Cryptanalysis of Microsofts PointtoPoint Tunneling Protocol 6 Mar






- Slides: 26

Cryptanalysis of Microsoft’s Point-to-Point Tunneling Protocol 6 Mar. 2007 Amit Golander

Mainly based on: Cryptanalysis of MS-PPTP (Point-to-Point Tunneling Protocol) Schneier and Mudge, Proceedings of the 5 th Conference on Computer and Communications Security (1998) Cited 41 times (according to scholar. google) Tel-Aviv University Page 2 Topics in Information Security 2007

Outline: • Background • Authentication • Encryption • Other attacks • Follow-up Tel-Aviv University Page 3 Topics in Information Security 2007

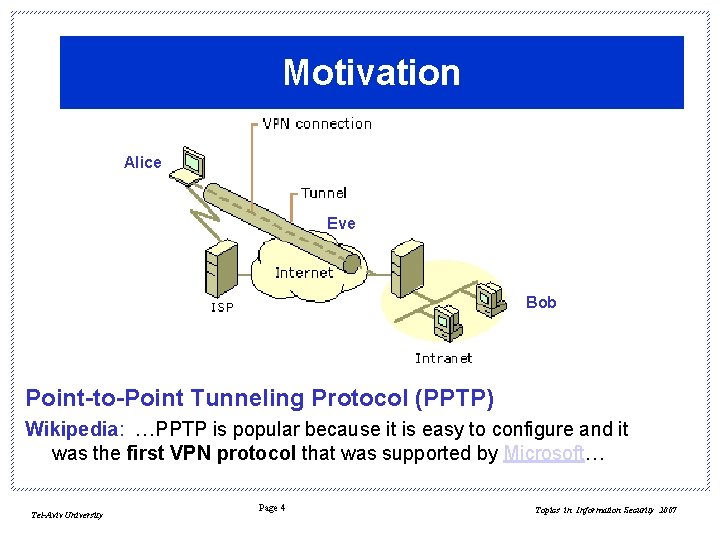
Motivation Alice Eve Bob Point-to-Point Tunneling Protocol (PPTP) Wikipedia: …PPTP is popular because it is easy to configure and it was the first VPN protocol that was supported by Microsoft… Tel-Aviv University Page 4 Topics in Information Security 2007

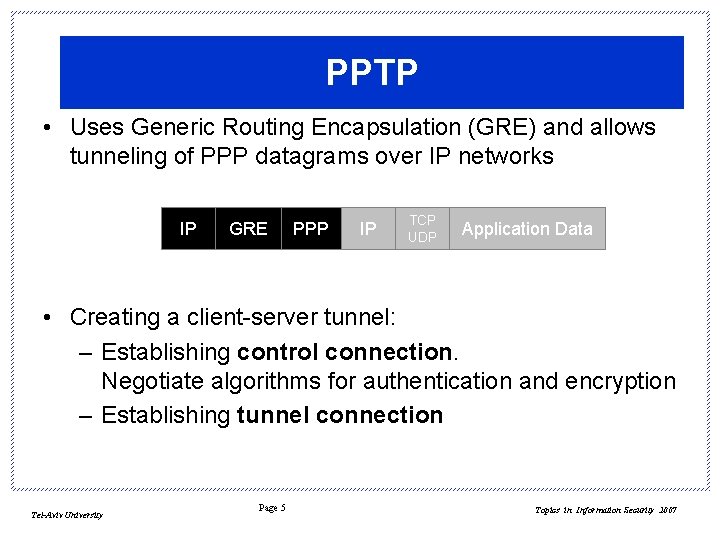
PPTP • Uses Generic Routing Encapsulation (GRE) and allows tunneling of PPP datagrams over IP networks IP GRE PPP IP TCP UDP Application Data • Creating a client-server tunnel: – Establishing control connection. Negotiate algorithms for authentication and encryption – Establishing tunnel connection Tel-Aviv University Page 5 Topics in Information Security 2007

What is the paper about? The paper analyzes Microsoft's Windows NT implementation of PPTP It shows how to: • Break the authentication protocols (including challenge/response MS-CHAP) • Break the RC 4 encryption protocol (MPPE) • Attack the control channel The story is about bad architecture and terrible design… Tel-Aviv University Page 6 Topics in Information Security 2007

Outline: • Background • Authentication • Encryption • Other attacks • Follow-up Tel-Aviv University Page 7 Topics in Information Security 2007

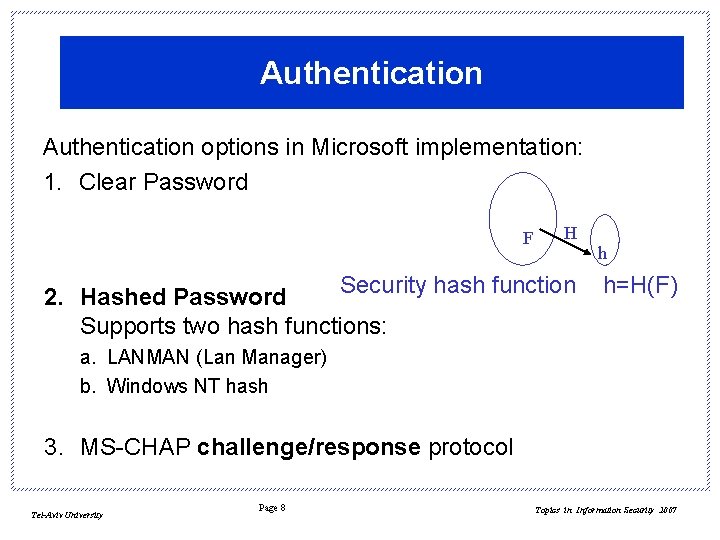
Authentication options in Microsoft implementation: 1. Clear Password F H Security hash function 2. Hashed Password Supports two hash functions: h h=H(F) a. LANMAN (Lan Manager) b. Windows NT hash 3. MS-CHAP challenge/response protocol Tel-Aviv University Page 8 Topics in Information Security 2007

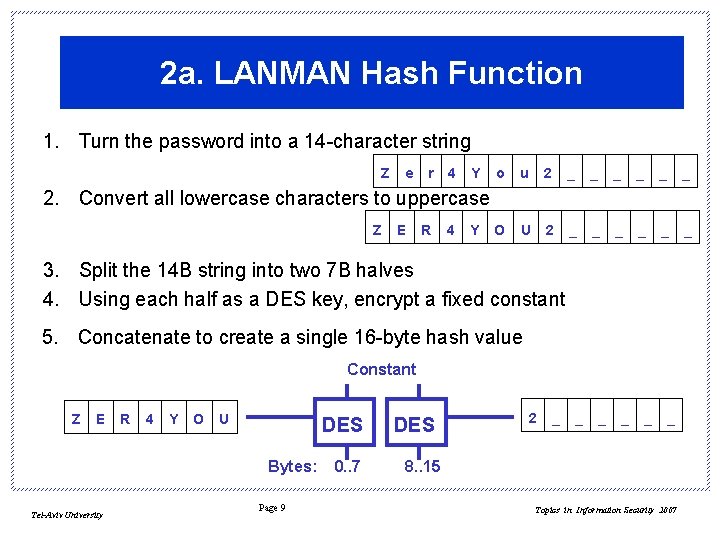
2 a. LANMAN Hash Function 1. Turn the password into a 14 -character string Z e r 4 Y o u 2 _ _ _ O U 2 _ _ _ 2. Convert all lowercase characters to uppercase Z E R 4 Y 3. Split the 14 B string into two 7 B halves 4. Using each half as a DES key, encrypt a fixed constant 5. Concatenate to create a single 16 -byte hash value Constant Z E R 4 Y O U DES Bytes: Tel-Aviv University Page 9 0. . 7 DES 2 _ _ _ 8. . 15 Topics in Information Security 2007

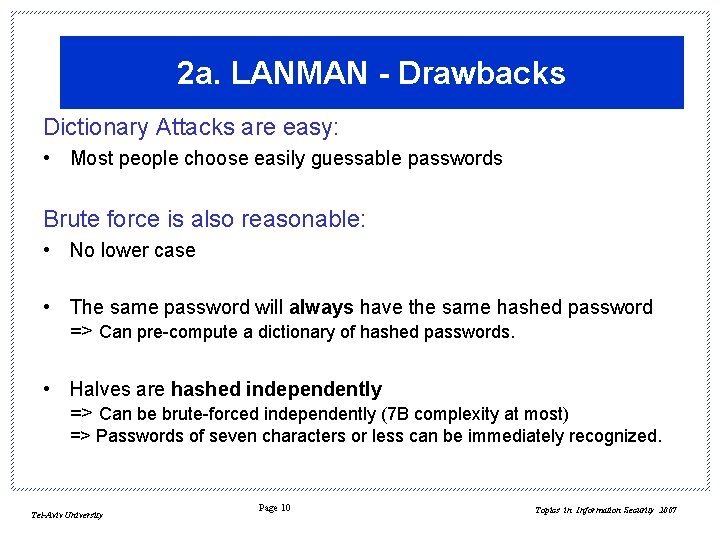
2 a. LANMAN - Drawbacks Dictionary Attacks are easy: • Most people choose easily guessable passwords Brute force is also reasonable: • No lower case • The same password will always have the same hashed password => Can pre-compute a dictionary of hashed passwords. • Halves are hashed independently => Can be brute-forced independently (7 B complexity at most) => Passwords of seven characters or less can be immediately recognized. Tel-Aviv University Page 10 Topics in Information Security 2007

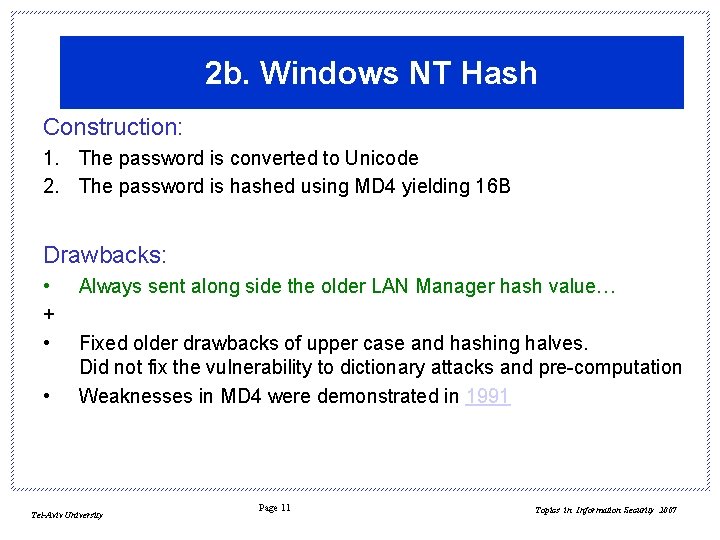
2 b. Windows NT Hash Construction: 1. The password is converted to Unicode 2. The password is hashed using MD 4 yielding 16 B Drawbacks: • + • • Always sent along side the older LAN Manager hash value… Fixed older drawbacks of upper case and hashing halves. Did not fix the vulnerability to dictionary attacks and pre-computation Weaknesses in MD 4 were demonstrated in 1991 Tel-Aviv University Page 11 Topics in Information Security 2007

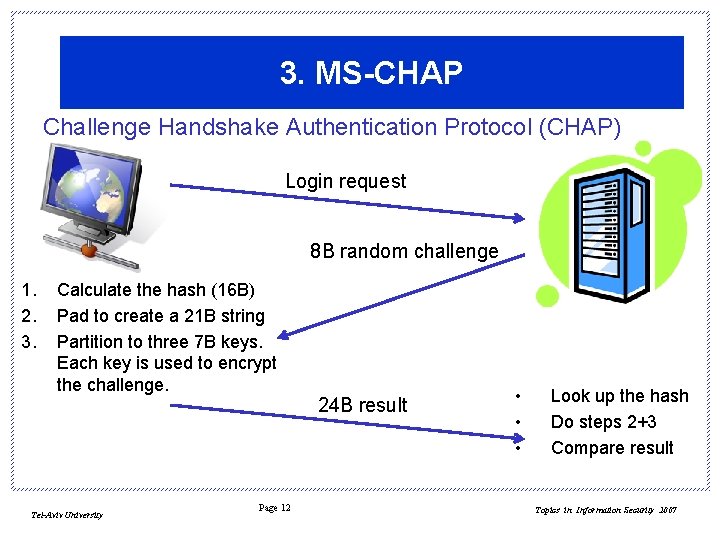
3. MS-CHAP Challenge Handshake Authentication Protocol (CHAP) Login request 8 B random challenge 1. 2. 3. Calculate the hash (16 B) Pad to create a 21 B string Partition to three 7 B keys. Each key is used to encrypt the challenge. Tel-Aviv University Page 12 24 B result • • • Look up the hash Do steps 2+3 Compare result Topics in Information Security 2007

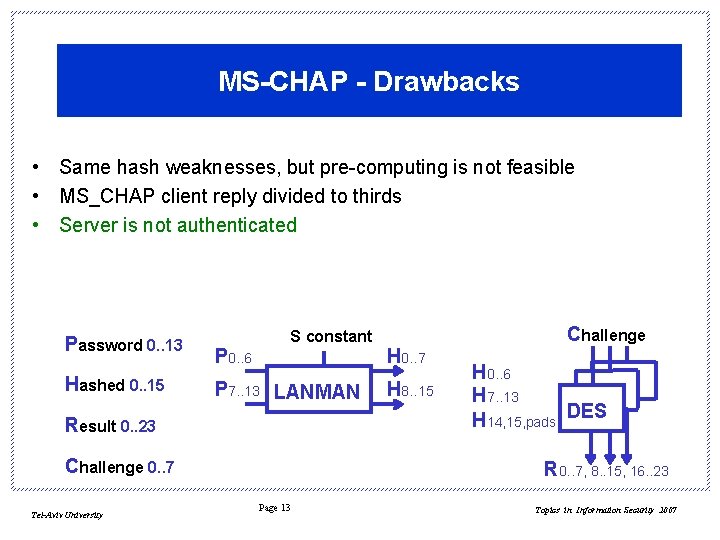
MS-CHAP - Drawbacks • Same hash weaknesses, but pre-computing is not feasible • MS_CHAP client reply divided to thirds • Server is not authenticated Password 0. . 13 Hashed 0. . 15 P 0. . 6 S constant P 7. . 13 LANMAN Result 0. . 23 Challenge 0. . 7 Tel-Aviv University H 0. . 7 H 8. . 15 Challenge H 0. . 6 H 7. . 13 H 14, 15, pads DES R 0. . 7, 8. . 15, 16. . 23 Page 13 Topics in Information Security 2007

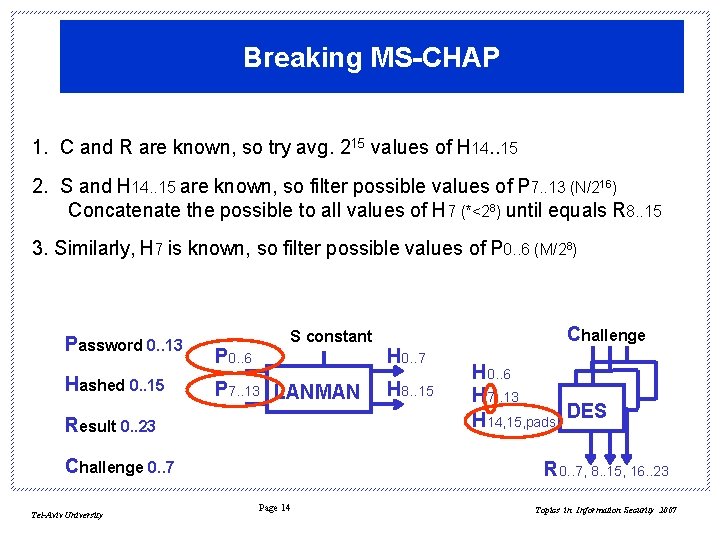
Breaking MS-CHAP 1. C and R are known, so try avg. 215 values of H 14. . 15 2. S and H 14. . 15 are known, so filter possible values of P 7. . 13 (N/216) Concatenate the possible to all values of H 7 (*<28) until equals R 8. . 15 3. Similarly, H 7 is known, so filter possible values of P 0. . 6 (M/28) Password 0. . 13 Hashed 0. . 15 P 0. . 6 S constant P 7. . 13 LANMAN Result 0. . 23 Challenge 0. . 7 Tel-Aviv University H 0. . 7 H 8. . 15 Challenge H 0. . 6 H 7. . 13 H 14, 15, pads DES R 0. . 7, 8. . 15, 16. . 23 Page 14 Topics in Information Security 2007

Outline: • Background • Authentication • Encryption • Other attacks • Follow-up Tel-Aviv University Page 15 Topics in Information Security 2007

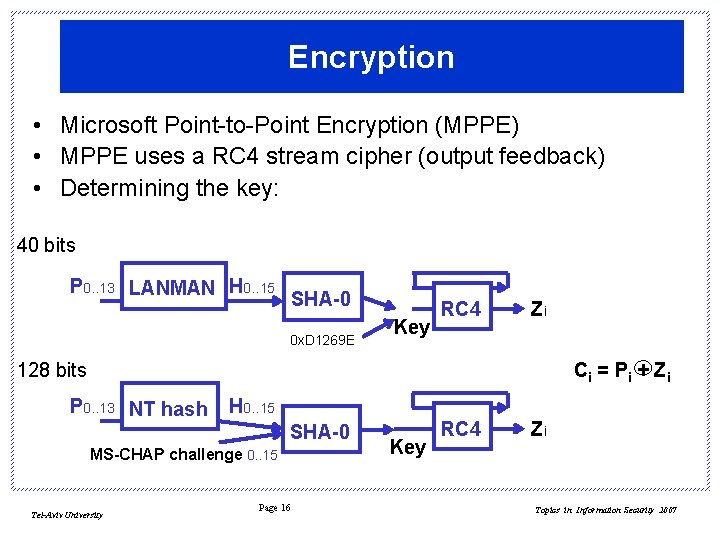
Encryption • Microsoft Point-to-Point Encryption (MPPE) • MPPE uses a RC 4 stream cipher (output feedback) • Determining the key: 40 bits P 0. . 13 LANMAN H 0. . 15 SHA-0 0 x. D 1269 E Key RC 4 Zi 128 bits Ci = P i + Z i P 0. . 13 NT hash H 0. . 15 SHA-0 MS-CHAP challenge 0. . 15 Tel-Aviv University Page 16 Key RC 4 Zi Topics in Information Security 2007

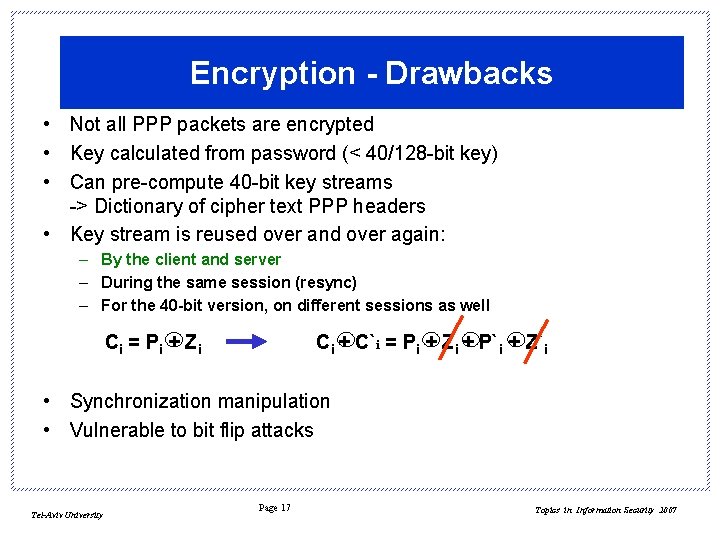
Encryption - Drawbacks • Not all PPP packets are encrypted • Key calculated from password (< 40/128 -bit key) • Can pre-compute 40 -bit key streams -> Dictionary of cipher text PPP headers • Key stream is reused over and over again: – By the client and server – During the same session (resync) – For the 40 -bit version, on different sessions as well Ci = P i + Z i Ci + C`i = Pi + Zi + P`i + Z`i • Synchronization manipulation • Vulnerable to bit flip attacks Tel-Aviv University Page 17 Topics in Information Security 2007

Outline: • Background • Authentication • Encryption • Other attacks • Follow-up Tel-Aviv University Page 18 Topics in Information Security 2007

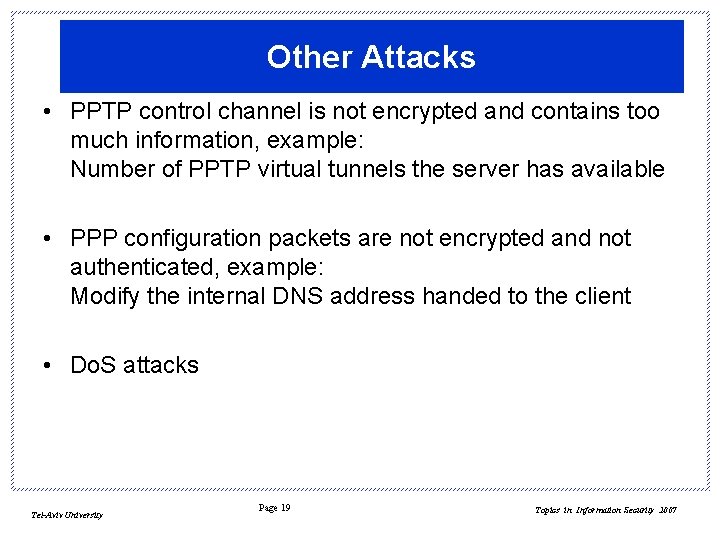
Other Attacks • PPTP control channel is not encrypted and contains too much information, example: Number of PPTP virtual tunnels the server has available • PPP configuration packets are not encrypted and not authenticated, example: Modify the internal DNS address handed to the client • Do. S attacks Tel-Aviv University Page 19 Topics in Information Security 2007

Outline: • Background • Authentication • Encryption • Other attacks • Follow-up Tel-Aviv University Page 20 Topics in Information Security 2007

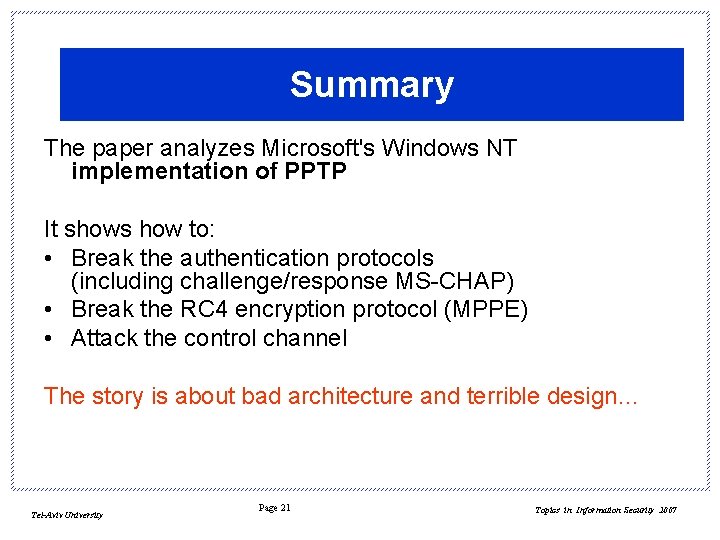
Summary The paper analyzes Microsoft's Windows NT implementation of PPTP It shows how to: • Break the authentication protocols (including challenge/response MS-CHAP) • Break the RC 4 encryption protocol (MPPE) • Attack the control channel The story is about bad architecture and terrible design… Tel-Aviv University Page 21 Topics in Information Security 2007

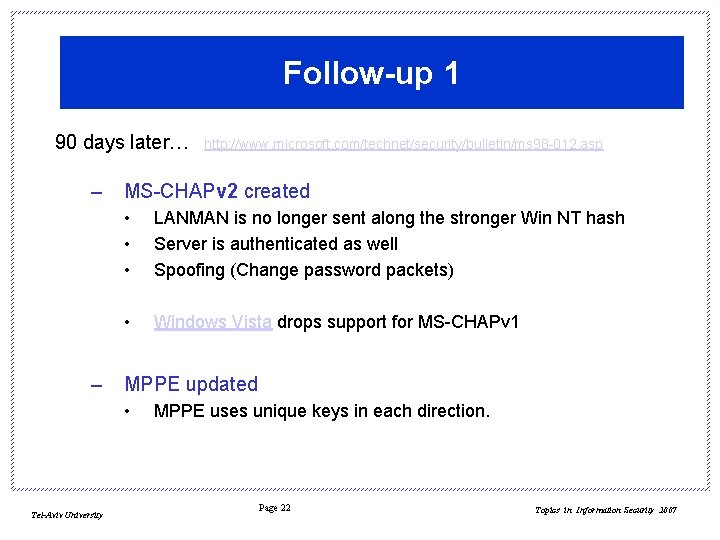
Follow-up 1 90 days later… – – MS-CHAPv 2 created • • • LANMAN is no longer sent along the stronger Win NT hash Server is authenticated as well Spoofing (Change password packets) • Windows Vista drops support for MS-CHAPv 1 MPPE updated • Tel-Aviv University http: //www. microsoft. com/technet/security/bulletin/ms 98 -012. asp MPPE uses unique keys in each direction. Page 22 Topics in Information Security 2007

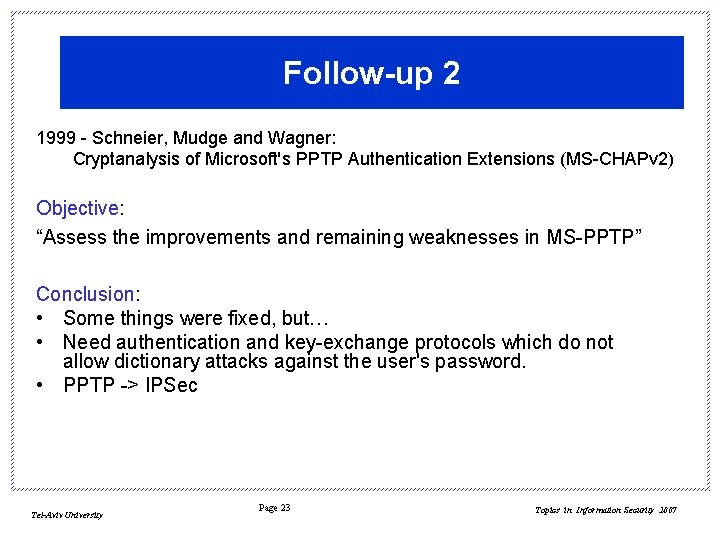
Follow-up 2 1999 - Schneier, Mudge and Wagner: Cryptanalysis of Microsoft's PPTP Authentication Extensions (MS-CHAPv 2) Objective: “Assess the improvements and remaining weaknesses in MS-PPTP” Conclusion: • Some things were fixed, but… • Need authentication and key-exchange protocols which do not allow dictionary attacks against the user's password. • PPTP -> IPSec Tel-Aviv University Page 23 Topics in Information Security 2007

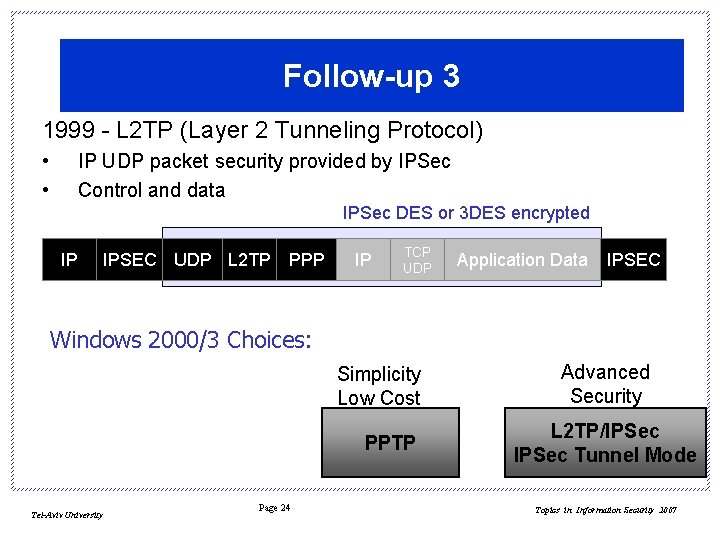
Follow-up 3 1999 - L 2 TP (Layer 2 Tunneling Protocol) • • IP UDP packet security provided by IPSec Control and data IPSec DES or 3 DES encrypted IP IPSEC UDP L 2 TP PPP IP TCP UDP Application Data IPSEC Windows 2000/3 Choices: Simplicity Low Cost PPTP Tel-Aviv University Page 24 Advanced Security L 2 TP/IPSec Tunnel Mode Topics in Information Security 2007

Thank You Questions and Discussions amigos@eng. tau. ac. il Tel-Aviv University Page 25 Topics in Information Security 2007

Home Assignment 1. What is PPTP used for? 2. In one line, define the terms: RC 4, MD 5, SHA, GRE. 3. Demonstrate the “Lan Manager hash function” using a password which is your first name. Assume DES does nothing when the key is all zeroes. 4. The paper was published in 1998. Shortly (2 -3 lines) describe how Microsoft solved the problems presented by this paper. Tel-Aviv University Page 26 Topics in Information Security 2007