Cryptography with Quantum Data Adam Smith Weizmann IPAM


![Some Things That Change • • • Unconditional key exchange [BB 84, …] Factoring Some Things That Change • • • Unconditional key exchange [BB 84, …] Factoring](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-3.jpg)




![Basic Feasibility Results (assuming broadcast) t=0 n/4 Perfect MPC [BGW, CCD] n/3 n/2 n Basic Feasibility Results (assuming broadcast) t=0 n/4 Perfect MPC [BGW, CCD] n/3 n/2 n](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-14.jpg)
![Basic Feasibility Results (assuming broadcast) • n/3 [CGS’ 02]: use error-correcting codes n n/2 Basic Feasibility Results (assuming broadcast) • n/3 [CGS’ 02]: use error-correcting codes n n/2](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-16.jpg)

![Authenticating Quantum Messages • How does Alice know it’s Bob? § • [BCGST] classical Authenticating Quantum Messages • How does Alice know it’s Bob? § • [BCGST] classical](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-22.jpg)
![Authenticating Quantum Messages [BCGST] Classical key k | i Ak(| i) Eve Alice • Authenticating Quantum Messages [BCGST] Classical key k | i Ak(| i) Eve Alice •](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-23.jpg)
![Approximate Codes [CGS’ 05] • Code “correcting” (n-1)/2 errors • Start with (n-1)/2 erasure-correcting Approximate Codes [CGS’ 05] • Code “correcting” (n-1)/2 errors • Start with (n-1)/2 erasure-correcting](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-24.jpg)
![Approximate Codes [CGS’ 05] • AQECC “correcting” (n-1)/2 errors § If any majority of Approximate Codes [CGS’ 05] • AQECC “correcting” (n-1)/2 errors § If any majority of](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-25.jpg)






- Slides: 38

Cryptography with Quantum Data Adam Smith Weizmann à IPAM à Penn State IPAM Workshop on Foundations of Cryptography November 14, 2006

Cryptography in a Quantum World • Landscape changes! § § § New features appear New difficulties arise Some key pieces unchanged • Needed: Tools and language for reasoning about quantum adversaries • The field is still very young § § § Some successes… … occasional mistakes Lots of questions! quantum thinkers needed Isaac Newton 1642 -1727 2
![Some Things That Change Unconditional key exchange BB 84 Factoring Some Things That Change • • • Unconditional key exchange [BB 84, …] Factoring](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-3.jpg)
Some Things That Change • • • Unconditional key exchange [BB 84, …] Factoring + DL broken [Sho] Weak 2 -party unconditional primitives § § • • Some multi-prover commitments insecure [CST] Some extractors fail vs quantum memory [IKW] § • • But some are OK [KMR] Some simulators for ZK proofs fail § • coin flipping [ATVY, Amb] string commitment [BCHLW] but new ones can sometimes be built[Wat] Bounded Storage Model more Powerful [DFSS] See survey talk on http: //theory. csail. mit. edu/~asmith 3

= incomplete and biased This talk: Salient Features (a partial • Multiparty Quantum Computing § § § • Parties hold quantum inputs Want to evaluate a quantum circuit Generalizes classical MPC Two Feasibility results § § • * list) Statistical MPQC , cheating minority à la [RB’ 89] Computational MPQC for arbitrary subsets à la [GMW’ 87] under non-standard assumption Along the way: § § § Some infeasibility results Authentication and Approximate Error-Correction ZK Proofs of Knowledge 4

This Talk • Basics of quantum computing • Multiparty Quantum Computing (MPQC) • Codes and Authentication • MPQC with a cheating minority • Beyond a faulty minority: 2 -party QC § ZK for quantum adversaries 5

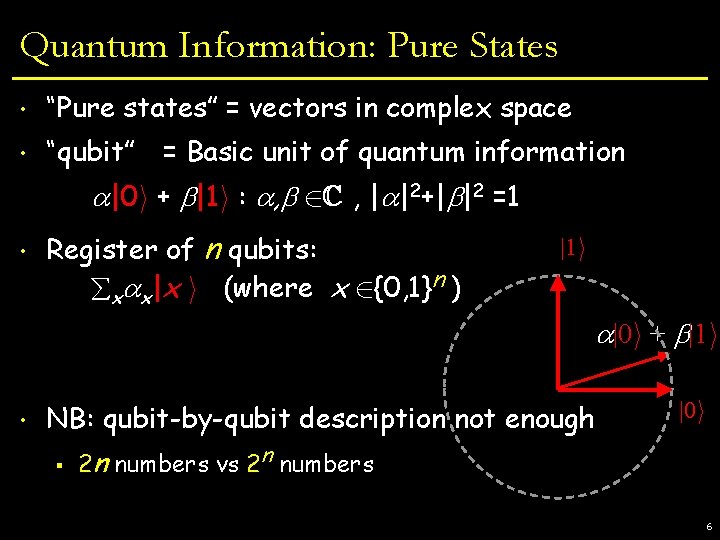
Quantum Information: Pure States • “Pure states” = vectors in complex space • “qubit” = Basic unit of quantum information |0 i + |1 i : , 2 C , | |2+| |2 =1 • Register of n qubits: x x|x i (where x 2{0, 1}n ) |1 i |0 i + |1 i • NB: qubit-by-qubit description not enough § |0 i 2 n numbers vs 2 n numbers 6

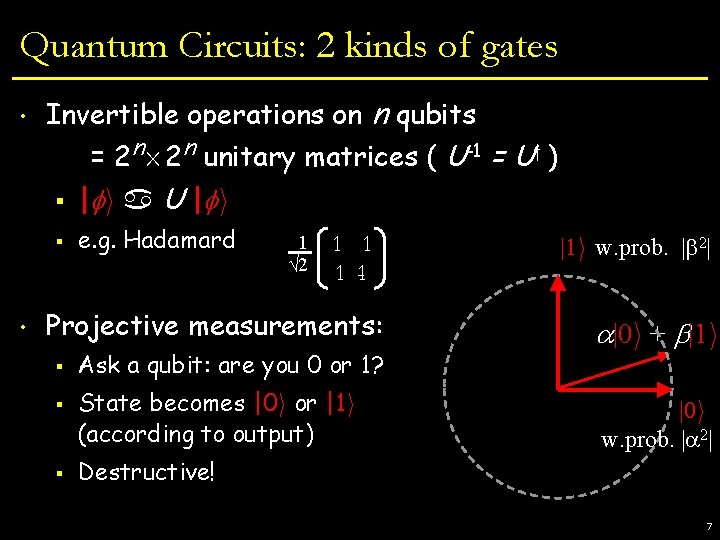
Quantum Circuits: 2 kinds of gates • • Invertible operations on n qubits = 2 n£ 2 n unitary matrices ( U-1 = Uy ) § | i U | i § e. g. Hadamard 1 √ 2. . 1 1 Projective measurements: § § § Ask a qubit: are you 0 or 1? State becomes |0 i or |1 i (according to output) |1 i w. prob. | 2| |0 i + |1 i |0 i w. prob. | 2| Destructive! 7

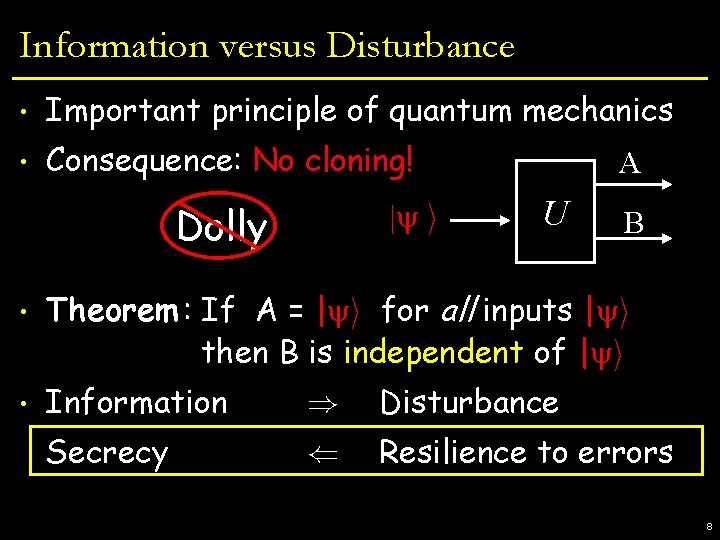
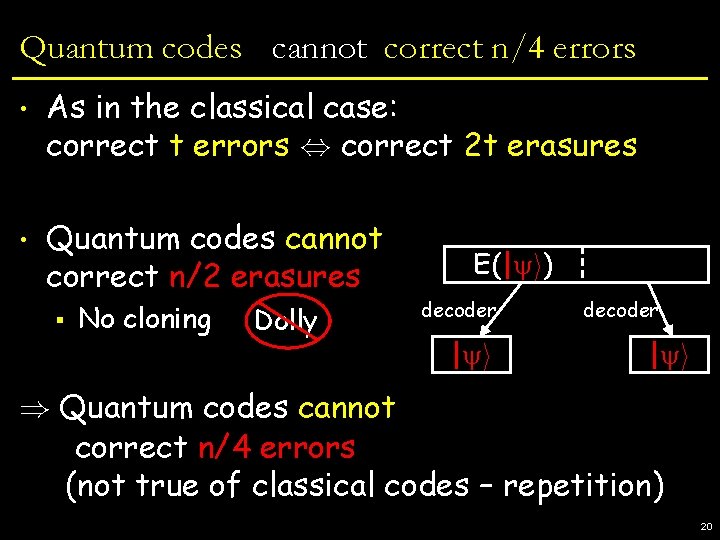
Information versus Disturbance • Important principle of quantum mechanics • Consequence: No cloning! Dolly | i A U B • Theorem : If A = | i for all inputs | i then B is independent of | i • Information ) Disturbance Secrecy ( Resilience to errors 8

This Talk • Basics of quantum computing • Multiparty Quantum Computing • Codes and Authentication • MPQC with a cheating minority • Beyond a faulty minority: 2 -party QC § ZK for quantum adversaries 9

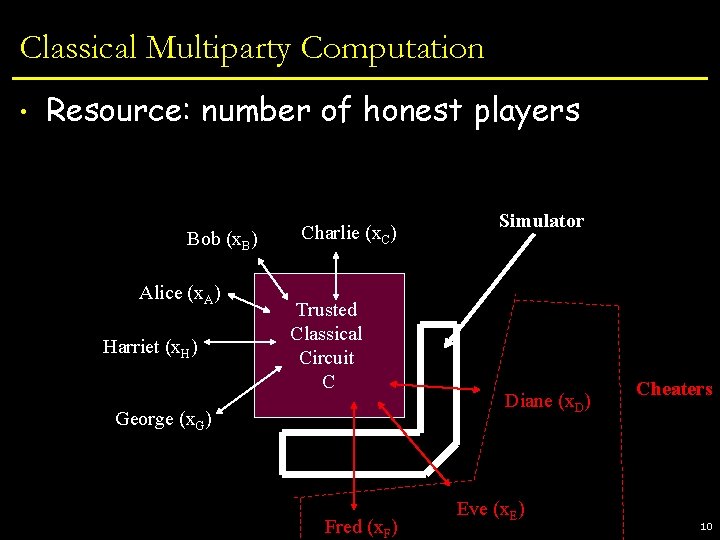
Classical Multiparty Computation • Resource: number of honest players Bob (x. B) Alice (x. A) Harriet (x. H) Charlie (x. C) Trusted Classical Circuit C George (x. G) Fred (x. F) Simulator Diane (x. D) Eve (x. E) Cheaters 10

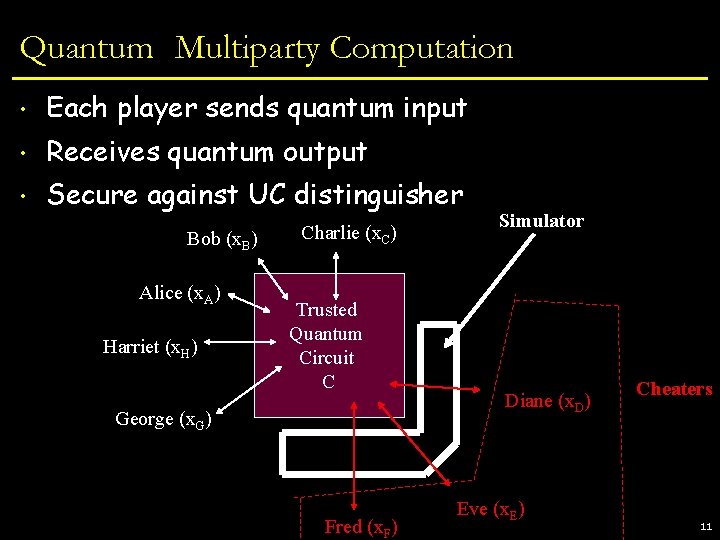
Quantum Multiparty Computation • Each player sends quantum input • Receives quantum output • Secure against UC distinguisher Bob (x. B) Alice (x. A) Harriet (x. H) Charlie (x. C) Trusted Quantum Circuit C George (x. G) Fred (x. F) Simulator Diane (x. D) Eve (x. E) Cheaters 11

Quantum Multiparty Computation • Each player sends quantum input • Receives quantum output • Secure against UC distinguisher • Generalizes Classical SFE • New techniques are needed § Players cannot keep copies of their input § Rewinding may not be possible § Dolly Need to operate on encoded / encrypted quantum states 12

Some Terminology • With Abort? § • • This talk: unfair abort (based on cheaters’ output) Perfect / statistical security Computational security 13
![Basic Feasibility Results assuming broadcast t0 n4 Perfect MPC BGW CCD n3 n2 n Basic Feasibility Results (assuming broadcast) t=0 n/4 Perfect MPC [BGW, CCD] n/3 n/2 n](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-14.jpg)
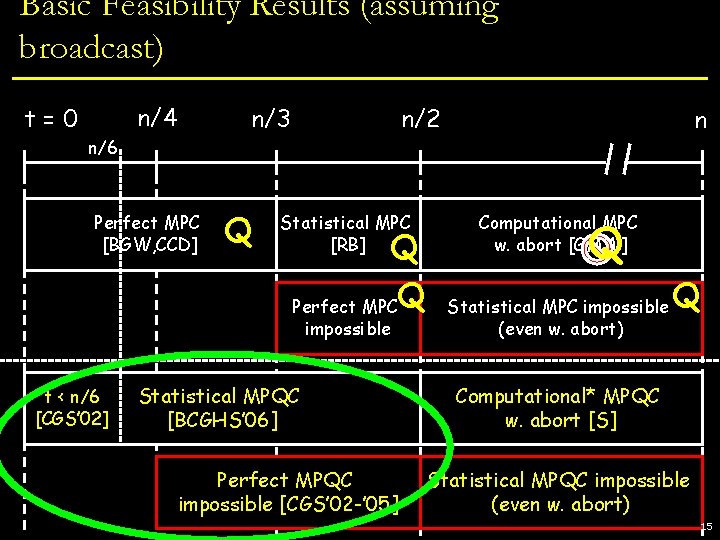
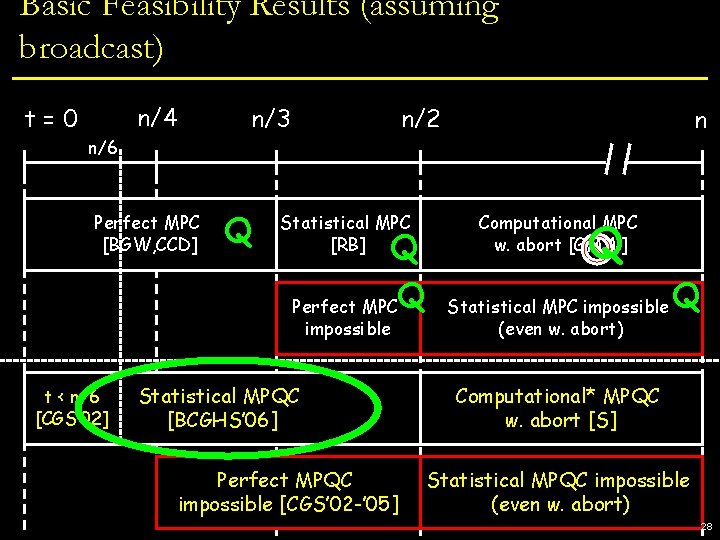
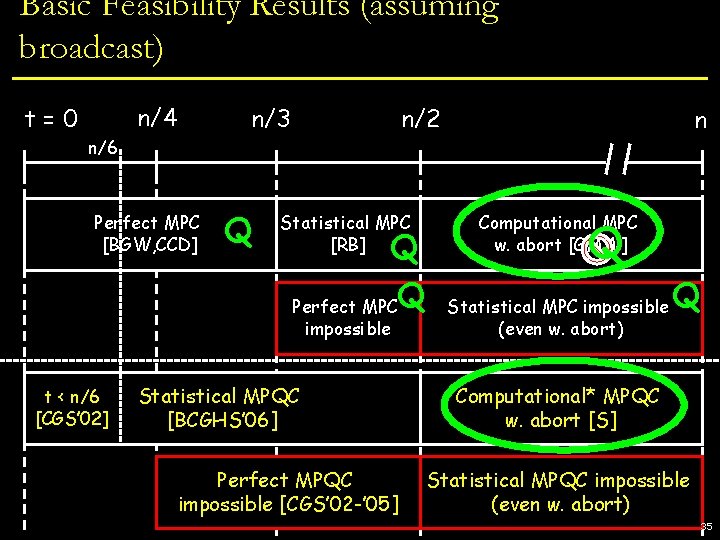
Basic Feasibility Results (assuming broadcast) t=0 n/4 Perfect MPC [BGW, CCD] n/3 n/2 n Statistical MPC [RB] Computational MPC w. abort [GMW] Perfect MPC impossible Statistical MPC impossible (even w. abort) 14

Basic Feasibility Results (assuming broadcast) n/4 t=0 n/3 n/2 n n/6 Perfect MPC [BGW, CCD] Q Statistical MPC [RB] Q Q Perfect MPC impossible t < n/6 [CGS’ 02] Statistical MPQC [BCGHS’ 06] Perfect MPQC impossible [CGS’ 02 -’ 05] Computational MPC w. abort [GMW] Q Statistical MPC impossible (even w. abort) Q Computational* MPQC w. abort [S] Statistical MPQC impossible (even w. abort) 15
![Basic Feasibility Results assuming broadcast n3 CGS 02 use errorcorrecting codes n n2 Basic Feasibility Results (assuming broadcast) • n/3 [CGS’ 02]: use error-correcting codes n n/2](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-16.jpg)
Basic Feasibility Results (assuming broadcast) • n/3 [CGS’ 02]: use error-correcting codes n n/2 and fault-tolerant circuits [AB] • 2 nd real proof of quantum security n/4 t=0 n/6 Perfect MPC [BGW, CCD] Statistical MPC Computational MPC at n/4 : quantum codes [KL] Q • Barrier [RB] Q w. abort [GMW] Q • Authentication codes [BCGST ‘ 02] give Q Perfect MPC Statistical MPC impossible Q • impossible approximate codes [CGS ‘ 05] (even w. abort) • reduction to computation on keys t < n/6 [CGS’ 02] Statistical MPQC [BCGHS’ 06] Perfect MPQC impossible [CGS’ 02 -’ 05] Computational* MPQC w. abort [S] Statistical MPQC impossible (even w. abort) 16

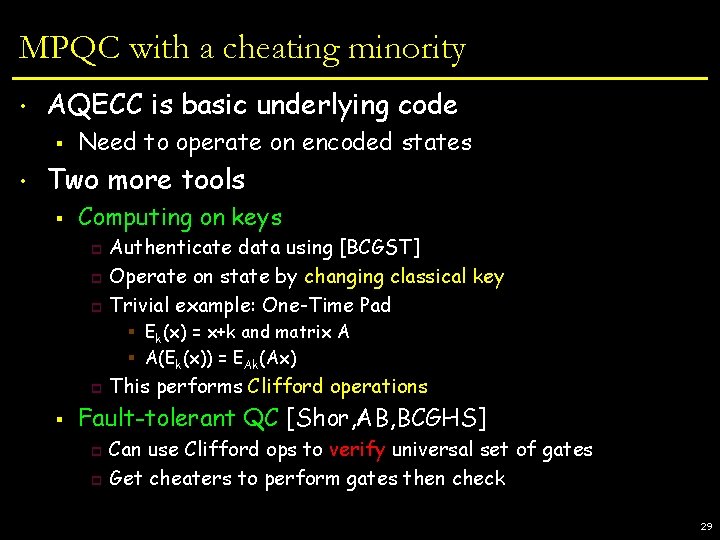
This Talk • Basics of quantum computing • Multiparty Quantum Computing • Codes and Authentication § Quantum error-correcting codes § A spurious lower bound § Authentication § Approximate Codes and Secret Sharing • MPQC with a cheating minority • Beyond a faulty minority: 2 -party QC § ZK for quantum adversaries 17

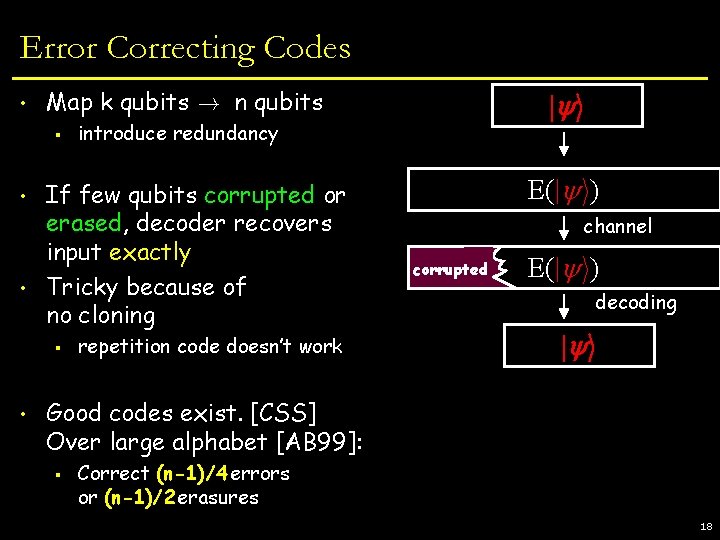
Error Correcting Codes • Map k qubits ! n qubits § • • • introduce redundancy If few qubits corrupted or erased, decoder recovers input exactly Tricky because of no cloning § | i repetition code doesn’t work E(| i) channel corrupted E(| i) decoding | i Good codes exist. [CSS] Over large alphabet [AB 99]: § Correct (n-1)/4 errors or (n-1)/2 erasures 18

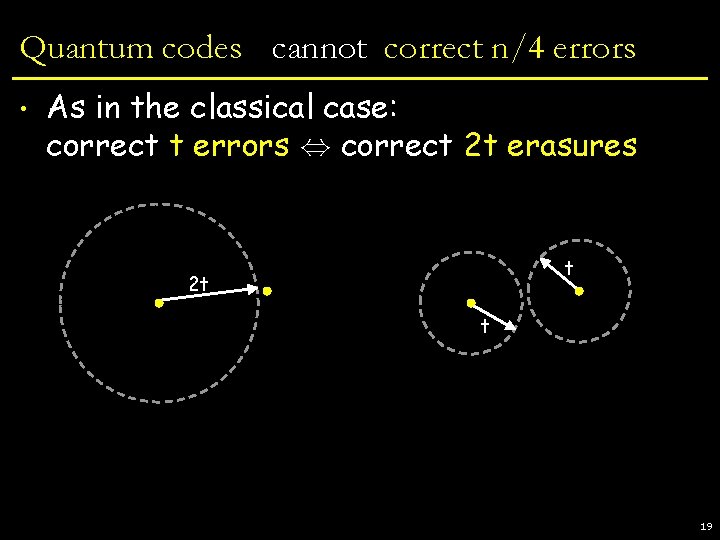
Quantum codes cannot correct n/4 errors • As in the classical case: correct t errors , correct 2 t erasures t 2 t t 19

Quantum codes cannot correct n/4 errors • As in the classical case: correct t errors , correct 2 t erasures • Quantum codes cannot correct n/2 erasures § No cloning Dolly E(| i) decoder | i ) Quantum codes cannot correct n/4 errors (not true of classical codes – repetition) 20

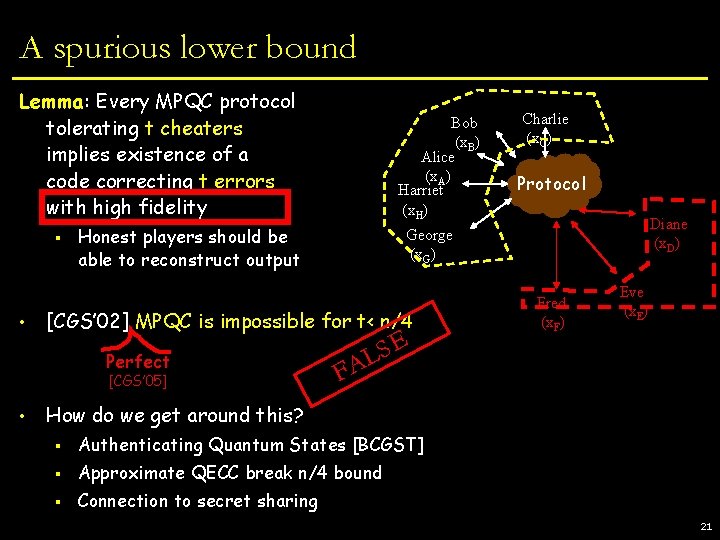
A spurious lower bound Lemma: Every MPQC protocol tolerating t cheaters implies existence of a code correcting t errors with high fidelity § • Honest players should be able to reconstruct output [CGS’ 05] Charlie (x. C) Protocol Diane (x. D) George (x. G) [CGS’ 02] MPQC is impossible for t< n/4 Perfect • Bob (x. B) Alice (x. A) Harriet (x. H) SE L FA Fred (x. F) Eve (x. E) How do we get around this? § Authenticating Quantum States [BCGST] § Approximate QECC break n/4 bound § Connection to secret sharing 21
![Authenticating Quantum Messages How does Alice know its Bob BCGST classical Authenticating Quantum Messages • How does Alice know it’s Bob? § • [BCGST] classical](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-22.jpg)
Authenticating Quantum Messages • How does Alice know it’s Bob? § • [BCGST] classical MACs What if he needs to send her qubits? 22
![Authenticating Quantum Messages BCGST Classical key k i Ak i Eve Alice Authenticating Quantum Messages [BCGST] Classical key k | i Ak(| i) Eve Alice •](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-23.jpg)
Authenticating Quantum Messages [BCGST] Classical key k | i Ak(| i) Eve Alice • Bob or ? System behaves like “channel with veto” § § • | i Eve inputs one bit (accept/reject) No cloning ) If Bob accepts, Eve learns nothing In fact, Eve learns nothing. Ever. Authentication ) encryption Dolly [BCGST’ 02] poly-time protocols § m qubits à 2 m + 2 log (m/ ) bits of key § Construction on board? 23
![Approximate Codes CGS 05 Code correcting n12 errors Start with n12 erasurecorrecting Approximate Codes [CGS’ 05] • Code “correcting” (n-1)/2 errors • Start with (n-1)/2 erasure-correcting](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-24.jpg)
Approximate Codes [CGS’ 05] • Code “correcting” (n-1)/2 errors • Start with (n-1)/2 erasure-correcting code § Authenticate each piece § Secret-share keys § Use classical MACs to authenticate keys Ak(| 1 i) Ak(| 2 i) | i E(| i) Ak(| 3 i) Ak(| 4 i) + classical shares + MAC of authentication keys Ak(| 5 i) 24
![Approximate Codes CGS 05 AQECC correcting n12 errors If any majority of Approximate Codes [CGS’ 05] • AQECC “correcting” (n-1)/2 errors § If any majority of](https://slidetodoc.com/presentation_image/089976d38d70e061612aaaad0decdea2/image-25.jpg)
Approximate Codes [CGS’ 05] • AQECC “correcting” (n-1)/2 errors § If any majority of pieces untouched § Then original state recovered approximately § Correct twice as many errors § No classical analogue in codes… (see also [LNCY]) Ak(| 1 i) Ak(| 2 i) | i E(| i) Ak(| 3 i) Ak(| 4 i) + classical shares + MAC of authentication keys Ak(| 5 i) 25

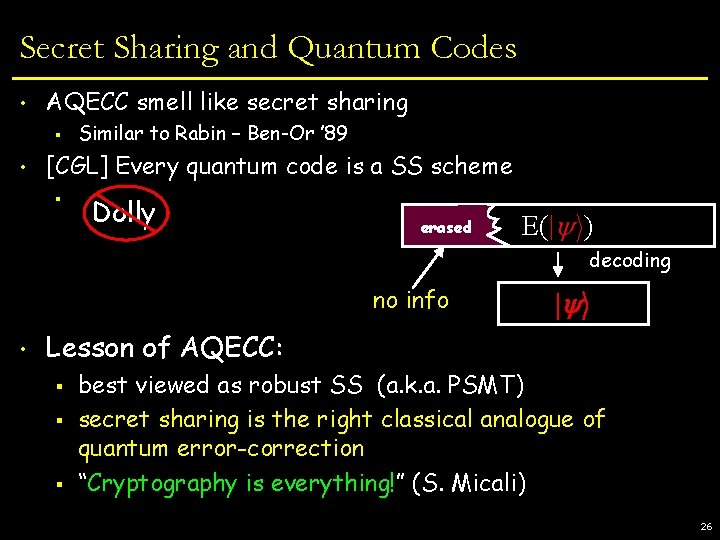
Secret Sharing and Quantum Codes • AQECC smell like secret sharing § • Similar to Rabin – Ben-Or ’ 89 [CGL] Every quantum code is a SS scheme § Dolly erased E(| i) decoding no info • | i Lesson of AQECC: § § § best viewed as robust SS (a. k. a. PSMT) secret sharing is the right classical analogue of quantum error-correction “Cryptography is everything!” (S. Micali) 26

This Talk • Basics of quantum computing • Multiparty Quantum Computing • Codes and Authentication • MPQC with a cheating minority • Beyond a faulty minority: 2 -party QC § ZK for quantum adversaries 27

Basic Feasibility Results (assuming broadcast) n/4 t=0 n/3 n/2 n n/6 Perfect MPC [BGW, CCD] Q Statistical MPC [RB] Q Q Perfect MPC impossible t < n/6 [CGS’ 02] Statistical MPQC [BCGHS’ 06] Perfect MPQC impossible [CGS’ 02 -’ 05] Computational MPC w. abort [GMW] Q Statistical MPC impossible (even w. abort) Q Computational* MPQC w. abort [S] Statistical MPQC impossible (even w. abort) 28

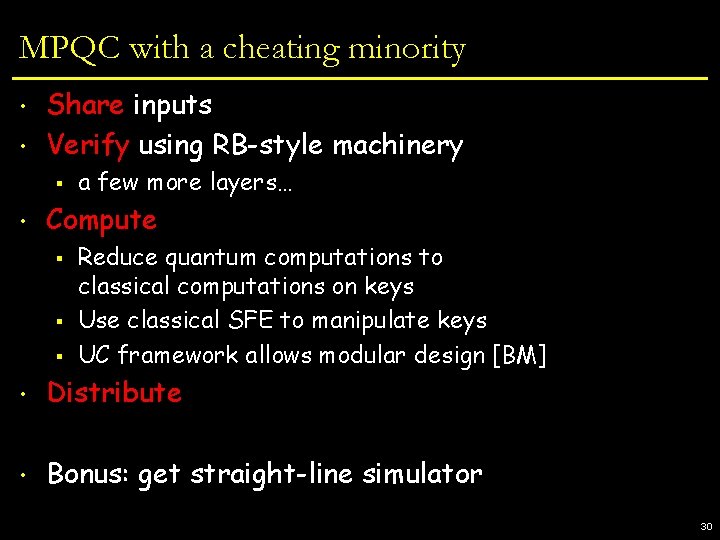
MPQC with a cheating minority • AQECC is basic underlying code § • Need to operate on encoded states Two more tools § Computing on keys Authenticate data using [BCGST] p Operate on state by changing classical key p Trivial example: One-Time Pad p § Ek(x) = x+k and matrix A § A(Ek(x)) = EAk(Ax) p § This performs Clifford operations Fault-tolerant QC [Shor, AB, BCGHS] Can use Clifford ops to verify universal set of gates p Get cheaters to perform gates then check p 29

MPQC with a cheating minority • • Share inputs Verify using RB-style machinery § • a few more layers… Compute § § § Reduce quantum computations to classical computations on keys Use classical SFE to manipulate keys UC framework allows modular design [BM] • Distribute • Bonus: get straight-line simulator 30

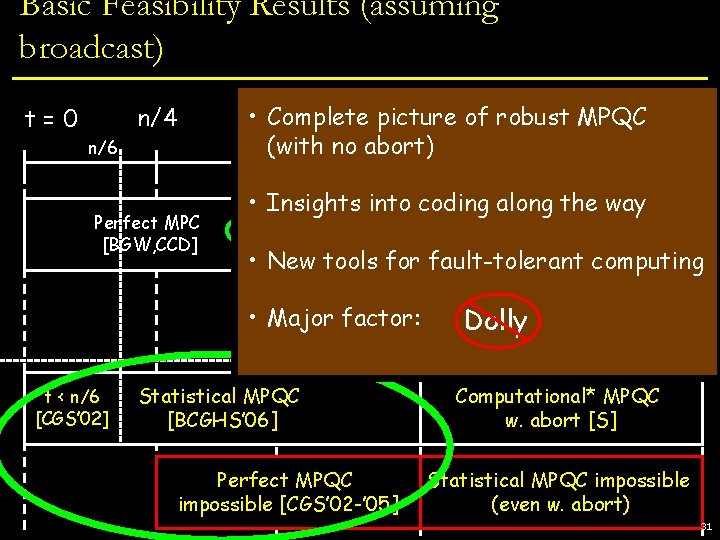
Basic Feasibility Results (assuming broadcast) • n/3 Complete picture n/2 of robust MPQC (with no abort) n/4 t=0 n/6 Perfect MPC [BGW, CCD] • Insights into coding along the way Q Statistical MPC [RB] Computational MPC w. abort [GMW] Q Q fault-tolerant computing • New tools for • t < n/6 [CGS’ 02] n Q Perfect MPC Major factor: impossible Statistical MPQC [BCGHS’ 06] Perfect MPQC impossible [CGS’ 02 -’ 05] Statistical MPC impossible Dolly (even w. abort) Q Computational* MPQC w. abort [S] Statistical MPQC impossible (even w. abort) 31

This Talk • Basics of quantum computing • Multiparty Quantum Computing • Codes and Authentication • MPQC with a cheating minority • Beyond a faulty minority: 2 -party QC § ZK for quantum adversaries 32

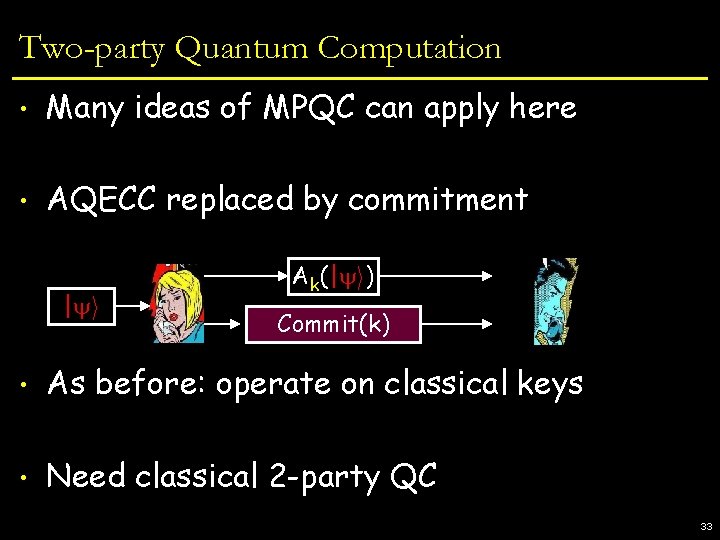
Two-party Quantum Computation • Many ideas of MPQC can apply here • AQECC replaced by commitment | i Ak(| i) Commit(k) • As before: operate on classical keys • Need classical 2 -party QC 33

Two-party Quantum Computation • Problem: standard ZK simulation + extraction arguments may not work in quantum world § § • Big step: Watrous’ simulator for 3 -round ZK § • Rewinding = cloning auxiliary info Dolly Sequential composition is lost Does not give knowledge extractor Idea: We can lie, need to read minds § § § Attach special preamble Work in progress: need funny assumptions Refine understanding of how we argue security 34

Basic Feasibility Results (assuming broadcast) n/4 t=0 n/3 n/2 n n/6 Perfect MPC [BGW, CCD] Q Statistical MPC [RB] Q Q Perfect MPC impossible t < n/6 [CGS’ 02] Statistical MPQC [BCGHS’ 06] Perfect MPQC impossible [CGS’ 02 -’ 05] Computational MPC w. abort [GMW] Q Statistical MPC impossible (even w. abort) Q Computational* MPQC w. abort [S] Statistical MPQC impossible (even w. abort) 35

Cryptography in a Quantum World • Landscape changes! § § § New features appear New difficulties arise Some key pieces unchanged • Needed: Tools and language for reasoning about quantum adversaries • The field is still very young § § § Some successes… … occasional mistakes Lots of questions! quantum thinkers needed Isaac Newton 1642 -1727 36

Things I Did Not Talk About • Proofs! • Quantum Key Distribution • Byzantine Agreement in full info model [BH] • Randomness Extraction with Quantum Memories § [AS. ’ 04, KMR’ 04, D’ 06, GIKRd. W’ 06] • Fault-tolerant QC • Multiprover commitments [CST] • … 37

Thanks Co-authors: Howard Barnum (LANL), Michael Ben-Or (HUJI), Claude Crépeau (Mc. Gill), Daniel Gottesman (Perimeter/Waterloo), Avinatan Hasidim (HUJI), Alain Tapp (Montreal) Discussions: Boaz Barak, Louis Salvail, Jon Katz, …