Cryptography Lecture 6 Arpita Patra Quick Recall and




- Slides: 24

Cryptography Lecture 6 Arpita Patra

Quick Recall and Today’s Roadmap >> MAC for fixed-length messages >> Domain Extension for MAC >> Authenticated Encryption: Privacy and Integrity; Definition: CCA-security + unforgeability. >> AE: Other definitions; >> AE CCA Security >> Construction (again a bit tricky) based on CPA secure SKE + CMA-secure MAC >> AE: proof of Security >> Hash Function: Various Security Notions >> Markle-Damgaard Domain Extension >> Davis-Meyer Construction

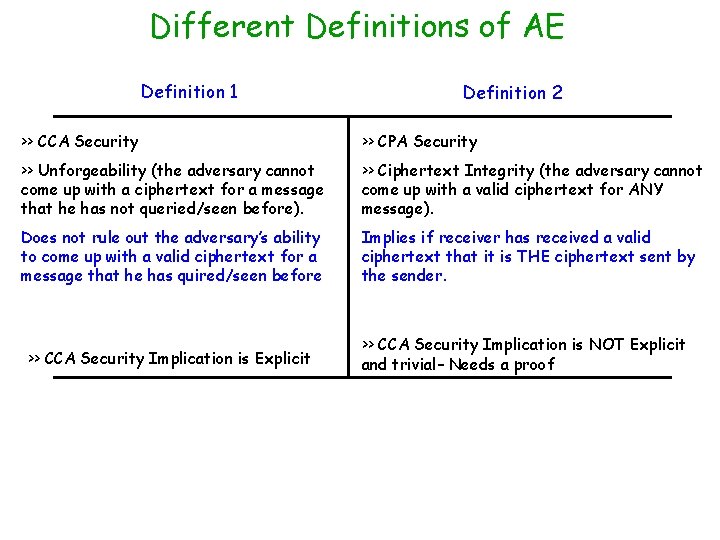
Different Definitions of AE Definition 1 Definition 2 >> CCA Security >> CPA Security >> Unforgeability (the adversary cannot come up with a ciphertext for a message that he has not queried/seen before). >> Ciphertext Integrity (the adversary cannot come up with a valid ciphertext for ANY message). Does not rule out the adversary’s ability to come up with a valid ciphertext for a message that he has quired/seen before Implies if receiver has received a valid ciphertext that it is THE ciphertext sent by the sender. >> CCA Security Implication is Explicit >> CCA Security Implication is NOT Explicit and trivial– Needs a proof

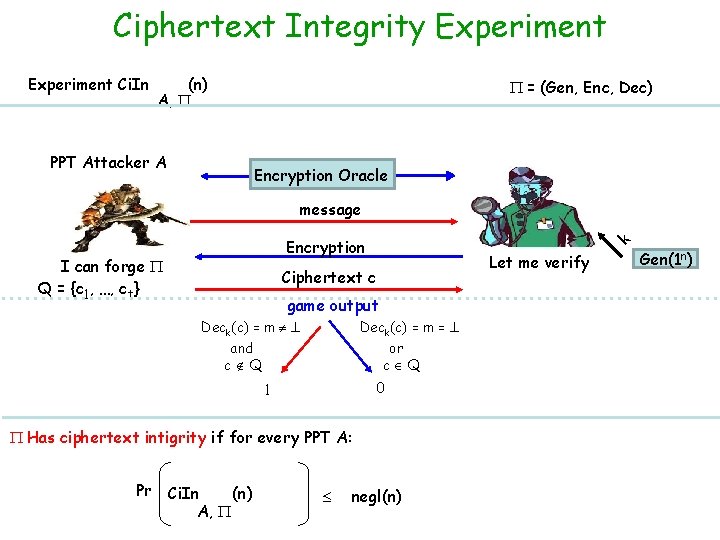
Ciphertext Integrity Experiment Ci. In (n) A, = (Gen, Enc, Dec) PPT Attacker A Encryption Oracle message I can forge Q = {c 1, …, ct} k Encryption Let me verify Ciphertext c game output Deck(c) = m = and c Q or c Q 0 1 Has ciphertext intigrity if for every PPT A: Pr Ci. In (n) A, negl(n) Gen(1 n)

Authenticated Encryption is CCA-secure Theorem: Every Authenticated Encryption is CCA-secure Proof: On the board.

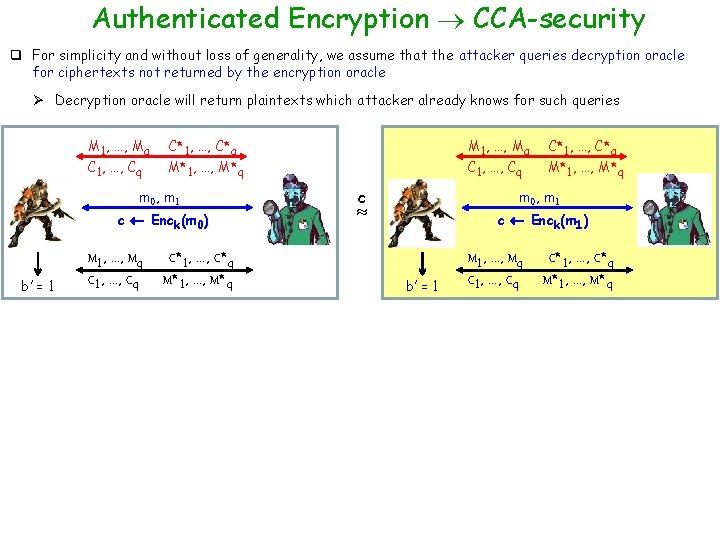
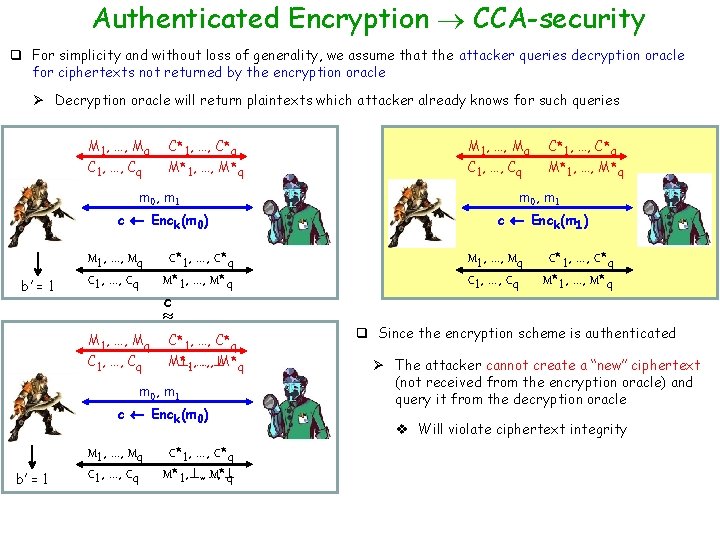
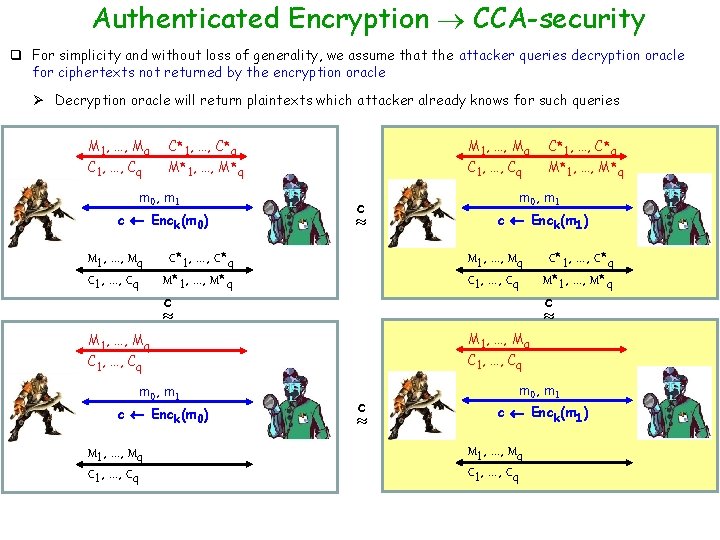
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) b’ = 1 M 1, …, Mq C 1, …, Cq M 1, …, Mq C*1, …, C*q M*1, …, M*q C 1, …, Cq c C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 1) b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q

Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq b’ = 1 C*1, …, C*q M*1, …, M*q C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c M 1, …, Mq C 1, …, Cq C*1, …, C*q M* , 1, …, …, M*q m 0, m 1 c Enck(m 0) b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, , …, …, M* q M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q q Since the encryption scheme is authenticated Ø The attacker cannot create a “new” ciphertext (not received from the encryption oracle) and query it from the decryption oracle v Will violate ciphertext integrity

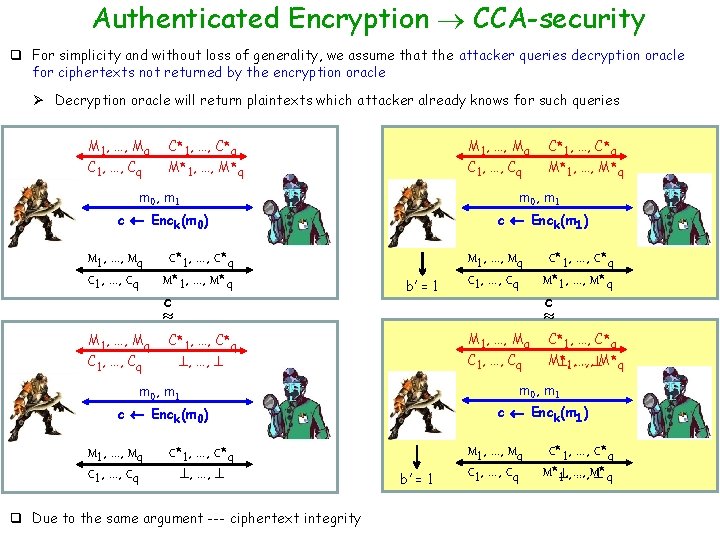
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M 1, …, Mq M*1, …, M*q C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c b’ = 1 M 1, …, Mq C 1, …, Cq c M 1, …, Mq C*1, …, C*q C 1, …, Cq , …, q Due to the same argument --- ciphertext integrity M* …, M*q , 1, …, c Enck(m 1) c Enck(m 0) C*1, …, C*q , …, C*1, …, C*q m 0, m 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M* , …, M* q 1, …,

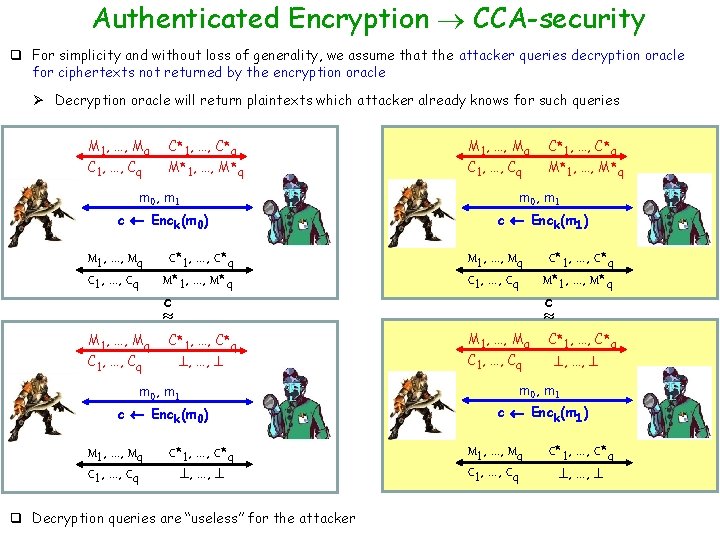
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c M 1, …, Mq C 1, …, Cq c C*1, …, C*q , …, m 0, m 1 c Enck(m 0) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q C*1, …, C*q , …, q Decryption queries are “useless” for the attacker M 1, …, Mq C 1, …, Cq C*1, …, C*q , …, m 0, m 1 c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q , …,

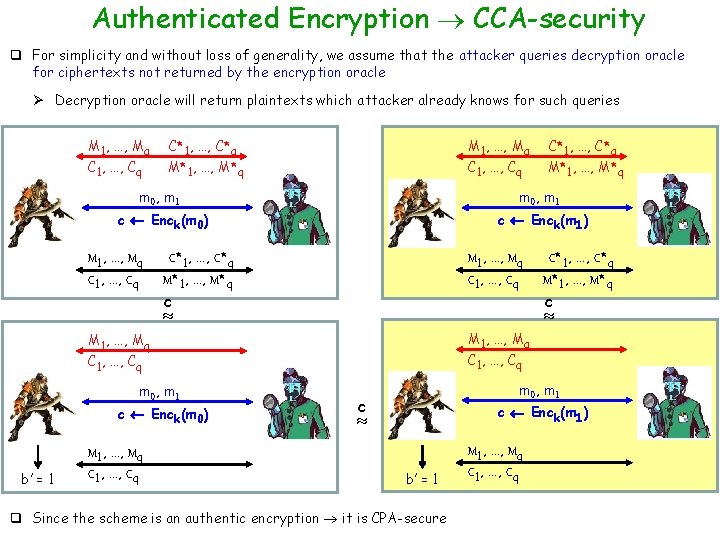
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M 1, …, Mq M*1, …, M*q C 1, …, Cq M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q M 1, …, Mq C 1, …, Cq c c Enck(m 0) M 1, …, Mq C 1, …, Cq c M 1, …, Mq C 1, …, Cq m 0, m 1 C*1, …, C*q M*1, …, M*q M 1, …, Mq b’ = 1 C*1, …, C*q m 0, m 1 c c Enck(m 1) b’ = 1 q Since the scheme is an authentic encryption it is CPA-secure M 1, …, Mq C 1, …, Cq

Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) M 1, …, Mq C 1, …, Cq c C*1, …, C*q M*1, …, M*q c Enck(m 1) M 1, …, Mq C 1, …, Cq c Enck(m 0) C*1, …, C*q M*1, …, M*q M 1, …, Mq m 0, m 1 M*1, …, M*q m 0, m 1 M 1, …, Mq C 1, …, Cq c C*1, …, C*q c m 0, m 1 c Enck(m 1) M 1, …, Mq C 1, …, Cq

Ingredients for Authenticated Encryption >> CPA-secure SKE >> CMA-secure MAC >> How to combine them– crux of AE

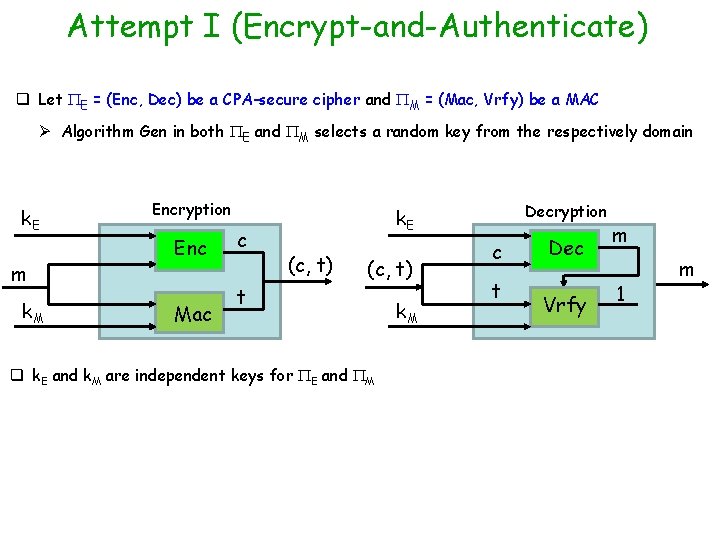
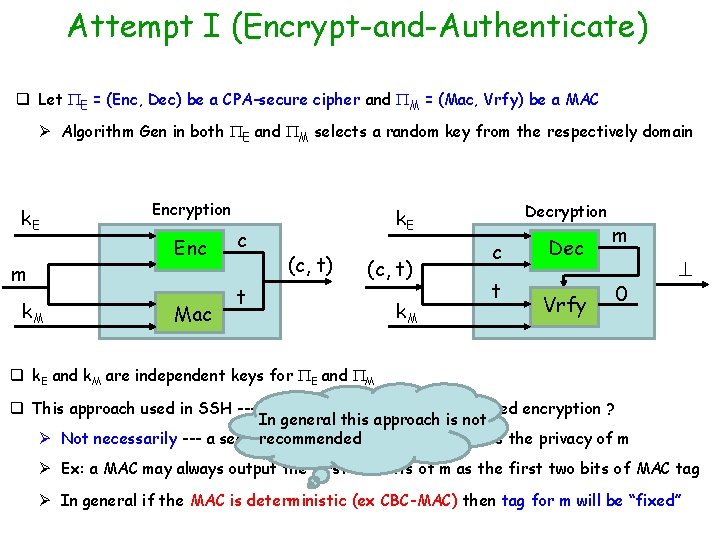
Attempt I (Encrypt-and-Authenticate) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. M Encryption Enc Mac c Decryption k. E (c, t) t q k. E and k. M are independent keys for E and M k. M c t Dec Vrfy m 1 m

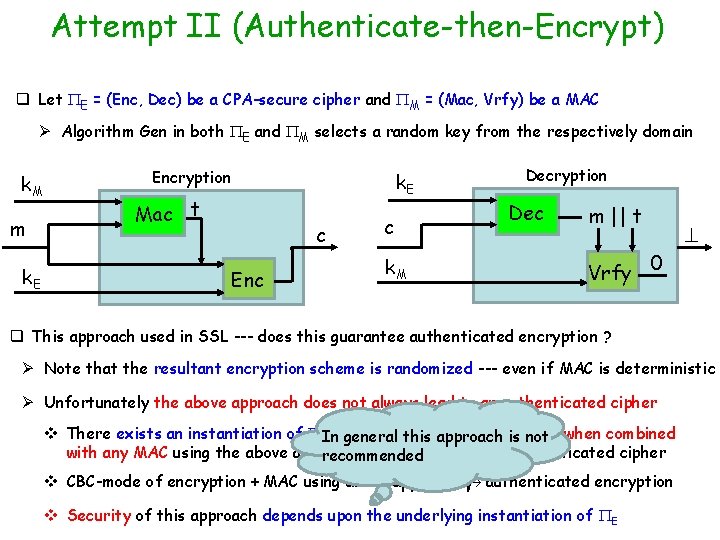
Attempt I (Encrypt-and-Authenticate) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. M Encryption Enc Mac c Decryption k. E (c, t) t k. M c t Dec Vrfy m 0 q k. E and k. M are independent keys for E and M q This approach used in SSH --- does this guarantee authenticated encryption ? In general this approach is not recommended Ø Not necessarily --- a secure MAC not necessarily preserves the privacy of m Ø Ex: a MAC may always output the first two bits of m as the first two bits of MAC tag Ø In general if the MAC is deterministic (ex CBC-MAC) then tag for m will be “fixed”

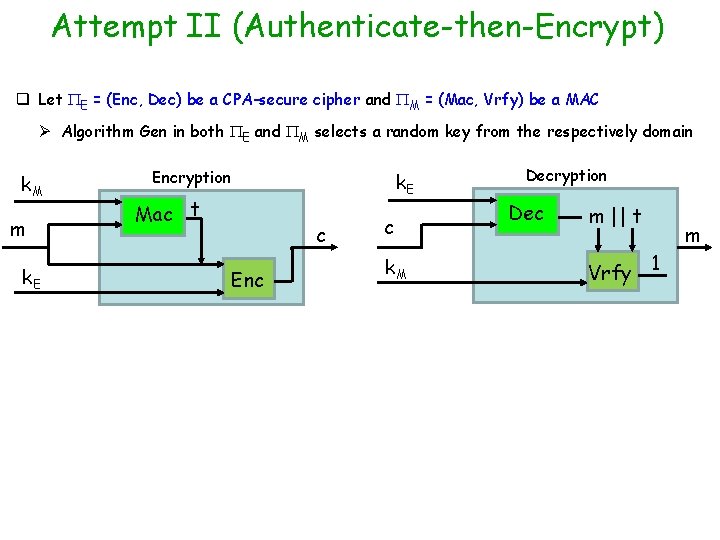
Attempt II (Authenticate-then-Encrypt) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. M m k. E Encryption Mac t k. E c Enc c k. M Decryption Dec m || t Vrfy 1 m

Attempt II (Authenticate-then-Encrypt) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. M m k. E Encryption Mac t k. E c Enc c k. M Decryption Dec m || t Vrfy 0 q This approach used in SSL --- does this guarantee authenticated encryption ? Ø Note that the resultant encryption scheme is randomized --- even if MAC is deterministic Ø Unfortunately the above approach does not always lead to an authenticated cipher v There exists an instantiation of EInwhich is CPA-secure andiswhich general this approach not when combined with any MAC using the above approach does not lead to an authenticated cipher recommended v CBC-mode of encryption + MAC using above approach authenticated encryption v Security of this approach depends upon the underlying instantiation of E

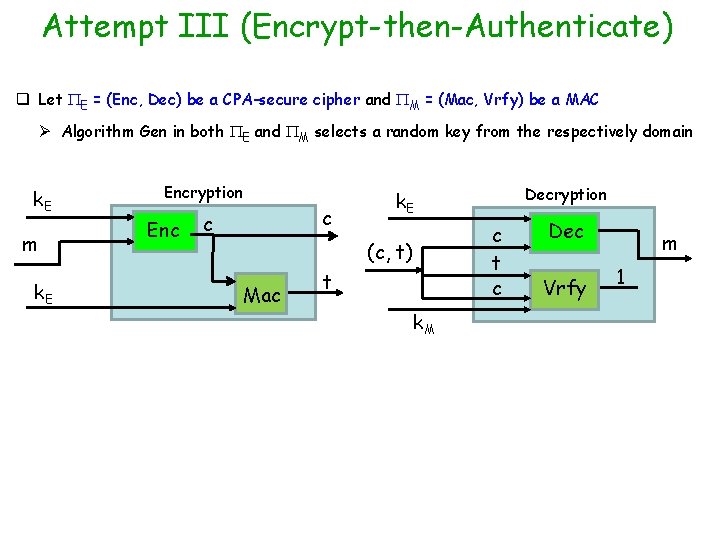
Attempt III (Encrypt-then-Authenticate) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. E Encryption Enc c t c (c, t) Mac Decryption k. E t k. M Dec Vrfy m 1

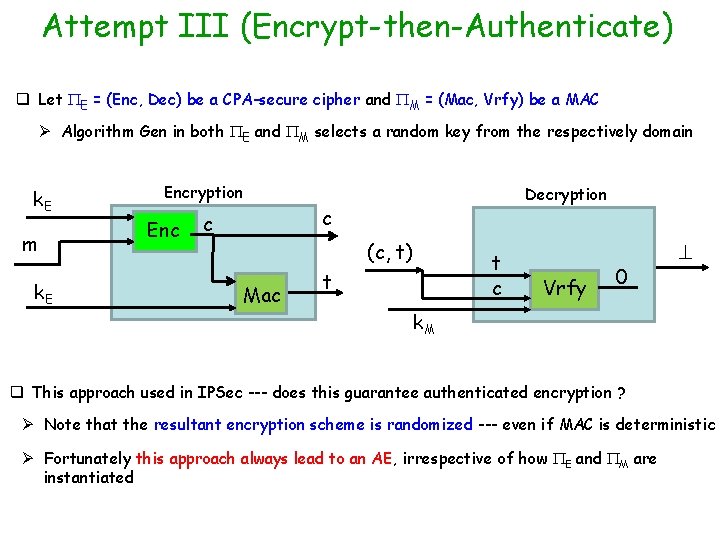
Attempt III (Encrypt-then-Authenticate) q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. E Encryption Enc c Decryption c (c, t) Mac t Vrfy 0 k. M q This approach used in IPSec --- does this guarantee authenticated encryption ? Ø Note that the resultant encryption scheme is randomized --- even if MAC is deterministic Ø Fortunately this approach always lead to an AE, irrespective of how E and M are instantiated

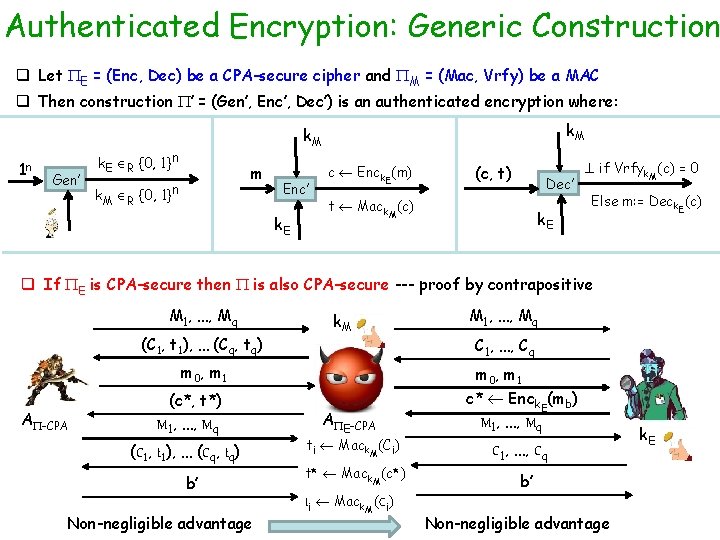
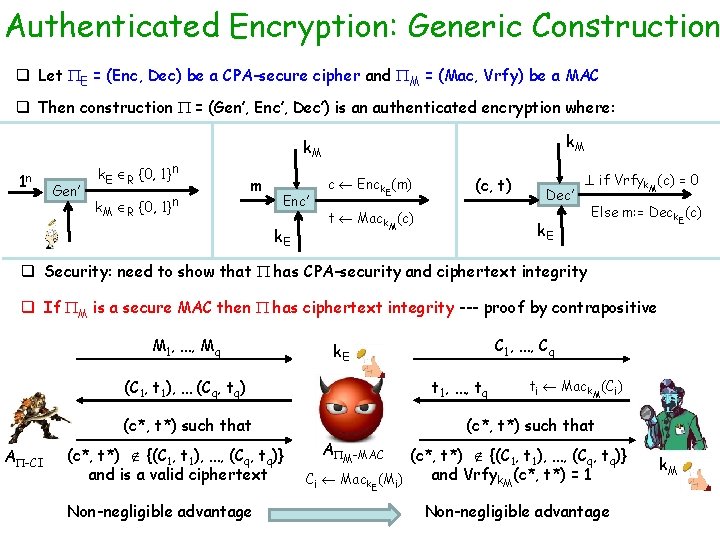
Authenticated Encryption: Generic Construction q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC q Then construction ’ = (Gen’, Enc’, Dec’) is an authenticated encryption where: 1 n Gen’ k. M k. E R {0, 1}n m k. M R {0, 1}n Enc’ k. E c Enck. E(m) (c, t) Dec’ t Mack. M(c) k. E if Vrfyk. M(c) = 0 Else m: = Deck. E(c) q If E is CPA-secure then is also CPA-secure --- proof by contrapositive M 1, …, Mq (C 1, t 1), … (Cq, tq) k. M m 0 , m 1 A -CPA (c*, t*) M 1, …, Mq (C 1, t 1), … (Cq, tq) b’ Non-negligible advantage M 1, …, Mq C 1, …, Cq m 0 , m 1 A E-CPA ti Mack. M(Ci) t* Mack. M(c*) ti Mack. M(Ci) c* Enck. E(mb) M 1, …, Mq C 1, …, Cq b’ Non-negligible advantage k. E

Authenticated Encryption: Generic Construction q Let E = (Enc, Dec) be a CPA-secure cipher and M = (Mac, Vrfy) be a MAC q Then construction = (Gen’, Enc’, Dec’) is an authenticated encryption where: 1 n Gen’ k. E R {0, 1}n k. M m Enc’ k. E c Enck. E(m) (c, t) t Mack. M(c) Dec’ if Vrfyk. M(c) = 0 k. E Else m: = Deck. E(c) q Security: need to show that has CPA-security and ciphertext integrity q If M is a secure MAC then has ciphertext integrity --- proof by contrapositive M 1, …, Mq (C 1, t 1), … (Cq, tq) t 1, …, tq (c*, t*) such that A -CI (c*, t*) {(C 1, t 1), …, (Cq, tq)} and is a valid ciphertext Non-negligible advantage C 1, …, Cq k. E ti Mack. M(Ci) (c*, t*) such that A (c*, t*) {(C 1, t 1), …, (Cq, tq)} and Vrfyk. M(c*, t*) = 1 Ci Mack. E(Mi) M-MAC Non-negligible advantage k. M

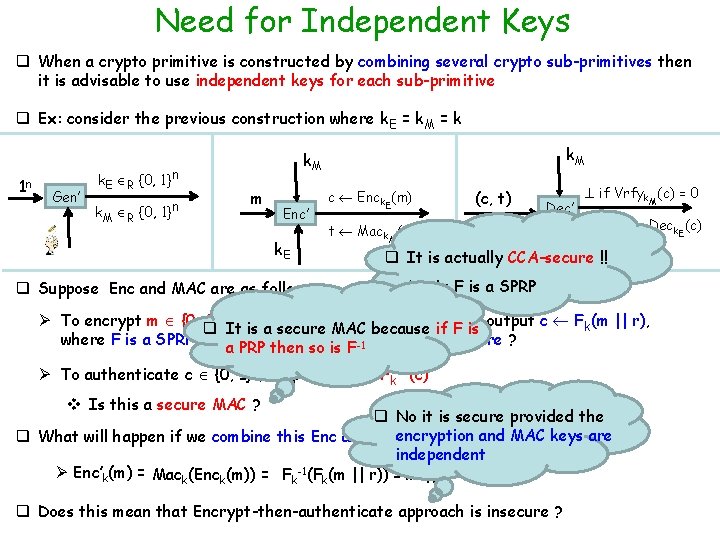
Need for Independent Keys q When a crypto primitive is constructed by combining several crypto sub-primitives then it is advisable to use independent keys for each sub-primitive q Ex: consider the previous construction where k. E = k. M = k 1 n Gen’ k. E R {0, 1}n k. M m Enc’ k. E q Suppose Enc and MAC are as follows: c Enck. E(m) (c, t) Dec’ t Mack. M(c) if Vrfyk. M(c) = 0 Else m: = Deck. E(c) k. E q It is actually CCA-secure !! Ø As F is a SPRP Ø To encrypt m {0, q 1}n/2 a random {0, 1}n/2 It, select is a secure MAC rbecause if Fand is output c Fk(m || r), where F is a SPRP --- is then encryption scheme CPA-secure ? a PRP so is F-1 Ø To authenticate c {0, 1}n, output tag t : = Fk-1(c) v Is this a secure MAC ? q No it is secure provided the encryption q What will happen if we combine this Enc and MAC with k. E =and k. M =MAC k ? keys are independent -1 Ø Enc’k(m) = Mack(Enck(m)) = Fk (Fk(m || r)) = m || r q Does this mean that Encrypt-then-authenticate approach is insecure ?

CCA-security vs Authenticated Encryption q Every authenticated encryption scheme is also a CCA-secure cipher Ø What about the converse ? Ø There are encryption schemes which are only CCA-secure (Assignment problem) q Conceptually the goal of CCA-security and authenticated encryption are different Ø CCA-security : aim to achieve only privacy even if an attacker disrupts the communication Ø Authenticated encryption: aim is to achieve both privacy as well as integrity q Which is more efficient ? Ø In the symmetric-key world both are almost equivalent Ø No reason to just use a CCA-secure scheme (instead of an authenticated encryption) if the major concern is efficiency Ø In the public-key world, the difference is more pronounced v Depending upon the application need to determine whether to go for CCA-security or authenticated encryption

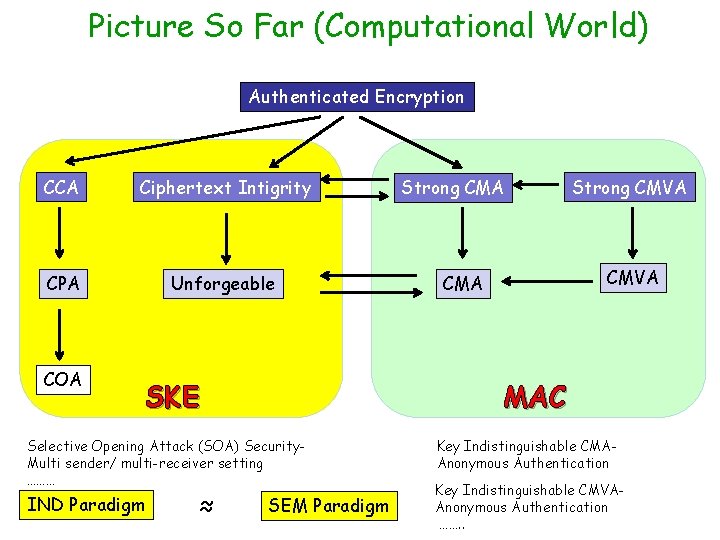
Picture So Far (Computational World) Authenticated Encryption CCA Ciphertext Intigrity CPA Unforgeable COA SKE ≈ Strong CMVA CMA MAC Selective Opening Attack (SOA) Security. Multi sender/ multi-receiver setting ……… IND Paradigm Strong CMA SEM Paradigm Key Indistinguishable CMAAnonymous Authentication Key Indistinguishable CMVAAnonymous Authentication ……. .
