Creating a European Identity Management Architecture for e






- Slides: 17

Creating a European Identity Management Architecture for e. Government www. guide-project. org GUIDE Keiron Salt keiron. salt@bt. com

What is GUIDE ? GUIDE (Government User Identity for Europe) is an European Union funded research project conducting research and technological development with the aim of creating a technologica institutional, policy and socio-economic architecture for secure and interoperable e-government electronic identity services and transactions for Europe.

Road of GUIDE and EU 2004: Lisbon Agenda 2006: Manchester ‘ 2010 Declaration’ Encourage Free Movement of Citizens, Capital and Services across the EU to encourage the Internal Market Pan-European Identity Interoperability

GUIDE Architecture Summary Objective Creating an open architecture for Pan-European e-government electronic identity interoperability To enable Member States to agree on the identity of an entity (for example a citizen or a business) In order to enable e. Government sectoral applications to conduct crossborder transactions with respect to that entity The GUIDE architecture aligns with, leverages, and exploits both of • The IDABC European Interoperability Framework(EIF) architecture • Emerging International Standards for Federated Identity Management

The Motivation ‘View’ - What are the Business Problems we’re trying to solve? - Getting the Scope right. • Guide delivers identity interoperability across the Member States of the EU. • Guide is not an end in itself, but a key enabler for Application interoperability to enable the Lisbon Initiatives which deliver the real benefits. • Guide aims to enable uninhibited movement and seamless government engagement for citizens & businesses across the EU. Is About • • • Identity data interoperability Authentication Cross border services Standards adoption Standards specification Is Not About • • • Storing Identity data will in GUIDE Application data interoperability Authorisation Internal MS services Re-inventing Implementation

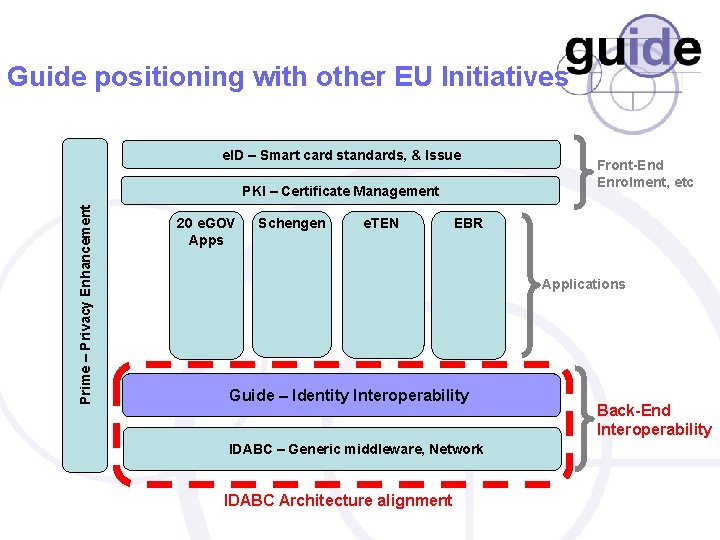
Guide positioning with other EU Initiatives e. ID – Smart card standards, & Issue Prime – Privacy Enhancement PKI – Certificate Management 20 e. GOV Apps Schengen e. TEN Front-End Enrolment, etc EBR Applications Guide – Identity Interoperability IDABC – Generic middleware, Network IDABC Architecture alignment Back-End Interoperability

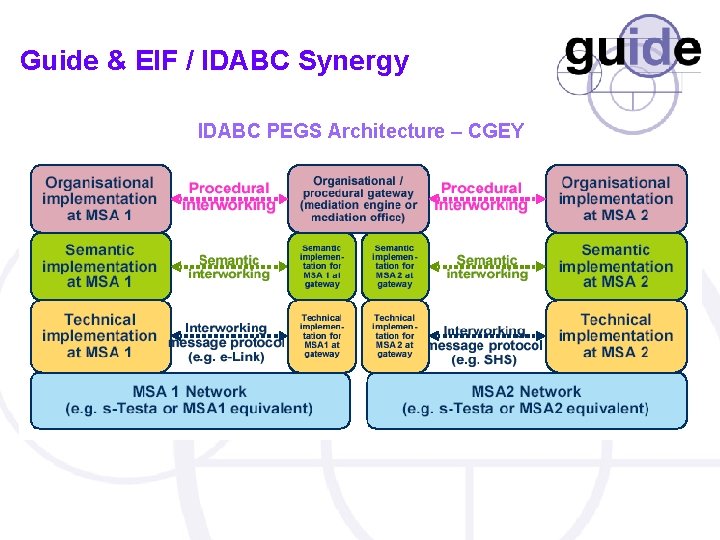
Guide & EIF / IDABC Synergy IDABC PEGS Architecture – CGEY

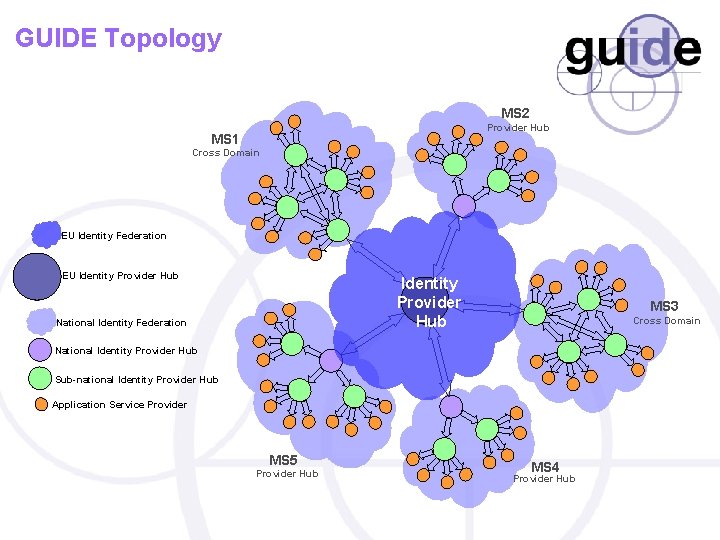
GUIDE Topology MS 2 Provider Hub MS 1 Cross Domain EU Identity Federation EU Identity Provider Hub National Identity Federation MS 3 Cross Domain National Identity Provider Hub Sub-national Identity Provider Hub Application Service Provider MS 5 Provider Hub MS 4 Provider Hub

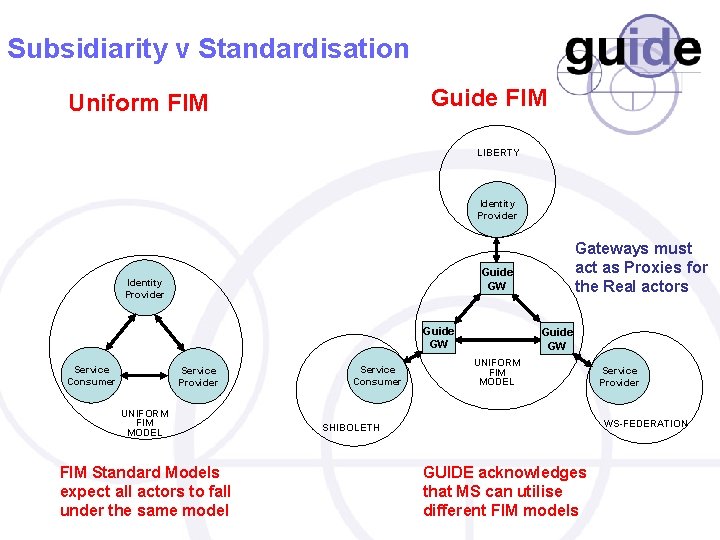
Subsidiarity v Standardisation Guide FIM Uniform FIM LIBERTY Identity Provider Guide GW Service Consumer Gateways must act as Proxies for the Real actors Service Provider UNIFORM FIM MODEL FIM Standard Models expect all actors to fall under the same model Service Consumer Guide GW UNIFORM FIM MODEL Service Provider WS-FEDERATION SHIBOLETH GUIDE acknowledges that MS can utilise different FIM models

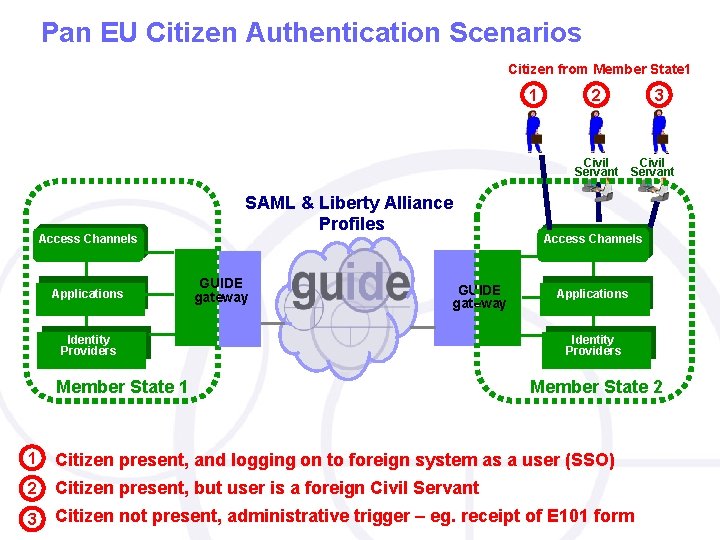
Pan EU Citizen Authentication Scenarios Citizen from Member State 1 1 Civil Servant Access Channels Applications SAML & Liberty Alliance Profiles GUIDE gateway Identity Providers Member State 1 3 2 Civil Servant Access Channels Applications Identity Providers Member State 2 1 Citizen present, and logging on to foreign system as a user (SSO) 2 Citizen present, but user is a foreign Civil Servant 3 Citizen not present, administrative trigger – eg. receipt of E 101 form

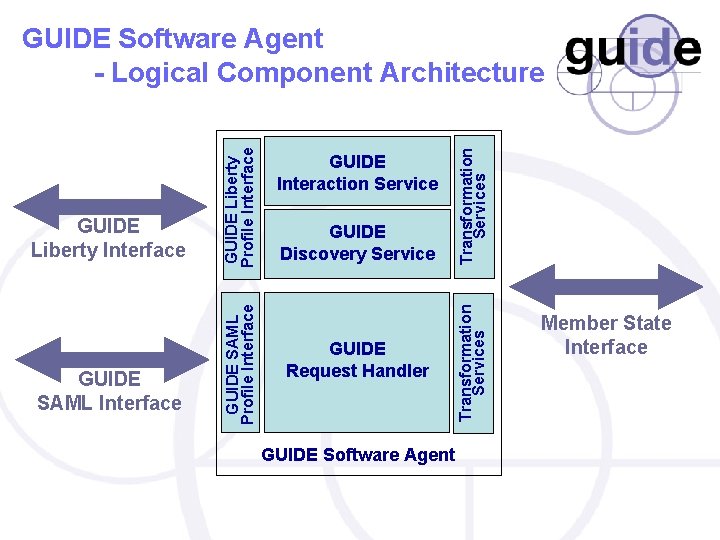
GUIDE Discovery Service GUIDE Request Handler GUIDE Software Agent Transformation Services GUIDE Interaction Service Transformation Services GUIDE SAML Interface GUIDE SAML Profile Interface GUIDE Liberty Profile Interface GUIDE Software Agent - Logical Component Architecture Member State Interface

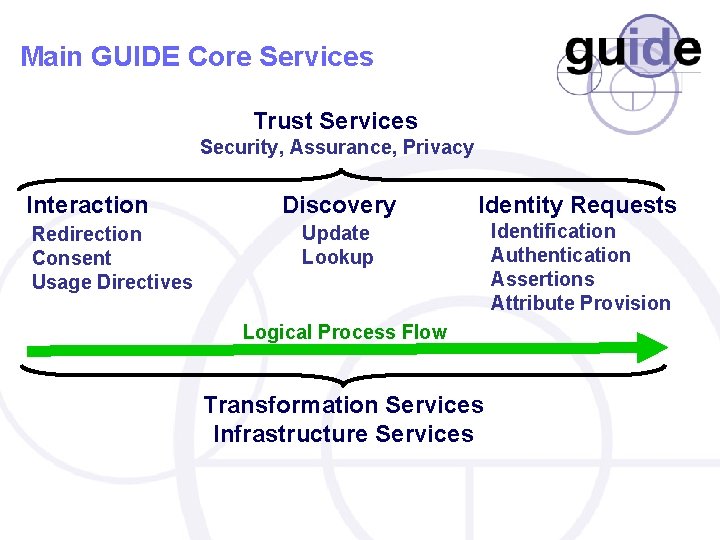
Main GUIDE Core Services Trust Services Security, Assurance, Privacy Interaction Redirection Consent Usage Directives Discovery Identity Requests Update Lookup Identification Authentication Assertions Attribute Provision Logical Process Flow Transformation Services Infrastructure Services

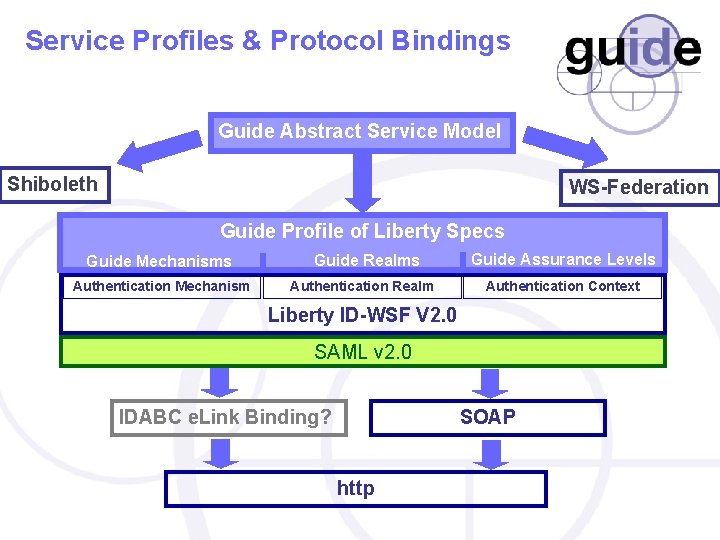
Service Profiles & Protocol Bindings Guide Abstract Service Model Shiboleth WS-Federation Guide Profile of Liberty Specs Guide Mechanisms Authentication Mechanism Guide Realms Authentication Realm Guide Assurance Levels Authentication Context Liberty ID-WSF V 2. 0 SAML v 2. 0 IDABC e. Link Binding? SOAP http

Guide Liberty Profile for Discovery Naming standards <soap: Body> <Query xmlns = “urn: liberty: disco: 2003 -08”> <Resource. ID>http: //example. gov/g 048 Hqe. R 4 ts. B</Resource. ID> <Requested. Service. Type> <Service. Type>urn: liberty: id-sis-pp: 2003 -08</Service. Type> <Options> Profiling <Option>urn: liberty: id-sis-pp: home</Option> <Option>urn: liberty: id-sis-pp: informal. Name</Option> <Option>urn: GUIDE: Realm: Social. Security</Option> <Option>urn: GUIDE: Assurance: 2</Option> </Options> <Security. Mech. ID> not used </Security. Mech. ID> </Requested. Service. Type> </Query> </soap: Body>

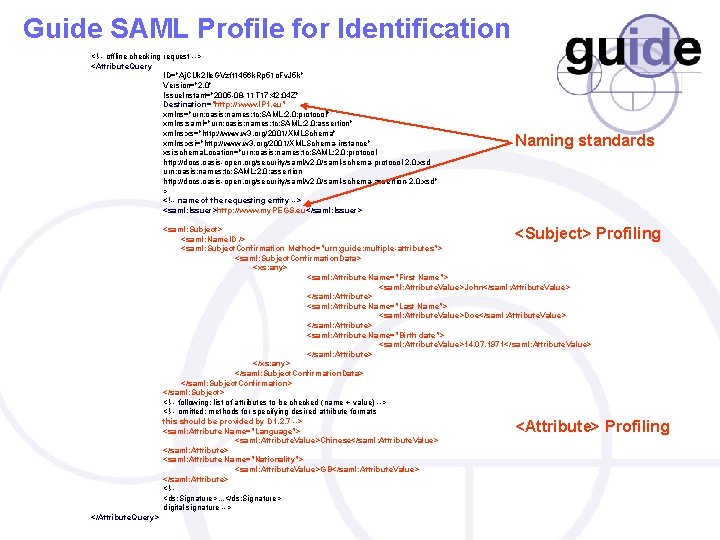
Guide SAML Profile for Identification <!-- offline checking request --> <Attribute. Query ID="Aj. CUk 2 lle. GVzft 1456 k. Rp 51 o. Fv. J 5 k" Version="2. 0" Issue. Instant="2005 -08 -11 T 17: 42: 04 Z" Destination="http: //www. IP 1. eu" xmlns="urn: oasis: names: tc: SAML: 2. 0: protocol" xmlns: saml="urn: oasis: names: tc: SAML: 2. 0: assertion" xmlns: xs="http: //www. w 3. org/2001/XMLSchema" xmlns: xsi="http: //www. w 3. org/2001/XMLSchema-instance" xsi: schema. Location="urn: oasis: names: tc: SAML: 2. 0: protocol http: //docs. oasis-open. org/security/saml/v 2. 0/saml-schema-protocol-2. 0. xsd urn: oasis: names: tc: SAML: 2. 0: assertion http: //docs. oasis-open. org/security/saml/v 2. 0/saml-schema-assertion-2. 0. xsd" > <!-- name of the requesting entity --> <saml: Issuer>http: //www. my. PEGS. eu</saml: Issuer> Naming standards <Subject> Profiling <saml: Subject> <saml: Name. ID /> <saml: Subject. Confirmation Method="urn: guide: multiple-attributes"> <saml: Subject. Confirmation. Data> <xs: any> <saml: Attribute Name="First Name"> <saml: Attribute. Value>John</saml: Attribute. Value> </saml: Attribute> <saml: Attribute Name="Last Name"> <saml: Attribute. Value>Doe</saml: Attribute. Value> </saml: Attribute> <saml: Attribute Name="Birth date"> <saml: Attribute. Value>14. 07. 1971</saml: Attribute. Value> </saml: Attribute> </xs: any> </saml: Subject. Confirmation. Data> </saml: Subject. Confirmation> </saml: Subject> <!-- following: list of attributes to be checked (name + value) --> <!-- omitted: methods for specifying desired attribute formats this should be provided by D 1. 2. 7 --> <saml: Attribute Name="Language"> <saml: Attribute. Value>Chinese</saml: Attribute. Value> </saml: Attribute> <saml: Attribute Name="Nationality"> <saml: Attribute. Value>GB</saml: Attribute. Value> </saml: Attribute> <!-<ds: Signature>. . . </ds: Signature> digital signature --> <Attribute> Profiling </Attribute. Query>

Guide & EIF / IDABC Synergy IDABC PEGS Architecture – CGEY

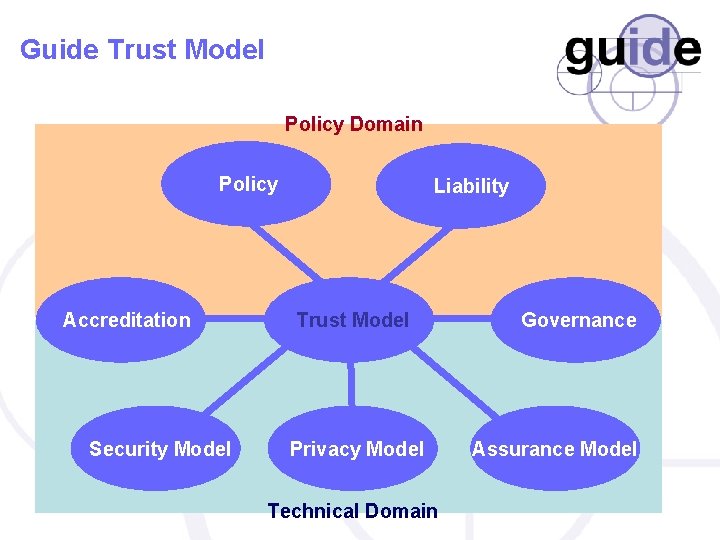
Guide Trust Model Policy Domain Policy Accreditation Security Model Liability Trust Model Privacy Model Technical Domain Governance Assurance Model