CPSC 607 John Brosz Artificial Immune Systems AlgorithmsSystems

CPSC 607 John Brosz
Artificial Immune Systems Algorithms/Systems inspired by the human immune system. Use results from Computational Immunology for other applications.
3 Types of Systems 1. Artificial Negative Selection. 2. Artificial Clonal Selection & Hypermutation. 3. Artificial Immune Networks.
Artificial Negative Selection These systems model the immune system’s ability to differentiate between self and non-self entities. The main idea is to use binary strings to represent antigens.

Artificial Negative Selection Implementation Initialization & Training Create a set, S, of self strings (self antigens). Randomly generate a set R 0 of binary strings (lymphocyte antibodies). Test each string in R 0 against S, adding non-reactive* strings to set R. * - Reactive/non-reactive will be defined soon.
Artificial Negative Selection Implementation System Checking Test elements of self against elements of R. If reaction found, there is a non-self intruder in the system.
Artificial Negative Selection Reaction: Indicates a strong match between bit sequences. Reaction defined by a matching function compared to a threshold: m(r, s) > T. m(r, s) returns the largest number of matching contiguous bits between strings r and s. T is a chosen threshold. Many possibilities for matching function. Another popular choice is Hamming distance.
Applications Detecting viruses in machine code. Change/breakage detection in hardware and software. Detecting network intrusions.

Variation Positive Selection The inverse of negative selection. Keep the elements of R 0 that react to S. Strings that do not react to elements of R are then labeled as non-self.
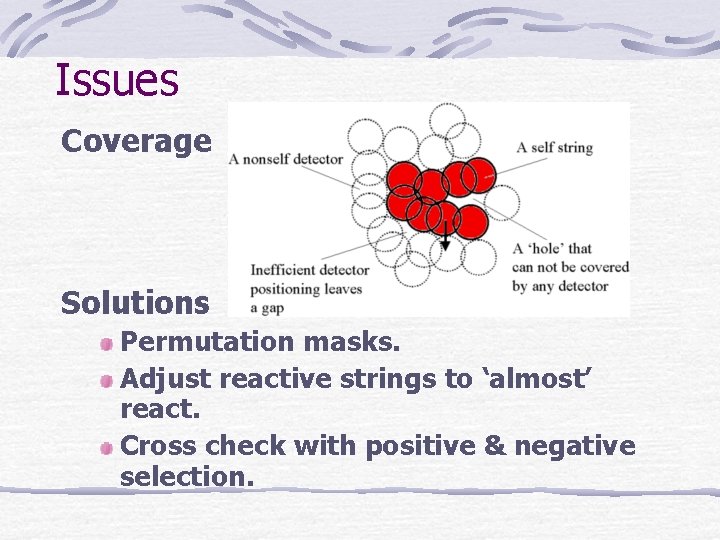
Issues Coverage Solutions Permutation masks. Adjust reactive strings to ‘almost’ react. Cross check with positive & negative selection.

Issues Speed Can be slow, especially with large strings and large self & detector sets. Solutions Nonrandom generation of detectors. Eliminate detectors that are too similar.
Artificial Clonal Selection & Hypermutation (ACSH) These systems are based on how b-cell lymphocytes adapt to match & destroy foreign objects.

ACSH – Example Implementation 1. 2. 3. 4. 5. 6. Create a set of n random strings (antibodies). Evaluate each string’s fitness (antibody success in matching antigen). Subset of the most fit strings are selected. Copies of fit strings are mutated at a rate inversely proportional to fitness. Strings from 3 & 4 are collected into a set & the least fit strings are culled until set has size n. Repeat 2 -5 until termination condition met.

ACSH – Applications Many types of optimization problems. Pattern recognition. Graph coloring.
ACSH – Issues Very similar to Genetic Algorithms. Difference lies in determination of mutation rate. Outperformed by other techniques. Scalability is issue due to increases in the number of clones yielding large increases in fitness evaluations. Can been seen as a simplified case of artificial immune network models.
Artificial Immune Network Models Immune system has two responses: Primary – antigen encountered for first time, reaction eventually created against antigen. Secondary – occurs when a particular or similar antigen is encountered again. Results in rapid production of appropriate Bcells. This second response indicates that the immune system has memory and is capable of learning appropriate responses.
Artificial Immune Network Models Immune network models imitate the immune system’s learning and memory by mimicking the interactions and feedback that occurs between antibodies and antigens.
Artificial Immune Network Models Captured Behaviors: Antibodies have paratopes & epitopes. Antigens only have epitopes. Paratopes bind to complementary epitopes. Substances with bound epitopes decrease in numbers/concentration. Substances (antibodies) with bound paratopes increase in numbers/concentration.
Artificial Immune Network Models Network Setup Create antibodies with random paratopes and epitopes (binary strings). Each antibody’s concentration is determined based on interaction of paratopes/epitopes with other antibodies. Antibodies with lowest concentrations are removed and replaced with new random antibodies. Repeat several times.
Artificial Immune Network Models Primary Response (Learning/Immunization) Introduce an antigen. Antigens have epitopes that are binary strings representing input. Fitness function & differential equation determine how antibodies increase/decrease in concentration.
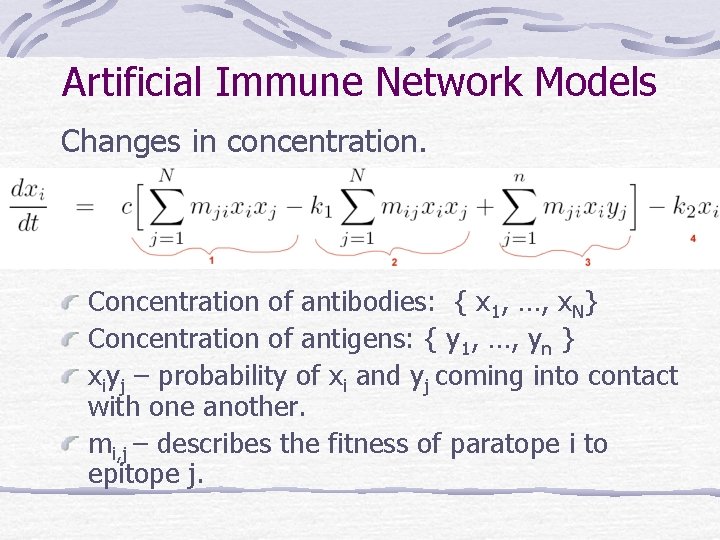
Artificial Immune Network Models Changes in concentration. Concentration of antibodies: { x 1, …, x. N} Concentration of antigens: { y 1, …, yn } xiyj – probability of xi and yj coming into contact with one another. mi, j – describes the fitness of paratope i to epitope j.
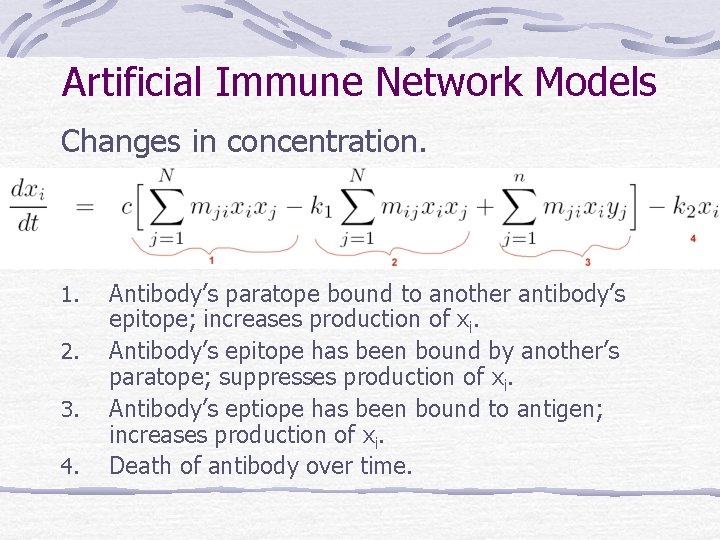
Artificial Immune Network Models Changes in concentration. 1. 2. 3. 4. Antibody’s paratope bound to another antibody’s epitope; increases production of xi. Antibody’s epitope has been bound by another’s paratope; suppresses production of xi. Antibody’s eptiope has been bound to antigen; increases production of xi. Death of antibody over time.
Artificial Immune Network Models Primary Response Antibody concentration updated via the differential function. When a particular antibody’s concentration falls below threshold, that type of antibody is removed from system. New antibodys are introduced to replace old ones. New antibodies are created by mutating current antibodies in the system. Antibody selection for mutation is based concentration of antibody.
Artificial Immune Network Models Secondary Response (Classification) Introduce input to system via antigen (binary sequence for epitope). Update concentrations with differential equations. Antibody response is output. Depends on system but usually response is epitope of antibody with best matching paratope.
Artificial Immune Network Models How Does It Work? The key is the antibody/antibody reactions. These form cycles that save useful antibodies when they aren’t responding to antigens. Only antibodies that do not react with other antibodies get forgotten. If we increase the number of antibodies, this increases the number of cycles and the average cycle length.
Artificial Immune Network Models Applications Pattern recognition & classification. Optimization problems. Finding centers of radial basis functions. Cleaning GPS data.
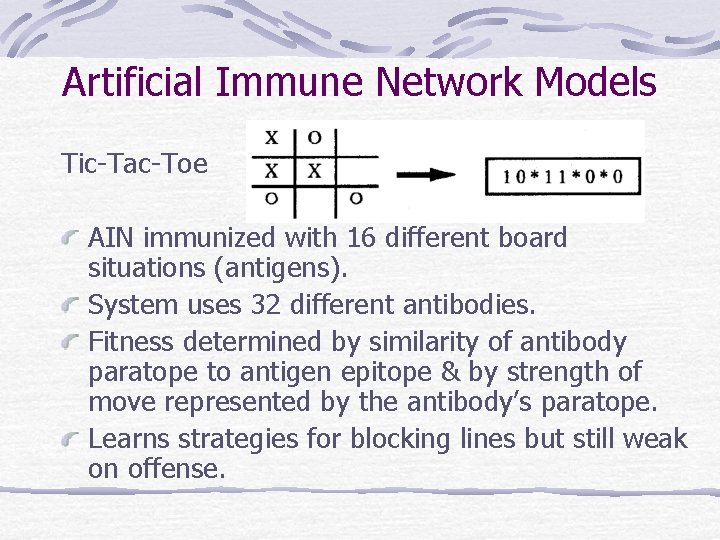
Artificial Immune Network Models Tic-Tac-Toe AIN immunized with 16 different board situations (antigens). System uses 32 different antibodies. Fitness determined by similarity of antibody paratope to antigen epitope & by strength of move represented by the antibody’s paratope. Learns strategies for blocking lines but still weak on offense.
AIS Overview References S. Garrett (2005). How do we evaluate artificial immune systems? Evoluationary Computation, 13(2): 145 -178. Negative Selection S. Forrest, A. Perelson, L. Allen, & R. Cherukuri (1994). Self-nonself discrimination in a computer. IEEE Symposium on Research in Security and Privacy, 132 -143. ACSH L. de Castro & F. Von Zuben (2000). The clonal selection algorithm with engineering applications. GECCO Workshop on Artificial Immune Systems & Their Applications, 36 -37. Artificial Immune Networks J. Farmer, N. Packard, & A. Perelson (1986). The immune system adaptation and machine learning. Physica D, 22: 187 -204. J. Hunt & D. Cooke (1995). An Adaptive Distributed Learning System Based on the Immune System. IEEE International Conference on Systems, Man, and Cybernetics, 2494 -2499.

Variations & Issues Danger Theory Observations in ’ 90 s show inconsistencies in original self/non-self theory. Danger theory is a new explanation. Immune system does not respond directly to nonself elements. It responds to cells in distress (necrosis). Response is not system-wide, it is local. Nature of danger signals is unclear.

Variations & Issues Danger Theory Idea: the system looks for danger indications & finds cause(s). Great potential since its more local. Drawback is that damage occurs before the system responds. Theoretical applications, none implemented. Difficult because danger theory still “sketchy”.
- Slides: 30