CS 59506030 Computer Security and Information Assurance Section
















![Note: Row Row. . . Row Vigenere Tableaux (1) [cf. J. Leiwo, VU, NL] Note: Row Row. . . Row Vigenere Tableaux (1) [cf. J. Leiwo, VU, NL]](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-35.jpg)




















![Overview of DES (2) Basic Structure n n [Fig. – cf. J. Leiwo] Input: Overview of DES (2) Basic Structure n n [Fig. – cf. J. Leiwo] Input:](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-82.jpg)










![2 F. 4. Comparison of DES & AES (1) Date Block size [bits] Key 2 F. 4. Comparison of DES & AES (1) Date Block size [bits] Key](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-98.jpg)


- Slides: 101

CS 5950/6030 – Computer Security and Information Assurance Section 2: Introduction to Cryptology (Part 1) Dr. Leszek Lilien Department of Computer Science Western Michigan University Slides based on Security in Computing. Third Edition by Pfleeger and Pfleeger. Using some slides courtesy of: Prof. Aaron Striegel — course taught at U. of Notre Dame Prof. Barbara Endicott-Popovsky and Prof. Deborah Frincke (U. Idaho) — taught at U. Washington Prof. Jussipekka Leiwo — taught at Vrije Universiteit (Free U. ), Amsterdam, The Netherlands Slides not created by the above authors are © 2006 by Leszek T. Lilien Requests to use original slides for non-profit purposes will be gladly granted upon a written request.

Students’ Background Survey CS 5950/6030 - Spring 2006 – L. Lilien Computer Security and Information Assurance Please print all your answers. First name: _____________ Last name: _______________ Email ___________________________________ Undergrad. /Year ____ OR: Grad. /Year or Status (e. g. , Ph. D. student) ________ Major ___________________________________ PART 1. Background and Experience 1 -1)Please rate your knowledge in the following areas (0 = None, 5 = Excellent). UNIX/Linux/Solaris/etc. Experience (use, administration, etc. ) 0 1 2 3 Network Protocols (TCP, UDP, IP, etc. ) 0 1 2 3 Cryptography (basic ciphers, DES, RSA, PGP, etc. ) 0 1 2 3 Computer Security (access control, security fundamentals, etc. ) 0 1 2 3 4 5 4 5 Any new students who did not fill out the survey? Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 2

Introduction to Cryptology – Outline (1) 2 A. Terminology and Background 2 A. 1. Threats to Messages 2 A. 2. Basic Terminology and Notation 2 A. 3. Requirements for Crypto Protocols 2 A. 4. Representing Characters 2 B. Basic Types of Ciphers 2 B. 1. Substitution Ciphers a. The Ceasar Cipher b. Other Substitution Ciphers c. One-Time Pads 2 B. 2. Transposition Ciphers 2 B. 3. Product Ciphers Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 3

Introduction to Cryptology – Outline (2) 2 C. Making „Good” Ciphers 2 C. 1. Criteria for „Good” Ciphers 2 C. 2. Stream and Block Ciphers 2 C. 3. Cryptanalysis 2 C. 4. Symmetric and Asymm. Cryptosystems 2 D. The DES (Data Encryption Standard) Algorithm 2 D. 1. Background and History of DES 2 D. 2. Overview of DES 2 D. 3. Double and Triple DES 2 D. 4. Security of DES Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 4

Introduction to Cryptology – Outline (3) 2 E. The Clipper Story 2 F. AES (Advanced Encryption Standard) 2 F. 1. The AES Contest 2 F. 2. Overview of Rijndael 2 F. 3. Strength of AES 2 F. 4. Comparison of DES and AES . . . More in Part 2 of Section 2. . . Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 5

2 A. Terminology and Background 2 A. 1. Threats to Messages n n Interception Interruption n Blocking msgs Modification Fabrication “A threat is blocked by control of a vulnerability” [Pfleeger & Pfleeger] [cf. B. Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 6

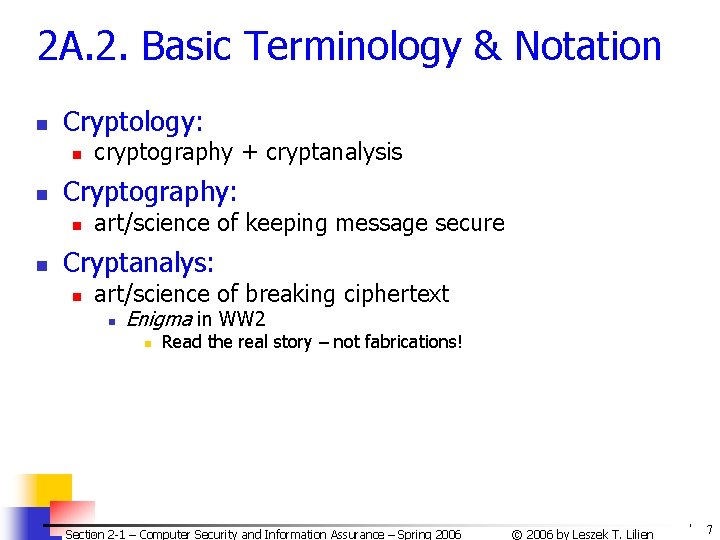
2 A. 2. Basic Terminology & Notation n Cryptology: n n Cryptography: n n cryptography + cryptanalysis art/science of keeping message secure Cryptanalys: n art/science of breaking ciphertext n Enigma in WW 2 n Read the real story – not fabrications! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 7

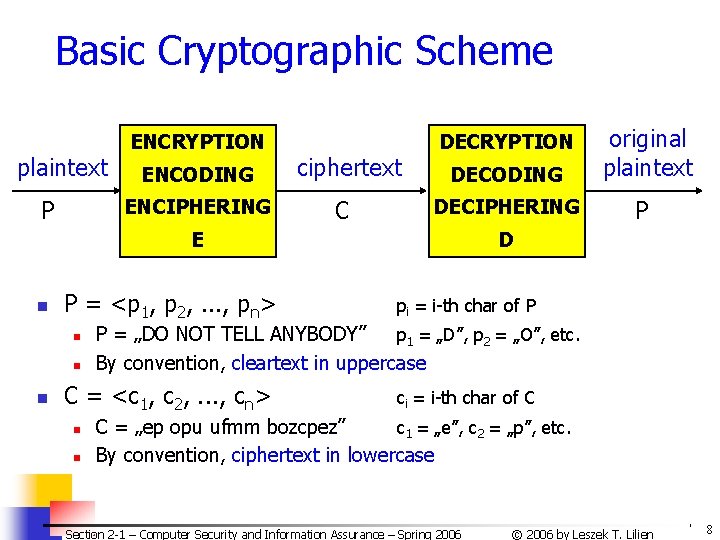
Basic Cryptographic Scheme plaintext ENCRYPTION ENCODING ENCIPHERING P ciphertext C DECODING original plaintext DECIPHERING P DECRYPTION E n P = <p 1, p 2, . . . , pn> n n pi = i-th char of P P = „DO NOT TELL ANYBODY” p 1 = „D”, p 2 = „O”, etc. By convention, cleartext in uppercase C = <c 1, c 2, . . . , cn> n D ci = i-th char of C C = „ep opu ufmm bozcpez” c 1 = „e”, c 2 = „p”, etc. By convention, ciphertext in lowercase Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 8

Benefits of Cryptography n Improvement not a Solution! n n Minimizes problems Doesn’t solve them n n Remember: There is no solution! Adds an envelope (encoding) to an open postcard (cleartext) [cf. D. Frincke, U. of Idaho] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 9

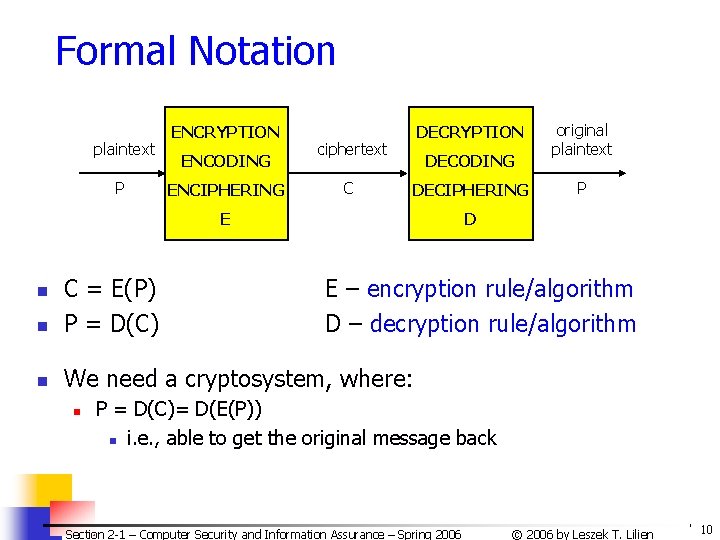
Formal Notation plaintext P ENCRYPTION ENCODING ENCIPHERING DECRYPTION ciphertext C DECODING DECIPHERING E n n We need a cryptosystem, where: n P D C = E(P) P = D(C) n original plaintext E – encryption rule/algorithm D – decryption rule/algorithm P = D(C)= D(E(P)) n i. e. , able to get the original message back Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 10

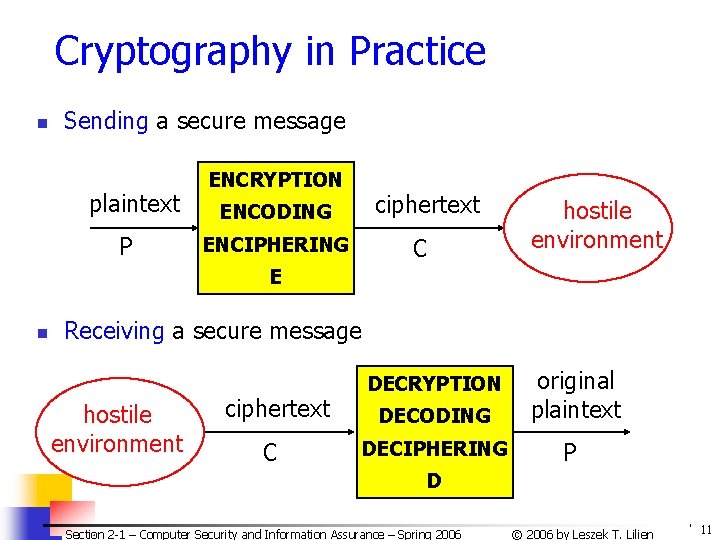
Cryptography in Practice n Sending a secure message plaintext P ENCRYPTION ENCODING ENCIPHERING ciphertext C hostile environment E n Receiving a secure message hostile environment ciphertext C DECODING original plaintext DECIPHERING P DECRYPTION D Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 11

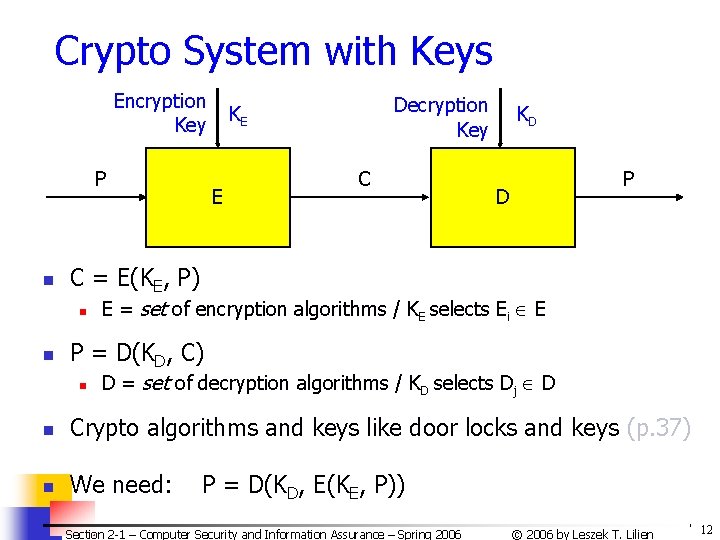
Crypto System with Keys Encryption Key P n E C KD P D C = E(KE, P) n n Decryption Key KE E = set of encryption algorithms / KE selects Ei E P = D(KD, C) n D = set of decryption algorithms / KD selects Dj D n Crypto algorithms and keys like door locks and keys (p. 37) n We need: P = D(KD, E(KE, P)) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 12

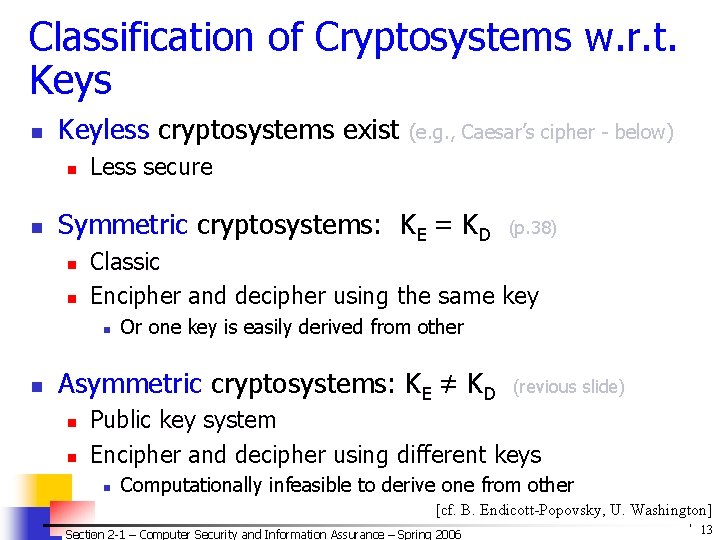
Classification of Cryptosystems w. r. t. Keys n Keyless cryptosystems exist n n Less secure Symmetric cryptosystems: KE = KD n n Or one key is easily derived from other Asymmetric cryptosystems: KE ≠ KD n n (p. 38) Classic Encipher and decipher using the same key n n (e. g. , Caesar’s cipher - below) (revious slide) Public key system Encipher and decipher using different keys n Computationally infeasible to derive one from other [cf. B. Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 13

Cryptanalysis (1) n Cryptanalysts goals: n n n Break a single msg Recognize patterns in encrypted msgs, to be able to break the subsequent ones Infer meaning w/o breaking encryption n n Unusual volume of msgs between enemy troops may indicate a coming attack Busiest node may be enemy headquarters Deduce the key, to facilitate breaking subsequent msgs Find vulnerabilities in implementation or environment of an encryption algorithm Find a general weakness in an encryption algorithm Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 14

Cryptanalysis (2) n Information for cryptanalysts: n n n Intercepted encrypted msgs Known encryption algorithms Intercepted plaintext Data known or suspected to be ciphertext Math or statistical tools and techniques Properties of natural languages n Esp. adversary’s natural language n n To confuse the enemy, Americans used Navajo language in WW 2 Propertiers of computer systems Role of ingenuity / luck There are no rules!!! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 15

Breakable Encryption (1) n Breakable encryption n n Theoretically, it is possible to devise unbreakable cryptosystems Based on Shannon’s theory of information Practical cryptosystems almost always are breakable, given adequate time and computing power The trick is to make breaking a cryptosystem hard enough for the intruder [cf. J. Leiwo, VU, NL] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 16

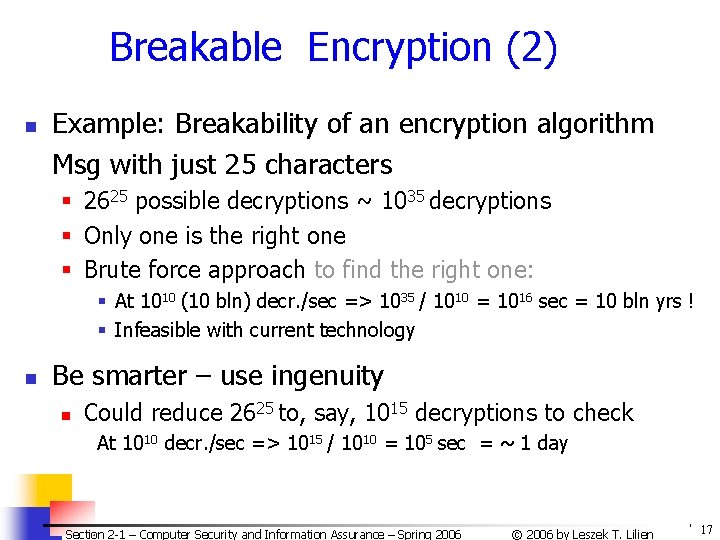
Breakable Encryption (2) n Example: Breakability of an encryption algorithm Msg with just 25 characters § 2625 possible decryptions ~ 1035 decryptions § Only one is the right one § Brute force approach to find the right one: § At 1010 (10 bln) decr. /sec => 1035 / 1010 = 1016 sec = 10 bln yrs ! § Infeasible with current technology n Be smarter – use ingenuity n Could reduce 2625 to, say, 1015 decryptions to check At 1010 decr. /sec => 1015 / 1010 = 105 sec = ~ 1 day Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 17

2 A. 3. Requirements for Crypto Protocols n n n Messages should get to destination Only the recipient should get it Only the recipient should see it Proof of the sender’s identity Message shouldn’t be corrupted in transit Message should be sent/received once [cf. D. Frincke, U. of Idaho] n Proofs that message was sent/received (nonrepudiation) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 18

2 A. 4. Representing Characters n Letters (uppercase only) represented by numbers 0 -25 (modulo 26). A B C D. . . X Y Z 0 1 2 3. . . 23 24 25 n Operations on letters: A + 2 = C X + 4 = B (circular!). . . Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 19

2 B. Basic Types of Ciphers n Substitution ciphers n n Transposition (permutation) ciphers n n Letters of P replaced with other letters by E Order of letters in P rearranged by E Product ciphers n E „=” E 1 „+” E 2 „+”. . . „+” En n Combine two or more ciphers to enhance the security of the cryptosystem Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 20

2 B. 1. Substitution Ciphers n Substitution ciphers: n n Letters of P replaced with other letters by E Outline: a. The Caesar Cipher b. Other Substitution Ciphers c. One-Time Pads Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 21

a. The Caesar Cipher (1) § ci=E(pi)=pi+3 mod 26 (26 letters in the English alphabet) Change each letter to the third letter following it (circularly) A D, B E, . . . X A, Y B, Z C § Can represent as a permutation : (i) = i+3 mod 26 (0)=3, (1)=4, . . . , (23)=26 mod 26=0, (24)=1, (25)=2 § Key = 3, or key = ‘D’ (bec. D represents 3) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 22

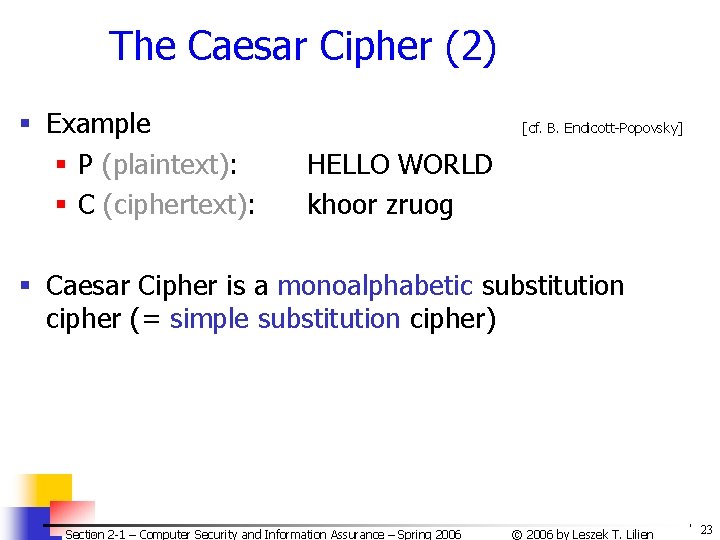
The Caesar Cipher (2) § Example § P (plaintext): § C (ciphertext): [cf. B. Endicott-Popovsky] HELLO WORLD khoor zruog § Caesar Cipher is a monoalphabetic substitution cipher (= simple substitution cipher) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 23

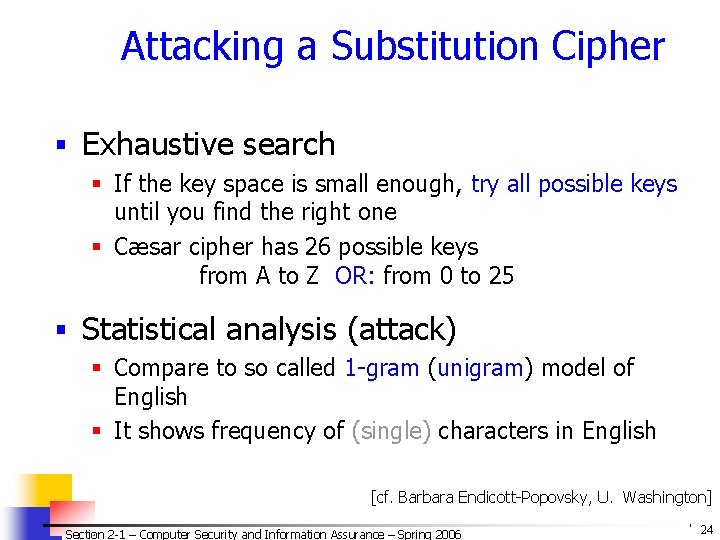
Attacking a Substitution Cipher § Exhaustive search § If the key space is small enough, try all possible keys until you find the right one § Cæsar cipher has 26 possible keys from A to Z OR: from 0 to 25 § Statistical analysis (attack) § Compare to so called 1 -gram (unigram) model of English § It shows frequency of (single) characters in English [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 24

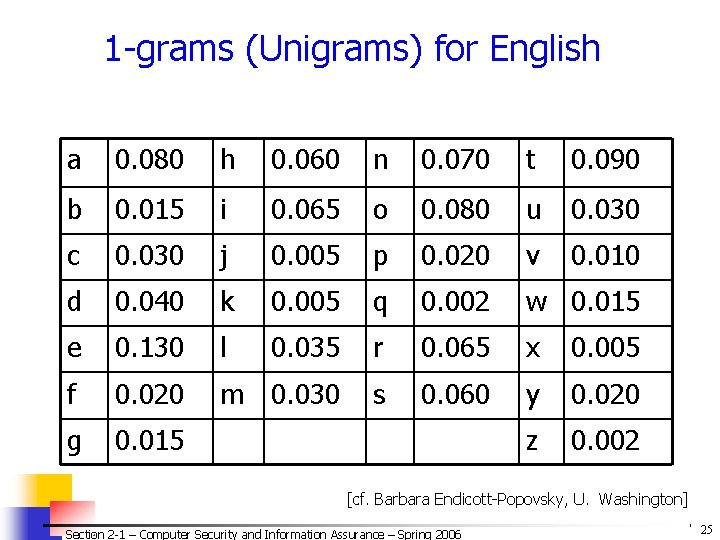
1 -grams (Unigrams) for English a 0. 080 h 0. 060 n 0. 070 t 0. 090 b 0. 015 i 0. 065 o 0. 080 u 0. 030 c 0. 030 j 0. 005 p 0. 020 v 0. 010 d 0. 040 k 0. 005 q 0. 002 w 0. 015 e 0. 130 l 0. 035 r 0. 065 x 0. 005 f 0. 020 m 0. 030 s 0. 060 y 0. 020 g 0. 015 z 0. 002 [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 25

Statistical Attack – Step 1 § Compute frequency f(c) of each letter c in ciphertext § Example: c = ‘khoor zruog’ § 10 characters: 3 * ‘o’, 2 * ‘r’, 1 * {k, h, z, u, g} § f(c): f(g)=0. 1 f(h)=0. 1 f(k)=0. 1 f(o)=0. 3 f(r)= 0. 2 f(u)=0. 1 f(z)=0. 1 f(ci) = 0 for any other ci § Apply 1 -gram model of English § Frequency of (single) characters in English § 1 -grams on previous slide [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 26

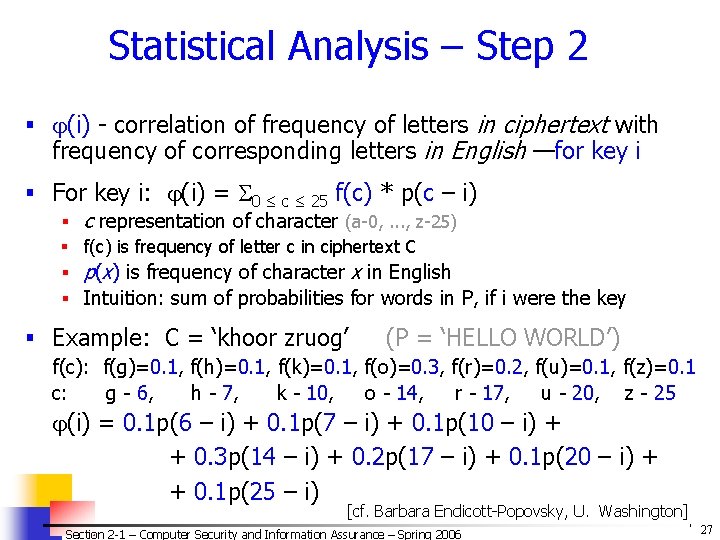
Statistical Analysis – Step 2 § (i) - correlation of frequency of letters in ciphertext with frequency of corresponding letters in English —for key i § For key i: (i) = 0 ≤ c ≤ 25 f(c) * p(c – i) § c representation of character (a-0, . . . , z-25) § f(c) is frequency of letter c in ciphertext C § p(x) is frequency of character x in English § Intuition: sum of probabilities for words in P, if i were the key § Example: C = ‘khoor zruog’ (P = ‘HELLO WORLD’) f(c): f(g)=0. 1, f(h)=0. 1, f(k)=0. 1, f(o)=0. 3, f(r)=0. 2, f(u)=0. 1, f(z)=0. 1 c: g - 6, h - 7, k - 10, o - 14, r - 17, u - 20, z - 25 (i) = 0. 1 p(6 – i) + 0. 1 p(7 – i) + 0. 1 p(10 – i) + + 0. 3 p(14 – i) + 0. 2 p(17 – i) + 0. 1 p(20 – i) + + 0. 1 p(25 – i) [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 27

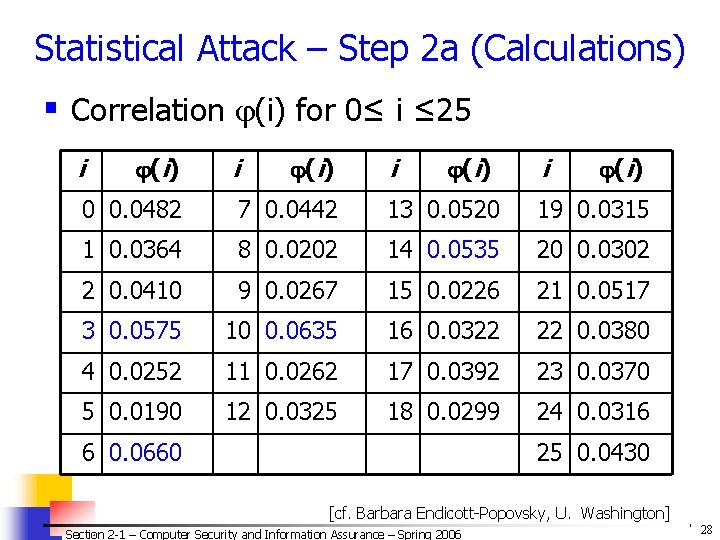
Statistical Attack – Step 2 a (Calculations) § Correlation (i) for 0≤ i ≤ 25 i (i) 0 0. 0482 7 0. 0442 13 0. 0520 19 0. 0315 1 0. 0364 8 0. 0202 14 0. 0535 20 0. 0302 2 0. 0410 9 0. 0267 15 0. 0226 21 0. 0517 3 0. 0575 10 0. 0635 16 0. 0322 22 0. 0380 4 0. 0252 11 0. 0262 17 0. 0392 23 0. 0370 5 0. 0190 12 0. 0325 18 0. 0299 24 0. 0316 6 0. 0660 25 0. 0430 [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 28

Statistical Attack – Step 3 (The Result) ¨ Most probable keys (largest (i) values): – i = 6, (i) = 0. 0660 • plaintext EBIIL TLOLA – i = 10, (i) = 0. 0635 • plaintext AXEEH PHKEW – i = 3, (i) = 0. 0575 • plaintext HELLO WORLD – i = 14, (i) = 0. 0535 • plaintext WTAAD LDGAS ¨ Only English phrase is for i = 3 – That’s the key (3 or ‘D’) – code broken [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 29

Caesar’s Problem § Conclusion: Key is too short § 1 -char key – monoalphabetic substitution § Can be found by exhaustive search § Statistical frequencies not concealed well by short key § They look too much like ‘regular’ English letters § Solution: Make the key longer § n-char key (n 2) – polyalphabetic substitution § Makes exhaustive search much more difficult § Statistical frequencies concealed much better § Makes cryptanalysis harder [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 30

b. Other Substitution Ciphers n-char key n Polyalphabetic substitution ciphers n Vigenere Tableaux cipher Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 31

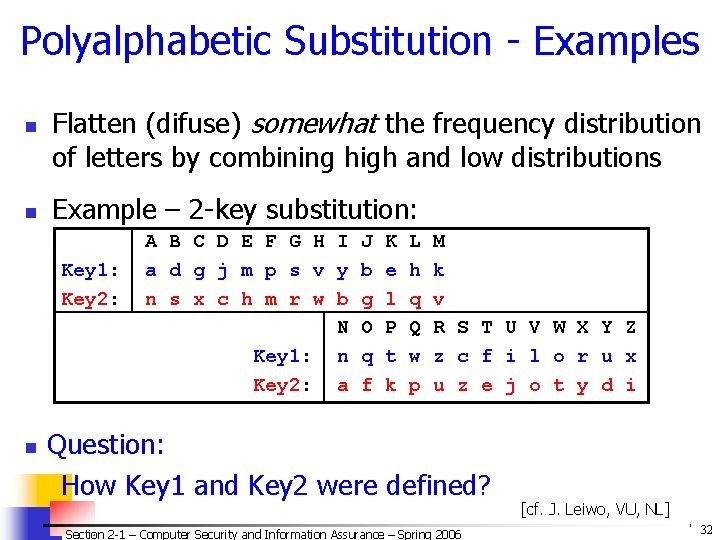
Polyalphabetic Substitution - Examples n n Flatten (difuse) somewhat the frequency distribution of letters by combining high and low distributions Example – 2 -key substitution: Key 1: Key 2: n A B C D E F G H I J a d g j m p s v y b n s x c h m r w b g N O Key 1: n q Key 2: a f K e l P t k L h q Q w p M k v R S T U V W X Y Z z c f i l o r u x u z e j o t y d i Question: How Key 1 and Key 2 were defined? Section 2 -1 – Computer Security and Information Assurance – Spring 2006 [cf. J. Leiwo, VU, NL] © 2006 by Leszek T. Lilien 32

n n . . . Example: Key 1: Key 2: n A B C D E F G H I J a d g j m p s v y b n s x c h m r w b g N O Key 1: n q Key 2: a f K e l P t k L h q Q w p M k v R S T U V W X Y Z z c f i l o r u x u z e j o t y d i Answer: Key 1 – start with ‘a’, skip 2, take next letter, . . . (circular) Key 2 - start with ‘n’ (2 nd half of alphabet), skip 4, take next, . . . (circular) [cf. J. Leiwo, VU, NL] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 33

Example: A B C D E F G H I J K Key 1: a d g j m p s v y b e Key 2: n s x c h m r w b g l N O P Key 1: n q t Key 2: a f k n n n Plaintext: Ciphertext: L h q Q w p M k v R S T U V W X Y Z z c f i l o r u x u z e j o t y d i TOUGH STUFF ffirv zfjpm use n (=2) keys in turn for consecutive P chars in P n Note: n n n Different chars mapped into the same one: T, O f Same char mapped into different ones: F p, m ‘f’ most frequent in C (0. 30); in English: f(f) = 0. 02 << f(e) = 0. 13 [cf. J. Leiwo, VU, NL] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 34
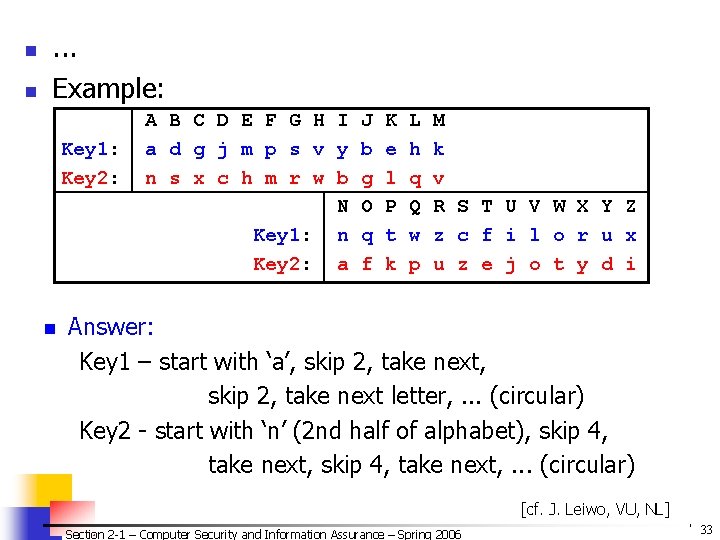
![Note Row Row Row Vigenere Tableaux 1 cf J Leiwo VU NL Note: Row Row. . . Row Vigenere Tableaux (1) [cf. J. Leiwo, VU, NL]](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-35.jpg)
Note: Row Row. . . Row Vigenere Tableaux (1) [cf. J. Leiwo, VU, NL] n P Section 2 -1 – Computer Security and Information Assurance – Spring 2006 A – shift 0 (a->a) B – shift 1 (a->b) C – shift 2 (a->c) Z – shift 25 (a->z) © 2006 by Leszek T. Lilien 35

Vigenère Tableaux (2) n Example Key: EXODUS Plaintext P: YELLOW SUBMARINE FROM YELLOW RIVER Extended keyword (re-applied to mimic words in P): YELLOW SUBMARINE FROM YELLOW RIVER EXODUSEXO DUSE XODUS Ciphertext: cbxoio wlppujmks ilgq vsofhb owyyj § Question: How derived from the keyword and Vigenère tableaux? [cf. J. Leiwo, VU, NL] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 36

Vigenère Tableaux (3) n Example. . . Extended keyword (re-applied to mimic words in P): YELLOW SUBMARINE FROM YELLOW RIVER EXODUSEXO DUSE XODUS Ciphertext: cbzoio wlppujmks ilgq vsofhb owyyj § Answer: c from P indexes row c from extended key indexes column e. g. : row Y and column e ‘c’ row E and column x ‘b’ row L and column o ‘z’. . . Section 2 -1 – Computer Security and Information Assurance – Spring 2006 [cf. J. Leiwo, VU, NL] © 2006 by Leszek T. Lilien 37

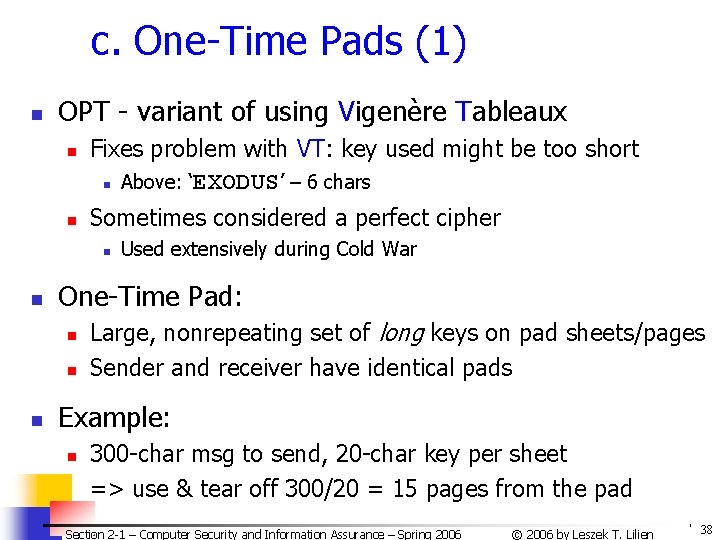
c. One-Time Pads (1) n OPT - variant of using Vigenère Tableaux n n Fixes problem with VT: key used might be too short n Above: ‘EXODUS’ – 6 chars Sometimes considered a perfect cipher n n One-Time Pad: n n n Used extensively during Cold War Large, nonrepeating set of long keys on pad sheets/pages Sender and receiver have identical pads Example: n 300 -char msg to send, 20 -char key per sheet => use & tear off 300/20 = 15 pages from the pad Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 38

One-Time Pads (2) n Example – cont. : § Encryption: § Sender writes letters of consecutive 20 -char keys above the letters of P (from the pad 15 pages) § Sender encipher P using Vigenère Tableaux (or other prearranged chart) § Sender destroys used keys/sheets § Decryption: § Receiver uses Vigenère Tableaux § Receiver uses the same set of consecutive 20 -char keys from the same 15 consecutive pages of the pad § Receiver destroys used keys/sheets Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 39

One-Time Pads (3) n Note: n Effect: a key as long as the message n n n If only key length ≤ the number of chars in the pad The key is always changing (and destroyed after use) Weaknesses n n n Perfect synchronization required between S and R n Intercepted or dropped messages can destroy synchro Need lots of keys Needs to distribute pads securely n No problem to generate keys n n Problem: printing, distribution, storing, accounting Frequency distribution not flat enough n Non-flat distribution facilitates breaking Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 40

Types of One-Time Pads n Vernam Cipher n n = (lttr + random nr) mod 26 (p. 48) Need (pseudo) random nr generator E. g. , V = 21; (V +76) mod 26 = 97 mod 26 = 19; 19 = t Book Ciphers (p. 49) n Book used as a pad n need not destroy – just don’t reuse keys Use common Vigenère Tableaux Details: textbook n Incl. example of breaking a book cipher n Bec. distribution not flat Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 41

n Question: Does anybody know other ciphers using books? Or invent your own cipher using books? Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 42

n n Question: . . . other ciphers using books? My examples: n Use any agreed upon book n P: SECRET § Example 1: Page 52 from a book: 52 ever, making predictions in ten letter seven of those secret positi gorithm § Example 2: Use: (page_nr, line_nr, letter_in_line) Use: (page_nr, line_nr, word_nr) C: 52 2 1 52 1 16. . . C: 52 2 4 Better: use different pages for each char in P Computer can help find words in a big electronic book quickly! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 43

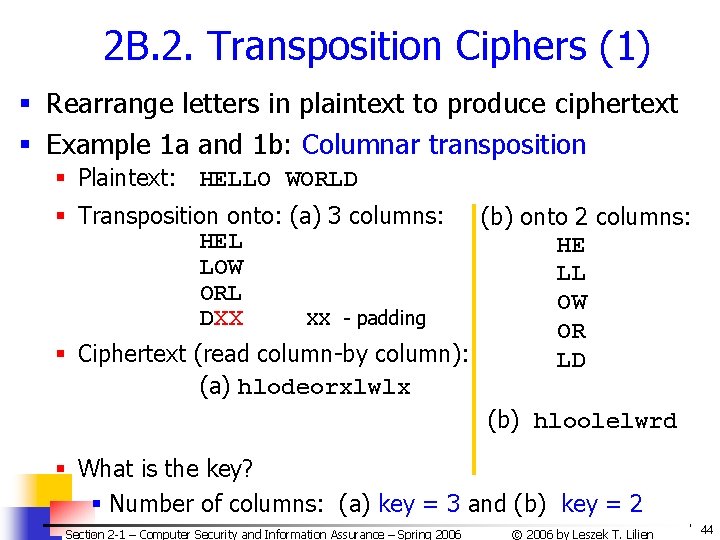
2 B. 2. Transposition Ciphers (1) § Rearrange letters in plaintext to produce ciphertext § Example 1 a and 1 b: Columnar transposition § Plaintext: HELLO WORLD § Transposition onto: (a) 3 columns: (b) onto 2 columns: HEL LOW ORL DXX XX - padding § Ciphertext (read column-by column): (a) hlodeorxlwlx HE LL OW OR LD (b) hloolelwrd § What is the key? § Number of columns: (a) key = 3 and (b) key = 2 Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 44

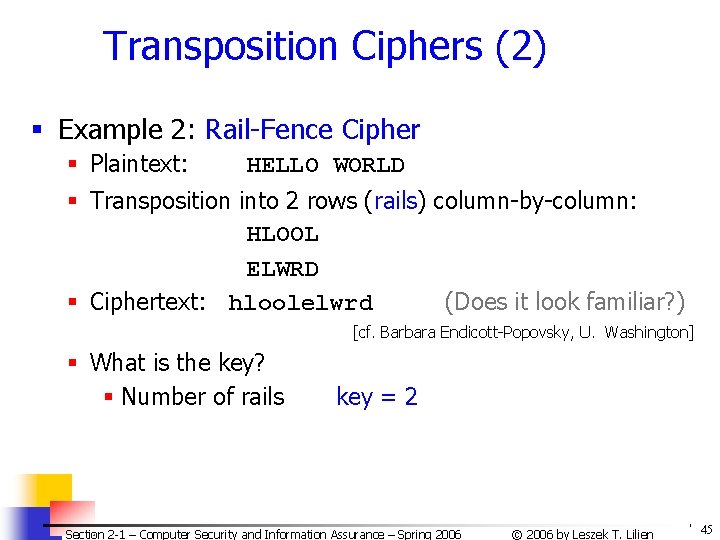
Transposition Ciphers (2) § Example 2: Rail-Fence Cipher § Plaintext: HELLO WORLD § Transposition into 2 rows (rails) column-by-column: HLOOL ELWRD § Ciphertext: hloolelwrd (Does it look familiar? ) [cf. Barbara Endicott-Popovsky, U. Washington] § What is the key? § Number of rails key = 2 Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 45

Attacking Transposition Ciphers § Anagramming § n-gram – n-char strings in English § Digrams (2 -grams) for English alphabet are: aa, ab, ac, . . . az, ba, bb, bc, . . . , zz (262 rows in digram table) § Trigrams are: aaa, aab, . . . (263 rows) § 4 -grams (quadgrams? ) are: aaaa, aaab, . . . (264 rows) § Attack procedure: § If 1 -gram frequencies in C match their freq’s in English but other n-gram freq’s in C do not match their freq’s in English, then it is probably a transposition encryption § Find n-grams with the highest frequencies in C § Start with n=2 § Rearrange substrings in C to form n-grams with highest freq’s [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 46

Example: Step 1 Ciphertext C: hloolelwrd (from Rail-Fence cipher) § N-gram frequency check § 1 -gram frequencies in C do match their frequencies in English § 2 -gram (hl, lo, oo, . . . ) frequencies in C do not match their frequencies in English § Question: How frequency of „hl” in C is calculated? § 3 -gram (hlo, loo, ool, . . . ) frequencies in C do not match their frequencies in English §. . . => it is probably a transposition § Frequencies in English for all 2 -grams from C starting with h § he 0. 0305 § ho 0. 0043 § hl, hw, hr, hd < 0. 0010 as table of freq’s of English diagrams shows § Implies that in hloolelwrd e follows h [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 47

Example: Step 2 § Arrange so the h and e are adjacent Since 2 -gram suggests a solution, cut C into 2 substrings – the 2 nd substring starting with e: hlool elwrd Put them in 2 columns: he ll ow or ld § Read row by row, to get original P: HELLO WORLD [cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 48

2 B. 3. Product Ciphers n A. k. a. combination ciphers n Built of multiple blocks, each is: n Substitution n Transposition or: n Example: two-block product cipher n n E 2(E 1(P, KE 1), KE 2) Product cipher might not be stronger than its individual components used separately! n Might not be even as strong as individual components Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 49

2 C. Making „Good” Ciphers Cipher = encryption algorithm n Outline 2 C. 1. Criteria for „Good” Ciphers 2 C. 2. Stream and Block Ciphers 2 C. 3. Cryptanalysis 2 C. 4. Symmetric and Asymmetric Cryptosystems Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 50

2 C. 1. Criteria for „Good” Ciphers (1) n „Good” depends on intended application n Substitution n Transposition n n C scrambles text => hides n-grams for n > 1 Product ciphers n n C hides chars of P If > 1 key, C dissipates high frequency chars Can do all of the above What is more important for your app? What facilities available to sender/receiver? n E. g. , no supercomputer support on the battlefield Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 51

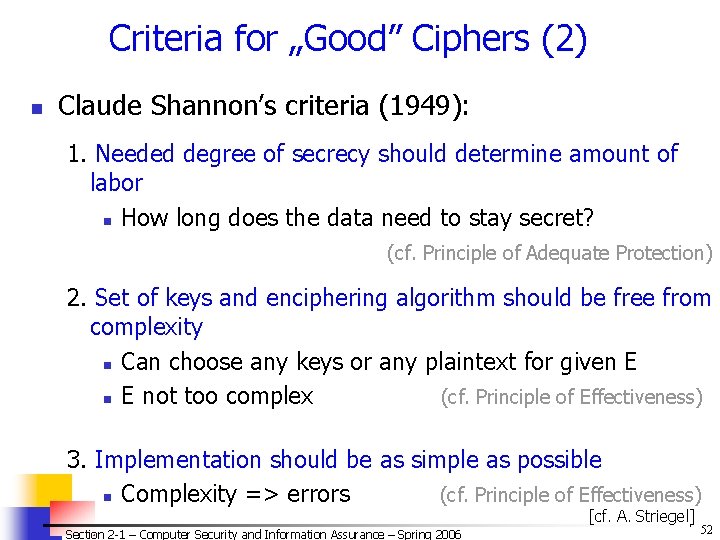
Criteria for „Good” Ciphers (2) n Claude Shannon’s criteria (1949): 1. Needed degree of secrecy should determine amount of labor n How long does the data need to stay secret? (cf. Principle of Adequate Protection) 2. Set of keys and enciphering algorithm should be free from complexity n Can choose any keys or any plaintext for given E not too complex (cf. Principle of Effectiveness) 3. Implementation should be as simple as possible n Complexity => errors (cf. Principle of Effectiveness) [cf. A. Striegel] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 52

Criteria for „Good” Ciphers (3) n Shannon’s criteria (1949) – cont. 4. Propagation of errors should be limited n Errors happen => their effects should be limited One error should not invlidate the whole C (None of the 4 Principles — Missing? — Invent a new Principle? ) n 5. Size / storage of C should be restricted n Size (C) should not be > size (P) n More text is more data for cryptanalysts to work with n Need more space for storage, more time to send (cf. Principle of Effectiveness) n Proposed at the dawn of computer era – [cf. A. Striegel] still valid! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 53

Criteria for „Good” Ciphers (4) n Characteristics of good encryption schemes n n Confusion: interceptor cannot predict what will happen to C when she changes one char in P n E with good confusion: hides well relationship between P”+”K, and C Diffusion: changes in P spread out over many parts of C n Good diffusion => attacker needs access to much of C to infer E Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 54

Criteria for „Good” Ciphers (5) n Commercial Principles of Sound Encryption Systems 1. Sound mathematics § Proven vs. not broken so far 2. Verified by expert analysis § Including outside experts 3. Stood the test of time § Long-term success is not a guarantee § Still. Flows in many E’s discovered soon after their release n Examples of popular commercial E’s: n DES / RSA / AES DES = Data Encryption Standard RSA = Rivest-Shamir-Adelman AES = Advanced Encryption Standard (rel. new) [cf. A. Striegel] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 55

2 C. 2. Stream and Block Ciphers (1) a. Stream ciphers b. Problems with stream ciphers c. Block ciphers d. Pros / cons for stream and block ciphers Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 56

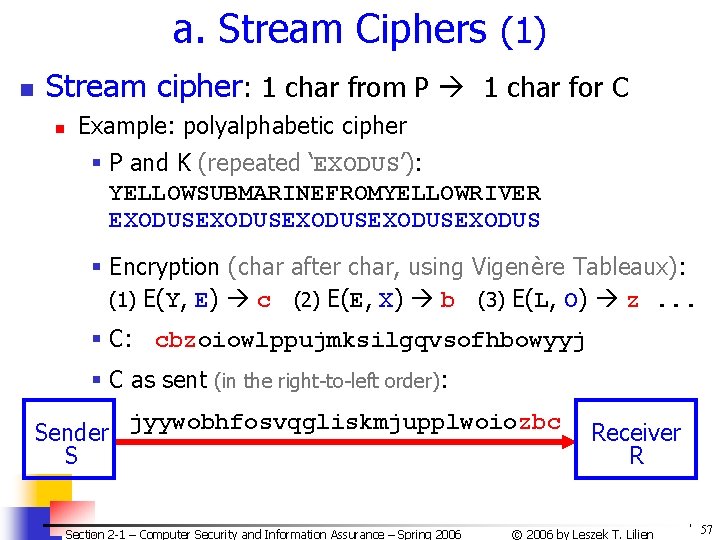
a. Stream Ciphers (1) n Stream cipher: 1 char from P 1 char for C n Example: polyalphabetic cipher § P and K (repeated ‘EXODUS’): YELLOWSUBMARINEFROMYELLOWRIVER EXODUSEXODUSEXODUS § Encryption (char after char, using Vigenère Tableaux): (1) E(Y, E) c (2) E(E, X) b (3) E(L, O) z. . . § C: cbzoiowlppujmksilgqvsofhbowyyj § C as sent (in the right-to-left order): Sender S jyywobhfosvqgliskmjupplwoiozbc Section 2 -1 – Computer Security and Information Assurance – Spring 2006 Receiver R © 2006 by Leszek T. Lilien 57

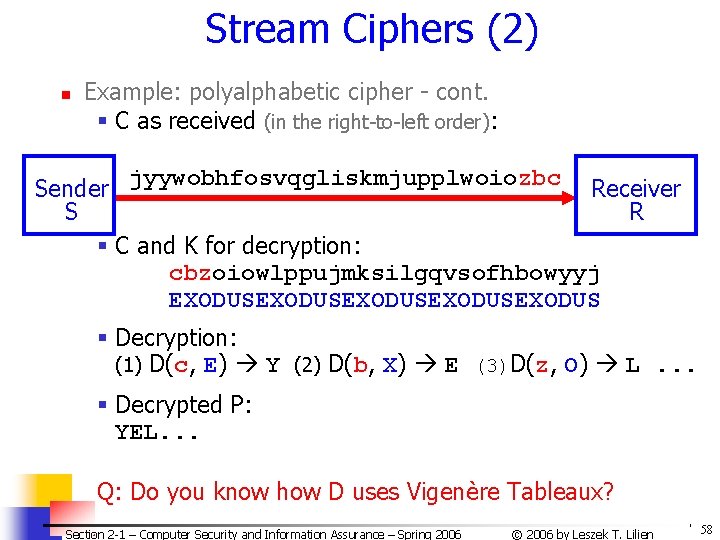
Stream Ciphers (2) n Example: polyalphabetic cipher - cont. § C as received (in the right-to-left order): jyywobhfosvqgliskmjupplwoiozbc Sender Receiver S R § C and K for decryption: cbzoiowlppujmksilgqvsofhbowyyj EXODUSEXODUSEXODUS § Decryption: (1) D(c, E) Y (2) D(b, X) E (3)D(z, O) L. . . § Decrypted P: YEL. . . Q: Do you know how D uses Vigenère Tableaux? Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 58

b. Problems with Stream Ciphers n (1) Problems with stream ciphers n Dropping a char from key K results in wrong decryption n Example: § P and K (repeated ‘EXODUS’) with a char in K missing: YELLOWSUBMARINEFROMYELLOWRIVER EODUSEXODUSEXODUSE missing X in K ! (no errors in repeated K later) § Encryption (using VT): 1) E(Y, E) c 2) E(E, O) s 3) E(L, D) o. . . § Ciphertext: cso. . . C in the order as sent (right-to-left): Section 2 -1 – Computer Security and Information Assurance – Spring 2006 . . . osc © 2006 by Leszek T. Lilien 59

Problems with Stream Ciphers (2) § C as received (in the right-to-left order): . . . osc § C and correct K (‘EXODUS’) for decryption: cso. . . EXO. . . n n Decryption (using VT, applying correct key): 1) D(c, E) Y 2) D(s, X) V 3) D(o, O) A. . . Decrypted P: YVA. . . - Wrong! n We know it’s wrong, Receiver might not know it yet! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 60

Problems with Stream Ciphers (3) n The problem might be recoverable n Example: If R had more characters decoded, R might be able to detect that S dropped a key char, and R could recover n E. g. , suppose that R decoded: YELLOW SUBMAZGTR § R could guess, that the 2 nd word should really be: SUBMARINE § => R would know that S dropped a char from K after sending „SUBMA” § => R could go back 4 chars, drop a char from K („recalibrate K with C”), and get „resynchronized” with S Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 61

c. Block Ciphers (1) n n We can do better than using recovery for stream ciphers n Solution: use block ciphers Block cipher: 1 block of chars from P 1 block of chars for C n n Example of block cipher: columnar transposition Block size = „o(message length)” (informally) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 62

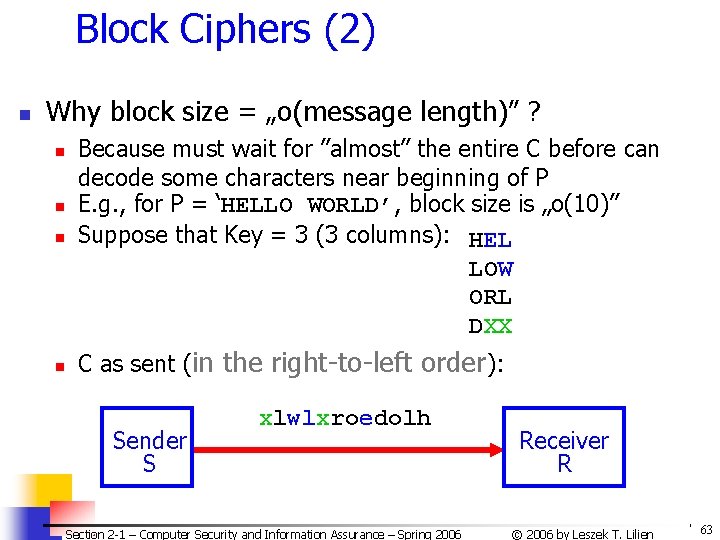
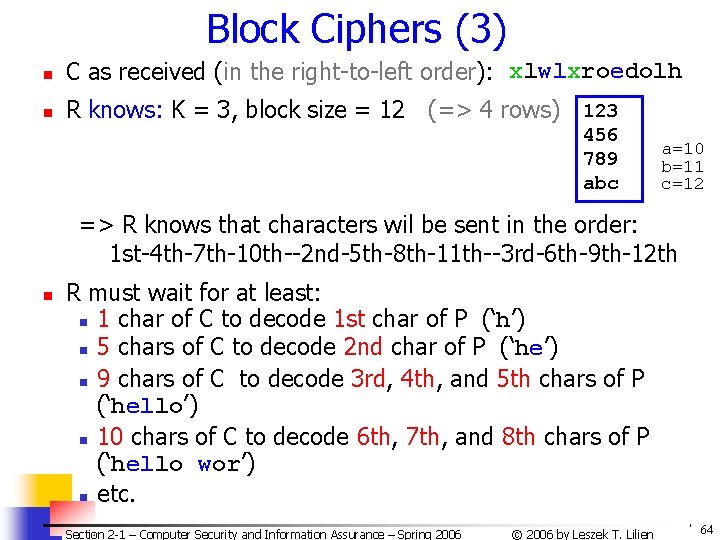
Block Ciphers (2) n Why block size = „o(message length)” ? n Because must wait for ”almost” the entire C before can decode some characters near beginning of P E. g. , for P = ‘HELLO WORLD’, block size is „o(10)” Suppose that Key = 3 (3 columns): HEL LOW ORL DXX n C as sent (in the right-to-left order): n n Sender S xlwlxroedolh Section 2 -1 – Computer Security and Information Assurance – Spring 2006 Receiver R © 2006 by Leszek T. Lilien 63

Block Ciphers (3) n C as received (in the right-to-left order): xlwlxroedolh n R knows: K = 3, block size = 12 (=> 4 rows) 123 456 789 abc a=10 b=11 c=12 => R knows that characters wil be sent in the order: 1 st-4 th-7 th-10 th--2 nd-5 th-8 th-11 th--3 rd-6 th-9 th-12 th n R must wait for at least: n 1 char of C to decode 1 st char of P (‘h’) n 5 chars of C to decode 2 nd char of P (‘he’) n 9 chars of C to decode 3 rd, 4 th, and 5 th chars of P (‘hello’) n 10 chars of C to decode 6 th, 7 th, and 8 th chars of P (‘hello wor’) n etc. Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 64

Block Ciphers (4) n Informally, we might call ciphers like the above example columnar transposition cipher „weak-block” ciphers n R can get some (even most) but not all chars of P before entire C is received n n R can get one char of P immediately n the 1 st-after 1 of C (delay of 1 - 1 = 0) R can get some chars of P with „small” delay n e. g. , 2 nd-after 5 of C (delay of 5 - 2 = 3) R can get some chars of P with „large” delay n e. g. , 3 rd-after 9 of C (delay of 9 – 3 = 6) There are block ciphers when R cannot even start decoding C before receiving the entire C n Informally, we might call them „strong-block” ciphers Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 65

d. Pros / Cons for Stream and Block Ciphers n (1) Pros / cons for stream ciphers n n + Low delay for decoding individual symbols n Can decode ASA received + Low error propagation n Error in E(c 1) does not affect E(c 2) - Low diffusion n Each char separately encoded => carries over its frequency info - Susceptibility to malicious insertion / modification n Adversary can fabricate a new msg from pieces of broken msgs, even if he doesn’t know E (just broke a few msgs) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 66

Pros / Cons for Stream and Block Ciphers (2) n Pros / cons for block ciphers n n + High diffusion n Frequency of a char from P diffused over (a few chars of) a block of C + Immune to insertion n Impossible to insert a char into a block without easy detection (block size would change) n Impossible to modify a char in a block without easy detection (if checksums are used) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 67

Pros / Cons for Stream and Block Ciphers (3) n Pros / cons for block ciphers — Part 2 n - High delay for decoding individual chars n See example for ‘hello worldxx’ above n n For some E can’t decode even the 1 st char before whole k chars of a block are received - High error propagation n It affects the block, not just a single char Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 68

2 C. 3. Cryptanalysis (1) n What cryptanalysts do when confronted with unknown? Four 1) 2) 3) 4) n possible situations w. r. t. available info: C available Full P available Partial P available E available (or D available) (1) – (4) suggest 5 different approaches Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 69

Cryptanalysis (2) n Cryptanalyst approaches 1) Ciphertext-only attack n We have shown examples for such attacks n E. g. , for Caesar’s cipher, columnar transposition cipher 2) Known plaintext attack n Analyst have C and P n Needs to deduce E such that C=E(P), then finds D 3) Probable plaintext attack n Partial decryption provides partial match to C n This provides more clues Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 70

Cryptanalysis (3) n Cryptanalyst approaches – cont. 4) Chosen plaintext attack n Analyst able to fabricate encrypted msgs n Then observe effects of msgs on adversary’s actions n This provides further hints 5) Chosen ciphertext attack n n Analyst has both E and C Run E for many candidate plaintexts to find P for which E(P) = C n Purpose: to find KE Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 71

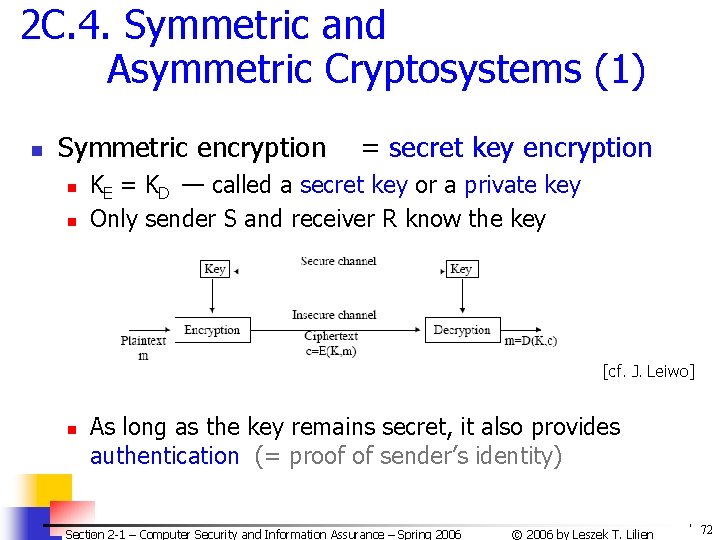
2 C. 4. Symmetric and Asymmetric Cryptosystems (1) n Symmetric encryption n n = secret key encryption KE = KD — called a secret key or a private key Only sender S and receiver R know the key [cf. J. Leiwo] n As long as the key remains secret, it also provides authentication (= proof of sender’s identity) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 72

Symmetric and Asymmetric Cryptosystems (2) n Problems with symmetric encryption: n n Ensuring security of the „key channel” Need an efficient key distribution infrastructure n A separate key needed for each communicating S-R pair n For n communicating users, need: n * (n -1) /2 keys Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 73

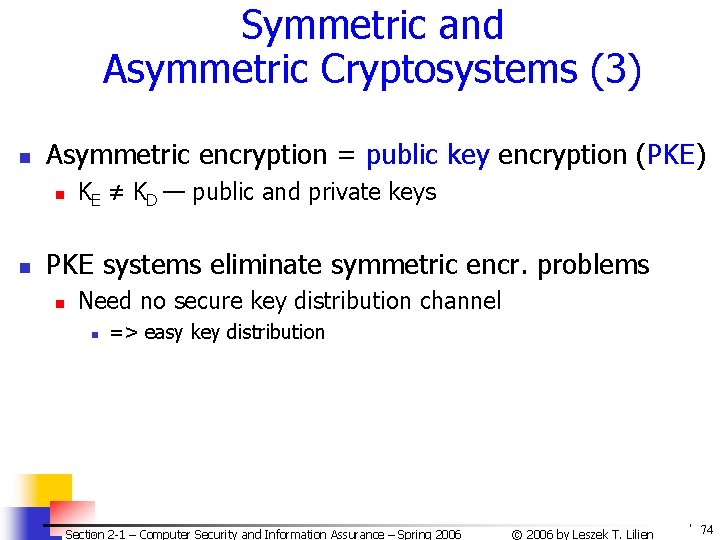
Symmetric and Asymmetric Cryptosystems (3) n Asymmetric encryption = public key encryption (PKE) n n KE ≠ KD — public and private keys PKE systems eliminate symmetric encr. problems n Need no secure key distribution channel n => easy key distribution Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 74

Symmetric and Asymmetric Cryptosystems (4) n One PKE approach: n n n R keeps her private key KD R can distribute the correspoding public key KE to anybody who wants to send encrypted msgs to her n No need for secure channel to send KE n Can even post the key on an open Web site — it is public! Only private KD can decode msgs encoded with public KE! n Anybody (KE is public) can encode n Only owner of KD can decode Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 75

Symmetric and Asymmetric Cryptosystems (5) Symm. vs. Asymm. Key Algorithms Symmetric Asymmetric n Key: D = E n n K kept secret n K agreed upon between 2 parties in advance n n n Like using a „simple” safe (with one door) n Need safe key to deposit doc in safe n Need safe key to get doc from safe n Key pair: <E, D>, D ≠ E D kept secret E public (usually; or known to n users) E distributed to k users before first communication (by owner of D) Like using a safe with locked deposit slot n Need deposit slot key to slide doc into safe n Need safe door key to get doc from safe [Symmetric - cf. Barbara Endicott-Popovsky, U. Washington, Source: D. Frincke, U. of Idaho] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 76

Symmetric and Asymmetric Cryptosystems (6) Need for Key Management n Private key must be carefully managed in both SE and PKE (asymm. ) cryptosystems n Storing / safeguarding / activating-deactivating Keys can expire - e. g. to take a key away from a fired employee n Public key must be carefully distributed in PKE systems => Key management is a major issue [cf. A. Striegel] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 77

2 D. DES (Data Encryption Standard) n Outline 2 D. 1. Background and History of DES 2 D. 2. Overview of DES 2 D. 3. Double and Triple DES 2 D. 4. Security of DES Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 78

2 D. 1. Background and History of DES n (1) Early 1970’s - NBS (Nat’l Bureau of Standards) recognized general public’s need for a secure crypto system NBS – part of US gov’t / Now: NIST – Nat’l Inst. of Stand’s & Technology n n n „Encryption for the masses” [A. Striegel] Existing US gov’t crypto systems were not meant to be made public n E. g. Do. D, State Dept. Problems with proliferation of commercial encryption devices n Incompatible n Not extensively tested by independent body Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 79

Background and History of DES (2) n 1972 - NBS calls for proposals for a public crypto system n Criteria: Highly secure / easy to understand / publishable / available to all / adaptable to diverse app’s / economical / efficient to use / able to be validated / exportable § In truth: Not too strong (for NSA, etc. ) n n 1974 – IBM proposed its Lucifer n n n DES based on it Tested by NSA (Nat’l Security Agency) and the general public Nov. 1976 – DES adopted as US standard for sensitive but unclassified data / communication n n Later adopted by ISO (Int’l Standards Organization) Official name: DEA - Data Encryption Algorithm / DEA-1 abroad Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 80

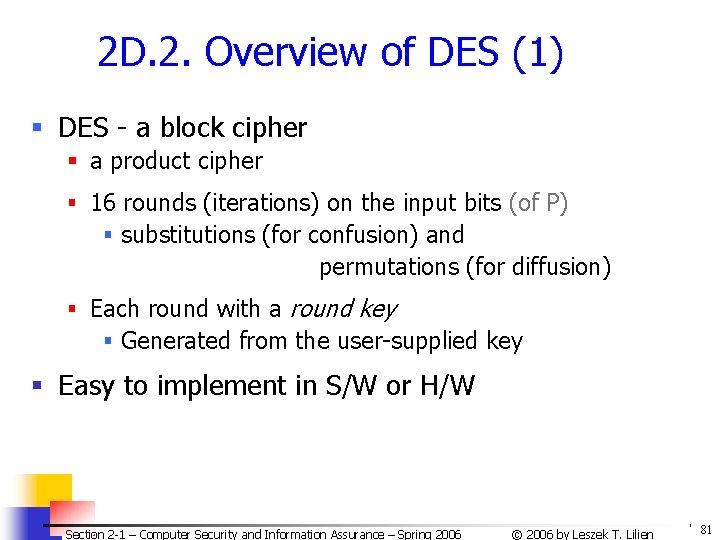
2 D. 2. Overview of DES (1) § DES - a block cipher § a product cipher § 16 rounds (iterations) on the input bits (of P) § substitutions (for confusion) and permutations (for diffusion) § Each round with a round key § Generated from the user-supplied key § Easy to implement in S/W or H/W Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 81
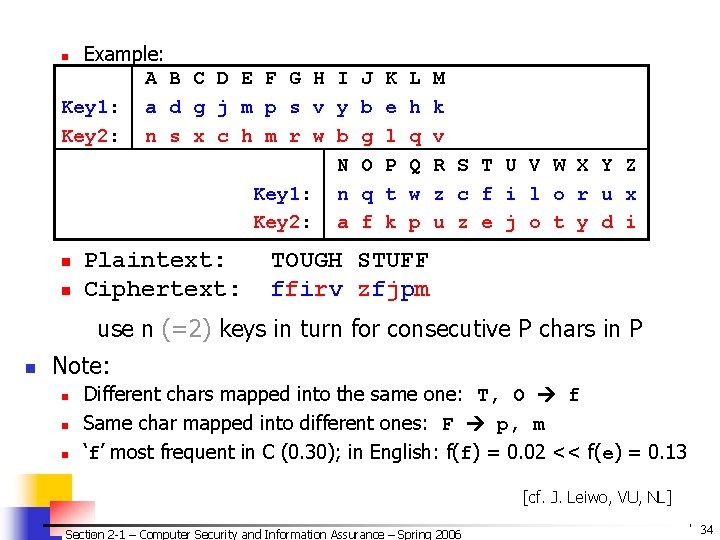
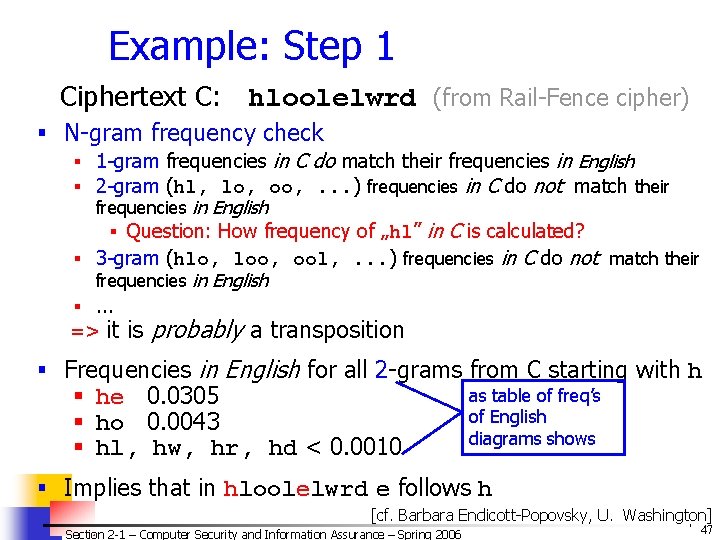
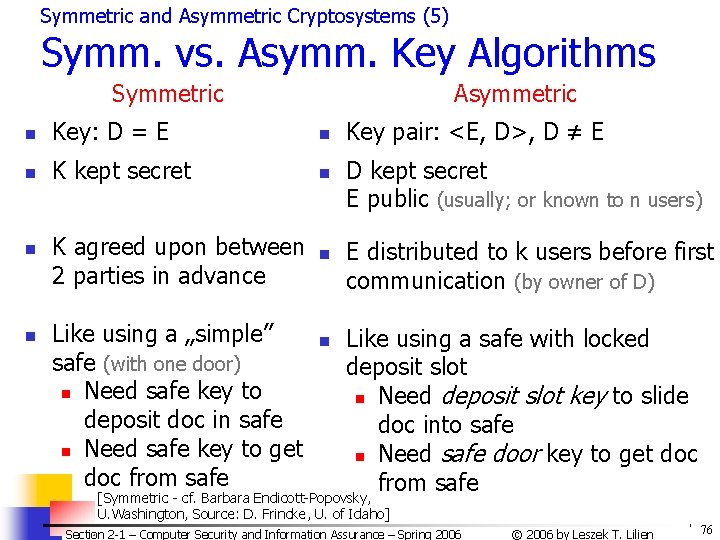
![Overview of DES 2 Basic Structure n n Fig cf J Leiwo Input Overview of DES (2) Basic Structure n n [Fig. – cf. J. Leiwo] Input:](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-82.jpg)
Overview of DES (2) Basic Structure n n [Fig. – cf. J. Leiwo] Input: 64 bits (a block) Li/Ri– left/right half of the input block Input Permutation for iteration i (32 bits) – subject to L 0 R 0 substitution S and permutation P (cf. Fig 2 -8 – text) n n K - user-supplied key Ki - round key: n n S 56 bits used +8 unused (unused for E but often used for error checking) Output: 64 bits (a block) Note: Ri becomes L(i+1) All basic op’s are simple logical ops n Left shift / XOR Section 2 -1 – Computer Security and Information Assurance – Spring 2006 K P L 1 R 1 L 16 R 16 K 16 Final Permutation Output © 2006 by Leszek T. Lilien 82

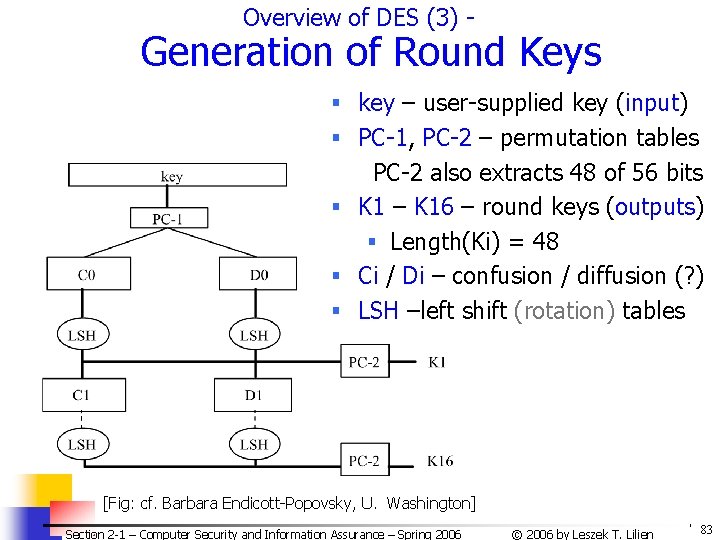
Overview of DES (3) - Generation of Round Keys § key – user-supplied key (input) § PC-1, PC-2 – permutation tables PC-2 also extracts 48 of 56 bits § K 1 – K 16 – round keys (outputs) § Length(Ki) = 48 § Ci / Di – confusion / diffusion (? ) § LSH –left shift (rotation) tables [Fig: cf. Barbara Endicott-Popovsky, U. Washington] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 83

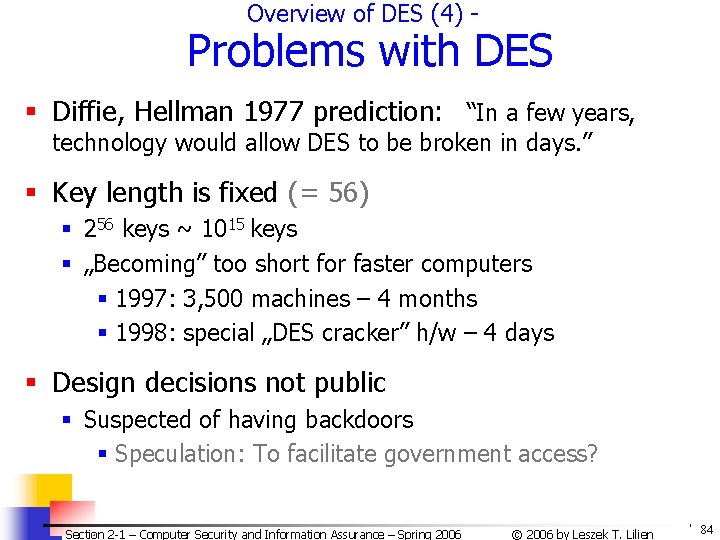
Overview of DES (4) - Problems with DES § Diffie, Hellman 1977 prediction: “In a few years, technology would allow DES to be broken in days. ” § Key length is fixed (= 56) § 256 keys ~ 1015 keys § „Becoming” too short for faster computers § 1997: 3, 500 machines – 4 months § 1998: special „DES cracker” h/w – 4 days § Design decisions not public § Suspected of having backdoors § Speculation: To facilitate government access? Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 84

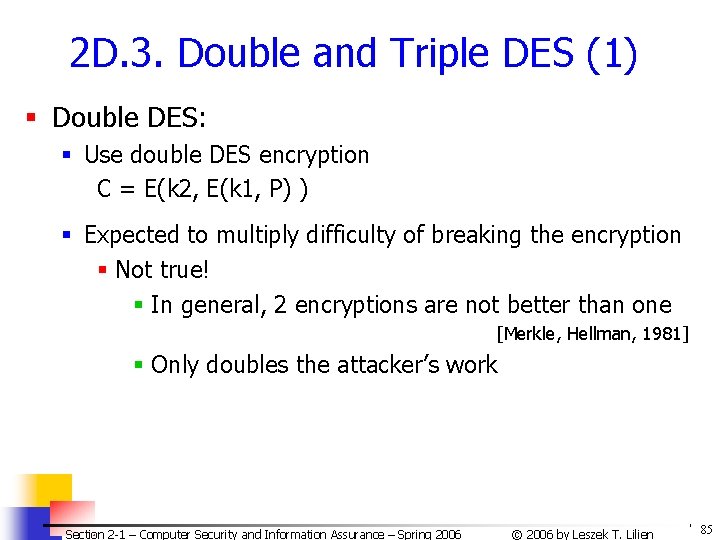
2 D. 3. Double and Triple DES (1) § Double DES: § Use double DES encryption C = E(k 2, E(k 1, P) ) § Expected to multiply difficulty of breaking the encryption § Not true! § In general, 2 encryptions are not better than one [Merkle, Hellman, 1981] § Only doubles the attacker’s work Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 85

Double and Triple DES (2) § Triple DES: § Is it C = E(k 3, E(k 2, E(k 1, P) ) ? § Not soooo simple! Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 86

Double and Triple DES (3) § Triple DES: § Tricks used: D not E in the 2 nd step, k 1 used twice (in steps 1 & 3) § It is: C = E(k 1, D(k 2, E(k 1, P) ) and P = D(k 1, E(k 2, D(k 1, C) ) § Doubles the effective key length § 112 -bit key is quite strong § Even for today’s computers § For all feasible known attacks Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 87

2 D. 4. Security of DES § So, is DES insecure? § No, not yet § 1997 attack required a lot of coperation § The 1998 special-purpose machine is still very expensive § Triple DES still beyong the reach of these 2 attack § But. . . § In 1995, NIST (formerly NBS) began search for new strong encryption standard Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 88

2 E. The Clipper Story (1) §. . . Or: How not to set up a standard § A scenario § Only a single electronic copy of a corporation’s crucial (and sensitive) document § To prevent espionage, strong encryption used to protect that document § Only CEO knows the key § CEO gets hit by a truck § Is the document lost forever? § Key escrow (a depository) facilitates recovery of the document if the key is lost [cf. J. Leiwo] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 89

The Clipper Story (2) § 1993 - Clipper - U. S. Government’s attempt to mandate key escrow § Secret algorithm, invented by National Security Agency § Only authorities, can recover any communications § Add an escrow key and split into halves § Give each half to a different authority § If there is a search warrant, authorities can combine their halves and recover intercepted communication § Of course, government will use it for legitimate purposes only [cf. J. Leiwo] Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 90

The Clipper Story (3) § Clipper failed big time: § Classified algorithm, h/w (Clipper chip) implement’s only § Equipment AND keys provided by the government § No export of equipment [above -cf. J. Leiwo] § Public relations disaster § “Electronic civil liberties" organizations (incl. Electronic Privacy Information Center & Electronic Frontier Foundation) challenged the Clipper chip proposal § Their claims: § It would subject citizens to increased, possibly illegal, government surveillance § strength of encryption could not be evaluated by the public (bec. secret algorithm) – might be insecure Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 91

2 F. AES (Advanced Encryption Standard) n . . . Or: How to set up a standard n Outline 2 F. 1. The AES Contest 2 F. 2. Overview of Rijndael 2 F. 3. Strength of AES 2 F. 4. Comparison of DES and AES Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 92

2 F. 1. The AES Contest (1) n Institute of 1997 – NIST calls for proposals NIST (Nat’l Standards and n n Technology) Criteria: n Unclassifed code n Publicly disclosed n Royalty-free worldwide n Symmetric block cipher for 128 -bit blocks n Usable with keys of 128, 192, and 256 bits 1998 – 15 algorithms selected Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 93

The AES Contest (2) n 1999 – 5 finalists n n n [cf. J. Leiwo] MARS by IBM RC 6 by RSA Laboratories Rijndael by Joan Daemen and Vincent Rijmen Serpent by Ross Anderson, Eli Biham and Lars Knudsen Twofish by Bruce Schneier, John Kelsey, Doug Whiting, Dawid Wagner, Chris Hall and Niels Ferguson Evaluation of finalists n n Public and private scrutiny Key evaluation areas: security / cost or efficiency of operation / ease of software implementation Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 94

The AES Contest (3) n 2001 - … and the winner is … Rijndael (RINE-dahl) Authors: Vincent Rijmen + Joan Daemen (Dutchmen) n Adopted by US gov’t as Federal Info Processing Standard 197 (FIPS 197) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 95

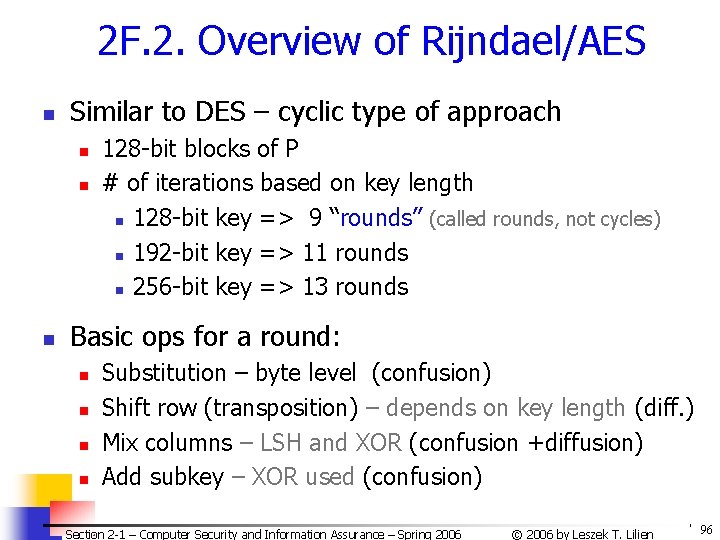
2 F. 2. Overview of Rijndael/AES n Similar to DES – cyclic type of approach n n n 128 -bit blocks of P # of iterations based on key length n 128 -bit key => 9 “rounds” (called rounds, not cycles) n 192 -bit key => 11 rounds n 256 -bit key => 13 rounds Basic ops for a round: n n Substitution – byte level (confusion) Shift row (transposition) – depends on key length (diff. ) Mix columns – LSH and XOR (confusion +diffusion) Add subkey – XOR used (confusion) Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 96

2 F. 3. Strengths of AES n Not much experience so far (since 2001) n But: n n n Extensive cryptanalysis by US gov’t and independent experts Dutch inventors have no ties to NSA or other US gov’t bodies (less suspicion of trapdoor) Solid math basis n Despite seemingly simple steps within rounds Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 97
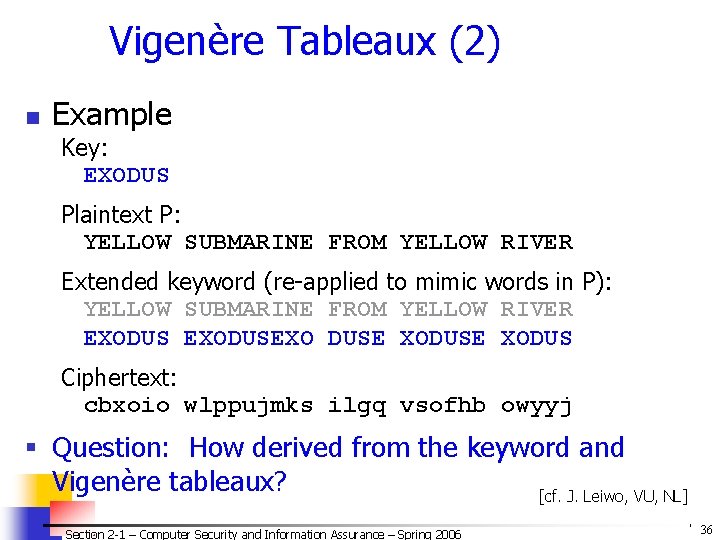
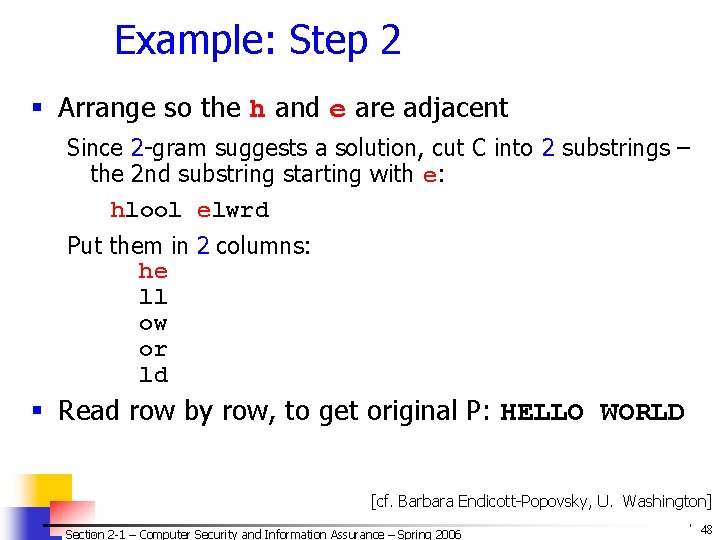
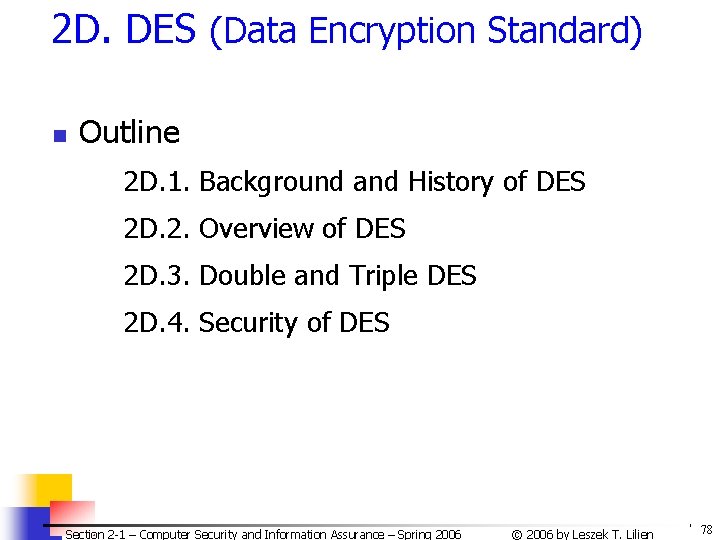
![2 F 4 Comparison of DES AES 1 Date Block size bits Key 2 F. 4. Comparison of DES & AES (1) Date Block size [bits] Key](https://slidetodoc.com/presentation_image_h/78e5999b4f680d5371e58b9f1e56d412/image-98.jpg)
2 F. 4. Comparison of DES & AES (1) Date Block size [bits] Key length [bits] Encryption Primitives Cryptographic Primitives Design Rationale Selection process Source DES 1976 64 56 (effect. ) substitution, permutation confusion, diffusion open closed AES 1999 128, 192, 256, or more substitution, shift, bit mixing confusion, diffusion open secret, but accepted public comments independent Dutch cryptographers IBM, enhanced by NSA Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 98

Comparison of DES & AES (2) n Weaknesses in AES? n n 20+ yrs of experience with DES eliminated fears of its weakness (intentional or not) n Might be naïve… Experts pored over AES for 2 -year review period Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 99

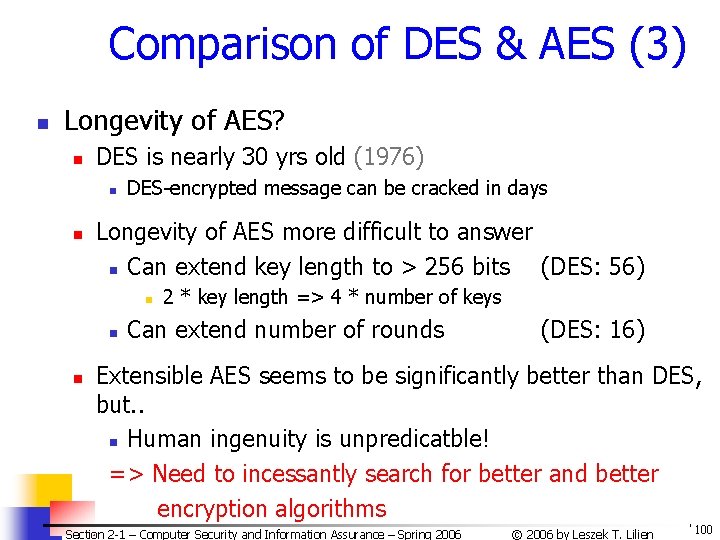
Comparison of DES & AES (3) n Longevity of AES? n DES is nearly 30 yrs old (1976) n n DES-encrypted message can be cracked in days Longevity of AES more difficult to answer n Can extend key length to > 256 bits (DES: 56) n n n 2 * key length => 4 * number of keys Can extend number of rounds (DES: 16) Extensible AES seems to be significantly better than DES, but. . n Human ingenuity is unpredicatble! => Need to incessantly search for better and better encryption algorithms Section 2 -1 – Computer Security and Information Assurance – Spring 2006 © 2006 by Leszek T. Lilien 100

End of Part 1 of Section 2: Introduction to Cryptology