Cryptography Deffie hellman organization Foundations Symmetric key weaknesses


![Foundation • Encryption: Sk[P] -> [C] • Polynomial if k is given • Decryption: Foundation • Encryption: Sk[P] -> [C] • Polynomial if k is given • Decryption:](https://slidetodoc.com/presentation_image/57cef3887c9c2c521d612c9299e3b1d6/image-3.jpg)



- Slides: 27

Cryptography Deffie hellman

organization • Foundations • Symmetric key weaknesses • Assymmetric key • Deffie hellman – key exchange • RSA – public key, private key • Applications of new idea
![Foundation Encryption SkP C Polynomial if k is given Decryption Foundation • Encryption: Sk[P] -> [C] • Polynomial if k is given • Decryption:](https://slidetodoc.com/presentation_image/57cef3887c9c2c521d612c9299e3b1d6/image-3.jpg)
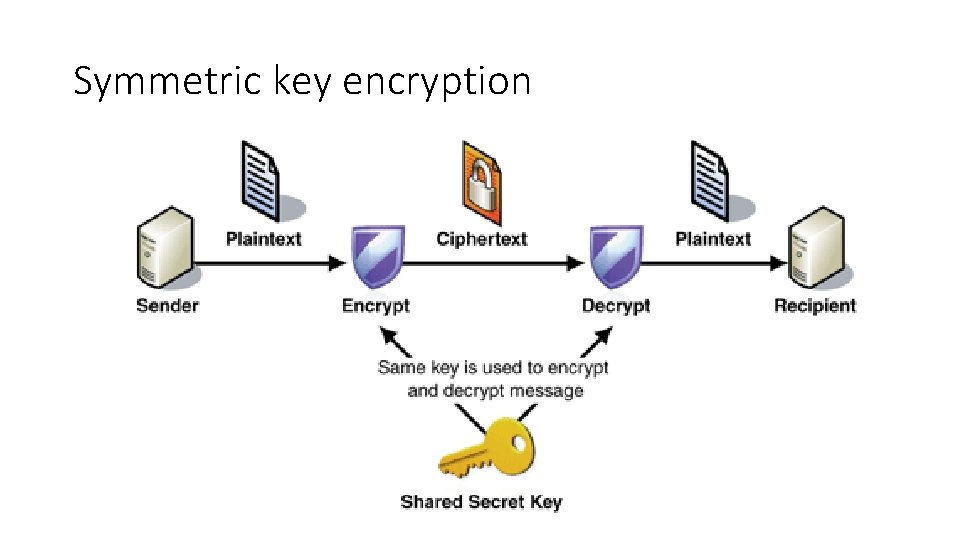
Foundation • Encryption: Sk[P] -> [C] • Polynomial if k is given • Decryption: Sk-1[C] -> [P] • Polynomial if k is given • Hacker? • Figure out Sk • Unconditionally secure • No matter what • K – key • P – plain text • C – Cypher text • Computationally secure • Summumb to unlimited computation

Symmetric key encryption

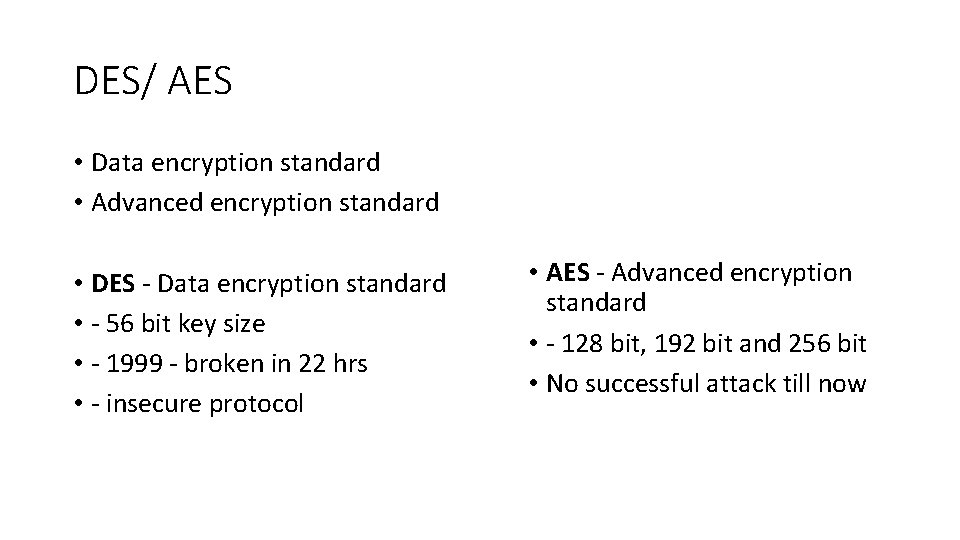
DES/ AES • Data encryption standard • Advanced encryption standard • DES - Data encryption standard • - 56 bit key size • - 1999 - broken in 22 hrs • - insecure protocol • AES - Advanced encryption standard • - 128 bit, 192 bit and 256 bit • No successful attack till now

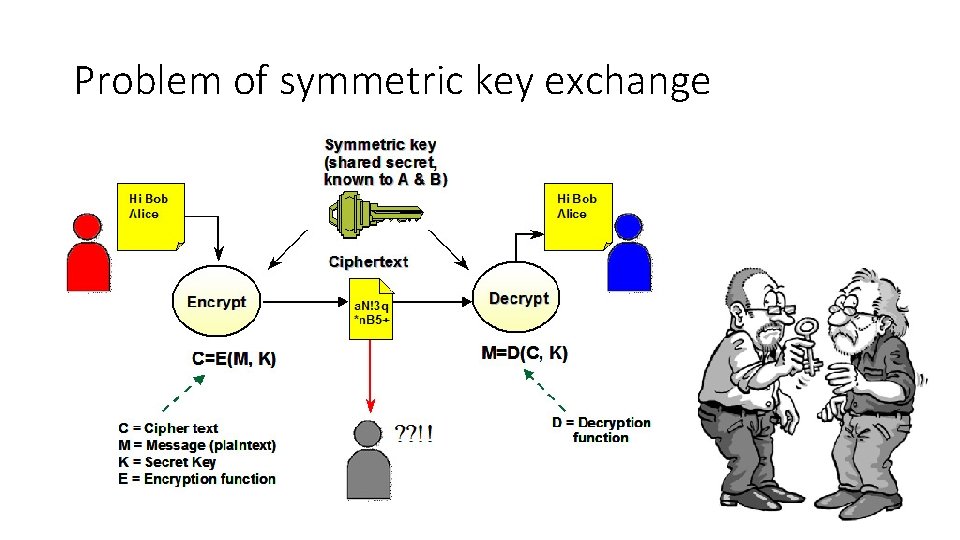
Problem of symmetric key exchange

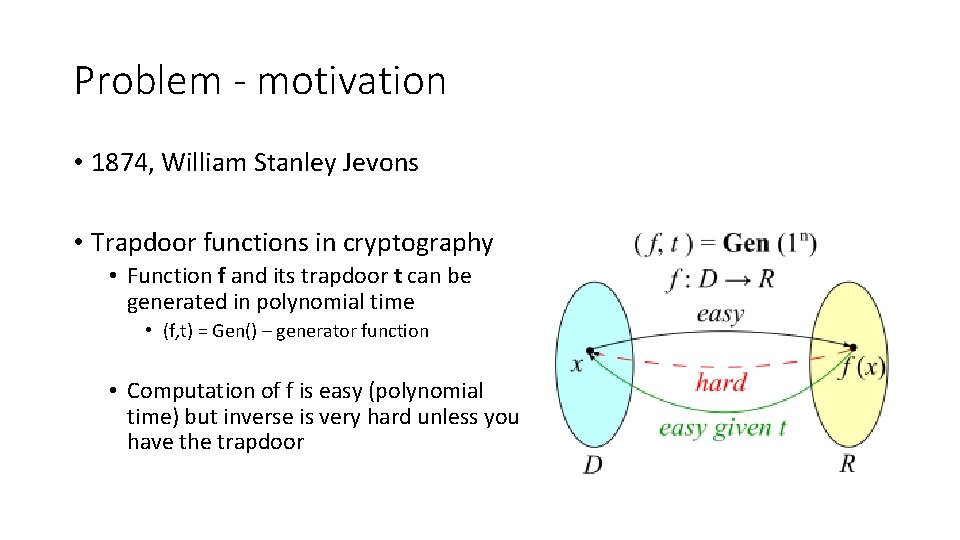
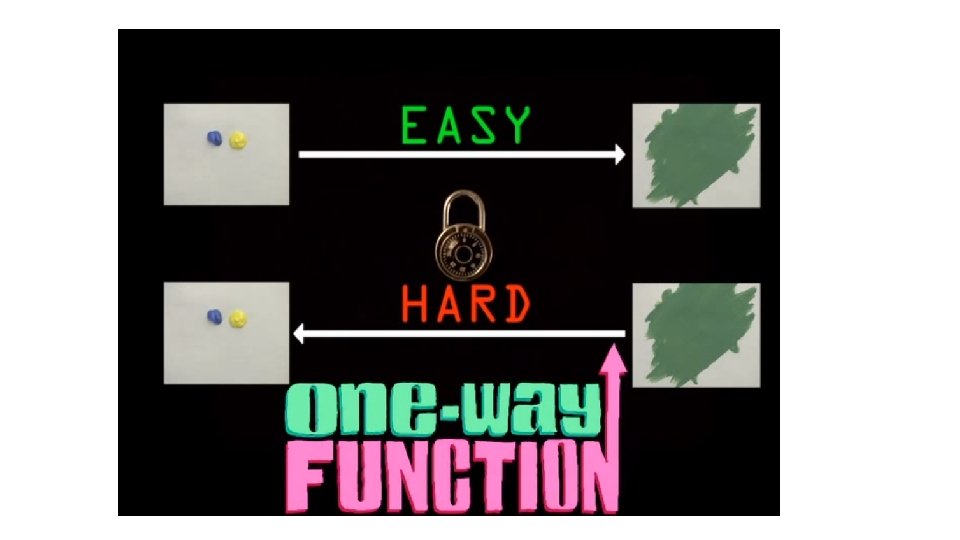
Problem - motivation • 1874, William Stanley Jevons • Trapdoor functions in cryptography • Function f and its trapdoor t can be generated in polynomial time • (f, t) = Gen() – generator function • Computation of f is easy (polynomial time) but inverse is very hard unless you have the trapdoor

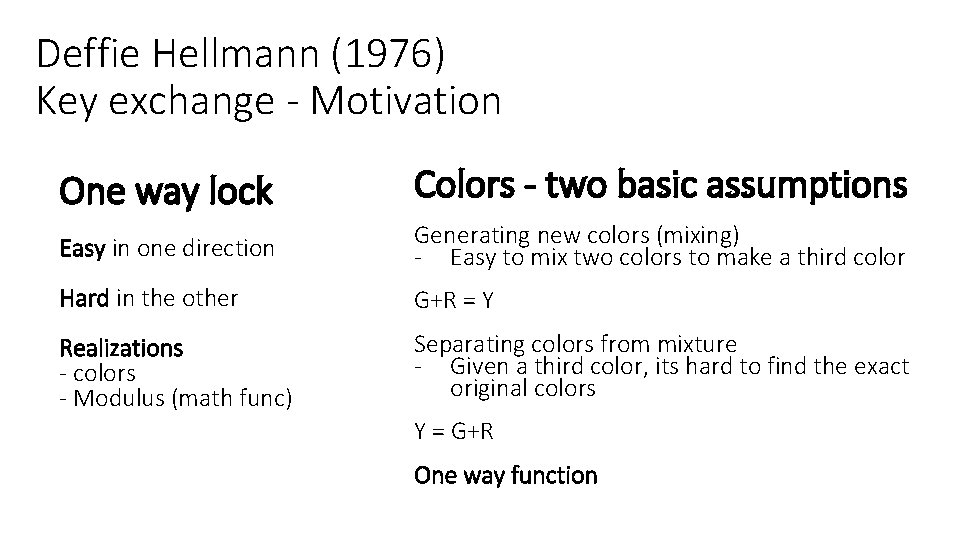
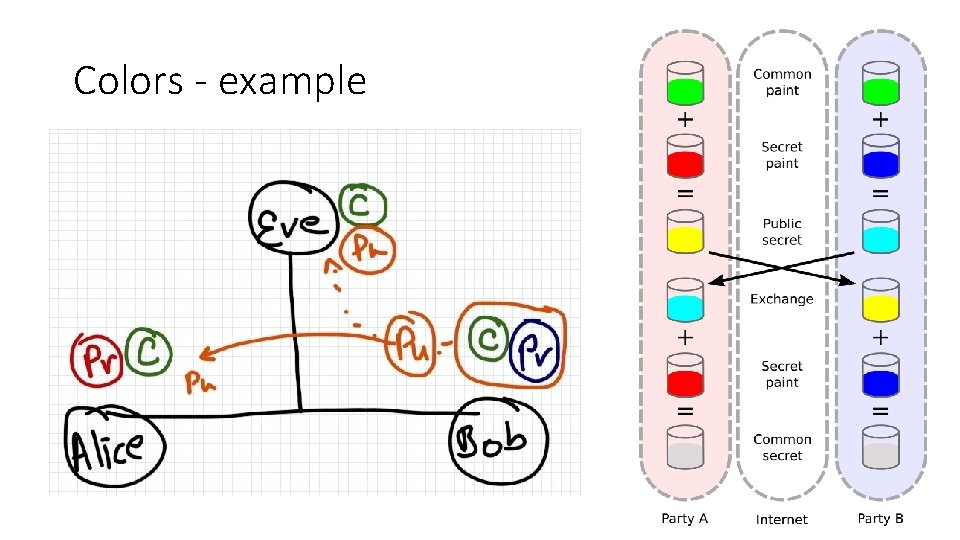
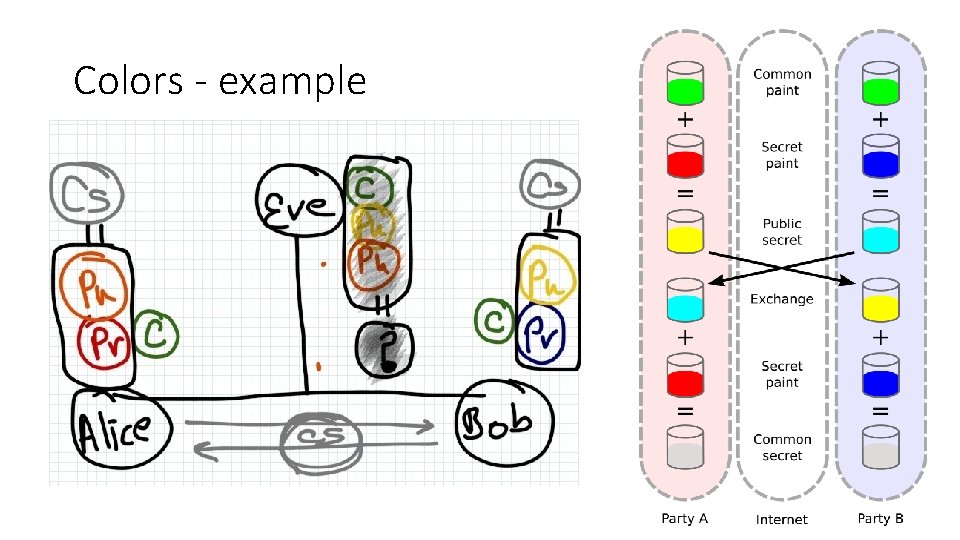
Deffie Hellmann (1976) Key exchange - Motivation One way lock Colors - two basic assumptions Easy in one direction Generating new colors (mixing) - Easy to mix two colors to make a third color Hard in the other G+R = Y Realizations - colors - Modulus (math func) Separating colors from mixture - Given a third color, its hard to find the exact original colors Y = G+R One way function


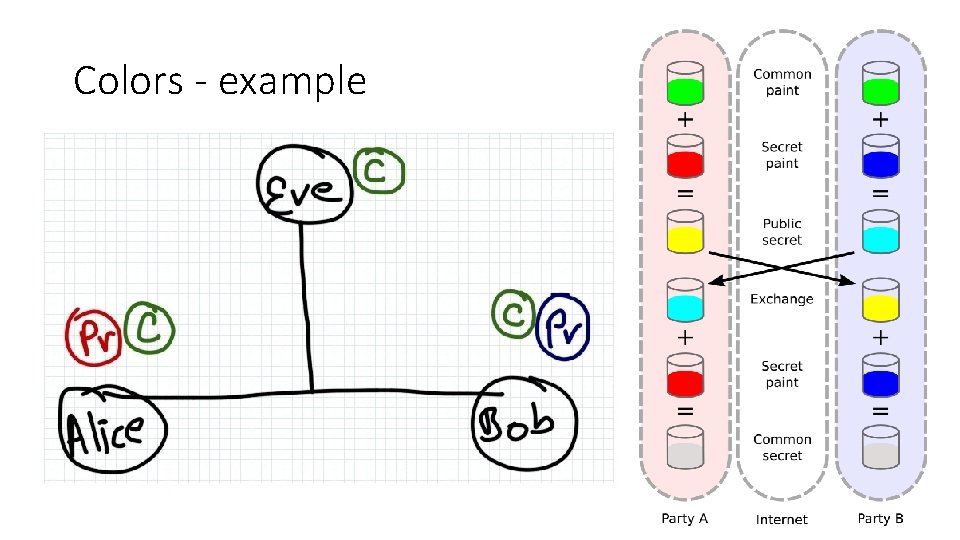
Colors - example

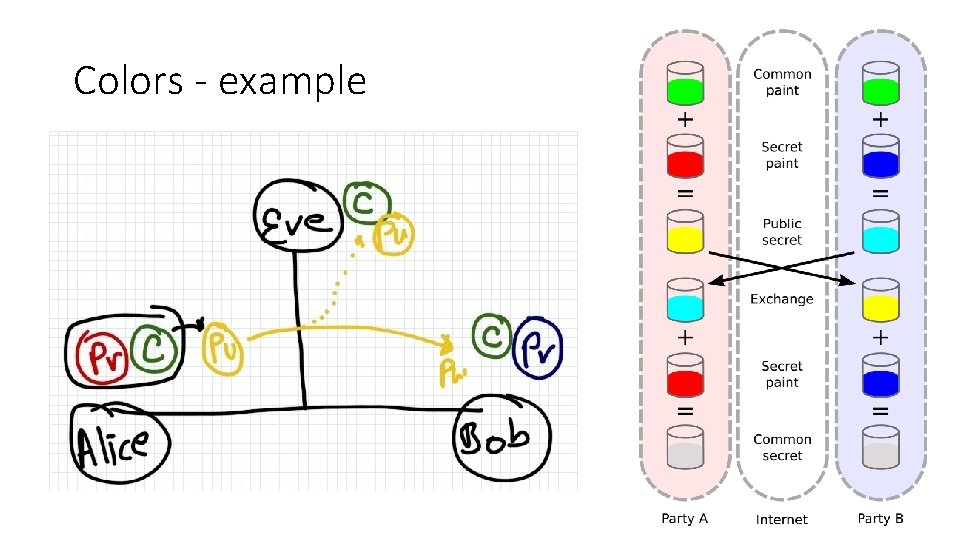
Colors - example

Colors - example

Colors - example

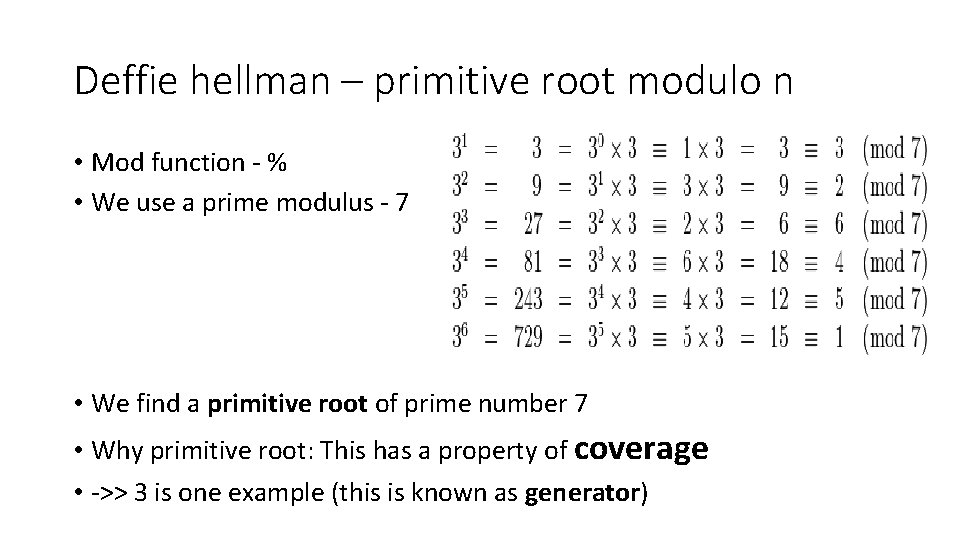
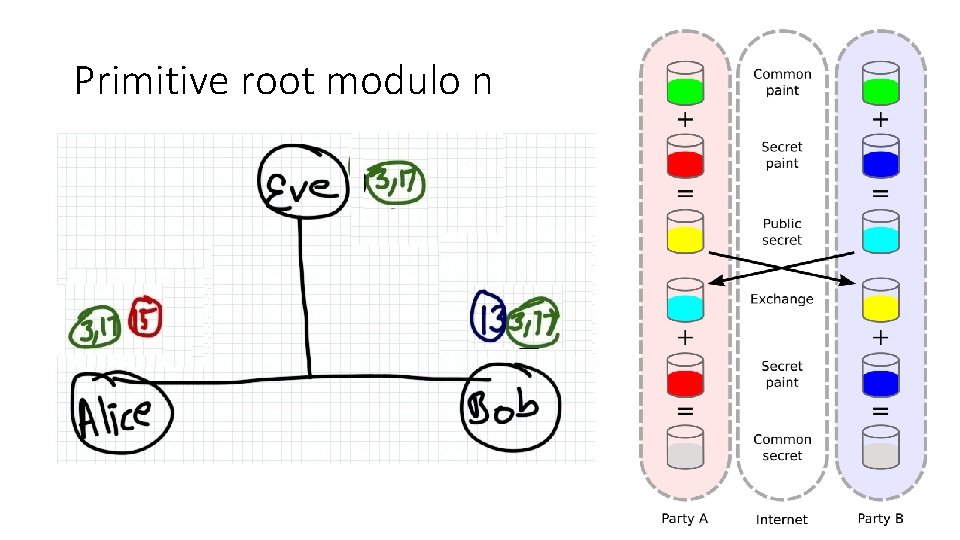
Deffie hellman – primitive root modulo n • Mod function - % • We use a prime modulus - 7 • We find a primitive root of prime number 7 • Why primitive root: This has a property of coverage • ->> 3 is one example (this is known as generator)

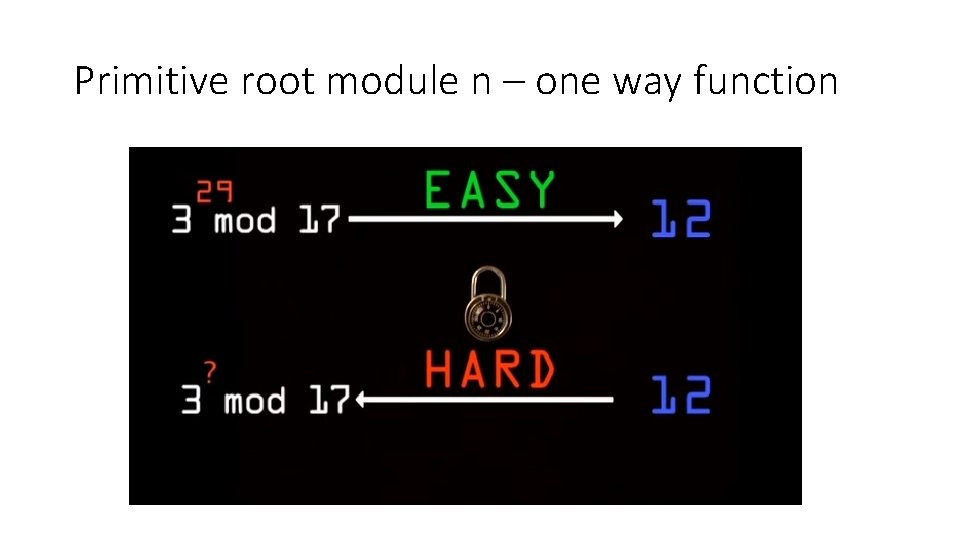
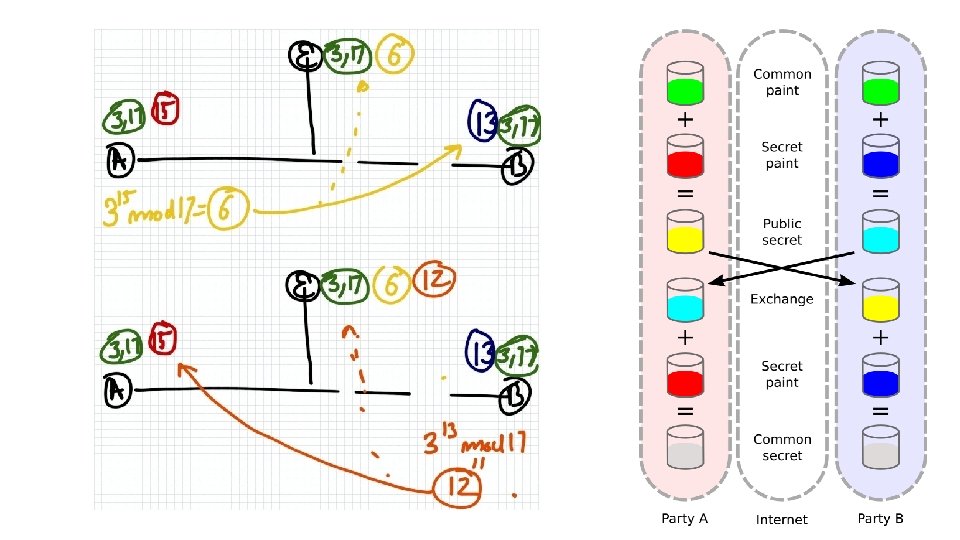
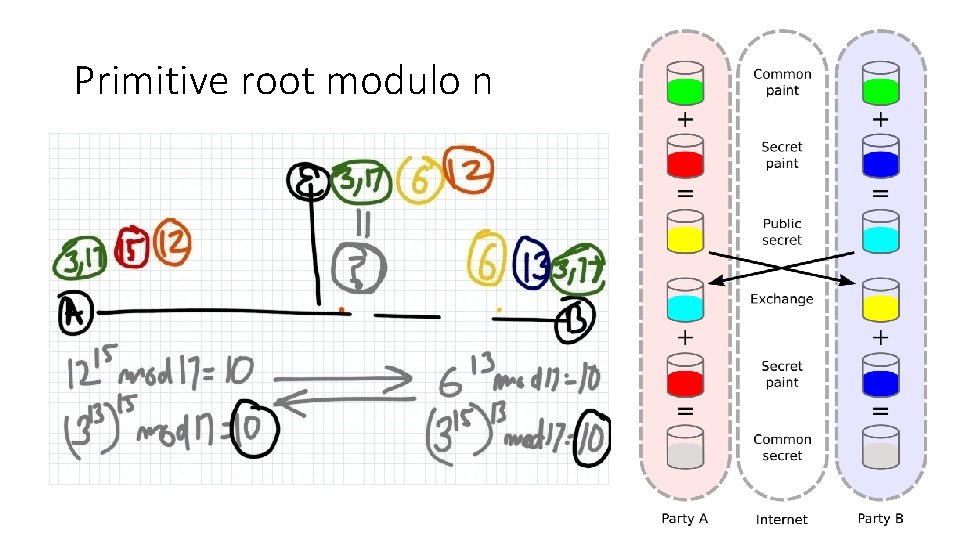
Deffie hellman - one way lock • Primitive root • Prime modulo – 17 • Primitive root – 3 (generator) • Coverage - If 3 is raised to an integer x, then solution (3^x%17) is equally likely to be any integer between 1, 17 • One way function • Finding modulus is easy • 3^29%17 = 12 (easy) • Reverse problem is hard • 3^x mod 17 = 12; only way to find x is brute(hard) (this is discrete log problem)

Primitive root module n – one way function

Primitive root modulo n


Primitive root modulo n

Problem with deffie hellman key exchange • Have to maintain many keys • Open problem – public and private keys (introduced by deffie hellman) • Solutions • 1977 • RSA • 2002 turing award • 1985 • Elgamal excyption, based on deffie hellman

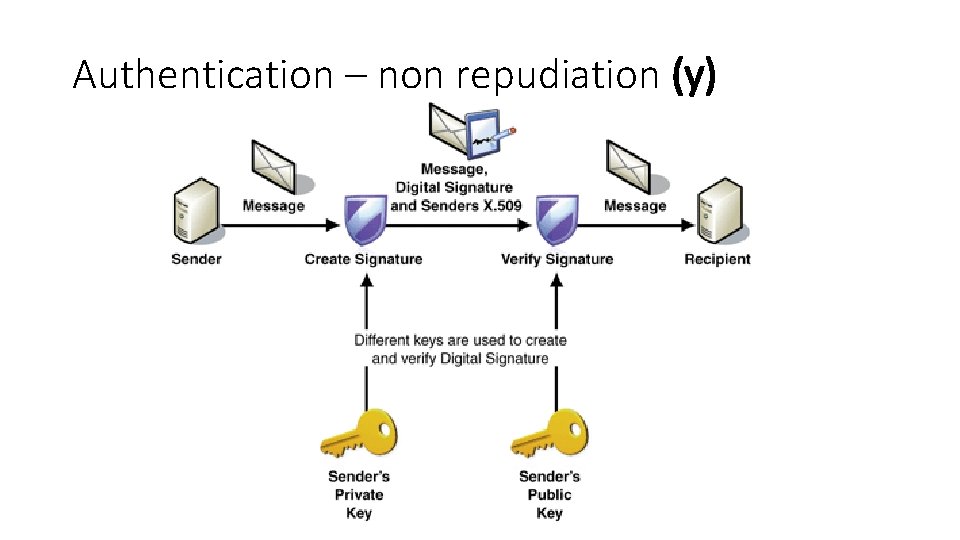
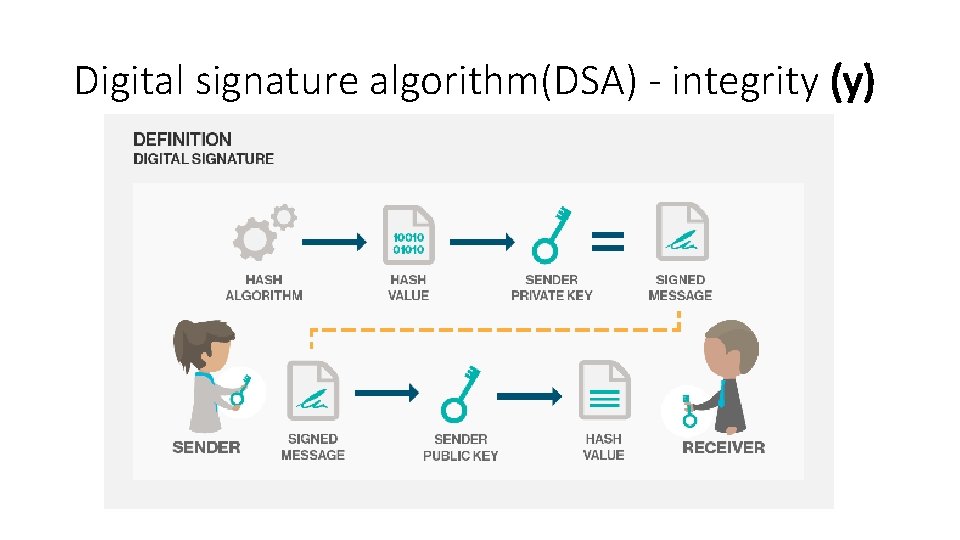
Fundamental issues in crypto • Privacy • No shall be able to read messages • Authentication/ non repudiation • The sender should be verifiable • Integrity • The message is same (no modification)

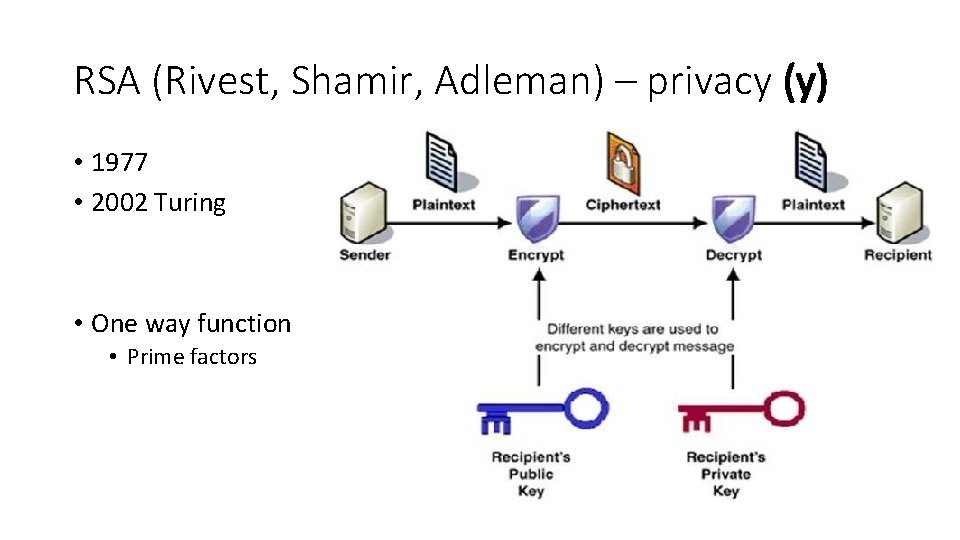
RSA (Rivest, Shamir, Adleman) – privacy (y) • 1977 • 2002 Turing • One way function • Prime factors

Authentication – non repudiation (y)

Digital signature algorithm(DSA) - integrity (y)

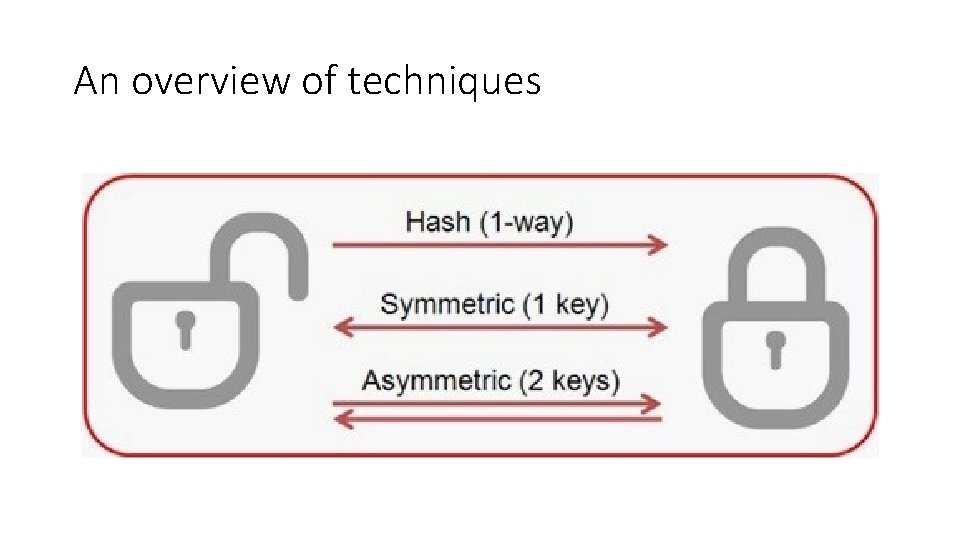
An overview of techniques

Common attacks – not exhaustive • Replay attack • Problem of public key distribution • Breaking the math – (P=NP) • Open problems – may be? • Unconditionally secure • Timed keys
Thanks