Cryptographic Authentication Protocols CS 470 Introduction to Applied




![Public Key Challenge-Response By signature: CS 470, A. Selcuk R [R]A Cryptographic Authentication Bob Public Key Challenge-Response By signature: CS 470, A. Selcuk R [R]A Cryptographic Authentication Bob](https://slidetodoc.com/presentation_image_h/346c015995133be7a28c5b7d2998dd82/image-7.jpg)




- Slides: 18

Cryptographic Authentication Protocols CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk CS 470, A. Selcuk Cryptographic Authentication 1

Cryptographic Authentication • Password authentication subject to eavesdropping • Alternative: Cryptographic challenge-response – Symmetric key – Public key CS 470, A. Selcuk Cryptographic Authentication 2

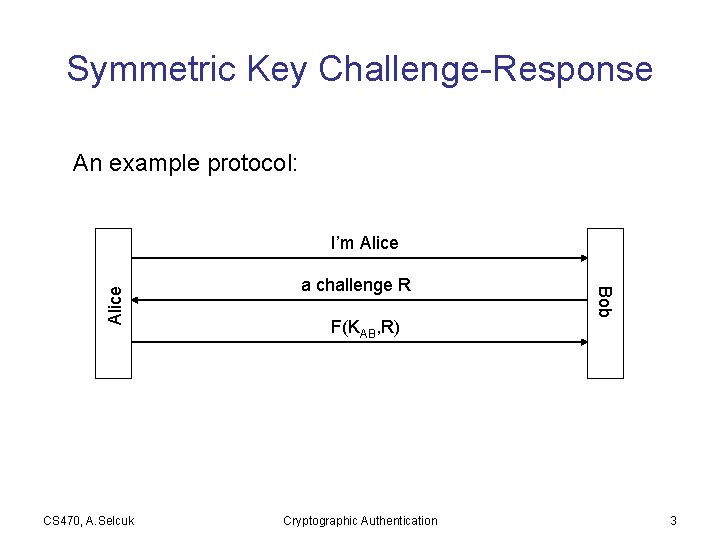
Symmetric Key Challenge-Response An example protocol: CS 470, A. Selcuk a challenge R F(KAB, R) Cryptographic Authentication Bob Alice I’m Alice 3

Limitations: • Authentication not mutual (login only) • Subject to connection hijacking (login only) • Subject to off-line password guessing (if K is derived from password) • Bob’s database has keys in the clear CS 470, A. Selcuk Cryptographic Authentication 4

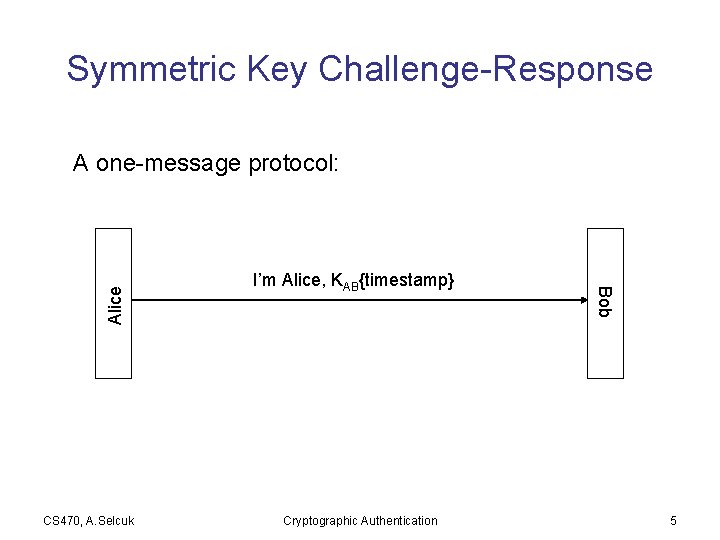
Symmetric Key Challenge-Response CS 470, A. Selcuk I’m Alice, KAB{timestamp} Cryptographic Authentication Bob Alice A one-message protocol: 5

• • • Easy integration into password-sending systems More efficient: Single message, stateless Care needed against replays Care needed if key is common across servers Clock has to be protected as well Alternatively, with a hash function, send, I’m Alice, timestamp, H(KAB, timestamp) CS 470, A. Selcuk Cryptographic Authentication 6
![Public Key ChallengeResponse By signature CS 470 A Selcuk R RA Cryptographic Authentication Bob Public Key Challenge-Response By signature: CS 470, A. Selcuk R [R]A Cryptographic Authentication Bob](https://slidetodoc.com/presentation_image_h/346c015995133be7a28c5b7d2998dd82/image-7.jpg)
Public Key Challenge-Response By signature: CS 470, A. Selcuk R [R]A Cryptographic Authentication Bob Alice I’m Alice 7

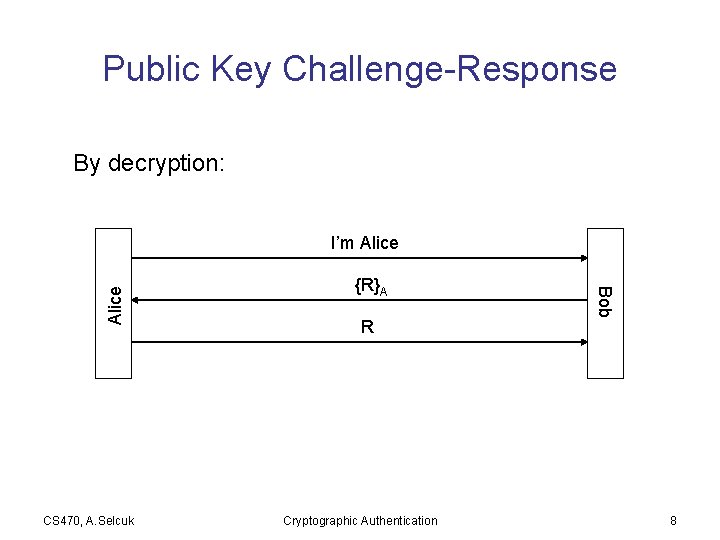
Public Key Challenge-Response By decryption: CS 470, A. Selcuk {R}A R Cryptographic Authentication Bob Alice I’m Alice 8

• Problem: Bob (or Trudy) can get Alice to sign/decrypt any text he chooses. • Solutions: – Never use the same key for different purposes (e. g. , for login and signature) – Have formatted challenges CS 470, A. Selcuk Cryptographic Authentication 9

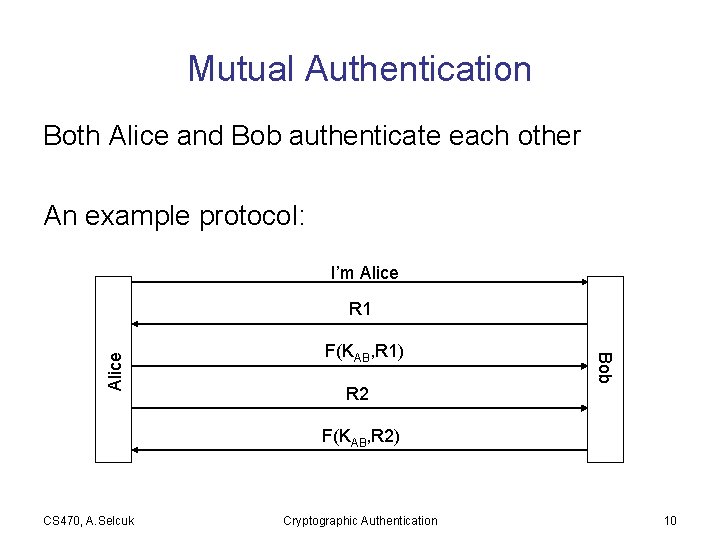
Mutual Authentication Both Alice and Bob authenticate each other An example protocol: I’m Alice F(KAB, R 1) Bob Alice R 1 R 2 F(KAB, R 2) CS 470, A. Selcuk Cryptographic Authentication 10

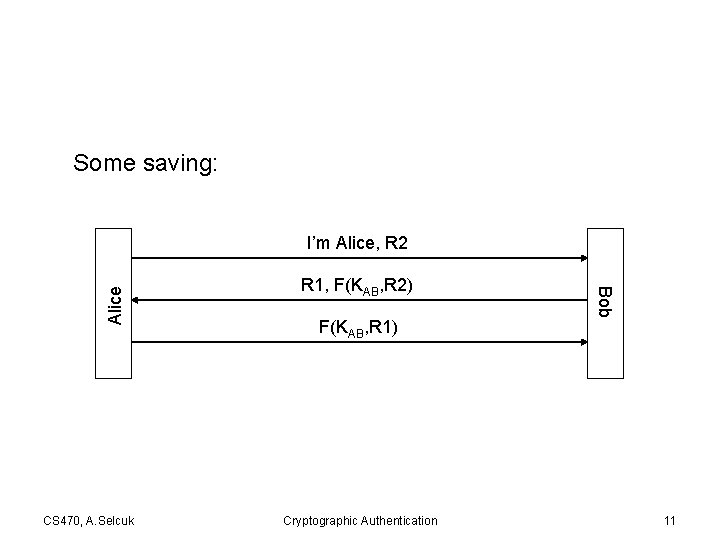
Some saving: CS 470, A. Selcuk R 1, F(KAB, R 2) F(KAB, R 1) Cryptographic Authentication Bob Alice I’m Alice, R 2 11

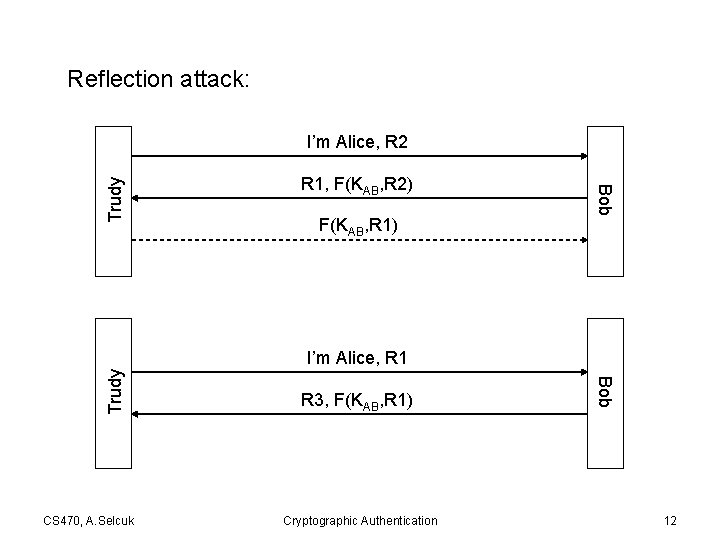
Reflection attack: R 1, F(KAB, R 2) F(KAB, R 1) Bob Trudy I’m Alice, R 2 CS 470, A. Selcuk R 3, F(KAB, R 1) Cryptographic Authentication Bob Trudy I’m Alice, R 1 12

• Solutions: – Different keys for Alice and Bob – Formatted challenges, different for Alice and Bob • Principle: Initiator should be the first to prove its identity CS 470, A. Selcuk Cryptographic Authentication 13

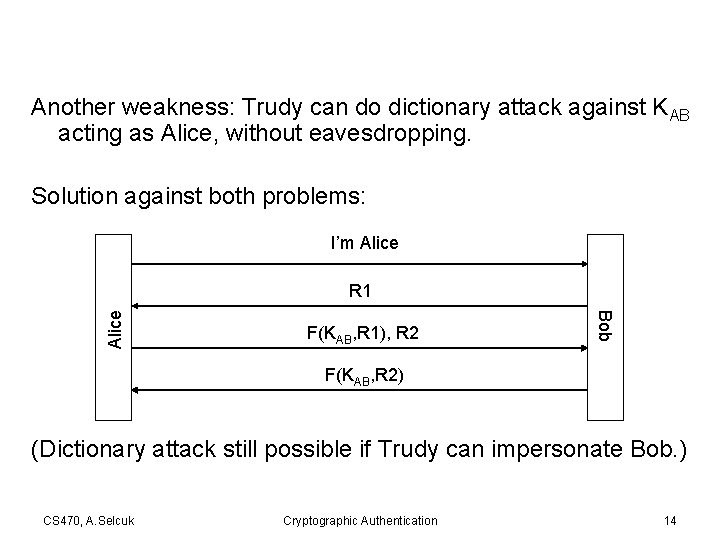
Another weakness: Trudy can do dictionary attack against KAB acting as Alice, without eavesdropping. Solution against both problems: I’m Alice F(KAB, R 1), R 2 Bob Alice R 1 F(KAB, R 2) (Dictionary attack still possible if Trudy can impersonate Bob. ) CS 470, A. Selcuk Cryptographic Authentication 14

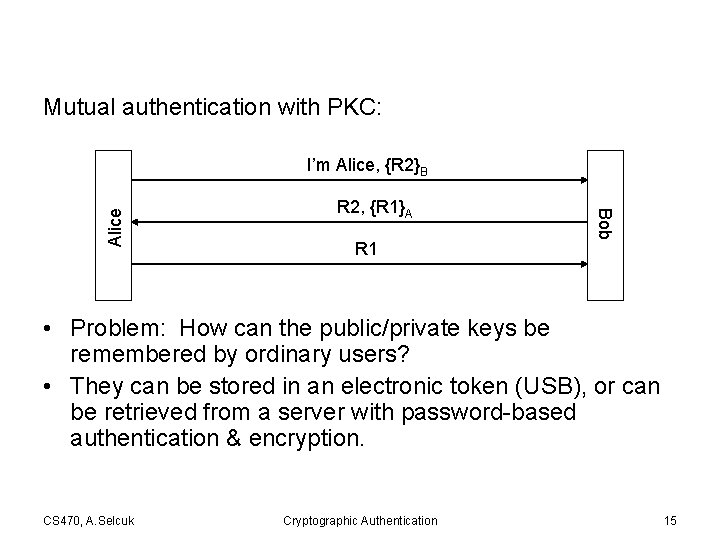
Mutual authentication with PKC: R 2, {R 1}A R 1 Bob Alice I’m Alice, {R 2}B • Problem: How can the public/private keys be remembered by ordinary users? • They can be stored in an electronic token (USB), or can be retrieved from a server with password-based authentication & encryption. CS 470, A. Selcuk Cryptographic Authentication 15

Session Key Establishment • A session key is needed to authenticate/encrypt the rest of the session. • The session key must be – different for each session – unguessable by an eavesdropper – not KAB{x} for some x predictable/extractable by an attacker • Good if both sides contribute – avoids replays (“freshness guarantee”) – works if either side has a good random number generator CS 470, A. Selcuk Cryptographic Authentication 16

Nonces • Nonce: Something created for one particular occasion • Nonce types: – Random numbers – Timestamps – Sequence numbers • Random nonces needed for unpredictability • Obtaining random nonces from timestamps: encryption with a secret key. CS 470, A. Selcuk Cryptographic Authentication 17

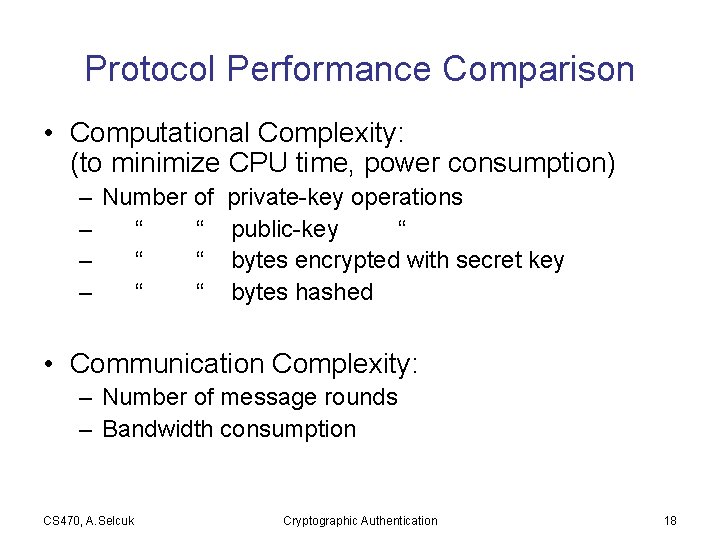
Protocol Performance Comparison • Computational Complexity: (to minimize CPU time, power consumption) – Number of – “ “ private-key operations public-key “ bytes encrypted with secret key bytes hashed • Communication Complexity: – Number of message rounds – Bandwidth consumption CS 470, A. Selcuk Cryptographic Authentication 18