Cracking Wi Fi Faster Faster Pwnin G Assured






![Introduction to WPA PBKDF 2 unsigned char hash[32]; t = sha 1_hmac(MK, SSID, 1); Introduction to WPA PBKDF 2 unsigned char hash[32]; t = sha 1_hmac(MK, SSID, 1);](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-15.jpg)










![pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; for(i pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; for(i](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-50.jpg)
![pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; // pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; //](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-51.jpg)
![pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; // pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; //](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-56.jpg)









- Slides: 75

Cracking Wi. Fi… Faster! (Faster Pwnin. G Assured) RECON 2006 – June 16 th, 2006 David Hulton <dhulton@openciphers. org>

Cracking Wi. Fi… Faster! FPGAs Quick Intro (I swear!) co. WPAtty WPA Overview Precomputing tables Performance Airbase jc-aircrack jc-wepcrack pico-wepcrack Performance Conclusion

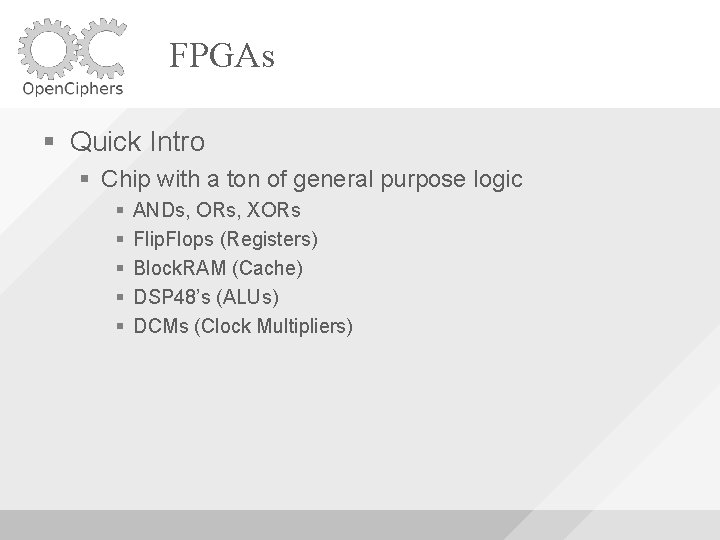
FPGAs Quick Intro Chip with a ton of general purpose logic ANDs, ORs, XORs Flip. Flops (Registers) Block. RAM (Cache) DSP 48’s (ALUs) DCMs (Clock Multipliers)

FPGAs Virtex-4 LX 25

FPGAs Virtex-4 LX 25 IOBs (448)

FPGAs Virtex-4 LX 25 IOBs Slices (10, 752)

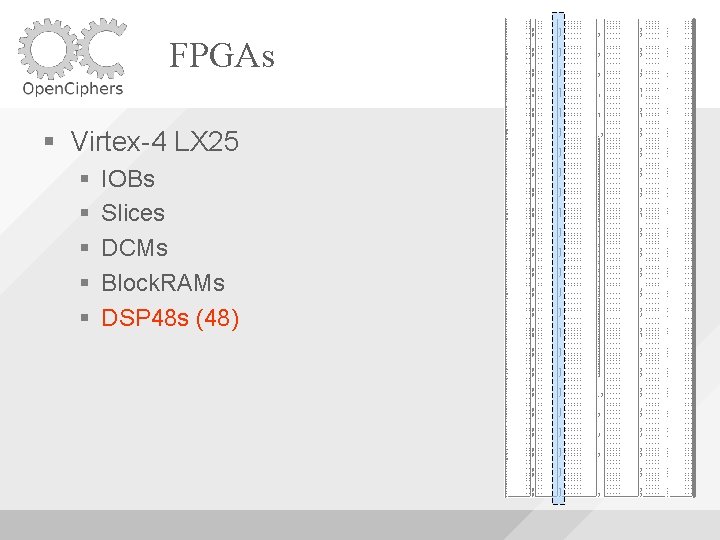
FPGAs Virtex-4 LX 25 IOBs Slices DCMs (8)

FPGAs Virtex-4 LX 25 IOBs Slices DCMs Block. RAMs (72)

FPGAs Virtex-4 LX 25 IOBs Slices DCMs Block. RAMs DSP 48 s (48)

FPGAs Virtex-4 LX 25 IOBs Slices DCMs Block. RAMs DSP 48 s Programmable Routing Matrix (~18 layers)

Introduction to WPA Wi. Fi Protected Access

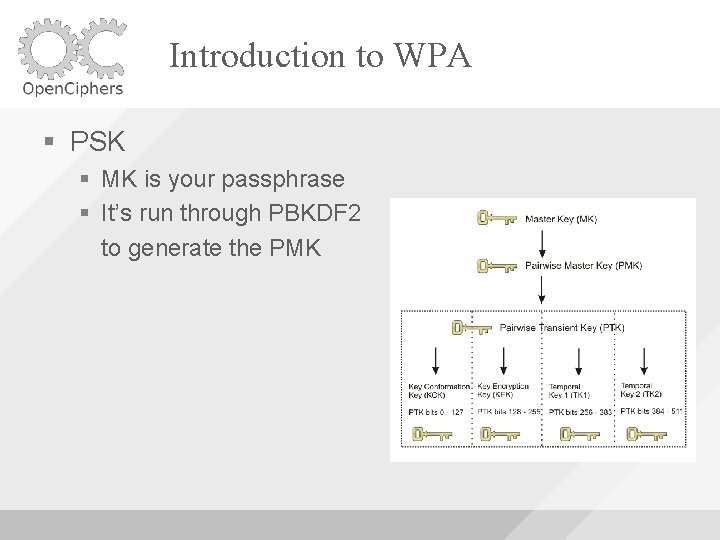
Introduction to WPA PSK MK is your passphrase It’s run through PBKDF 2 to generate the PMK

Introduction to WPA PSK MK is your passphrase It’s run through PBKDF 2 to generate the PMK

Introduction to WPA PSK MK is your passphrase It’s run through PBKDF 2 to generate the PMK
![Introduction to WPA PBKDF 2 unsigned char hash32 t sha 1hmacMK SSID 1 Introduction to WPA PBKDF 2 unsigned char hash[32]; t = sha 1_hmac(MK, SSID, 1);](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-15.jpg)
Introduction to WPA PBKDF 2 unsigned char hash[32]; t = sha 1_hmac(MK, SSID, 1); for(i = 1; i < 4096; i++) t = sha 1_hmac(MK, t); memcpy(hash, &t, 20); t = sha 1_hmac(MK, SSID, 1); for(i = 1; i < 4096; i++) t = sha 1_hmac(MK, t); memcpy(hash + 20, &t, 12);

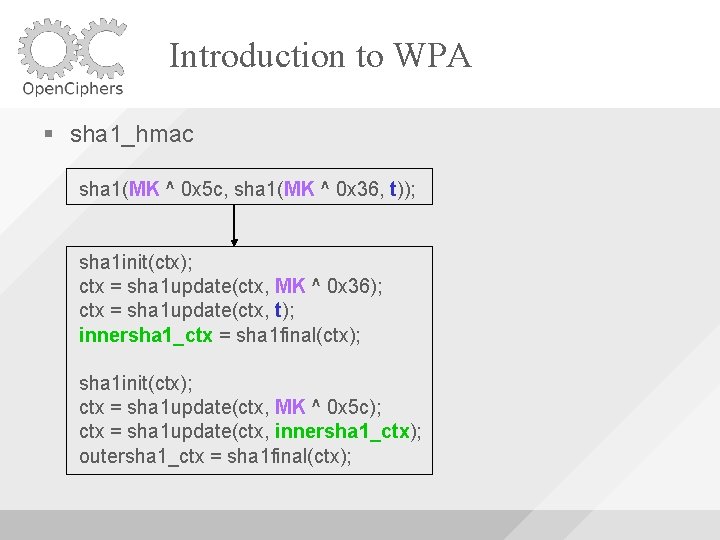
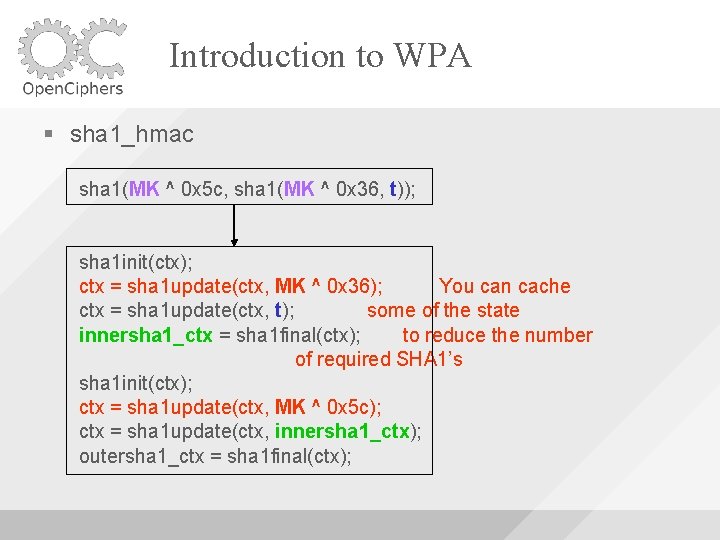
Introduction to WPA sha 1_hmac sha 1(MK ^ 0 x 5 c, sha 1(MK ^ 0 x 36, t)); sha 1 init(ctx); ctx = sha 1 update(ctx, MK ^ 0 x 36); ctx = sha 1 update(ctx, t); innersha 1_ctx = sha 1 final(ctx); sha 1 init(ctx); ctx = sha 1 update(ctx, MK ^ 0 x 5 c); ctx = sha 1 update(ctx, innersha 1_ctx); outersha 1_ctx = sha 1 final(ctx);

Introduction to WPA sha 1_hmac sha 1(MK ^ 0 x 5 c, sha 1(MK ^ 0 x 36, t)); sha 1 init(ctx); ctx = sha 1 update(ctx, MK ^ 0 x 36); You can cache ctx = sha 1 update(ctx, t); some of the state innersha 1_ctx = sha 1 final(ctx); to reduce the number of required SHA 1’s sha 1 init(ctx); ctx = sha 1 update(ctx, MK ^ 0 x 5 c); ctx = sha 1 update(ctx, innersha 1_ctx); outersha 1_ctx = sha 1 final(ctx);

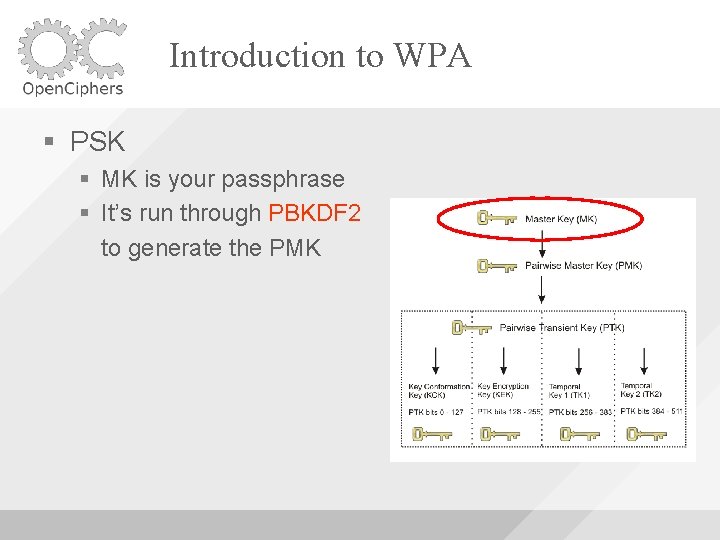
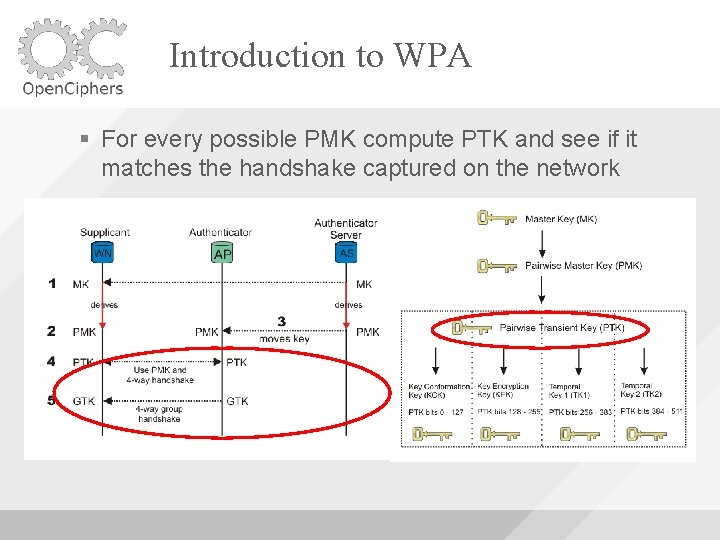
Introduction to WPA For every possible PMK compute PTK and see if it matches the handshake captured on the network

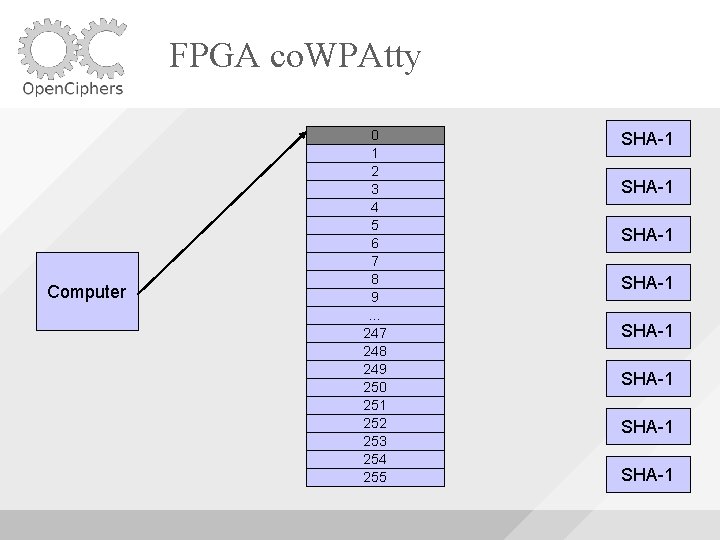
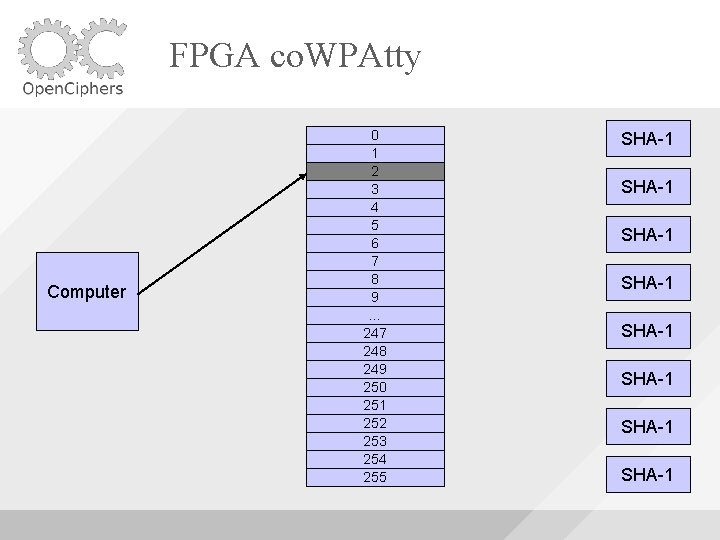
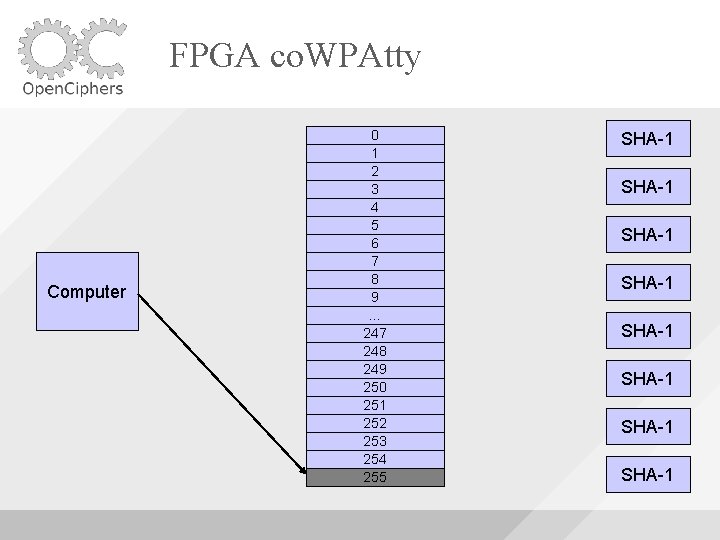
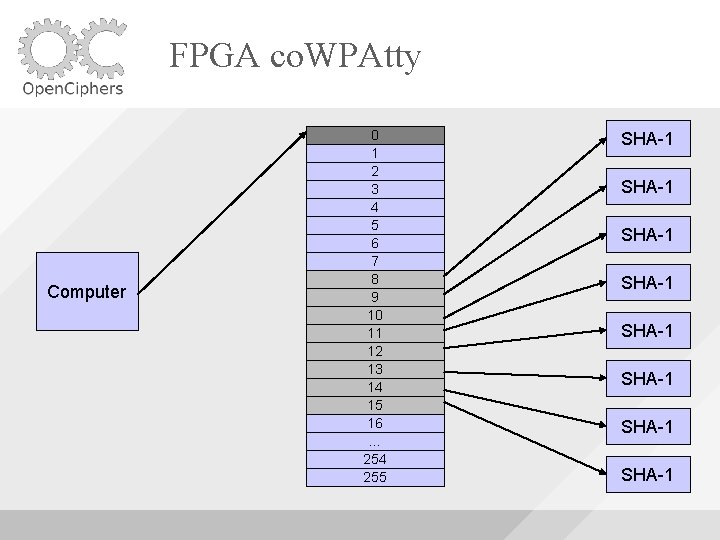
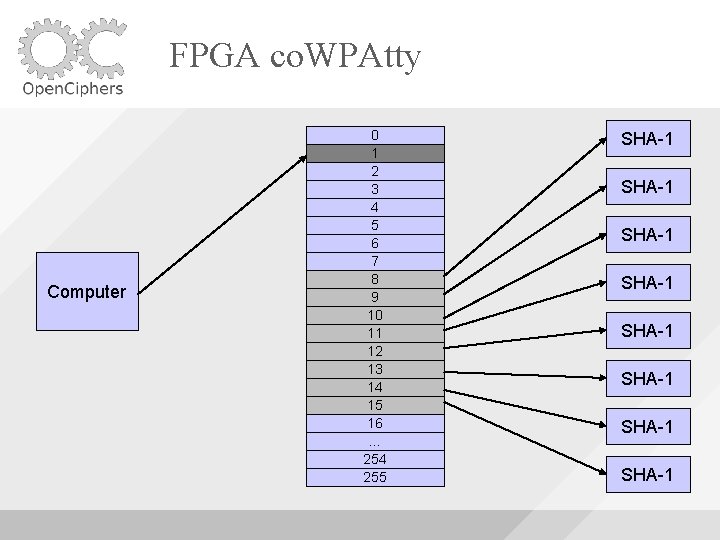
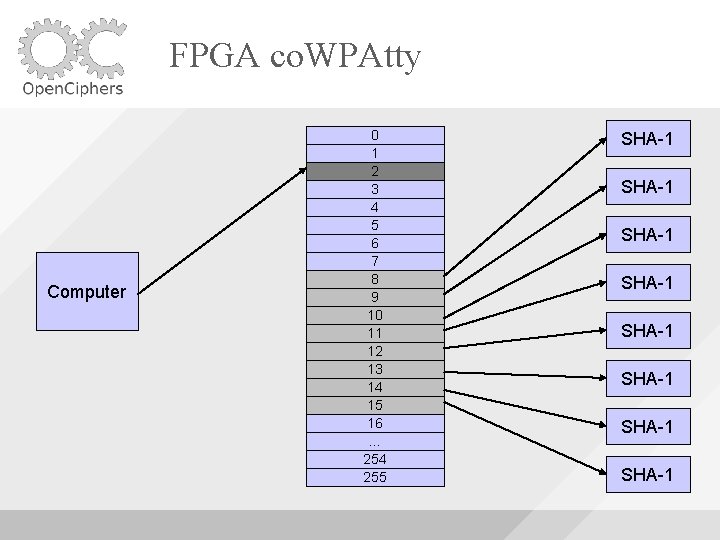
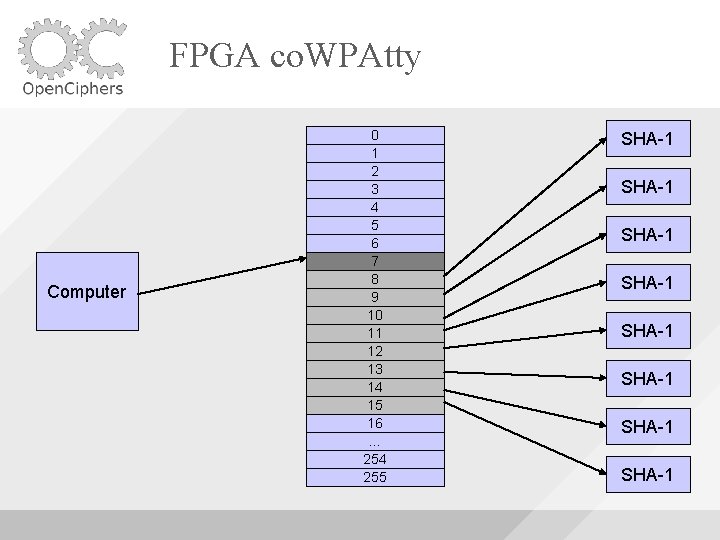
FPGA co. WPAtty Uses 8 SHA-1 Cores Uses Block. RAM to buffer the words fed to the cores As long as the machine is able to supply words fast enough, the SHA-1 cores will be utilized fully

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 … 247 248 249 250 251 252 253 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 … 247 248 249 250 251 252 253 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 … 247 248 249 250 251 252 253 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 … 247 248 249 250 251 252 253 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 … 247 248 249 250 251 252 253 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 … 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 … 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 … 254 255 SHA-1 SHA-1

FPGA co. WPAtty Computer 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 … 254 255 SHA-1 SHA-1

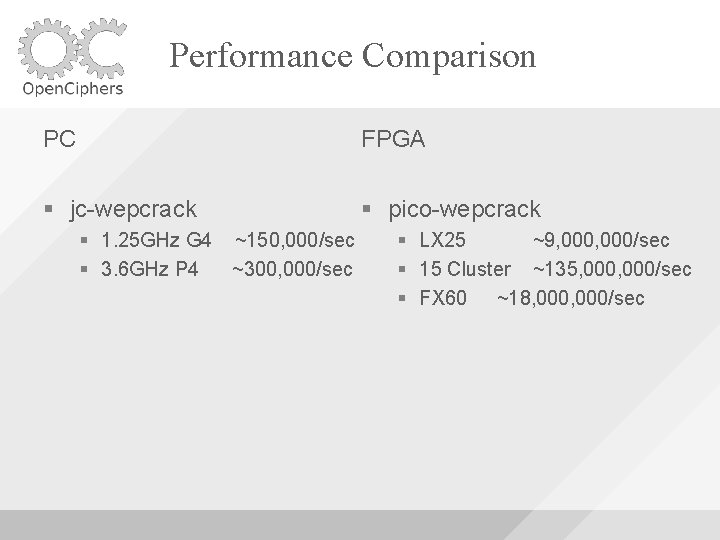
Performance Comparison PC FPGA Cowpatty 800 MHz P 3 ~25/sec 3. 6 GHz P 4 ~60/sec AMD Opteron ~70/sec 2. 16 GHz Intel. Duo ~70/sec Aircrack 3. 6 GHz P 4 ~100/sec LX 25 ~430/sec 15 Cluster ~6, 500/sec FX 60 ~1, 000/sec

Results Decided to compute hash tables for a 1, 000 passphrase wordlist for the top 1, 000 SSIDs “That million word list that I fed you incorporated a 430, 000 word list from Mark Burnett and Kevin Mitnick (of all people) and was made up of actual harvested passwords acquired through some google hacking. They are passwords that people have actually used. I padded it out to 1 million by adding things like websters dictionary, and other such lists, and then stripped the short word (<8 chars. ) out of it. ”

Results Took Render. Man 1 month to compute on his cluster Found out that his wordlist had return characters at the end of every line (after computing for a month) He sent me an email asking for help A 15 card cluster did it in 2 days ; -)

FPGA co. WPAtty + + = ?

Demo

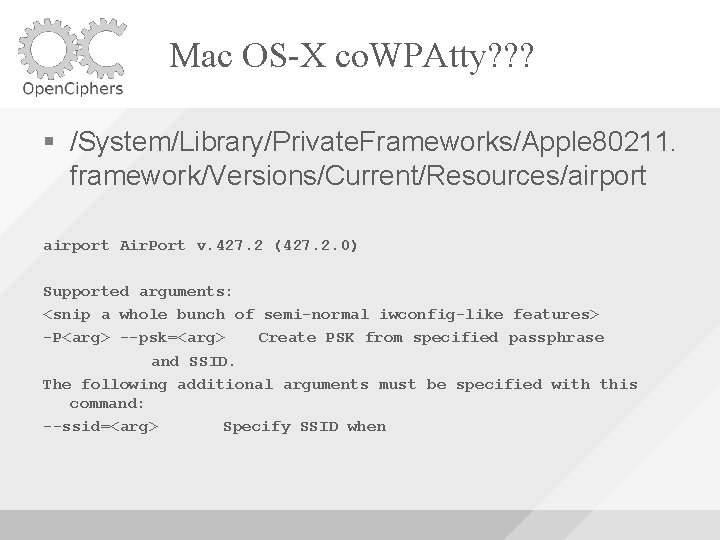
Mac OS-X co. WPAtty? ? ? /System/Library/Private. Frameworks/Apple 80211. framework/Versions/Current/Resources/airport Air. Port v. 427. 2 (427. 2. 0) Supported arguments: <snip a whole bunch of semi-normal iwconfig-like features> -P<arg> --psk=<arg> Create PSK from specified passphrase and SSID. The following additional arguments must be specified with this command: --ssid=<arg> Specify SSID when

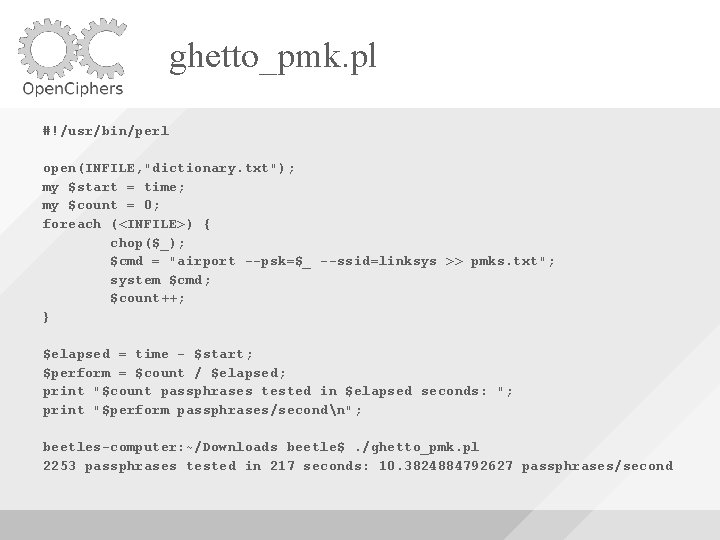
ghetto_pmk. pl #!/usr/bin/perl open(INFILE, "dictionary. txt"); my $start = time; my $count = 0; foreach (<INFILE>) { chop($_); $cmd = "airport --psk=$_ --ssid=linksys >> pmks. txt"; system $cmd; $count++; } $elapsed = time - $start; $perform = $count / $elapsed; print "$count passphrases tested in $elapsed seconds: "; print "$perform passphrases/secondn"; beetles-computer: ~/Downloads beetle$. /ghetto_pmk. pl 2253 passphrases tested in 217 seconds: 10. 3824884792627 passphrases/second

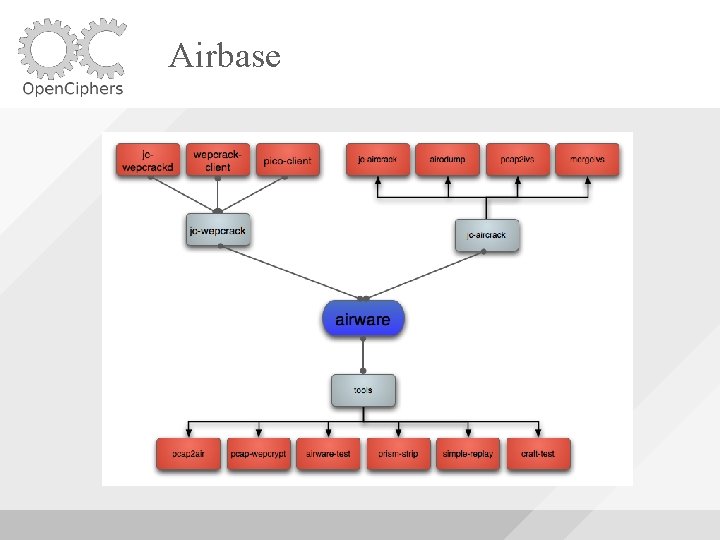
Airbase

Airbase

Airbase

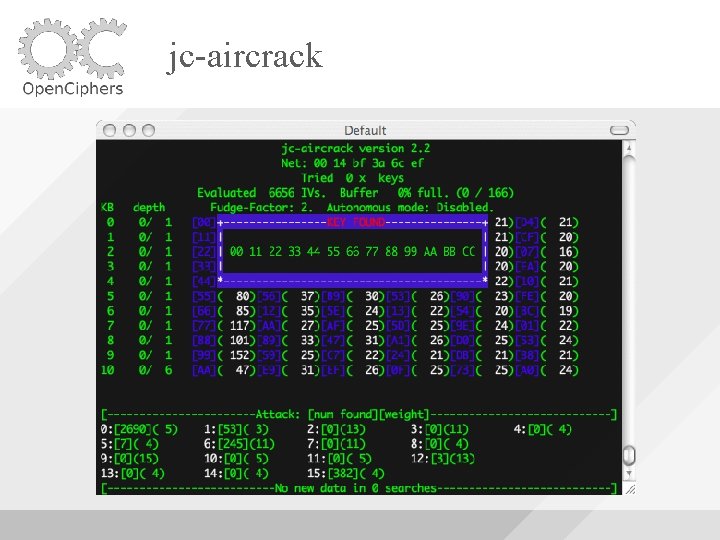
jc-aircrack

jc-aircrack

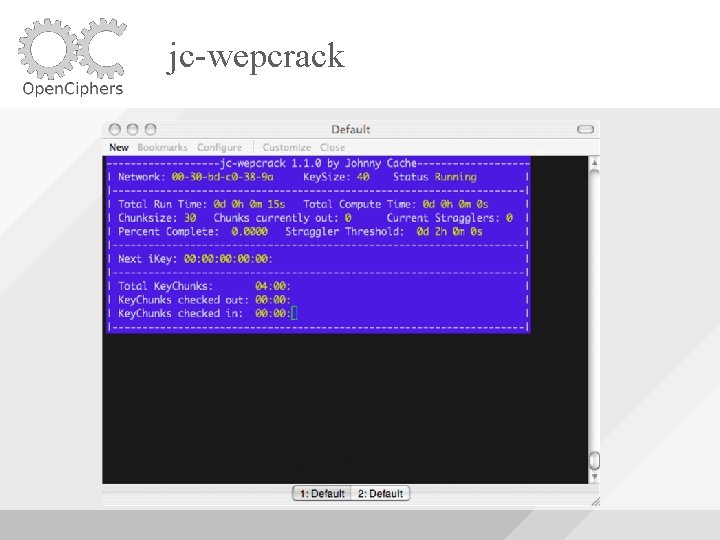
jc-wepcrack

jc-wepcrack

jc-wepcrack, no pico

Accelerating brute forcing

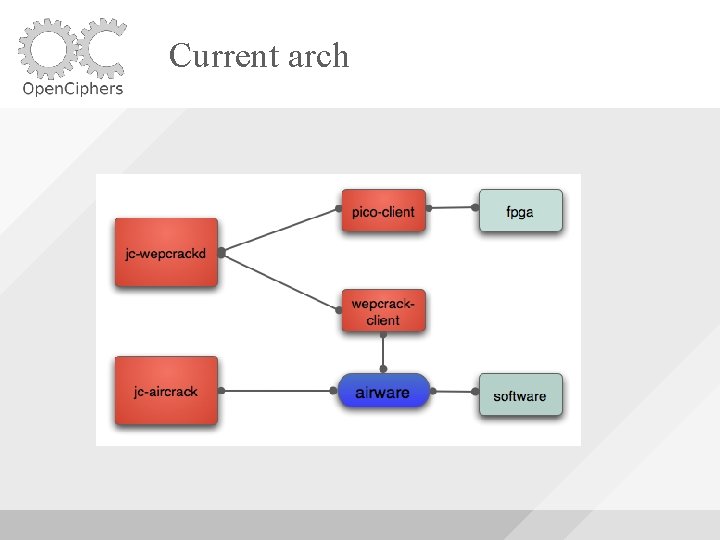
Current arch

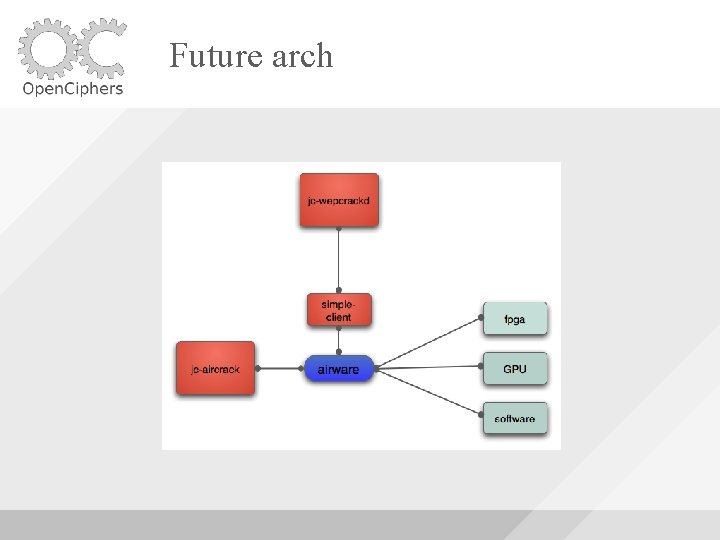
Future arch

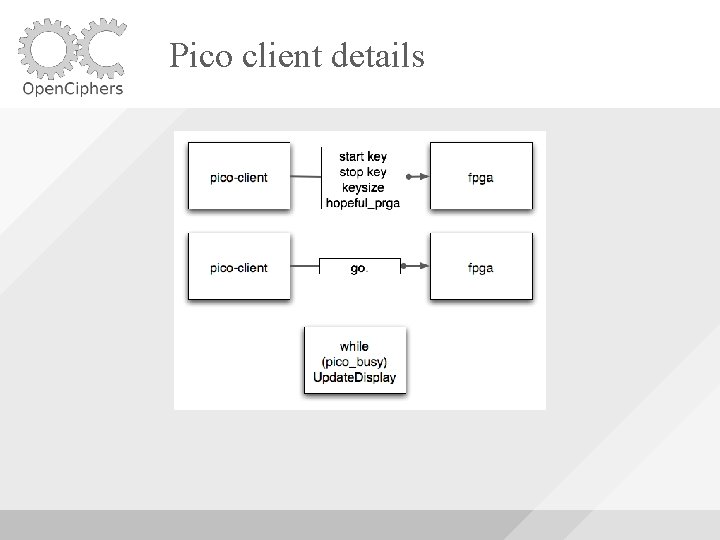
Pico client details

Airbase

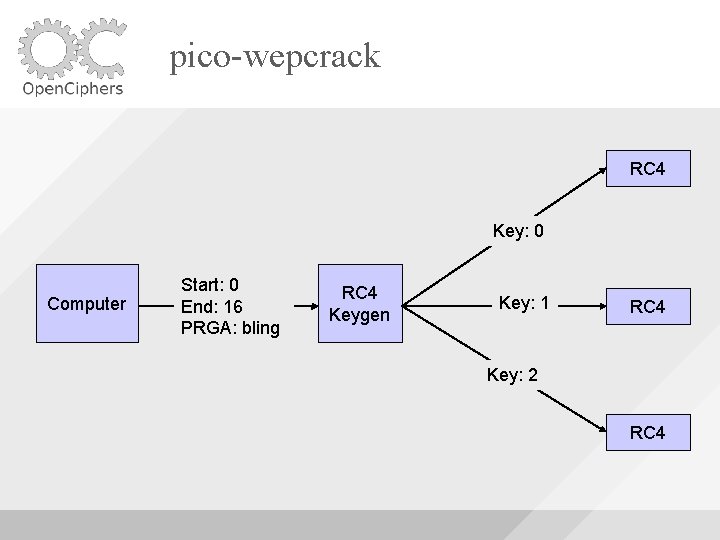
pico-wepcrack FPGA Core Uses 32/48 custom RC 4 cores Uses Block. RAM for S-Boxes Will try every key between a start and end
![picowepcrack RC 4 fori 0 i 256 i Si i fori pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; for(i](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-50.jpg)
pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; for(i = j = 0; i < 256; i++) { j += S[i] + K[i]; Swap(S[i], S[j]); } for(i = 1, j = 0; ; i++) { j += S[i]; Swap(S[i], S[j]); PRGA[i – 1] = S[S[i] + S[j]]; } // Initialization // KSA // PRGA
![picowepcrack RC 4 fori 0 i 256 i Si i pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; //](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-51.jpg)
pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; // Initialization for(i = j = 0; i < 256; i++) { // KSA j += S[i] + K[i]; // K is input Swap(S[i], S[j]); } for(i = 1, j = 0; ; i++) { j += S[i]; Swap(S[i], S[j]); PRGA[i – 1] = S[S[i] + S[j]]; } // PRGA is output

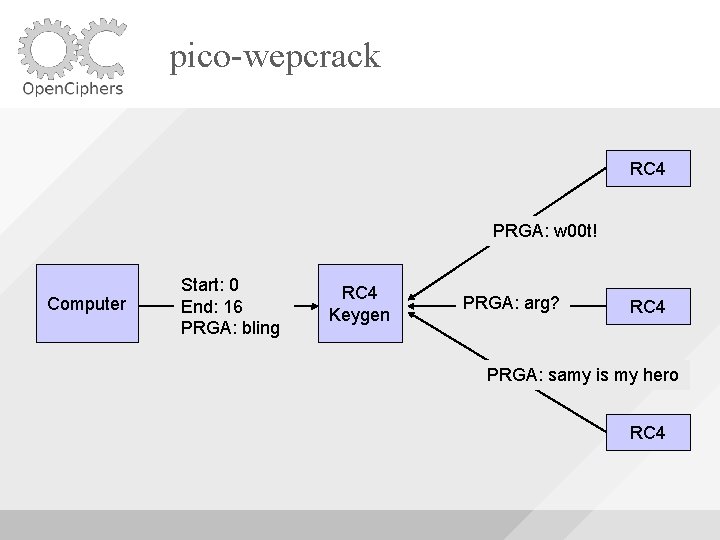
pico-wepcrack RC 4 Key: 0 Computer Start: 0 End: 16 PRGA: bling RC 4 Keygen Key: 1 RC 4 Key: 2 RC 4

pico-wepcrack RC 4 PRGA: w 00 t! Computer Start: 0 End: 16 PRGA: bling RC 4 Keygen PRGA: arg? RC 4 PRGA: samy is my hero RC 4

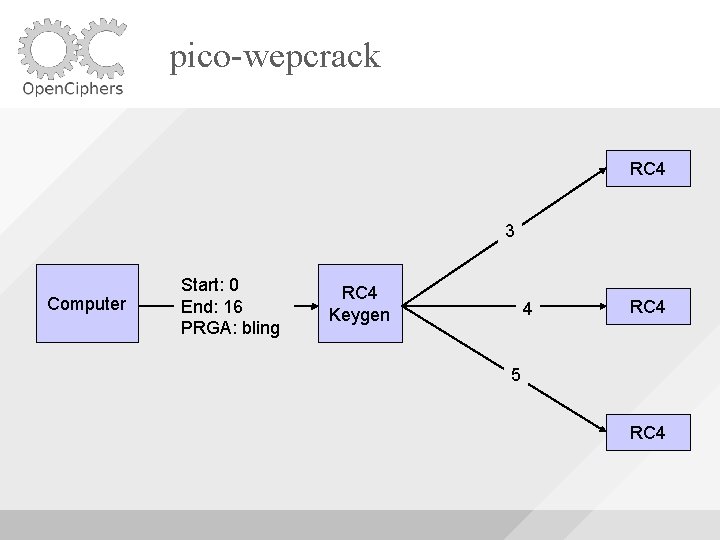
pico-wepcrack RC 4 3 Computer Start: 0 End: 16 PRGA: bling RC 4 Keygen 4 RC 4 5 RC 4

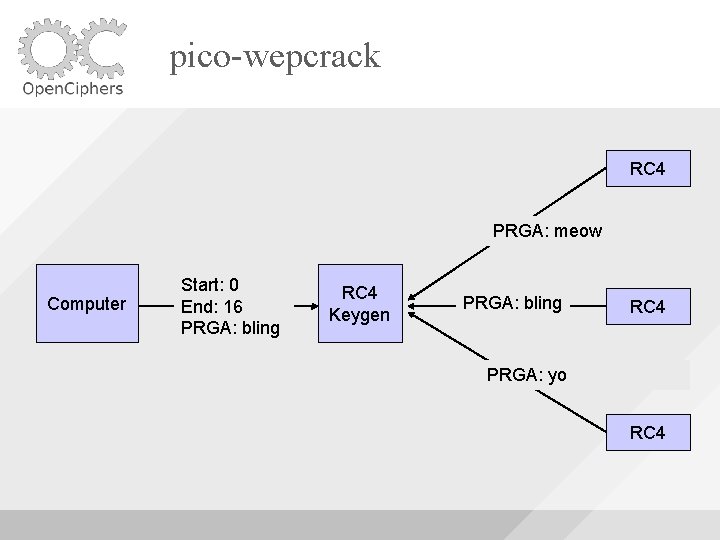
pico-wepcrack RC 4 PRGA: meow Computer Start: 0 End: 16 PRGA: bling RC 4 Keygen PRGA: bling RC 4 PRGA: yo RC 4
![picowepcrack RC 4 fori 0 i 256 i Si i pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; //](https://slidetodoc.com/presentation_image_h/f6ac569a2f599507908a326b92d8d25e/image-56.jpg)
pico-wepcrack RC 4: for(i = 0; i < 256; i++) S[i] = i; // Initialization // S-Box must be reset for(i = j = 0; i < 256; i++) { j += S[i] + K[i]; Swap(S[i], S[j]); } for(i = 1, j = 0; ; i++) { j += S[i]; Swap(S[i], S[j]); PRGA[i – 1] = S[S[i] + S[j]]; } // KSA // PRGA

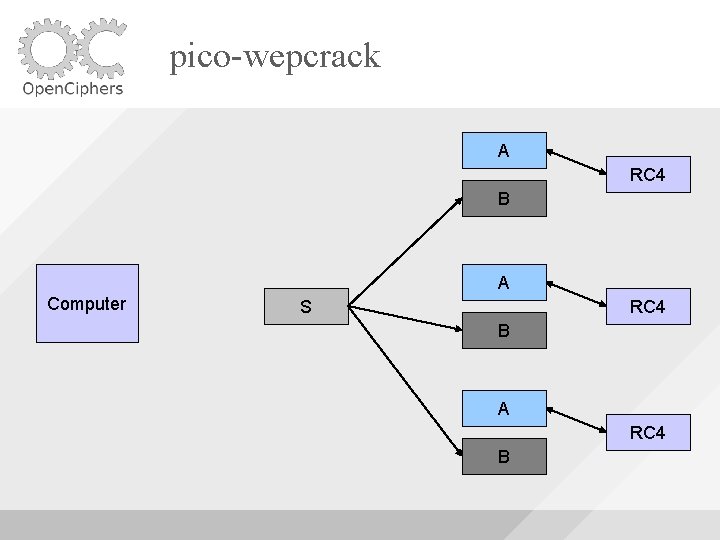
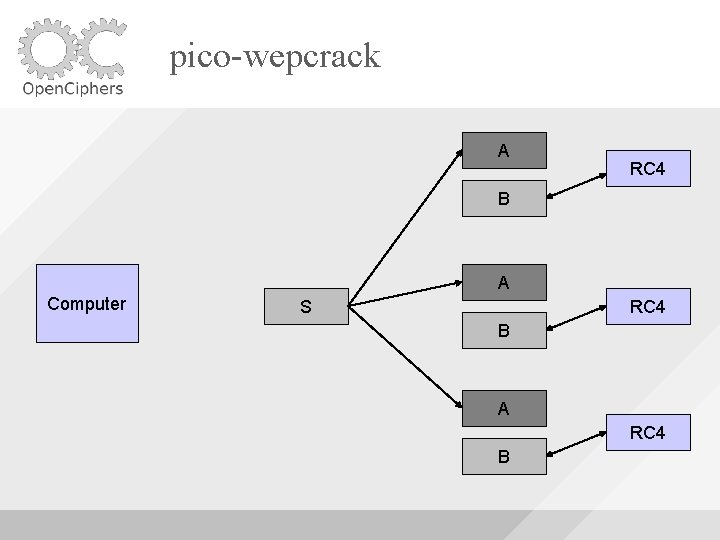
pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

pico-wepcrack A RC 4 B A Computer S RC 4 B A RC 4 B

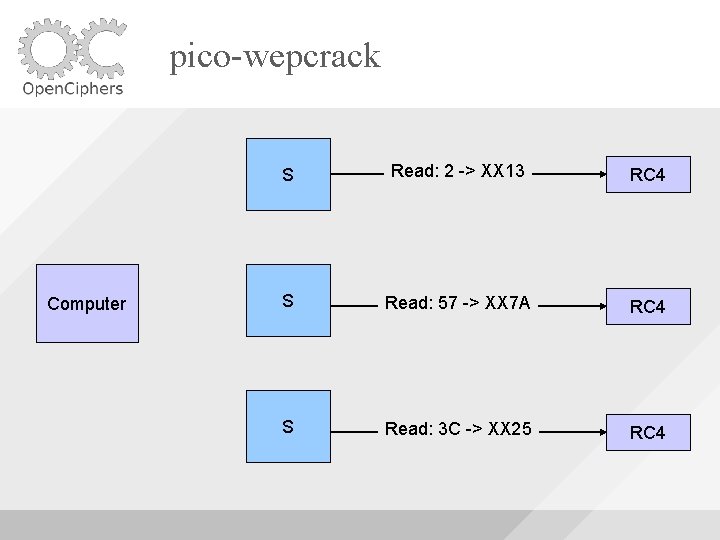
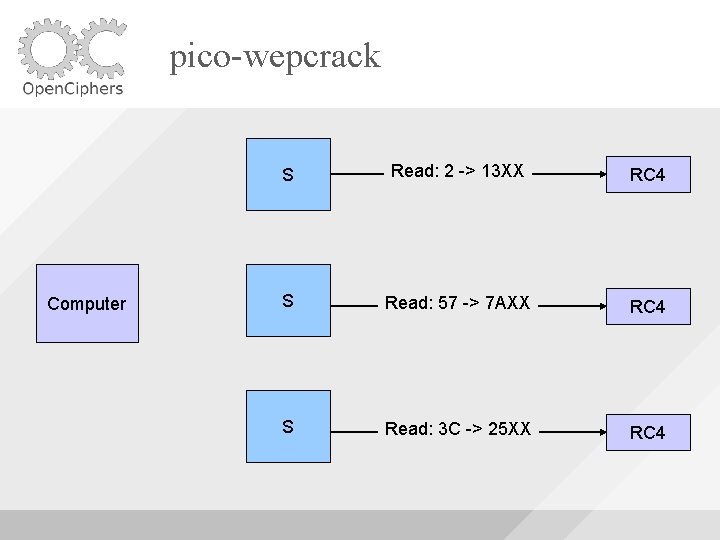
pico-wepcrack Computer S Read: 2 -> XX 13 RC 4 S Read: 57 -> XX 7 A RC 4 S Read: 3 C -> XX 25 RC 4

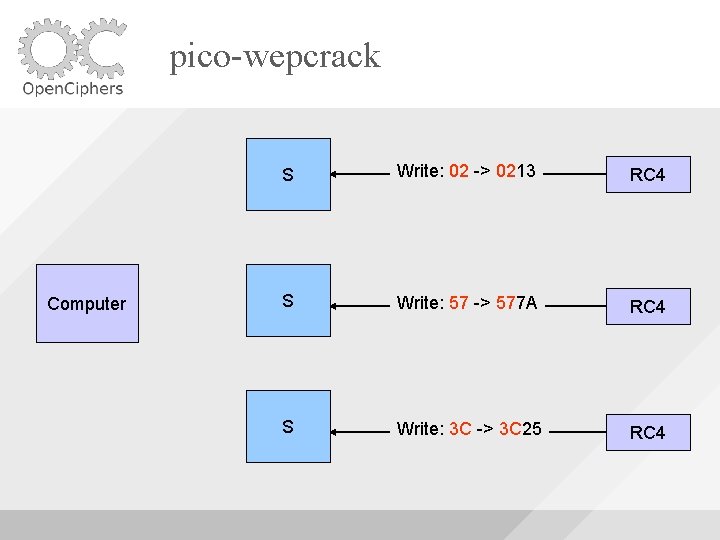
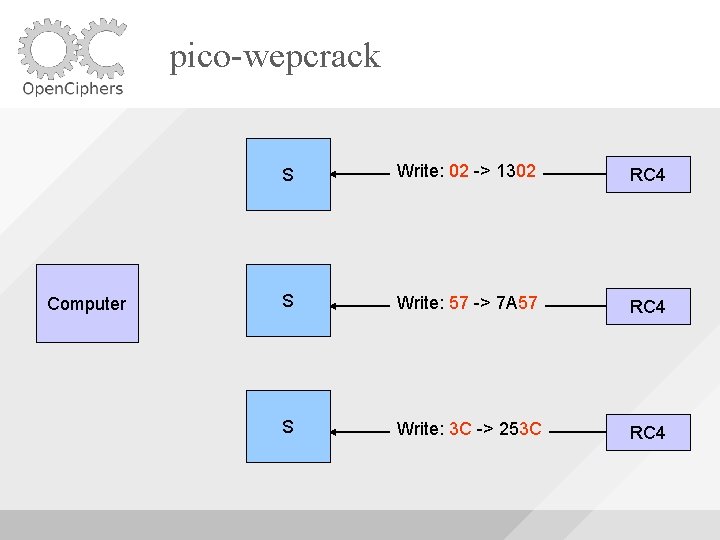
pico-wepcrack Computer S Write: 02 -> 0213 RC 4 S Write: 57 -> 577 A RC 4 S Write: 3 C -> 3 C 25 RC 4

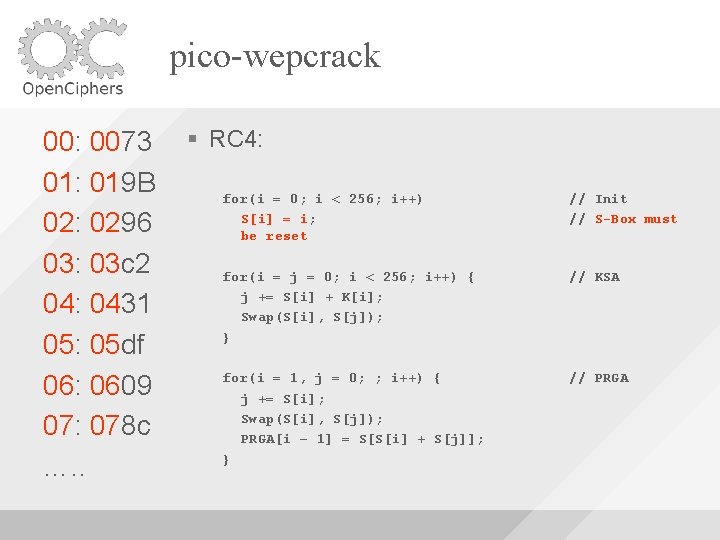
pico-wepcrack 00: 0073 01: 019 B 02: 0296 03: 03 c 2 04: 0431 05: 05 df 06: 0609 07: 078 c …. . RC 4: for(i = 0; i < 256; i++) S[i] = i; be reset // Init // S-Box must for(i = j = 0; i < 256; i++) { j += S[i] + K[i]; Swap(S[i], S[j]); } // KSA for(i = 1, j = 0; ; i++) { j += S[i]; Swap(S[i], S[j]); PRGA[i – 1] = S[S[i] + S[j]]; } // PRGA

pico-wepcrack Computer S Read: 2 -> 13 XX RC 4 S Read: 57 -> 7 AXX RC 4 S Read: 3 C -> 25 XX RC 4

pico-wepcrack Computer S Write: 02 -> 1302 RC 4 S Write: 57 -> 7 A 57 RC 4 S Write: 3 C -> 253 C RC 4

pico-wepcrack + + = ?

Demo

Performance Comparison PC FPGA jc-wepcrack pico-wepcrack 1. 25 GHz G 4 ~150, 000/sec 3. 6 GHz P 4 ~300, 000/sec LX 25 ~9, 000/sec 15 Cluster ~135, 000/sec FX 60 ~18, 000/sec

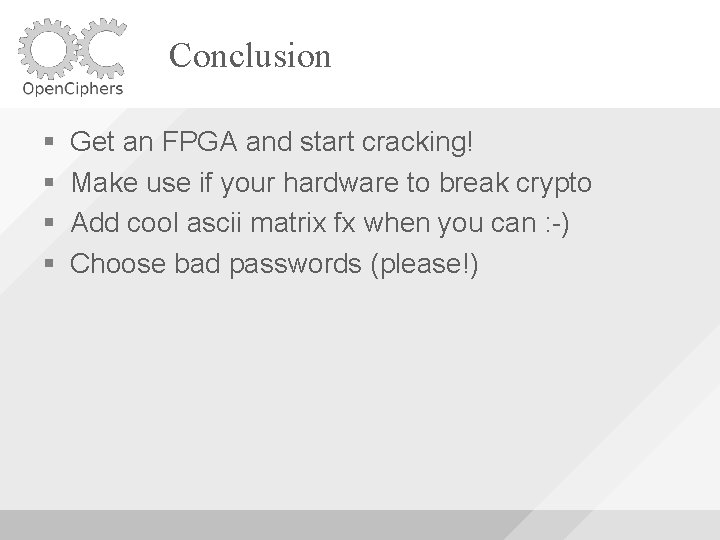
Conclusion Get an FPGA and start cracking! Make use if your hardware to break crypto Add cool ascii matrix fx when you can : -) Choose bad passwords (please!)

Hardware Used Pico E-12 Compact Flash 64 MB Flash 128 MB SDRAM Gigabit Ethernet Optional 450 MHz Power. PC 405

Hardware Used Pico E-12 Super Cluster 15 - E-12’s 2 - 2. 8 GHz Pentium 4’s 2 - 120 GB HDD 2 - DVD-RW 550 Watt Power Supply

Greetz Johny Cache (airbase/jc-wepcrack/jc-aircrack) Josh Wright (cowpatty) Render. Man (pmk hashtable monkey) Beetle (ghettopmk!) Audience (feel free to throw rotten fruit now!!)

Questions? I’ll give you a free set of hash tables! David Hulton dhulton@openciphers. org http: //www. picocomputing. com http: //www. 802. 11 mercenary. net http: //www. churchofwifi. org
 Mutually assured destruction cartoon
Mutually assured destruction cartoon Intelligent manufacturing software
Intelligent manufacturing software Assured criteria
Assured criteria Assured availability
Assured availability Strom thurmond apush
Strom thurmond apush Mutually assured destruction cuban missile crisis
Mutually assured destruction cuban missile crisis Isaiah 15 16
Isaiah 15 16 Social engineering password cracking
Social engineering password cracking Why do we need cracking
Why do we need cracking Password cracking definition
Password cracking definition Hydrogen assisted cracking
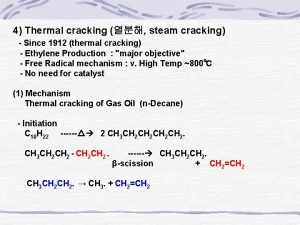
Hydrogen assisted cracking Catalytic cracking of octane
Catalytic cracking of octane Cracking the sales management code summary
Cracking the sales management code summary Cracking wep
Cracking wep Is cracking an egg a physical change
Is cracking an egg a physical change Aci 224
Aci 224 Silver bullet cracking
Silver bullet cracking Pharmaceutical application of emulsion
Pharmaceutical application of emulsion Family name origin
Family name origin Cracking the facebook coding interview
Cracking the facebook coding interview Catalytic cracking
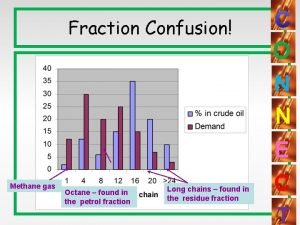
Catalytic cracking Fractional distillation of petroleum
Fractional distillation of petroleum Naphthenes in crude oil
Naphthenes in crude oil Suburbanization definition ap human geography
Suburbanization definition ap human geography Unit 4
Unit 4 The witches of easter-wick in finland
The witches of easter-wick in finland Corliss jackson
Corliss jackson Cyclopentadiene cracking
Cyclopentadiene cracking Bigger better stronger faster
Bigger better stronger faster Faster than fairies
Faster than fairies Painted stations whistle by
Painted stations whistle by Faster higher stronger
Faster higher stronger What faster than light
What faster than light The universe faster than should be
The universe faster than should be Temperature and activation energy
Temperature and activation energy Fast scale
Fast scale Do heavier objects fall faster
Do heavier objects fall faster Which one is faster
Which one is faster The faster should
The faster should What is electrophoresis
What is electrophoresis They've always been faster
They've always been faster Do heavier things fall faster
Do heavier things fall faster 28 day faster diagnosis standard
28 day faster diagnosis standard Driving faster can cause disaster
Driving faster can cause disaster Game who is faster
Game who is faster Because you speak english unnaturally
Because you speak english unnaturally Do heavier objects fall faster
Do heavier objects fall faster Faster rcnn
Faster rcnn Http://www.allthingshairy.com grow hair faster
Http://www.allthingshairy.com grow hair faster The universe expanding faster than
The universe expanding faster than Degree of comparison of merry
Degree of comparison of merry Which chocolate melts faster experiment
Which chocolate melts faster experiment Do heavier objects fall faster
Do heavier objects fall faster Wwwgames
Wwwgames Sonography means
Sonography means 28 day faster diagnosis standard
28 day faster diagnosis standard The universe expanding faster should
The universe expanding faster should Are switch statements faster than if/else
Are switch statements faster than if/else Reaction pairs
Reaction pairs Domain adaptive faster rcnn
Domain adaptive faster rcnn Im faster than you
Im faster than you Faster dynamic voltage scaling
Faster dynamic voltage scaling Tachyonization
Tachyonization Princess pat song lyrics
Princess pat song lyrics A cart is pushed and undergoes a certain acceleration
A cart is pushed and undergoes a certain acceleration Mara runs faster than gail
Mara runs faster than gail Sound travels fastest through
Sound travels fastest through Which car is going faster a or b
Which car is going faster a or b