Creation of an Actionable Cybersecurity Risk Management Framework

Creation of an Actionable Cybersecurity Risk Management Framework for Digital Financial Services in the Developing World Keith Bowie Associate Research Scholar kb 3171@gsb. columbia. edu 20 th August, 2020 Digital Financial Services Observatory

Introduction

A-RMF Mission Statement The DFSO is developing an actionable Cybersecurity Risk Management Framework (ARMF) for actors involved in the DFS ecosystem in developing countries. This work has been made possible due to a grant from the Bill and Melinda Gates Foundation. Aim of the A-RMF: • Ensure that DFS organizational operations and services are contained within a safe and secure environment that maintains the confidentiality and integrity of data and information. • Secure transactions to limit and confine access and availability to authorized persons/parties. • Acts proactively and reactively to cybersecurity incidents to minimize impact and disruption. NOTE: The A-RMF is currently a DRAFT and is for review only. It is not intended to indicate compliance with any national or regulatory cybersecurity laws and/or regulations

Approach
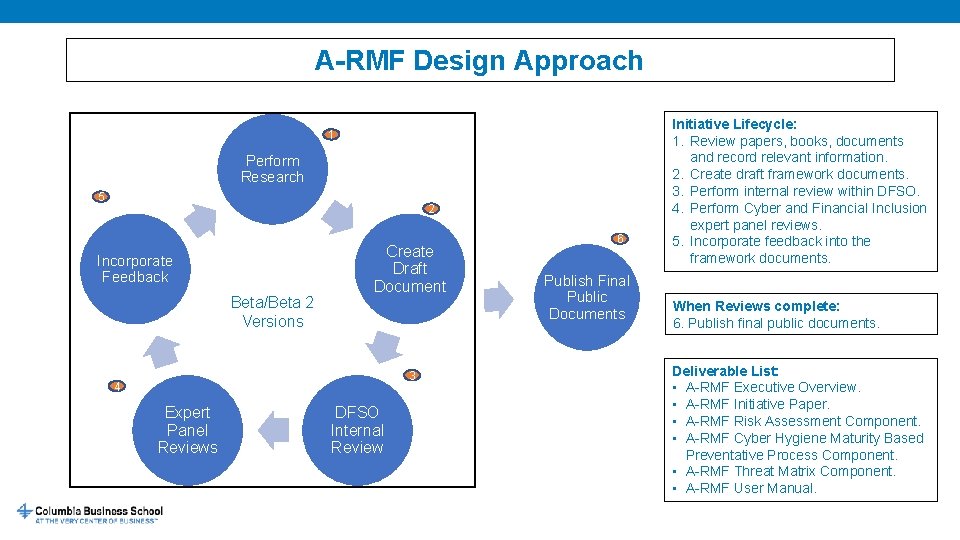
A-RMF Design Approach 1 Perform Research 5 2 Incorporate Feedback Beta/Beta 2 Versions Create Draft Document 3 4 Expert Panel Reviews DFSO Internal Review 6 Publish Final Public Documents Initiative Lifecycle: 1. Review papers, books, documents and record relevant information. 2. Create draft framework documents. 3. Perform internal review within DFSO. 4. Perform Cyber and Financial Inclusion expert panel reviews. 5. Incorporate feedback into the framework documents. When Reviews complete: 6. Publish final public documents. Deliverable List: • A-RMF Executive Overview. • A-RMF Initiative Paper. • A-RMF Risk Assessment Component. • A-RMF Cyber Hygiene Maturity Based Preventative Process Component. • A-RMF Threat Matrix Component. • A-RMF User Manual.
Reference Sources Various reference sources have been consulted during the construction of the A-RMF: • Small sample of documents reviewed: • International standards (ISO 27001, NIST 800. 53 r 4). • Office of the Under Secretary of Defense for Acquisition & Sustainment Cybersecurity Maturity Model Certification V 0. 7 (Note: Latest published version V 1. 02). • Alliance for Financial Inclusion – Cybersecurity for Financial Inclusion: Framework & Risk Guide. • Multiple CGAP publications. • DFSO Reference documents. • People: • Consultation via conference calls, in-person meetings and Web. Ex meetings with: • US and International Cybersecurity experts in financial services and Financial Inclusion. • US and International Financial Inclusion and DFS ecosystem experts. • CGAP and World Bank experts. • Validation that our proposal that the Cybersecurity maturity model approach will be the most beneficial and flexible.

Deliverable Summary and Timeline

A-RMF Deliverables • A-RMF Executive Overview • Brief overview of the initiative and deliverables. • A-RMF Initiative Paper • Description of the initiative, approach and methodology. • A-RMF Risk Assessment Component • Risk Assessment Tool based on FFIEC Cybersecurity Assessment Tool (CAT). • A-RMF Cyber Hygiene Maturity Based Preventative Process Component • Catalog of preventative processes per Cybersecurity maturity/Cybersecurity domain/capability. • A-RMF Threat Matrix Component • Matrix of DFS cybersecurity threats with suggested responses based on cybersecurity maturity. • A-RMF User Manual • Describes the individual component operation and interaction with each other.
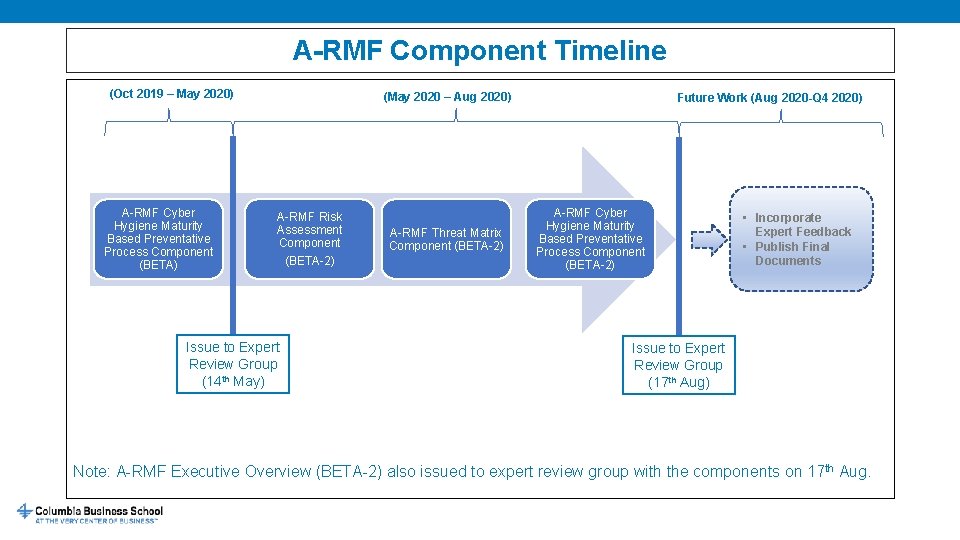
A-RMF Component Timeline (Oct 2019 – May 2020) A-RMF Cyber Hygiene Maturity Based Preventative Process Component (BETA) (May 2020 – Aug 2020) A-RMF Risk Assessment Component (BETA-2) Issue to Expert Review Group (14 th May) A-RMF Threat Matrix Component (BETA-2) Future Work (Aug 2020 -Q 4 2020) A-RMF Cyber Hygiene Maturity Based Preventative Process Component (BETA-2) • Incorporate Expert Feedback • Publish Final Documents Issue to Expert Review Group (17 th Aug) Note: A-RMF Executive Overview (BETA-2) also issued to expert review group with the components on 17 th Aug.

Methodology
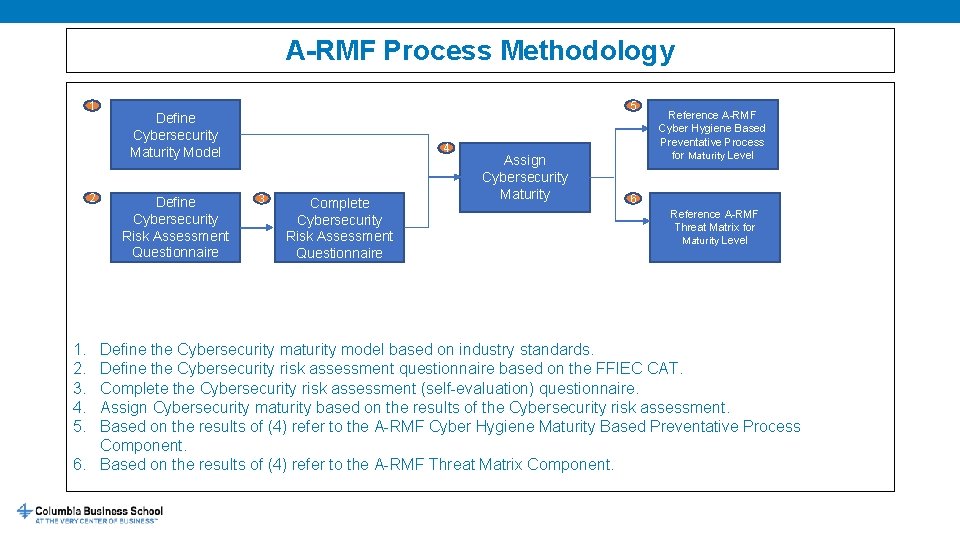
A-RMF Process Methodology 1 2 1. 2. 3. 4. 5. 5 Define Cybersecurity Maturity Model Define Cybersecurity Risk Assessment Questionnaire 4 3 Complete Cybersecurity Risk Assessment Questionnaire Assign Cybersecurity Maturity Reference A-RMF Cyber Hygiene Based Preventative Process for Maturity Level 6 Reference A-RMF Threat Matrix for Maturity Level Define the Cybersecurity maturity model based on industry standards. Define the Cybersecurity risk assessment questionnaire based on the FFIEC CAT. Complete the Cybersecurity risk assessment (self-evaluation) questionnaire. Assign Cybersecurity maturity based on the results of the Cybersecurity risk assessment. Based on the results of (4) refer to the A-RMF Cyber Hygiene Maturity Based Preventative Process Component. 6. Based on the results of (4) refer to the A-RMF Threat Matrix Component.

A-RMF Components
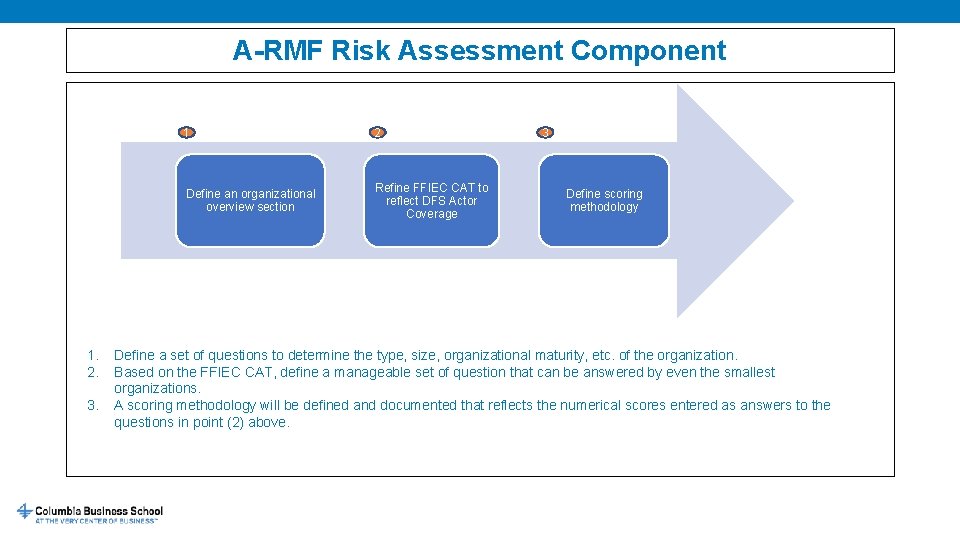
A-RMF Risk Assessment Component 1. 2. 3. 1 2 Define an organizational overview section Refine FFIEC CAT to reflect DFS Actor Coverage 3 Define scoring methodology Define a set of questions to determine the type, size, organizational maturity, etc. of the organization. Based on the FFIEC CAT, define a manageable set of question that can be answered by even the smallest organizations. A scoring methodology will be defined and documented that reflects the numerical scores entered as answers to the questions in point (2) above.
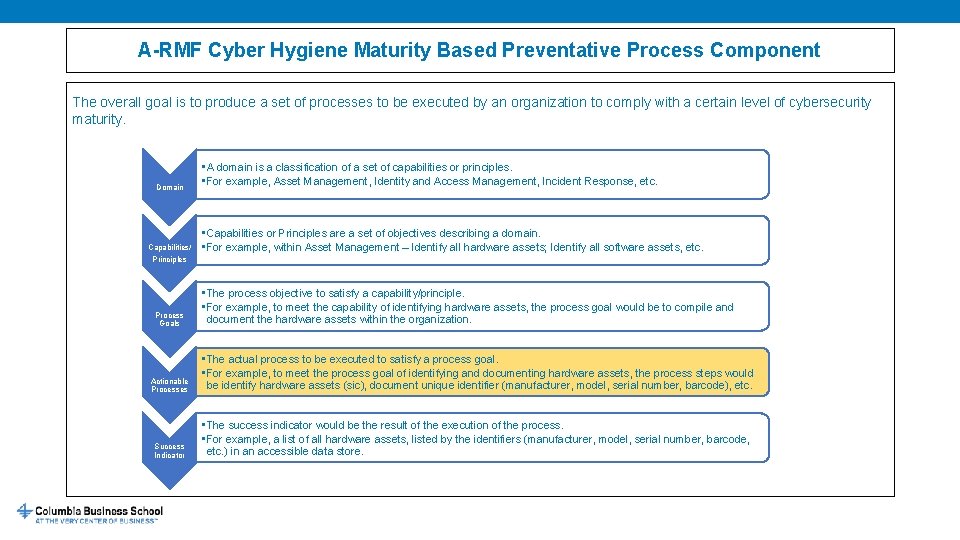
A-RMF Cyber Hygiene Maturity Based Preventative Process Component The overall goal is to produce a set of processes to be executed by an organization to comply with a certain level of cybersecurity maturity. Domain Capabilities/ • A domain is a classification of a set of capabilities or principles. • For example, Asset Management, Identity and Access Management, Incident Response, etc. • Capabilities or Principles are a set of objectives describing a domain. • For example, within Asset Management – Identify all hardware assets; Identify all software assets, etc. Principles Process Goals • The process objective to satisfy a capability/principle. • For example, to meet the capability of identifying hardware assets, the process goal would be to compile and document the hardware assets within the organization. Actionable Processes • The actual process to be executed to satisfy a process goal. • For example, to meet the process goal of identifying and documenting hardware assets, the process steps would be identify hardware assets (sic), document unique identifier (manufacturer, model, serial number, barcode), etc. Success Indicator • The success indicator would be the result of the execution of the process. • For example, a list of all hardware assets, listed by the identifiers (manufacturer, model, serial number, barcode, etc. ) in an accessible data store.
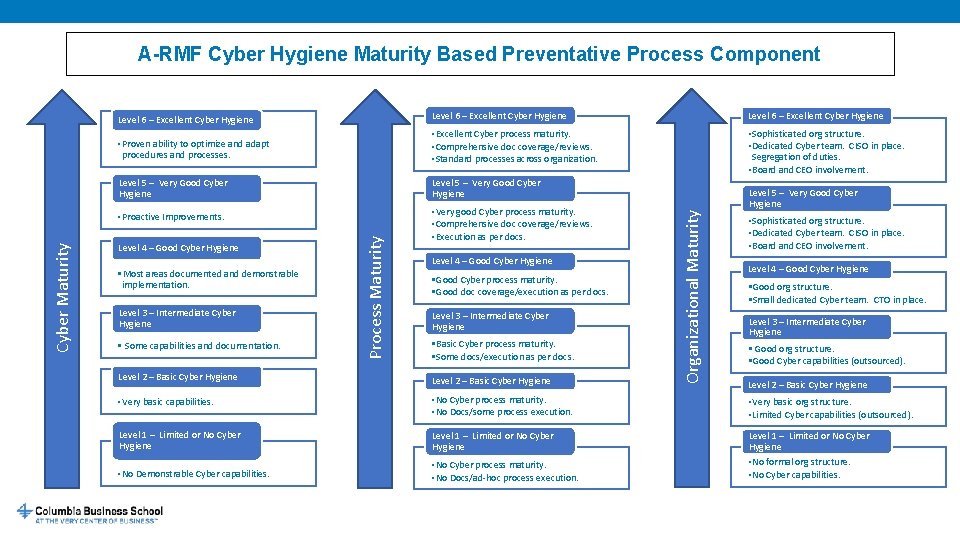
A-RMF Cyber Hygiene Maturity Based Preventative Process Component Level 6 – Excellent Cyber Hygiene • Proven ability to optimize and adapt procedures and processes. • Excellent Cyber process maturity. • Comprehensive doc coverage/reviews. • Standard processes across organization. • Sophisticated org structure. • Dedicated Cyber team. CISO in place. Segregation of duties. • Board and CEO involvement. Level 5 – Very Good Cyber Hygiene Level 4 – Good Cyber Hygiene • Most areas documented and demonstrable implementation. Level 3 – Intermediate Cyber Hygiene • Some capabilities and documentation. Process Maturity Cyber Maturity • Proactive Improvements. • Very good Cyber process maturity. • Comprehensive doc coverage/reviews. • Execution as per docs. Level 4 – Good Cyber Hygiene • Good Cyber process maturity. • Good doc coverage/execution as per docs. Level 3 – Intermediate Cyber Hygiene • Basic Cyber process maturity. • Some docs/execution as per docs. Organizational Maturity Level 6 – Excellent Cyber Hygiene Level 5 – Very Good Cyber Hygiene • Sophisticated org structure. • Dedicated Cyber team. CISO in place. • Board and CEO involvement. Level 4 – Good Cyber Hygiene • Good org structure. • Small dedicated Cyber team. CTO in place. Level 3 – Intermediate Cyber Hygiene • Good org structure. • Good Cyber capabilities (outsourced). Level 2 – Basic Cyber Hygiene • Very basic capabilities. • No Cyber process maturity. • No Docs/some process execution. • Very basic org structure. • Limited Cyber capabilities (outsourced). Level 1 – Limited or No Cyber Hygiene • No Demonstrable Cyber capabilities. • No Cyber process maturity. • No Docs/ad-hoc process execution. • No formal org structure. • No Cyber capabilities. Level 2 – Basic Cyber Hygiene
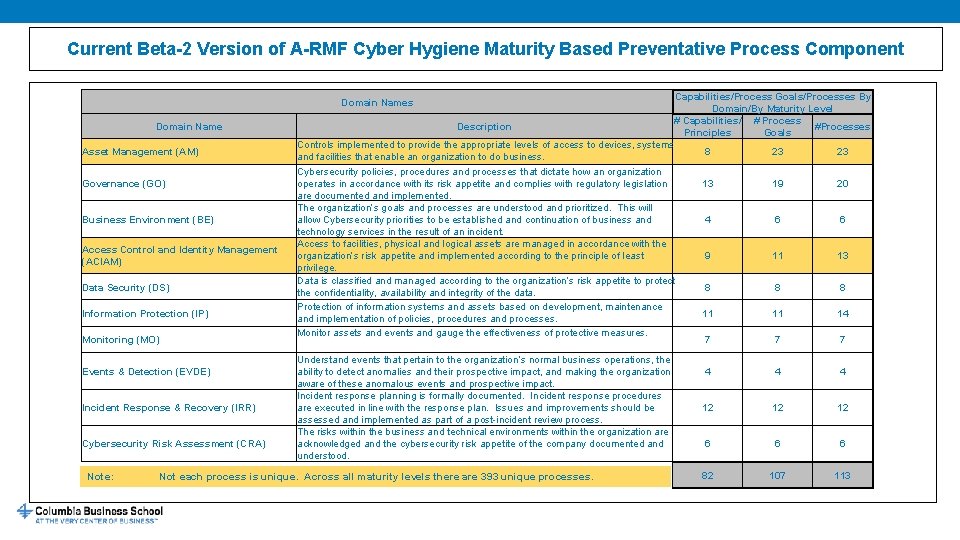
Current Beta-2 Version of A-RMF Cyber Hygiene Maturity Based Preventative Process Component Domain Names Domain Name Asset Management (AM) Governance (GO) Business Environment (BE) Access Control and Identity Management (ACIAM) Data Security (DS) Information Protection (IP) Monitoring (MO) Events & Detection (EVDE) Incident Response & Recovery (IRR) Cybersecurity Risk Assessment (CRA) Note: Description Capabilities/Process Goals/Processes By Domain/By Maturity Level # Capabilities/ # Process #Processes Principles Goals Controls implemented to provide the appropriate levels of access to devices, systems and facilities that enable an organization to do business. Cybersecurity policies, procedures and processes that dictate how an organization operates in accordance with its risk appetite and complies with regulatory legislation are documented and implemented. The organization’s goals and processes are understood and prioritized. This will allow Cybersecurity priorities to be established and continuation of business and technology services in the result of an incident. Access to facilities, physical and logical assets are managed in accordance with the organization’s risk appetite and implemented according to the principle of least privilege. Data is classified and managed according to the organization’s risk appetite to protect the confidentiality, availability and integrity of the data. Protection of information systems and assets based on development, maintenance and implementation of policies, procedures and processes. Monitor assets and events and gauge the effectiveness of protective measures. Understand events that pertain to the organization’s normal business operations, the ability to detect anomalies and their prospective impact, and making the organization aware of these anomalous events and prospective impact. Incident response planning is formally documented. Incident response procedures are executed in line with the response plan. Issues and improvements should be assessed and implemented as part of a post-incident review process. The risks within the business and technical environments within the organization are acknowledged and the cybersecurity risk appetite of the company documented and understood. Not each process is unique. Across all maturity levels there are 393 unique processes. 8 23 23 13 19 20 4 6 6 9 11 13 8 8 8 11 11 14 7 7 7 4 4 4 12 12 12 6 6 6 82 107 113
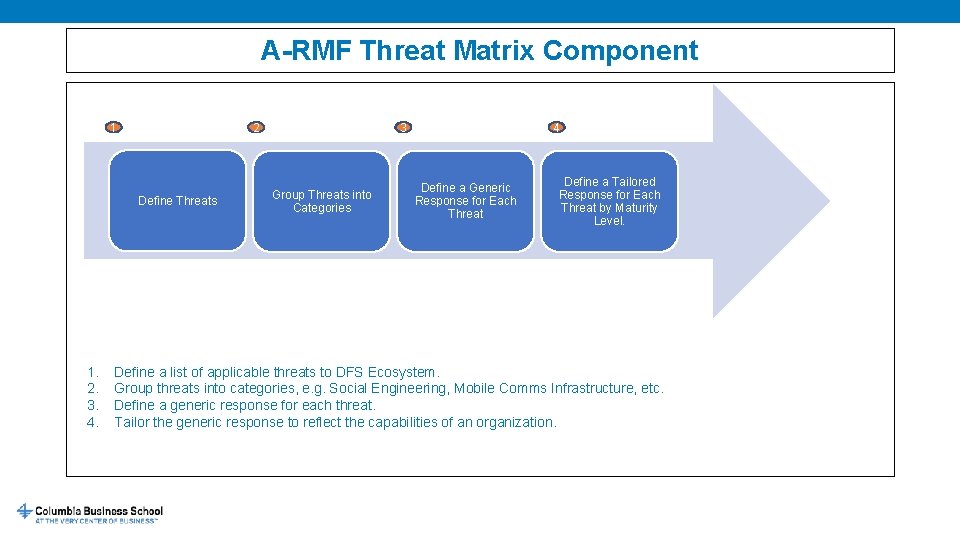
A-RMF Threat Matrix Component 1 2 Define Threats 1. 2. 3. 4. 3 Group Threats into Categories 4 Define a Generic Response for Each Threat Define a Tailored Response for Each Threat by Maturity Level. Define a list of applicable threats to DFS Ecosystem. Group threats into categories, e. g. Social Engineering, Mobile Comms Infrastructure, etc. Define a generic response for each threat. Tailor the generic response to reflect the capabilities of an organization.
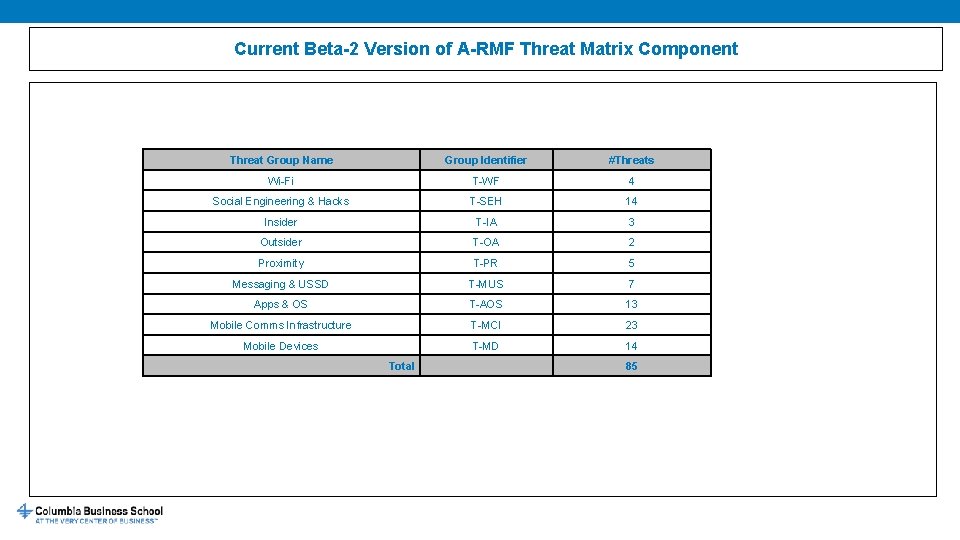
Current Beta-2 Version of A-RMF Threat Matrix Component Threat Group Name Group Identifier #Threats Wi-Fi T-WF 4 Social Engineering & Hacks T-SEH 14 Insider T-IA 3 Outsider T-OA 2 Proximity T-PR 5 Messaging & USSD T-MUS 7 Apps & OS T-AOS 13 Mobile Comms Infrastructure T-MCI 23 Mobile Devices T-MD 14 Total 85

For more information on the DFSO, please visit: www. dfsobservatory. com To become an expert panel member or for more information on the A-RMF, please contact: Keith Bowie - kb 3171@gsb. columbia. edu

Digital Financial Services Observatory www. dfsobservatory. com
- Slides: 20