Creating Signatures at User Agents Comparing Transport Bindings

Creating Signatures at User Agents Comparing Transport Bindings
Use Case Assumptions • A User-Agent is connected to used as a Signature Creation Device, possibly by means of an SSCD. , but cannot perform all verification functions nor all kinds of complex signature creation functions. • This User-Agent may be equipped with a gradual set of signature-related functionality ranging from the simple forwarding of APDUs e. g. according to ISO/IEC 7816 to the (S)SCD to full blown signature functionality according to the different OASIS DSS(-X) profiles. • A User-Agent may have has limited software & performance capabilities and hence may be supported by a remote Digital Signature Service to handle the complexities of the signature creation if it cannot manipulate the document itself. • A User-Agent always initiates the transaction and serves as HTTP-client. • A document may remain on the client or server side s or move from one side to the other. at it’s current location at the Remote-End. • A remote Digital Signature Service may be is used to handle the complexities of the signature creation (see above). • As an example, a User-Agent can be a Mobile Device or an Applet in the browser. • The OASIS DSS Core is used.

Use Case Actor • The End-User of the User-Agent. System • The User-Agent, communicating with a remote system for document handling and signature creation.

Use Case • Basic Flow – Actor selects document. – User Agent remembers the selected document at the remote end. – Actor requests a signing operation for the document. – User Agent asks the user for a PIN or Password. – Actor enters the PIN or Password – User Agent calculates the signature using the (Secure) Signature Creation Device and presents the signed document, at the remote end, to the user. – Actor views the signed document.

System Aspects • The User Agent is capable of creating a raw digital signature; it needs the hash of the document to create the raw signature. • The document is at the Remote End. • Scenario’s – 1: Remote End requests DSS to do the signature creation; DSS delegates the raw signature creation to the User Agent. – 2: Remote End calculates the hash, requests the User Agent to create a raw signature and requests DSS to ‘complete’ the signature creation (the request contains the raw signature). – Case 2 requires the User Agent to have a ‘thin’ implemention of the DSS interface. – Both cases require 2 interactions between the User Agent and the Remote End for the signature creation. 1 2
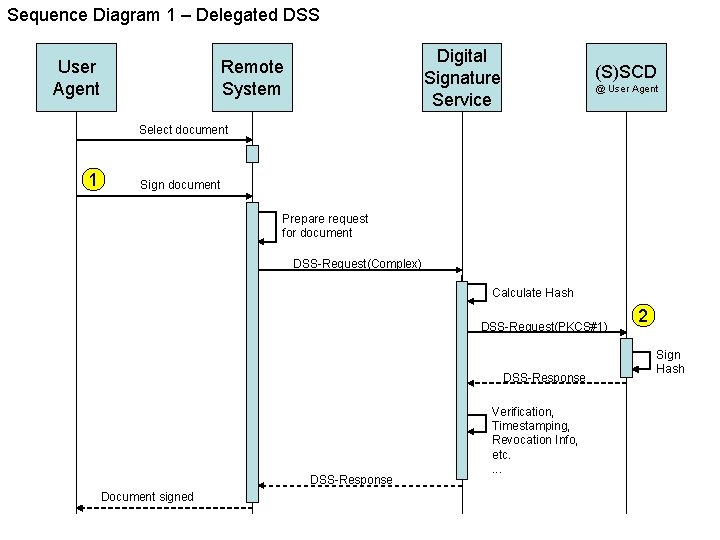
Sequence Diagram 1 – Delegated DSS User Agent Digital Signature Service Remote System (S)SCD @ User Agent Select document 1 Sign document Prepare request for document DSS-Request(Complex) Calculate Hash DSS-Request(PKCS#1) DSS-Response Document signed Verification, Timestamping, Revocation Info, etc. . 2 Sign Hash
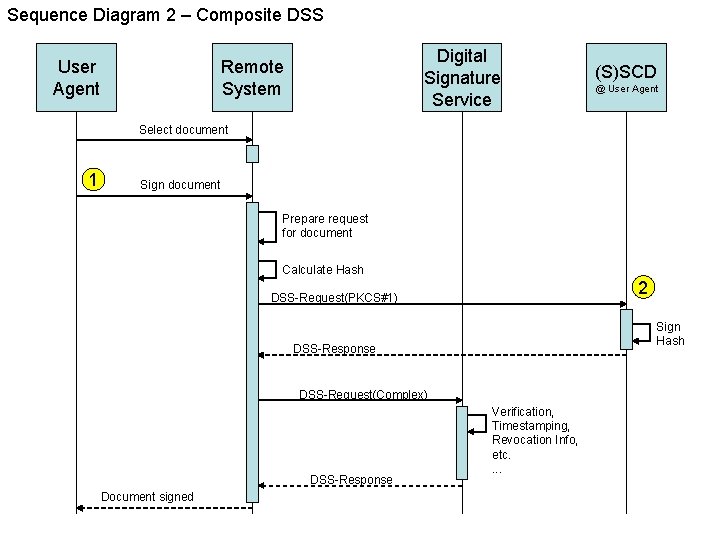
Sequence Diagram 2 – Composite DSS User Agent Digital Signature Service Remote System (S)SCD @ User Agent Select document 1 Sign document Prepare request for document Calculate Hash 2 DSS-Request(PKCS#1) Sign Hash DSS-Response DSS-Request(Complex) DSS-Response Document signed Verification, Timestamping, Revocation Info, etc. .
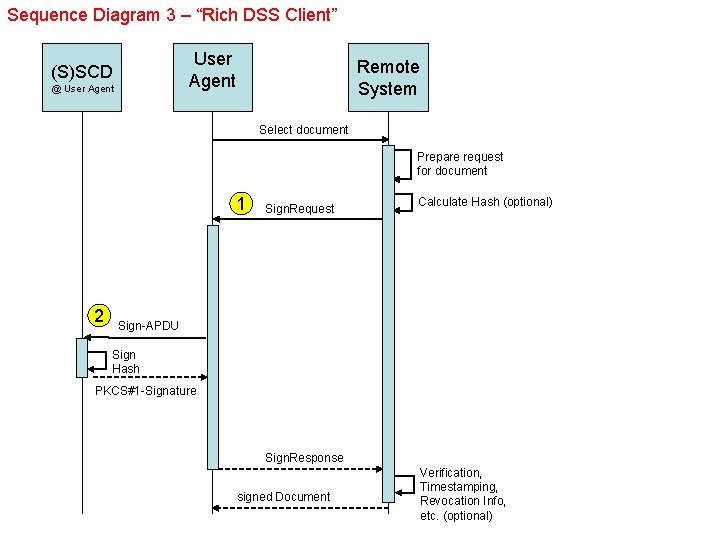
Sequence Diagram 3 – “Rich DSS Client” User Agent (S)SCD @ User Agent Remote System Select document Prepare request for document 1 2 Sign. Request Calculate Hash (optional) Sign-APDU Sign Hash PKCS#1 -Signature Sign. Response signed Document Verification, Timestamping, Revocation Info, etc. (optional)
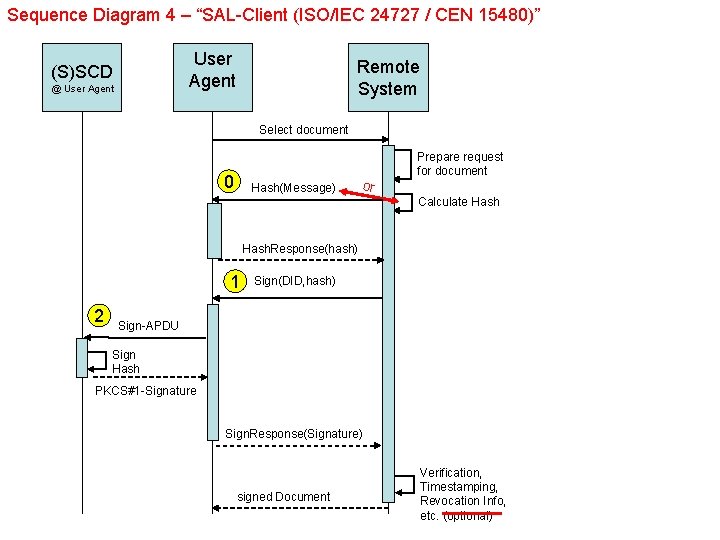
Sequence Diagram 4 – “SAL-Client (ISO/IEC 24727 / CEN 15480)” User Agent (S)SCD @ User Agent Remote System Select document Prepare request for document 0 Hash(Message) or Calculate Hash. Response(hash) 1 2 Sign(DID, hash) Sign-APDU Sign Hash PKCS#1 -Signature Sign. Response(Signature) signed Document Verification, Timestamping, Revocation Info, etc. (optional)
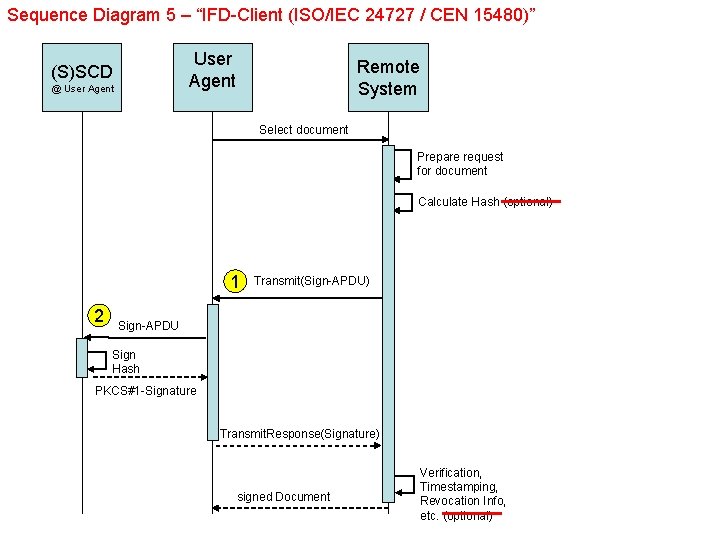
Sequence Diagram 5 – “IFD-Client (ISO/IEC 24727 / CEN 15480)” User Agent (S)SCD @ User Agent Remote System Select document Prepare request for document Calculate Hash (optional) 1 2 Transmit(Sign-APDU) Sign-APDU Sign Hash PKCS#1 -Signature Transmit. Response(Signature) signed Document Verification, Timestamping, Revocation Info, etc. (optional)
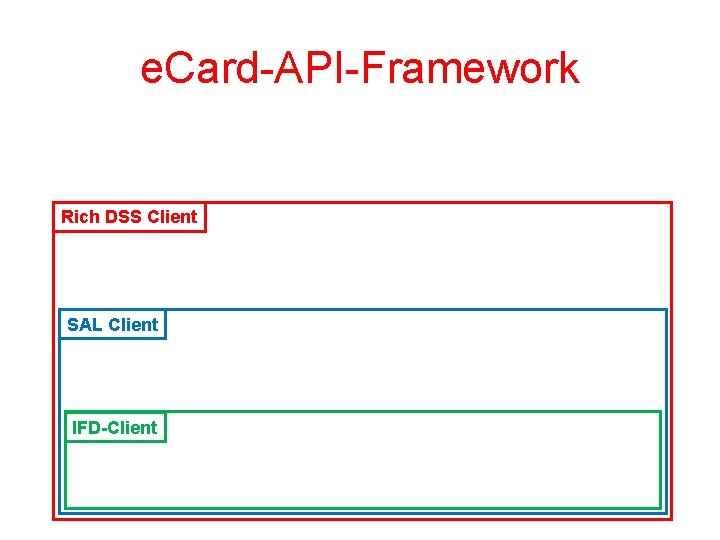
e. Card-API-Framework Rich DSS Client SAL Client IFD-Client
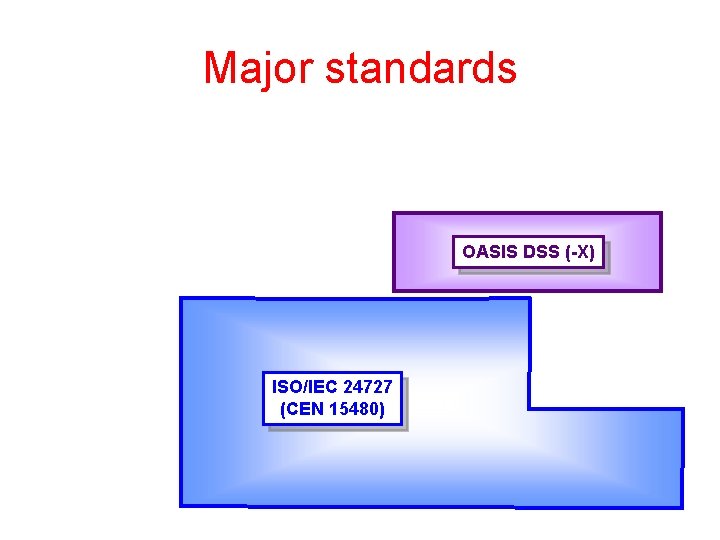
Major standards OASIS DSS (-X) ISO/IEC 24727 (CEN 15480)

Signature-related functions
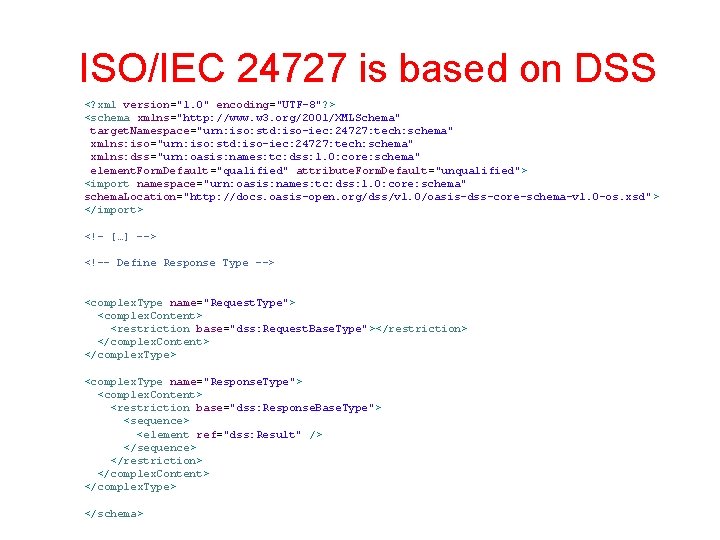
ISO/IEC 24727 is based on DSS <? xml version="1. 0" encoding="UTF-8"? > <schema xmlns="http: //www. w 3. org/2001/XMLSchema" target. Namespace="urn: iso: std: iso-iec: 24727: tech: schema" xmlns: iso="urn: iso: std: iso-iec: 24727: tech: schema" xmlns: dss="urn: oasis: names: tc: dss: 1. 0: core: schema" element. Form. Default="qualified" attribute. Form. Default="unqualified"> <import namespace="urn: oasis: names: tc: dss: 1. 0: core: schema" schema. Location="http: //docs. oasis-open. org/dss/v 1. 0/oasis-dss-core-schema-v 1. 0 -os. xsd" > </import> <!– […] --> <!-- Define Response Type --> <complex. Type name="Request. Type"> <complex. Content> <restriction base="dss: Request. Base. Type"></restriction> </complex. Content> </complex. Type> <complex. Type name="Response. Type"> <complex. Content> <restriction base="dss: Response. Base. Type"> <sequence> <element ref="dss: Result" /> </sequence> </restriction> </complex. Content> </complex. Type> </schema>
Interaction User Agent • Initiate Request – Hash is calculated at the ‘Remote End’ • Create signature – Hash is signed at the User Agent In all cases the client (User Agent) initiates the requests to the Remote End. Possible Transport Bindings: • PAOS, reverse SOAP. • eb. MS v 3, using the ‘polling’ mode. • Two separate SOAP calls.
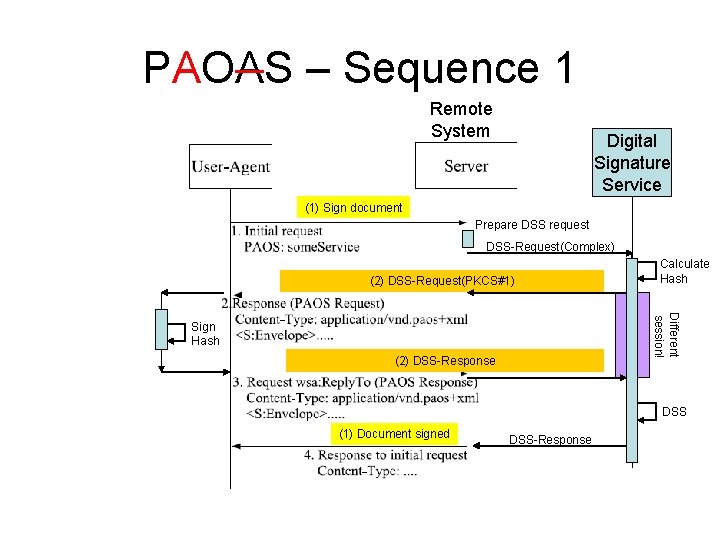
PAOAS – Sequence 1 Remote System Digital Signature Service (1) Sign document Prepare DSS request DSS-Request(Complex) (2) DSS-Request(PKCS#1) Calculate Hash Different session! Sign Hash (2) DSS-Response DSS (1) Document signed DSS-Response
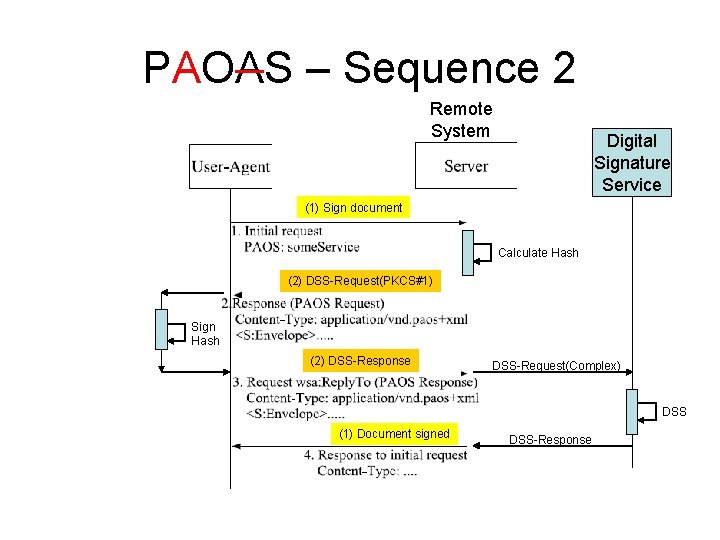
PAOAS – Sequence 2 Remote System Digital Signature Service (1) Sign document Calculate Hash (2) DSS-Request(PKCS#1) Sign Hash (2) DSS-Response DSS-Request(Complex) DSS (1) Document signed DSS-Response
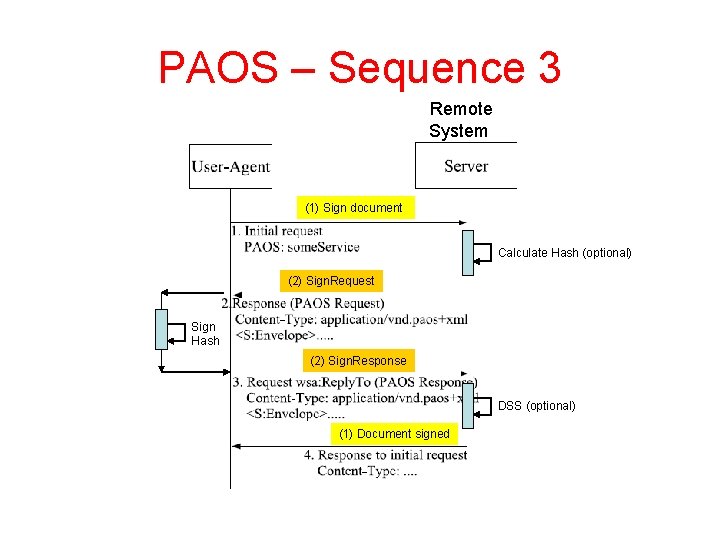
PAOS – Sequence 3 Remote System (1) Sign document Calculate Hash (optional) (2) Sign. Request Sign Hash (2) Sign. Response DSS (optional) (1) Document signed
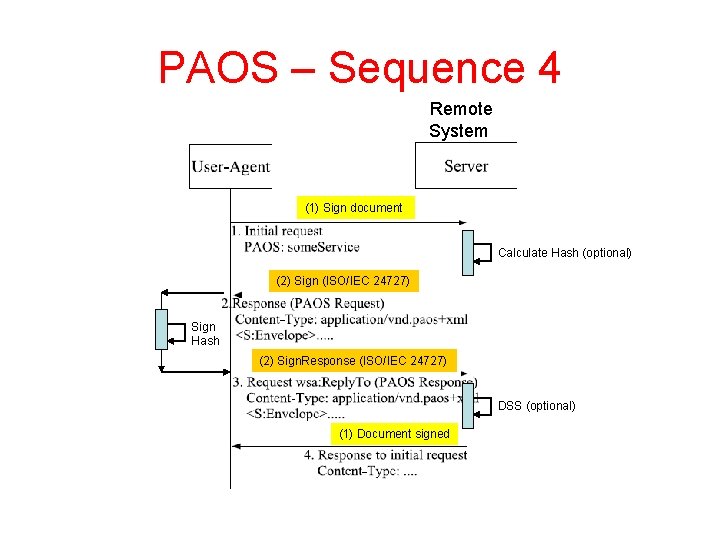
PAOS – Sequence 4 Remote System (1) Sign document Calculate Hash (optional) (2) Sign (ISO/IEC 24727) Sign Hash (2) Sign. Response (ISO/IEC 24727) DSS (optional) (1) Document signed
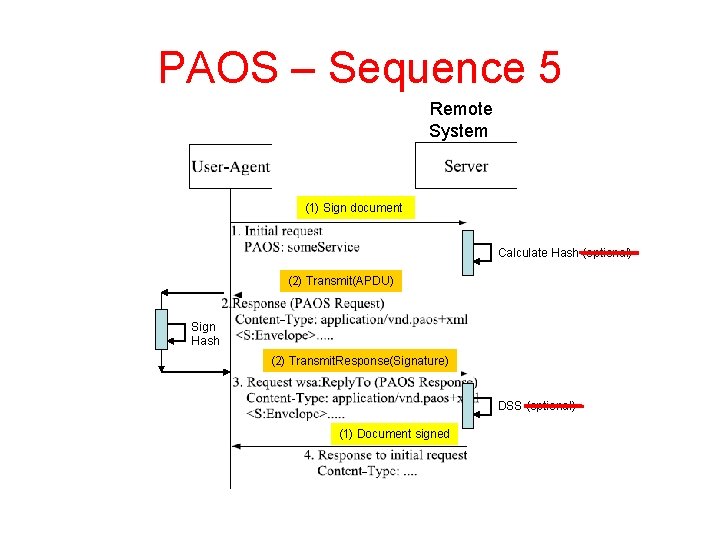
PAOS – Sequence 5 Remote System (1) Sign document Calculate Hash (optional) (2) Transmit(APDU) Sign Hash (2) Transmit. Response(Signature) DSS (optional) (1) Document signed
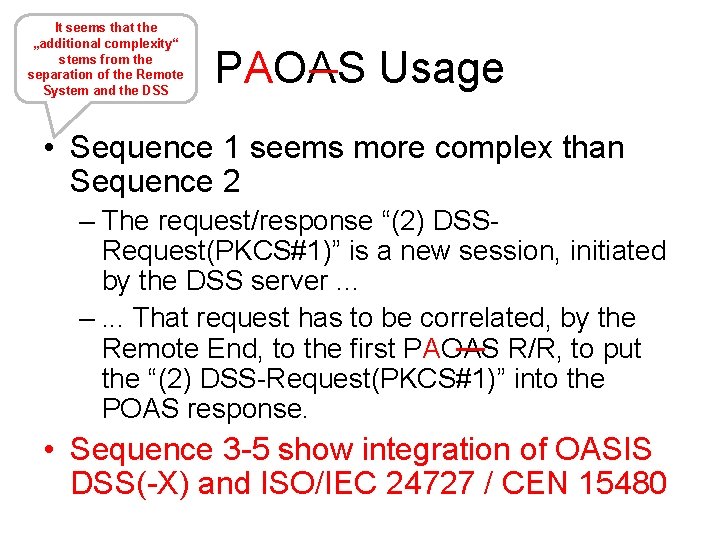
It seems that the „additional complexity“ stems from the separation of the Remote System and the DSS PAOAS Usage • Sequence 1 seems more complex than Sequence 2 – The request/response “(2) DSSRequest(PKCS#1)” is a new session, initiated by the DSS server. . . –. . . That request has to be correlated, by the Remote End, to the first PAOAS R/R, to put the “(2) DSS-Request(PKCS#1)” into the POAS response. • Sequence 3 -5 show integration of OASIS DSS(-X) and ISO/IEC 24727 / CEN 15480
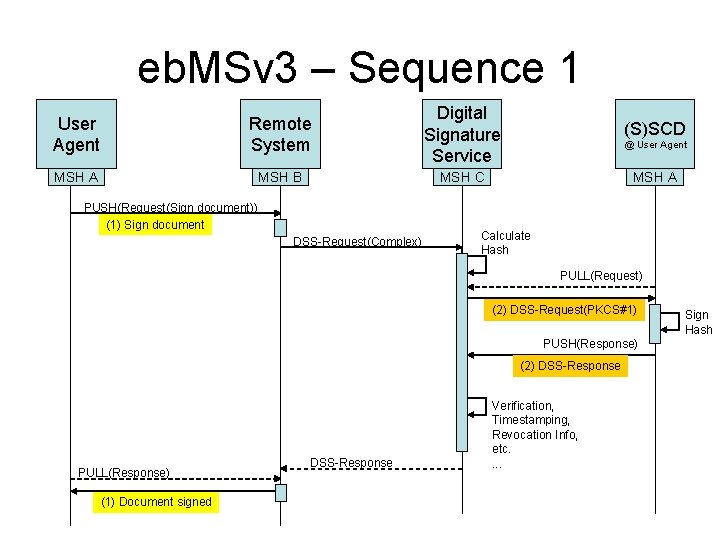
eb. MSv 3 – Sequence 1 User Agent Remote System Digital Signature Service MSH A MSH B MSH C PUSH(Request(Sign document)) (1) Sign document DSS-Request(Complex) (S)SCD @ User Agent MSH A Calculate Hash PULL(Request) (2) DSS-Request(PKCS#1) PUSH(Response) (2) DSS-Response PULL(Response) (1) Document signed DSS-Response Verification, Timestamping, Revocation Info, etc. . Sign Hash
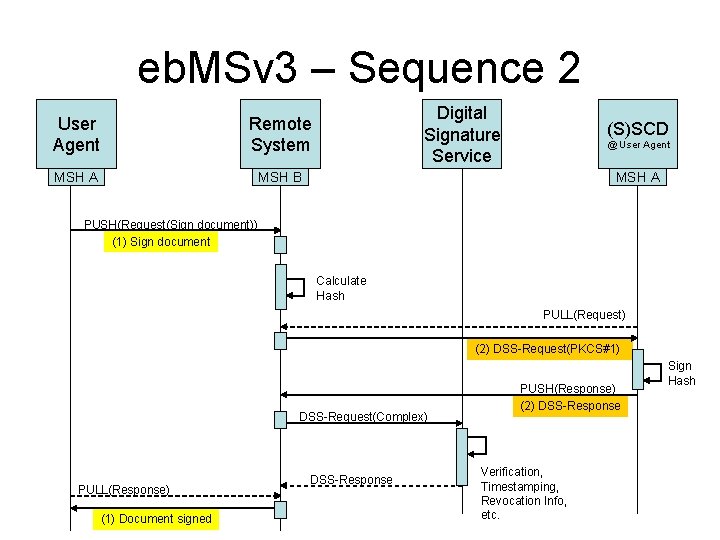
eb. MSv 3 – Sequence 2 User Agent Remote System MSH A MSH B Digital Signature Service (S)SCD @ User Agent MSH A PUSH(Request(Sign document)) (1) Sign document Calculate Hash PULL(Request) (2) DSS-Request(PKCS#1) DSS-Request(Complex) PULL(Response) (1) Document signed DSS-Response PUSH(Response) (2) DSS-Response Verification, Timestamping, Revocation Info, etc. Sign Hash
eb. MS Usage • Sequence 1 – Requires DSS server to use eb. MSv 3 – Pull Request from User Agent has to be routed via the Remote System. • Sequence 2 – Does not require DSS server to use eb. MSv 3 – No routing issue • How does the eb. MSv 3 ‘client’ compare to the PAOAS ‘client’ at the User Agent regarding implementation complexity? • A simple PAOS-applet may be as small as 100 k. B.
- Slides: 24