CPIT 425 Chapter Three Symmetric Key Cryptography Index









![Example 2: DES Plain text = p= [0000] P 4= [2431] IP= [26314857]; IP-1=[41357286] Example 2: DES Plain text = p= [0000] P 4= [2431] IP= [26314857]; IP-1=[41357286]](https://slidetodoc.com/presentation_image_h2/97ecd64841c19a6b1a9648befccd1559/image-52.jpg)




- Slides: 63

CPIT 425 Chapter Three: Symmetric Key Cryptography

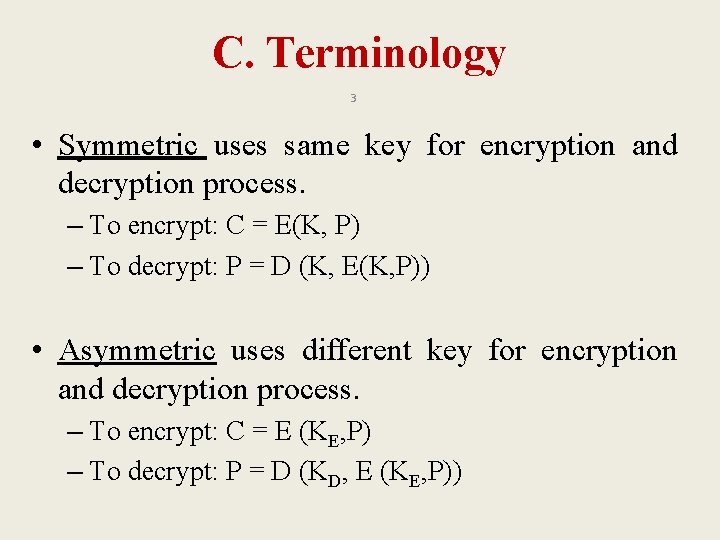
Index A. Introduction A. 1 Terminology A. 2 Symmetric Key Algorithms-Introduction B. Stream Cipher B. 1 A 5/1 B 2 RC 4 C. Block Cipher C. 1 Components of Block Cipher C. 2 Electronics Code Book Mode (ECB) C. 3 Cipher Block Channing Mode (CBC) D. Product Cipher E. Fiestal Cipher F. Data Encryption Standard (DES) G. Conclusion 2

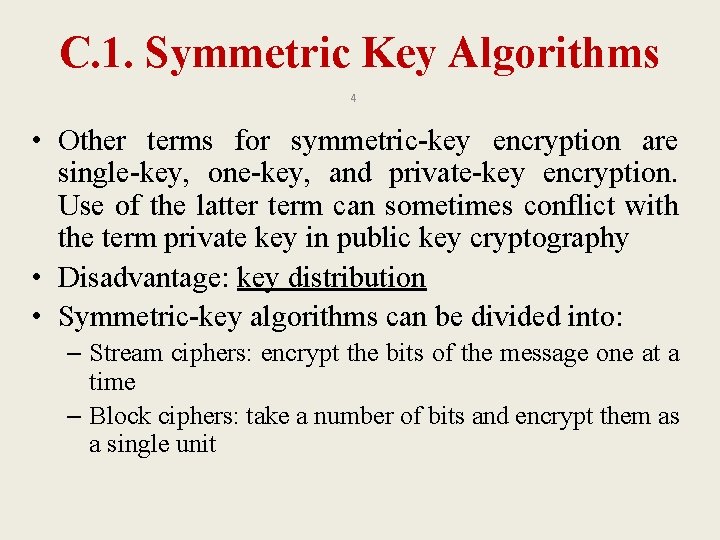
C. Terminology 3 • Symmetric uses same key for encryption and decryption process. – To encrypt: C = E(K, P) – To decrypt: P = D (K, E(K, P)) • Asymmetric uses different key for encryption and decryption process. – To encrypt: C = E (KE, P) – To decrypt: P = D (KD, E (KE, P))

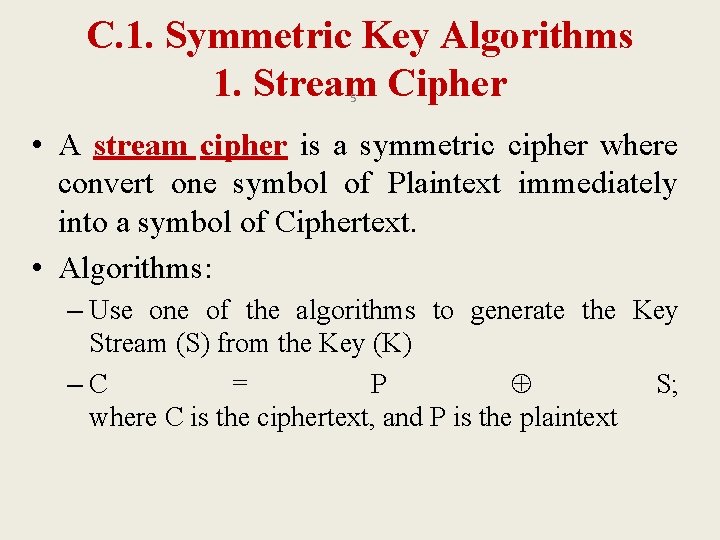
C. 1. Symmetric Key Algorithms 4 • Other terms for symmetric-key encryption are single-key, one-key, and private-key encryption. Use of the latter term can sometimes conflict with the term private key in public key cryptography • Disadvantage: key distribution • Symmetric-key algorithms can be divided into: – Stream ciphers: encrypt the bits of the message one at a time – Block ciphers: take a number of bits and encrypt them as a single unit

C. 1. Symmetric Key Algorithms 1. Stream Cipher 5 • A stream cipher is a symmetric cipher where convert one symbol of Plaintext immediately into a symbol of Ciphertext. • Algorithms: – Use one of the algorithms to generate the Key Stream (S) from the Key (K) –C = P S; where C is the ciphertext, and P is the plaintext

Stream Ciphers • Not as popular today as block ciphers • We’ll discuss two examples • A 5/1 – Based on shift registers – Used in GSM mobile phone system • RC 4 – Based on a changing lookup table – Used many places Part 1 Cryptography 7

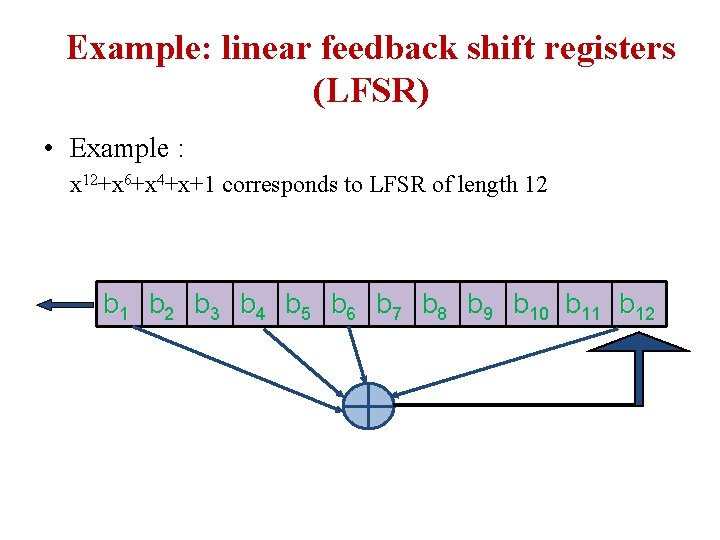
Example: linear feedback shift registers (LFSR) • Example : x 12+x 6+x 4+x+1 corresponds to LFSR of length 12 b 1 b 2 b 3 b 4 b 5 b 6 b 7 b 8 b 9 b 10 b 11 b 12

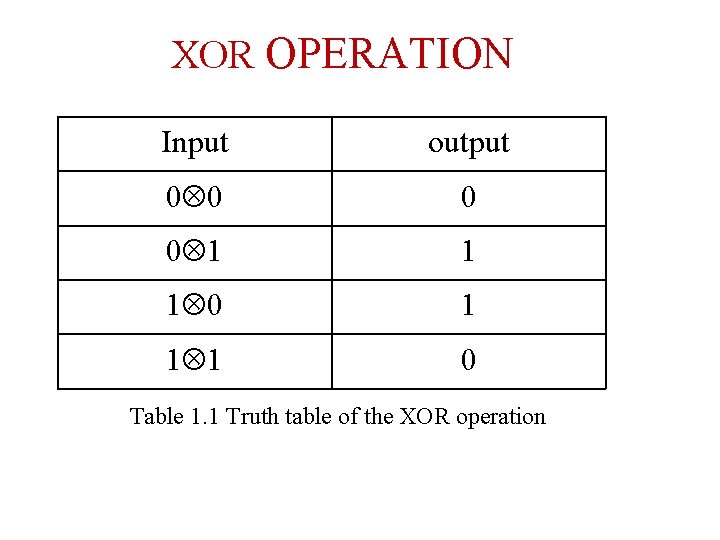
XOR OPERATION Input output 0 0 1 1 1 0 Table 1. 1 Truth table of the XOR operation

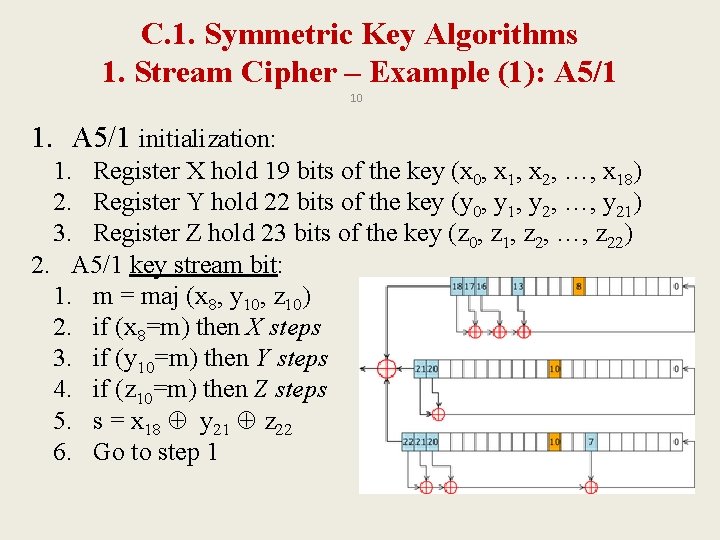
C. 1. Symmetric Key Algorithms 1. Stream Cipher – Example (1): A 5/1 10 1. A 5/1 initialization: 1. Register X hold 19 bits of the key (x 0, x 1, x 2, …, x 18) 2. Register Y hold 22 bits of the key (y 0, y 1, y 2, …, y 21) 3. Register Z hold 23 bits of the key (z 0, z 1, z 2, …, z 22) 2. A 5/1 key stream bit: 1. m = maj (x 8, y 10, z 10) 2. if (x 8=m) then X steps 3. if (y 10=m) then Y steps 4. if (z 10=m) then Z steps 5. s = x 18 y 21 z 22 6. Go to step 1

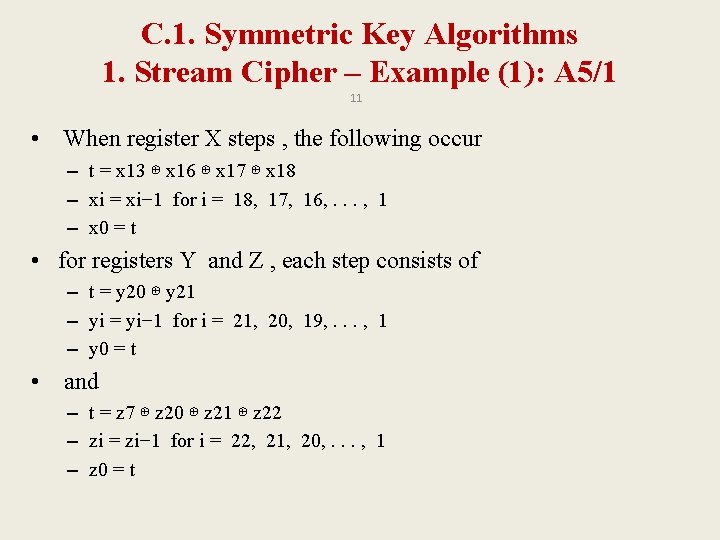
C. 1. Symmetric Key Algorithms 1. Stream Cipher – Example (1): A 5/1 11 • When register X steps , the following occur – t = x 13 ⊕ x 16 ⊕ x 17 ⊕ x 18 – xi = xi− 1 for i = 18, 17, 16, . . . , 1 – x 0 = t • for registers Y and Z , each step consists of – t = y 20 ⊕ y 21 – yi = yi− 1 for i = 21, 20, 19, . . . , 1 – y 0 = t • and – t = z 7 ⊕ z 20 ⊕ z 21 ⊕ z 22 – zi = zi− 1 for i = 22, 21, 20, . . . , 1 – z 0 = t

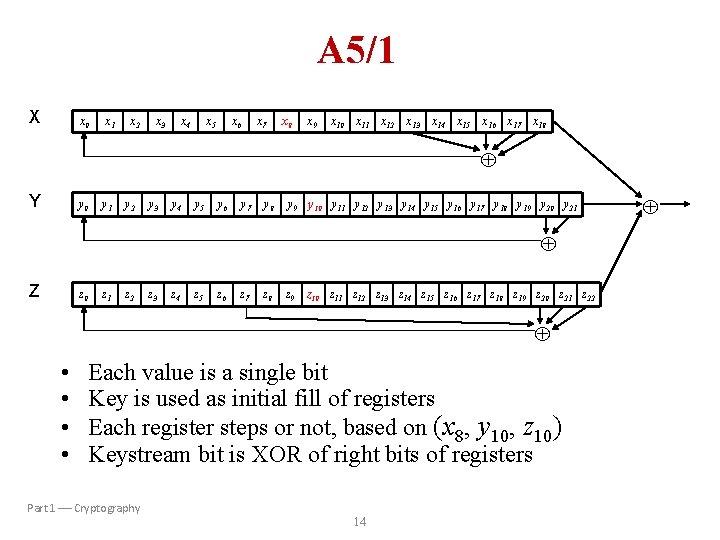
A 5/1 • A 5/1 consists of 3 shift registers – X: 19 bits (x 0, x 1, x 2, …, x 18) – Y: 22 bits (y 0, y 1, y 2, …, y 21) – Z: 23 bits (z 0, z 1, z 2, …, z 22) Part 1 Cryptography 12

A 5/1 • At each step: m = maj(x 8, y 10, z 10) – Examples: maj(0, 1, 0) = 0 and maj(1, 1, 0) = 1 • If x 8 = m then X steps – t = x 18 x 17 x 16 x 13 – xi = xi 1 for i = 18, 17, …, 1 and x 0 = t • If y 10 = m then Y steps – t = y 21 y 20 – yi = yi 1 for i = 21, 20, …, 1 and y 0 = t • If z 10 = m then Z steps – t = z 22 z 21 z 20 z 7 – zi = zi 1 for i = 22, 21, …, 1 and z 0 = t • Keystream bit is x 18 y 21 z 22 Part 1 Cryptography 13

A 5/1 X x 0 x 1 x 2 x 3 x 4 x 5 x 6 x 7 x 8 x 9 x 10 x 11 x 12 x 13 x 14 x 15 x 16 x 17 x 18 Y y 0 y 1 y 2 y 3 y 4 y 5 y 6 y 7 y 8 y 9 y 10 y 11 y 12 y 13 y 14 y 15 y 16 y 17 y 18 y 19 y 20 y 21 Z z 0 z 1 z 2 z 3 z 4 z 5 z 6 z 7 z 8 z 9 z 10 z 11 z 12 z 13 z 14 z 15 z 16 z 17 z 18 z 19 z 20 z 21 z 22 • • Each value is a single bit Key is used as initial fill of registers Each register steps or not, based on (x 8, y 10, z 10) Keystream bit is XOR of right bits of registers Part 1 Cryptography 14

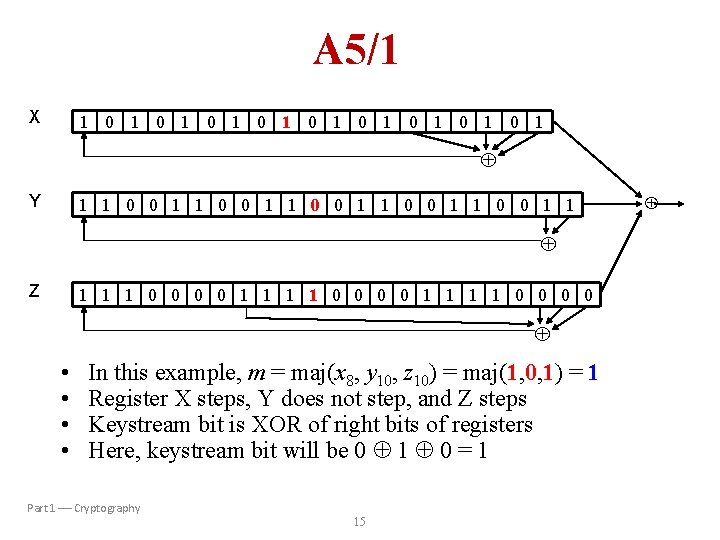
A 5/1 X 1 0 1 0 1 0 1 Y 1 1 0 0 1 1 0 0 1 1 Z 1 1 1 0 0 0 0 1 1 1 1 0 0 • • In this example, m = maj(x 8, y 10, z 10) = maj(1, 0, 1) = 1 Register X steps, Y does not step, and Z steps Keystream bit is XOR of right bits of registers Here, keystream bit will be 0 1 0 = 1 Part 1 Cryptography 15

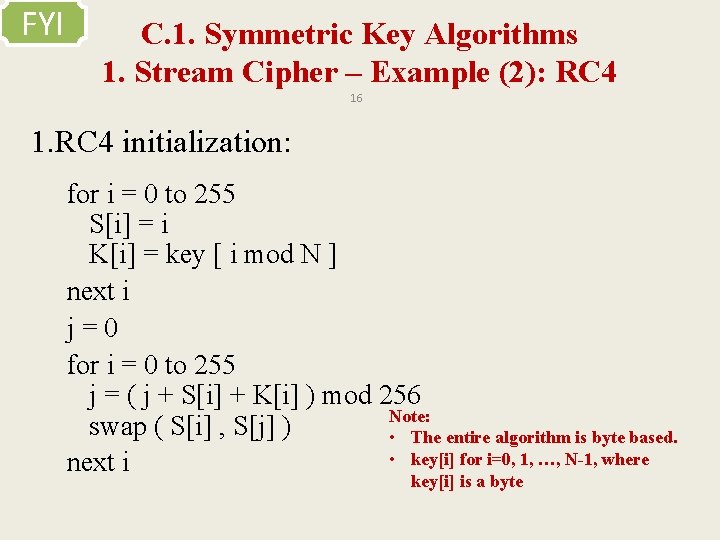
FYI C. 1. Symmetric Key Algorithms 1. Stream Cipher – Example (2): RC 4 16 1. RC 4 initialization: for i = 0 to 255 S[i] = i K[i] = key [ i mod N ] next i j=0 for i = 0 to 255 j = ( j + S[i] + K[i] ) mod 256 Note: swap ( S[i] , S[j] ) • The entire algorithm is byte based. • key[i] for i=0, 1, …, N-1, where next i key[i] is a byte

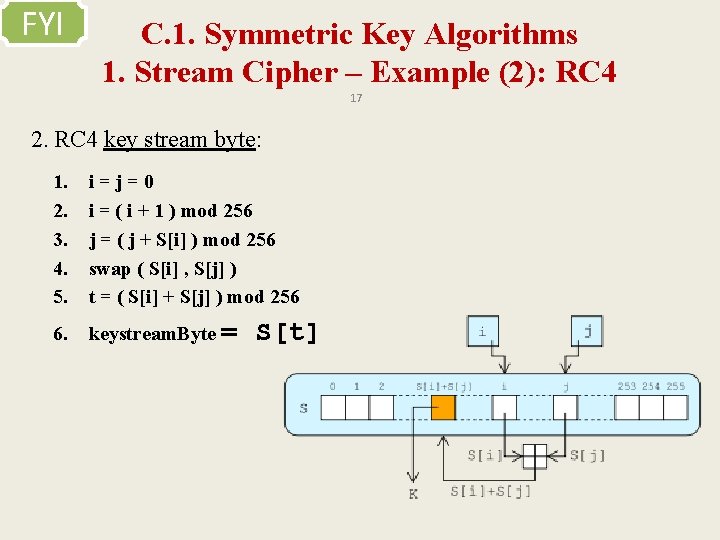
FYI C. 1. Symmetric Key Algorithms 1. Stream Cipher – Example (2): RC 4 17 2. RC 4 key stream byte: 1. 2. 3. 4. 5. i=j=0 i = ( i + 1 ) mod 256 j = ( j + S[i] ) mod 256 swap ( S[i] , S[j] ) t = ( S[i] + S[j] ) mod 256 6. keystream. Byte = S[t]

RC 4: Example 2: Lets consider the stream cipher RC 4, but instead of the full 256 bytes, we will use 8 x 3 -bits. That is, the state vector S is 8 x 3 -bits. We will operate on 3 -bits of plaintext at a time since S can take the values 0 to 7, which can be represented as 3 bits. Assume we use a 4 x 3 -bit key of K = [1 2 3 6]. And a plaintext P = [1 2 2 2] The first step is to generate the stream. Initialise the state vector S and temporary vector T. S is initialised so the S[i] = i, and T is initialised so it is the key K (repeated as necessary). S = [0 1 2 3 4 5 6 7] T = [1 2 3 6] 18

RC 4: Example 2(cont): Solution: i, j = 0; while (true) { i = (i + 1) mod 8; j = (j + S[i]) mod 8; Swap (S[i], S[j]); t = (S[i] + S[j]) mod 8; k = S[t]; } The first iteration: S = [2 3 7 4 0 1 6 5] i = (0 + 1) mod 8 = 1 j = (0 + S[1]) mod 8 = 3 Swap(S[1], S[3]) S = [2 4 7 3 0 1 6 5] t = (S[1] + S[3]) mod 8 = 7 k = S[7] = 5 Remember, P = [1 2 2 2] So our first 3 -bits of ciphertext is obtained by: k XOR P 5 XOR 1 = 101 XOR 001 = 100 = 4 19

C. 1. Symmetric Key Algorithms 2. Block Cipher 20 • Encrypts a group of plaintext symbols as one block. – It works on blocks of plaintext and produce blocks of ciphertext – The columnar transposition is an example of block ciphers • A block cipher might take a 128 -bit block of plaintext as input, and output.

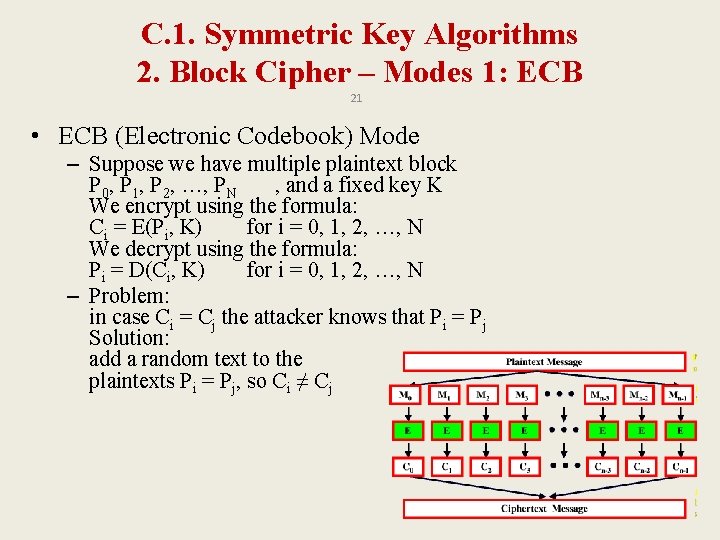
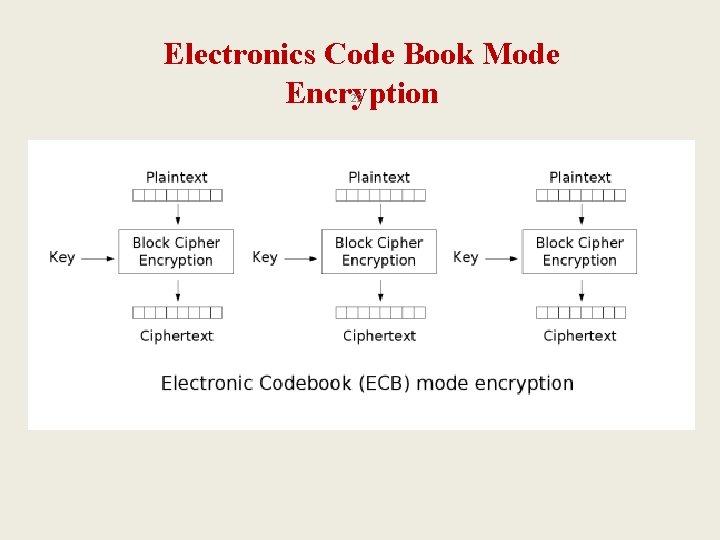
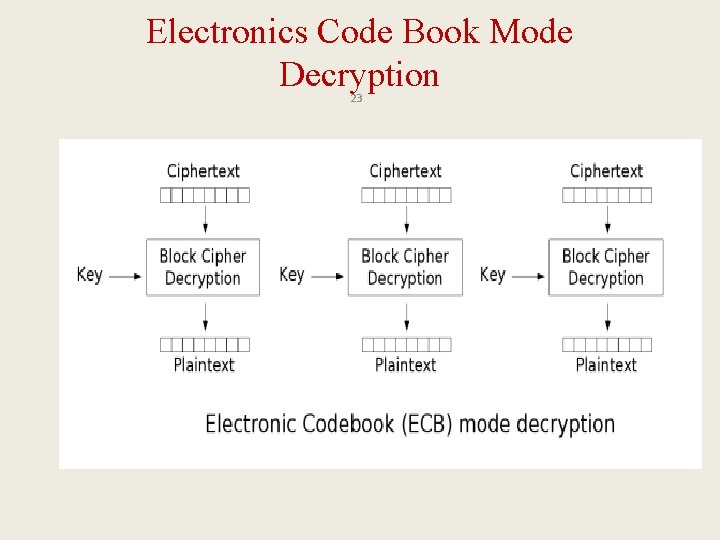
C. 1. Symmetric Key Algorithms 2. Block Cipher – Modes 1: ECB 21 • ECB (Electronic Codebook) Mode – Suppose we have multiple plaintext block P 0, P 1, P 2, …, PN , and a fixed key K We encrypt using the formula: Ci = E(Pi, K) for i = 0, 1, 2, …, N We decrypt using the formula: Pi = D(Ci, K) for i = 0, 1, 2, …, N – Problem: in case Ci = Cj the attacker knows that Pi = Pj Solution: add a random text to the plaintexts Pi = Pj, so Ci ≠ Cj

Electronics Code Book Mode Encryption 22

Electronics Code Book Mode Decryption 23

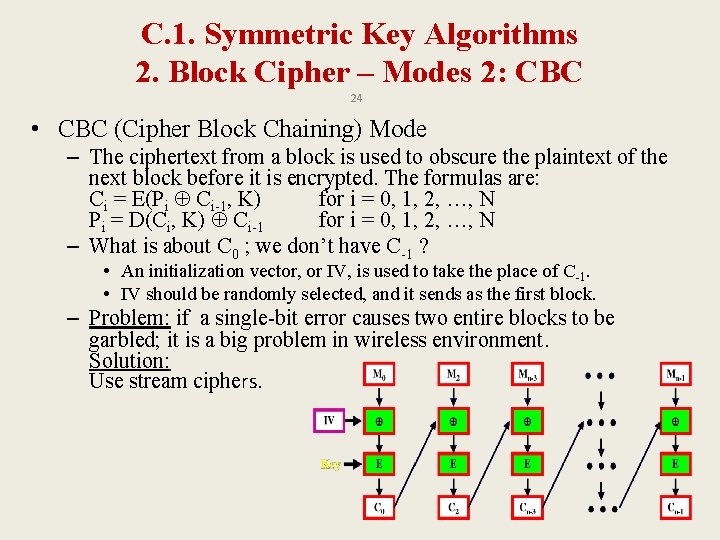
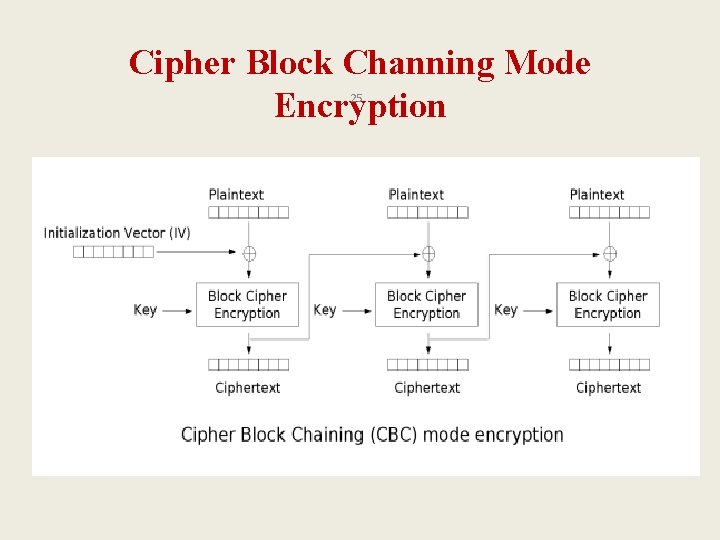
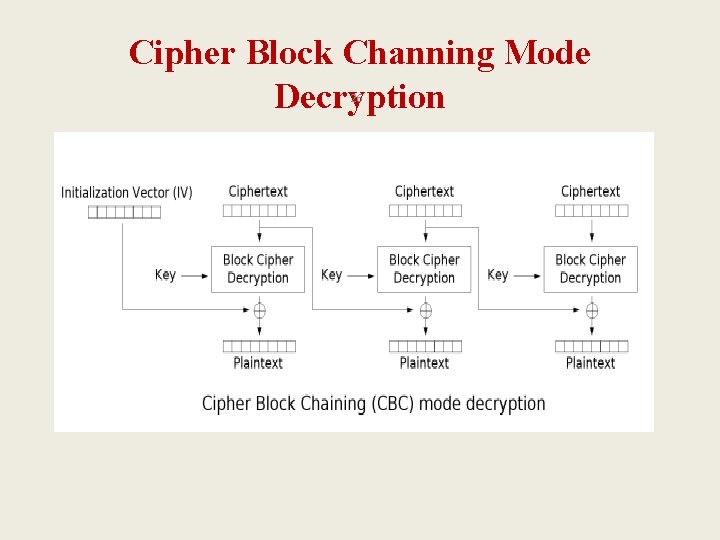
C. 1. Symmetric Key Algorithms 2. Block Cipher – Modes 2: CBC 24 • CBC (Cipher Block Chaining) Mode – The ciphertext from a block is used to obscure the plaintext of the next block before it is encrypted. The formulas are: Ci = E(Pi Ci-1, K) for i = 0, 1, 2, …, N Pi = D(Ci, K) Ci-1 for i = 0, 1, 2, …, N – What is about C 0 ; we don’t have C-1 ? • An initialization vector, or IV, is used to take the place of C-1. • IV should be randomly selected, and it sends as the first block. – Problem: if a single-bit error causes two entire blocks to be garbled; it is a big problem in wireless environment. Solution: Use stream ciphers.

Cipher Block Channing Mode Encryption 25

Cipher Block Channing Mode Decryption 26

C. 1. Symmetric Key Algorithms 2. Block Cipher – Advantages (Integrity) 27 • Block ciphers used for confidentiality and integrity. • A message authentication code, or MAC, uses a block cipher to ensure data integrity by encrypting the data un CBC mode, and use the final block only, called MAC. C 0 = E(P 0 IV, K), C 1 = E(P 1 C 0, K), … CN-1 = E(PN-1 CN-2, K) = MAC • The recipient repeats the process on the plaintext and re -calculate the MAC.

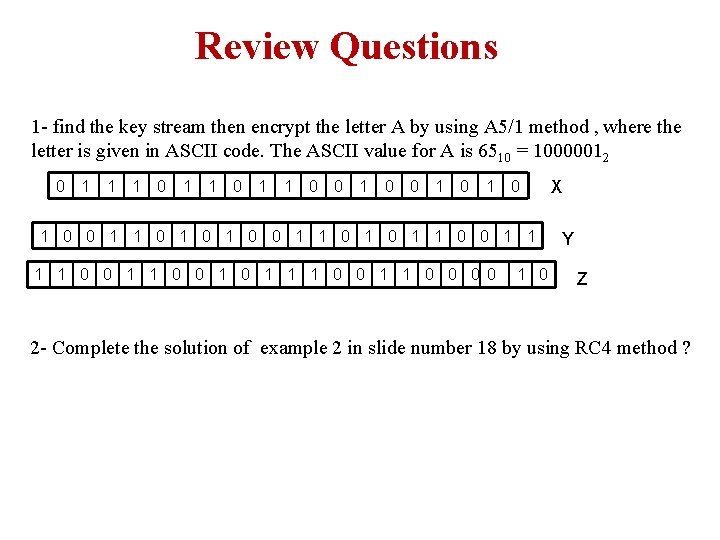
Review Questions 1 - find the key stream then encrypt the letter A by using A 5/1 method , where the letter is given in ASCII code. The ASCII value for A is 6510 = 10000012 0 1 1 1 0 0 1 0 1 0 1 0 0 1 1 0 0 1 1 1 0 0 0 0 1 0 X Y Z 2 - Complete the solution of example 2 in slide number 18 by using RC 4 method ?

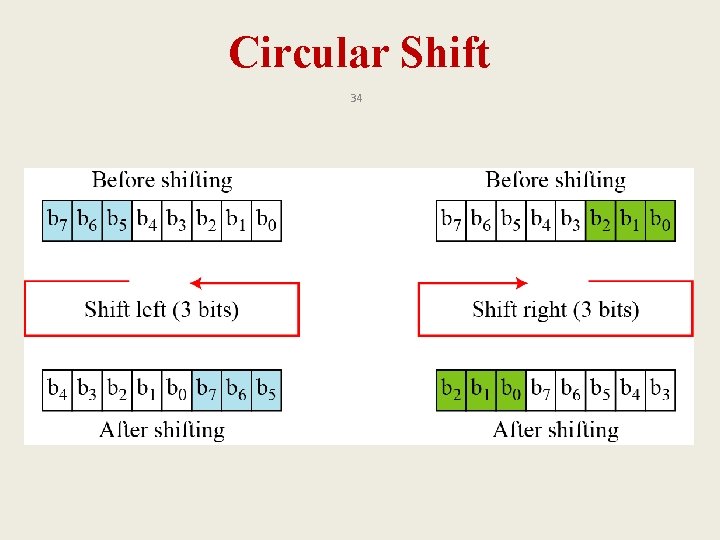
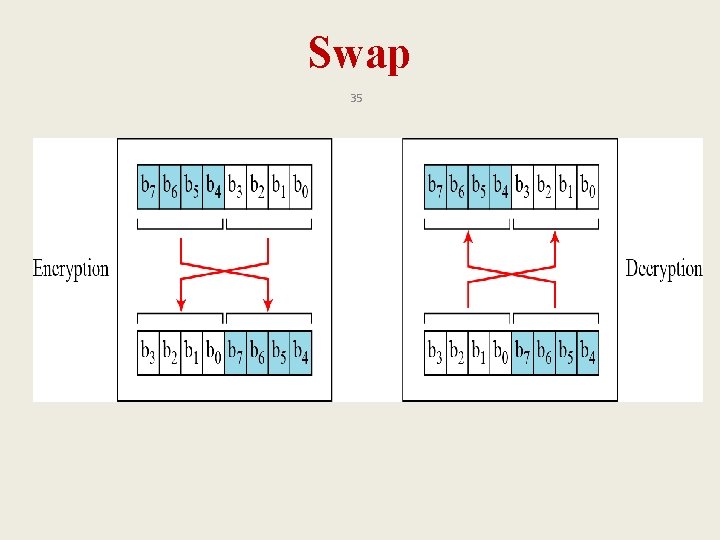
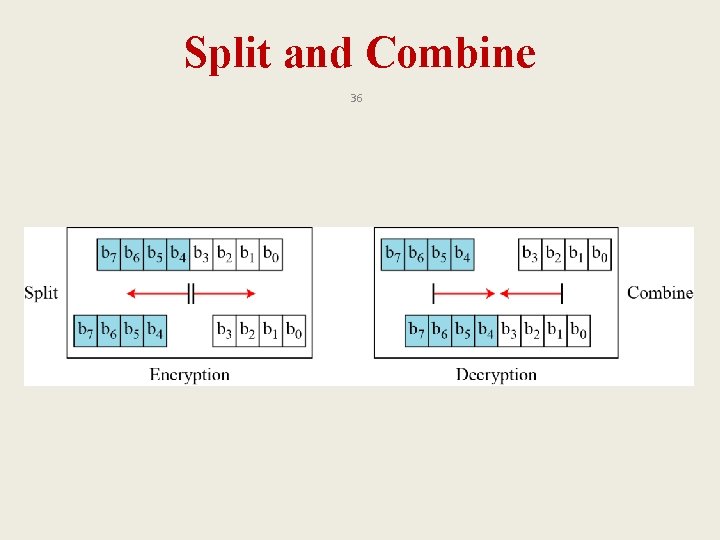
Components of a Modern Block Cipher 29 q P-Boxes q S-Boxes q Exclusive OR q Circular shift q Swap q Split and Combine

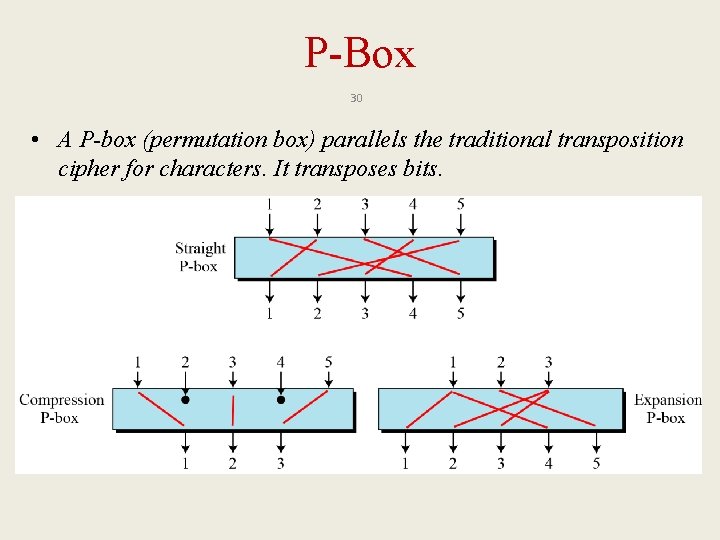
P-Box 30 • A P-box (permutation box) parallels the traditional transposition cipher for characters. It transposes bits.

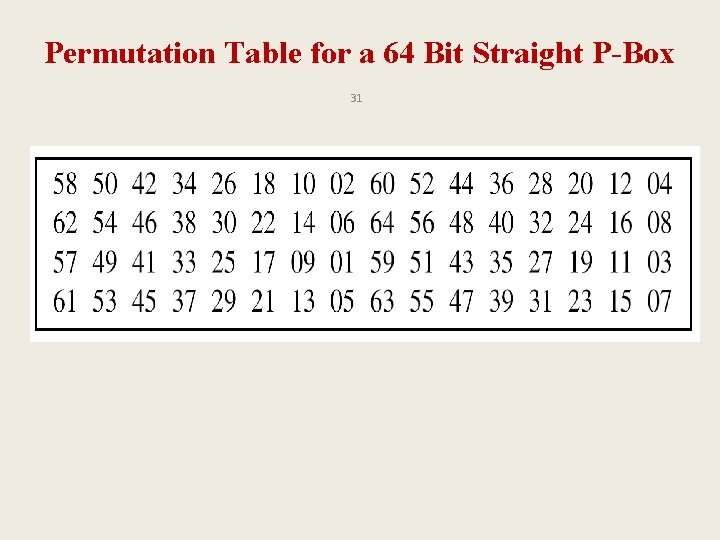
Permutation Table for a 64 Bit Straight P-Box 31

S-Box 32 • An S-box (substitution box) can be thought of as a miniature substitution cipher. • Like P-Box, S-Box can be straight, compression or expansion

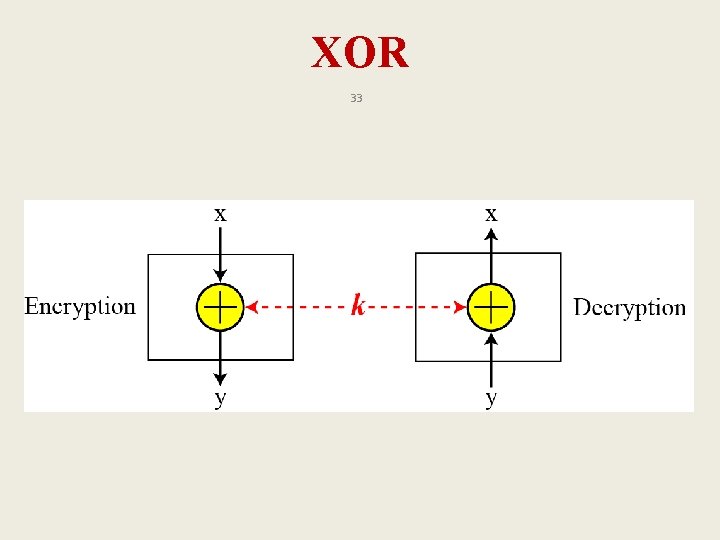
XOR 33

Circular Shift 34

Swap 35

Split and Combine 36

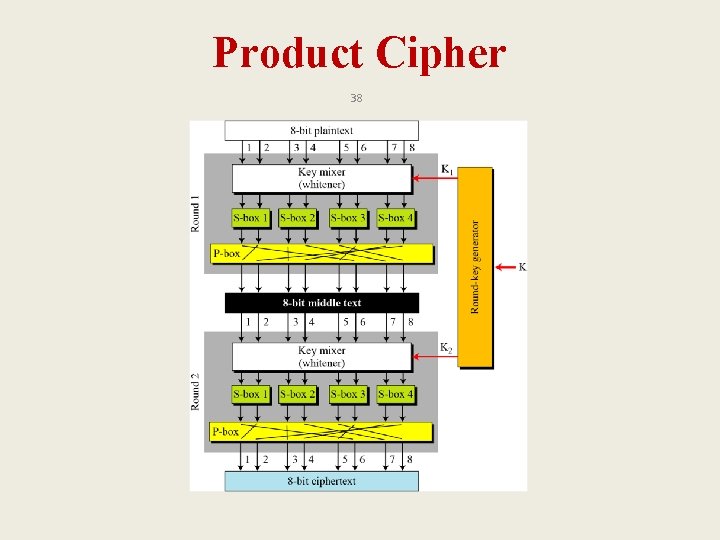
Product Cipher 37 • Shannon introduced the concept of a product cipher. A product cipher is a complex cipher combining substitution, permutation, and other components.

Product Cipher 38

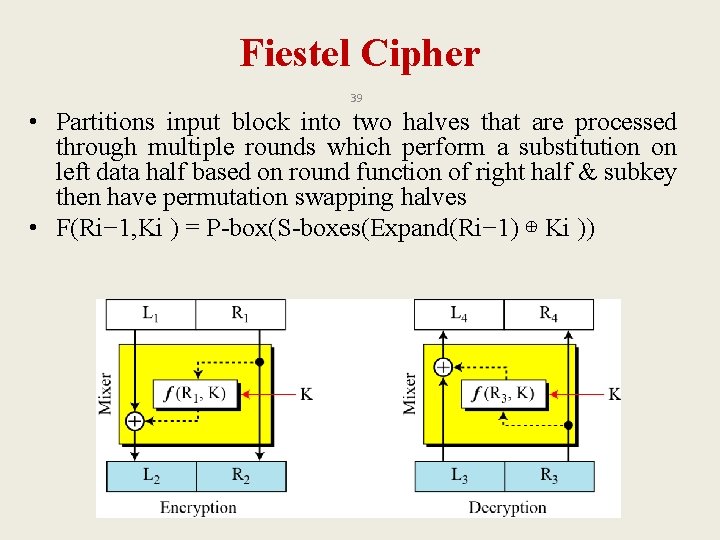
Fiestel Cipher 39 • Partitions input block into two halves that are processed through multiple rounds which perform a substitution on left data half based on round function of right half & subkey then have permutation swapping halves • F(Ri− 1, Ki ) = P-box(S-boxes(Expand(Ri− 1) ⊕ Ki ))

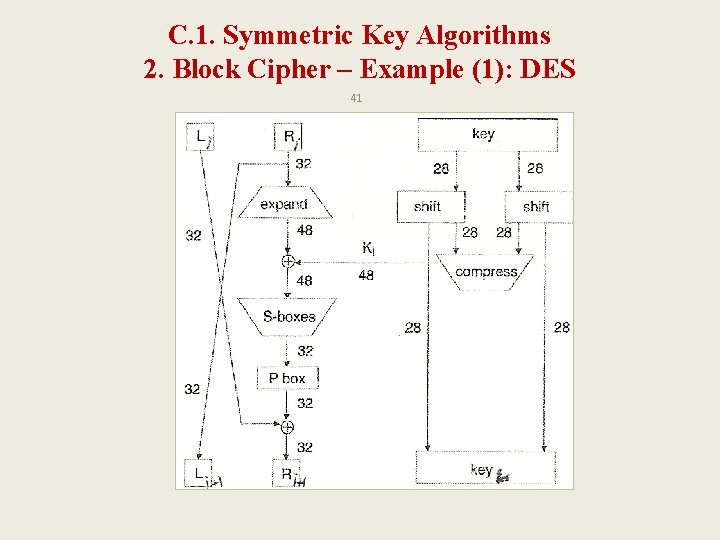
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): Data Encryption Standard (DES) 40 • most widely used block cipher in world • adopted in 1977 by NBS (now NIST) – as FIPS PUB 46 • • encrypts 64 -bit data using 56 -bit key had widespread use based upon Fiestel cipher has been considerable controversy over its security

C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 41

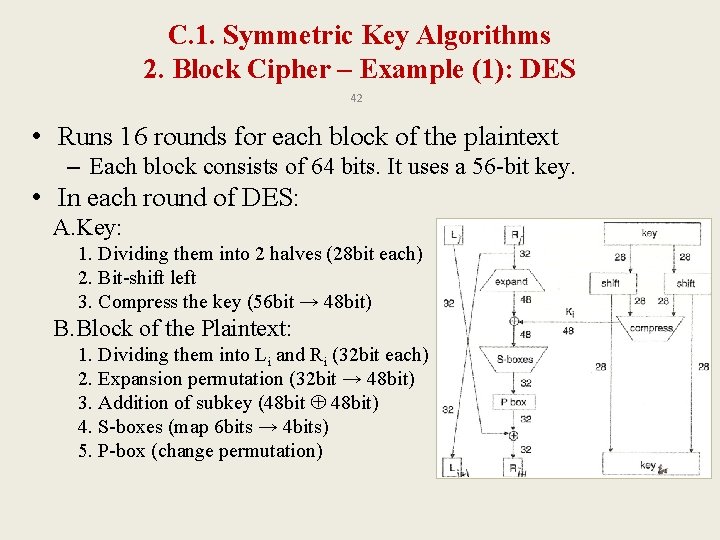
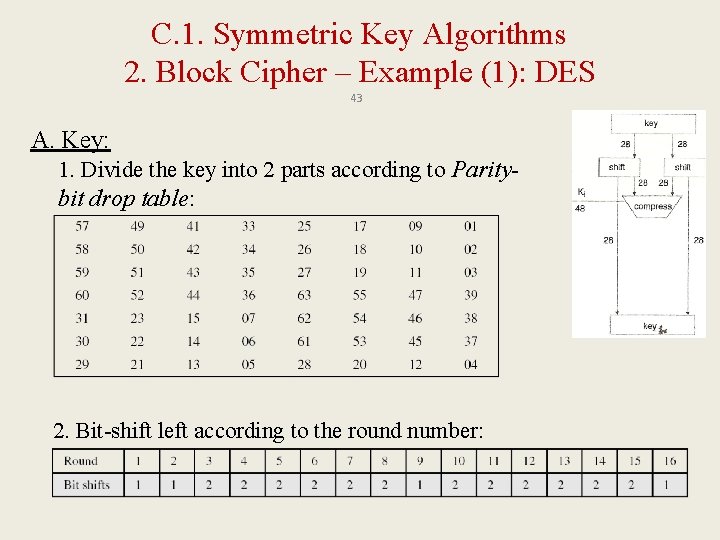
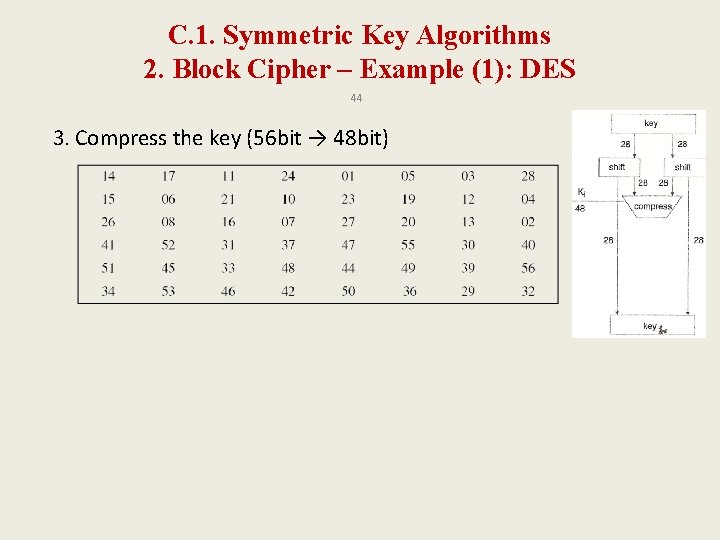
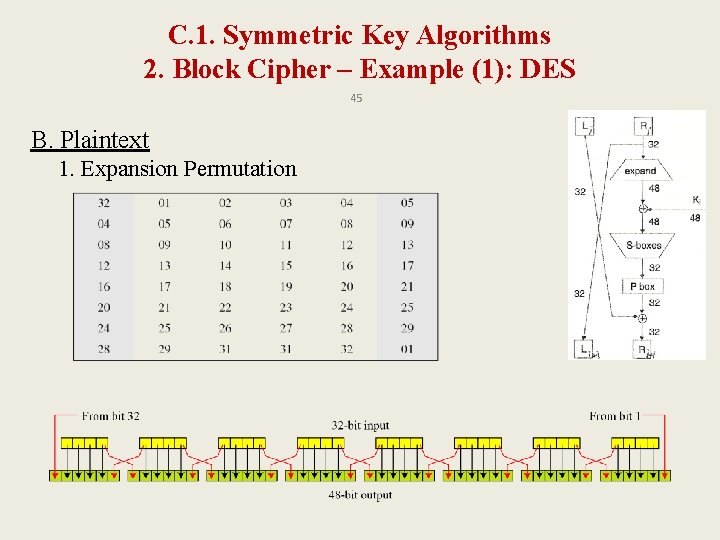
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 42 • Runs 16 rounds for each block of the plaintext – Each block consists of 64 bits. It uses a 56 -bit key. • In each round of DES: A. Key: 1. Dividing them into 2 halves (28 bit each) 2. Bit-shift left 3. Compress the key (56 bit → 48 bit) B. Block of the Plaintext: 1. Dividing them into Li and Ri (32 bit each) 2. Expansion permutation (32 bit → 48 bit) 3. Addition of subkey (48 bit 48 bit) 4. S-boxes (map 6 bits → 4 bits) 5. P-box (change permutation)

C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 43 A. Key: 1. Divide the key into 2 parts according to Paritybit drop table: 2. Bit-shift left according to the round number:

C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 44 3. Compress the key (56 bit → 48 bit)

C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 45 B. Plaintext 1. Expansion Permutation

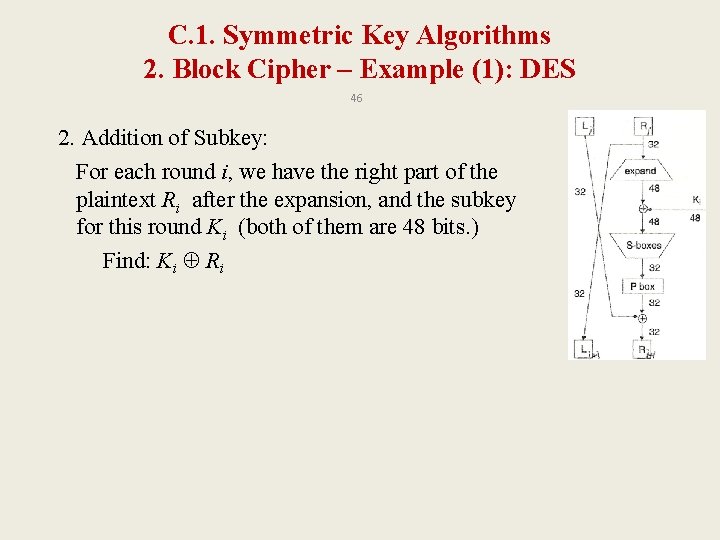
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 46 2. Addition of Subkey: For each round i, we have the right part of the plaintext Ri after the expansion, and the subkey for this round Ki (both of them are 48 bits. ) Find: Ki Ri

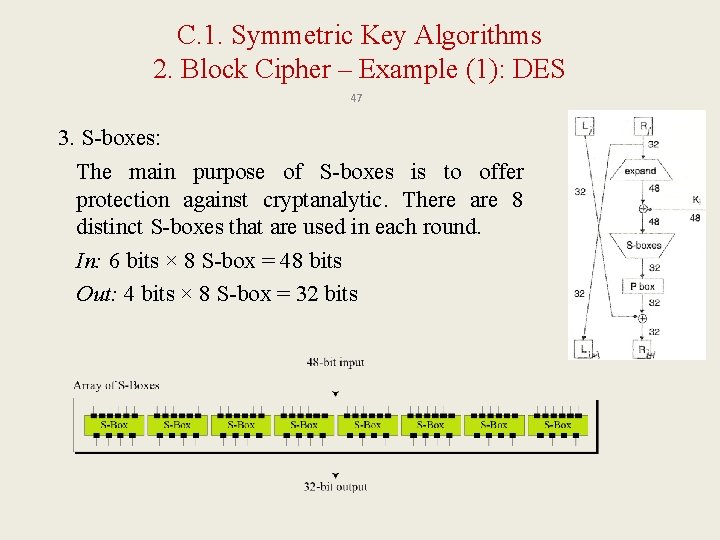
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 47 3. S-boxes: The main purpose of S-boxes is to offer protection against cryptanalytic. There are 8 distinct S-boxes that are used in each round. In: 6 bits × 8 S-box = 48 bits Out: 4 bits × 8 S-box = 32 bits

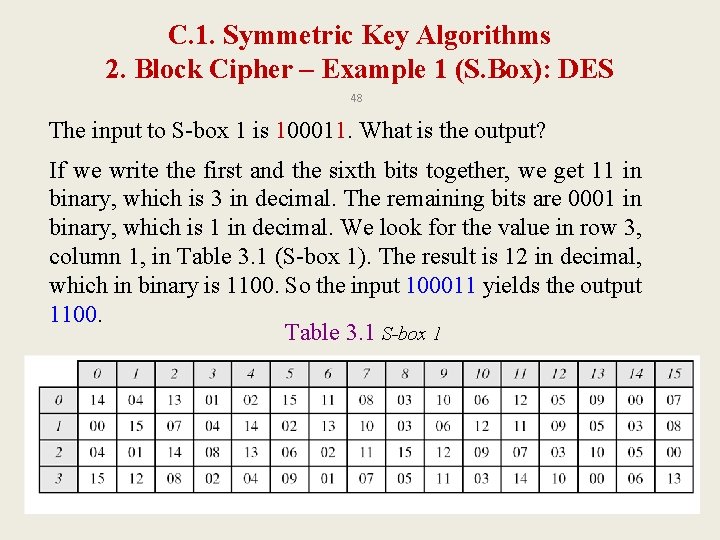
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example 1 (S. Box): DES 48 The input to S-box 1 is 100011. What is the output? If we write the first and the sixth bits together, we get 11 in binary, which is 3 in decimal. The remaining bits are 0001 in binary, which is 1 in decimal. We look for the value in row 3, column 1, in Table 3. 1 (S-box 1). The result is 12 in decimal, which in binary is 1100. So the input 100011 yields the output 1100. Table 3. 1 S-box 1

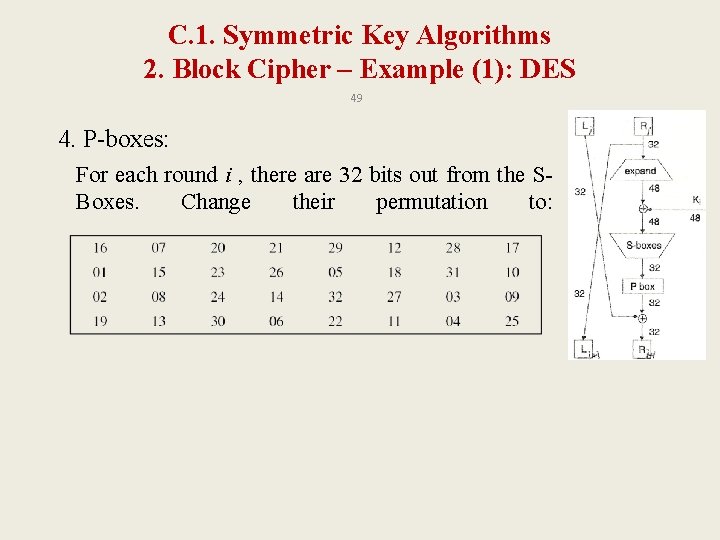
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 49 4. P-boxes: For each round i , there are 32 bits out from the SBoxes. Change their permutation to:

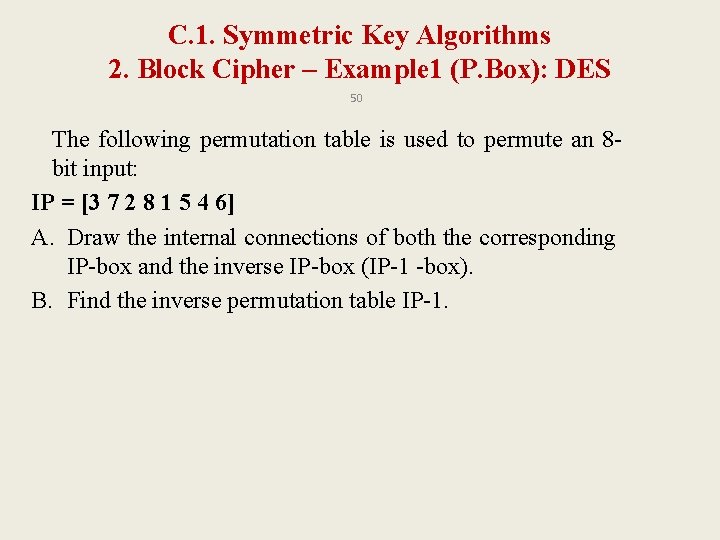
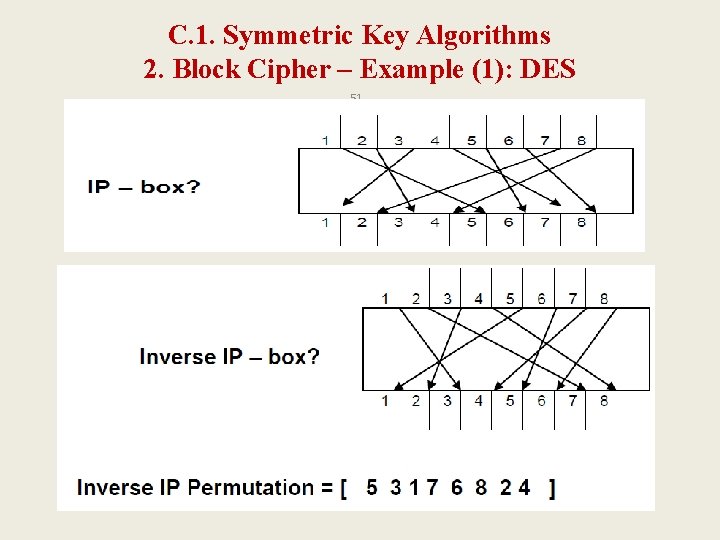
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example 1 (P. Box): DES 50 The following permutation table is used to permute an 8 bit input: IP = [3 7 2 8 1 5 4 6] A. Draw the internal connections of both the corresponding IP-box and the inverse IP-box (IP-1 -box). B. Find the inverse permutation table IP-1.

C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 51

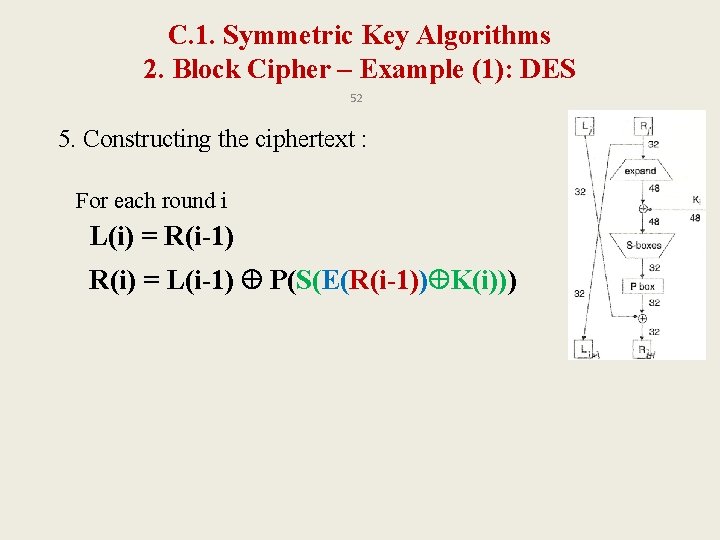
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (1): DES 52 5. Constructing the ciphertext : For each round i L(i) = R(i-1) R(i) = L(i-1) P(S(E(R(i-1)) K(i)))
![Example 2 DES Plain text p 0000 P 4 2431 IP 26314857 IP141357286 Example 2: DES Plain text = p= [0000] P 4= [2431] IP= [26314857]; IP-1=[41357286]](https://slidetodoc.com/presentation_image_h2/97ecd64841c19a6b1a9648befccd1559/image-52.jpg)
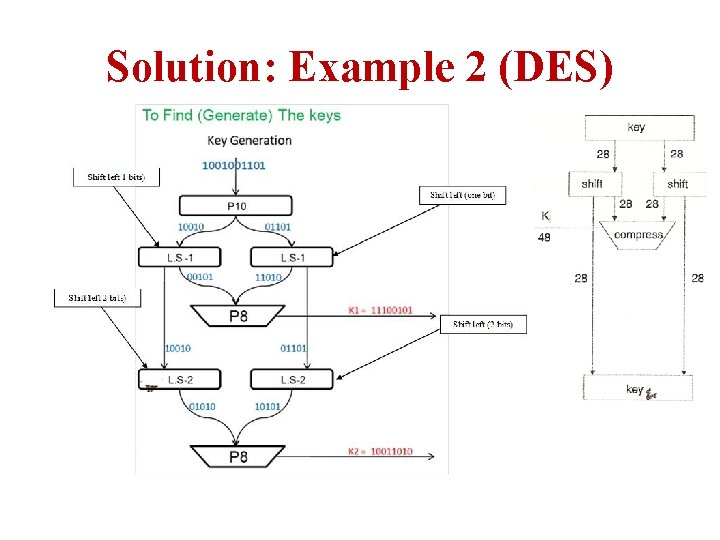
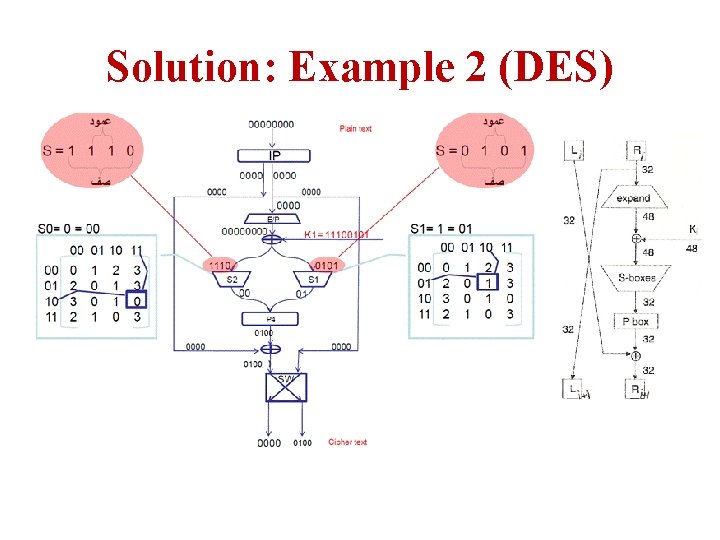
Example 2: DES Plain text = p= [0000] P 4= [2431] IP= [26314857]; IP-1=[41357286] E/P= [41232341] P 8=[637485109] S 0= S 1=

Solution: Example 2 (DES)

Solution: Example 2 (DES)

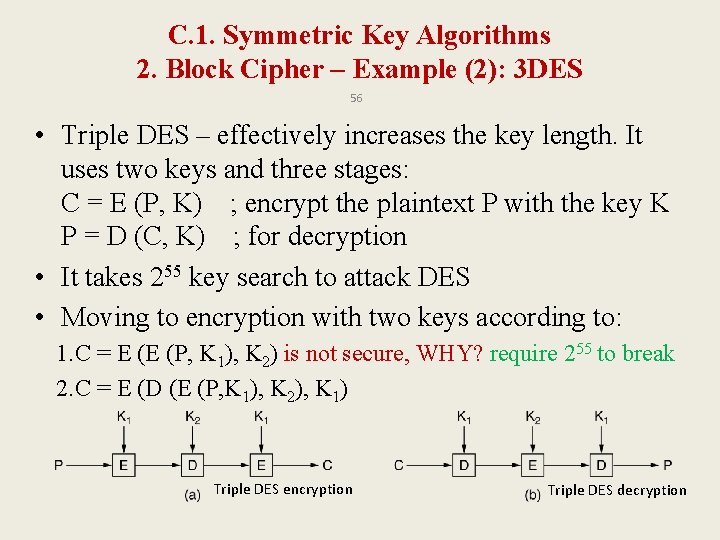
C. 1. Symmetric Key Algorithms 2. Block Cipher – Example (2): 3 DES 56 • Triple DES – effectively increases the key length. It uses two keys and three stages: C = E (P, K) ; encrypt the plaintext P with the key K P = D (C, K) ; for decryption • It takes 255 key search to attack DES • Moving to encryption with two keys according to: 1. C = E (E (P, K 1), K 2) is not secure, WHY? require 255 to break 2. C = E (D (E (P, K 1), K 2), K 1) Triple DES encryption Triple DES decryption

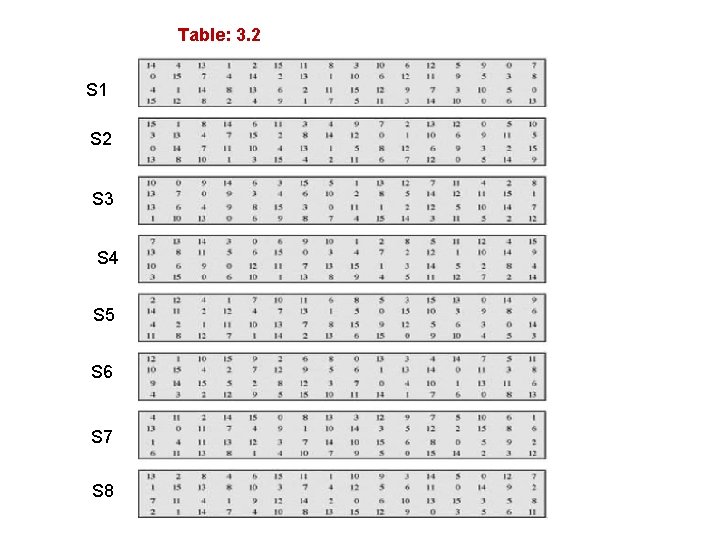
Review Questions 1 - The following input is applied to the eight S-boxes (S 1: S 8) of the DES 57 algorithm. The input is specified as eight 6 bits hexadecimal numbers. Find the corresponding 32 bits output and specify it as a hexadecimal number. See table 3. 2 3 E 19 0 F 24 1 D 2 A 39 2 B 3 E 111110 2. The following permutation table is used to permute an 8 -bit input: IP = [4 6 1 5 3 7 2 8] A. Draw the internal connections of both the corresponding IP-box and the inverse IP-box (IP-1 -box). B. Find the inverse permutation table IP-1. 3. complete the example 2(DES) by using k 2=10011010

Table: 3. 2 S 1 S 2 S 3 S 4 S 5 S 6 S 7 S 8

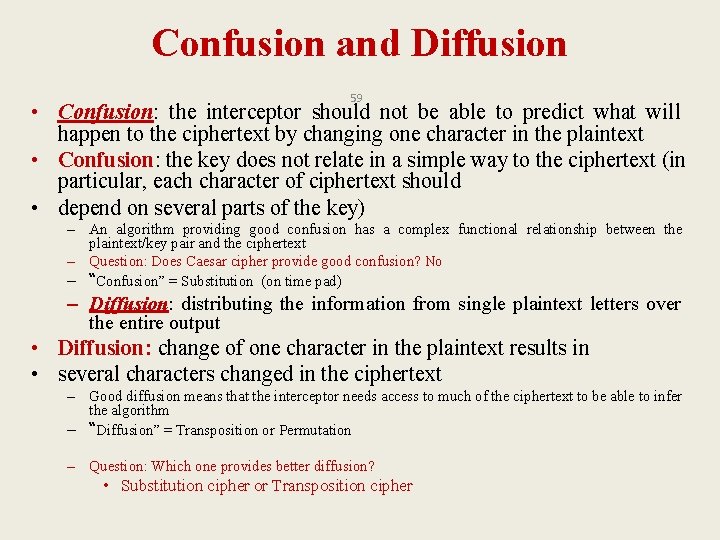
Confusion and Diffusion 59 • Confusion: the interceptor should not be able to predict what will happen to the ciphertext by changing one character in the plaintext • Confusion: the key does not relate in a simple way to the ciphertext (in particular, each character of ciphertext should • depend on several parts of the key) – An algorithm providing good confusion has a complex functional relationship between the plaintext/key pair and the ciphertext – Question: Does Caesar cipher provide good confusion? No – “Confusion” = Substitution (on time pad) – Diffusion: distributing the information from single plaintext letters over the entire output • Diffusion: change of one character in the plaintext results in • several characters changed in the ciphertext – Good diffusion means that the interceptor needs access to much of the ciphertext to be able to infer the algorithm – “Diffusion” = Transposition or Permutation – Question: Which one provides better diffusion? • Substitution cipher or Transposition cipher

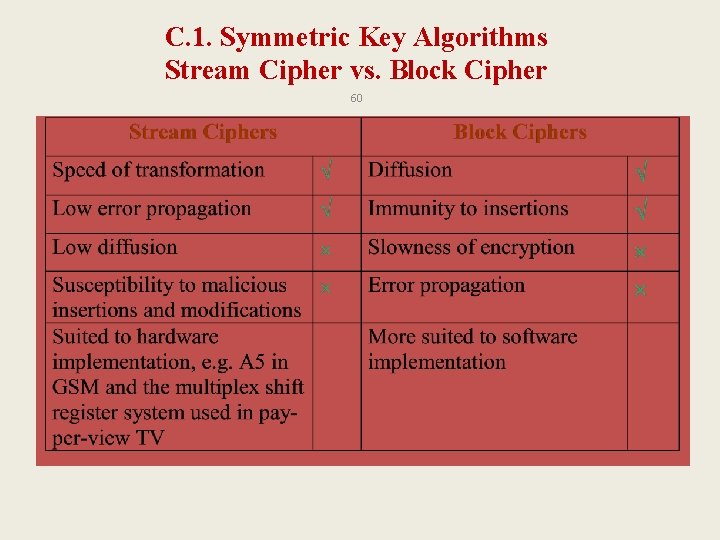
C. 1. Symmetric Key Algorithms Stream Cipher vs. Block Cipher 60

C. 1. Symmetric Key Algorithms Other Examples 61

Conclusion 62 • Modern symmetric ciphers come in two variants: block ciphers and stream ciphers. • The mostly used block cipher is used to be DES. • To use a block cipher one needs to also specify a mode of operation: – The simplest mode is ECB mode, which has problems associated with it: • same plaintext will always generate same ciphertext; • suffers from possible insertion/deletion attacks. – Hence it is common to use a more advanced mode such as CBC mode.

Conclusion 63 • Symmetrical cryptography is reasonably secure, more efficient, and more suitable for encryption of large messages - provide message confidentiality. • But it has key exchange problem and does not support non-repudiation.

Terms and Concepts • • 64 Symmetric & Asymmetric Block & Stream Cipher key distribution key stream bit / key stream byte Initialization Vector Confusion & Diffusion MAC