Cryptography 101 Cryptography Goals Manage WHO can view










![Samples OO example: Keyed Component file kf←� New Keyed. File ('D: downloadKeyed') kf['Products' 'Sales']←'Many' Samples OO example: Keyed Component file kf←� New Keyed. File ('D: downloadKeyed') kf['Products' 'Sales']←'Many'](https://slidetodoc.com/presentation_image_h2/86df76aaff739a00facd028c2394a315/image-20.jpg)






- Slides: 32

Cryptography 101

Cryptography: Goals • Manage WHO can view data (Secrecy) • Make sure data is unmodified (Authentication/data integrity) • Know the origin of the data (Non-Repudiation)

Dramatis Personæ Alice & Bob Are two persons who want to communicate without anybody else knows the content Eve Eavesdropper, normally a passive person that will try to listen in on Alice and Bob (perhaps an ex-girlfriend or wife) Oscar Opponent, an active person that will try to send messages in the name of Bob or Alice, or modify messages in transit

What is in our toolbox? Hash functions Symmetric encryption Asymmetric encryption

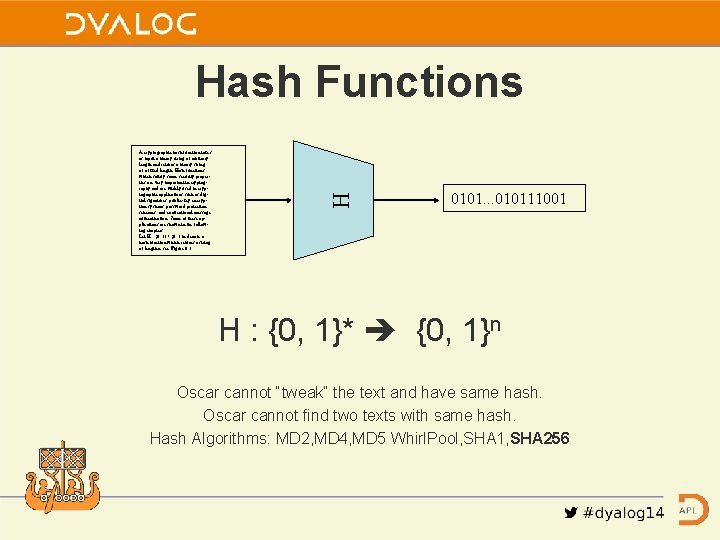
A cryptographic hash function takes as input a binary string of arbitrary length and returns a binary string of a fixed length. Hash functions which satisfy some security properties are very important in cryptography and are widely used in cryptographic applications such as digital signatures, public-key encryption systems, password protection schemes, and conventional message authentication. Some of these applications are shown in the following chapters. Let H : {0, 1} ! {0, 1}n denote a hash function which returns a string of length n, see Figure 6. 1. H Hash Functions 0101. . . 010111001 H : {0, 1}* {0, 1}n Oscar cannot “tweak” the text and have same hash. Oscar cannot find two texts with same hash. Hash Algorithms: MD 2, MD 4, MD 5 Whirl. Pool, SHA 1, SHA 256

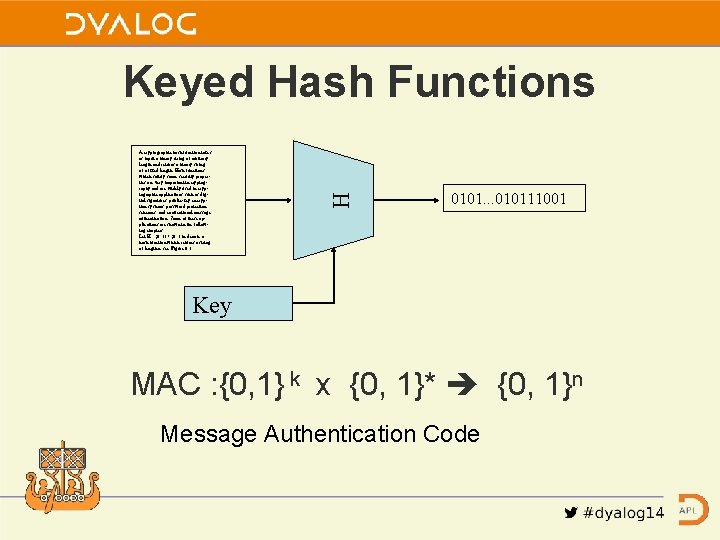
A cryptographic hash function takes as input a binary string of arbitrary length and returns a binary string of a fixed length. Hash functions which satisfy some security properties are very important in cryptography and are widely used in cryptographic applications such as digital signatures, public-key encryption systems, password protection schemes, and conventional message authentication. Some of these applications are shown in the following chapters. Let H : {0, 1} ! {0, 1}n denote a hash function which returns a string of length n, see Figure 6. 1. H Keyed Hash Functions 0101. . . 010111001 Key MAC : {0, 1} k x {0, 1}* {0, 1}n Message Authentication Code

Symmetric encryption Both Alice and Bob use the same key for encryption and decryption Example of Cipher Algorithms: DES, 3 -DES, Blow. Fish, RC 2, RC 4, AES and Cameillia

Asymmetric encryption Alice and Bob each have a Key Pair: A Public key and a Private Key Each Key Pair is constructed so that data encrypted with either key can be decrypted with the other.

Asymmetric encryption • Public keys are published for all to see, private keys kept secret, thus: • If Alice encrypts with her private key, anyone can decrypt the message • If Alice encrypts with Bobs public key, only Bob can decrypt the messages with his private key • Examples: RSA, DSA and EC elliptic curves.

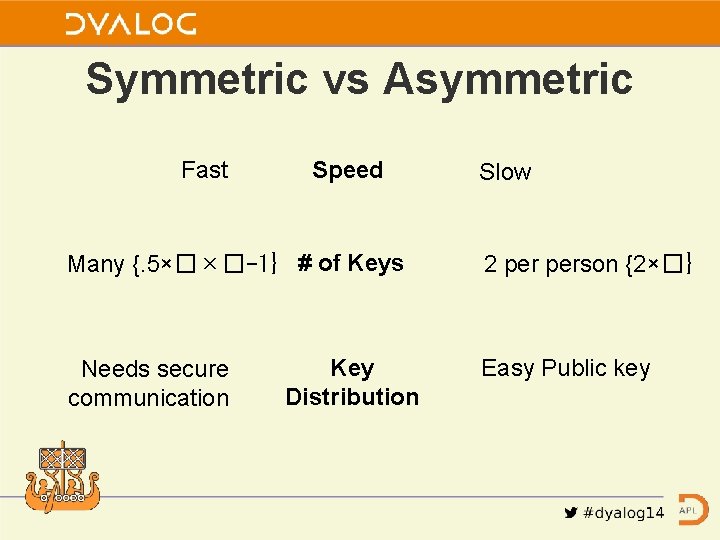
Symmetric vs Asymmetric Fast Speed Many {. 5��-1} # of Keys Needs secure communication Key Distribution Slow 2 person {2�} Easy Public key

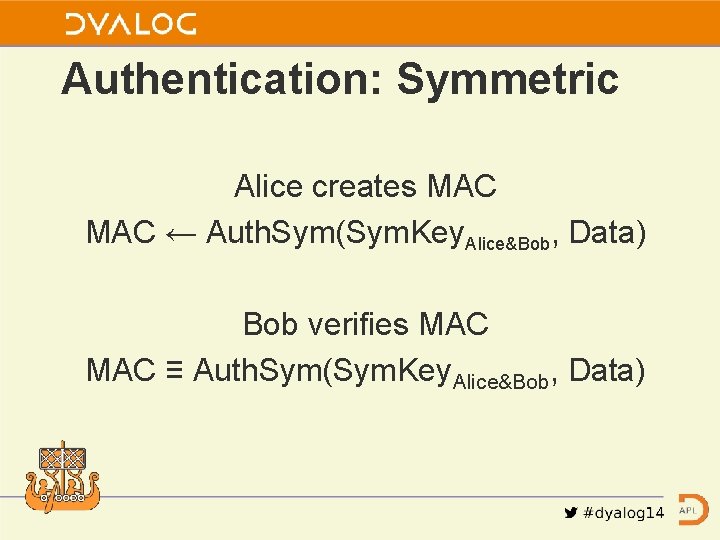
Authentication: Symmetric Alice creates MAC ← Auth. Sym(Sym. Key. Alice&Bob, Data) Bob verifies MAC ≡ Auth. Sym(Sym. Key. Alice&Bob, Data)

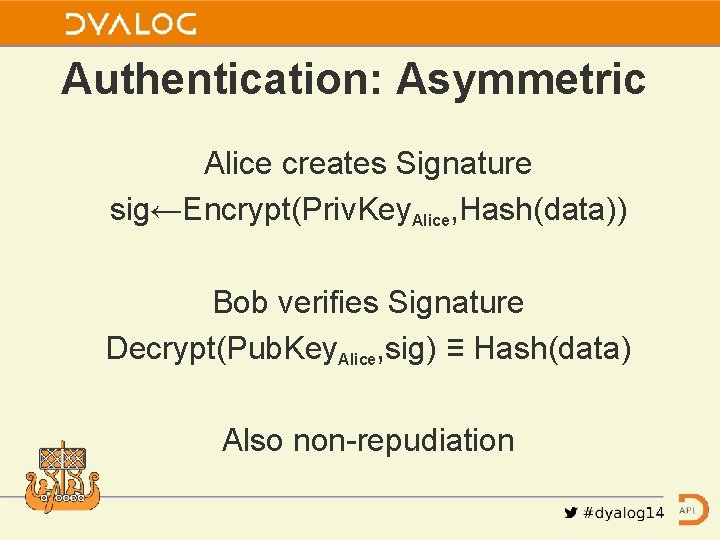
Authentication: Asymmetric Alice creates Signature sig←Encrypt(Priv. Key. Alice, Hash(data)) Bob verifies Signature Decrypt(Pub. Key. Alice, sig) ≡ Hash(data) Also non-repudiation

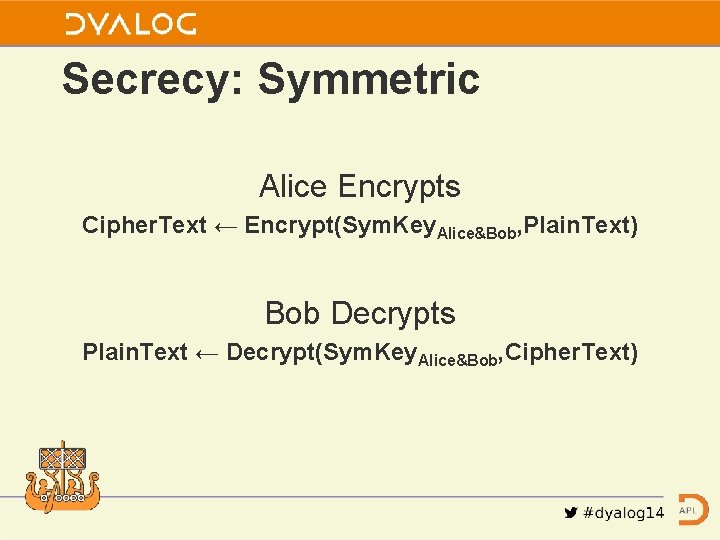
Secrecy: Symmetric Alice Encrypts Cipher. Text ← Encrypt(Sym. Key. Alice&Bob, Plain. Text) Bob Decrypts Plain. Text ← Decrypt(Sym. Key. Alice&Bob, Cipher. Text)

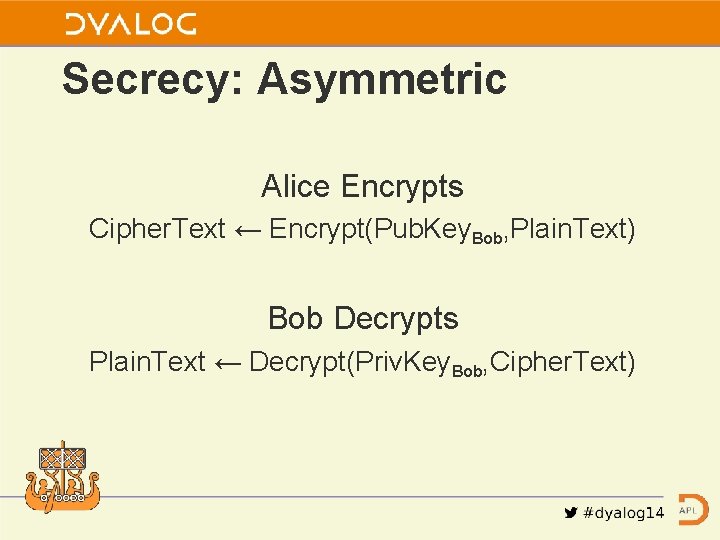
Secrecy: Asymmetric Alice Encrypts Cipher. Text ← Encrypt(Pub. Key. Bob, Plain. Text) Bob Decrypts Plain. Text ← Decrypt(Priv. Key. Bob, Cipher. Text)

Better Secrecy: Asymmetric Alice Encrypts Sym. Key←Random Cipher. Text ←Encrypt(Sym. Key, Plain. Text) Enc. Sym. Key←Encrypt(Pub. Key. Bob, Sym. Key) Bob Decrypts Sym. Key←Decrypt(Priv. Key. Bob, Enc. Sym. Key) Plain. Text←Decrypt(Sym. Key, Cipher. Text)

Even Better Secrecy Alice Encrypts Sym. Key←Random Enc. Sym. Key←Encrypt(Pub. Key. Bob, Sym. Key) Cipher. Text ←Encrypt(Sym. Key, Plain. Text) sig←Encrypt(Priv. Key. Alice, Hash(Plain. Text)) Bob Decrypts Sym. Key←Decrypt(Priv. Key. Bob, Enc. Sym. Key) Plain. Text←Decrypt(Sym. Key, Cipher. Text) Decrypt(Pub. Key. Alice, sig)=Hash(Plain. Text)

Key Problem How do we keep our keys safe? Windows Certificate Store PKCS#11 smartcard From APL: in a PKCS#8 PKCS => Public-Key Cryptographics Standard

Dyalog Cryptographic Library • • The DCL is a DLL/so and a set of cover-functions Provides access to a large set of hashing and encryption functions Provides tools for dealing with ”certificates” containing keys Cross-platform (but cross Unicode/Classic is problematic due to translation issues)

Certificate Stores • Store certificates and keep private keys secret. But: • Limits on available algorithms • Mimited tools for Dyalog • Microsoft. Net • Some Conga support
![Samples OO example Keyed Component file kf New Keyed File D downloadKeyed kfProducts SalesMany Samples OO example: Keyed Component file kf←� New Keyed. File ('D: downloadKeyed') kf['Products' 'Sales']←'Many'](https://slidetodoc.com/presentation_image_h2/86df76aaff739a00facd028c2394a315/image-20.jpg)
Samples OO example: Keyed Component file kf←� New Keyed. File ('D: downloadKeyed') kf['Products' 'Sales']←'Many' 'None' kf[⊂'Products'] Many

Samples OO example: Keyed Component file Extended to handle encrypted and compressed components.

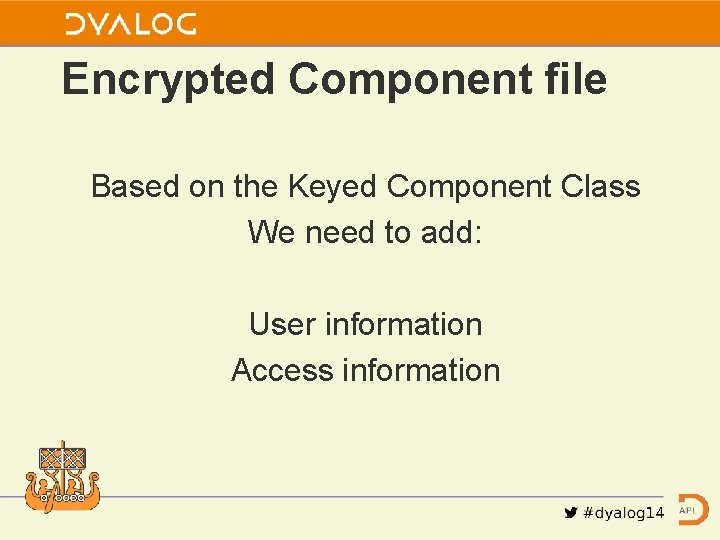
Encrypted Component file Based on the Keyed Component Class We need to add: User information Access information

User Information 1. 2. 3. 4. 5. 6. User Id Public Key Salt Repetitions Initial Vector Encrypted Private Key

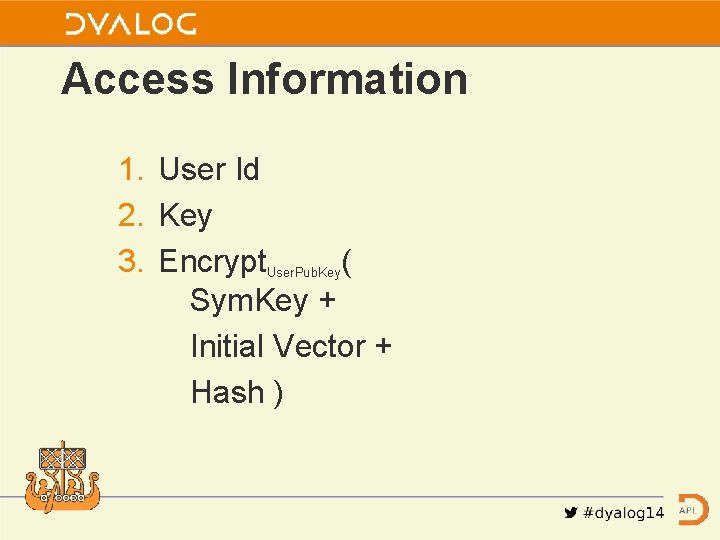
Access Information 1. User Id 2. Key 3. Encrypt. User. Pub. Key( Sym. Key + Initial Vector + Hash )

Add New User ∇ Add. User(user para); . . . (Priv. Key Pub. Key)←Generate. Asym. Keys Asym. Key. Pair. Size Salt←Random Salt. Size iv←Random Cipher. Block. Size rep←PBKDF 2 Repetitions Derived. Key←Derive. Key para Salt rep Cipher. Key. Size Enc. Priv. Key←Priv. Key Encrypt. Sym Derived. Key iv users� ←user Pub. Key Salt rep iv Enc. Priv. Key ∇

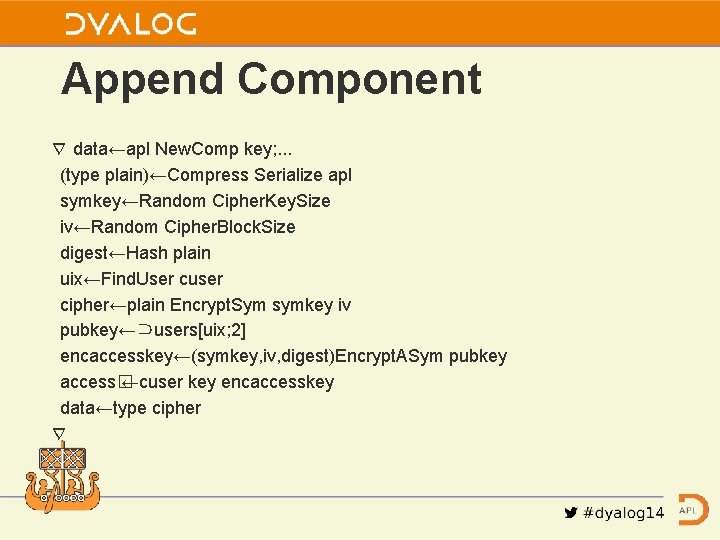
Append Component ∇ data←apl New. Comp key; . . . (type plain)←Compress Serialize apl symkey←Random Cipher. Key. Size iv←Random Cipher. Block. Size digest←Hash plain uix←Find. User cuser cipher←plain Encrypt. Sym symkey iv pubkey←⊃users[uix; 2] encaccesskey←(symkey, iv, digest)Encrypt. ASym pubkey access� ←cuser key encaccesskey data←type cipher ∇

Read a Component ∇ apl←data Decrypt. Comp key; . . . (type cipher)←data (secret iv digest)←Get. Access cuser key cpara plain←cipher Decrypt. Sym secret iv apl←Deserialize Decompress type plain ∇

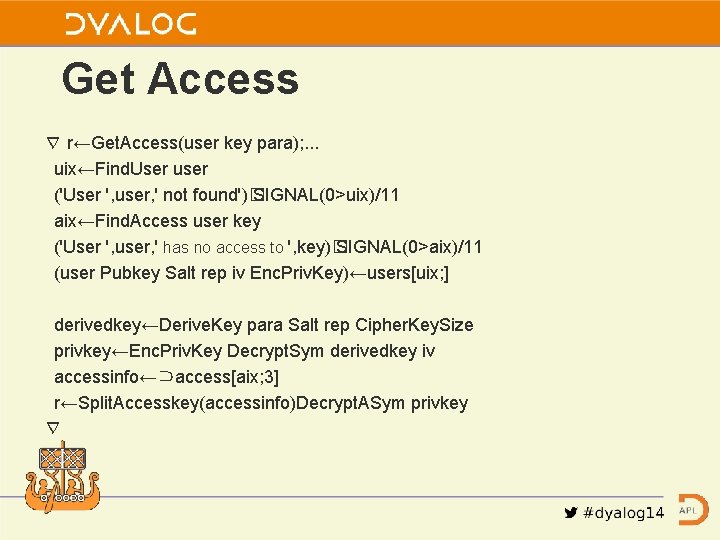
Get Access ∇ r←Get. Access(user key para); . . . uix←Find. User user ('User ', user, ' not found')� SIGNAL(0>uix)/11 aix←Find. Access user key ('User ', user, ' has no access to ', key)� SIGNAL(0>aix)/11 (user Pubkey Salt rep iv Enc. Priv. Key)←users[uix; ] derivedkey←Derive. Key para Salt rep Cipher. Key. Size privkey←Enc. Priv. Key Decrypt. Sym derivedkey iv accessinfo←⊃access[aix; 3] r←Split. Accesskey(accessinfo)Decrypt. ASym privkey ∇

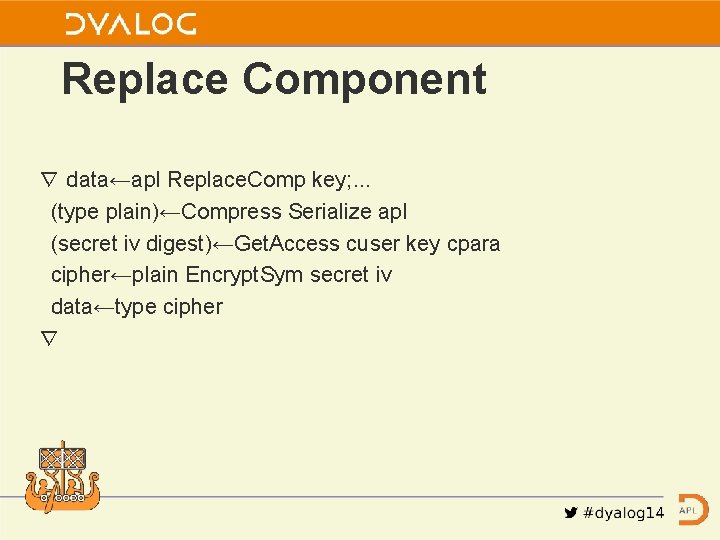
Replace Component ∇ data←apl Replace. Comp key; . . . (type plain)←Compress Serialize apl (secret iv digest)←Get. Access cuser key cpara cipher←plain Encrypt. Sym secret iv data←type cipher ∇

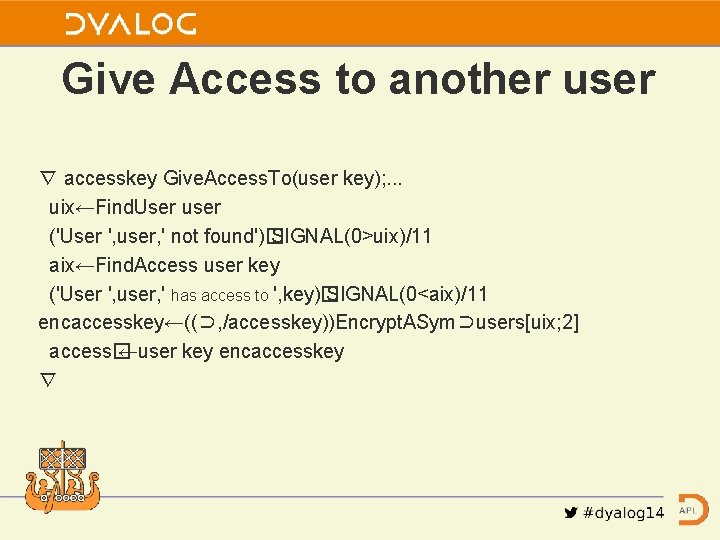
Give Access to another user ∇ accesskey Give. Access. To(user key); . . . uix←Find. User user ('User ', user, ' not found')� SIGNAL(0>uix)/11 aix←Find. Access user key ('User ', user, ' has access to ', key)� SIGNAL(0<aix)/11 encaccesskey←((⊃, /accesskey))Encrypt. ASym⊃users[uix; 2] access� ←user key encaccesskey ∇

On your own Without experience and deep knowledge, it is difficult to evaluate the security of any mechanism: Use established standards!

Futher infomation • • • RFC for Public Key Cryptography Standard (PKCS#) The Handbook of Applied Cryptograhy Dyalog Cryptographic Library