Cryptography Jordi Cortadella and Jordi Petit Department of














- Slides: 37

Cryptography Jordi Cortadella and Jordi Petit Department of Computer Science

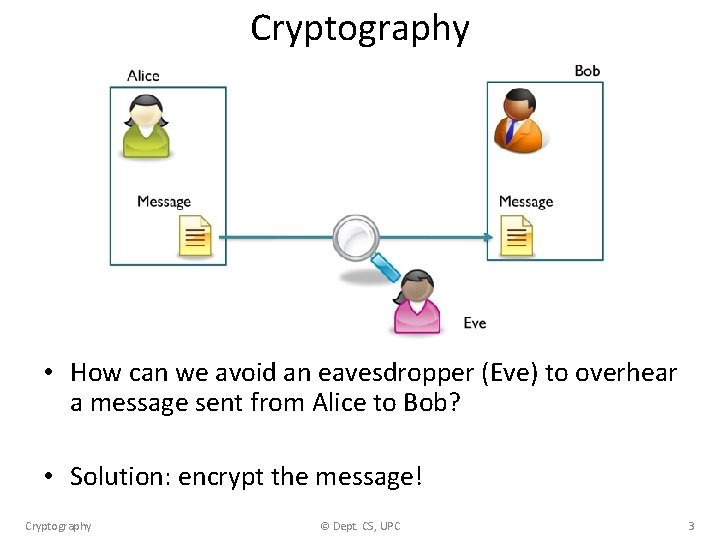
Where do we need cryptography? • Communication (e. g. , sending private emails). • Digital signatures, i. e. , guarantee that digital documents are authentic. • Network services over unsecure networks (e. g. , secure shell (ssh) for remote login, file transfers, remote command execution, etc. ). • Hyper. Text Transfer Protocol Secure (HTTPS): secure communication on Internet. • Cryptocurrencies (e. g. , bitcoin) Cryptography © Dept. CS, UPC 2

Cryptography • How can we avoid an eavesdropper (Eve) to overhear a message sent from Alice to Bob? • Solution: encrypt the message! Cryptography © Dept. CS, UPC 3

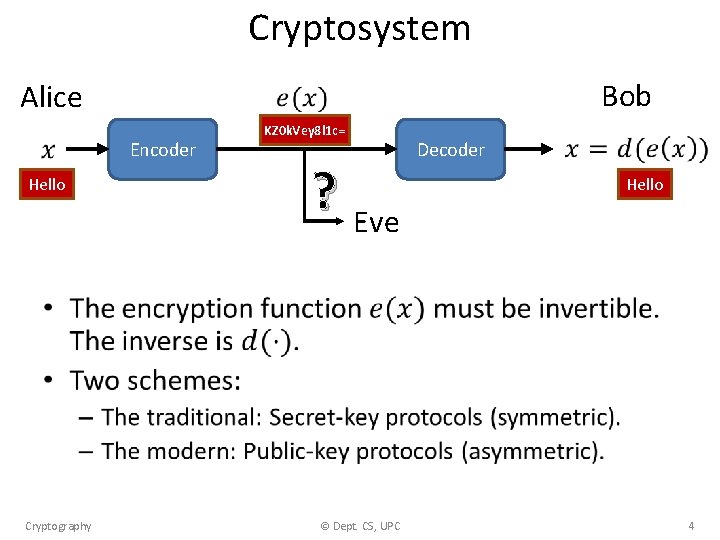
Cryptosystem Alice Encoder Hello Bob KZ 0 k. Vey 8 l 1 c= ? Eve Decoder Hello • Cryptography © Dept. CS, UPC 4

Secret-key protocols • Alice and Bob have to meet privately and chose a secret key. • They can use the secret key to mutually exchange messages. • There are many secret-key protocols. We will explain two of them: – XOR encoding. – Advanced Encryption Standard (AES). Cryptography © Dept. CS, UPC 5

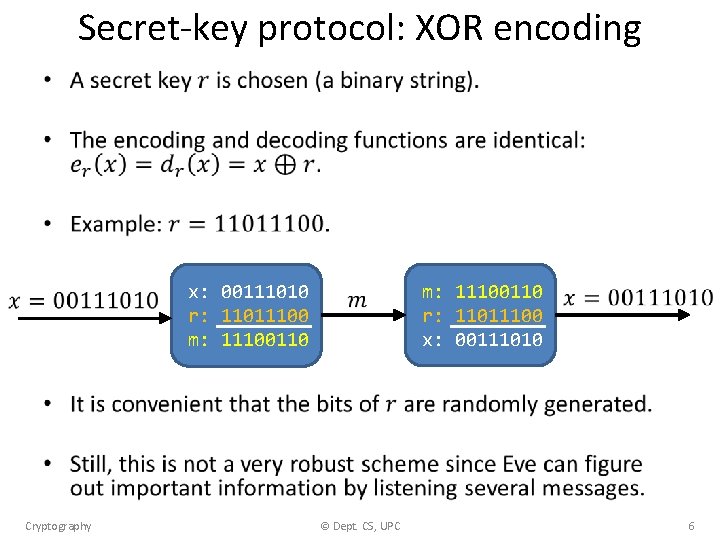
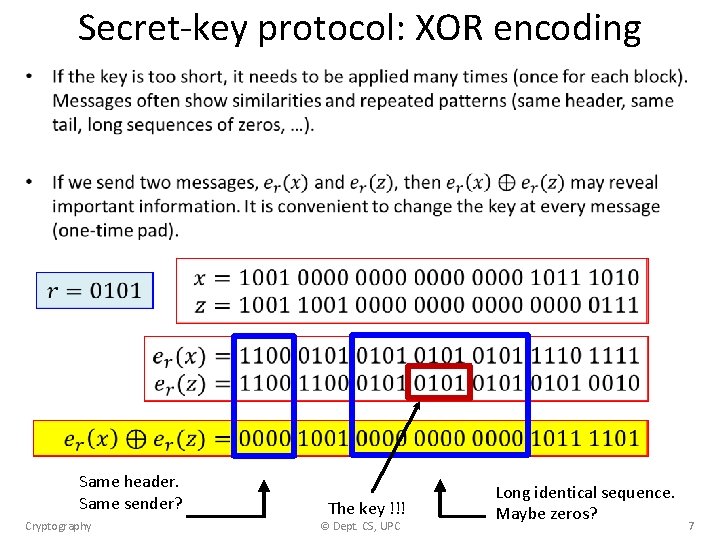
Secret-key protocol: XOR encoding • x: 00111010 r: 11011100 m: 11100110 Cryptography © Dept. CS, UPC m: 11100110 r: 11011100 x: 00111010 6

Secret-key protocol: XOR encoding • Same header. Same sender? Cryptography The key !!! © Dept. CS, UPC Long identical sequence. Maybe zeros? 7

Secret-key protocol: AES • AES: Advanced Encryption Standard. • Established as a standard by the U. S. National Institute of Standards and Technology (NIST) in 2001. • Very robust and used worldwide. • A family of ciphers with different key and block sizes (key sizes: 128, 196 and 256 bits). Cryptography © Dept. CS, UPC 8

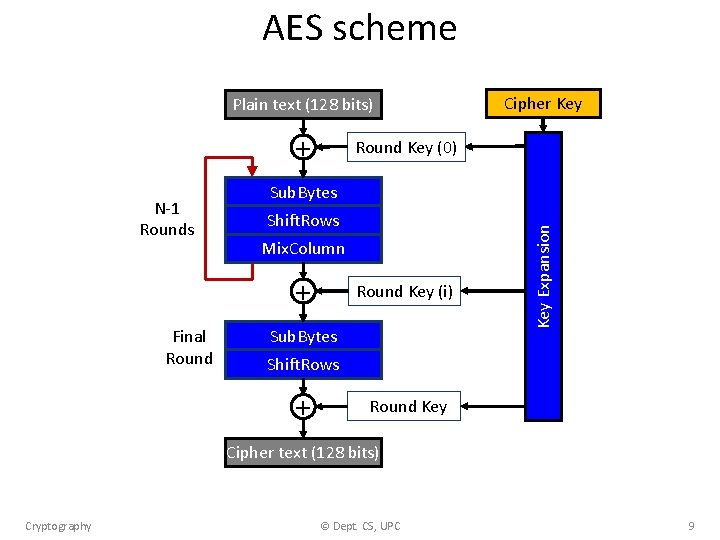
AES scheme Plain text (128 bits) + Round Key (0) Sub. Bytes Shift. Rows Mix. Column + Final Round Key (i) Sub. Bytes Key Expansion N-1 Rounds Cipher Key Shift. Rows + Round Key Cipher text (128 bits) Cryptography © Dept. CS, UPC 9

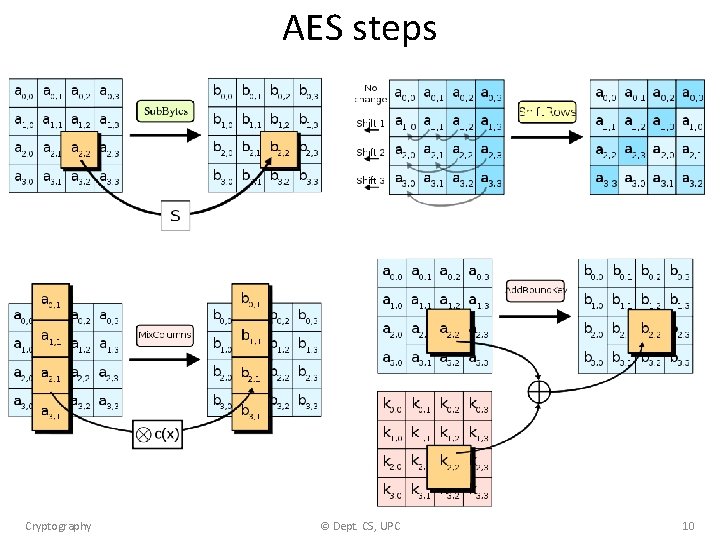
AES steps Cryptography © Dept. CS, UPC 10

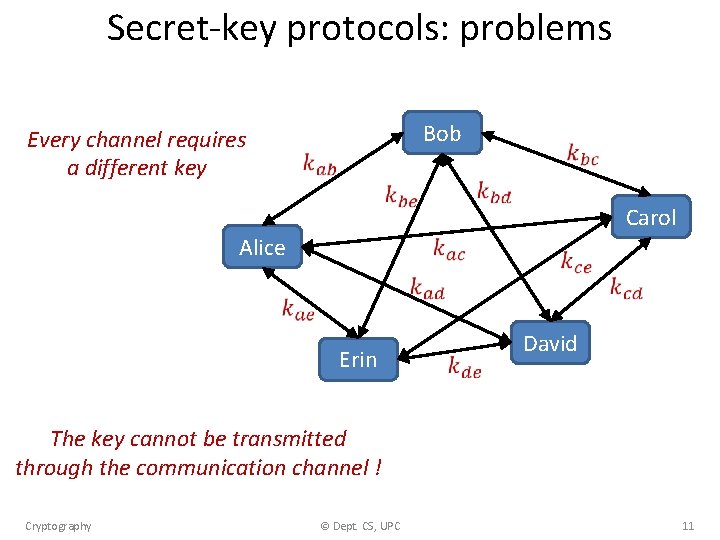
Secret-key protocols: problems Bob Every channel requires a different key Carol Alice Erin David The key cannot be transmitted through the communication channel ! Cryptography © Dept. CS, UPC 11

Public-key protocols Private Public Cryptography © Dept. CS, UPC 12

Public-key protocols Private Public Cryptography © Dept. CS, UPC 13

Public-key protocols Private Public Cryptography © Dept. CS, UPC 14

Public-key protocols • Cryptography © Dept. CS, UPC 15

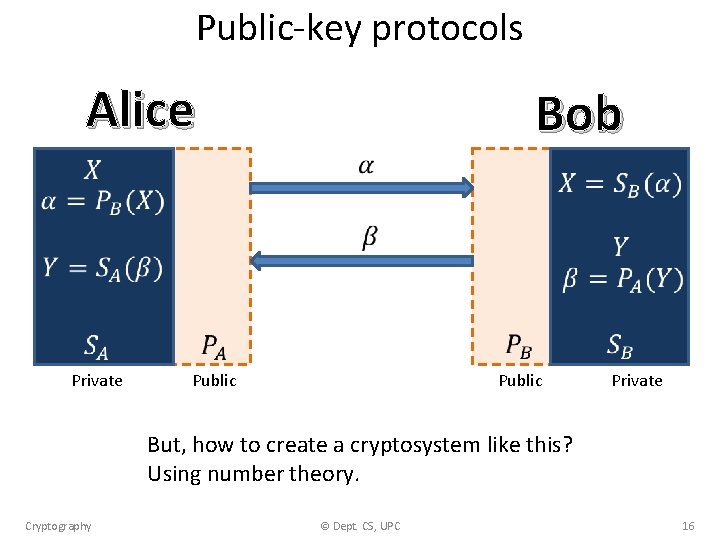
Public-key protocols Alice Bob Private Public Private But, how to create a cryptosystem like this? Using number theory. Cryptography © Dept. CS, UPC 16

RSA cryptosystem • Public-key cryptosystem (Rivest-Shamir-Adleman, 1977). • Based upon number theory: modular arithmetic and prime numbers. • Security: based on the fact that factoring a large number (product of two large primes) is hard. Cryptography © Dept. CS, UPC 17

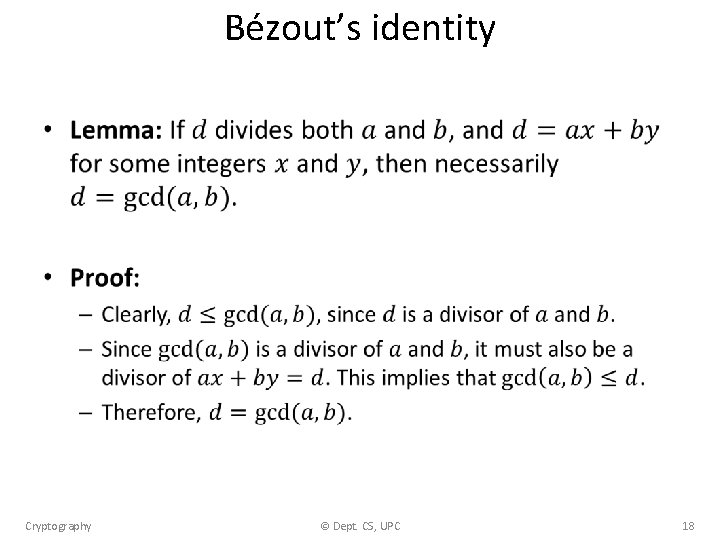
Bézout’s identity • Cryptography © Dept. CS, UPC 18

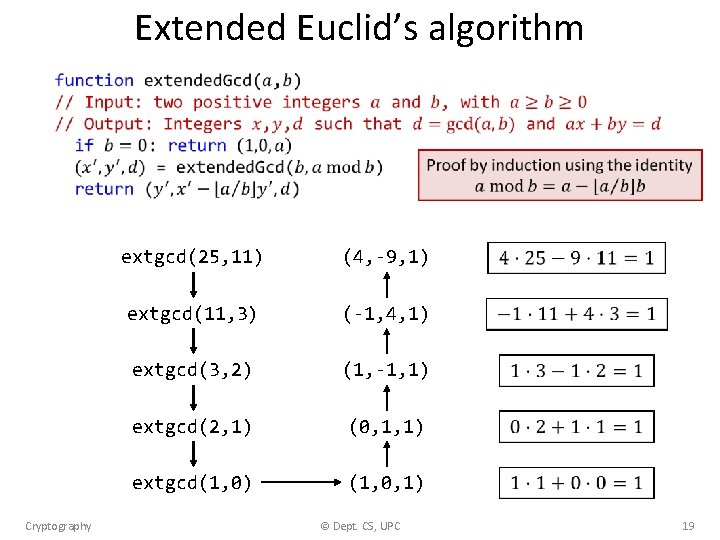
Extended Euclid’s algorithm Cryptography extgcd(25, 11) (4, -9, 1) extgcd(11, 3) (-1, 4, 1) extgcd(3, 2) (1, -1, 1) extgcd(2, 1) (0, 1, 1) extgcd(1, 0) (1, 0, 1) © Dept. CS, UPC 19

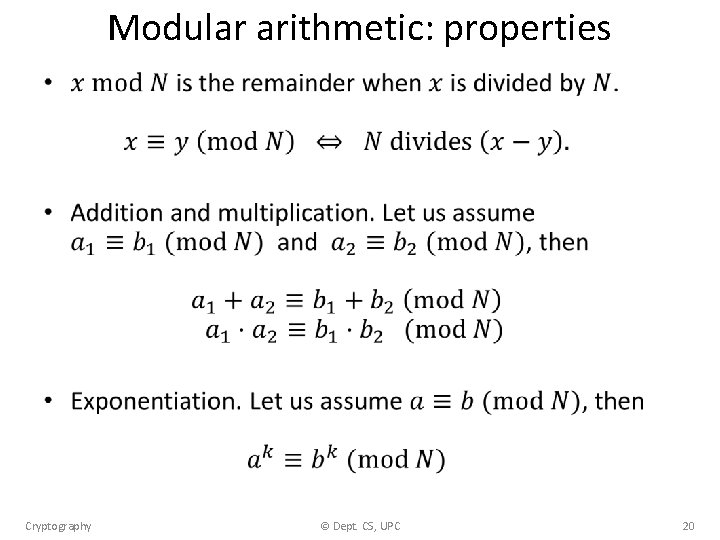
Modular arithmetic: properties • Cryptography © Dept. CS, UPC 20

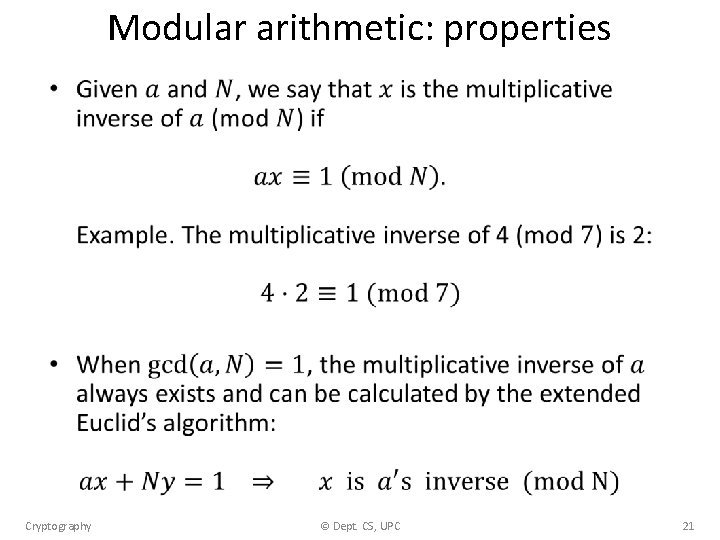
Modular arithmetic: properties • Cryptography © Dept. CS, UPC 21

Fundamental property • Cryptography © Dept. CS, UPC 22

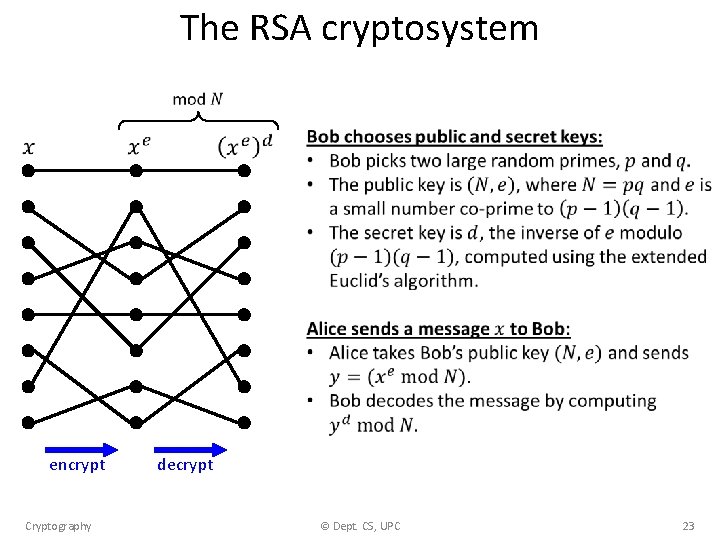
The RSA cryptosystem encrypt Cryptography decrypt © Dept. CS, UPC 23

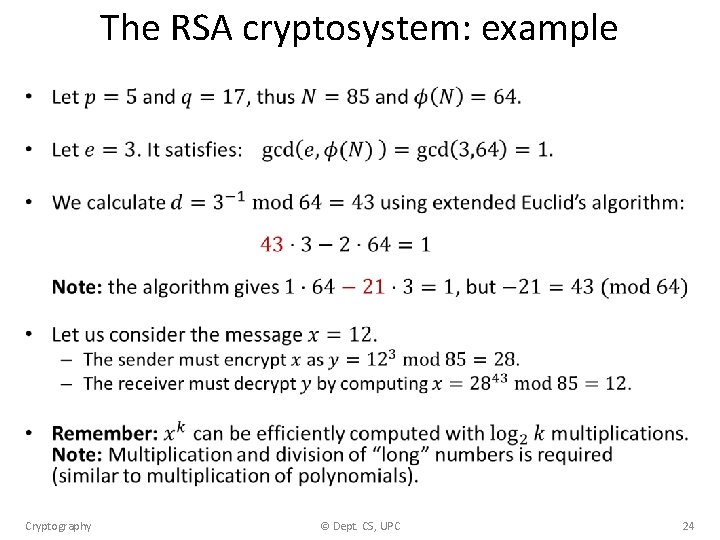
The RSA cryptosystem: example • Cryptography © Dept. CS, UPC 24

Why is RSA secure? • Cryptography © Dept. CS, UPC 25

Hybrid cryptosystems • Cryptography © Dept. CS, UPC 26

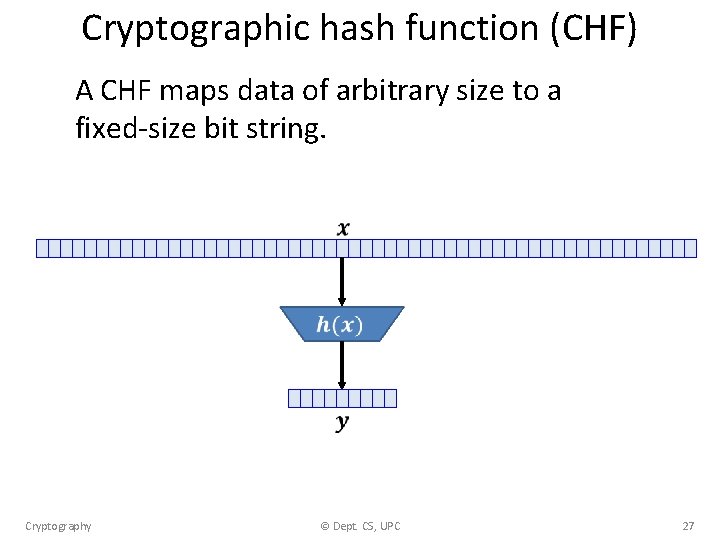
Cryptographic hash function (CHF) A CHF maps data of arbitrary size to a fixed-size bit string. Cryptography © Dept. CS, UPC 27

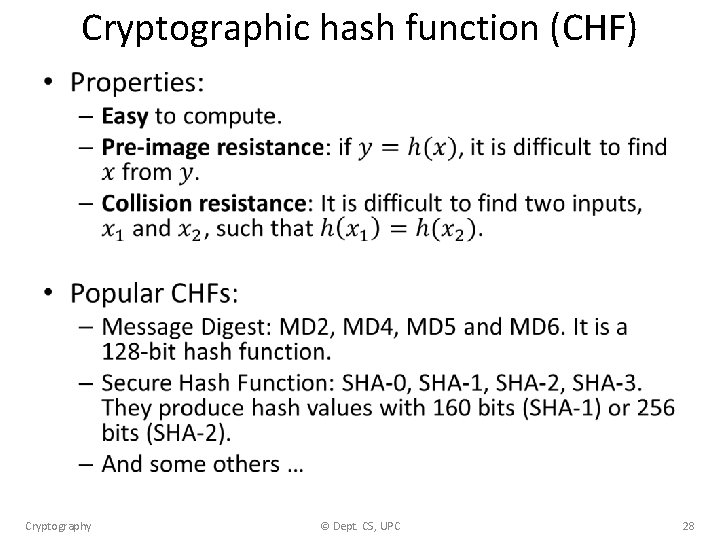
Cryptographic hash function (CHF) • Cryptography © Dept. CS, UPC 28

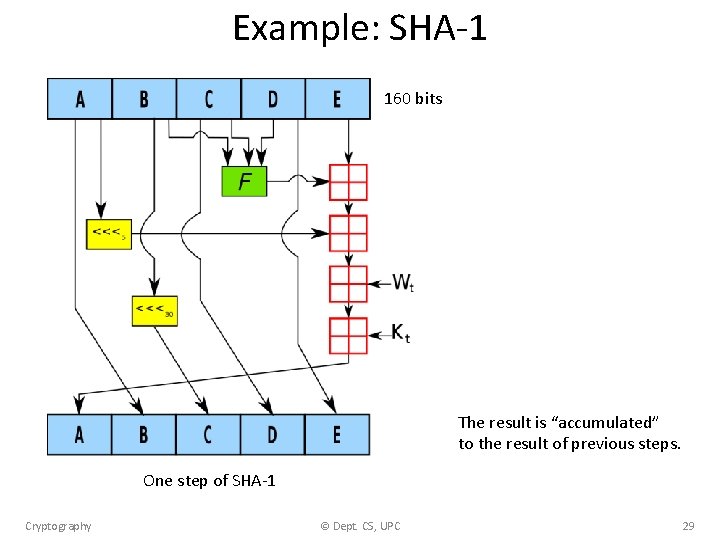
Example: SHA-1 160 bits The result is “accumulated” to the result of previous steps. One step of SHA-1 Cryptography © Dept. CS, UPC 29

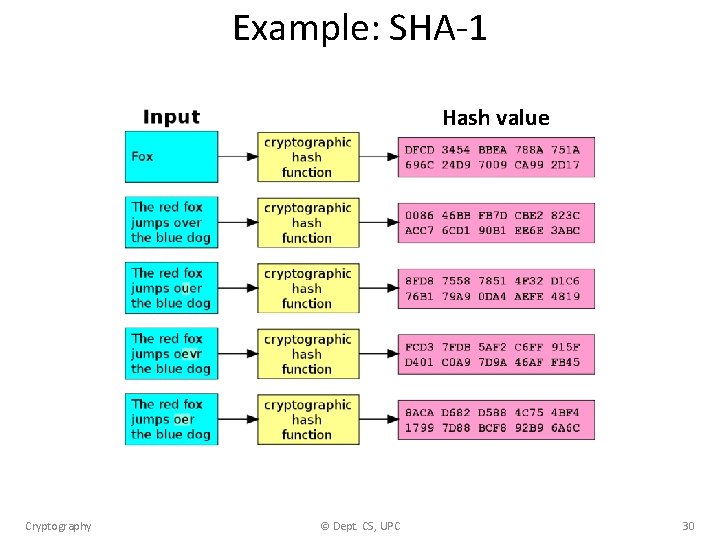
Example: SHA-1 Hash value Cryptography © Dept. CS, UPC 30

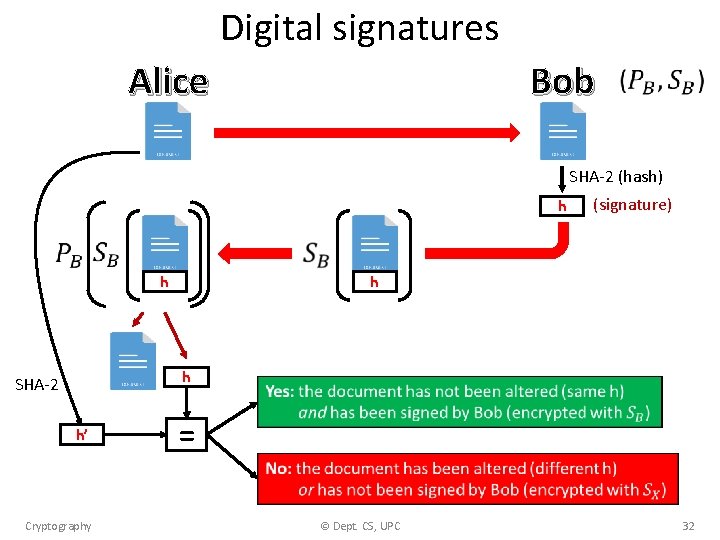
Digital signatures • A scheme to guarantee that a message is authentic. • Consider the following case: – Alice sends a document (possibly unencrypted) to Bob and wants Bob to electronically sign the document. – Bob “signs” the document and sends it back to Alice. • Questions: – How does Alice know that the document has not been altered? integrity. – How does Alice know that Bob has signed the document (and not somebody else)? authentication. Cryptography © Dept. CS, UPC 31

Digital signatures Bob Alice SHA-2 (hash) h h h h SHA-2 h’ (signature) = Cryptography © Dept. CS, UPC 32

The pending challenge How to generate large prime numbers? (not explained in this lecture) Cryptography © Dept. CS, UPC 33

EXERCISES Cryptography © Dept. CS, UPC 34

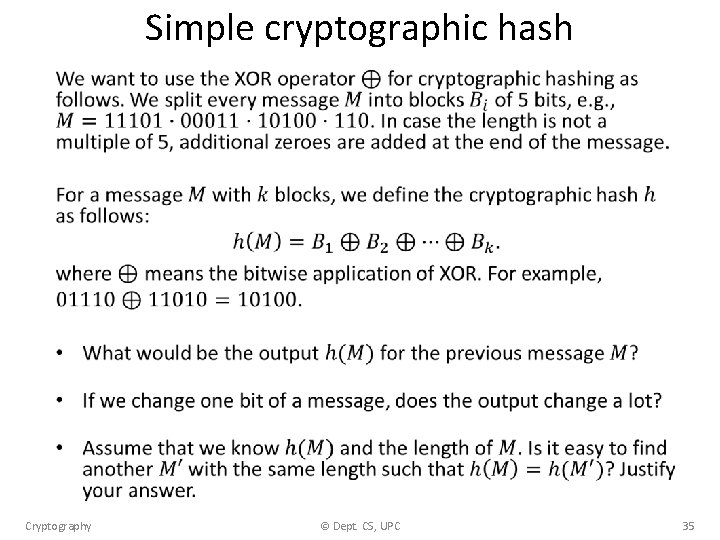
Simple cryptographic hash • Cryptography © Dept. CS, UPC 35

Simple RSA • Cryptography © Dept. CS, UPC 36

Implement an RSA cryptosystem • Cryptography © Dept. CS, UPC 37
 Jordi cortadella
Jordi cortadella Jordi petit upc
Jordi petit upc Jordi reviriego
Jordi reviriego Jordi ustrell
Jordi ustrell Jordi benlliure
Jordi benlliure Jordi juanico sabate
Jordi juanico sabate Jordi timmers
Jordi timmers Jordi ayala
Jordi ayala Jordi vives i batlle
Jordi vives i batlle Jordi garcia cehic
Jordi garcia cehic Jordi graells costa
Jordi graells costa Jordi npa
Jordi npa Jordi scene
Jordi scene Kerma
Kerma Dosmasuno arquitectos
Dosmasuno arquitectos Jordi gisbert
Jordi gisbert La hija del sastre summary
La hija del sastre summary Wireless security in cryptography
Wireless security in cryptography Cryptography and network security 6th edition
Cryptography and network security 6th edition криптографический модуль
криптографический модуль Number theory in cryptography and network security
Number theory in cryptography and network security Firewall base layer
Firewall base layer Authentication in cryptography and network security
Authentication in cryptography and network security Cryptography standards and protocols
Cryptography standards and protocols Confusion and diffusion
Confusion and diffusion Public key cryptography and message authentication
Public key cryptography and message authentication Divisibility and division algorithm in cryptography
Divisibility and division algorithm in cryptography Intruders in cryptography
Intruders in cryptography Elliptic curves number theory and cryptography
Elliptic curves number theory and cryptography Security services of cryptography
Security services of cryptography Primitive root
Primitive root Cryptography and network security 6th edition pdf
Cryptography and network security 6th edition pdf Pearson cryptography and network security
Pearson cryptography and network security Source
Source Cryptography and network security 4th edition
Cryptography and network security 4th edition What are cryptography and cryptanalysis
What are cryptography and cryptanalysis Euler's theorem in cryptography
Euler's theorem in cryptography Finite fields in cryptography and network security
Finite fields in cryptography and network security