CRYPTOGRAPHY Block 6 Unit 1 Section 2 Prepared
CRYPTOGRAPHY Block 6, Unit 1, Section 2 Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
Contents l l l l Overview Method of Encryption Caesar Technique (Shift cipher) Improved Caesar Method (code word) Transposition Cipher (n-gram) One-time pad scheme (ploy-alphabetic) Q & A + Implementation of Java code Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Overview l In this section, we will discuss how each of the following encryption technique works a Caesar cipher or often called shift cipher. Then, an enhanced version of Caesar's code using ‘code word’. After that, we will discuss the Transposition encryption techniques. And before we end this presentation will know how One-time pad scheme is calculated. Finally, Questions & Answers and a short demo. Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Method of Encryption l There are two method of encryption: l Substitution l Transposition Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Caesar Technique (Shift cipher) l One of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Caesar Technique (Shift cipher) Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Caesar Technique (Shift cipher) l l Example (TMA 06 -Q 2(i)(a)): The message: WILLIAMSHAKESPEARE Key: 12 Encipher to: IUXXUMYETMWQEBQMDQ HOW? Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
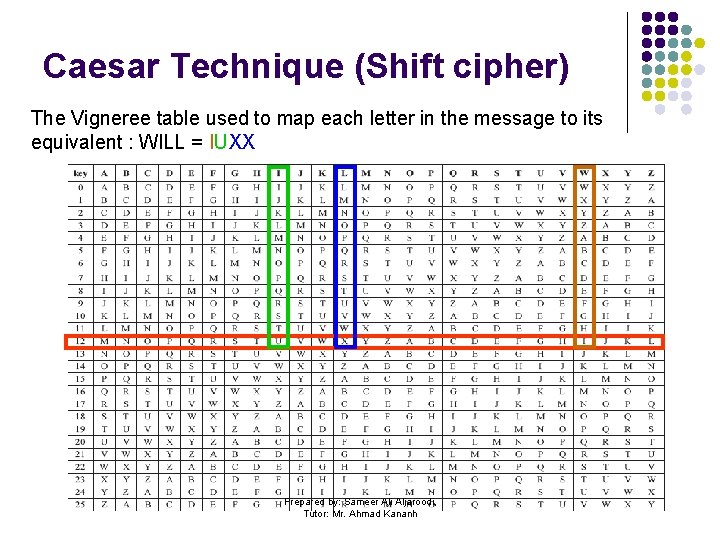
Caesar Technique (Shift cipher) The Vigneree table used to map each letter in the message to its equivalent : WILL = IUXX Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
Improved Caesar Method (code word) l An improved technique of shift-cipher were introduced which relays on two elements: 1. 2. Code Word Shift number (the Key) Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Improved Caesar Method (code word) l Example (TMA 06, Q 2(i)(b)): Message: WILLIAMSHAKESPEARE Code word: TEMPLAR Key: 4 Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Improved Caesar Method (code word) l Step 1: Generating the alphabet-table A B CDE F GHI J K L T ME P L A R B C D F G M N O P Q R S T U V W X Y Z H I J K N O Q S U V W X Y Z Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Improved Caesar Method (code word) l Step 2: Transforming the letters (Simple letter mapping): A B CDE F GHI J K L T ME P L A R B C D F G M N O P Q R S T U V W X Y Z H I J K N O Q S U V W X Y Z Message: WILLIAMSHAKESPEARE Transformed to: WCGGCTHQBTFLQKLTOL Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

Improved Caesar Method (code word) Step 3: Shifting the letters Take the transformed text and shift each letter by 4 (refer to Vigenere table) l Transformed to: WCGGCTHQBTFLQKLTOL Shift by 4: AGKKGXLUFXJPUOPXSP Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
So far… ü ü l l l Overview Method of Encryption Caesar Technique (Shift cipher) Improved Caesar Method (code word) Transposition Cipher (n-gram) One-time pad scheme (ploy-alphabetic) Q & A + Implementation of Java code Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
Transposition Cipher (n-gram) l Also, known as mono-alphabetic. Simply, it’s a process that divide the message into number of columns called grams. See next example for explanations. Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
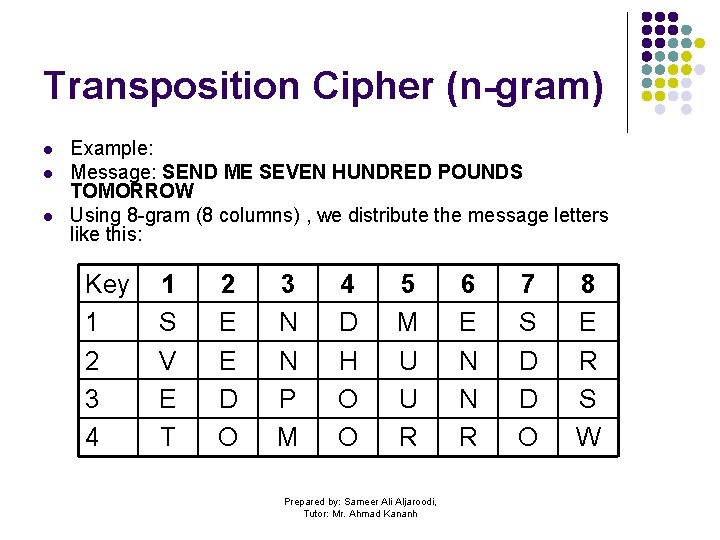
Transposition Cipher (n-gram) l l l Example: Message: SEND ME SEVEN HUNDRED POUNDS TOMORROW Using 8 -gram (8 columns) , we distribute the message letters like this: Key 1 2 3 4 1 S V E T 2 E E D O 3 N N P M 4 D H O O 5 M U U R Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh 6 E N N R 7 S D D O 8 E R S W
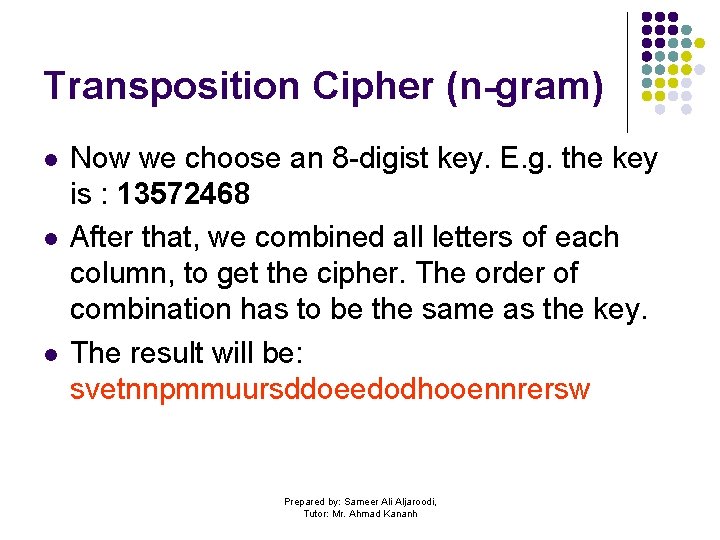
Transposition Cipher (n-gram) l l l Now we choose an 8 -digist key. E. g. the key is : 13572468 After that, we combined all letters of each column, to get the cipher. The order of combination has to be the same as the key. The result will be: svetnnpmmuursddoeedodhooennrersw Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh

One-time pad scheme (ploy-alphabetic) l Also known as a poly-alphabetic code. This code is theoretically unbreakable. Let’s take an example. . >> Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
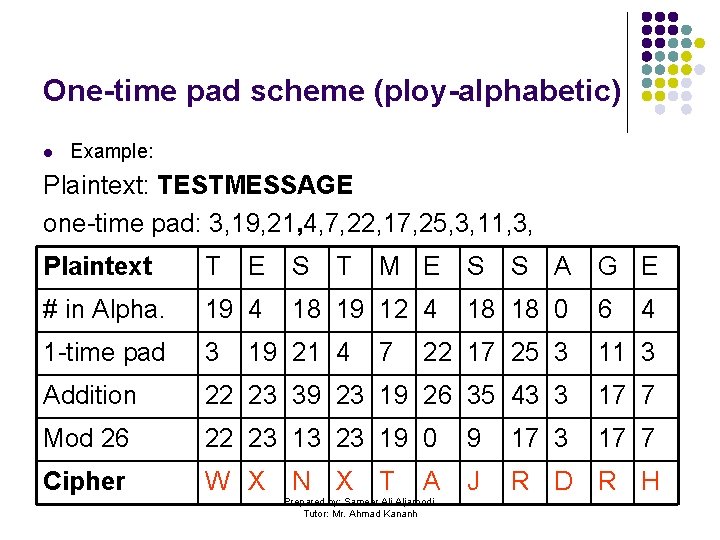
One-time pad scheme (ploy-alphabetic) l Example: Plaintext: TESTMESSAGE one-time pad: 3, 19, 21, 4, 7, 22, 17, 25, 3, 11, 3, Plaintext T E S T M E # in Alpha. 19 4 1 -time pad 3 22 17 25 3 11 3 Addition 22 23 39 23 19 26 35 43 3 17 7 Mod 26 22 23 13 23 19 0 9 17 3 17 7 Cipher W X J R D R H 18 19 12 4 19 21 4 N X 7 T A Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh S S A 18 18 0 G E 6 4
Q & A + Demo Prepared by: Sameer Ali Aljaroodi, Tutor: Mr. Ahmad Kananh
- Slides: 20