Creating Confidentiality Agreements that Protect Data and Privacy



































- Slides: 48

Creating Confidentiality Agreements that Protect Data and Privacy: The Challenge of Keeping up With Changes in State and Federal Regulations Elaine S. Reber California Institute of Technology

Agenda • • • Speaker’s Qualifications Background Focus/Goal Access to Data Noteworthy Federal and State Laws Policies versus Confidentiality Statements What do we need to protect data? Summary Questions and Answers 2

Speaker’s Qualifications • Associate Director of Infrastructure for Administrative Applications for Caltech • Oversees the areas of System Administration, Database Administration, Operations, Applications Security, and Telecommunications 3

Background • Caltech’s Mission: To expand human knowledge and benefit society by developing creative scientists and engineers • Students: 900 undergraduates and 1200 graduates • Faculty: 300 Full Time and 700 post-doctoral fellows • Staff: 2, 000 • Research Funding: Over $200 million • Total Budget: ~ $500 million • Caltech administers the JPL (Jet Propulsion Laboratory) budget for NASA. 4

Background (continued) • July 1999 – Caltech upgraded its network and replaced of its legacy administrative systems with new applications, including: – Oracle HRMS and Financials on 10. 7 Network Computing Architecture (NCA) – Exeter Student System – Famis Job Costing System – CEI Purchasing Card System • Since 1999, Caltech has upgraded all of its administrative applications multiple times and has added several 3 rd party applications and tools. 5

Focus/Goal • Understand the challenges of protecting personal data, student information, and financial and business records that we maintain for our community (students, faculty, staff, etc. ) 6

Focus/Goal – continued • Be aware of the laws and regulations that protect the privacy of data • Recognize that security and privacy are different, but security is essential to privacy 1 • Make recommendations to create more robust data security environments on our campuses 1. Dr. Michael Zastrocky, “Higher Education and IT: What’s in the Future, http: //www. njedge. net/conference 2003/presentations/Gartner. ppt 7

Who gets access to protected data? • Internally: – – Human Resources Finance Student Affairs Development Offices – Faculty – Health Care Providers – Administrative Staff – Software Developers – Database Administrators – Application Security Staff – Business Analysts – Internal Auditors – Others 8

Who gets access to protected data? (continued) • Externally: – – – External Auditors 3 rd Party Vendors Gov’t Offices Law Enforcement Officials Schools Requesting Transcripts Organizations Conducting Certain Types of Studies – Others 9

What is the Process for Internal Staff to get Access to Data? – – – Identify Data Needs Identify Appropriate Responsibilities / Privileges Submit Access Request Form/s Obtain Approvals May receive Training May sign Confidentiality / Non-disclosure Agreement or Implied Consent – Receive Logon Credentials from Application Security Office 10

Is that protocol for getting data access sufficient to protect the privacy, security, and integrity of our Institutions’ data? 11

…in a perfect world, YES! But in this world, we face: • • Hackers Viruses Cyber takeovers S/W with security holes H/W with security holes Stolen laptops Opportunists Etc. 12

Perhaps, the laws surrounding privacy of data will fill in the gaps 13

Noteworthy Federal and State Laws • FEDERAL: Ø 1974 – Family Education Right To Privacy Act (FERPA) Ø 1996 – Health Insurance Portability and Accountability Act (HIPAA) Ø 1999 – Financial Services Modernization Act (Gramm-Leach Bliley Act) Ø 2002 – Sarbanes-Oxley (SOX) • STATE: Ø 1977 – California Information Practices Act 14

Family Educational Rights And Privacy Act of 1974 - FERPA (20 U. S. C § 1232 g) • FERPA, also known as the Buckley Amendment, is a federal law that protects the privacy of student education records. It is administered by the Family Policy Compliance Office (FPCO) at the U. S. Education Department. 1 • The Act went into law on 19 November 1974 and has been amended several times since its enactment. It applies to all educational agencies and institutions that are the recipients of federal funding. 2 • Schools are required to notify parents and eligible students annually of their rights under FERPA. 3 1. http: //chronicle. com/cgi-bin/printable. cgi? article=http: //dhronicle. com/weekly/v 50/i 06/06 a 02202. htm 2. http: //www. ed. gov/print/policy/gen/guid/fpco/ferpa/leg-history. html 3. Ibid. 15

FERPA - continued (20 U. S. C § 1232 g) • Schools may not furnish or release identifiable personal information without written consent specifying the records to be released, the reasons for release, and parties to whom they are being released. 1 The same rules apply to third parties acting on behalf of the schools. 2 • The act also provides the “eligible student” (18 years or older or attending post-secondary school) and parents the right to inspect and review education records, to seek to amend those records, and to limit disclosure of information from those records. 3 1. http: //www. ed. gov/print/policy/gen/guid/fpco/ferpa/leg-history. html 2. http: //nces. ed. gov/pubs 97/web/97859. asp 3. http: //www. ed. gov/print/policy/gen/guid/fpco/ferpa/index. html 16

FERPA - continued (20 U. S. C § 1232 g) • Any data collected by authorized officials must be protected from unauthorized access. It is the requester’s responsibility to destroy the data after it is no longer needed. 1 • Each school is required to keep a record of every request for student education information. Only the parents, the “eligible student”, and school officials responsible for the custody of records and auditing the system may see this information. 2 1. http: //www. epic. org/privacy/education/ferpa. html 2. http: //www. ed. gov/print/policy/gen/guid/fpco/ferpa/leg-history. html 17

FERPA - continued (20 U. S. C § 1232 g) • Growing demands for institutional accountability, greater transparency, and national security have increased the challenge of protecting student data. 1 • Various State Freedom-of-Information Acts, The 2001 USA Patriot Act, and the 2001 No Child Left Behind Act also require schools to provide student information under certain circumstances. 1. http: //chronicle. com/prm/weekly/v 50/i 42/42 b 00401. htm 2. http: //chronicle. com/prm/weekly/v 50/i 42/42 b 00401. htm 3. http: //www. ed. gov/print/policy/gen/guid/fpco/ferpa/leg-history. html 18

FERPA - continued (20 U. S. C § 1232 g) • The National Center for Education Statistics (NCES) is studying the feasibility of requiring colleges to provide “unit record (individually identifiable)” data rather than “aggregate” data for reporting. 1 • Officials at the Department of Education claim that “unit record” data would make it easier to measure a college’s retention and graduation rates and the net cost of tuition after financial aid is taken into account. 2 • FERPA would need to be amended to allow the release of student records without permission from the parents or student. 3 1. CLHE, The Campus Privacy Letter, Volume 1, No. 1, December 2004; http: //www. clhe. org/campusprivacy/cplv 1 n 1. pdf 2. Ibid. 3. http: //chronicle. com/weekly/v 5/i 14/14 a 2201. htm 19

Health Insurance Portability and Accountability Act (HIPAA) • HIPAA was implemented in 1996. The final HIPAA Security Rule establishing health data security standards was published in 2003. • The main goals of HIPAA are to: 1. Make the health care system more efficient, especially through increased use of electronic resources, and 2. Make health insurance more portable (“portability”) when persons change employers. 1, 1. http: //privacy. med. miami. edu/glossary/xd_hipaa. htm 20

HIPAA (continued) • HIPAA protects private health information. Health plans, health care clearinghouses, health providers, and other organizations that process, transmit, and/or store Protected Health Information (PHI) in electronic form are covered by the Act. 1 • PHI is any individually identifiable health information. • HIPAA is administered by the federal Department of Health and Human Services. 1. Marne Gordon, HIPAA Security Standards Cybertrust Implementation and Strategy and Management, 2005, http: //www. trusecure. com/cgi-bin/download. cgi? ESCD=W 0188&file=wp_HIPAA_Cybertrust. pdf 21

HIPAA (continued) • In general, covered entities are required to: – Ensure the confidentiality, integrity, and availability of all electronic PHI they create, receive, maintain, or transmit – Protect against threats or hazards to the security and integrity of the PHI – Protect against unauthorized disclosures of PHI – Ensure compliance by employees of the covered organization 1 1. Marne Gordon, HIPAA Security Standards Cybertrust Implementation and Strategy and Management, 2005, http: //www. trusecure. com/cgi-bin/download. cgi? ESCD=W 0188&file=wp_HIPAA_Cybertrust. pdf 22

HIPAA, FERPA, and State Laws • The definition of protected health information (PHI) under the Health Insurance Portability and Accountability Act (HIPAA), specifically excludes identifiable health information in "education records" subject to the Family Education Rights and Privacy Act (FERPA, 20 USC 1232 g). 1 • FERPA provides privacy protections for student health records held by federally funded educational institutions. 2 • If State laws are more stringent than HIPAA, then HIPAA gives way to State law. 3 1. http: //privacy. med. miami. edu/glossary/xd_education_records. htm 2. Ibid. 3. http: //www. bowditch. com/PDF/HIPPA. pdf 23

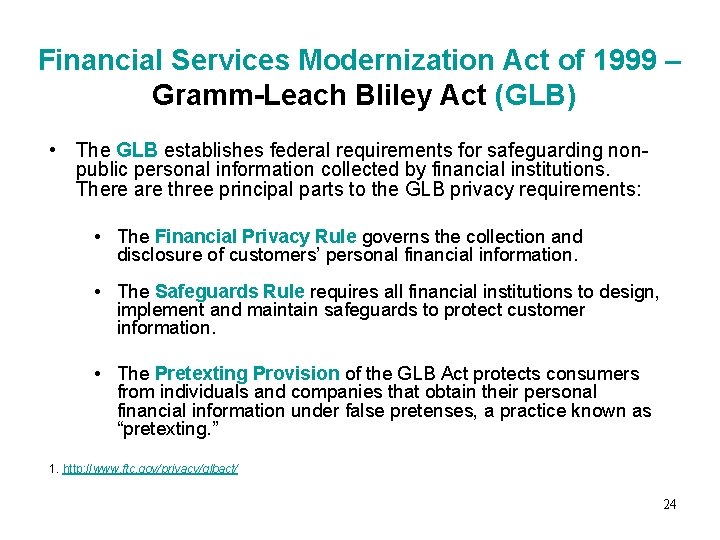
Financial Services Modernization Act of 1999 – Gramm-Leach Bliley Act (GLB) • The GLB establishes federal requirements for safeguarding nonpublic personal information collected by financial institutions. There are three principal parts to the GLB privacy requirements: • The Financial Privacy Rule governs the collection and disclosure of customers’ personal financial information. • The Safeguards Rule requires all financial institutions to design, implement and maintain safeguards to protect customer information. • The Pretexting Provision of the GLB Act protects consumers from individuals and companies that obtain their personal financial information under false pretenses, a practice known as “pretexting. ” 1. http: //www. ftc. gov/privacy/glbact/ 24

Gramm-Leach Bliley Act (GLB) continued • The GLB requires financial institutions to establish an information security program that will: • Insure the security and confidentiality of customer information; • Protect against any anticipated threats or hazards to the security or integrity of such information; and • Protect against unauthorized access to or use of such information that could result in substantial harm or inconvenience to any customer. 1 1. Federal Register / Vol. 67, No. 100 / Thursday, May 23, 2002 / Rules and Regulations 25

Gramm-Leach Bliley Act (GLB) continued • The GLB preempts only “inconsistent” state laws. It sets a minimum standard beyond which states may pass stricter laws. 1 1. http: //www. the-dma. org/government/grammleachblileyact. shtml 26

Sarbanes-Oxley Act of 2002 (SOX) • SOX sets new financial accountability standards for publicly held companies and their audit firms. • SOX does not apply to nonprofits, but companies that rate bonds for universities advise them to follow its guidelines. Investors are asking for “more disclosure and transparency of information. ” 1 • Officials in several States (California, Maryland, and New York) have proposed legislation to require nonprofits to follow the same rules as publicly traded companies. 2 1. http: //chronicle. com/weekly/v 50/i 23/23 a 02602. htm 2. http: //chronicle. com/weekly/v 50/i 18/18 a 03201. htm 27

SOX - continued • Some universities have already adopted reforms in response to SOX, such as: – – – Clarifying procedures for preparation and certification of financial statements Establishing policies for disclosure of transactions not usually included in main budget reports Creating standards for audit committees of governing boards Modifying code of ethics for senior financial officers Increasing protection for whistle-blowers 1 1. http: //chronicle. com/weekly/v 50/i 18/18 a 03201. htm 28

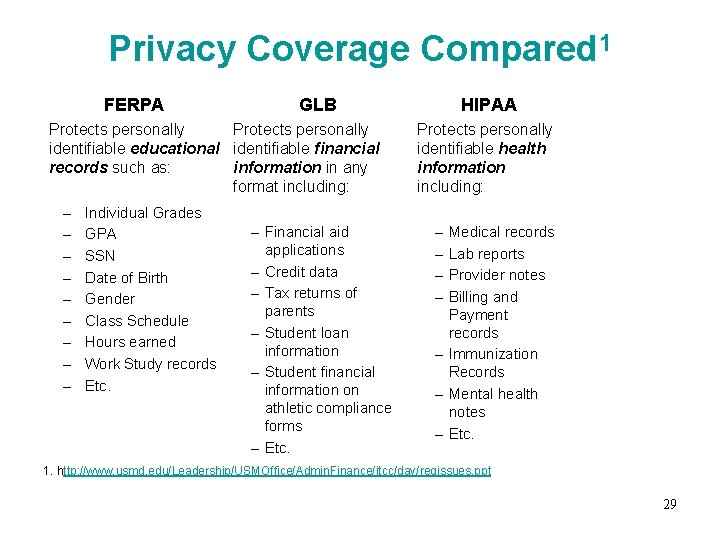
Privacy Coverage Compared 1 FERPA GLB Protects personally identifiable educational identifiable financial records such as: information in any format including: – – – – – Individual Grades GPA SSN Date of Birth Gender Class Schedule Hours earned Work Study records Etc. – Financial aid applications – Credit data – Tax returns of parents – Student loan information – Student financial information on athletic compliance forms – Etc. HIPAA Protects personally identifiable health information including: – – Medical records Lab reports Provider notes Billing and Payment records – Immunization Records – Mental health notes – Etc. 1. http: //www. usmd. edu/Leadership/USMOffice/Admin. Finance/itcc/day/regissues. ppt 29

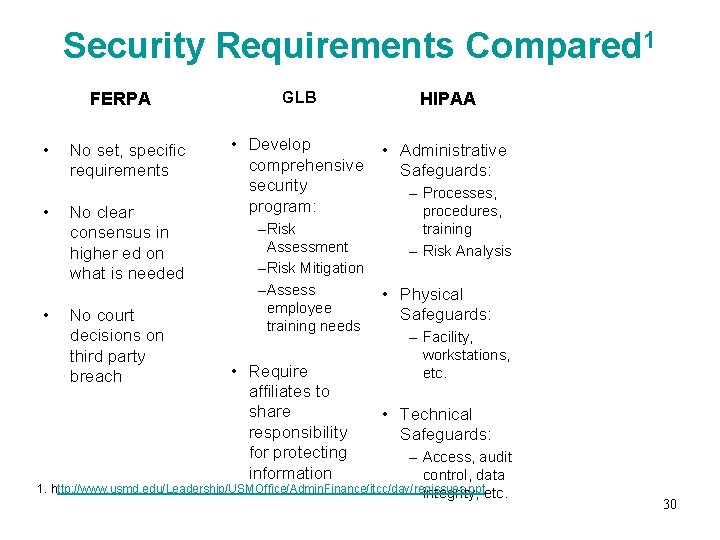
Security Requirements Compared 1 FERPA • • • No set, specific requirements No clear consensus in higher ed on what is needed No court decisions on third party breach GLB HIPAA • Develop comprehensive security program: • Administrative Safeguards: –Risk Assessment –Risk Mitigation –Assess employee training needs • Require affiliates to share responsibility for protecting information – Processes, procedures, training – Risk Analysis • Physical Safeguards: – Facility, workstations, etc. • Technical Safeguards: – Access, audit control, data 1. http: //www. usmd. edu/Leadership/USMOffice/Admin. Finance/itcc/day/regissues. ppt integrity, etc. 30

California Information Practices Act (California Civil Code §§ 1798) • Applies to California state agencies, including state -funded educational institutions. • Does not apply to student records, but does apply to records of potential students before enrollment, i. e. , records of applicants for admission. 1 • Establishes requirements for the collection, maintenance, and dissemination of any information that identifies or describes an individual. 2 1. http: //www. ucop. edu/ucophome/policies/bfb/rmp 8. html 2. Ibid. 31

California Information Practices Act (California Civil Code §§ 1798) - continued • Any information that identifies or describes an individual, the disclosure of which would constitute an unwarranted invasion of personal privacy, is considered personal information. Common types of personal information are: – – – – Birth date Citizenship Social Security Number Income Tax Withholding Information Performance evaluations Letter of corrective actions Names of spouse or other relatives 1 1. http: //www. ucop. edu/ucophome/policies/bfb/rmp 8. html 32

California Information Practices Act (California Civil Code §§ 1798) - continued • In recent years, the Act has been amended to require: – Notification of security breaches involving personal information 1 – Greater protection of Social Security Numbers (SSNs) by: • • • Reducing collection of SSNs Explaining the purpose of the collection, the intended use, whether it is mandatory, and consequences of refusing to provide SSN Eliminating public display of SSNs Controlling access to SSNs Improving security safeguards Making the organization accountable for protecting SSNs 2 1. http: //www. privacy. ca. gov/recommendations/secbreach. pdf 2. http: //www. privacy. ca. gov/recommendations/ssnrecommendations. pdf 33

Are the laws really sufficient to protect the privacy, security, and integrity of our Institutions’ data? 34

…in a perfect world, YES! But in this world, we face: • • Hackers Viruses Cyber takeovers S/W with security holes H/W with security holes Opportunists Legislation is not enough 35

Maybe policies and confidentiality agreements will fill in the gaps. 36

What is a Policy? A policy is “a definite course or method of action selected from among alternatives and in light of given conditions to guide and determine present and future decisions. ” 1 1. Webster’s Ninth New Collegiate Dictionary 37

What is a Confidentiality Agreement? A Confidentiality Agreement (or Non-disclosure Agreement) is a document that, when signed, will allow one party to discuss their confidential information (including their work and ideas) with other interested parties. It legally binds those parties to keep the information confidential and not to disclose it to third parties. 1. King’s College of London: Technology Transfer Group 38

What is a Confidentiality Agreement? (continued) A Confidentiality Agreement should give the purpose for the disclosure and also state that the receiving party shall not be permitted to use the confidential information for any purpose except the one defined in the agreement (e. g. , to evaluate their interest in collaborating/investing in the ideas/work). 1 1. King’s College of London: Technology Transfer Group 39

Will policies and confidentiality statements increase the likelihood that we can protect the privacy, security, and integrity of our Institutions’ data? 40

Not really…. Then, what do we Need? • Commitment from the University Leadership • IT security group/CSO • Resources • Institute Privacy Policies 41

Not really…. Then, what do we Need? (cont) • Institute Policies for the Acceptable Use of Electronic Information Resources • Confidentiality/ Non-Disclosure Agreements or Implied Consent • Active User Awareness Training • Periodic Risk Assessments • Firewalls • SSL 42

Not really…. Then, what do we Need? (cont) • • • Strong Authentication / Single Sign On Authorization Anti Virus Software Vigilant Network Monitoring Incident Reporting Enforcement 43

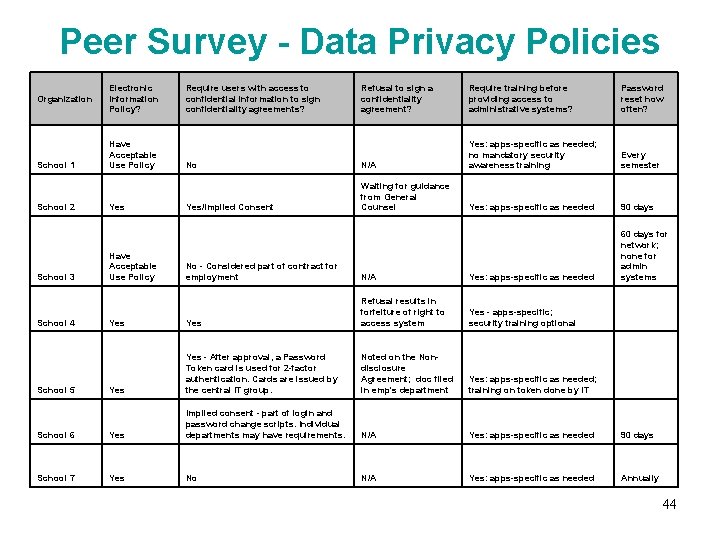
Peer Survey - Data Privacy Policies Organization School 1 School 2 Electronic Information Policy? Have Acceptable Use Policy Yes Have Acceptable Use Policy Require users with access to confidential information to sign confidentiality agreements? Refusal to sign a confidentiality agreement? Require training before providing access to administrative systems? Password reset how often? No N/A Yes: apps-specific as needed; no mandatory security awareness training Every semester Yes/Implied Consent Waiting for guidance from General Counsel Yes: apps-specific as needed 90 days 60 days for network; none for admin systems No - Considered part of contract for employment N/A Yes: apps-specific as needed Yes Refusal results in forfeiture of right to access system Yes - apps-specific; security training optional Yes - After approval, a Password Token card is used for 2 -factor authentication. Cards are issued by the central IT group. Noted on the Nondisclosure Agreement; doc filed in emp's department Yes: apps-specific as needed; training on token done by IT School 6 Yes Implied consent - part of login and password change scripts. Individual departments may have requirements. N/A Yes: apps-specific as needed 90 days School 7 Yes No N/A Yes: apps-specific as needed Annually School 3 School 4 School 5 44

Summary • To protect the privacy of our data; we need Ø Legislation Ø Institute commitment Ø Institute policy statements Ø Confidentiality statements Ø User awareness training programs Ø Develop Best Practices Ø Pro-Active Network Monitoring Ø Antivirus Protection 45

Summary • Authentication/Authorization • Utilize the experts Ø Legal Department Ø Risk Management Ø Human Resources Ø Security Department Ø Local Law Enforcement Ø Peer Institutions • Enforcement 46

Questions and Answers 47

Thank you! Elaine. reber@caltech. edu 48