CPS 120 Introduction to Computer Science LowLevel Programming















- Slides: 24

CPS 120: Introduction to Computer Science Low-Level Programming Languages Nell Dale • John Lewis

Bits, Bytes and Characters • Bytes are frequently used to hold individual characters in a text document. In the ASCII character set, each binary value between 0 and 127 is given a specific character. • Most computers extend the ASCII character set to use the full range of 256 characters available in a byte. • The upper 128 characters handle special things like accented characters from common foreign languages

ASCII • Each byte contains not a letter but a number -- the number is the ASCII code corresponding to the character (see below). So on disk, the numbers for the file look like this: • Four and seven • 70 111 117 114 32 97 110 100 32 115 101 118 101 110 – By looking in the ASCII table, you can see a one-to-one correspondence between each character and the ASCII code used. – Note the use of 32 for a space -- 32 is the ASCII code for a space. – We could expand these decimal numbers out to binary numbers (so 32 = 00100000) if we wanted to be technically correct -- that is how the computer really deals with things.

What the Computer Can Do • Store, retrieve and process are actions that the computer can take on data

Computer Operations • A computer is a programmable electronic device that can store, retrieve, and process data • Data and instructions to manipulate the data are logically the same and can be stored in the same place • Store, retrieve, and process are actions that the computer can perform on data

Machine Language • Machine language: the instructions built into the hardware of a particular computer

Machine Language • Every processor type has its own set of specific machine instructions • The relationship between the processor and the instructions it can carry out is completely integrated • Each machine-language instruction does only one very low-level task

Pep/7: A Virtual Computer • A virtual computer is a hypothetical machine designed to contain the important features of real computers that we want to illustrated

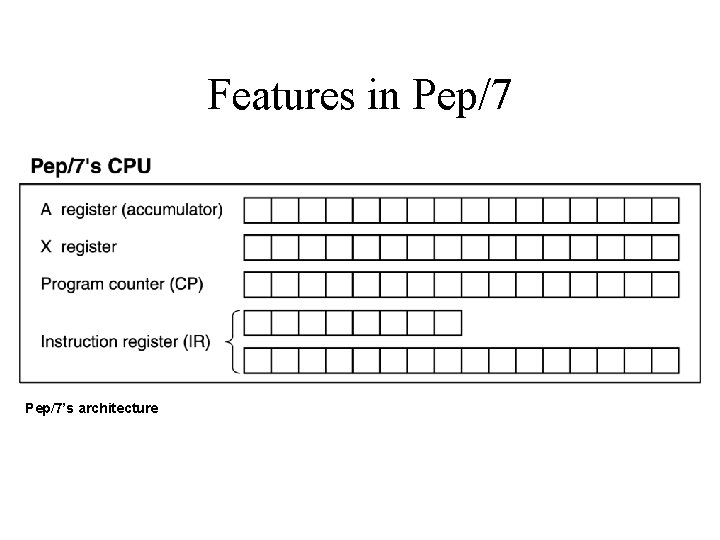
Features in Pep/7 • Pep/7 has 32 machine-language instructions • The memory unit is made up of 4, 096 bytes of storage (0 -4095 decimal) • The word length in Pep/7 is 16 bits • Pep/7 has seven registers, four of which we focus on at this point – The program counter (PC) (contains the address of the next instruction to be executed) – The instruction register (IR) (contains a copy of the instruction being executed) – The index register (X register) – holds data – The accumulator (A register) – holds data

Features in Pep/7’s architecture

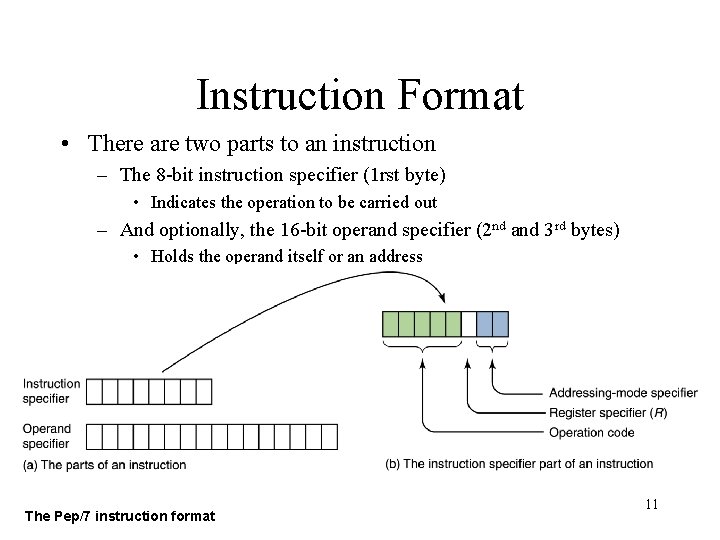
Instruction Format • There are two parts to an instruction – The 8 -bit instruction specifier (1 rst byte) • Indicates the operation to be carried out – And optionally, the 16 -bit operand specifier (2 nd and 3 rd bytes) • Holds the operand itself or an address The Pep/7 instruction format 11

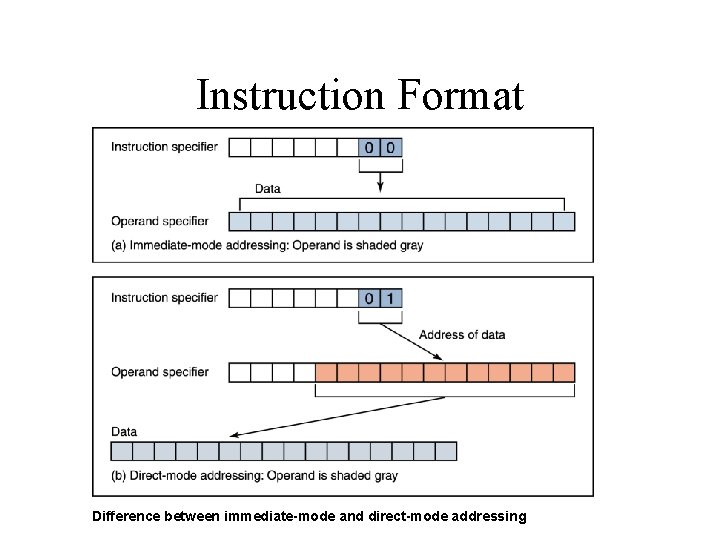
Instruction Format • The instruction specifier is made up of several sections – The operation code – The register specifier • 0 for A; 1 for X – The addressing-mode specifier • 00 immediate mode – last two bytes have operand • 01 direct mode – last two bytes contain an address

Instruction Format • The operation code specifies which instruction is to be carried out • The 1 -bit register specifier is 0 if register A (the accumulator) is involved in the operation and 1 if register X (the index register) is involved • The 2 -bit addressing-mode specifier says how to interpret the operand part of the instruction

Instruction Format Difference between immediate-mode and direct-mode addressing

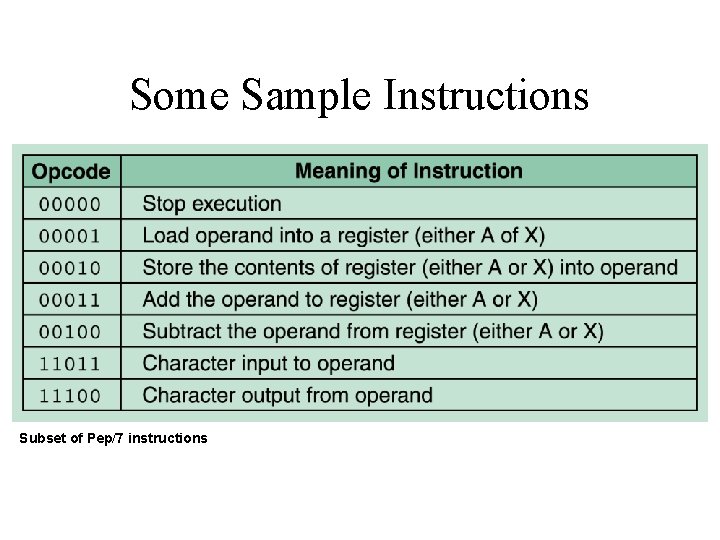
Some Sample Instructions Subset of Pep/7 instructions

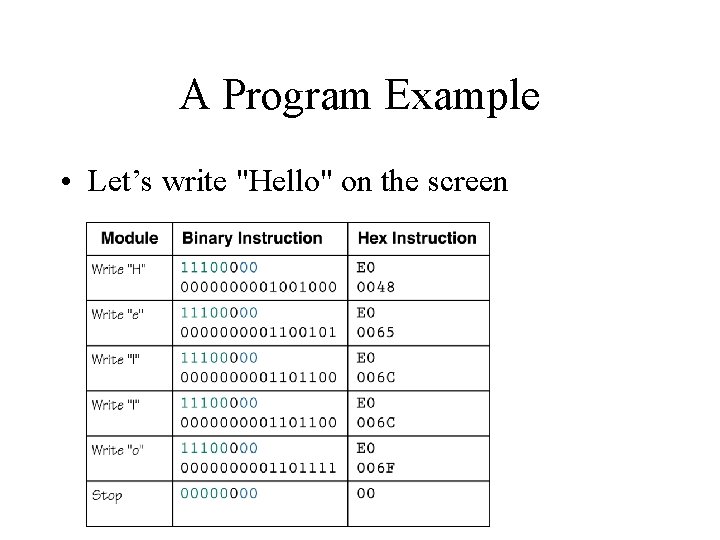
A Program Example • Let’s write "Hello" on the screen

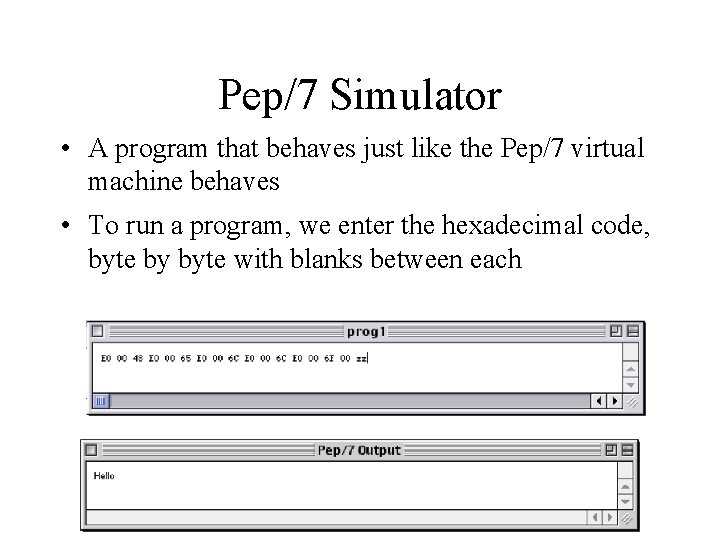
Pep/7 Simulator • A program that behaves just like the Pep/7 virtual machine behaves • To run a program, we enter the hexadecimal code, byte by byte with blanks between each

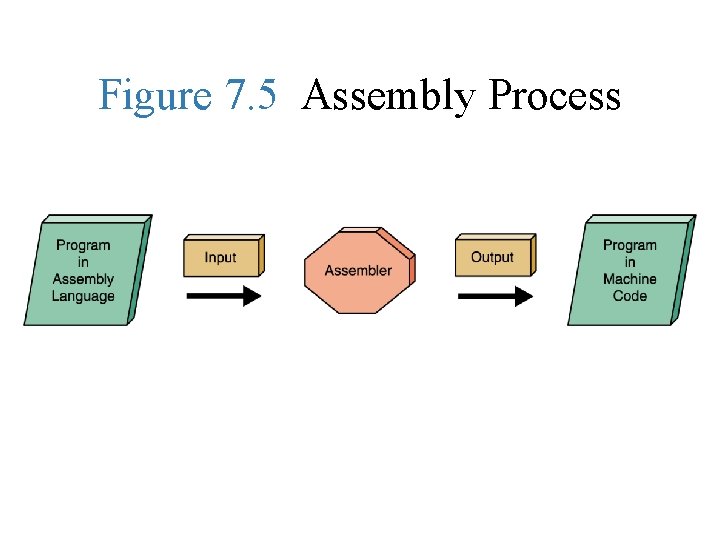
Assembly Language • Assembly languages: assign mnemonic letter codes to each machine-language instruction – The programmer uses these letter codes in place of binary digits – A program called an assembler reads each of the instructions in mnemonic form and translates it into the machine-language equivalent

Hello -- Assembly CHARO C#H/ J; Output 'H' CHARO C#e/ J; Output 'e' CHARO C#l/ J; Output 'l' CHARO C#o/ J; Output 'o' STOP END

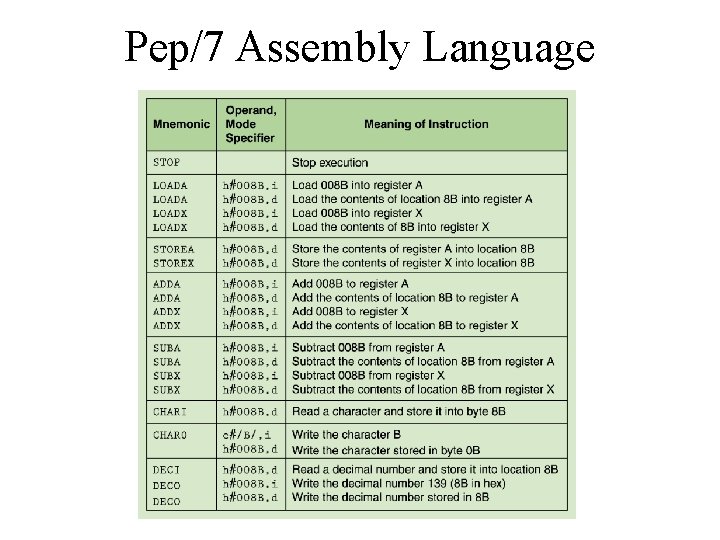
Pep/7 Assembly Language

Figure 7. 5 Assembly Process

A New Program

Our Completed Program

Testing • Test plan: a document that specifies how many times and with what data the program must be run in order to thoroughly test the program • A code-coverage approach designs test cases to ensure that each statement in the program is executed • Data-coverage testing is another approach; it designs test cases to ensure that the limits of the allowable data are covered