CRYPTOGRAPHY II SECURE COMMUNICATION Hakan Tolgay hakanhakantolgay co



![RSA – Eurlers Theorem m^ɸ[n] = 1 mod n Pick any two numbers. Let RSA – Eurlers Theorem m^ɸ[n] = 1 mod n Pick any two numbers. Let](https://slidetodoc.com/presentation_image/31bd5410437189950ba99148b02a6daa/image-12.jpg)








- Slides: 39

CRYPTOGRAPHY II & SECURE COMMUNICATION Hakan Tolgay hakan@hakantolgay. co m

Agenda Rivest-Shamir-Adleman (RSA) Hashing and hash functions (MD 5/SHA 1/SHA 256) Networking in basics Digital Signatures and Security Services Certificate and trust mechanism SSL/TLS

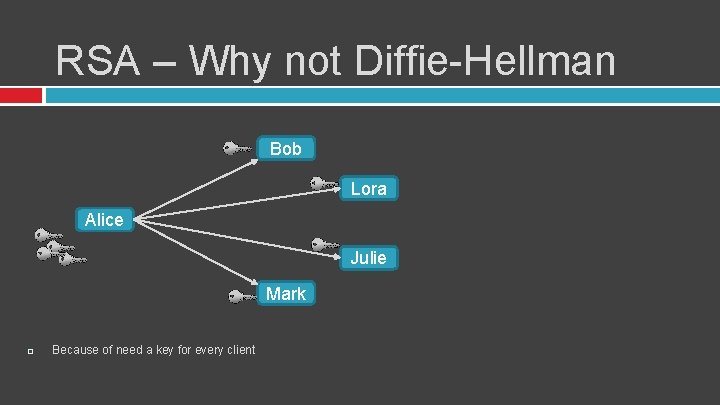
RSA – Why not Diffie-Hellman Bob Lora Alice Julie Mark Because of need a key for every client

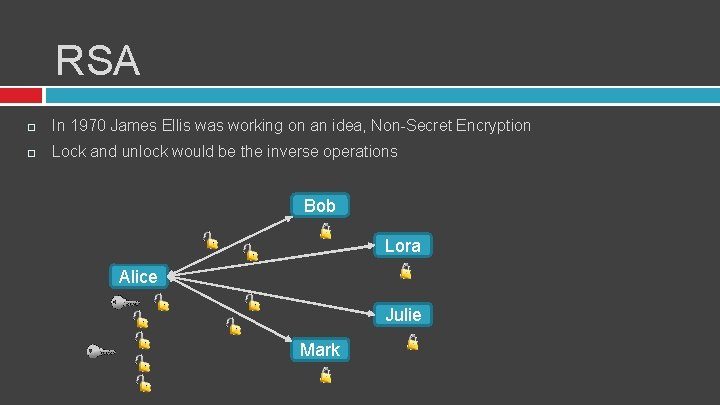
RSA In 1970 James Ellis was working on an idea, Non-Secret Encryption Lock and unlock would be the inverse operations Bob Lora Alice Julie Mark

RSA The idea was basically spliting the key into two part � Encryption key � Decryption key

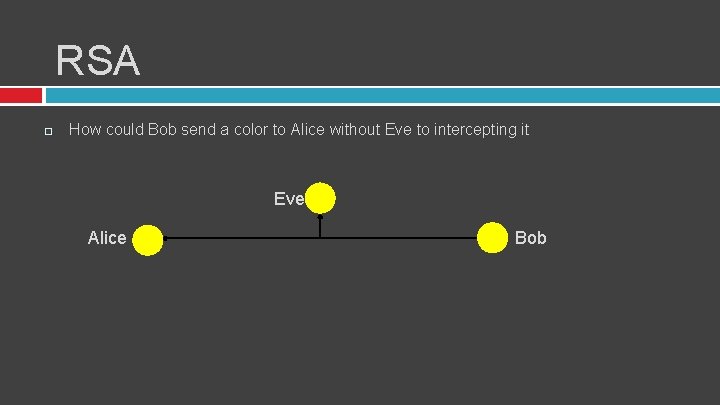
RSA How could Bob send a color to Alice without Eve to intercepting it Eve Alice Bob

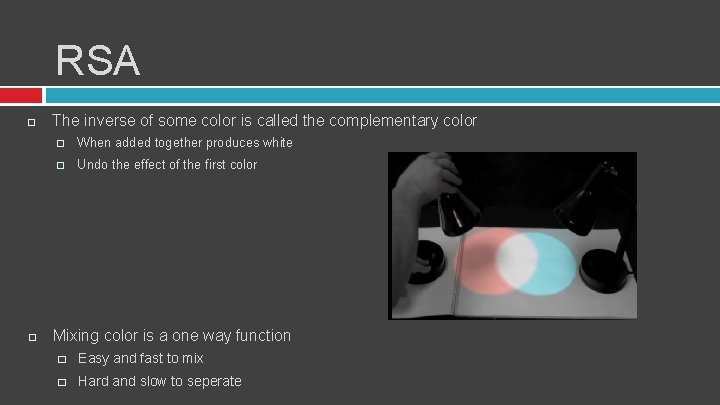
RSA The inverse of some color is called the complementary color � When added together produces white � Undo the effect of the first color Mixing color is a one way function � Easy and fast to mix � Hard and slow to seperate

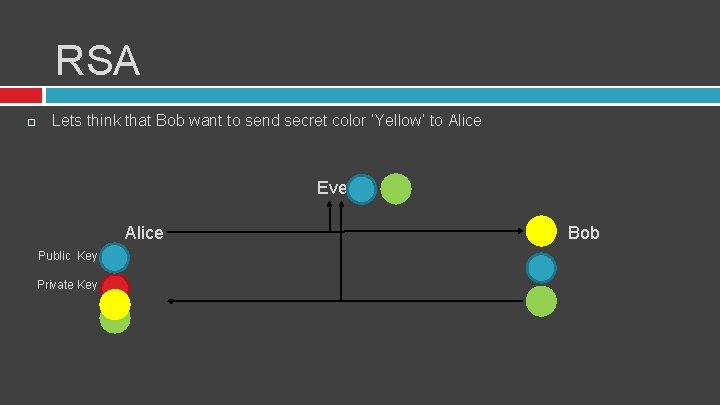
RSA Lets think that Bob want to send secret color ‘Yellow’ to Alice Eve Alice Public Key Private Key Bob

RSA – Mathematical Solution Prime factorization is the key point � It is always easy to multiple numbers � How about finding foctorization of primes? 589 ? 437231?

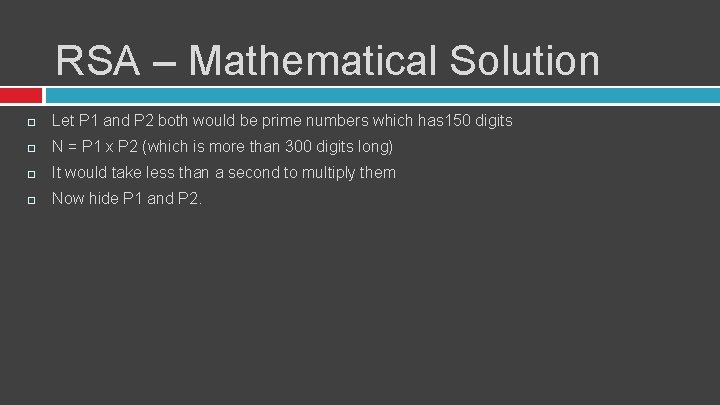
RSA – Mathematical Solution Let P 1 and P 2 both would be prime numbers which has 150 digits N = P 1 x P 2 (which is more than 300 digits long) It would take less than a second to multiply them Now hide P 1 and P 2.

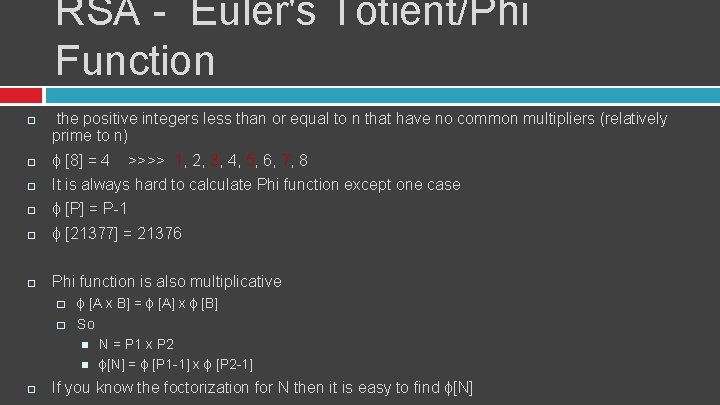
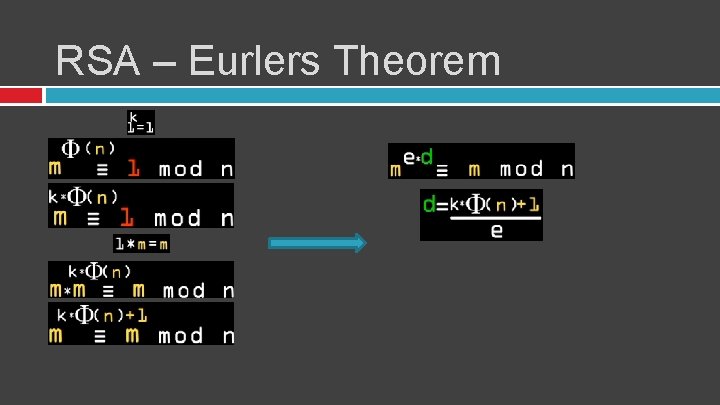
RSA - Euler's Totient/Phi Function the positive integers less than or equal to n that have no common multipliers (relatively prime to n) ɸ [8] = 4 >>>> 1, 2, 3, 4, 5, 6, 7, 8 It is always hard to calculate Phi function except one case ɸ [P] = P-1 ɸ [21377] = 21376 Phi function is also multiplicative � � ɸ [A x B] = ɸ [A] x ɸ [B] So N = P 1 x P 2 ɸ[N] = ɸ [P 1 -1] x ɸ [P 2 -1] If you know the foctorization for N then it is easy to find ɸ[N]
![RSA Eurlers Theorem mɸn 1 mod n Pick any two numbers Let RSA – Eurlers Theorem m^ɸ[n] = 1 mod n Pick any two numbers. Let](https://slidetodoc.com/presentation_image/31bd5410437189950ba99148b02a6daa/image-12.jpg)
RSA – Eurlers Theorem m^ɸ[n] = 1 mod n Pick any two numbers. Let m=5 n=8 � 5^4 = 1 mod 8 >> 625 =1 mod 8

RSA – Eurlers Theorem

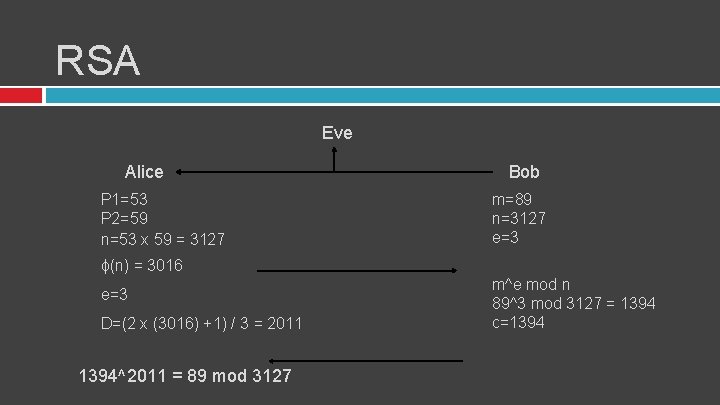
RSA Eve Alice P 1=53 P 2=59 n=53 x 59 = 3127 Bob m=89 n=3127 e=3 ɸ(n) = 3016 e=3 D=(2 x (3016) +1) / 3 = 2011 1394^2011 = 89 mod 3127 m^e mod n 89^3 mod 3127 = 1394 c=1394

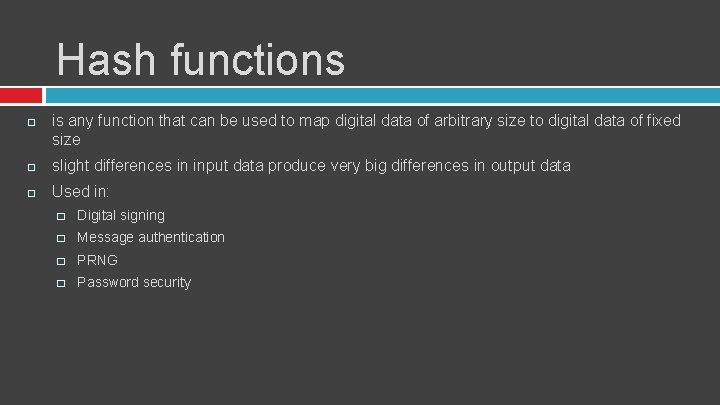
Hash functions is any function that can be used to map digital data of arbitrary size to digital data of fixed size slight differences in input data produce very big differences in output data Used in: � Digital signing � Message authentication � PRNG � Password security

Cryptographic Hash functions vs Cryptographic hash function � Transformation should be efficient, fast � Hide information about the input � Should be well distrubuted MD 5 SHA 1, SHA 2, SHA 3 Blake fff 5 bbf 073 c 6 add 1 c 635 e 9 d 43 dcba 5 b 3

Collision resistance A hash function is collision resistant if it is hard to find two inputs that hash to the same output Every hash function with more inputs than outputs will necessarily have collisions if a hash function produces N bits of output, an attacker who computes "only" 2 N/2 hash operations on random input is likely to find two matching outputs Cryptographic hash functions are usually designed to be collision resistant. MD 5 and SHA 1 in particular both have published techniques more efficient than brute force for finding collisions

Collision resistance DEMO

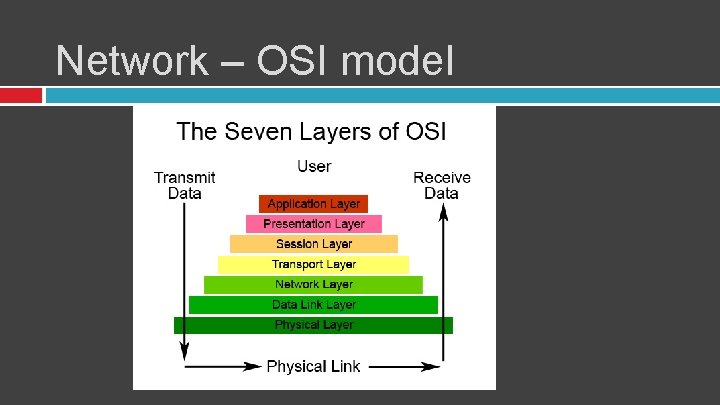
Network – OSI model

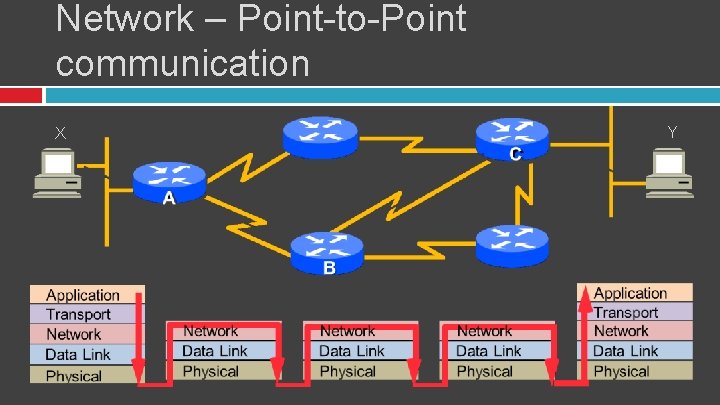
Network – Point-to-Point communication X Y

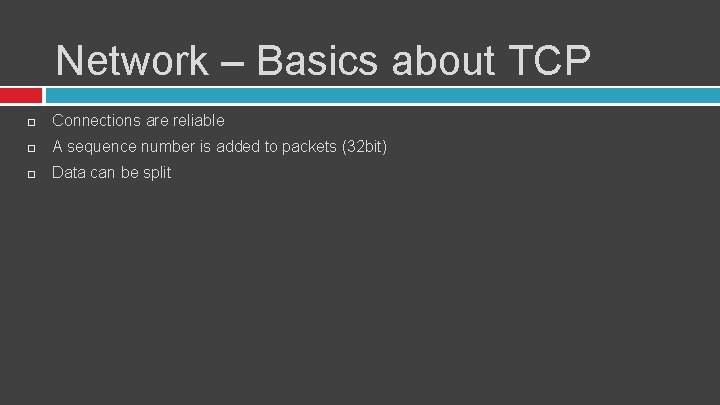
Network – Basics about TCP Connections are reliable A sequence number is added to packets (32 bit) Data can be split

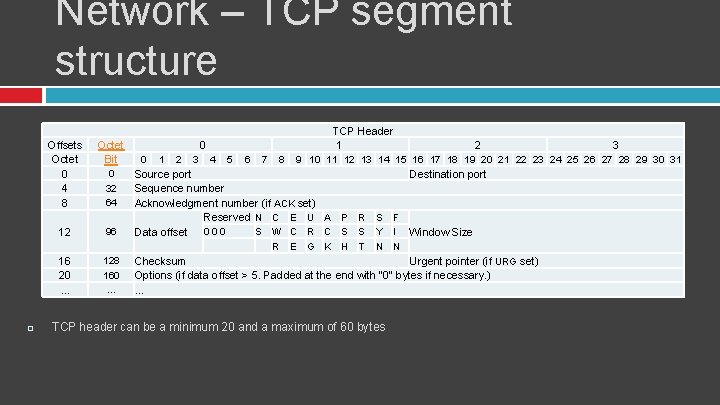
Network – TCP segment structure Offsets Octet 0 4 8 Octet Bit 12 96 0 32 64 TCP Header 1 0 Source port Sequence number Acknowledgment number (if ACK set) Reserved N C E U A P R S F S W C R C S S Y I Data offset 0 0 0 R E 16 20. . . 128 160. . . 2 3 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 G K H T Destination port Window Size N N Checksum Urgent pointer (if URG set) Options (if data offset > 5. Padded at the end with "0" bytes if necessary. ). . . TCP header can be a minimum 20 and a maximum of 60 bytes

Network – TCP segment structure Wireshark Demo

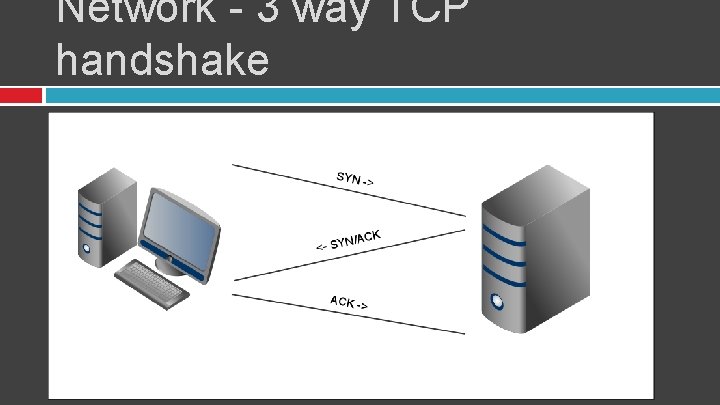
Network - 3 way TCP handshake

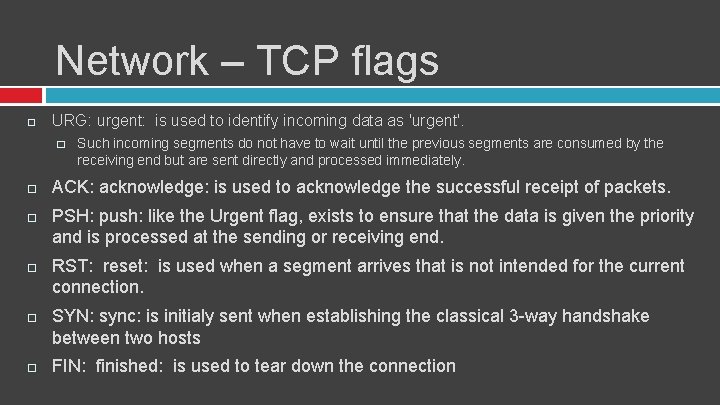
Network – TCP flags URG: urgent: is used to identify incoming data as 'urgent'. � Such incoming segments do not have to wait until the previous segments are consumed by the receiving end but are sent directly and processed immediately. ACK: acknowledge: is used to acknowledge the successful receipt of packets. PSH: push: like the Urgent flag, exists to ensure that the data is given the priority and is processed at the sending or receiving end. RST: reset: is used when a segment arrives that is not intended for the current connection. SYN: sync: is initialy sent when establishing the classical 3 -way handshake between two hosts FIN: finished: is used to tear down the connection

Digital Signatures and Security Services Goal: signature like function for electronic world a signed email, . . . Signk(x)=y ------------------------1001010011. . . . . . 101110

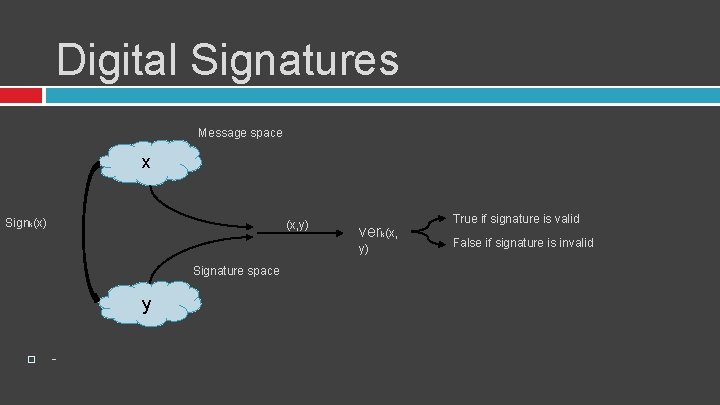
Digital Signatures Message space x Signk(x) (x, y) verk(x, y) Signature space y - True if signature is valid False if signature is invalid

Securtiy Services The objectives of security system are called «security services» 4 important points � 1. Confidentiality: Information is kept secret from all but the authorized parties � 2. Authentication: The send of the message is authentic � 3. Integrity: Message has not been modified during transmission � 4. Non-repudiation: The send of the message can not deny the creation of message

Certificate and trust mechanism Man-In-the-Middle (MITM) attack in asymmetric key approach � What if attacker is not only sniffing but also actively intercepting the traffic

Certificates Need of centrally trusted authority � Certifiying Authority «CA» � Certificate is only a public key of Allice digitally signed by a CA

Certification process Creating private key Prepare a Certification Signing Request (CSR) with you Private key Send CSR to CA CA sends your certificate

SSL/TLS Secure Sockets Layer (SSL) Transport Layer Security (TLS) They use X. 509 certificates and hence asymmetric cryptography to authenticate the counterparty with whom they are communicating This session key is then used to encrypt data flowing between the parties Uses hash fuctions for message integrity Defined Protocol Year SSL 1. 0 n/a SSL 2. 0 1995 SSL 3. 0 1996 TLS 1. 0 1999 TLS 1. 1 2006 TLS 1. 2 2008 TLS 1. 3 TBD

SSL The SSL protocol was originally developed by Netscape. Version 1. 0 was never publicly released because of serious security flaws in the protocol version 2. 0 was released in February 1995 SSL version 3. 0, released in 1996, was a complete redesign of the protocol produced by Paul Kocher

TLS 1. 0 was first defined in RFC 2246 in January 1999 as an upgrade of SSL Version 3. 0 As stated in the RFC, "the differences between this protocol and SSL 3. 0 are not dramatic TLS 1. 0 does include a means by which a TLS implementation can downgrade the connection to SSL 3. 0, thus weakening security TLS 1. 1 was defined in RFC 4346 in April 2006 � Added protection against cipher-block chaining (CBC) attacks. TLS 1. 2 was defined in RFC 5246 in August 2008. As of October 2014, TLS 1. 3 is a draft, and details have not fixed yet

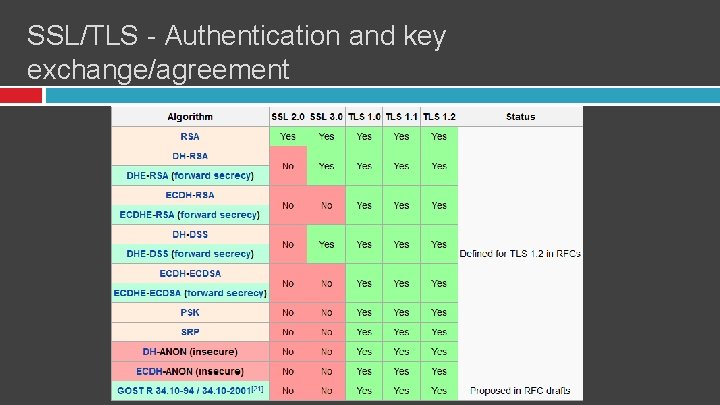
SSL/TLS - Authentication and key exchange/agreement

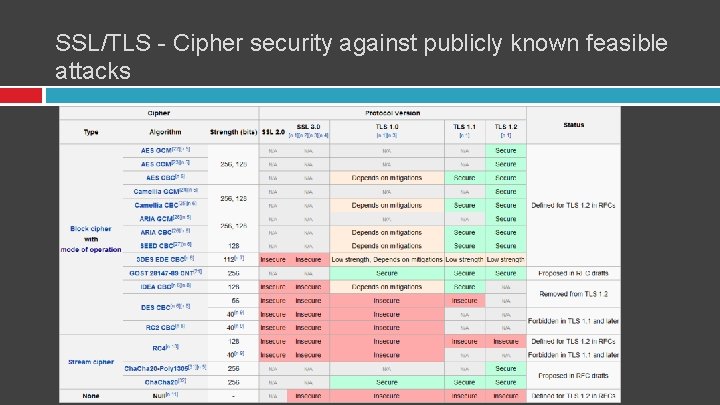
SSL/TLS - Cipher security against publicly known feasible attacks

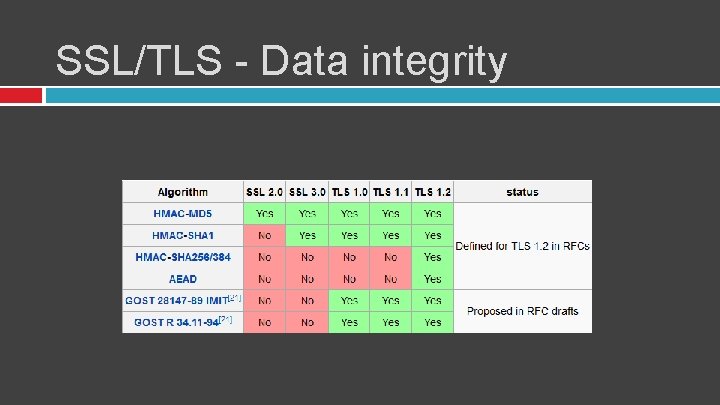
SSL/TLS - Data integrity

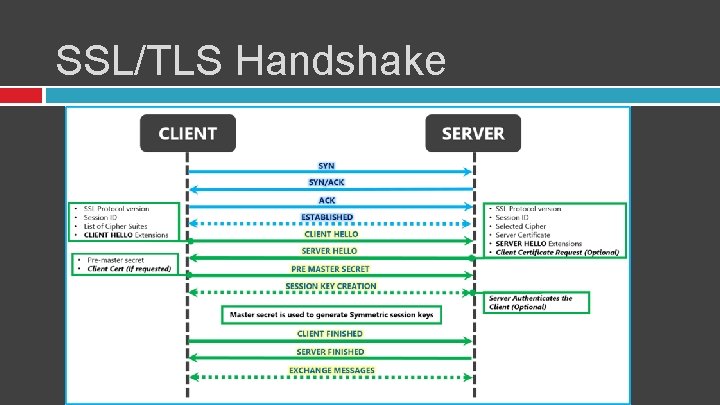
SSL/TLS Handshake

Thank you