CS 155 Computer and Network Security Programming Project















![TCP Flags n Synchronize flag [SYN] n n Acknowledgement flag [ACK] n n Used TCP Flags n Synchronize flag [SYN] n n Acknowledgement flag [ACK] n n Used](https://slidetodoc.com/presentation_image_h/a1e0d860586b4bd8835fd102050c6d21/image-25.jpg)
![TCP Flags (2) n Push flag [PSH] n n Do not buffer data on TCP Flags (2) n Push flag [PSH] n n Do not buffer data on](https://slidetodoc.com/presentation_image_h/a1e0d860586b4bd8835fd102050c6d21/image-26.jpg)
- Slides: 28

CS 155: Computer and Network Security Programming Project 3 – Spring 2008 Craig Gentry, Naef Imam, Arnab Roy {cgentry, nimam, arnab} @stanford. edu Thanks to Arpit Aggarwal and Elizabeth Stenson

Project Overview 1) 2) Learn to examine network packets to obtain useful information Implement a router that performs a simple scan detection

Part 1: Packet traces n We will use Wireshark to look at network packets. n n Available at: http: //www. wireshark. org/ Available for most platforms

Features useful for the project n n n Individual Packet info Filtering Following TCP/UDP streams String search For the 2 nd part of the project you will need to capture network packets as well

Part 2 Scan Detection

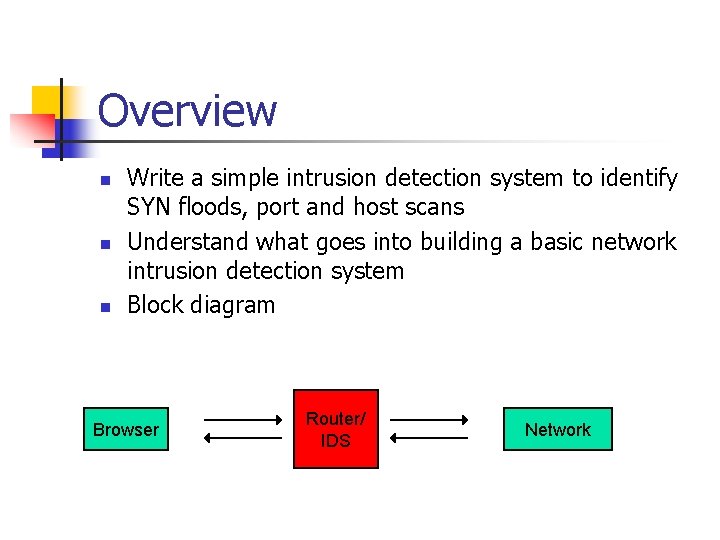
Overview n n n Write a simple intrusion detection system to identify SYN floods, port and host scans Understand what goes into building a basic network intrusion detection system Block diagram Browser Router/ IDS Network

Setup n n We’ll be using a VNS system Sample topology and Routing table Sample Routing table 192. 168. 131. 81 0. 0 192. 168. 131. 81 172. 24. 74. 17 255 eth 1 0. 0 eth 0

Setup(2) n n process_ip_packets() in process_ip. c is called for each IP packet protocol_headers. h and Network Sorcery website are good sources

SYN Floods n n n SYN Floods are Denial of Service attack used to make certain services unavailable on the target machine Attacker sets up numerous connections to victim machine using specific port When a SYN packet is received, the victim allocates resources to this new connection – since these resources are finite, a large number of connections will make the port on the target unusable

Port Scans n Port scans are used by attackers to see what ports and services are running on target machines n n n E. g. use port scans to find that victim machine is running the notorious sendmail program! Consist of any packet that would generate a response from a receiver – ICMP echo requests, TCP packets (including SYN Packets – Note the difference from SYN Flood!) These packets are sent to large number of ports on a machine with the aim of finding processes and possible open ports. Often they get –ve responses.

Host Scans n Similar methodology to port scans. Just does it over a large number of machines in the and checks them for the same open port

Assumptions n n Clients respond to data packets part of established flow You’re only working with TCP, UDP and ICMP Echo packets

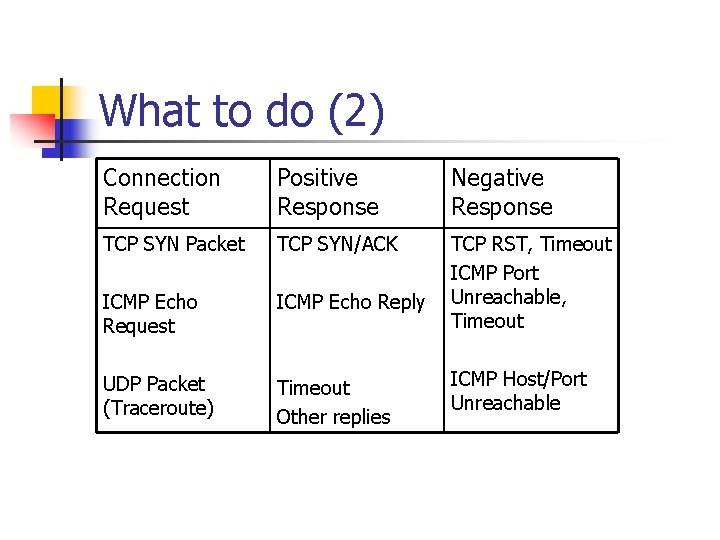
What to do n n We are only implementing Port Scans Explain in your README, how you will expand your program to track host scans and SYN Floods, incl. discussion about various cases. You do not need to implement them. (Note) Track number of connection requests vs. Positive Responses for each originating host If this ratio exceeds 3 to 1, your router must issue a warning. (Note: print them to a file called scan_warning) n n source ip<tab>SCANNING For each negative response received (not timeouts) source ip<tab>NEG<tab>TYPE (where type can be RST, ICMP_UNREACH)

What to do (2) Connection Request Positive Response Negative Response TCP SYN Packet TCP SYN/ACK ICMP Echo Request ICMP Echo Reply TCP RST, Timeout ICMP Port Unreachable, Timeout UDP Packet (Traceroute) Timeout Other replies ICMP Host/Port Unreachable

Considerations n Timeouts n n n Between Packets – 1 second ( to make sure packet bursts don’t get unduly noted) Keepalive for each host – 30 seconds No false positives n Consider cases like a buggy program making requests with –ve responses to a single port

Wrapup n The hard part is figuring out how to parse the various layers of headers. n You can find the header definitions at: n n Ethernet: /usr/include/net/ethernet. h IP: /usr/include/netinet/ip. h TCP: /usr/include/netinet/tcp. h The harder part is to create data structures to keep state info.

Wrapup(2) n This whole assignment shouldn’t take more than a couple hundred lines of code n n n However, it requires a good understanding of what’s happening on the network The programs seem simple, but they can take more time than anticipated Enjoy yourself – this is fun stuff!

Goals of the assignment n n Get some hands-on experience attacking and defending networks DON’T end up in jail n Never test your code outside of the VNS environment!

Good luck!

Addendum

Quick TCP/IP Review

TCP/IP Overview n n Basic knowledge of TCP/IP and DDOS with SYN Floods is required as discussed in class We assume a basic knowledge on the level of packets and ports n If you’re not that comfortable with this, stop by office hours

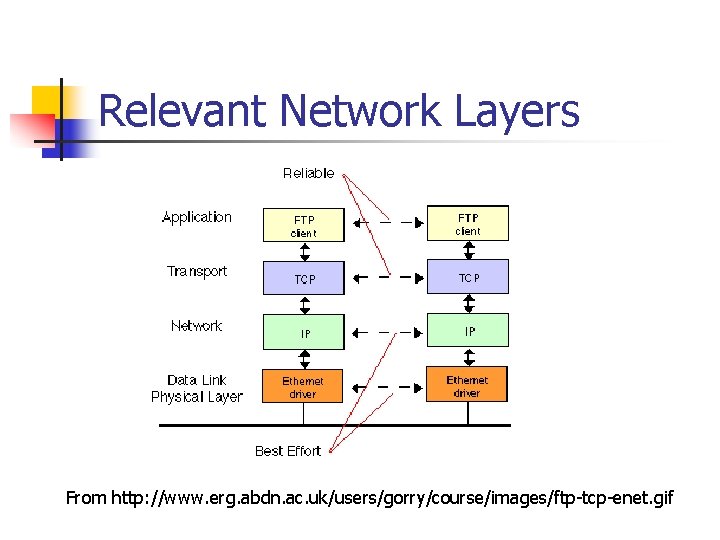
Relevant Network Layers From http: //www. erg. abdn. ac. uk/users/gorry/course/images/ftp-tcp-enet. gif

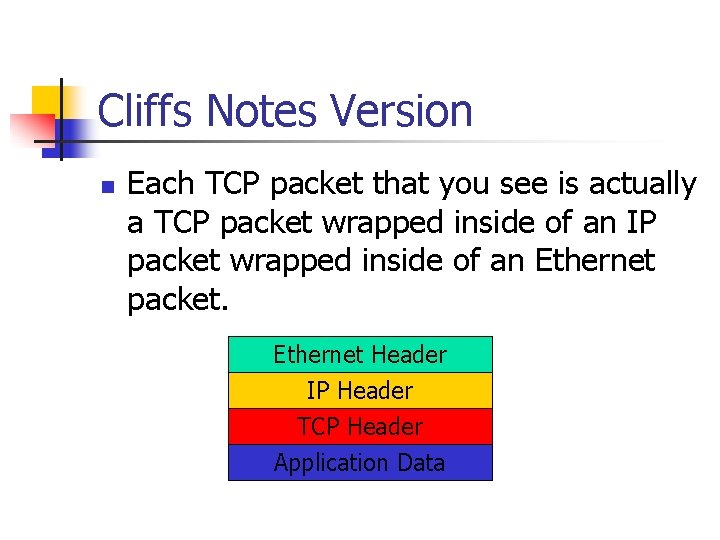
Cliffs Notes Version n Each TCP packet that you see is actually a TCP packet wrapped inside of an IP packet wrapped inside of an Ethernet packet. Ethernet Header IP Header TCP Header Application Data
![TCP Flags n Synchronize flag SYN n n Acknowledgement flag ACK n n Used TCP Flags n Synchronize flag [SYN] n n Acknowledgement flag [ACK] n n Used](https://slidetodoc.com/presentation_image_h/a1e0d860586b4bd8835fd102050c6d21/image-25.jpg)
TCP Flags n Synchronize flag [SYN] n n Acknowledgement flag [ACK] n n Used to initiate a TCP connection Used to confirm received data Finish flag [FIN] n Used to shut down the connection
![TCP Flags 2 n Push flag PSH n n Do not buffer data on TCP Flags (2) n Push flag [PSH] n n Do not buffer data on](https://slidetodoc.com/presentation_image_h/a1e0d860586b4bd8835fd102050c6d21/image-26.jpg)
TCP Flags (2) n Push flag [PSH] n n Do not buffer data on receiver side – send directly to application level Urgent flag [URG] n Used to signify data with a higher priority than the other traffic n n I. e Ctrl+C interrupt during an FTP transfer Reset flag [RST] n Tells receiver to tear down connection immediately

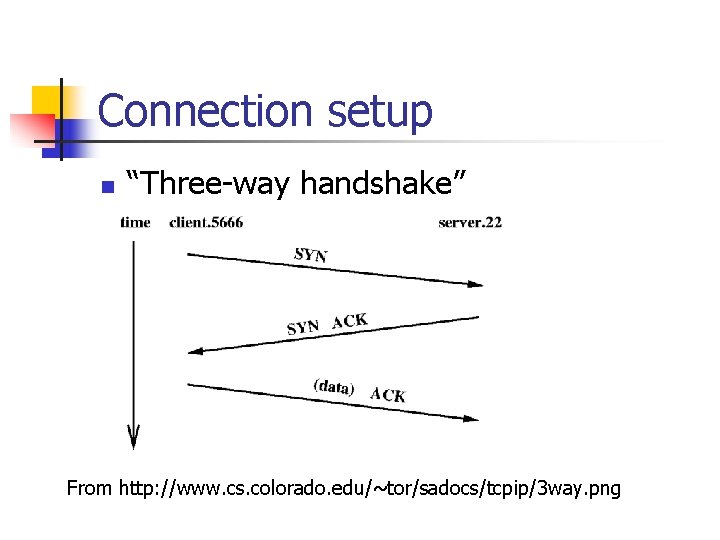
Connection setup n “Three-way handshake” From http: //www. cs. colorado. edu/~tor/sadocs/tcpip/3 way. png

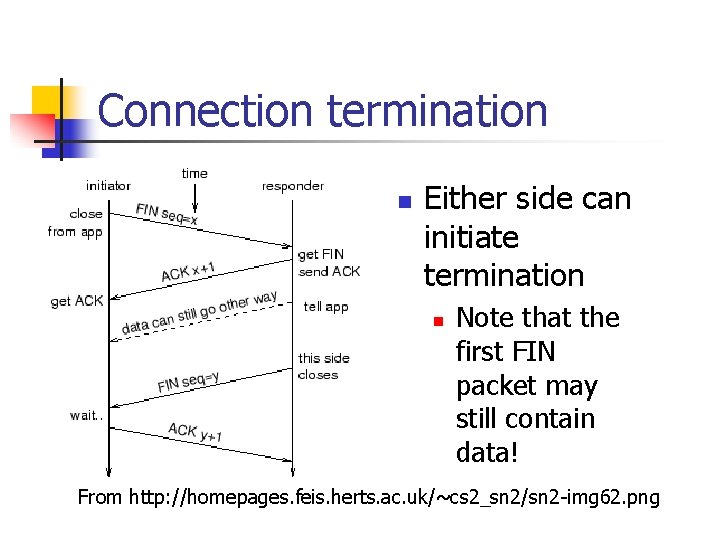
Connection termination n Either side can initiate termination n Note that the first FIN packet may still contain data! From http: //homepages. feis. herts. ac. uk/~cs 2_sn 2/sn 2 -img 62. png