CS 414 Multimedia Systems Design Lecture 20 Multimedia





- Slides: 18

CS 414 – Multimedia Systems Design Lecture 20 – Multimedia Transport Subsystem (Part 3) Klara Nahrstedt Spring 2014 CS 414 - Spring 2014

Administrative MP 1, HW 1, Midterm grades should be in by Wednesday/Thursday this week n MP 2 posting by the end of this week n CS 414 - Spring 2014

Transmission Phase Multimedia Streaming Protocol n Classification of Packets/Frames ¨ Identification of packets/frames ¨ Marking of Packets/Frames n Queueing ¨ Rate Control ¨ Error Control n Policies to drive classification and queueing ¨ Shaping and policing CS 414 - Spring 2014

Packet/Frame Classification Identification of packets/frames in the network n Three types of identifications n ¨ Access n control lists IP address, port ¨ Application source classification Video streaming n Voice over IP n Call signaling n Best effort http traffic n ¨ Switch ports CS 414 - Spring 2014

Classification of Multimedia Sources n Strongly Regular vs Weakly Regular traffic Strongly regular stream – has packets of the same size (e. g. , audio stream) ¨ Weakly regular streams – has packets of different sizes within one stream (e. g. , MPEG stream) ¨ n Strongly Periodic vs Weakly Periodic traffic Strongly periodic stream – when periods between packets/frames within a stream are the same ¨ Weakly periodic stream – when periods between packets within one stream deviate by x time units ¨ n Isochronous vs Synchronous vs Asynchronous Traffic n n n Isochronous traffic – packets have end-to-end bound and jitter bound Synchronous traffic – packets have end-to-end bound, but no jitter bound Asynchronous traffic – don’t have any bounds CSpackets 414 - Spring 2014

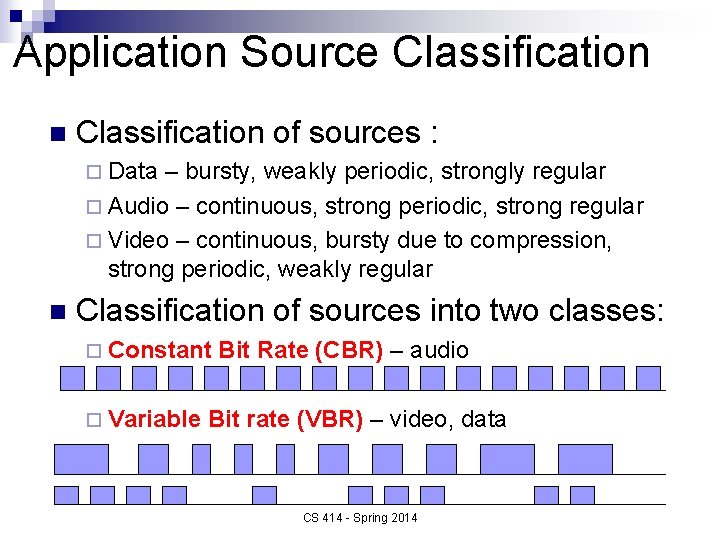
Application Source Classification n Classification of sources : ¨ Data – bursty, weakly periodic, strongly regular ¨ Audio – continuous, strong periodic, strong regular ¨ Video – continuous, bursty due to compression, strong periodic, weakly regular n Classification of sources into two classes: ¨ Constant ¨ Variable Bit Rate (CBR) – audio Bit rate (VBR) – video, data CS 414 - Spring 2014

Marking of Packets n Marking is done close to source flow ¨ Get differentiated treatment ¨ E. g in Layer 3 IP headers ¨ Hardware-based Qo. S Marking at high-speeds to keep up with speed of switch CS 414 - Spring 2014

Policies – Traffic Shaping and Policing n n n In Packet Network, admission control, reservation is not sufficient to provide Qo. S guarantees Need traffic shaping at the entry to network and within network Traffic shaping algorithm ¨ Decides how packets will be sent into the network , hence regulates traffic ¨ Decides whether to accept a flow’s data ¨ Polices flows CS 414 - Spring 2014

Purpose of Traffic Shaping n Traffic shape ¨A way of a flow to describe its traffic to the network Based on traffic shape, network manager (s) can determine if flow should be admitted into the network n Given traffic shape, network manager(s) can periodically monitor flow’s traffic n CS 414 - Spring 2014

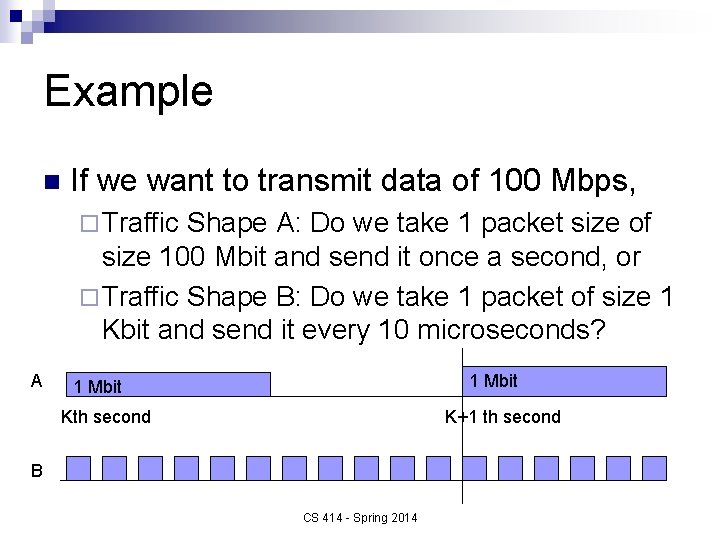
Example n If we want to transmit data of 100 Mbps, ¨ Traffic Shape A: Do we take 1 packet size of size 100 Mbit and send it once a second, or ¨ Traffic Shape B: Do we take 1 packet of size 1 Kbit and send it every 10 microseconds? A 1 Mbit Kth second K+1 th second B CS 414 - Spring 2014

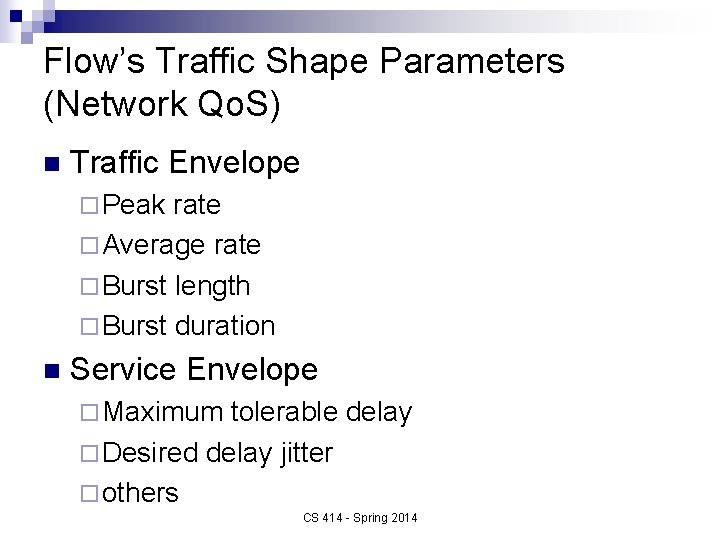
Flow’s Traffic Shape Parameters (Network Qo. S) n Traffic Envelope ¨ Peak rate ¨ Average rate ¨ Burst length ¨ Burst duration n Service Envelope ¨ Maximum tolerable delay ¨ Desired delay jitter ¨ others CS 414 - Spring 2014

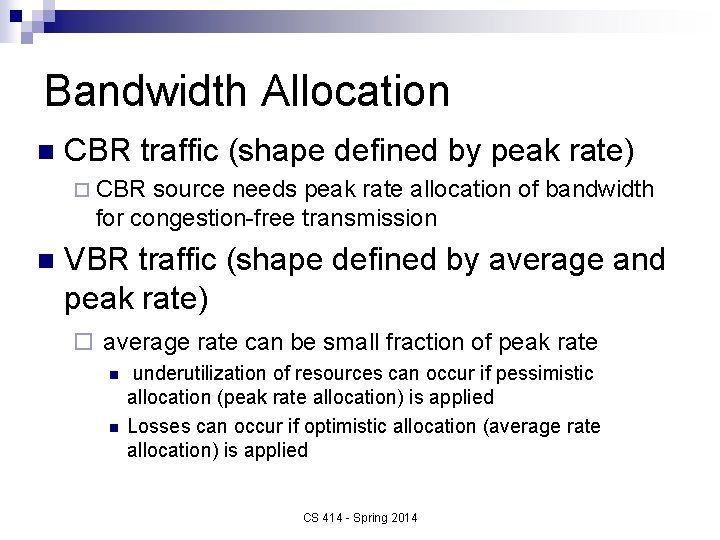
Bandwidth Allocation n CBR traffic (shape defined by peak rate) ¨ CBR source needs peak rate allocation of bandwidth for congestion-free transmission n VBR traffic (shape defined by average and peak rate) ¨ average rate can be small fraction of peak rate n n underutilization of resources can occur if pessimistic allocation (peak rate allocation) is applied Losses can occur if optimistic allocation (average rate allocation) is applied CS 414 - Spring 2014

Isochronous Traffic Shaping (Simple Leaky Bucket Traffic Shaper) n Developed by Jon Turner, 1986 (Washington University, St. Louis) CS 414 - Spring 2014

Example n Consider for audio flow, size of the bucket ¨ β = 16 Kbytes Packet size = 1 Kbytes (one can accumulate burst up to 16 packets in the bucket) ¨ Regulator’s rate ρ = 8 packets per second, or 8 KBps or 64 Kbps ¨ n Consider video flow, size of bucket ¨ β = 400 Kbytes ¨ Packet size = 40 Kbytes (burst of 10 packets) ¨ Regulator’s rate ρ = 5 packets per second, 200 KBps, 1600 Kbps CS 414 - Spring 2014

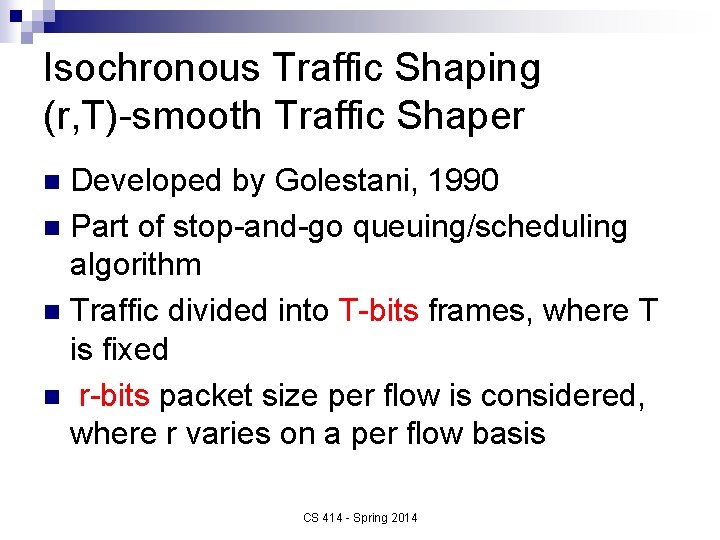
Isochronous Traffic Shaping (r, T)-smooth Traffic Shaper Developed by Golestani, 1990 n Part of stop-and-go queuing/scheduling algorithm n Traffic divided into T-bits frames, where T is fixed n r-bits packet size per flow is considered, where r varies on a per flow basis n CS 414 - Spring 2014

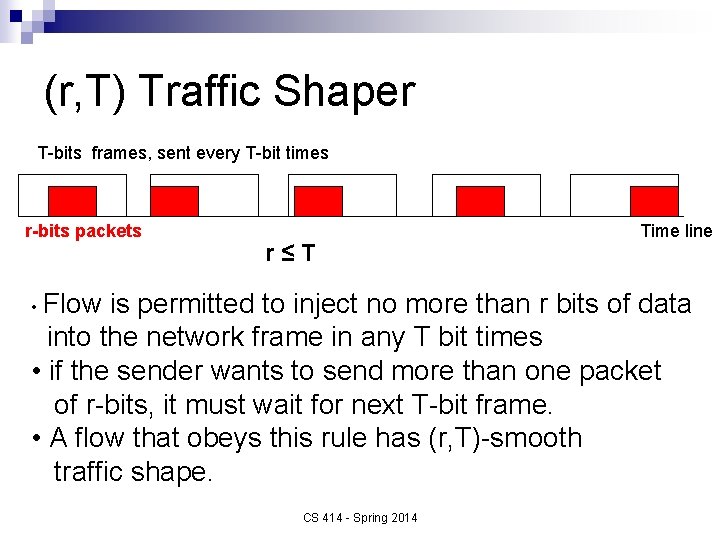
(r, T) Traffic Shaper T-bits frames, sent every T-bit times r-bits packets r≤T • Flow Time line is permitted to inject no more than r bits of data into the network frame in any T bit times • if the sender wants to send more than one packet of r-bits, it must wait for next T-bit frame. • A flow that obeys this rule has (r, T)-smooth traffic shape. CS 414 - Spring 2014

Comparison • It is relaxed from the simple leaky bucket traffic shaper because Rather than sending one packet of size c every 1/ρ time units, (in simple leaky bucket ) • The flow can send c*k bits every 1/ρ time units , where k is T-bits times within the period 1/ρ • 1/ρ K=2 CS 414 - Spring 2014

Conclusion Traffic Shaping happens at the entry to the network n It is a very important function to regular and police traffic at the edges to avoid huge bursts coming into the network n CS 414 - Spring 2014