CS 6393 and CS 4483 Cyber Security Foundations

CS 6393 and CS 4483 Cyber Security Foundations and Practice Module 2. 1 Crypto Essentials Ravi Sandhu Spring 2021 © Ravi Sandhu World-Leading Research with Real-World Impact! 1
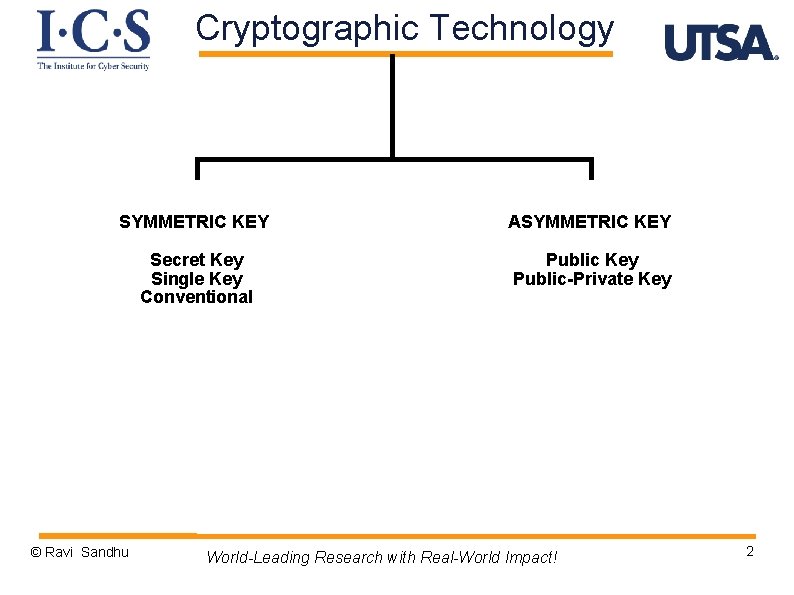
Cryptographic Technology SYMMETRIC KEY ASYMMETRIC KEY Secret Key Single Key Conventional Public Key Public-Private Key © Ravi Sandhu World-Leading Research with Real-World Impact! 2
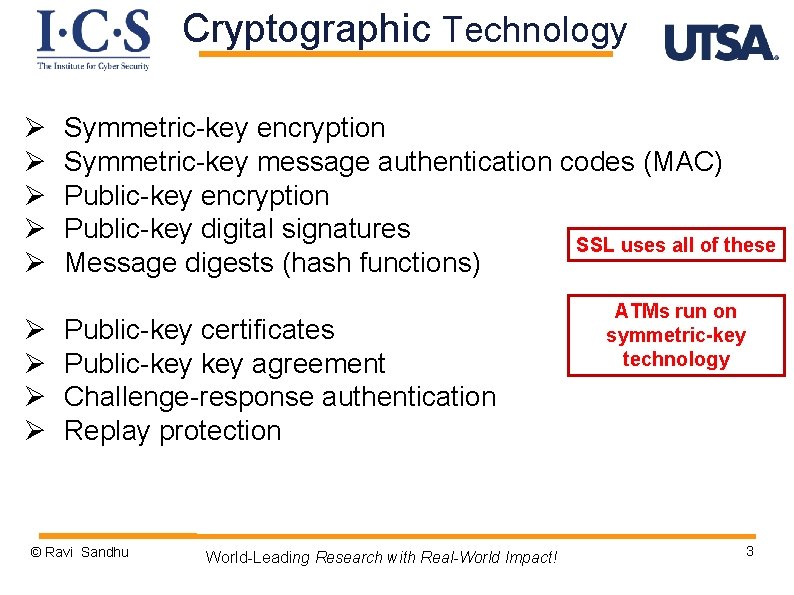
Cryptographic Technology Ø Ø Ø Ø Ø Symmetric-key encryption Symmetric-key message authentication codes (MAC) Public-key encryption Public-key digital signatures SSL uses all of these Message digests (hash functions) Public-key certificates Public-key agreement Challenge-response authentication Replay protection © Ravi Sandhu World-Leading Research with Real-World Impact! ATMs run on symmetric-key technology 3

Cryptographic Services Ø confidentiality v crypto keys leak profusely via side channels Ø integrity + authentication v no point having one without the other Ø non-repudiation v requires asymmetric cryptography v stronger form of integrity + authentication © Ravi Sandhu World-Leading Research with Real-World Impact! 4
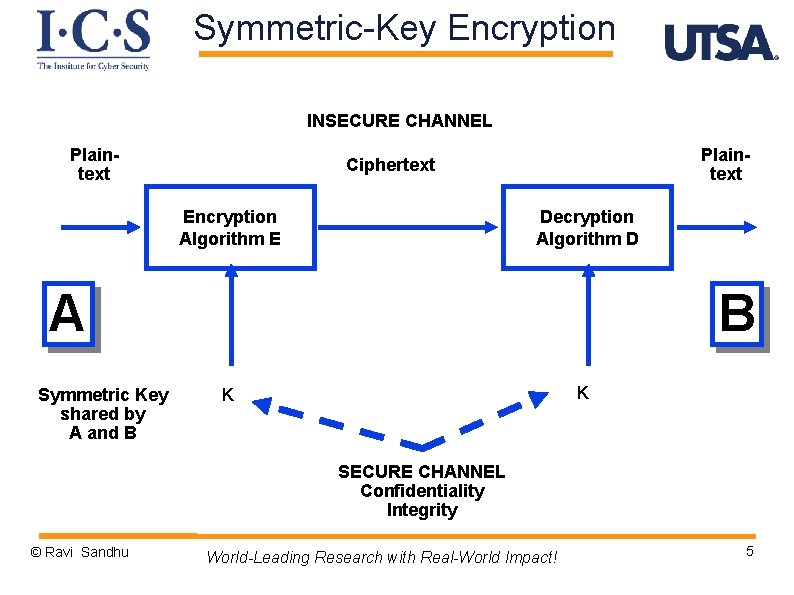
Symmetric-Key Encryption INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Symmetric Key shared by A and B B K K SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 5
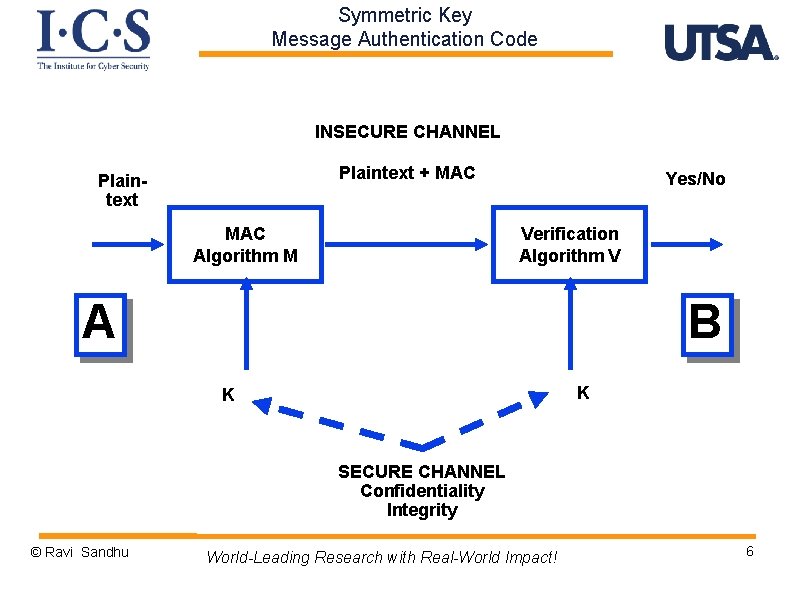
Symmetric Key Message Authentication Code INSECURE CHANNEL Plaintext + MAC Plaintext MAC Algorithm M Yes/No Verification Algorithm V A B K K SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 6
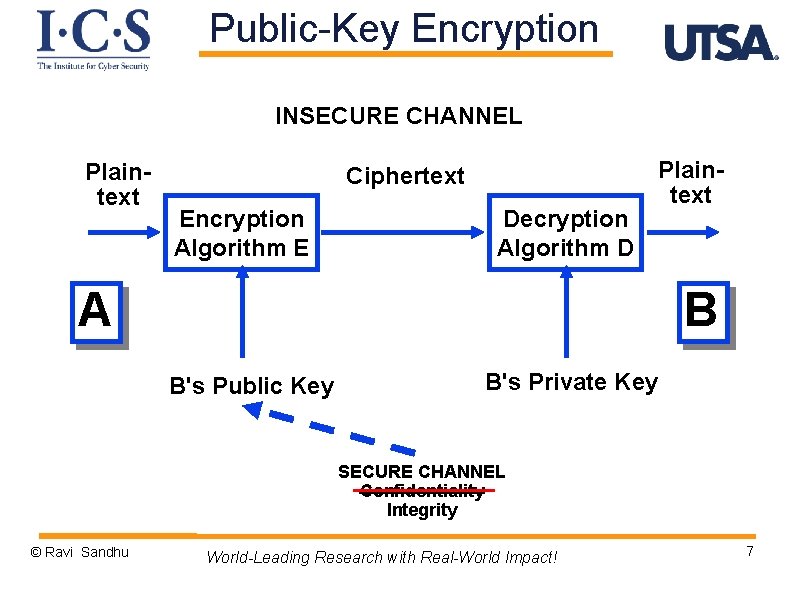
Public-Key Encryption INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Plaintext B B's Public Key B's Private Key SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 7
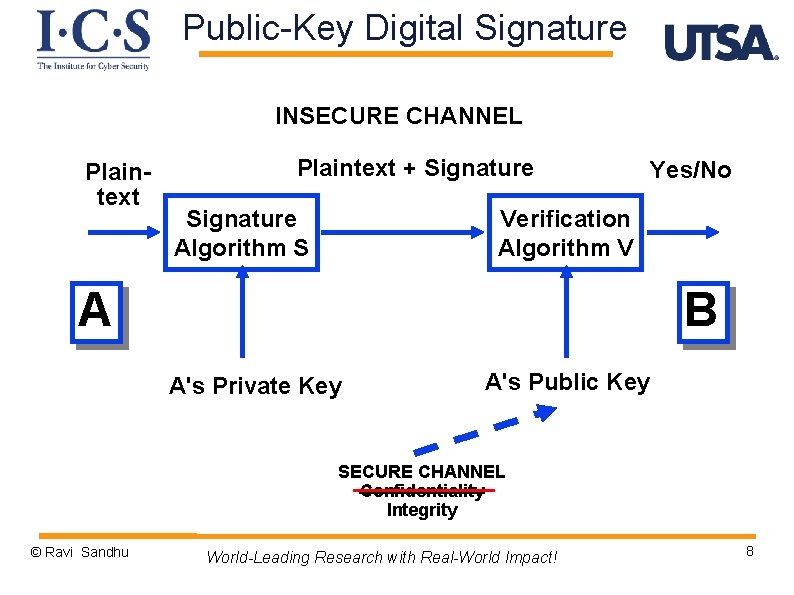
Public-Key Digital Signature INSECURE CHANNEL Plaintext + Signature Algorithm S Yes/No Verification Algorithm V A B A's Private Key A's Public Key SECURE CHANNEL Confidentiality Integrity © Ravi Sandhu World-Leading Research with Real-World Impact! 8
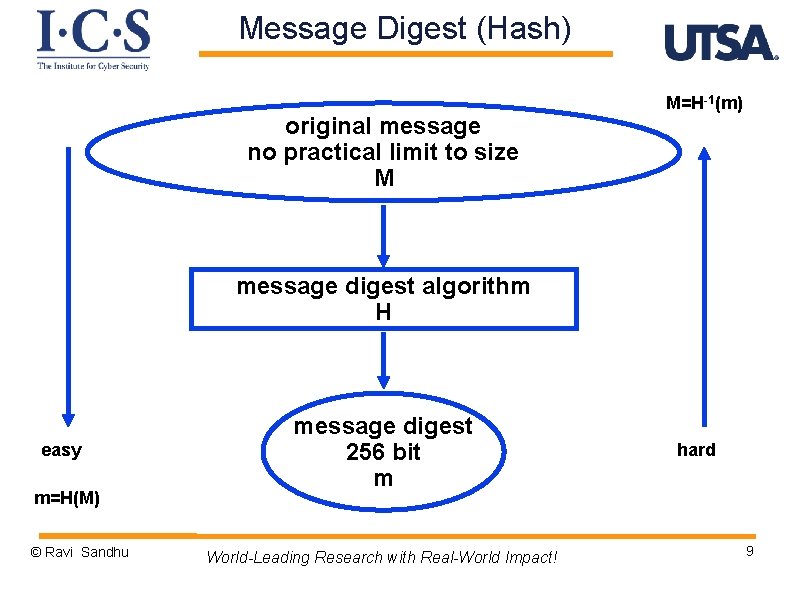
Message Digest (Hash) original message no practical limit to size M M=H-1(m) message digest algorithm H easy m=H(M) © Ravi Sandhu message digest 256 bit m World-Leading Research with Real-World Impact! hard 9
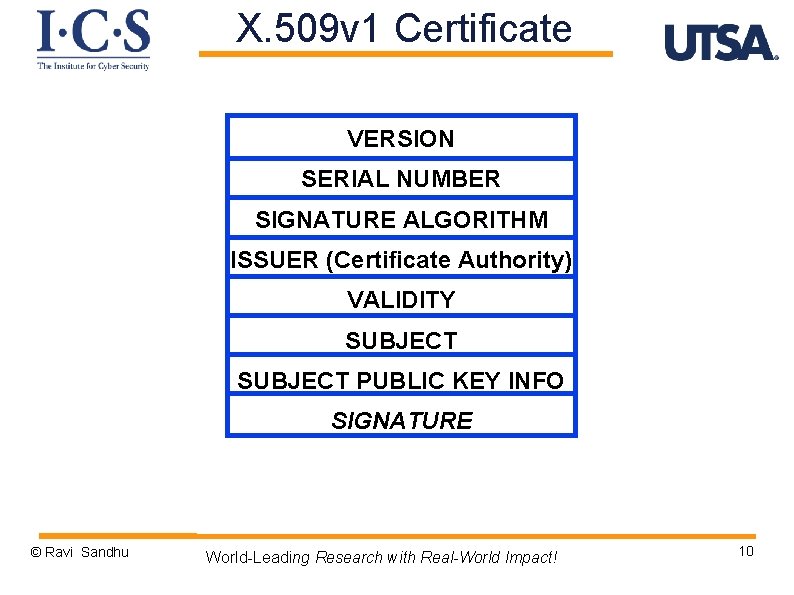
X. 509 v 1 Certificate VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER (Certificate Authority) VALIDITY SUBJECT PUBLIC KEY INFO SIGNATURE © Ravi Sandhu World-Leading Research with Real-World Impact! 10
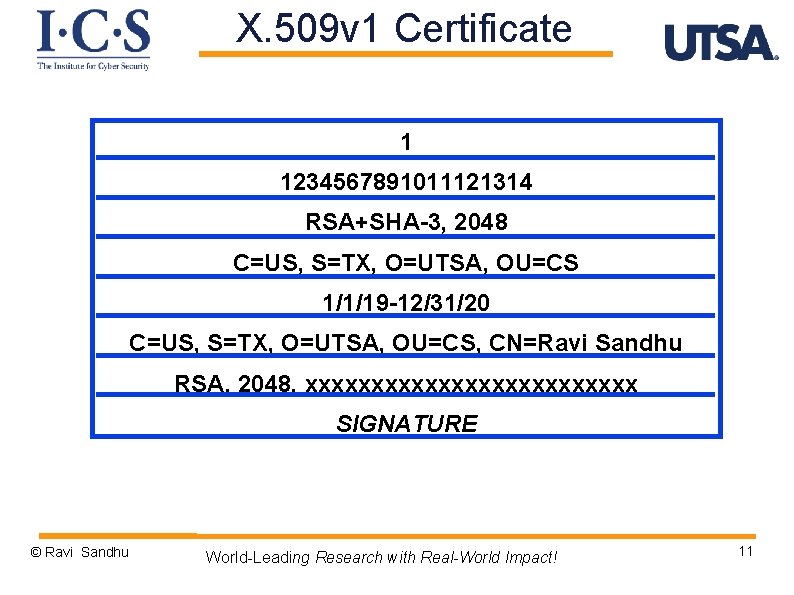
X. 509 v 1 Certificate 1 1234567891011121314 RSA+SHA-3, 2048 C=US, S=TX, O=UTSA, OU=CS 1/1/19 -12/31/20 C=US, S=TX, O=UTSA, OU=CS, CN=Ravi Sandhu RSA, 2048, xxxxxxxxxxxxx SIGNATURE © Ravi Sandhu World-Leading Research with Real-World Impact! 11
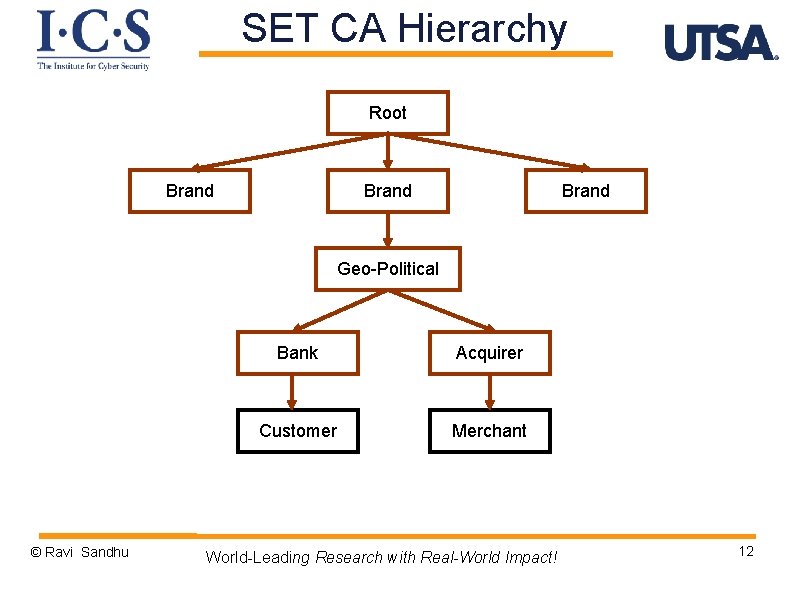
SET CA Hierarchy Root Brand Geo-Political © Ravi Sandhu Bank Acquirer Customer Merchant World-Leading Research with Real-World Impact! 12

Multiple Trusted Roots © Ravi Sandhu World-Leading Research with Real-World Impact! 13
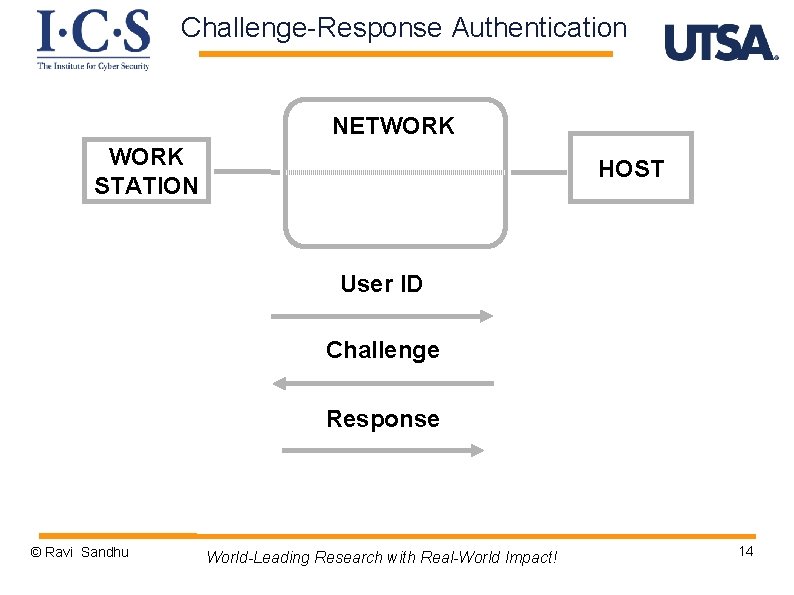
Challenge-Response Authentication NETWORK STATION HOST User ID Challenge Response © Ravi Sandhu World-Leading Research with Real-World Impact! 14
- Slides: 14