CRYPTOGRAPHY Cryptography in WWII German Encryption Method Enigma







- Slides: 16

CRYPTOGRAPHY

Cryptography in WWII • German Encryption Method : Enigma • American Encryption Method : Navajo • William F Friedman

The Enigma : 1930 -45 • • • Designed for military communications Designed by Professor David Lovelock 3 major changes made in: – 1930 -38 – 1938 -40 – 1941 -45 Photo Courtesy of http: //www. image-in. co. il/HTML/SEC 4 NET/images/aes_enigma. jpg

Navajo Language Encryption • Original language spoken on Navajo reservation in southwestern US • Until recently, an unwritten language • Idea for use as a cryptosystem proposed by Philip Johnstone

William F. Friedman • Leader in American Cryptology for half a century • Head of S. I. S. • Broke “PURPLE”, Japanese diplomatic cryptosystem • Member of NSA Photo courtesy of http: //www. liceofoscarini. it/studenti/crittografia/bio/friedman_pic. jpg

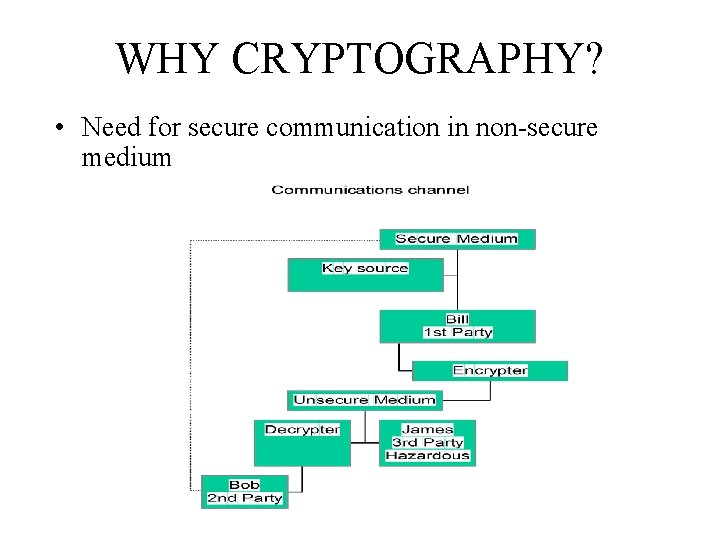
WHY CRYPTOGRAPHY? • Need for secure communication in non-secure medium

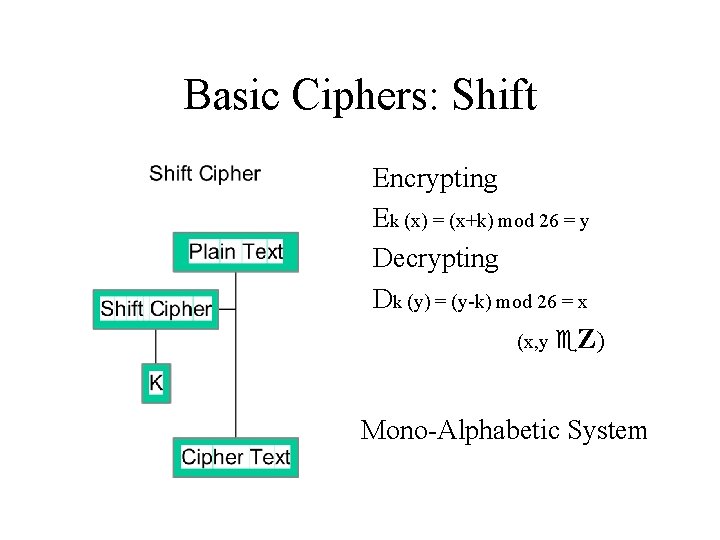
Basic Ciphers: Shift Encrypting Ek (x) = (x+k) mod 26 = y Decrypting Dk (y) = (y-k) mod 26 = x (x, y e. Z) Mono-Alphabetic System

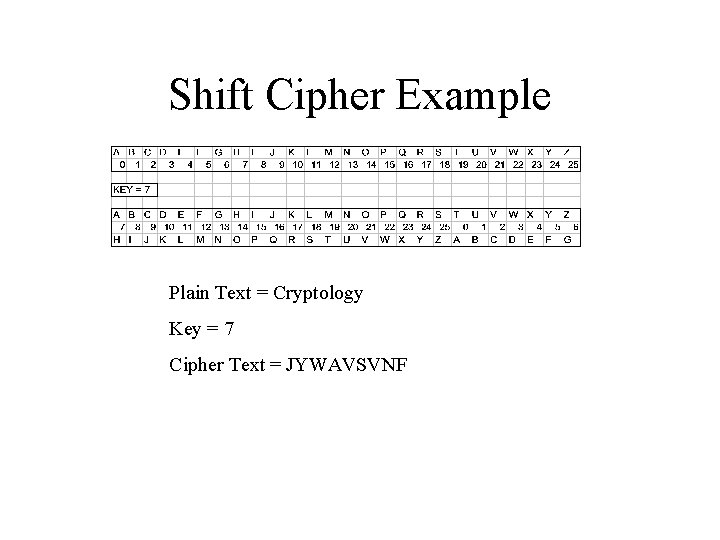
Shift Cipher Example Plain Text = Cryptology Key = 7 Cipher Text = JYWAVSVNF

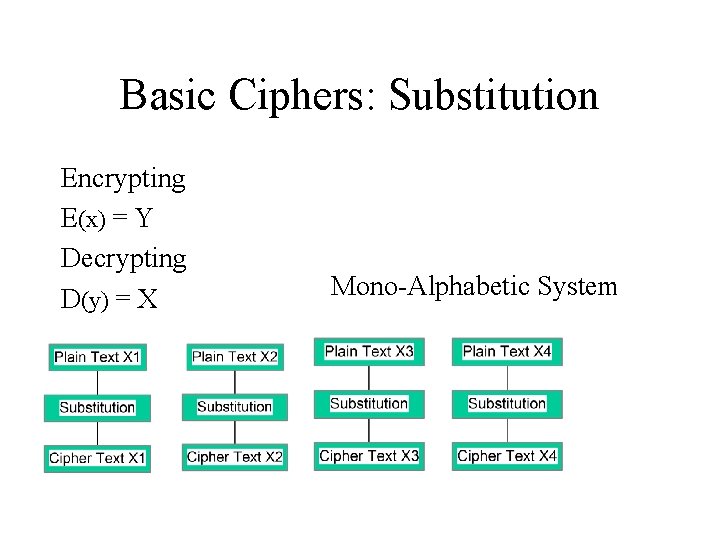
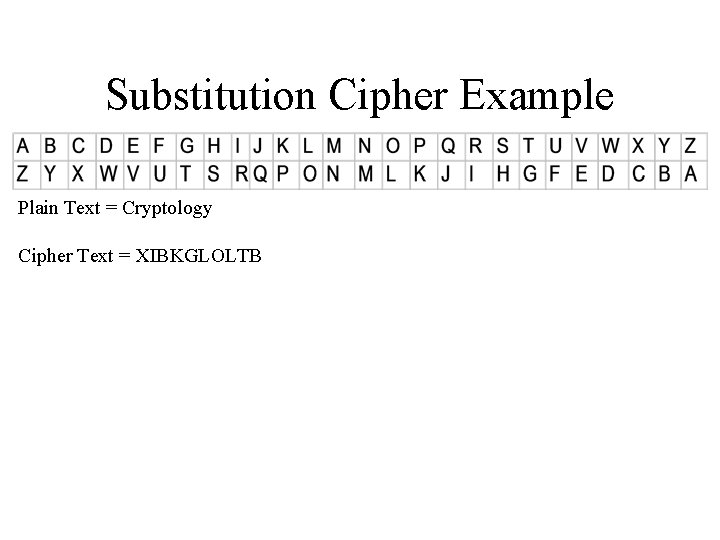
Basic Ciphers: Substitution Encrypting E(x) = Y Decrypting D(y) = X Mono-Alphabetic System

Substitution Cipher Example Plain Text = Cryptology Cipher Text = XIBKGLOLTB

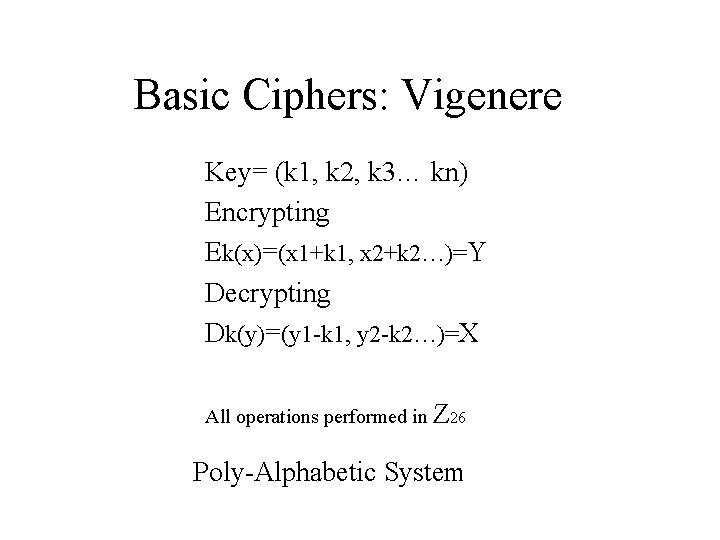
Basic Ciphers: Vigenere Key= (k 1, k 2, k 3… kn) Encrypting Ek(x)=(x 1+k 1, x 2+k 2…)=Y Decrypting Dk(y)=(y 1 -k 1, y 2 -k 2…)=X All operations performed in Z 26 Poly-Alphabetic System

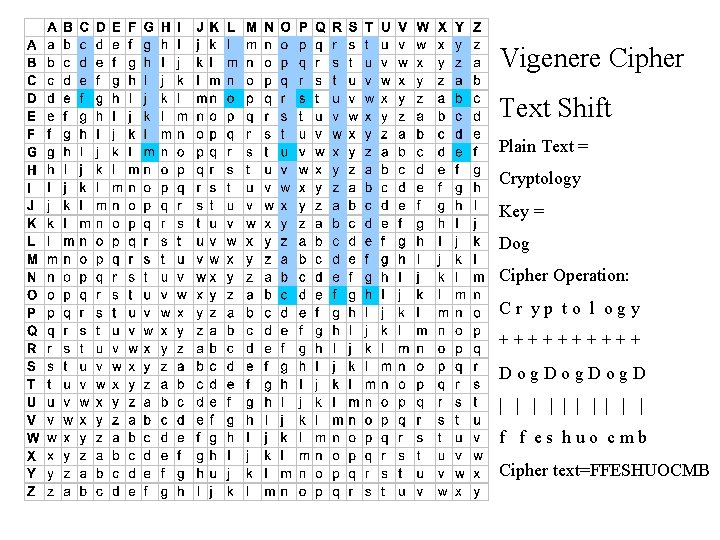
Vigenere Cipher Text Shift Plain Text = Cryptology Key = Dog Cipher Operation: Cr yp to l ogy +++++ Dog. D | | | | | f f es huo cmb Cipher text=FFESHUOCMB

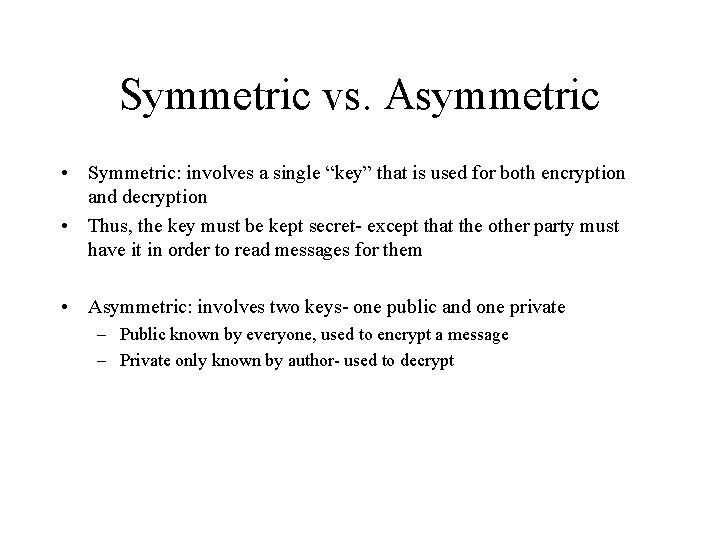
Symmetric vs. Asymmetric • Symmetric: involves a single “key” that is used for both encryption and decryption • Thus, the key must be kept secret- except that the other party must have it in order to read messages for them • Asymmetric: involves two keys- one public and one private – Public known by everyone, used to encrypt a message – Private only known by author- used to decrypt

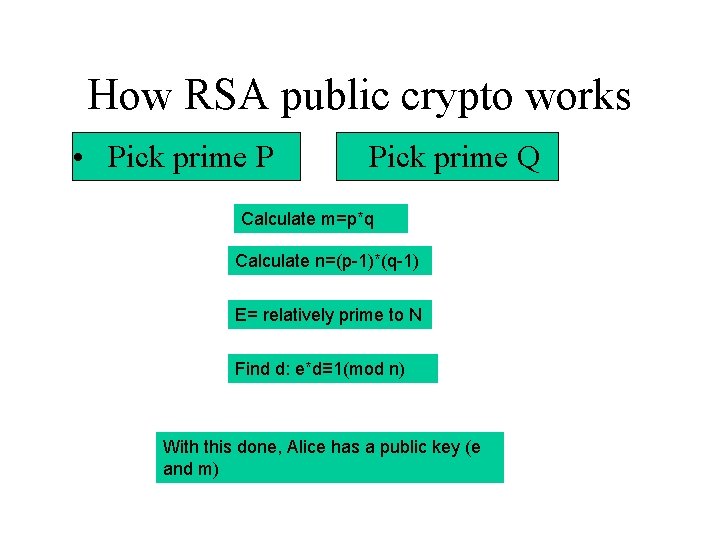
How RSA public crypto works • Pick prime P Pick prime Q Calculate m=p*q Calculate n=(p-1)*(q-1) E= relatively prime to N Find d: e*d≡ 1(mod n) With this done, Alice has a public key (e and m)

Advantages of Public Key • Based on (theoretically) difficult math problems • Solves the problem of distributing keys • Can be used to digitally sign documents

Bibliography Barr, Thomas H. Invitation to Cryptology. Upper Saddle River, NJ: Prentice Hall, 2002. http: //www. answers. com/topic/william-f-friedman http: //library. thinkquest. org/J 002073 F/thinkquest/home. htm http: //www. math. nmsu. edu/crypto/public_hrml/Enigma. html http: //www. theargon. com/articles/cryptology%20 lessons/hocryp. html