CS 519 Advanced Operating Systems Handling InterruptExceptions Yeongjin
















- Slides: 27

CS 519 Advanced Operating Systems Handling Interrupt/Exceptions Yeongjin Jang 01/29/19

Exam 1 on 2/7 • In-class, one and half hours • Questions on high-level concepts • • • How is JOS booted? How segmentation works? How page table works? How OS ‘traps’ executions? How does an OS process system call from user-level apps?

Exam 1 on 2/7 • In-class, one and half hours • Questions on OS (JOS) implementation details • • • How can you enable the ‘protected mode’? How can you enable paging? How JOS can access physical address? How can you set virtual address/flags to page table? Which register holds the address of page directory? • Is that virtual or physical? • How can you set descriptor tables? • GDT • IDT • Memory permission quiz • Kernel RW / User – • Kernel R- / User –W is this possible? • etc…

About Lab 3 Deadline • Part A: 1/31/2019 • Soft deadline, will not consume your tokens if not submitted • Part B: 2/8/2019 • Friday 11: 59 pm, 1 day shifted because we have exam on 2/7 • Hard Deadline

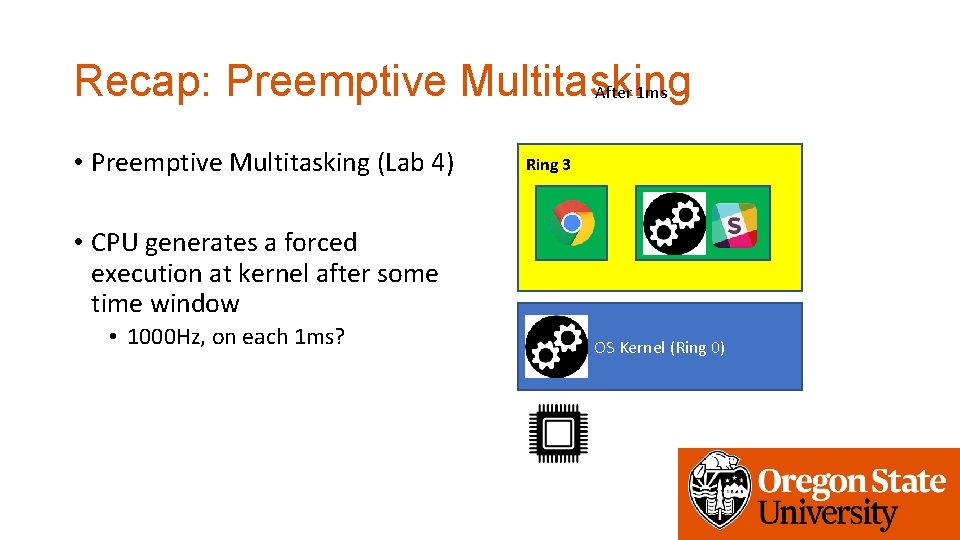
Recap: Preemptive Multitasking After 1 ms • Preemptive Multitasking (Lab 4) Ring 3 • CPU generates a forced execution at kernel after some time window • 1000 Hz, on each 1 ms? OS Kernel (Ring 0)

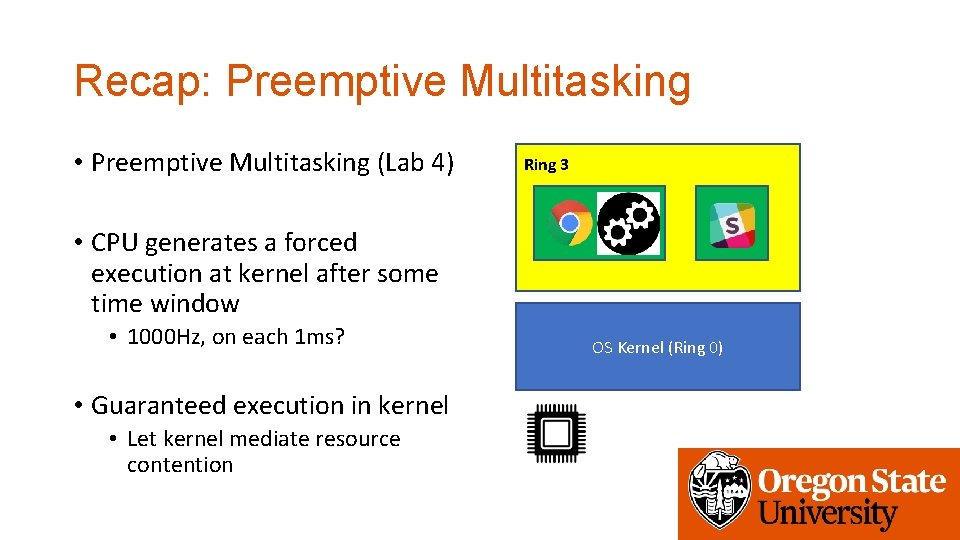
Recap: Preemptive Multitasking • Preemptive Multitasking (Lab 4) Ring 3 • CPU generates a forced execution at kernel after some time window • 1000 Hz, on each 1 ms? • Guaranteed execution in kernel • Let kernel mediate resource contention OS Kernel (Ring 0)

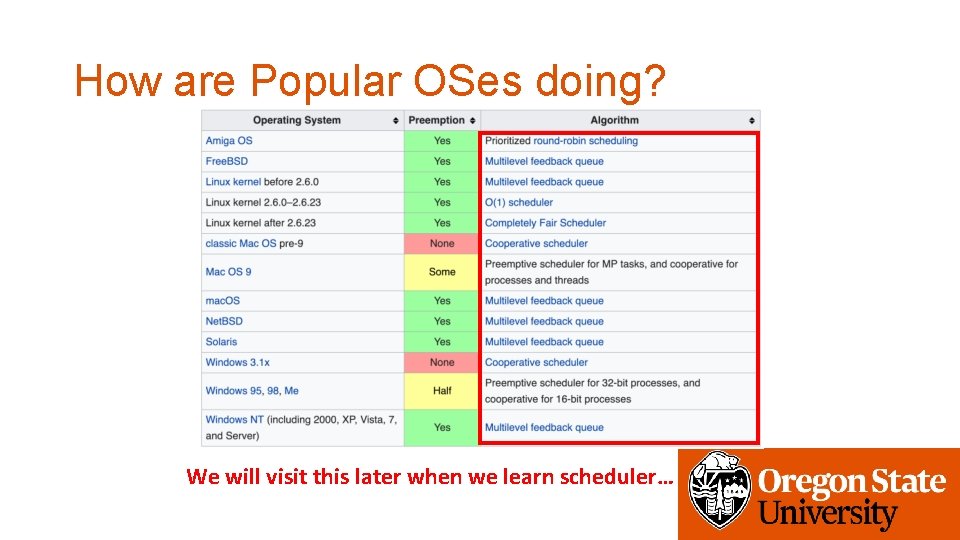
How are Popular OSes doing? We will visit this later when we learn scheduler…

Interrupt • Asynchronous (can happen at any time of execution) • Mostly caused by external hardware • Read • https: //en. wikipedia. org/wiki/Intel_8259 • https: //en. wikipedia. org/wiki/Advanced_Programmable_Interrupt_Controller • Software interrupt • int $0 x 30 system call in JOS

Exceptions • Synchronous (an execution of an instruction can generate this) • Faults • Faulting instruction has not executed (e. g. , page fault) • Resume the execution after handling the fault • Trapping instruction has been executed (e. g. , breakpoint) • Will not resume the trap instruction (if so, we will trap indefinitely…) • Abort • No way to recover (triple fault, etc. )

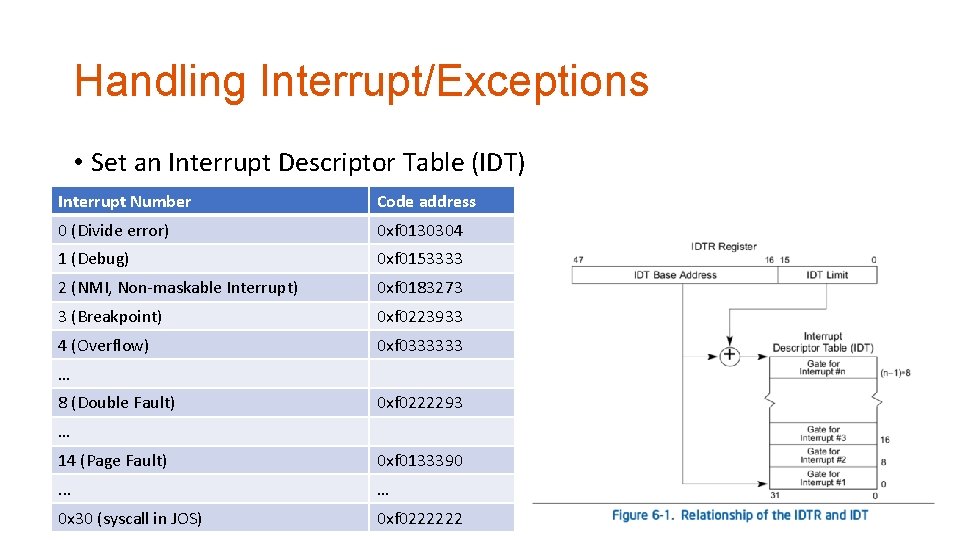
Handling Interrupt/Exceptions • Set an Interrupt Descriptor Table (IDT) Interrupt Number Code address 0 (Divide error) 0 xf 0130304 1 (Debug) 0 xf 0153333 2 (NMI, Non-maskable Interrupt) 0 xf 0183273 3 (Breakpoint) 0 xf 0223933 4 (Overflow) 0 xf 0333333 … 8 (Double Fault) 0 xf 0222293 … 14 (Page Fault) 0 xf 0133390 . . . … 0 x 30 (syscall in JOS) 0 xf 0222222

Interrupt/Exception Handler • Processing Interrupt/Exception • Usually disable interrupt on handling other interrupts • • • What if an interrupt comes while you are handling one of interrupt and another new interrupt comes on handling the 2 nd 3 rd 4 th … No execution!

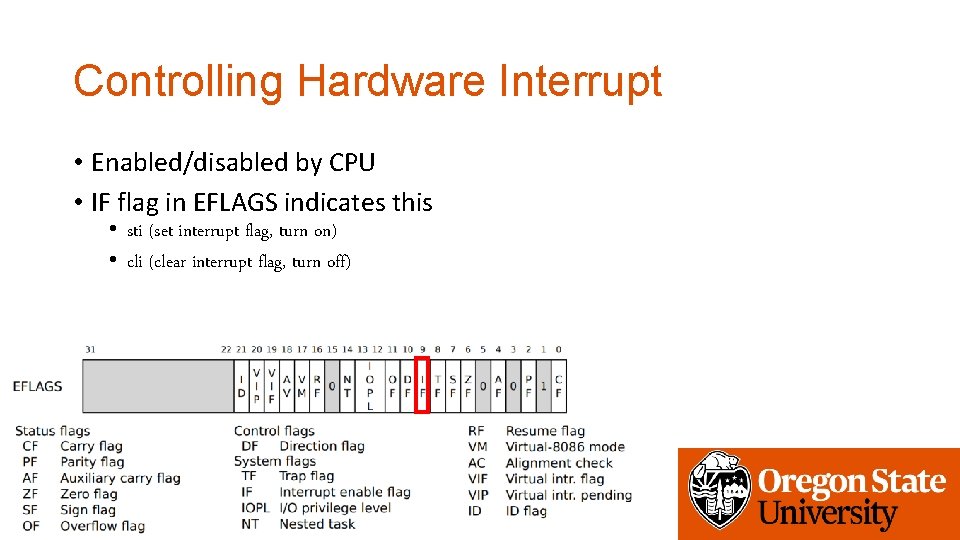
Controlling Hardware Interrupt • Enabled/disabled by CPU • IF flag in EFLAGS indicates this • sti (set interrupt flag, turn on) • cli (clear interrupt flag, turn off)

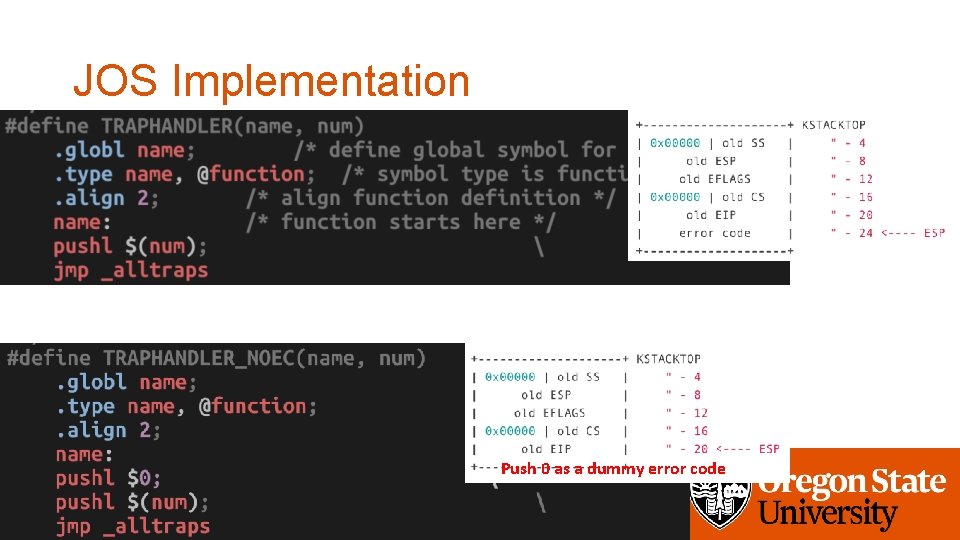
How dos JOS Handle Interrupt? • You will setup an interrupt gate per each interrupt/exception • Using a MACRO defined in trapentry. S • TRAPHANDLER(name, num) • TRAPHANDLER_NOEC(name, num) • Gate generated by this macro should call • trap() in kern/trap. c • Implement this in _alltraps:

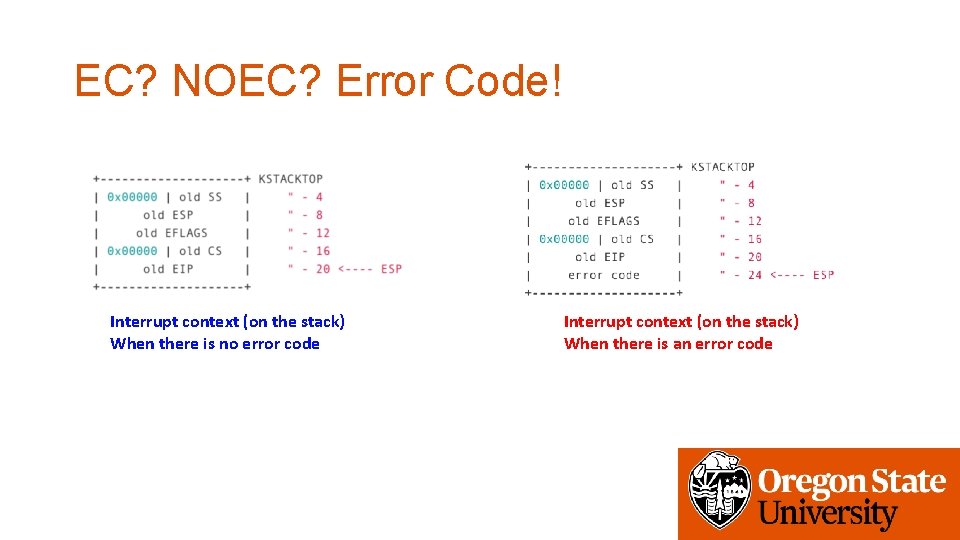
EC? NOEC? Error Code! Interrupt context (on the stack) When there is no error code Interrupt context (on the stack) When there is an error code

JOS Implementation Push 0 as a dummy error code

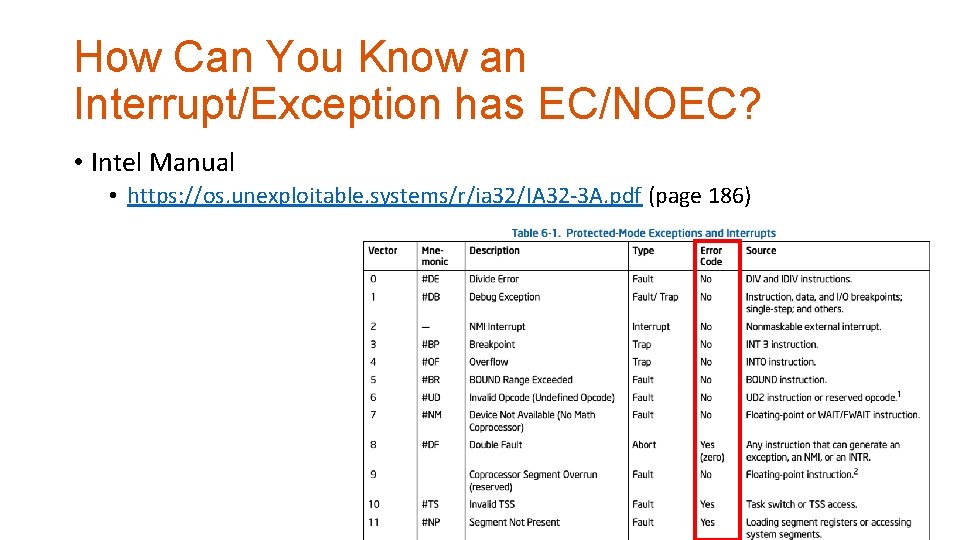
How Can You Know an Interrupt/Exception has EC/NOEC? • Intel Manual • https: //os. unexploitable. systems/r/ia 32/IA 32 -3 A. pdf (page 186)

JOS Interrupt Handling • Interrupt arrives to CPU! • Call an interrupt gate (setup at trap_init() in kern/trap. c) • Call _alltraps (in kern/trapentry. S) • Call trap() in kern/trap. c • Call trap_dispatch() in kern/trap. c

In trap_dispatch() • All Interrupt/Exceptions comes to this function • Check trap number from tf->trapno • Handle the following interrupts • T_PGFLT (page fault, 14) • T_BRKPT (breakpoint, 3) • T_SYSCALL (system call, 48)

System Call • An API of an OS for system services • User-level Application calls functions in kernel • • Open Read Write Exec Send Recv Socket Etc…

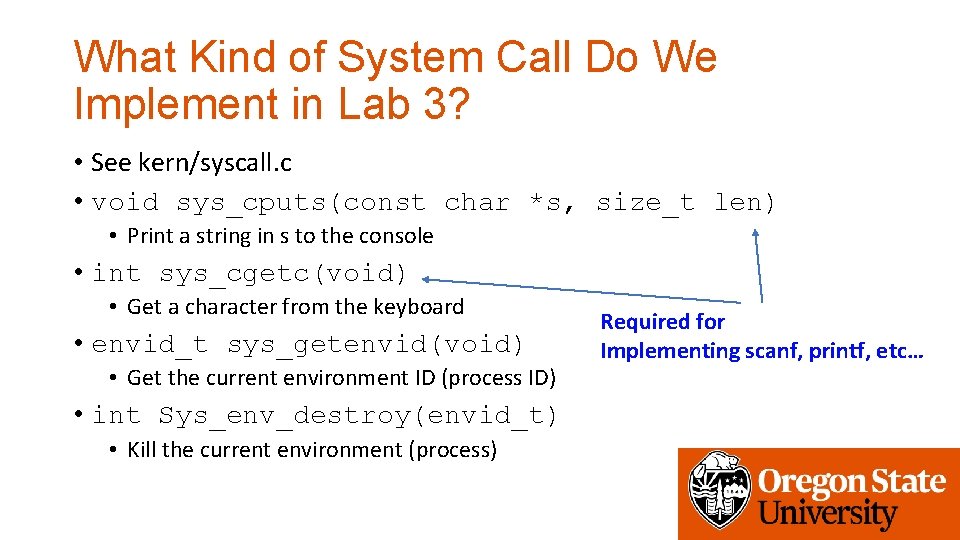
What Kind of System Call Do We Implement in Lab 3? • See kern/syscall. c • void sys_cputs(const char *s, size_t len) • Print a string in s to the console • int sys_cgetc(void) • Get a character from the keyboard • envid_t sys_getenvid(void) • Get the current environment ID (process ID) • int Sys_env_destroy(envid_t) • Kill the current environment (process) Required for Implementing scanf, printf, etc…

How Can We Pass Arguments to System Calls? • In JOS • • • eax = system call number edx = 1 st argument ecx = 2 nd argument ebx = 3 rd argument edi = 4 th argument esi = 5 th argument • You should get those values from • struct Trapframe *tf Will add more as our lab implementation progresses

How Can We Pass Arguments to System Calls? • In Linux x 86 (32 -bit) • • • eax = system call number ebx = 1 st argument ecx = 2 nd argument edx = 3 rd argument esi = 4 th argument edi = 5 th argument • See table • https: //syscalls. kernelgrok. com/

How Can We Invoke a System Call? • Set all arguments in the registers • Order: edx ecx ebx edi esi • int $0 x 30 (in JOS) • Software interrupt 48 • int $0 x 80 (in 32 bit Linux) • Software interrupt 128

System Call Handling Routine (User) • User calls a function • cprintf -> calls sys_cputs() • sys_cputs() at user code will call syscall() (lib/syscall. c) • This syscall() is at lib/syscall. c • Set args in the register and then • int $0 x 30 • Now kernel execution starts…

System Call Handling Routine (Kernel) • CPU gets software interrupt • TRAPHANDLER_NOEC(T_SYSCALL…) • _alltraps() • trap_dispatch() • Get registers that store arguments from struct Trapframe *tf • Call syscall() using those registers • This syscall() is at kern/syscall. c

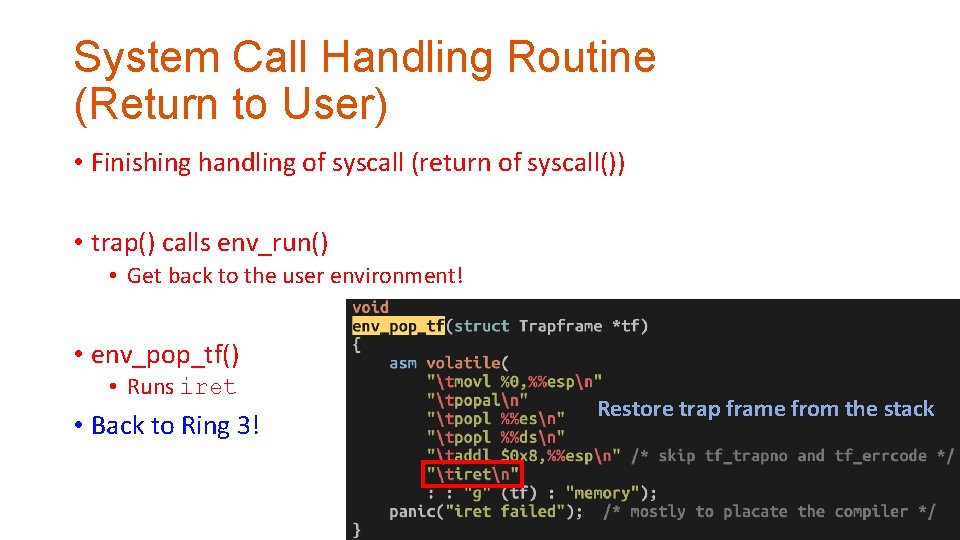
System Call Handling Routine (Return to User) • Finishing handling of syscall (return of syscall()) • trap() calls env_run() • Get back to the user environment! • env_pop_tf() • Runs iret • Back to Ring 3! Restore trap frame from the stack

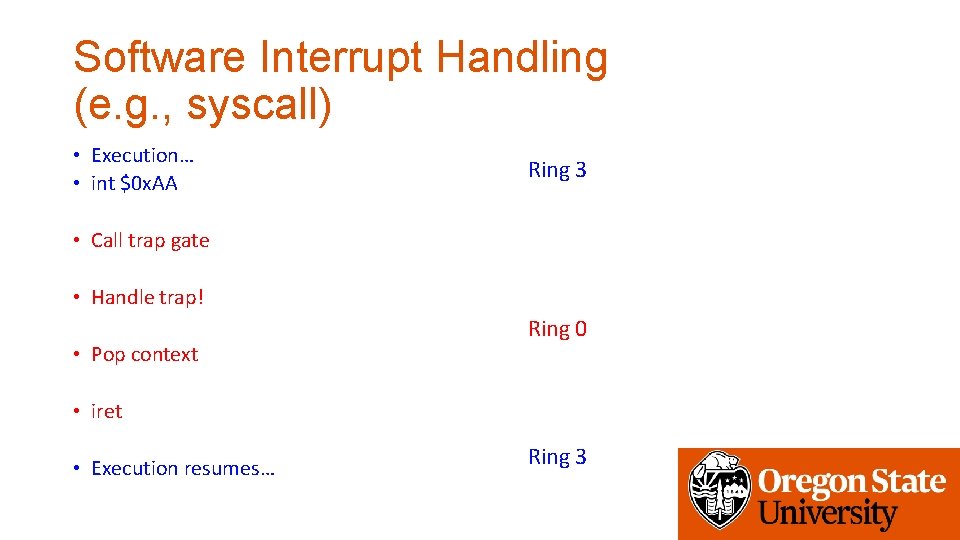
Software Interrupt Handling (e. g. , syscall) • Execution… • int $0 x. AA Ring 3 • Call trap gate • Handle trap! • Pop context Ring 0 • iret • Execution resumes… Ring 3