n Data + ACK + 2 * SIFS (original: “ 3 * SIFS [? ]) n = SIFS + Data + SIFS + ACK © 2003, Dharma P. Agrawal and of Qing-An Zeng. All(sl. rights ©Copyright 2006, Michael Hall, Helsinki Univ. Technology 26)reserved 59

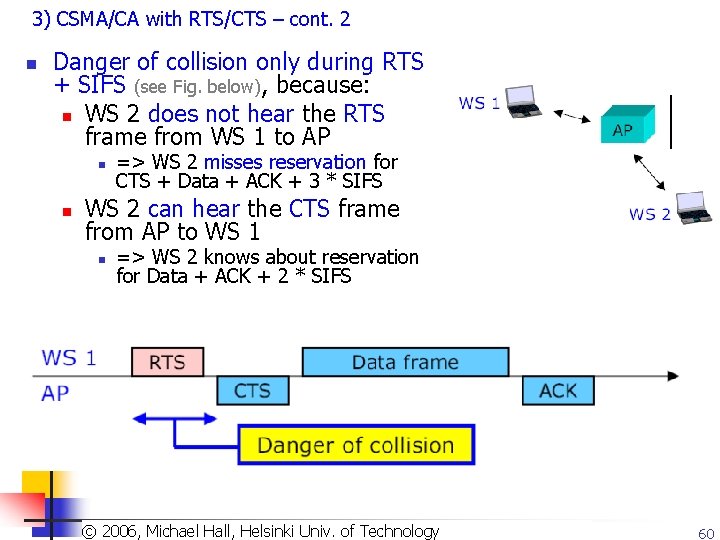
3) CSMA/CA with RTS/CTS – cont. 2 n Danger of collision only during RTS + SIFS (see Fig. below), because: n WS 2 does not hear the RTS frame from WS 1 to AP n n => WS 2 misses reservation for CTS + Data + ACK + 3 * SIFS WS 2 can hear the CTS frame from AP to WS 1 n => WS 2 knows about reservation for Data + ACK + 2 * SIFS © 2003, Dharma P. Agrawal and of Qing-An Zeng. All rights reserved ©Copyright 2006, Michael Hall, Helsinki Univ. Technology 60

Advantages of RTS & CTS n Advantage #1 of RTS/CTS: Reduces collision probability if the data frame is very long compared to the RTS frame n Does not prevent collisions during very short RTS frames n Not a big problem - they are not very likely n Prevents more likely collisions during long data frame © 2003, Dharma P. Agrawal and of Qing-An Zeng. All(sl. rights ©Copyright 2006, Michael Hall, Helsinki Univ. Technology 28)reserved 61

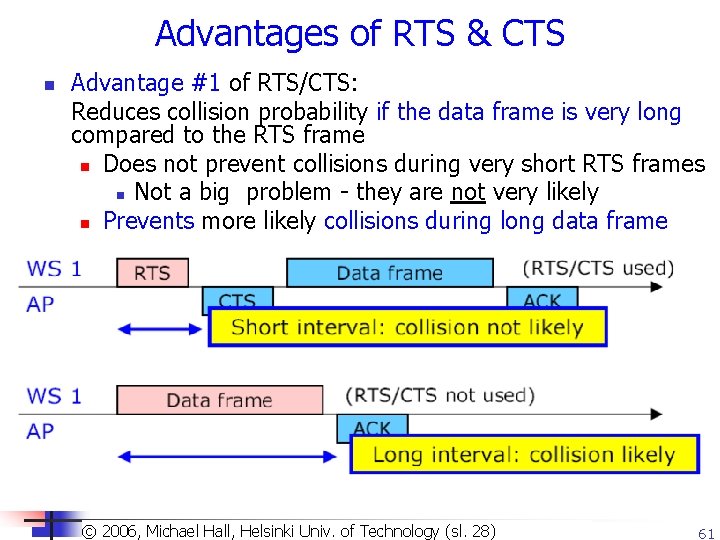
Advantage of RTS & CTS – cont. n Advantage #2 of RTS/CTS Avoids having long intervals with high collision danger n Good! Long interval w/ high collision danger should be avoided n n (same Fig) Should be for the following reasons: n Larger probability of collision n Greater waste of capacity if a collision occurs and the frame has to be retransmitted Frames shorter than a certain threshold value can be transmitted without using RTS/CTS n Because small waste of medium if collision occurs for short frames n Threshold parameter => low risk (dot 11 RTSThreshold) set in a xmitting station © 2003, Dharma P. Agrawal and of Qing-An Zeng. All(sl. rights ©Copyright 2006, Michael Hall, Helsinki Univ. Technology 29)reserved 62

Summary: Full Taxonomy of CSMA (Carrier Sense Multiple Access) Protocols 1) (Basic) CSMA 1 a) Nonpersistent CSMA – Slotted – Unslotted 1 b) Persistent CSMA Subcategories # 1 of Persistent CSMA: – Slotted – Unslotted Subcategories # 2 (orthogonal) of Persistent CSMA: – 1 -persistent CSMA – p-persistent CSMA 2) CSMA/CD (CSMA with Collision Detection) 3) CSMA/CA (CSMA with Collision Avoidance) 3 a) Basic CSMA/CA 3 b) CSMA/CA with ACK 3 c) CSMA/CA with RTS/CTS Copyright 2003, Dharma © 2007 by©Leszek T. Lilien. P. Agrawal and Qing-An Zeng. All rights reserved 63

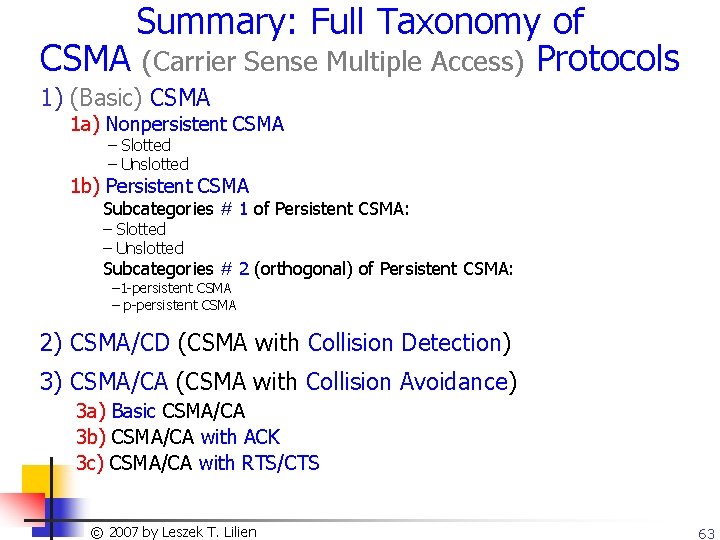
The End of Section 6 Copyright © 2003, Dharma P. Agrawal and Qing-An Zeng. All rights reserved 64