CS 558 Lecture on Passwords I Honeywords Making




















- Slides: 41

CS 558 Lecture on Passwords I Honeywords: Making Password-Cracking Detectable by Ari Juels , Ronald L. Rivest presenter : Eirini Aikaterini Degleri , 2735

Table of contents 1. Introduction 2. Technical Description 3. Honeyword Generations 4. Policy Choices 5. Attacks 2 Computer Science Department, Passwords

Introduction Passwords are a notoriously weak authentication mechanism. Users frequently choose poor passwords. Even hashed passwords are not a safe solution. 3 Computer Science Department, Passwords

Ideas � Make password hashing more complex and time- consuming. � can help � slows down the authentication process for legitimate users, and doesn’t make successful password cracking easier to detect. � Set up fake user accounts (“honeypot accounts”) � an alarm is raised when an adversary attempts to login. � the adversary may be able to distinguish real fake usernames, and thus avoid detection. 4 Computer Science Department, Passwords usernames from

Honeywords � Proposition � 5 a simple method for improving the security of hashed passwords: the maintenance of additional “honeywords”( false passwords) associated with each user’s account. Computer Science Department, Passwords

Technical Description Pi is the password for user ui. System uses a cryptographic hash function H and stores hashes of passwords and maintains a file F listing username / password-hash pairs of the form (ui, H(pi)) for i = 1, 2, …, n. 6 Computer Science Department, Passwords

Let’s stage the scenery � File F of usernames and associated hashed passwords � Values of the salt or other parameters required to compute the hash function H. � Can perform a brute-force search , until he determines the passwords for one or more users. If passwords are the only authentication mechanism in place, the adversary can then log in to the accounts of those users in a reliable and undetected manner. 7 Computer Science Department, Passwords

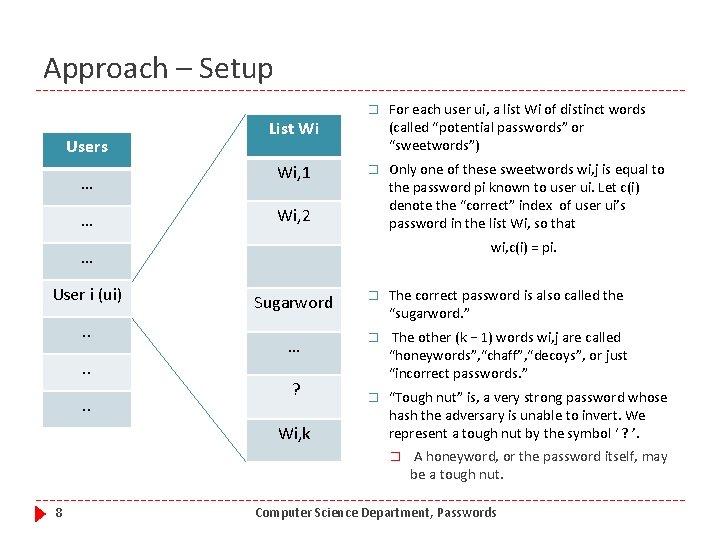
Approach – Setup Users … … � For each user ui, a list Wi of distinct words (called “potential passwords” or “sweetwords”) � Only one of these sweetwords wi, j is equal to the password pi known to user ui. Let c(i) denote the “correct” index of user ui’s password in the list Wi, so that List Wi Wi, 1 Wi, 2 wi, c(i) = pi. … User i (ui). . . Sugarword � The correct password is also called the “sugarword. ” … � The other (k − 1) words wi, j are called “honeywords”, “chaff”, “decoys”, or just “incorrect passwords. ” � “Tough nut” is, a very strong password whose hash the adversary is unable to invert. We represent a tough nut by the symbol ‘ ? ’. ? Wi, k � 8 A honeyword, or the password itself, may be a tough nut. Computer Science Department, Passwords

Honeychecker I � An auxiliary secure server , to assist with honeywords � System communicates with the honeychecker when a login attempt is made, or when a user changes her password. � In case of an irregularity, honeychecker is capable of raising an alarm. 9 Computer Science Department, Passwords

Honeychecker II � Honeychecker maintains a single database value c(i) for each user ui; � It accepts commands of exactly two types: Set: i, j , Sets c(i) to have value j. � Check: i, j , Checks that c(i) = j. May return result of check to requesting computer system. � 10 Computer Science Department, Passwords

Generation Algorithm � Honeyword generation scheme with user input pi. � of the form Gen(k; pi), Gen(k, pi) is run, using a user-provided input pi � Keyword generator Gen(k) generates a list Wi of length k of sweetwords for user ui � an index c(i) of the correct password pi within Wi: some randomly chosen honeywords output by Gen(k; pi) may be “tough nuts”; for those honeywords the adversary only sees the symbol ? and not the underlying (hard) honeyword. � Table c is maintained in a secure manner; in the proposal of this paper it is stored on the honeychecker. 11 Computer Science Department, Passwords

Approach – Login � Password “g”. � Is “g” a honeyword ? � setting off an alarm or notifying a system administrator, � letting login proceed as usual, � letting the login proceed, but on a honeypot system, � tracing the source of the login carefully, etc 12 Computer Science Department, Passwords

Approach – Change of password � When user ui changes her password, or sets it up account is first initialized, the system needs to: � � � when her use procedure Gen(k) securely notify the honeychecker of the new value of c(i), update the user’s entry in the file F to (ui, Hi). The honeychecker does not learn the new password or any of the new honeywords. All it learns is the position c(i) of the hash vi, c(i) of user ui’s new password in the user’s list Hi in F. 13 Computer Science Department, Passwords

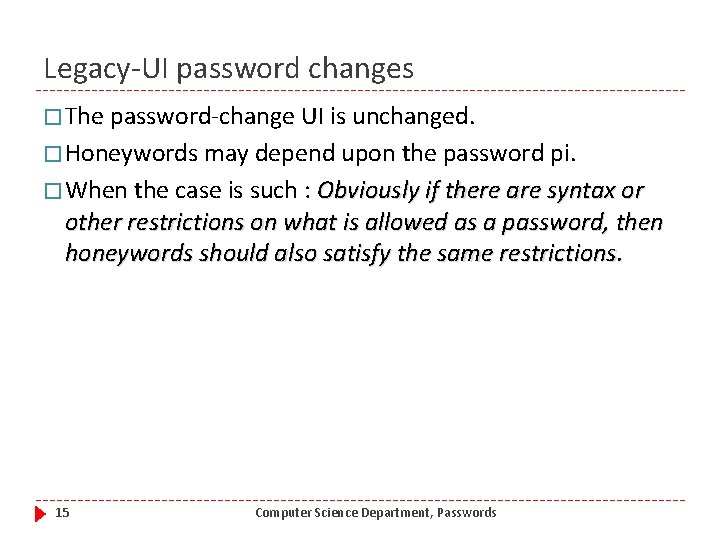
Honeyword Generations • Legacy-UI procedures, the password-change UI is unchanged (chaffing-by-tweaking, chaffing-with-a-password-model) • Modified-UI procedures, the password-change UI is modified to allow for better password/honeyword generation (take-a-tail ) 14 Computer Science Department, Passwords

Legacy-UI password changes � The password-change UI is unchanged. � Honeywords may depend upon the password pi. � When the case is such : Obviously if there are syntax or other restrictions on what is allowed as a password, then honeywords should also satisfy the same restrictions. 15 Computer Science Department, Passwords

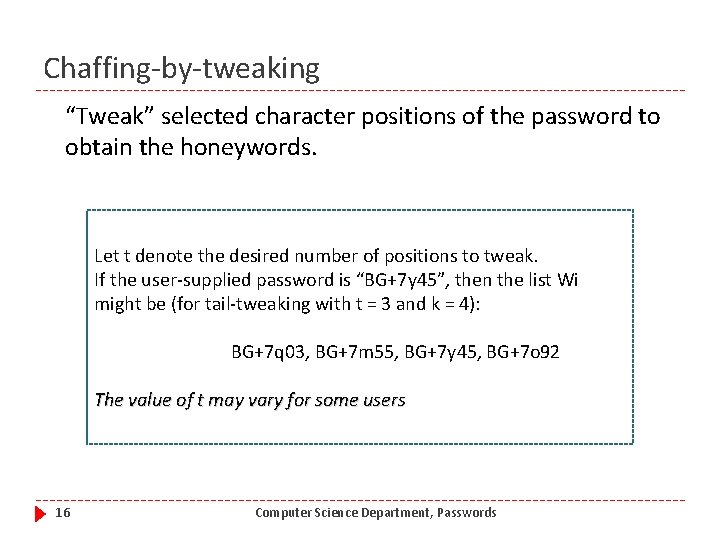
Chaffing-by-tweaking “Tweak” selected character positions of the password to obtain the honeywords. Let t denote the desired number of positions to tweak. If the user-supplied password is “BG+7 y 45”, then the list Wi might be (for tail-tweaking with t = 3 and k = 4): BG+7 q 03, BG+7 m 55, BG+7 y 45, BG+7 o 92 The value of t may vary for some users 16 Computer Science Department, Passwords

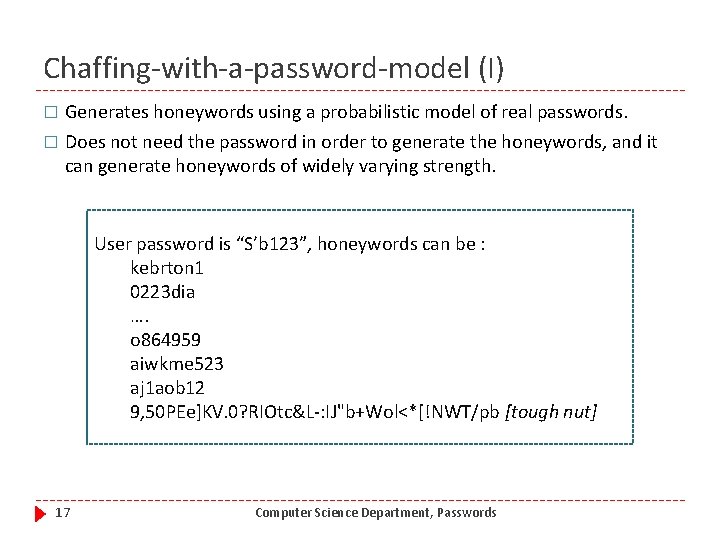
Chaffing-with-a-password-model (I) � Generates honeywords using a probabilistic model of real passwords. � Does not need the password in order to generate the honeywords, and it can generate honeywords of widely varying strength. User password is “S’b 123”, honeywords can be : kebrton 1 0223 dia …. o 864959 aiwkme 523 aj 1 aob 12 9, 50 PEe]KV. 0? RIOtc&L-: IJ"b+Wol<*[!NWT/pb [tough nut] 17 Computer Science Department, Passwords

Chaffing-with-a-password-model (II) � The password is parsed into a sequence of “tokens, ” each representing a distinct syntactic element—a word, number, or set of special characters. password “mice 3 blind” might be decomposed into the token sequence W 4 | D 1 | W 5 � Honeywords are then generated by replacing tokens with randomly selected values that match the tokens. 18 Computer Science Department, Passwords

Chaffing with “tough nuts” � In the presence of “tough nuts, ” the adversary cannot fully evaluate the likelihood of being detected during login, even if the adversary has cracked all other sweetwords. � To ensure that the adversary cannot tell whether the password itself lies among the set of “tough nuts” � Randomize the positions and the number of “tough nuts” added as honeywords. 19 Computer Science Department, Passwords

Modified-UI password changes “Take-a-tail” is identical to the chaffing-by-tail tweaking method, except that the tail of the new password is now randomly chosen by the system, and required in the user-entered new password. � The required tail is randomly and freshly generated for each password change session. � “Enter a new password: ” has changed to something like: “Propose a password: ” • • Append ‘ 413’ to make your new password. Enter your new password: • • • Thus, if the user proposes “Red. Eye 2, ” his new password is “Red. Eye 2413. ” 20 Computer Science Department, Passwords

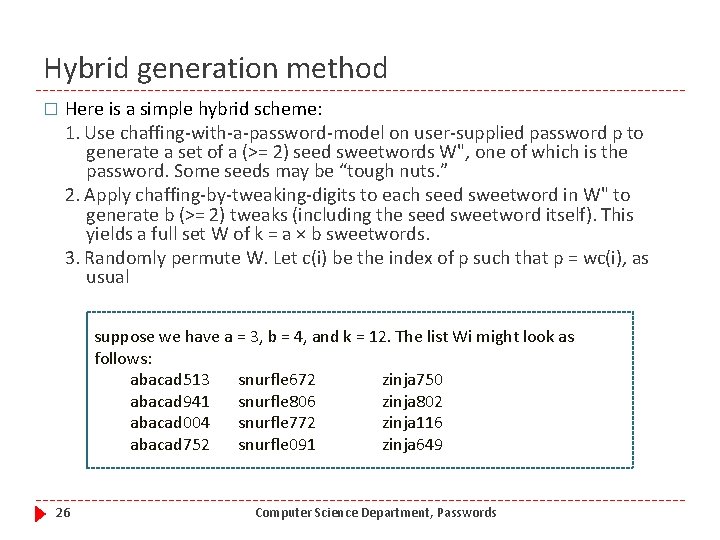
Hybrid generation method � Here is a simple hybrid scheme: 1. Use chaffing-with-a-password-model on user-supplied password p to generate a set of a (>= 2) seed sweetwords W", one of which is the password. Some seeds may be “tough nuts. ” 2. Apply chaffing-by-tweaking-digits to each seed sweetword in W" to generate b (>= 2) tweaks (including the seed sweetword itself). This yields a full set W of k = a × b sweetwords. 3. Randomly permute W. Let c(i) be the index of p such that p = wc(i), as usual suppose we have a = 3, b = 4, and k = 12. The list Wi might look as follows: abacad 513 snurfle 672 zinja 750 abacad 941 snurfle 806 zinja 802 abacad 004 snurfle 772 zinja 116 abacad 752 snurfle 091 zinja 649 26 Computer Science Department, Passwords

Policy Choices • Password Eligibility • Failover • Per user policies • Per sweetword policies 27 Computer Science Department, Passwords

Password Eligibility Some words may be ineligible as passwords because they violate one or more policies regarding eligibility, such as: � password syntax � dictionary words � password re-use � most common passwords � popular passwords 28 Computer Science Department, Passwords

Failover � The computer system can be designed to have a “failover” mode so that logins can proceed more-or-less as usual even if the honeychecker has failed or become unreachable. In failover mode, honeywords are temporarily promoted to become acceptable passwords; this prevents denial-of-service attacks resulting from attack on the honeychecker or the communications between the system and the honeychecker 29 Computer Science Department, Passwords

Per-user policies � Use honeypot accounts additionally to honeywords. Such accounts can help identify theft of F and distinguish over a Do. S attack. Which accounts are honeypot accounts would be known only to the honeychecker. Selective alarms � It may be helpful raise an alarm if there are honeyword hits against administrator accounts or other particularly sensitive accounts, even at the risk of extra sensitivity to Do. S attacks. 30 Computer Science Department, Passwords

Per-sweetword policies � The “Set: i, j” command to the honeychecker could have an optional third argument a, i, j, which says what action to take if a “Check: i, j” command is later issued. � Different actions � “Raise silent alarm” , “Allow login”, “Allow only”, etc. . . for single login � k different entries for a given user, with potentially k different policies, one per sweetword. 31 Computer Science Department, Passwords

Attacks Possible attacks against the methods proposed : General password guessing, Targeted password guessing, Attacking the Honeychecker, Likelihood Attack , Denial-of-service, Multiple systems 32 Computer Science Department, Passwords

General password guessing (-) Legacy-UI methods (+) Methods requiring users to choose uncommon passwords (+) Modified-UI methods ( take-a-tail ) 33 Computer Science Department, Passwords

Targeted password guessing � Personal information about a user could help an adversary distinguish the user’s password from his honeywords. � It is often feasible to deanonymize users (-) chaffing-with-a-password-model 34 Computer Science Department, Passwords

Attacking the Honeychecker � The adversary may decide to attack the honeychecker or its communications with the computer system. � authenticate communications to and from the honeychecker � By disabling communications between the computer system and the honeychecker, the adversary can cause a failover system either disallows login or � takes the risk of temporarily allowing login based on a honeyword and buffering messages for later processing by the honeychecker. � 35 Computer Science Department, Passwords

Likelihood Attack (-) Approach based on generating honeywords using a probabilistic model � In this context, a user might be well advised either to a) b) 36 choose a very strong password that the adversary will never crack, or choose a password of the sort that the honeyword generator might generate. Computer Science Department, Passwords

Denial-of-service � Adversary has not compromised the password file F, but nonetheless knows a user’s password can feasibly submit one of the user’s honeywords. � Mitigating Do. S attacks. � 37 to limit the impact of a Do. S attacks against chaffing-by-tweaking, one possible approach is to select a relatively small set of honeywords randomly from a larger class of possible sweetwords. Computer Science Department, Passwords

Multiple systems � Users commonly employ the same password across different systems � an adversary might seek an advantage in password those systems. � Two such forms of attack an “intersection” attack and � a “sweetword-submission” attack. � 38 Computer Science Department, Passwords

Intersection attack � User has the same password but distinct sets of honeywords on systems A and B, adversary that compromises the two password files learns the user’s password from their intersection. � If management of multiple systems is of concern, � take-a-tail generation approach � ensures that a user has different passwords on different systems is achieved without coordination between the systems 39 Computer Science Department, Passwords

Sweetword submission attack � User has the same password on systems A and B the adversary that compromises the password file on system A can submit the user’s sweetwords as password guesses to system B without special risk of detection to system B, system A’s honeywords will be indistinguishable from any other incorrect passwords. � “Take-a-tail” can also provide resistance to sweetword- submission attacks. 40 Computer Science Department, Passwords

Evaluation of methods 44 Computer Science Department, Passwords

Flatness � Let z denote the adversary’s expected probability of guessing the sugarword. � this probability is taken over the user’s choice of password pi, the generation procedure Gen(k; pi), and any randomization used by the adversary to produce its guess j. z = 1/k, since an adversary can with probability 1/k merely by guessing j at random. � A honeyword generation method is“ϵ-flat” for a parameter the maximum value over all adversaries of the adversary’s winning probability z is ϵ. � If the generation procedure is as flat as possible we say it is “perfectly flat”. 45 Computer Science Department, Passwords ϵ if

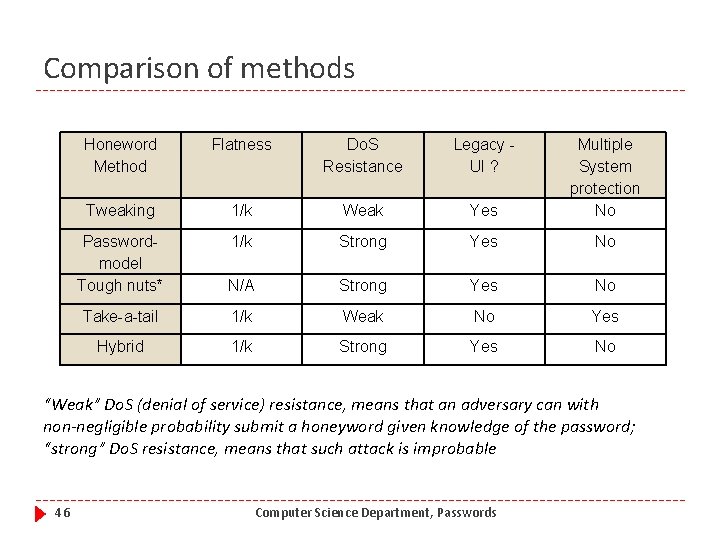
Comparison of methods Honeword Method Flatness Do. S Resistance Legacy UI ? Tweaking 1/k Weak Yes Multiple System protection No Passwordmodel Tough nuts* 1/k Strong Yes No N/A Strong Yes No Take-a-tail 1/k Weak No Yes Hybrid 1/k Strong Yes No “Weak” Do. S (denial of service) resistance, means that an adversary can with non-negligible probability submit a honeyword given knowledge of the password; “strong” Do. S resistance, means that such attack is improbable 46 Computer Science Department, Passwords

Conclusion 47 Computer Science Department, Passwords

48 Computer Science Department, Passwords

End of Part I 49 Computer Science Department, Passwords