Cryptography from Anonymity from carefully shuffling carefully chosen

















- Slides: 50

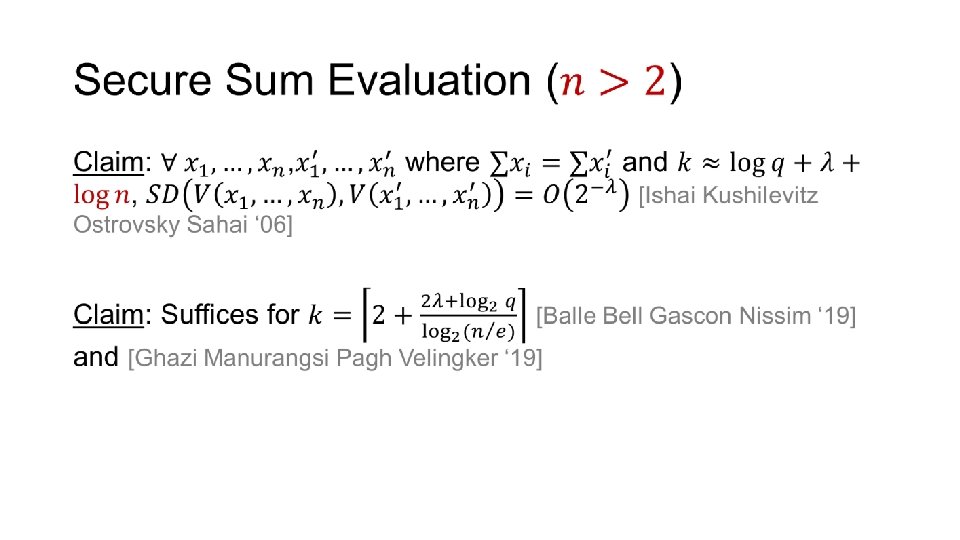
Cryptography from Anonymity = from (carefully) shuffling carefully chosen cards [ISHAI KUSHILEVITZ OSTROVSKY SAHAI ‘ 06] ALSO [BEIMEL HAITNER NISSIM STEMMER ‘ 20]

Outline • Define communication model • One possible instantiation • Single-Server Private Information Retrieval (PIR) • Secure Sum Evaluation • Key agreement from anonymity • Communication “without” key agreement [Beimel et al. ‘ 20] • Restricting the model

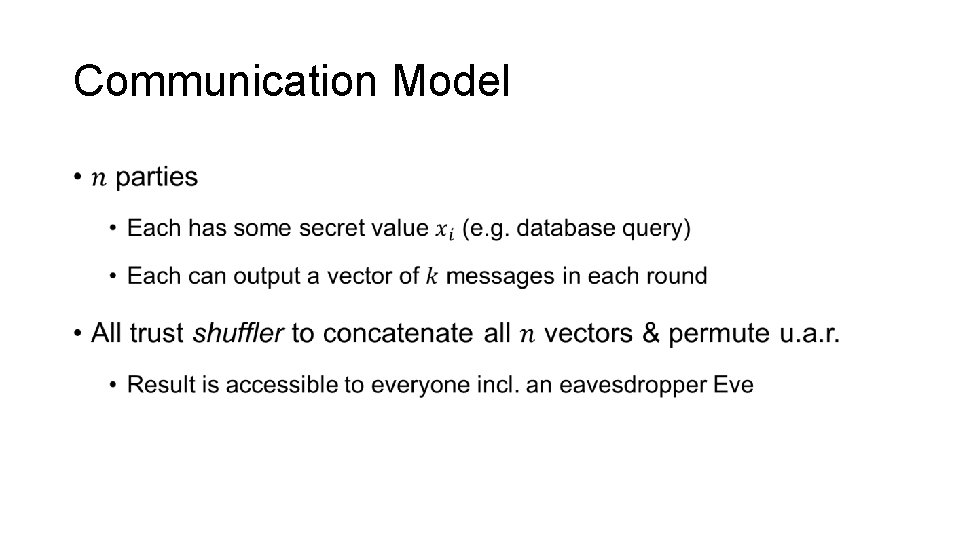
Communication Model •

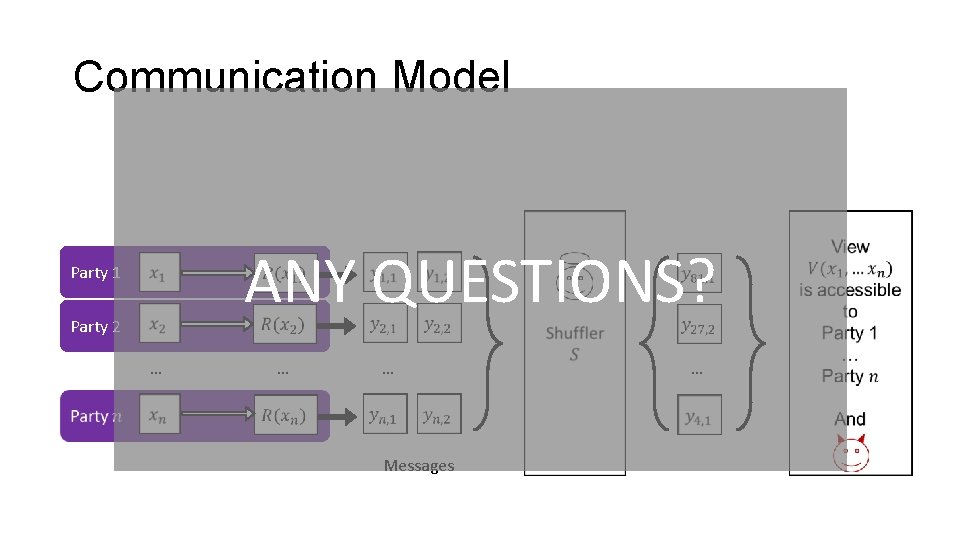
Communication Model ANY QUESTIONS? Party 1 Party 2 … … … Messages …

Communication Model •

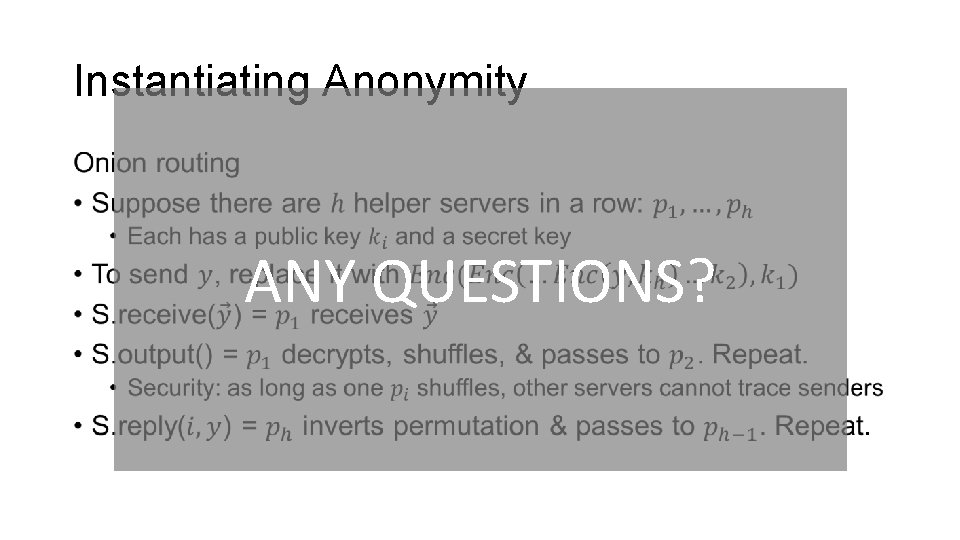
Instantiating Anonymity • ANY QUESTIONS?

Outline • Define communication model • One possible instantiation • Single-Server Private Information Retrieval (PIR) • Secure Sum Evaluation • Key agreement from anonymity • Communication “without” key agreement [Beimel et al. ‘ 20] • Restricting the model

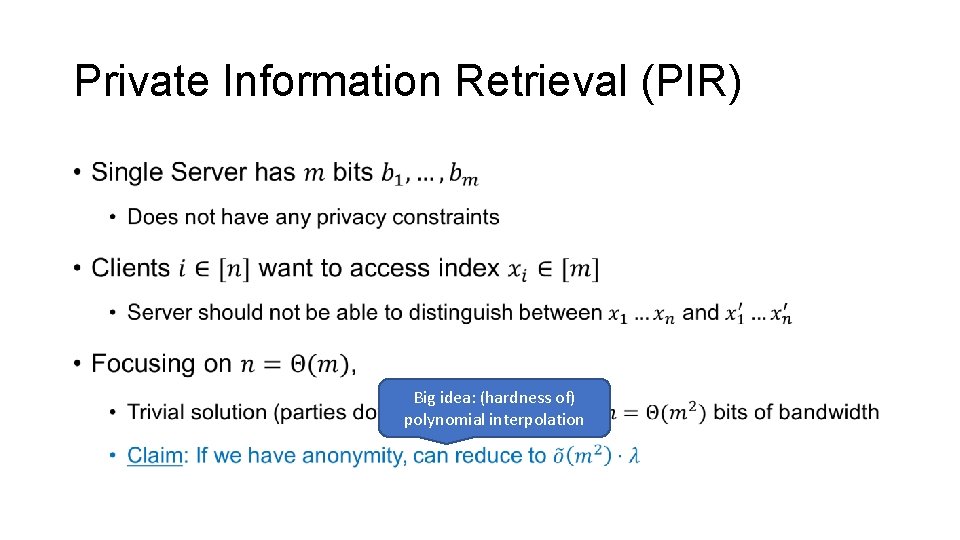
Private Information Retrieval (PIR) • Big idea: (hardness of) polynomial interpolation

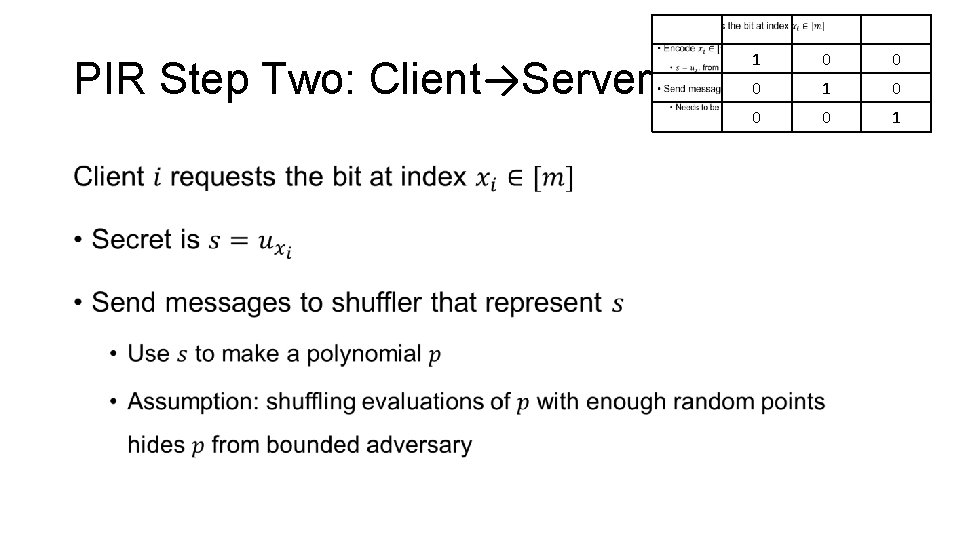
Private Information Retrieval (PIR) Four steps: 1. Setup: everyone creates same “toolbox” 2. Client → Server (via S. receive and S. output) 3. Server → Client (via S. reply) 4. Recover bit from replies

PIR Step One: The Toolbox • ANY QUESTIONS? 0 0 0 1 0 0 0

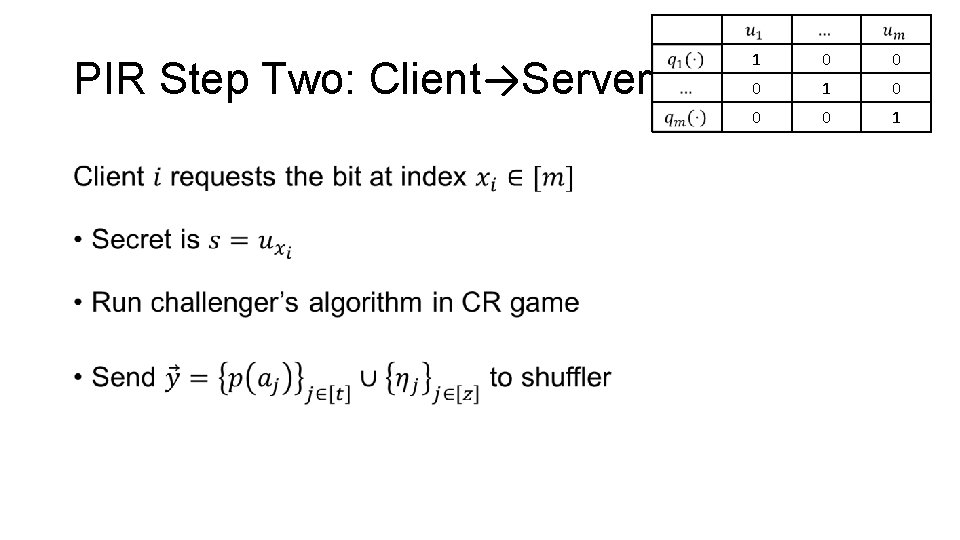
PIR Step Two: Client→Server • 1 0 0 0 1

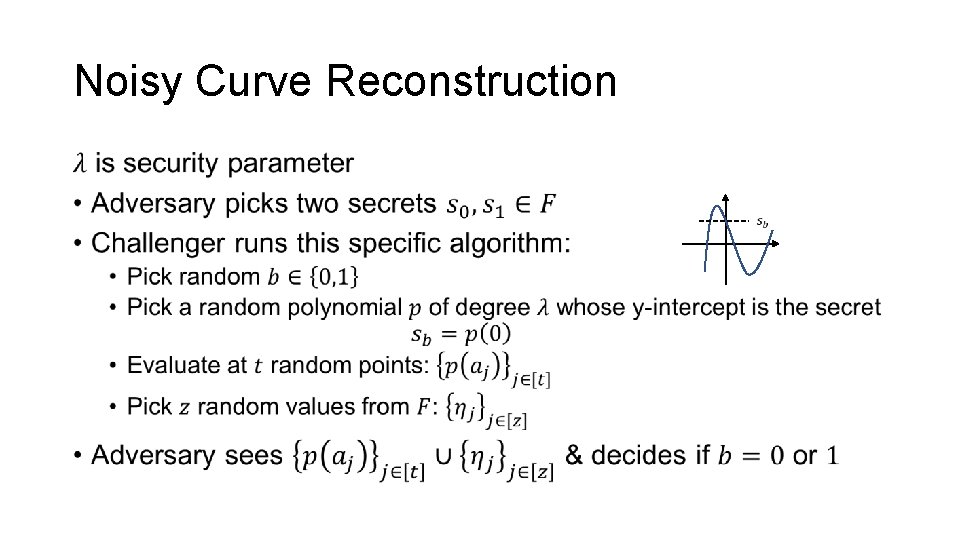
Noisy Curve Reconstruction •

Noisy Curve Reconstruction •

Noisy Curve Reconstruction • ANY QUESTIONS?

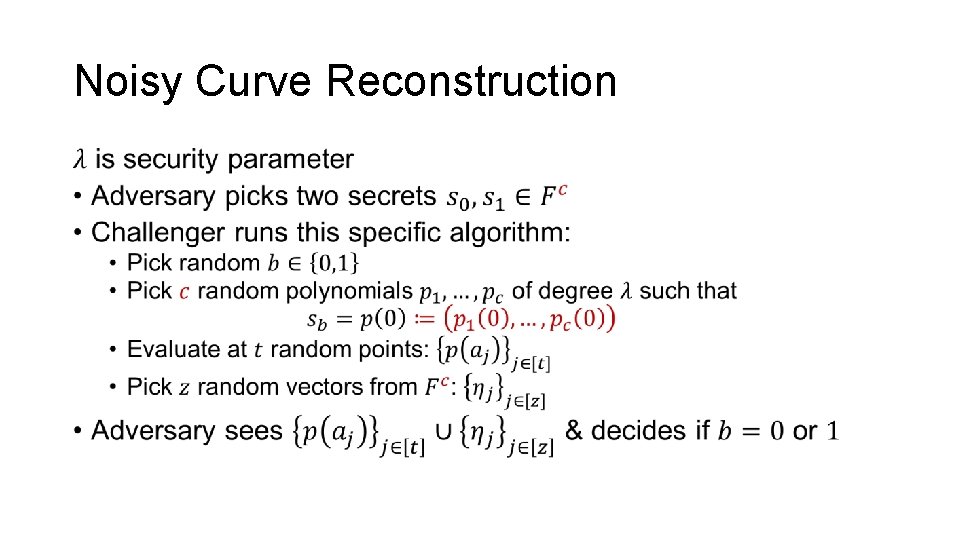
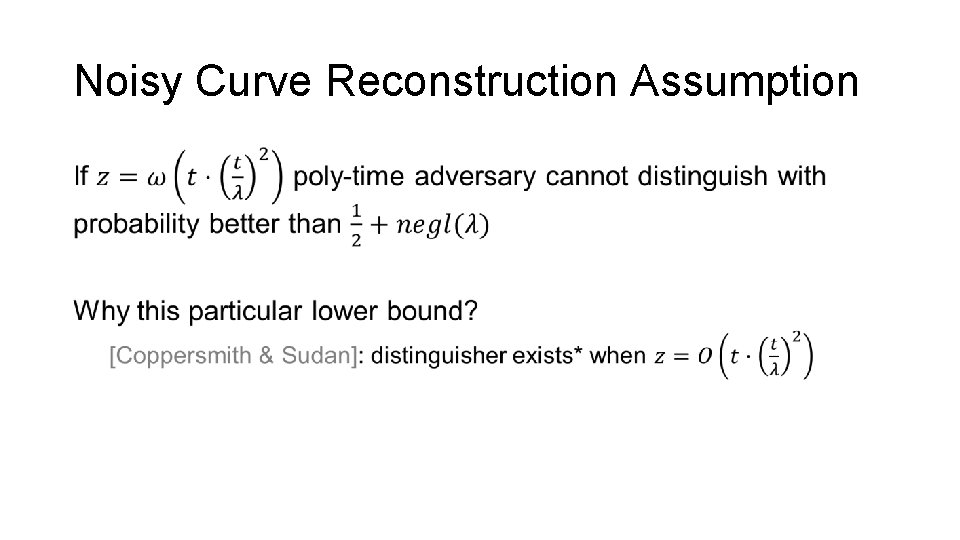
Noisy Curve Reconstruction Assumption •

PIR Step Two: Client→Server • 1 0 0 0 1

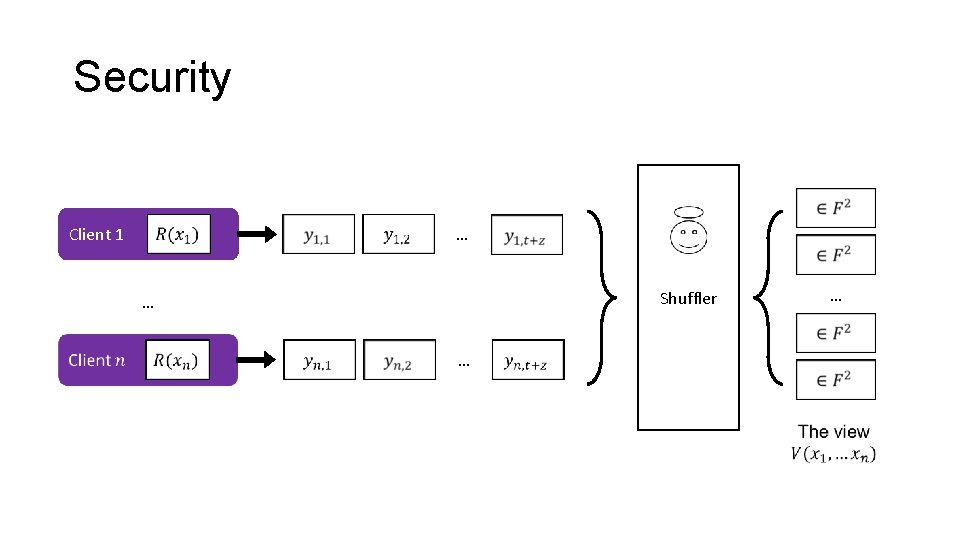
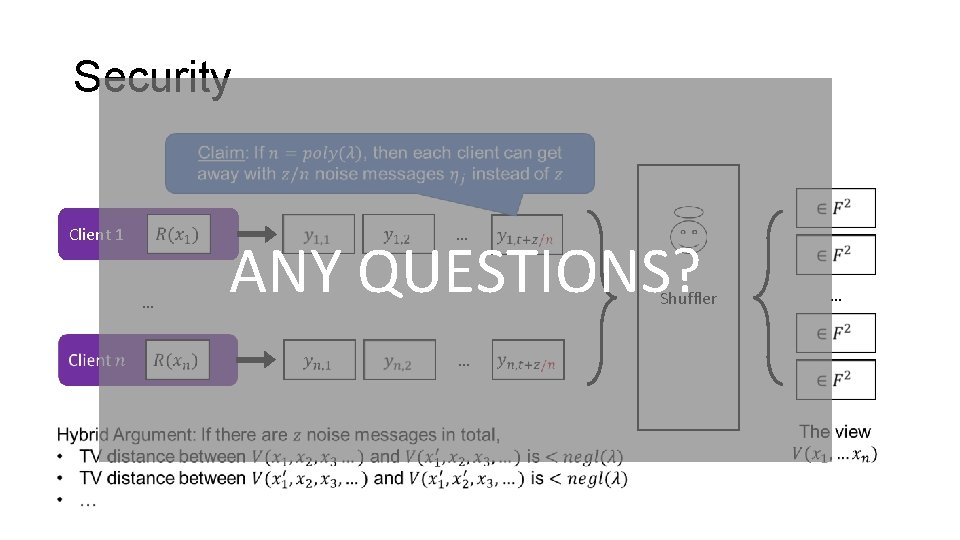
Security … Client 1 Shuffler … … …

Security … Client 1 … ANY QUESTIONS? Shuffler … …

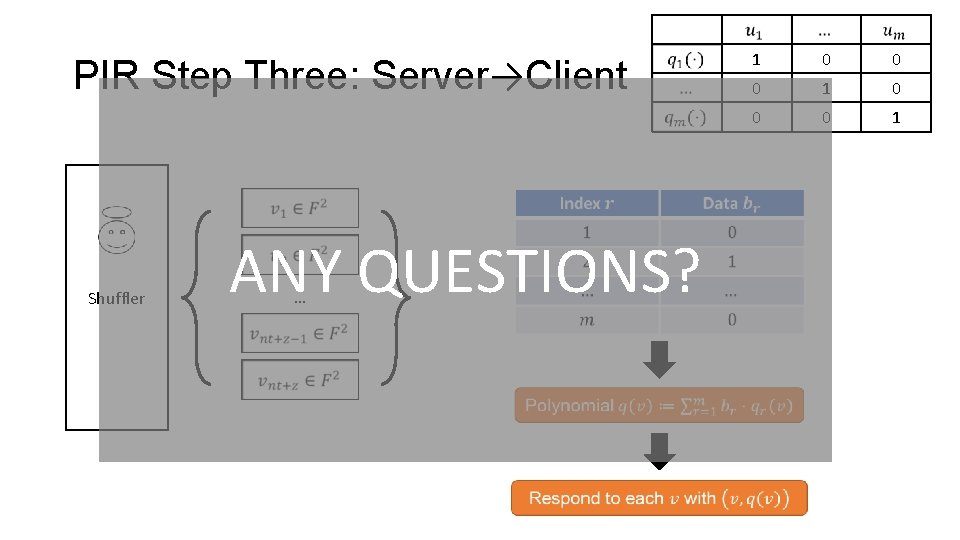
PIR Step Three: Server→Client Shuffler ANY QUESTIONS? … 1 0 0 0 1

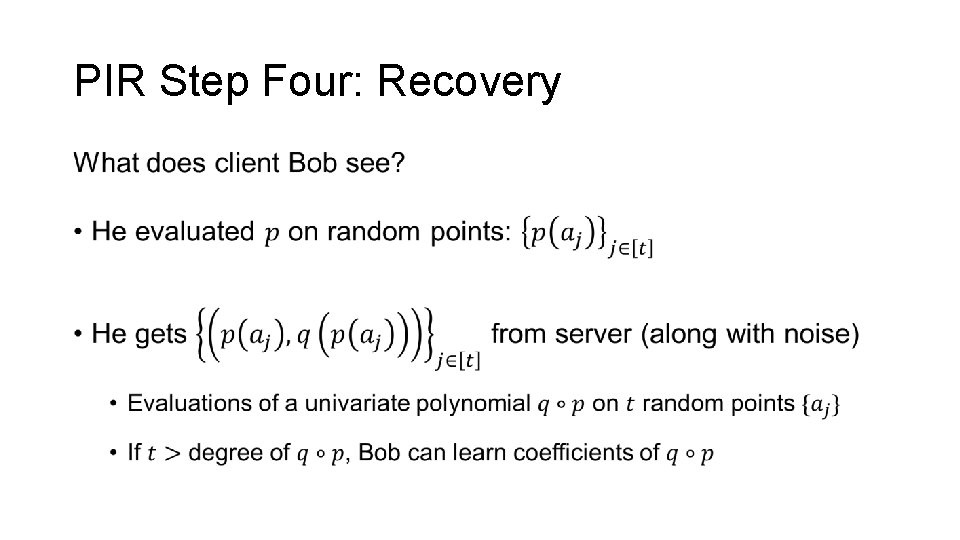
PIR Step Four: Recovery •

PIR Step Four: Recovery • ANY QUESTIONS? 1 0 0 0 1

Parameters •

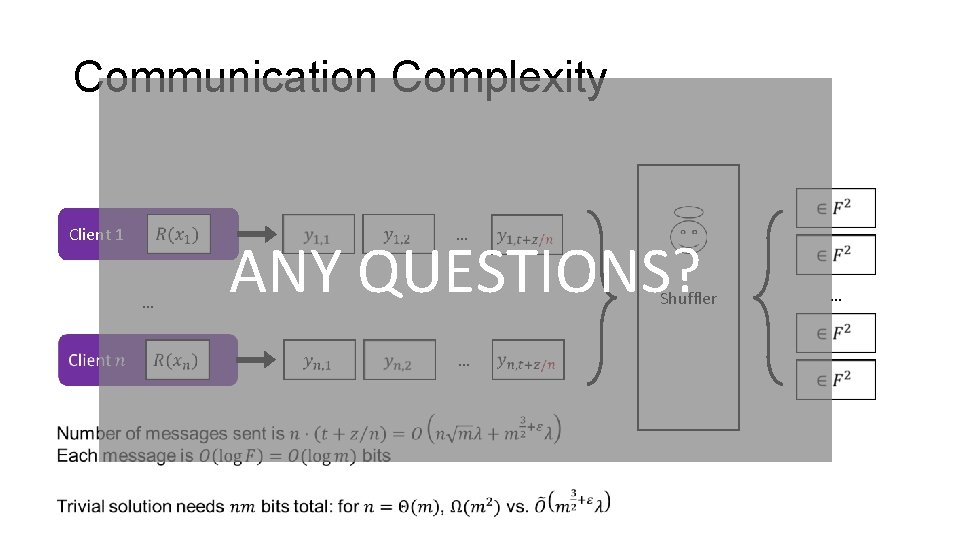
Communication Complexity … Client 1 … ANY QUESTIONS? Shuffler … …

Outline • Define communication model • One possible instantiation • Single-Server Private Information Retrieval (PIR) • Secure Sum Evaluation • Key agreement from anonymity • Communication “without” key agreement [Beimel et al. ‘ 20] • Restricting the model

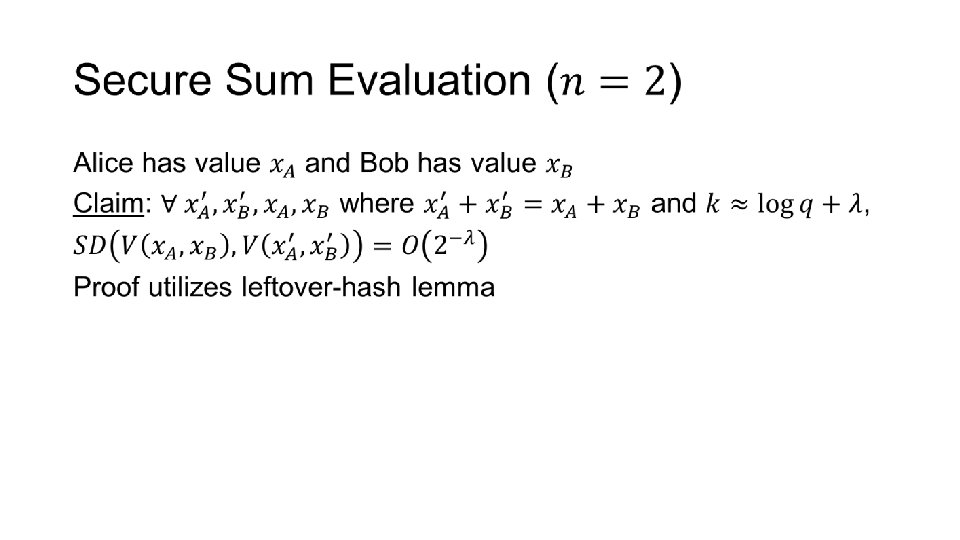
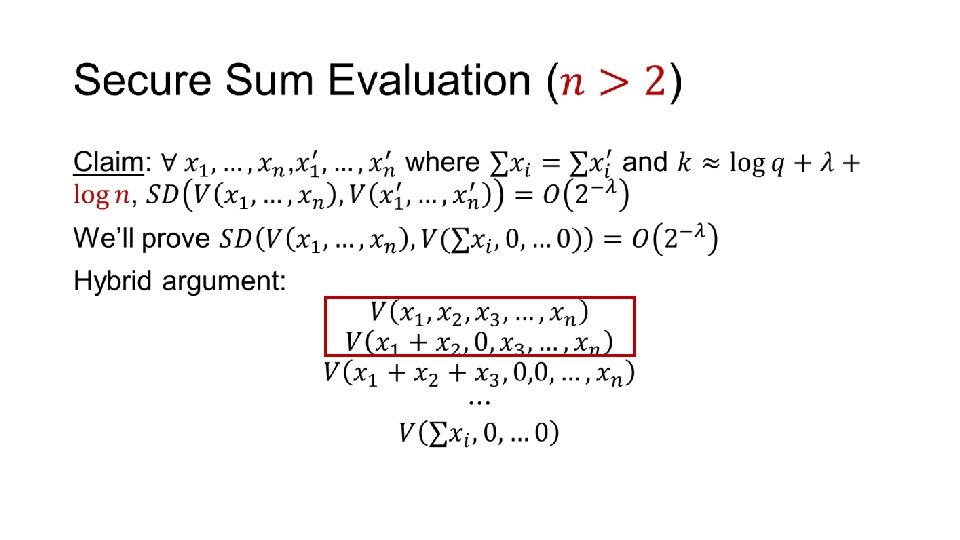
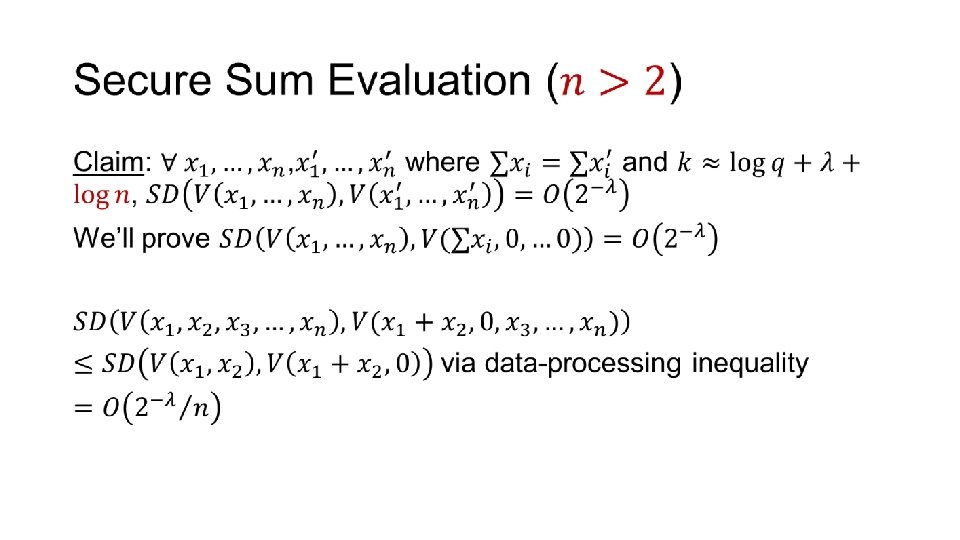
Secure Sum Evaluation • ANY QUESTIONS?

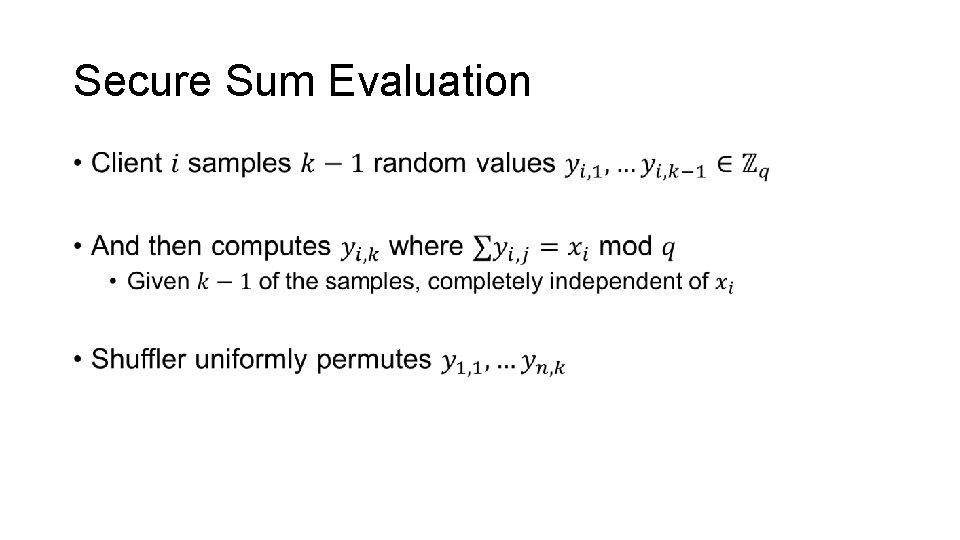
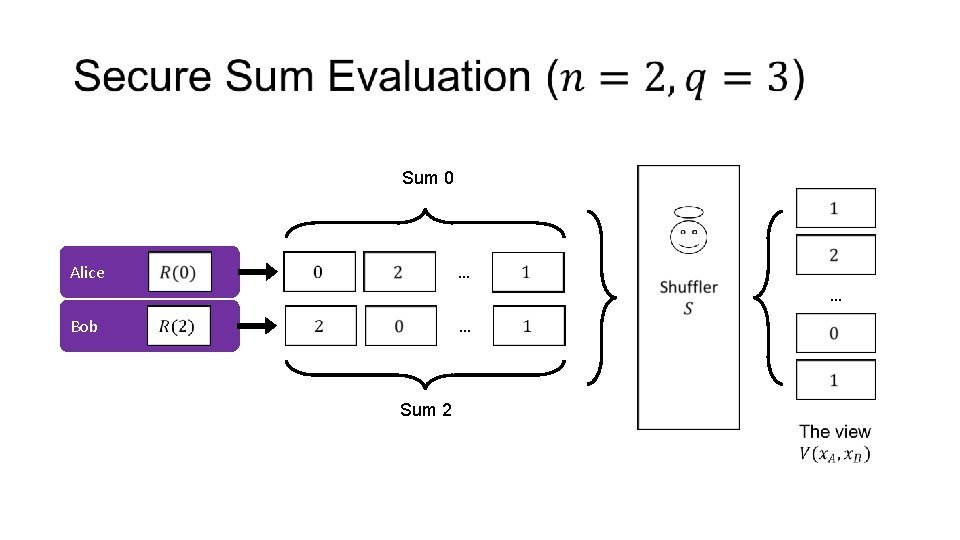
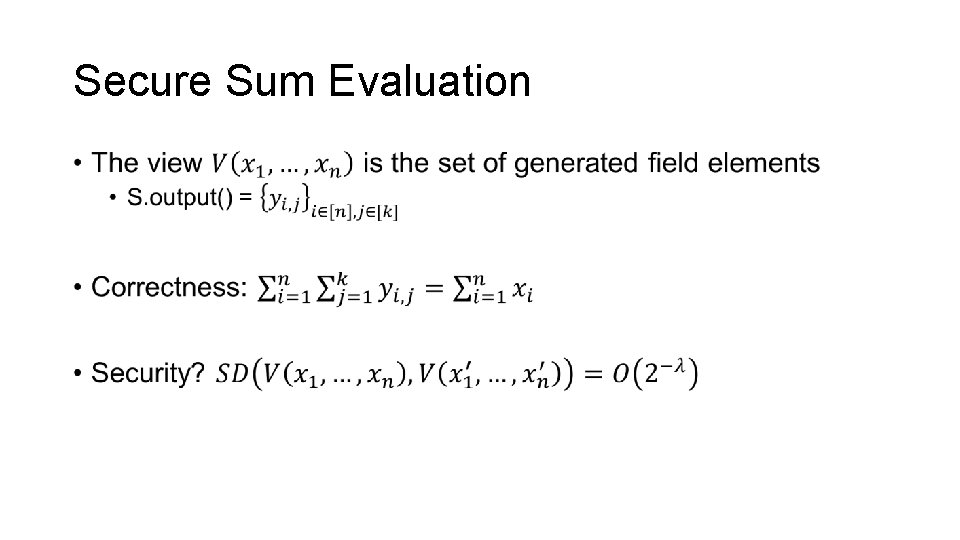
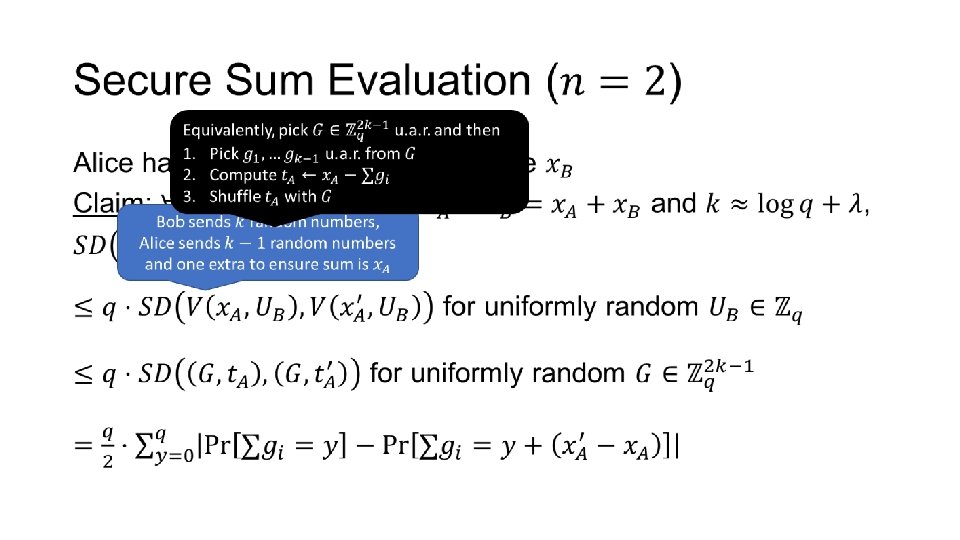
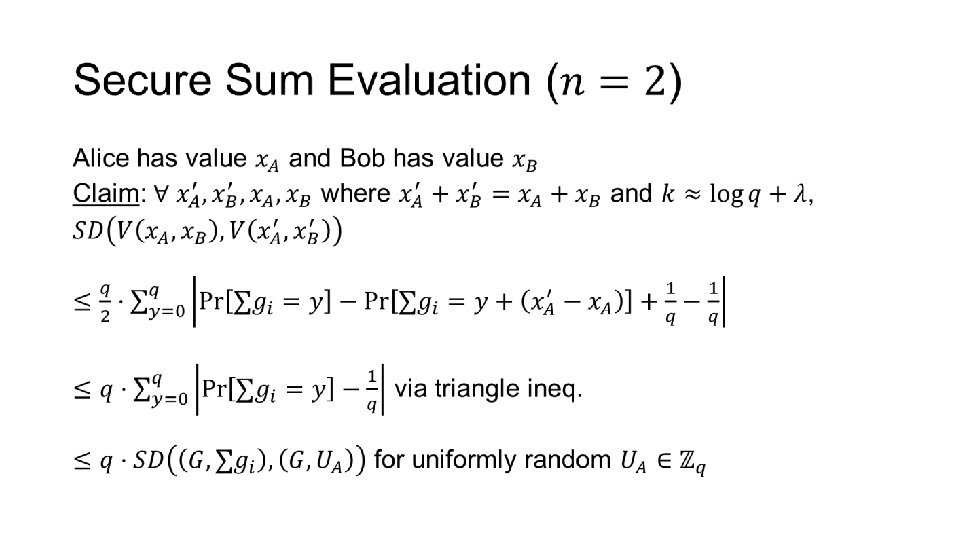
Secure Sum Evaluation •

Sum 0 … Alice … … Bob Sum 2

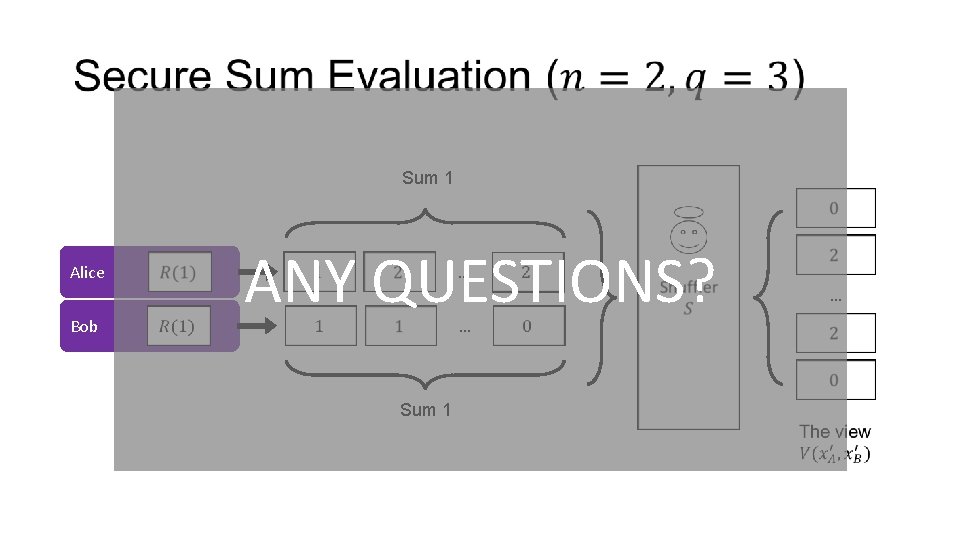
Sum 1 Alice Bob ANY QUESTIONS? … … Sum 1 …

Secure Sum Evaluation •







Outline • Define communication model • One possible instantiation • Single-Server Private Information Retrieval (PIR) • Secure Sum Evaluation • Key agreement from anonymity • Communication “without” key agreement [Beimel et al. ‘ 20] • Restricting the model

Key Agreement Assuming that a shuffler exists, how do we use it to set up a symmetric key? • A little strange if shuffler is made by (public-key) onion routing

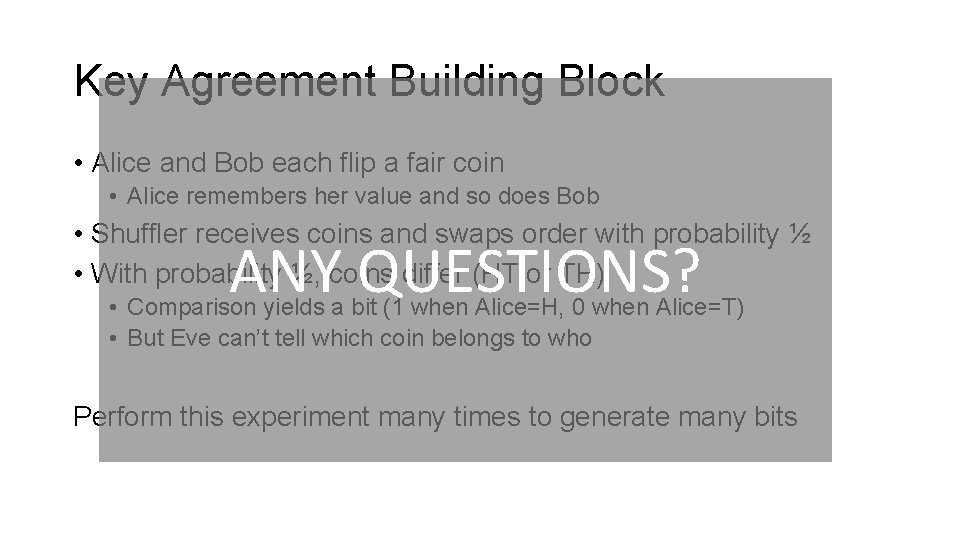
Key Agreement Building Block • Alice and Bob each flip a fair coin • Alice remembers her value and so does Bob • Shuffler receives coins and swaps order with probability ½ • With probability ½, coins differ (HT or TH) ANY QUESTIONS? • Comparison yields a bit (1 when Alice=H, 0 when Alice=T) • But Eve can’t tell which coin belongs to who Perform this experiment many times to generate many bits

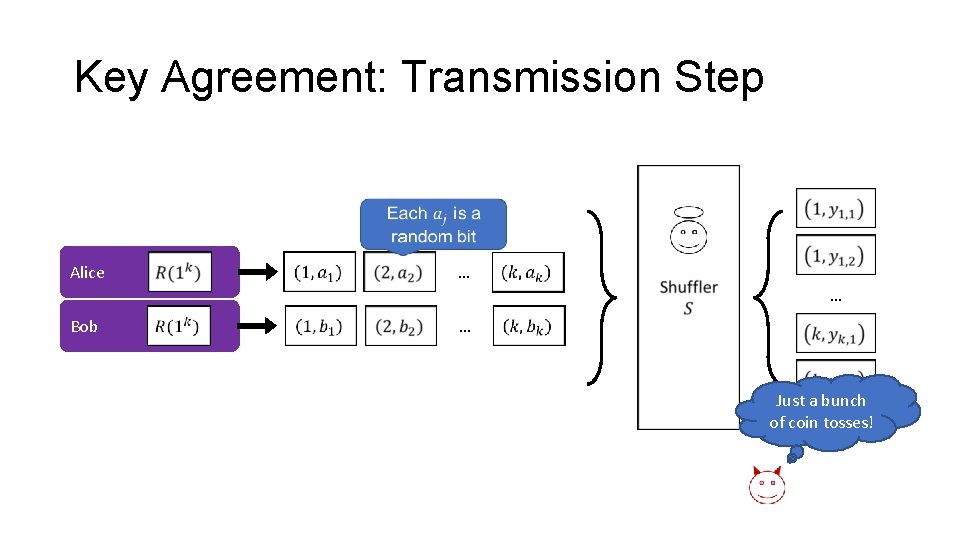
Key Agreement: Transmission Step Alice … … Bob … Just a bunch of coin tosses!

Key Agreement: Recovery Step • ANY QUESTIONS?

Key Agreement •

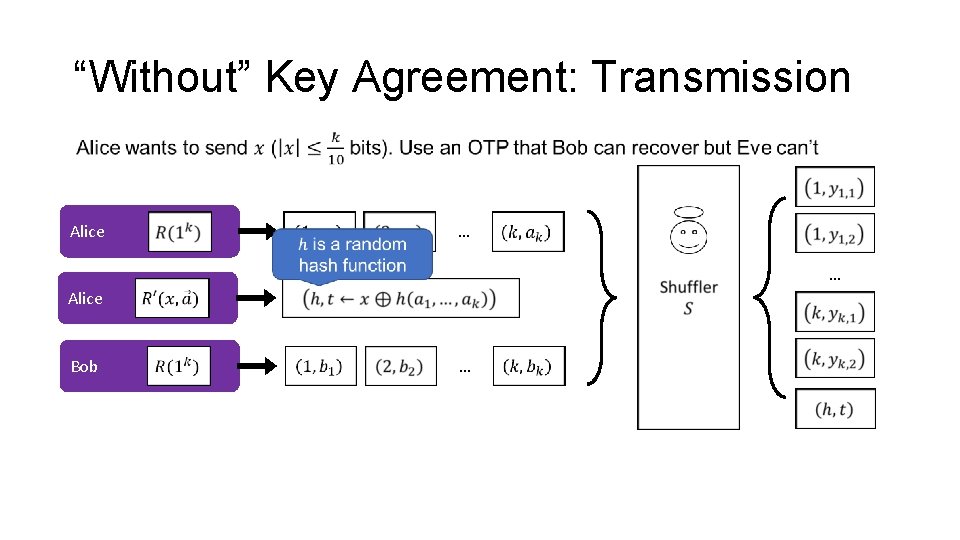
“Without” Key Agreement: Transmission Alice … … Alice Bob …

“Without” Key Agreement: Security • ANY QUESTIONS?

“Without” Key Agreement: Recovery • ANY QUESTIONS?

“Without” Key Agreement •

Outline • Define communication model • One possible instantiation • Single-Server Private Information Retrieval (PIR) • Secure Sum Evaluation • Key agreement from anonymity • Communication “without” key agreement [Beimel et al. ‘ 20] • Restricting the model

Restricting the Communication Model •

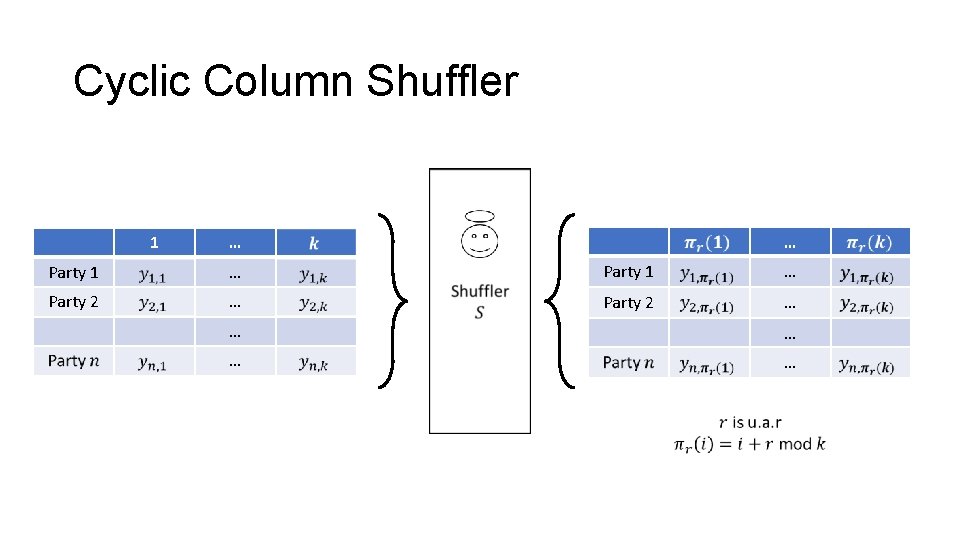
Cyclic Column Shuffler 1 … … Party 1 … Party 2 … … …

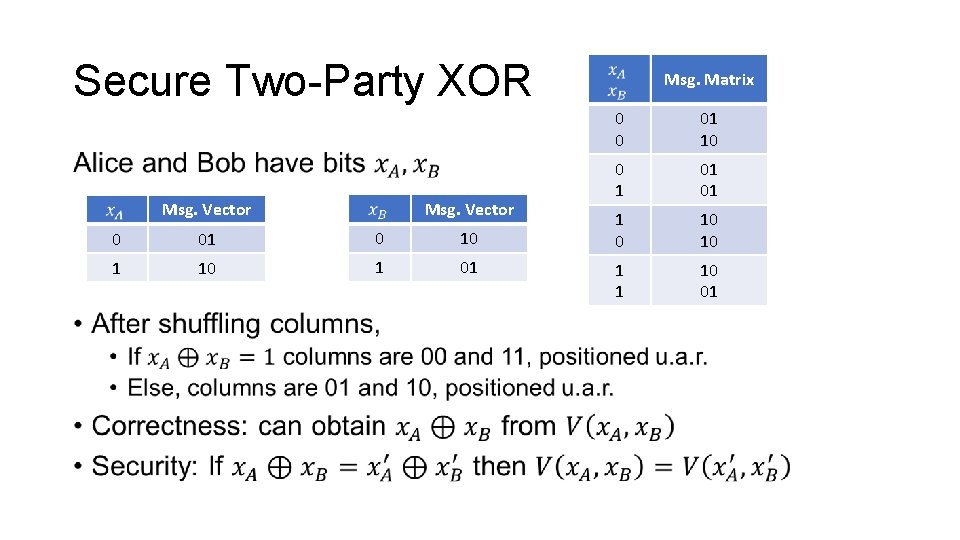
Secure Two-Party XOR • Msg. Vector 0 01 0 10 1 01 Msg. Matrix 0 0 01 10 0 1 01 01 1 0 10 10 1 1 10 01

Secure Two-Party Addition •