Creating a Zero Incident Culture Copyright 2004 Melissa





















































































































- Slides: 123

Creating a Zero Incident Culture Copyright 2004. Melissa Guenther, LLC. All rights reserved.

Measurement Measuring the effectiveness of security awareness programs usually becomes an assessment of security incident statistics. This is basically an exercise in measuring luck.

• A common thread of those that had success with security awareness efforts- giving people clear direction and immediately enlisting their energies in creating that future. • Involvement in security awareness efforts in academia, Fortune 100 and small businesses – variety of situations with one constant. People. • Regardless of presenting issues, success ultimately boils down to meeting a challenge, solving a problem, or forging a better future. And it takes people to accomplish these feats. Even if you define change as implementing technical solutions, such as a Firewall or automatic update installations, technology doesn’t work unless people decide to make it work. • Getting people involved in the process - because people are the ones who make changes work - is key. “Organizations don’t change – people change. And then people change organizations. ”

What is a Zero Incident Culture? It is not: • Having absolute security • Regulatory compliance

What is a Zero Incident Culture? • It is the presence of security, not the absence of threats/vulnerabilities. • Behavioral security awareness programs, like Zero Incident, optimize secure work practices and make line workers and supervisors jointly responsible for security. – Management’s role is to determine causes of incidents or potential incidents. – Supervisors focus on secure practices, even if it slows work. – And workers focus on getting the job done securely, making it a priority equal to getting the job done.

Why Strive For Zero? • Accepting a certain level of security incidents in your organization means accepting avoidable risk and loss – financial, public perception, legal, productivity and operational. • Anything less than Zero as an operating philosophy and goal is unacceptable.

What is a Zero Incident Culture? • A culture that views every incident as an operational error. • A culture in which security is integrated into all operations. .

What are the Benefits • Protection of our most important assets financial savings / ROI • Transcends security – improves quality, morale, productivity, profits & employee knowledge and ownership of success.

Danger Signs • Unclear who is responsible for what. • Belief that everything is ok, “we are in good shape” • Belief that rule compliance is enough for security (If we’re in compliance – we’re ok) • No tolerance for whistle-blowers – “culture of silence” • Problems experienced from other locations not applied as “lessons learned” • Lessons that are learned are not built into the system • Defects / errors became acceptable • Security is subordinate to production • Emergency procedures for severe events is lacking

Danger Signs • Policies and Procedures are confusing, complex and “hard to find” • Security resources and techniques are available but not used. • Organizational barriers prevent effective communication. • There are undefined responsibility, authority, and accountability for security. – Security belonged to “IT” • The acceptance of defects / errors becomes Institutionalized. – Because nothing has happened (or we are unaware of what has happened), we’re ok. • Culture is resilient, hard to change, and will revert to old habits if not steered by leadership.

Company Culture Production Culture - vs. - Security Culture Due to high costs of incidents there is no way a pure production culture can be profitable to it’s fullest potential.

What is a Production Culture? • • Belief that only production matters. Whatever it takes to get the job done. Security performance is not measured. Security performance is not part of supervisor’s job.

Security Culture • Security is not a priority - it is a corporate Value. • All levels of management accountable. • Security performance measured & tied to compensation. • Security integrated into all operations.

3 Major Steps to a Zero Incident Culture To get there you must take AIM • Assess your current culture • Implement the 12 upstream elements • Maintain the culture change

Assessing Security Culture Diagnosing Organizational Health

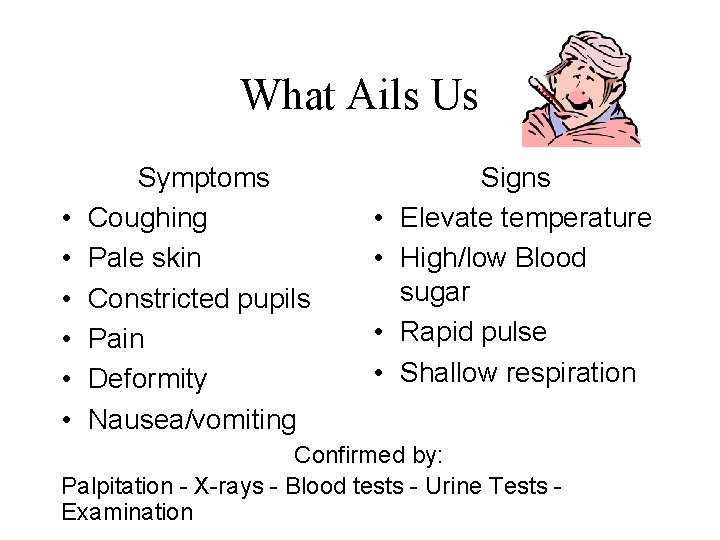
What Ails Us • • • Symptoms Coughing Pale skin Constricted pupils Pain Deformity Nausea/vomiting • • Signs Elevate temperature High/low Blood sugar Rapid pulse Shallow respiration Confirmed by: Palpitation - X-rays - Blood tests - Urine Tests Examination

What Ails An Organization • • Symptoms Uncorrected vulnerabilities Low employee involvement/accountability Fear Lack of feedback Poor security practices Zero-reporting Leaders not walking the talk • • • Signs High incident rates High frequency rates Low incident reporting Low security audit scores Increased cost per employee work-hour Confirmed by: Culture Surveys – Focus Group Interviews – Management Interviews

Why Measure Perceptions? • Perceptions are reality. • Regardless of management’s intent regarding security – reality is what employees perceive about security. Security Opinion Survey • Survey measures the drivers of a security culture against a potential perfect score of 100%. • The gap (how far from 100%) in each driver will

Key Drivers of Security • Risk/Hazard Correction • Security Communications • Behavioral Reinforcement • Security Values • Management Credibility • Accountability

Security Opinion Survey • Survey also measures the difference in what employees and management perceive about the security culture. • Typical results are that management perceives security as more positive than do employees. • The larger the gap the greater the

Risk/Vulnerability Correction • Measures employee beliefs about the importance a company places on identifying and correcting risks/vulnerability. • A belief that effort and resources are expended to correct risks/vulnerability supports a positive perception regarding the company’s commitment to security.

Accountability • Measures whether respondents believe that supervisors are truly accountable for security performance.

Communications • Security communications, or the lack of them, shape perceptions regarding the company’s security commitment. • Measures employees perceived freedom to discuss security issues. • Determines employee fears regarding communicating security issues.

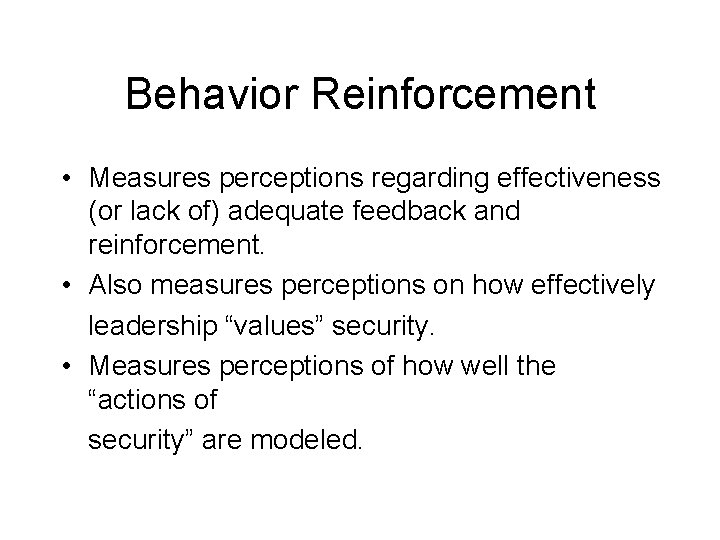
Behavior Reinforcement • Measures perceptions regarding effectiveness (or lack of) adequate feedback and reinforcement. • Also measures perceptions on how effectively leadership “values” security. • Measures perceptions of how well the “actions of security” are modeled.

Security Values • Measures perceptions regarding the company’s commitment to security as a value. • Also measures how the individual values security, as well as, their coworkers, leaders, and company as a whole. • The higher security is valued, the better the security performance.

Management Credibility • Measures how employees perceive management’s support for security – and how believable leaders are. • Sometimes “words” used by leaders are on target but their “actions” undermine their credibility.

Culture Assessment Report Provides gap analysis of security in the “real world” as opposed to the “ideal” security process. Defines the security culture – “what it’s really like” in the minds of employees. Measures disparity gap between management

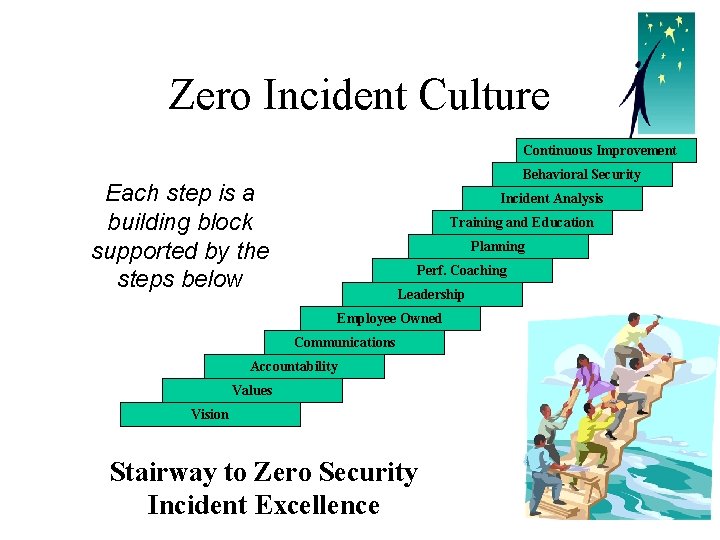
Zero Incident Culture Continuous Improvement Behavioral Security Each step is a building block supported by the steps below Incident Analysis Training and Education Planning Perf. Coaching Leadership Employee Owned Communications Accountability Values Vision Stairway to Zero Security Incident Excellence

VISION Vision answers the question “where are we going? ”

The Importance of Vision • Vision refers to a picture of the future and discusses why people should strive to create that future. • Clarifies any confusion – “Is this in line with the vision”.

VISION • One of the most famous vision speeches was made by John F. Kennedy regarding space travel. He committed that the United States would send a man to the moon within 10 years and bring him back alive. • It was certainly a stretch – great minds of the time said it was impossible.

VALUES • Values are the ideals or principles of society (organization) • Values define the ground rules (behaviors) for personal interactions in a company. • Clearly defined organizational values are the springboard for all other security efforts VALUES vs. PRIORITIES Priorities can be shifted – values cannot

Organizational Values • All companies have values, whether or not they have identified them. • Many managers may believe security is a value in the company, when in fact, it is not.

Individual Values • Individual values can influence group values. • This influence can be positive or negative.

Espoused Values • Are not the actual values in a company. • These are “what a company would like for it’s values to be. ” • If security is violated frequently, it is simply an espoused value.

Security as a Core Value The vast majority of people will adopt the organizations values if they perceive this is what upper management truly wants. • Employees who will not align themselves with the values of the organization do not fit – (regardless of position)

Accountability “The Engine That Drives Security”

Accountability • Accountability can take us from the reactive mode of constantly putting out fires, to a proactive mode of making sure the security process is in fact working at the operational level Accountability Defined • Someone is accountable when their performance is measured • When someone is responsible, their performance is not necessarily measured • The objective is to motivate performance

Accountability Defined • Obligation to perform duties to an accepted standard…………or else. • Has measurement system, evaluation, and consequences.

Accountability • Supervisors are usually measured on schedule, production, and cost. • They are often not measured on security performance, or not measured effectively and fairly.

Accountability • “What gets measured, gets done” • We tend to “get done” what is measured by our supervisor

Management Accountability • All levels of management and supervision must be held accountable • Security performance must be measured objectively • Must be controllable – Must be fair

Who Should Not Be Accountable? • Those without ultimate control…… The security Professional!! One of the most common structural mistakes

Measuring Performance • Upper management should be measured on results and activities. • Front line supervisors should be measured mostly on activities.

Measuring Performance • Remember – The absence of threats is not the same thing as the “presence of security” • Focus on defining what the Presence of Security would look like—then develop a system to measure it

Results • Results measurements may include: – Incident Rates – Incident Costs – Cost per man hour – Audit scores – Observation Frequency

Activities • Activities may include: – Self Inspections – Awareness – Security and Training and Education – Desktop Meetings – Security Planning – Task Analysis – Behavioral Reinforcement

Accountability Systems • Performance Appraisals – Should be at least annual, more is better, the more communication regarding performance, the more effective – Security should have equal weight to other performance measures

The Difference Between Incentives & Accountability Incentive Programs • Employee focused • Reward for “no incident” (trinkets) • Short-term (contest) • No real consequences • May not motivate • • • Accountability Process Mgr/Spvsr focused Rewards performance Long-term / Ongoing Impacts compensation Impacts career path

Security Communications • Communicating Vision & Values • Eliminating Fear from the Workforce • Communicating Instructions / Procedures

Communicating Vision & Values • You cannot over-communicate vision & values • Takes up to 50, 000 communications to anchor in culture • Must use a variety of methods / forums

Balancing Security with Production Messages • Management often sends mixed messages • Think about how many production or schedule messages employees receive daily in relation to security messages

“Fear is at the root of all the time people spend in meetings not saying what’s really on their mind” Vice President of Fortune 500 Company

Fear in the Workforce • If people are afraid to bring up security issues a serious flaw exists in the security process • It is not possible for a company to move to security excellence unless this problem is corrected

Communication • Build trust & drive out fear of bringing up security issues • Open up lines of communication with employees

Communication • Provide feedback & reinforcement • Provide regular forums (committees) with high employee involvement • Actively solicit & reward employee input about security vulnerabilities, issues, & improvements

Communication • Get personally involved in providing security awareness, training and education • Actions speak louder than words – set the example

Communicating Instructions / Procedures • Never assume that because we told someone what or how to do something, they understood • Explain, then have them to repeat • Follow-up and re-direct as necessary • Communication Includes Listening – Listen with the intent to understand

Employee Ownership • No one knows more about security needs than the people doing the work. • Lack of involvement (buy-in) is epidemic in traditional security programs • Caused by top-down management • Employees will get involved if you “make it safe for them to do so”

Employee Ownership • Start with involvement—work toward ownership • Get employees involved in: – Setting security policy, procedures – Inspections / audits – Behavioral observations & feedback – Conducting security training – Functional security committees

Leadership Developing Leadership for Security

“Walking the Talk” • If the “audio don’t match the video” you lose credibility • One of the most common complaints by employees • Management actions / decisions must be aligned with what we say about security

Performance Coaching Effective leaders help their teams practice perfection Don Shula

Why Employees Don’t Do What They are Supposed to Do • Don’t know: – Why/how • They think: – Your way won’t work – Their way is better – Something else more important – They’re already doing it • Rewarded for not doing • Punished for doing • No consequence for not doing • Obstacles beyond their control

Problems in the workplace are often created not by what we do, but by what we fail to do. Aubrey Daniels

New Focus “Catch me doing something right” • Traditional security only addresses the negatives • If people are not told they are appreciated – they will assume the opposite

EMPLOYEE MOTIVATION • SOON - CERTAIN – POSITIVE • “WHAT GETS REWARDED---GETS REPEATED”

What Gets Rewarded Gets Repeated • The job of the effective leader is to create positive consequences for positive performance • Decrease undesirable behaviors by arranging consequences that will stop them • Increase desirable behaviors by arranging consequences that will positively reinforce them

5 Steps for Effective Coaching 1. Observe the behavior 2. Reinforce all positive behaviors 3. Provide performance feedback (noninvasive) 4. Re-direct (if necessary) 5. Follow-up & reinforce new behaviors

Security Planning • Planning is a major differentiator between a security process that is proactive rather than reactive • When to plan for security – – – New operations / processes New equipment Shut-downs Acquisitions / mergers Downsizing

Security Planning • Plan for emergencies – develop a disaster recovery management plan and PRACTICE. • In a post 911 world, there is no excuse for failure to plan for emergencies.

Task Security Analysis • The single most effective technique for preventing incidents. • Organized system for breaking jobs into sequential steps. • Results in a secure work procedure (much more efficient than relying on “security policy, procedures and rules”).

Task Security Analysis • Perform for all high-risk activities • Use brainstorming process • Get employees involved in the process

Effective Security Awareness Training and Education The only thing worse than training people and losing them is not training them and keeping them.

Security Awareness, Training and Education • Who will conduct training • When, how often, who will keep documentation? • Account for: – Language barriers – Translation / Spanish trainers

Security Awareness, Training and Education • Supervisory and Management Training – Security Management – Leadership Training – Performance Coaching

New Hire Orientations • • Most Important Security Training Highest Rate of Incidents Compliance Required Training Buddy System

New Hire Orientations • Job Specific Security Awareness and Training • Job Rules • Incident Reporting • Retrain After First Day? • Language and Reading Issues

Supervisor Orientations • New Supervisors – Security Program – Duties/Responsibilities/Accountability – Training Needs

Training Improvements • Integrating security into job / task training is more effective than pure “security training”. • People learn more by doing than by hearing • Make all job security training as “handson” as possible

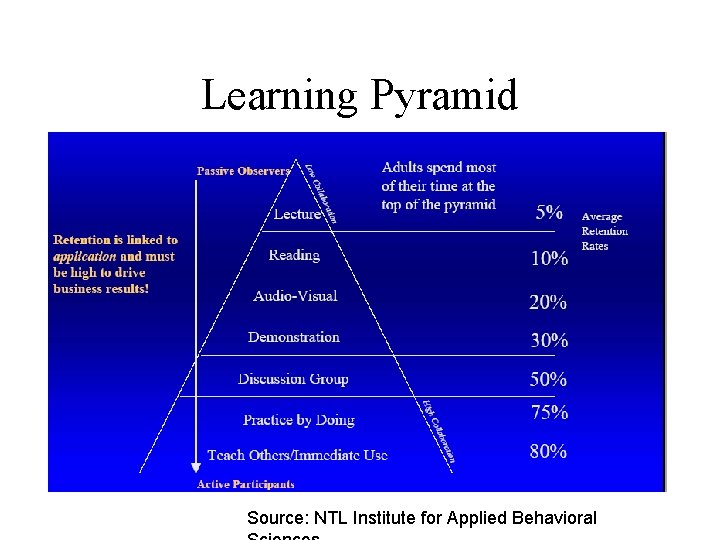
Learning Pyramid Source: NTL Institute for Applied Behavioral

Training Improvements • “See one, do one, teach one” • When we must teach others we are forced to learn it well • Getting employees involved in training other employees is invaluable

Five Step Training Process 1. Explain the task 2. Demonstrate how it is done 3. Allow employee(s) to do it under observation of the trainer 4. Re-direct as necessary 5. Follow-up

Incident Analysis • Only by getting to the root cause can we prevent a reoccurrence

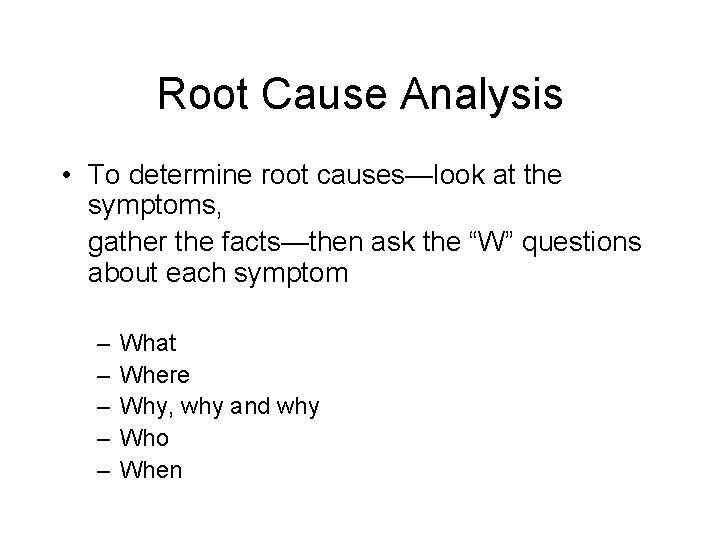
Effective Brainstorming • Use for problem-solving, root cause analysis, or for generating ideas • What is a Root Cause ? • The real or underlying causes of: – Incidents – Insecure behavior – Insecure conditions

Why Investigate for Root Causes ? • Most “causes” listed on incident reports are not causes at all – they are symptoms • Finding root causes allows us to prevent a reoccurrence

Why Analyze for Root Cause ? • Standard incident investigations do not go far enough • Insurance investigations seek to place: – Liability – Compensability – Blame / Fault

Key Security Management Principle • Insecure acts & conditions are symptoms of something wrong in the management system • Root causes will lead to the following general areas: – – Knowledge Skill Motivation Work Process

Symptoms -vs. - Causes • Insecure acts or conditions are not the causes of incidents, they are symptoms of a defect in our system • Symptoms can be observed, but they are not the root causes • Causes are the underlying reasons that allow the symptoms to occur • Root causes cannot be seen—they can only be identified through a thorough investigation.

Root Cause Analysis • To determine root causes—look at the symptoms, gather the facts—then ask the “W” questions about each symptom – – – What Where Why, why and why Who When

Root Cause Analysis • Management creates the job, the environment, the rules, the culture, and the “way things are done. ” • If symptoms are occurring, management must change the system, rather than blaming the employee(s).

Root Cause Analysis • Symptoms - The insecure acts and conditions which we can see that often result in incidents but are not necessarily the root cause.

Root Cause Analysis • Causes - The underlying reasons for incidents which we can’t see can only be identified by a thorough investigation. • Some common examples of causes are: – – – Inadequate training Lack of accountability Inadequate policies and procedures Improper environmental and equipment set up Conflicts in Values

Root Cause Analysis • Failure to address root causes will result in reoccurrence of: – Symptoms – Incidents

Behavioral Security How Behavior Effects Security

“The insecure acts of persons are responsible for a majority of incidents” Donn Parker Father of Security

Not A Magic Bullet Addressing behavior alone is not the magic bullet. • Insecure behavior however, is often a component of the chain of events leading to an incident. • Insecure behavior is a predictor of future incidents. • Looking for shortcuts is NORMAL human behavior. • Allowing insecure behavior to become the norm, reinforces that it is o. k. and that nothing bad

Behavioral Security – What is it? • Belief that human behavior accounts for the majority of incidents • Refocuses security efforts from conditions (regulatory), to behavior • Based on observation & feedback of performance

• • Insecure conditions may include: Poor housekeeping (drink by keyboard, unsecured recycled trash receptors) Insufficient equipment (share PC) PC that is not current in O/S Patches Improper data storage No data classification Facility faults (Doors don’t close correctly, A/C not working - door is left open, etc. Require SS# or other unnecessary personable identifier

Insecure Acts An insecure act might be: – Weak password construction and management – Failure to log off at end of day – Delayed pickup of faxed confidential information at fax machine – Victim to social engineering attempt – Allowing a stranger to walk through building unchallenged. – Door to secure area propped open.

Observation Process • Request to observe employee working: 1. Summarize the secure behaviors that you observed. 2. Describe areas of concern. 3. Ask the employee for suggestions for a more secure way to do the task. 4. Thank the employee for allowing the observation.

Resistance to Change • With change comes resistance. • Culture change will revert to old ways without constant measurement and reinforcement.

Success Factors for Managing Change • Address employee and management resistance factors • Engage employees in action planning process • Establish reasonable objectives and schedule for implementation • Focus on the journey not the destination

Success Factors for Managing Change • • Have an organized system (ZIPP) Pilot first, then implement Recognize early signs of shifting Measure Evaluate Redirect or continue plan Re-evaluate……………

Why Measure Perceptions? • “Perceptions are reality” • Regardless of management’s intent regarding security – reality is what employees perceive about security.

Security Opinion Survey • Survey measures the drivers of a security culture against a potential perfect score of 100%. • The gap (how far from 100%) in each driver will help focus security efforts on lower scoring drivers.

Key Drivers • Vulnerability Correction • Security Communications • Behavioral Reinforcement • Security Values • Management Credibility • Accountability

Security Opinion Survey • Survey also measures the difference in what employees and management perceive about the security culture. • Typical results are that management perceives security as more positive than do employees. • The larger the gap the greater the problem.


Survey Parameters • • Fifteen to twenty questions Likert scale of 1 -5 (negative to positive) Using weighted-average, or mean Standard deviation – how widely scattered are the answers

Vulnerability Correction • Measures the importance a company places on identifying and correcting vulnerabilities. • Are appropriate resources expended to eliminate vulnerabilities?

Security Communications • Do employees feel security is adequately communicated? • Is there freedom to discuss security issues? • Do employees fear that communicating negative security perceptions might lead to reprimands or terminations?

Behavior Reinforcement • Is behavior observed and appropriate feedback provided? • Are positive acts rewarded? • Are negative acts reprimanded?

Security Values • Do employees perceive security is a true value in the organization or an espoused value? • Are production messages overwhelming security value messages and degrading management’s intent?

Management Credibility • Does the audio match the video? • Leaders must “walk the talk” of a security culture to have credibility.

Focus Group Interviews • Helps validate survey results and provides grassroots suggestions for improvement • Employees have less fear communicating when part of a group. • May be the first step in employee involvement and buy-in.

Management Interviews • Identifies the views of management. • Identifies problems in the flow of communication between the corporate level and the field/floor level. • Pinpoints perceived implementation problems.

Confidentiality • Confidentiality cannot be overstressed if you want the truth. • Consider use of a third party for collections. • Perceived lack of confidentiality with online surveys.

Survey Collection Protocols • Keep survey short or will be pencil whipped. • Separate supervisors and employees. • Consider cultural and literacy issues

Baseline Measurement • Initial survey provides a baseline. • Should measure again no sooner than 18 months to determine degree of improvement. • Culture change takes time to anchor.

Sensitive Information • Be careful how sensitive information is used if used in a punitive manner, you will never regain trust. • Once you open the door to communication you may be surprised at what is going on.

Culture Assessment Report • Identifies the strengths & weaknesses in the security culture. • Provides starting points for effective intervention. • Makes specific recommendations for improving the security culture.

What To Do With Information • A survey without intent to change will send the wrong message and may do harm. • Communicate the results of the survey to employees. • Involve employees in improvement plan. All content is copyrighted material and may not be duplicated, distributed, transferred, transmitted, copied, altered, sold, used to create derivative works, or otherwise misused.