CPIS 371 Computer Network 1 CISCO SYSTEMS CCNA










- Slides: 82

CPIS 371 Computer Network 1 CISCO SYSTEMS CCNA VERSION 3 SEMESTER 4 MODULE 6 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Outlines 2 6. 1 Workstations and Servers 6. 1. 1 Workstations 6. 1. 2 Servers 6. 1. 3 Client-server relationship 6. 1. 4 Introduction to NOS 6. 1. 5 Microsoft NT, 2000, and. NET 6. 1. 6 UNIX, Sun, HP, and LINUX 6. 1. 7 Apple 6. 1. 8 Concept of service on servers 6. 2 Network Management 6. 2. 1 Introduction to network management 6. 2. 2 OSI and network management model 6. 2. 3 SNMP and CMIP standards 6. 2. 4 SNMP operation 6. 2. 5 Structure of management information and MIBs 6. 2. 6 SNMP protocol 6. 2. 7 Configuring SNMP 6. 2. 8 RMON 6. 2. 9 Syslog Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Introduction to Network Administration 3 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

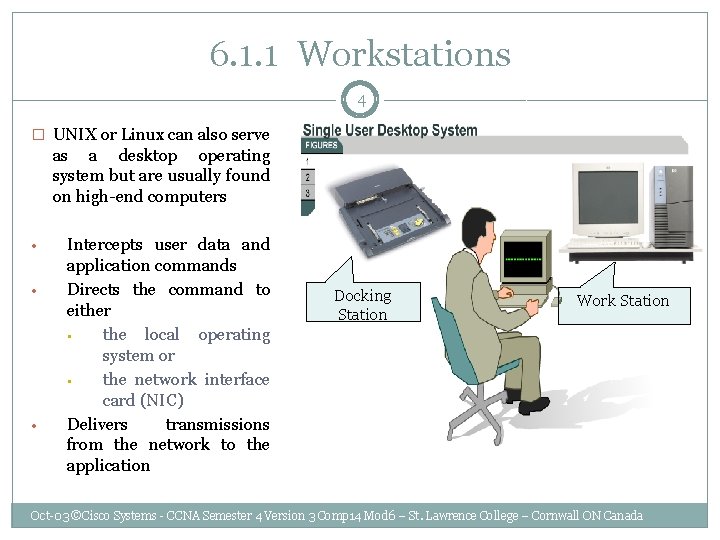
6. 1. 1 Workstations 4 � UNIX or Linux can also serve as a desktop operating system but are usually found on high-end computers • • • Intercepts user data and application commands Directs the command to either • the local operating system or • the network interface card (NIC) Delivers transmissions from the network to the application Docking Station Work Station Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

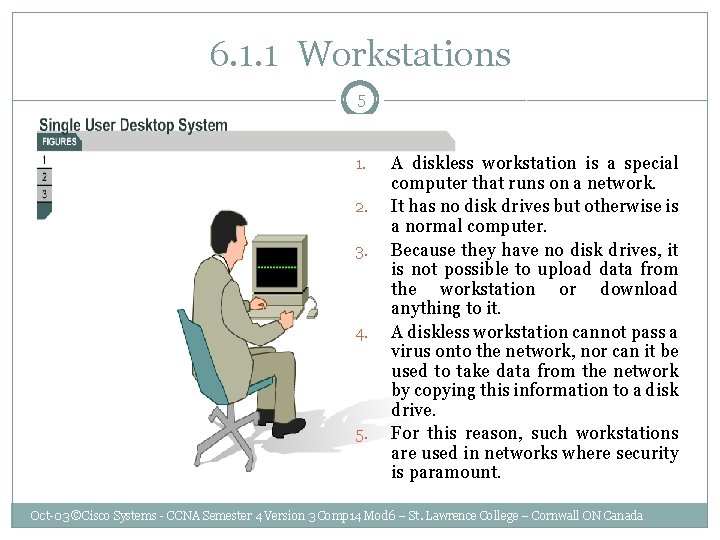
6. 1. 1 Workstations 5 1. 2. 3. 4. 5. A diskless workstation is a special computer that runs on a network. It has no disk drives but otherwise is a normal computer. Because they have no disk drives, it is not possible to upload data from the workstation or download anything to it. A diskless workstation cannot pass a virus onto the network, nor can it be used to take data from the network by copying this information to a disk drive. For this reason, such workstations are used in networks where security is paramount. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

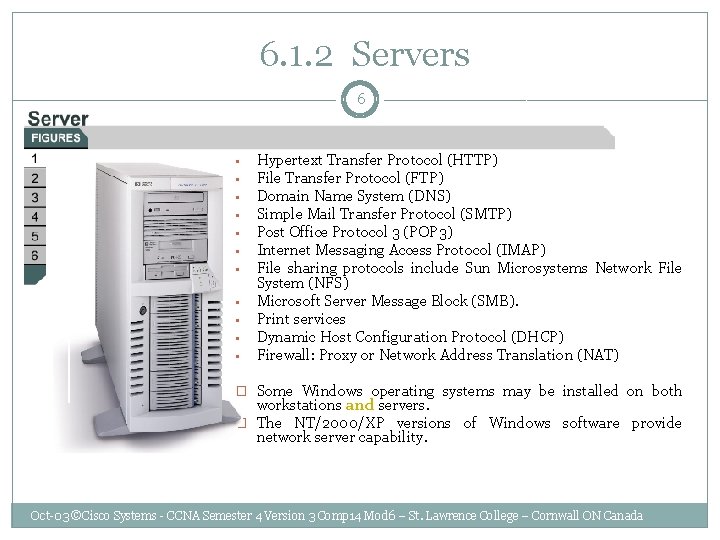
6. 1. 2 Servers 6 • • • Hypertext Transfer Protocol (HTTP) File Transfer Protocol (FTP) Domain Name System (DNS) Simple Mail Transfer Protocol (SMTP) Post Office Protocol 3 (POP 3) Internet Messaging Access Protocol (IMAP) File sharing protocols include Sun Microsystems Network File System (NFS) Microsoft Server Message Block (SMB). Print services Dynamic Host Configuration Protocol (DHCP) Firewall: Proxy or Network Address Translation (NAT) � Some Windows operating systems may be installed on both workstations and servers. � The NT/2000/XP versions of Windows software provide network server capability. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 2 Servers 7 • Servers are typically larger systems than workstations • Extra memory for multiple tasks that are active or resident in memory at the same time. • Extra disk space for shared files and as an extension to the internal memory on the system. • Extra expansion slots to connect shared devices, such as printers and multiple network interfaces. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 2 Servers 8 • • • Multiprocessor systems are capable of executing multiple tasks in parallel by assigning each task to a different processor. Must function effectively under heavy loads. Redundancy is a feature of fault tolerant systems that are designed to survive failures and can be repaired without interruption while the systems are up and running. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 2 Servers 9 One Very Busy Spigot Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

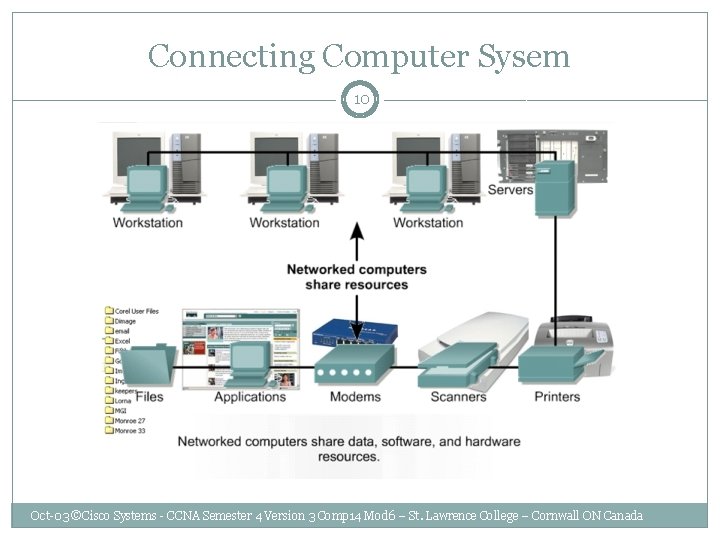
Connecting Computer Sysem 10 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

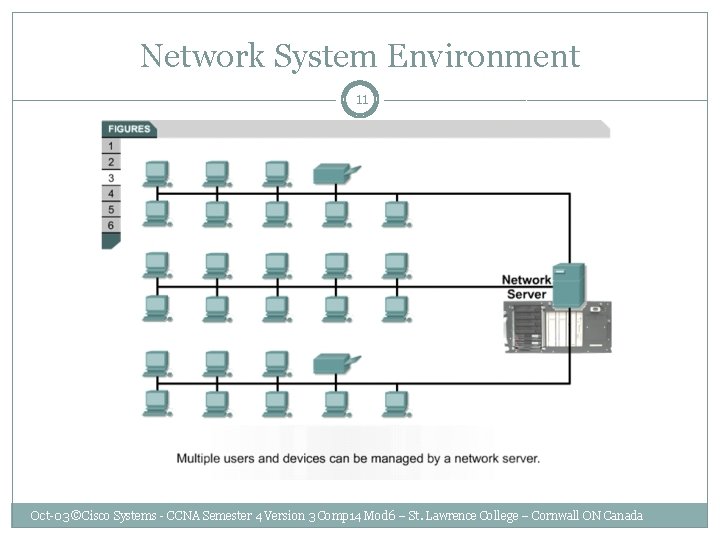
Network System Environment 11 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

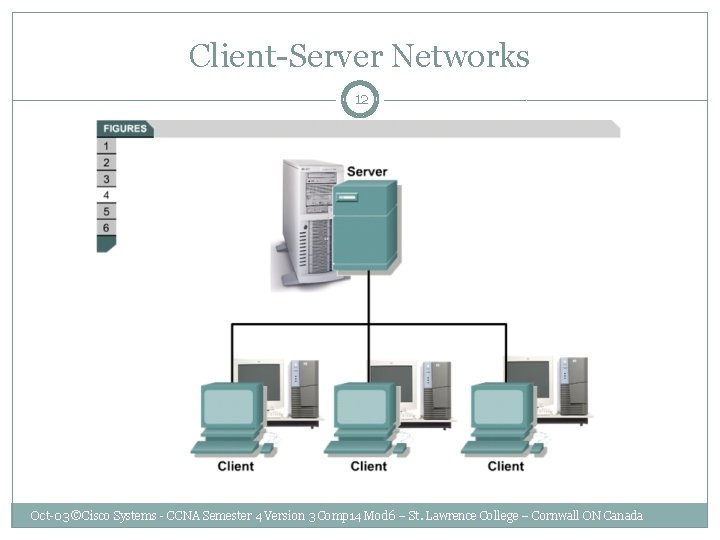
Client-Server Networks 12 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

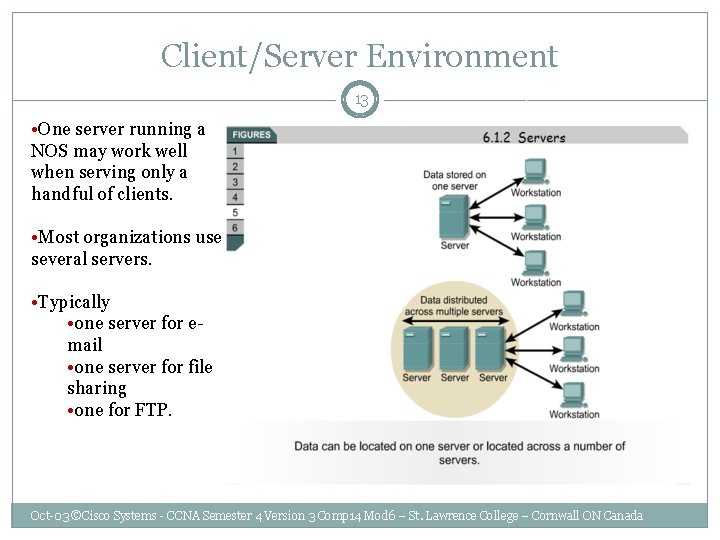
Client/Server Environment 13 • One server running a NOS may work well when serving only a handful of clients. • Most organizations use several servers. • Typically • one server for email • one server for file sharing • one for FTP. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

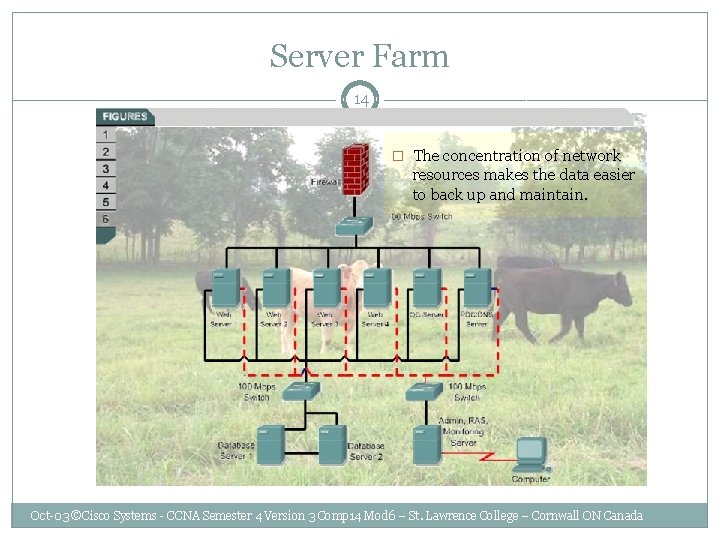
Server Farm 14 � The concentration of network resources makes the data easier to back up and maintain. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

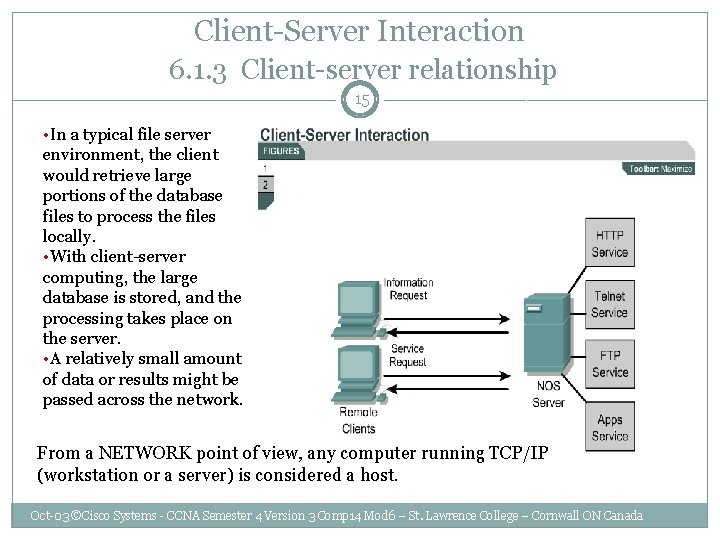
Client-Server Interaction 6. 1. 3 Client-server relationship 15 • In a typical file server environment, the client would retrieve large portions of the database files to process the files locally. • With client-server computing, the large database is stored, and the processing takes place on the server. • A relatively small amount of data or results might be passed across the network. From a NETWORK point of view, any computer running TCP/IP (workstation or a server) is considered a host. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

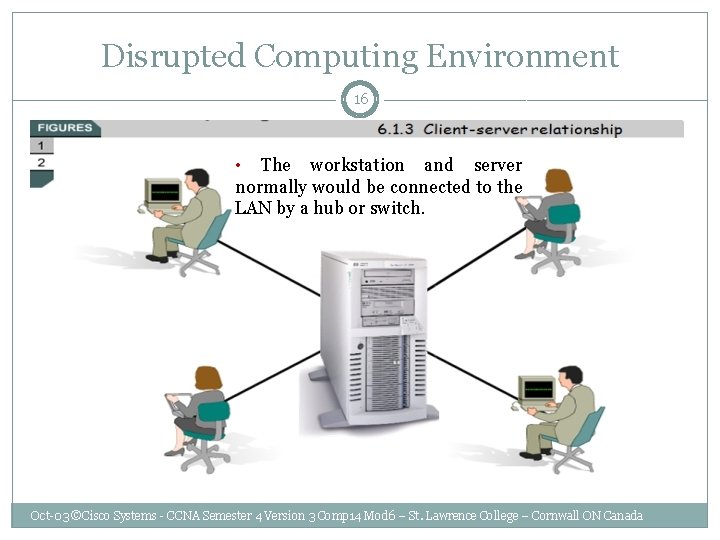
Disrupted Computing Environment 16 • The workstation and server normally would be connected to the LAN by a hub or switch. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

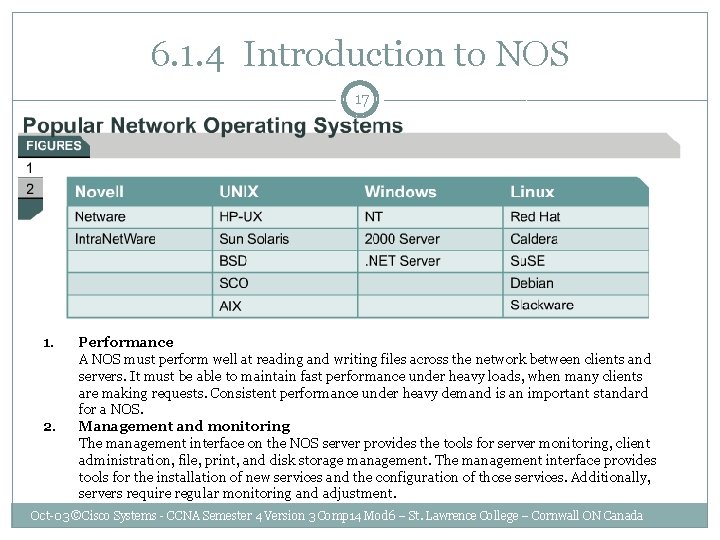
6. 1. 4 Introduction to NOS 17 1. 2. Performance A NOS must perform well at reading and writing files across the network between clients and servers. It must be able to maintain fast performance under heavy loads, when many clients are making requests. Consistent performance under heavy demand is an important standard for a NOS. Management and monitoring The management interface on the NOS server provides the tools for server monitoring, client administration, file, print, and disk storage management. The management interface provides tools for the installation of new services and the configuration of those services. Additionally, servers require regular monitoring and adjustment. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

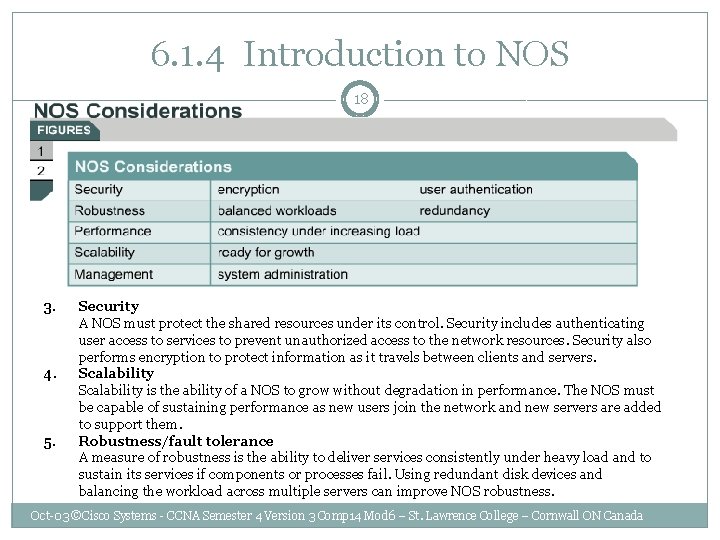
6. 1. 4 Introduction to NOS 18 3. 4. 5. Security A NOS must protect the shared resources under its control. Security includes authenticating user access to services to prevent unauthorized access to the network resources. Security also performs encryption to protect information as it travels between clients and servers. Scalability is the ability of a NOS to grow without degradation in performance. The NOS must be capable of sustaining performance as new users join the network and new servers are added to support them. Robustness/fault tolerance A measure of robustness is the ability to deliver services consistently under heavy load and to sustain its services if components or processes fail. Using redundant disk devices and balancing the workload across multiple servers can improve NOS robustness. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 5 Microsoft NT, 2000, and. NET 19 Windows 2000 Professional is not designed to be a full NOS. It does not provide a domain controller, DNS server, DHCP server, or render any of the services that can be deployed with Windows 2000 Server. • • Windows 2000 Server adds the normal server-specific functions. It provides integrated connectivity with Novell Net. Ware, UNIX, and Apple. Talk systems and can also be configured as a communications server. Windows. NET Server is built on the Windows 2000 Server kernel to run enterprise-level web and FTP sites. Equivalent to Linux and UNIX server operating systems. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

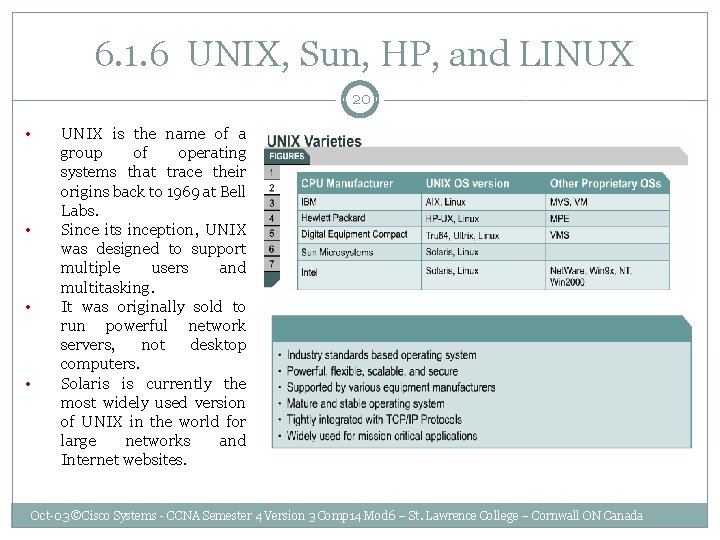
6. 1. 6 UNIX, Sun, HP, and LINUX 20 • • UNIX is the name of a group of operating systems that trace their origins back to 1969 at Bell Labs. Since its inception, UNIX was designed to support multiple users and multitasking. It was originally sold to run powerful network servers, not desktop computers. Solaris is currently the most widely used version of UNIX in the world for large networks and Internet websites. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 6 UNIX, Sun, HP, and LINUX 21 • • • Linux is one of the most powerful and reliable operating systems in the world today. Linux has already made inroads as a platform for power users and in the enterprise server arena. Linux is less often deployed as a corporate desktop operating system. Recent distributions of Linux have networking components built in for connecting to a LAN, establishing a dialup connection to the Internet, or other remote network. TCP/IP is integrated into the Linux kernel instead of being implemented as a separate subsystem. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 6 UNIX, Sun, HP, and LINUX 22 In 1991, a Finnish student named Linus Torvalds began work on an operating system for an Intel 80386 -based computer. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 6 UNIX, Sun, HP, and LINUX 23 Torvald's work led to a world-wide collaborative effort to develop Linux, an open source operating system that looks and feels like UNIX. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 6 UNIX, Sun, HP, and LINUX 24 Some advantages of Linux as a desktop operating system and network client: 1. It is a true 32 -bit operating system. 2. It supports preemptive multitasking and virtual memory. 3. The code is open source and thus available for anyone to enhance and improve. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 1. 7 Apple 25 • • • Mac OS X provides a new feature that allows for Apple. Talk and Windows connectivity. The Mac OS X core operating system is UNIX-based. The Mac GUI resembles a cross between Windows XP and Linux X-windows GUI. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

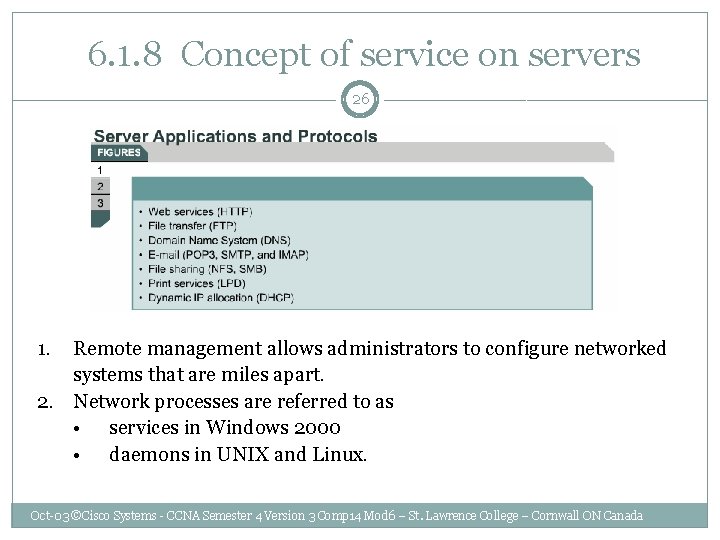
6. 1. 8 Concept of service on servers 26 1. Remote management allows administrators to configure networked systems that are miles apart. 2. Network processes are referred to as • services in Windows 2000 • daemons in UNIX and Linux. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

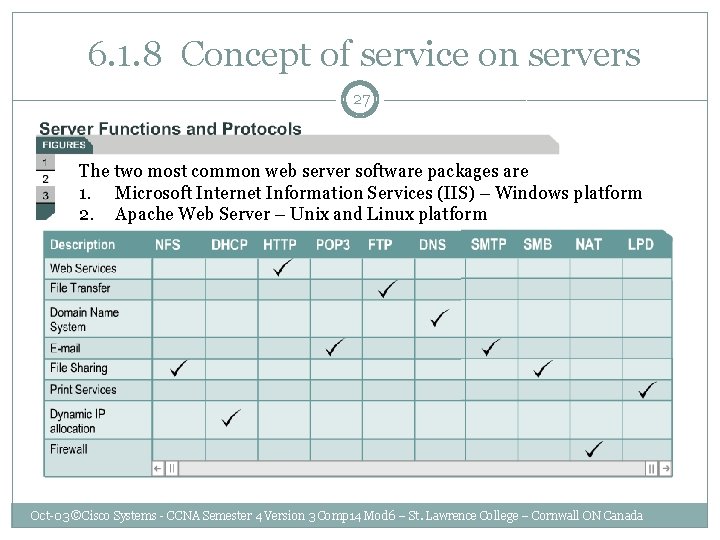
6. 1. 8 Concept of service on servers 27 The two most common web server software packages are 1. Microsoft Internet Information Services (IIS) – Windows platform 2. Apache Web Server – Unix and Linux platform Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

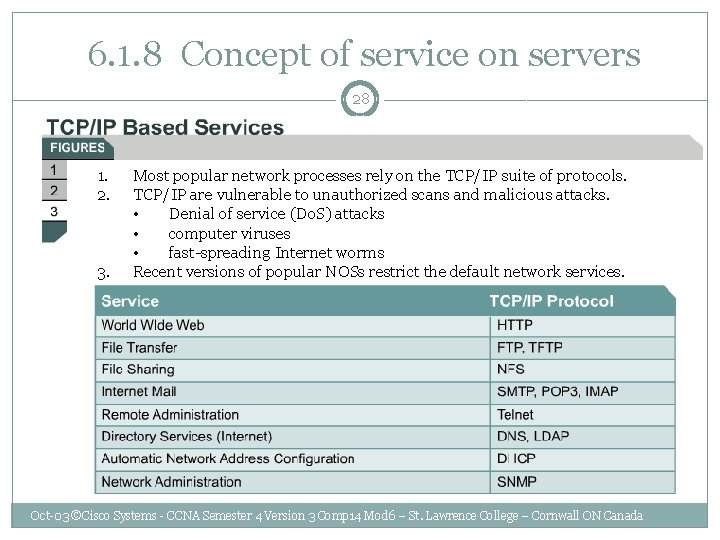
6. 1. 8 Concept of service on servers 28 1. 2. 3. Most popular network processes rely on the TCP/IP suite of protocols. TCP/IP are vulnerable to unauthorized scans and malicious attacks. • Denial of service (Do. S) attacks • computer viruses • fast-spreading Internet worms Recent versions of popular NOSs restrict the default network services. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Outlines 29 6. 1 Workstations and Servers 6. 1. 1 Workstations 6. 1. 2 Servers 6. 1. 3 Client-server relationship 6. 1. 4 Introduction to NOS 6. 1. 5 Microsoft NT, 2000, and. NET 6. 1. 6 UNIX, Sun, HP, and LINUX 6. 1. 7 Apple 6. 1. 8 Concept of service on servers 6. 2 Network Management 6. 2. 1 Introduction to network management 6. 2. 2 OSI and network management model 6. 2. 3 SNMP and CMIP standards 6. 2. 4 SNMP operation 6. 2. 5 Structure of management information and MIBs 6. 2. 6 SNMP protocol 6. 2. 7 Configuring SNMP 6. 2. 8 RMON 6. 2. 9 Syslog Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 1 Introduction to network management 30 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 1 Introduction to network management 31 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 1 Introduction to network management 32 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

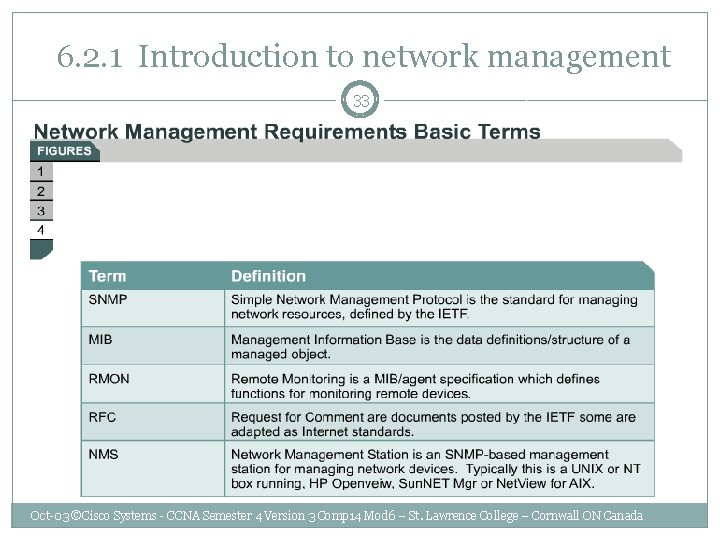
6. 2. 1 Introduction to network management 33 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

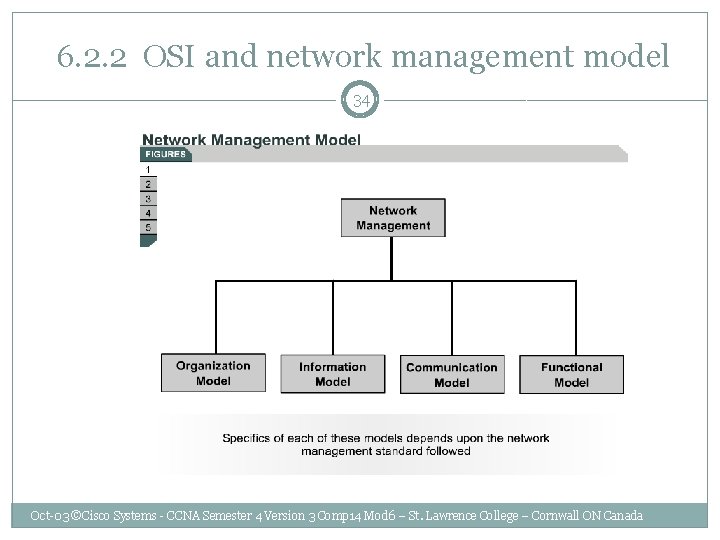
6. 2. 2 OSI and network management model 34 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

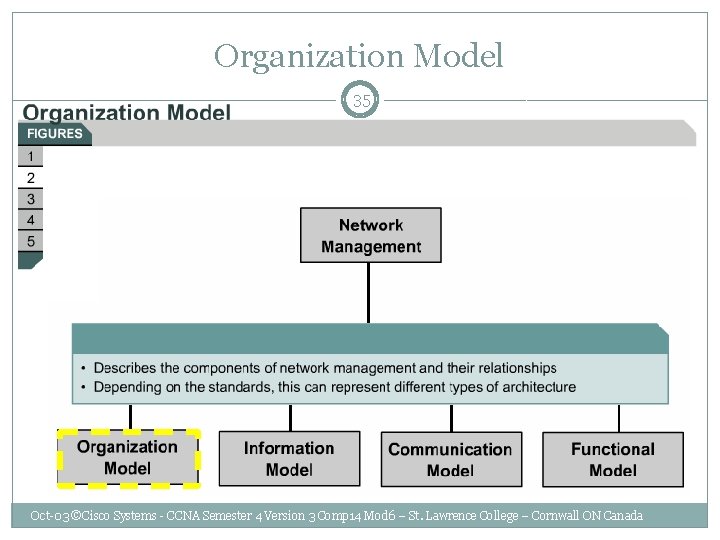
Organization Model 35 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

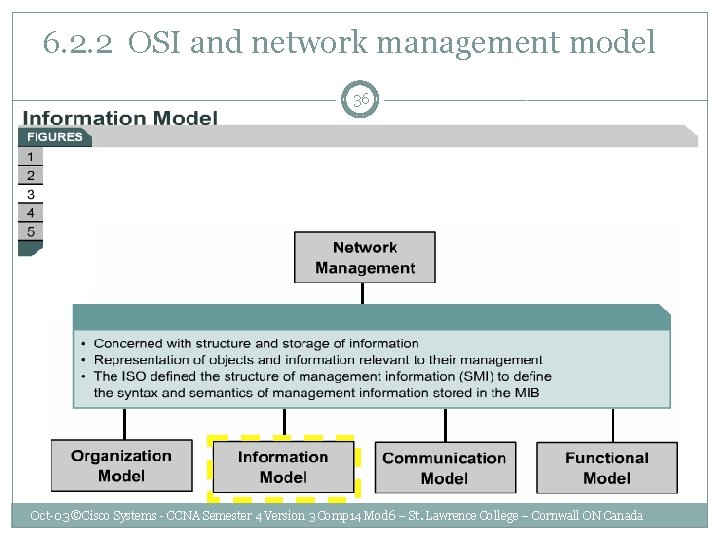
6. 2. 2 OSI and network management model 36 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

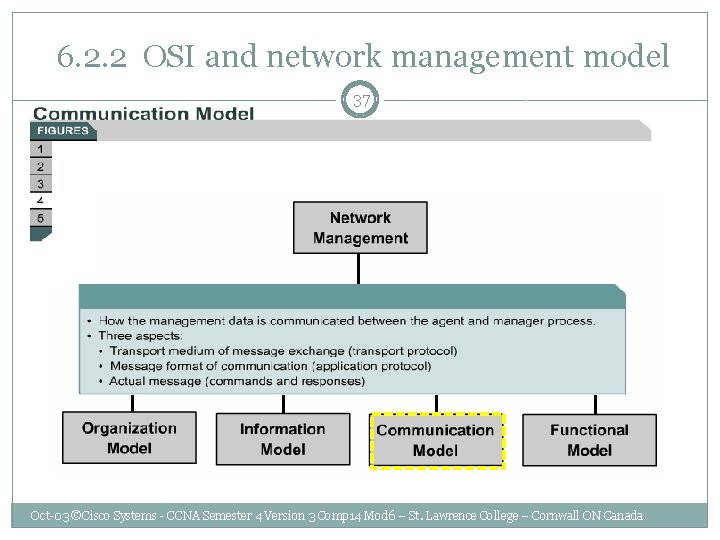
6. 2. 2 OSI and network management model 37 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

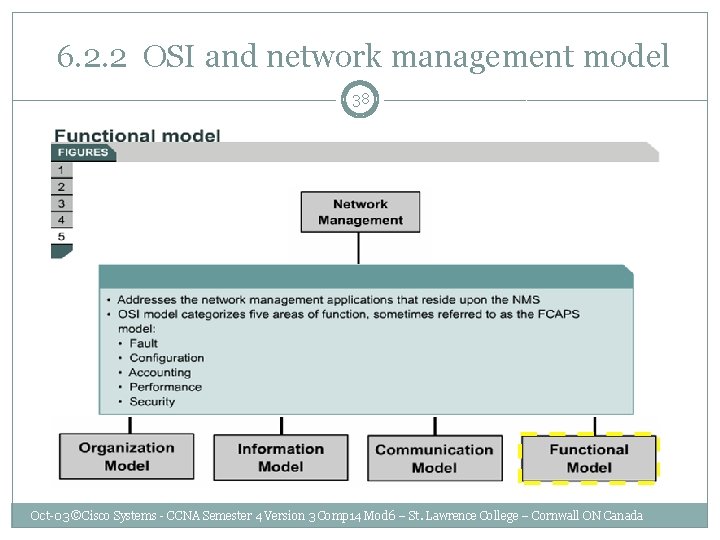
6. 2. 2 OSI and network management model 38 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

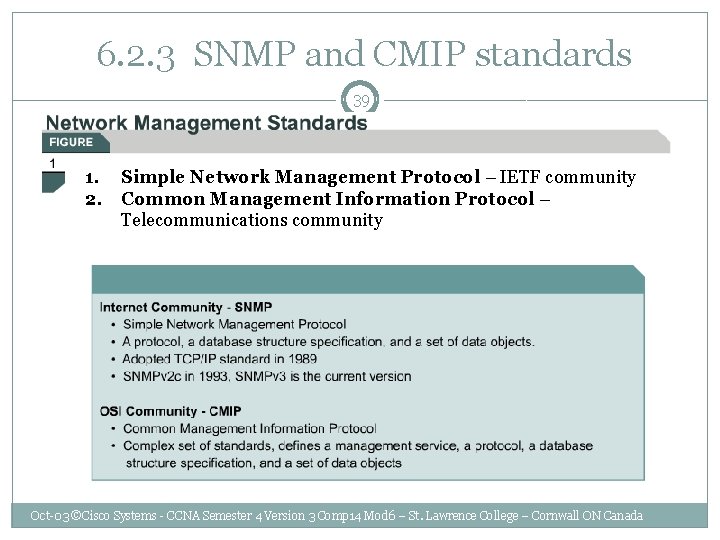
6. 2. 3 SNMP and CMIP standards 39 1. Simple Network Management Protocol – IETF community 2. Common Management Information Protocol – Telecommunications community Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

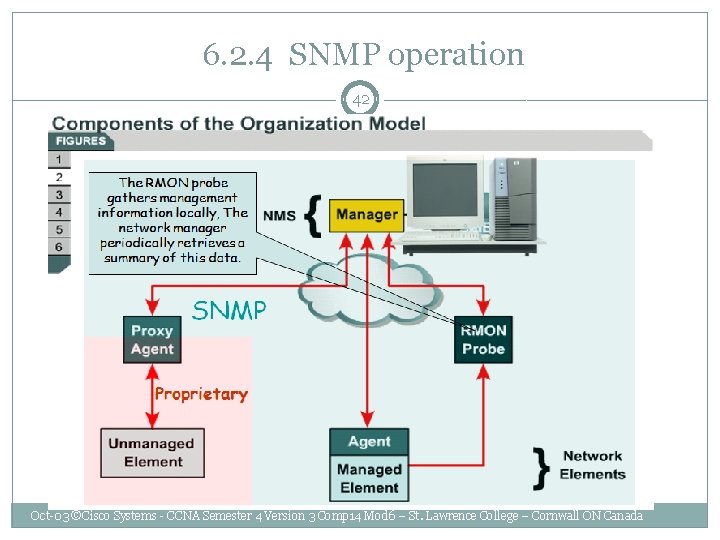
6. 2. 4 SNMP operation 40 Simple Network Management Protocol (SNMP) - application layer protocol that facilitates the exchange of management information between network devices. SNMP uses UDP over ports 161 and 162. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

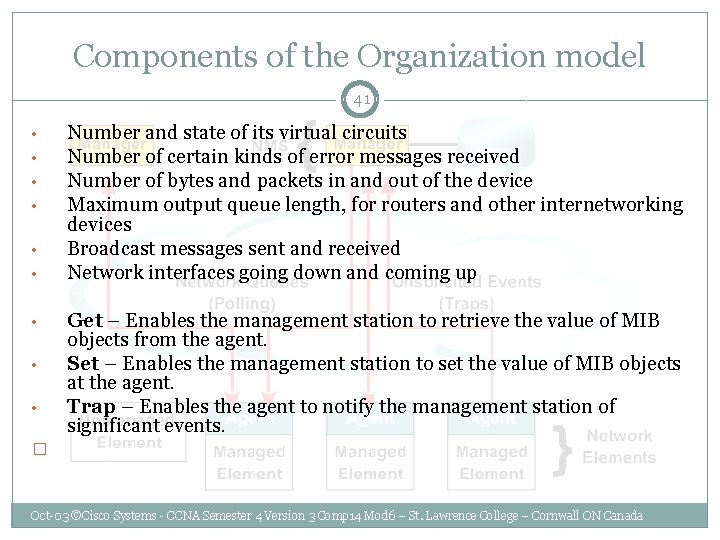
Components of the Organization model 41 • • • Number and state of its virtual circuits Number of certain kinds of error messages received Number of bytes and packets in and out of the device Maximum output queue length, for routers and other internetworking devices Broadcast messages sent and received Network interfaces going down and coming up • • • Get – Enables the management station to retrieve the value of MIB objects from the agent. Set – Enables the management station to set the value of MIB objects at the agent. Trap – Enables the agent to notify the management station of significant events. � Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 4 SNMP operation 42 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

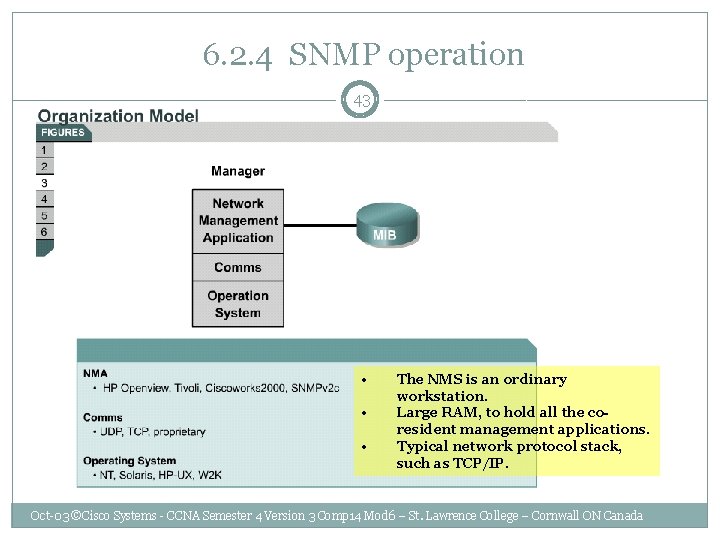
6. 2. 4 SNMP operation 43 • • • The NMS is an ordinary workstation. Large RAM, to hold all the coresident management applications. Typical network protocol stack, such as TCP/IP. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Components of the Organization model 44 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

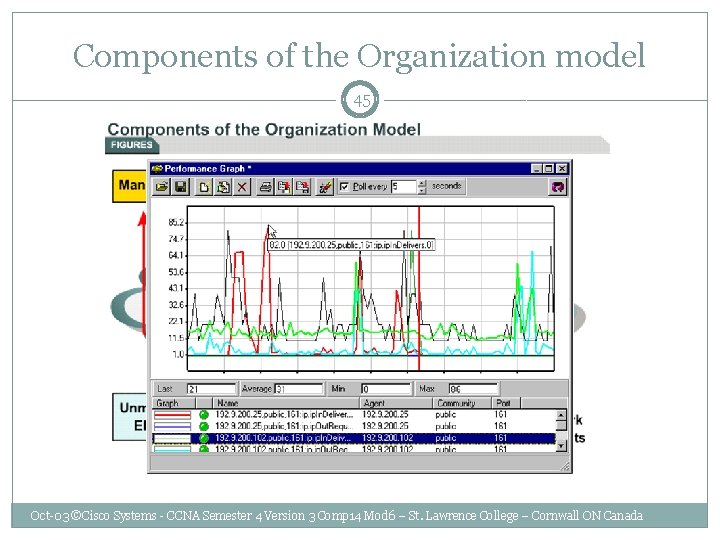
Components of the Organization model 45 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

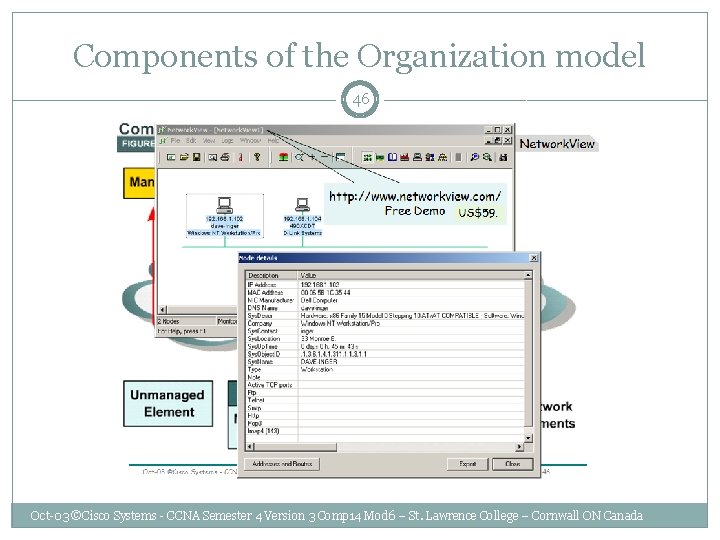
Components of the Organization model 46 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

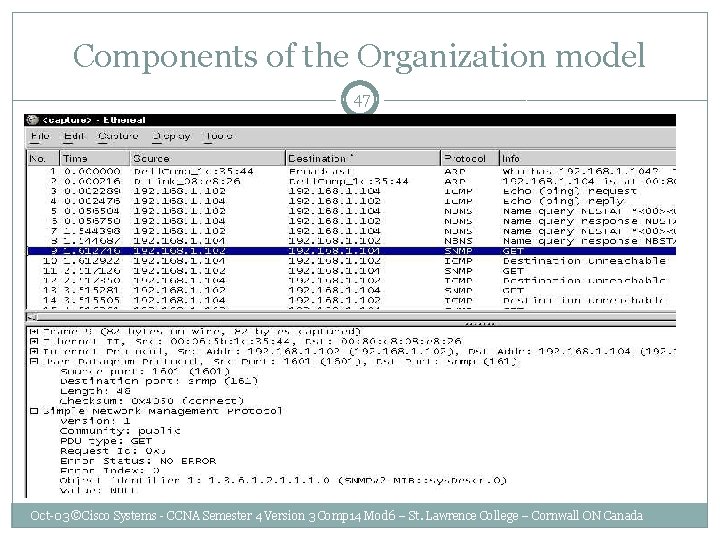
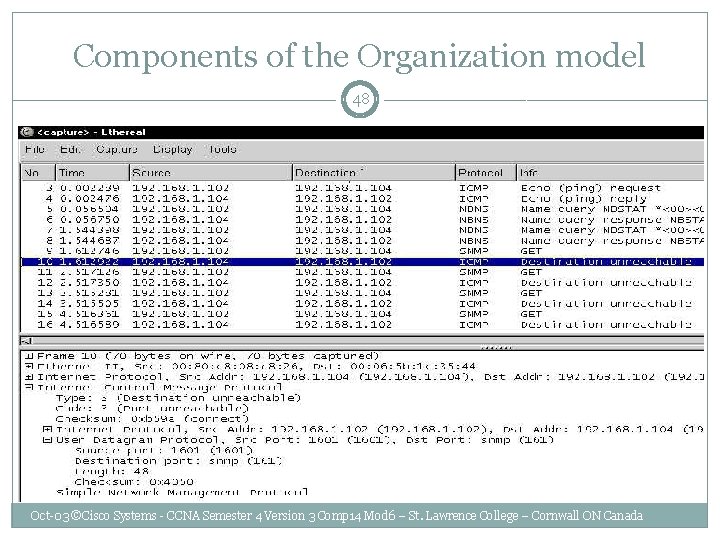
Components of the Organization model 47 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

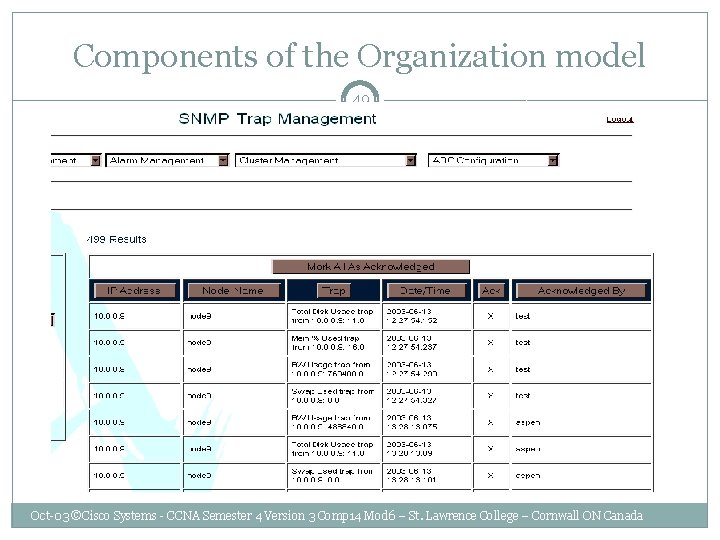
Components of the Organization model 48 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Components of the Organization model 49 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Components of the Organization model 50 Linux SNMP Network Management Tools • • • This page assumes that you already have a working knowledge of the basic tools -- ping, netstat, traceroute, nslookup, dig, tcpdump, /proc/net, ipfwadmin, tcpwrapper, maskd and are looking for graphical, distributed tools. SNMP FAQ Frequently asked questions about SNMP. Linux CMU SNMP Project -- provides the standard bilingual SNMPv 1/v 2 agent, incl USEC support, as well as command line tools; includes MIB-2 (RFC 1213) Identification MIB (RFC 1414) Host Resources MIB (RFC 1514) and the TUBS Linux MIB, as well as pointers to the Tcl and Perl snmp libs. SUNY Bufallo Network Management Archives -- the most complete archive around, including tools, MIB compilers, documentation. Not Linux specific. The Simple Web site maintains info on internet management. Simple Times A periodical for Internet network management. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Components of the Organization model 51 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

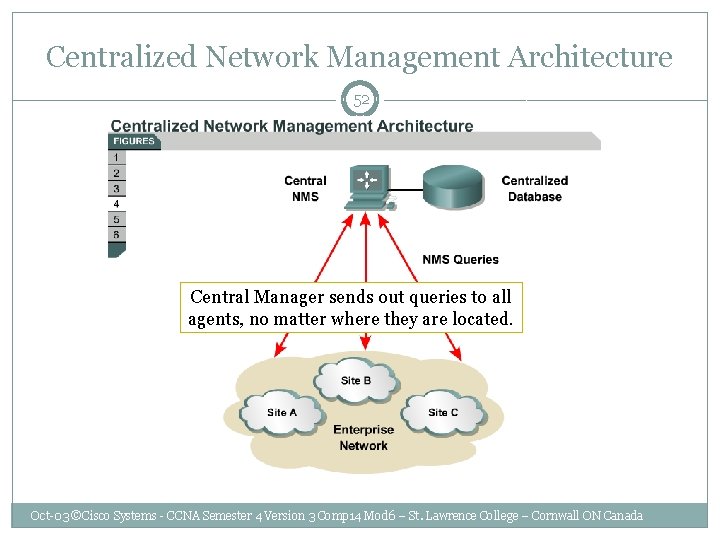
Centralized Network Management Architecture 52 Central Manager sends out queries to all agents, no matter where they are located. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

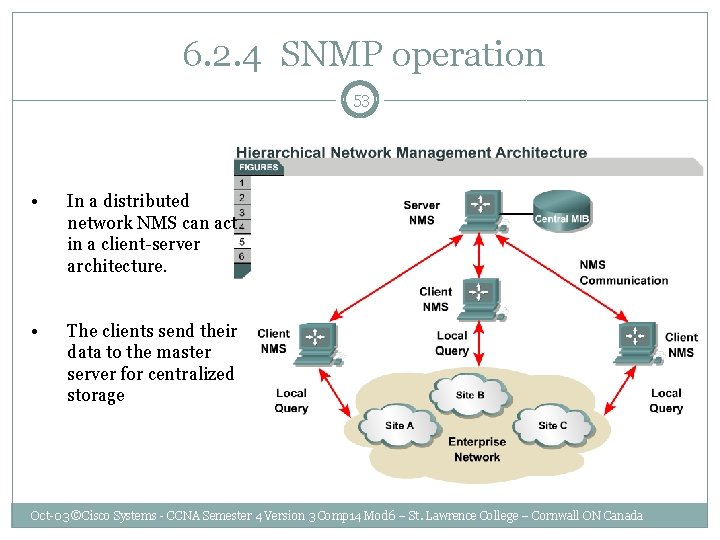
6. 2. 4 SNMP operation 53 • In a distributed network NMS can act in a client-server architecture. • The clients send their data to the master server for centralized storage Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

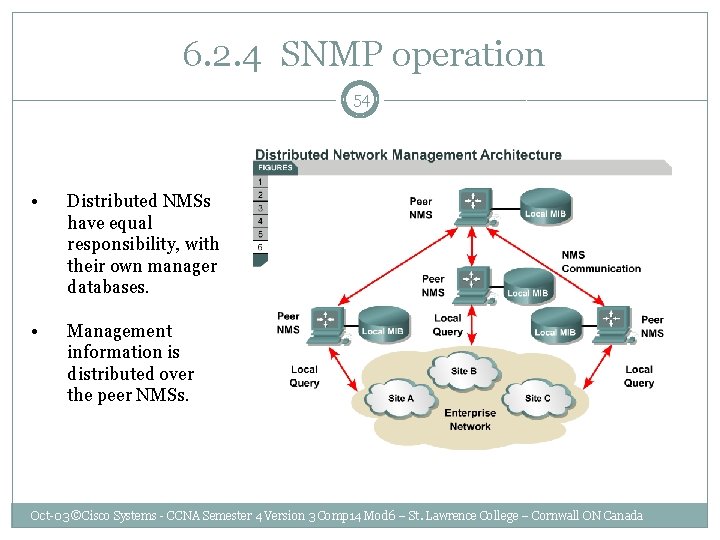
6. 2. 4 SNMP operation 54 • Distributed NMSs have equal responsibility, with their own manager databases. • Management information is distributed over the peer NMSs. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

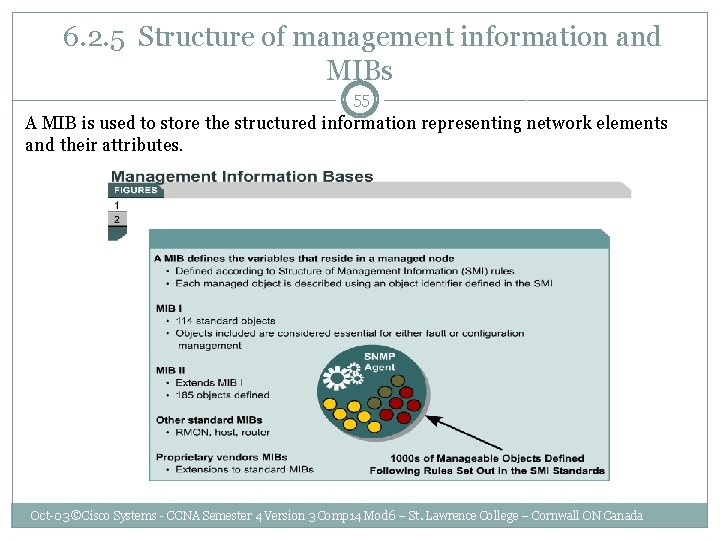
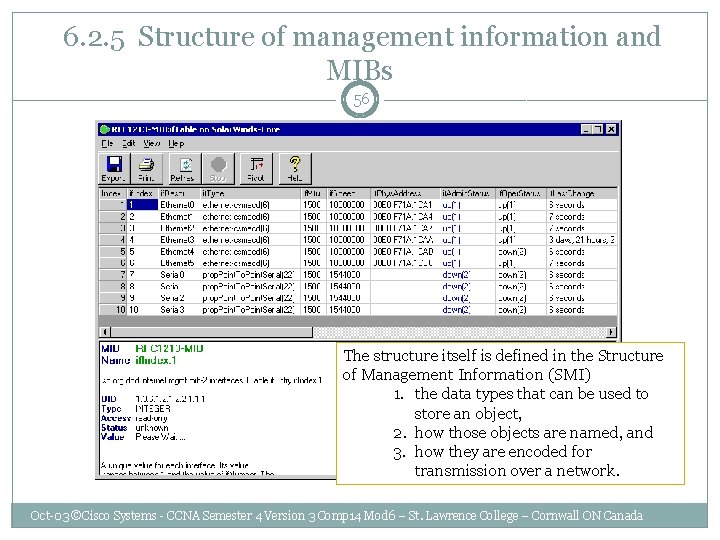
6. 2. 5 Structure of management information and MIBs 55 A MIB is used to store the structured information representing network elements and their attributes. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 5 Structure of management information and MIBs 56 The structure itself is defined in the Structure of Management Information (SMI) 1. the data types that can be used to store an object, 2. how those objects are named, and 3. how they are encoded for transmission over a network. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

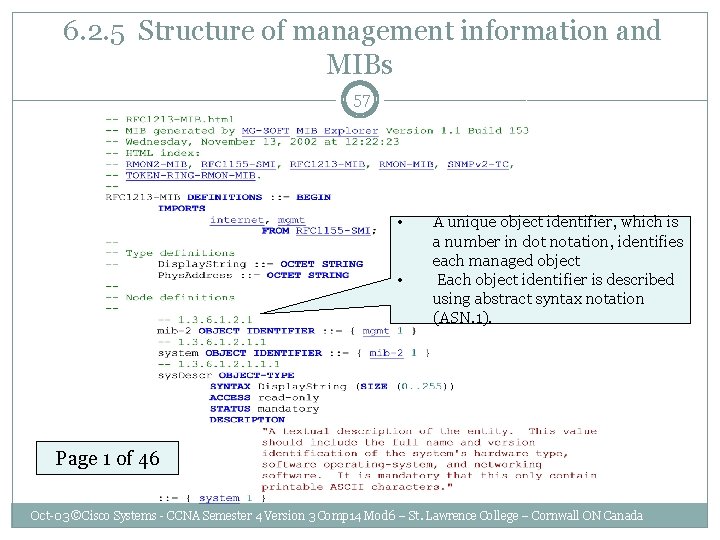
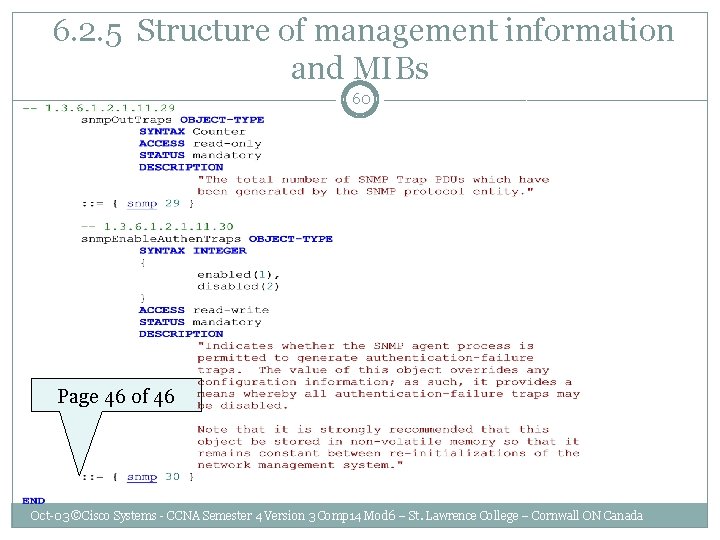
6. 2. 5 Structure of management information and MIBs 57 • • A unique object identifier, which is a number in dot notation, identifies each managed object Each object identifier is described using abstract syntax notation (ASN. 1). Page 1 of 46 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

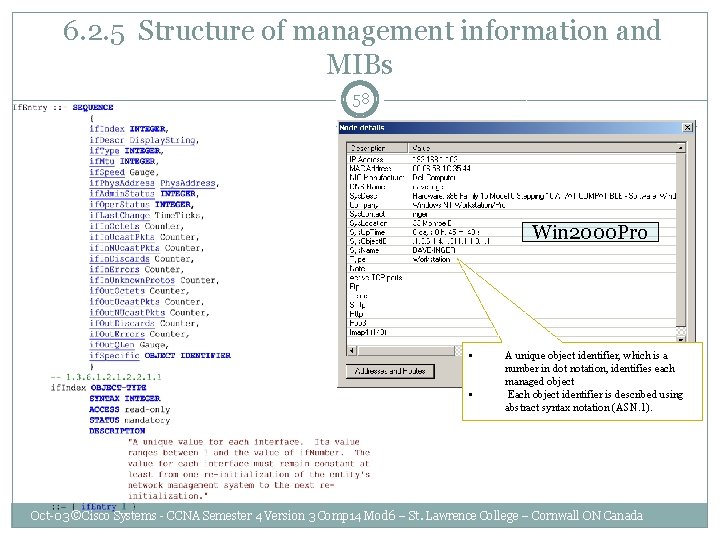
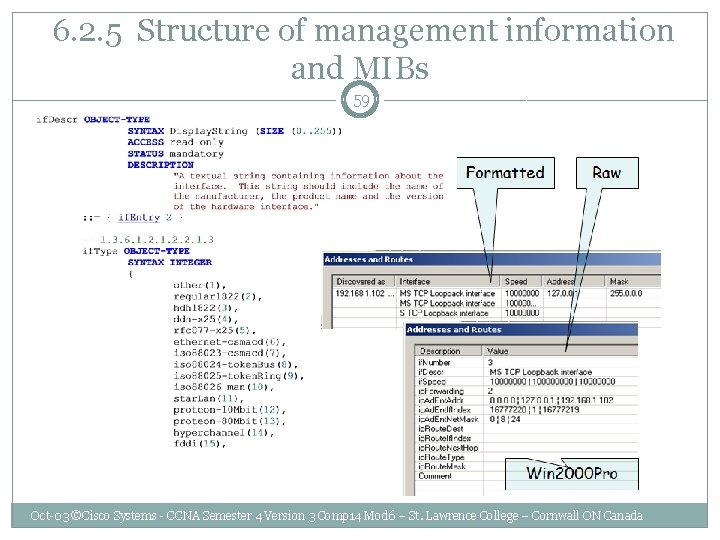
6. 2. 5 Structure of management information and MIBs 58 Win 2000 Pro • • A unique object identifier, which is a number in dot notation, identifies each managed object Each object identifier is described using abstract syntax notation (ASN. 1). Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 5 Structure of management information and MIBs 59 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 5 Structure of management information and MIBs 60 Page 46 of 46 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

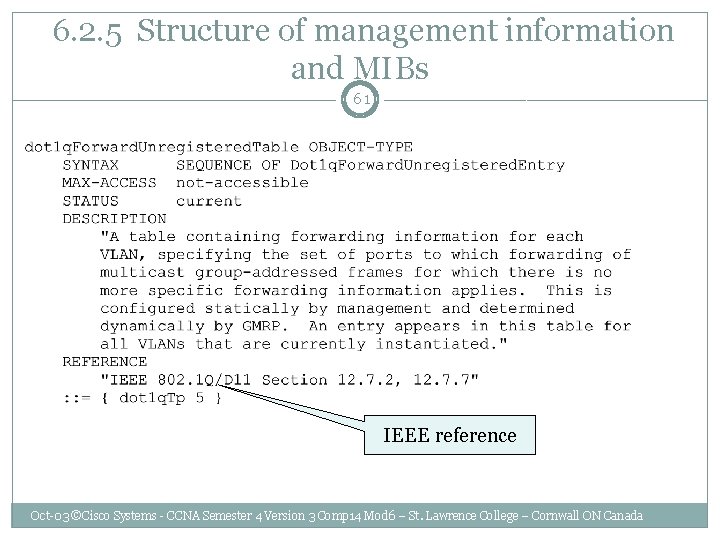
6. 2. 5 Structure of management information and MIBs 61 IEEE reference Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 5 Structure of management information and MIBs 62 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

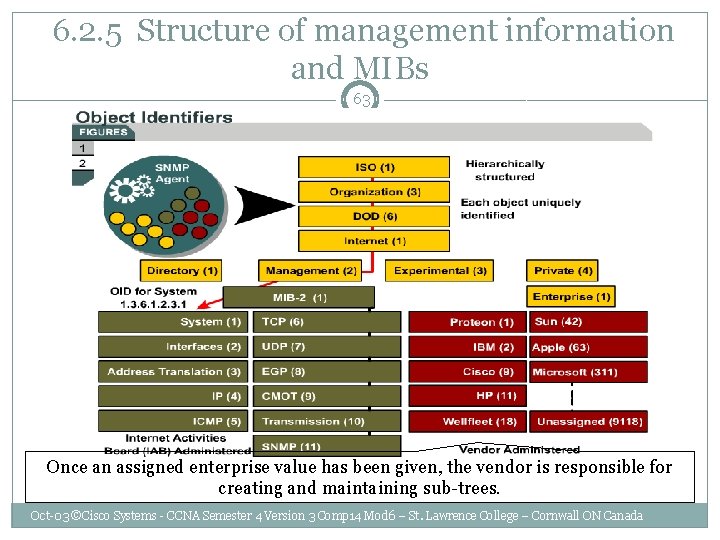
6. 2. 5 Structure of management information and MIBs 63 Once an assigned enterprise value has been given, the vendor is responsible for creating and maintaining sub-trees. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

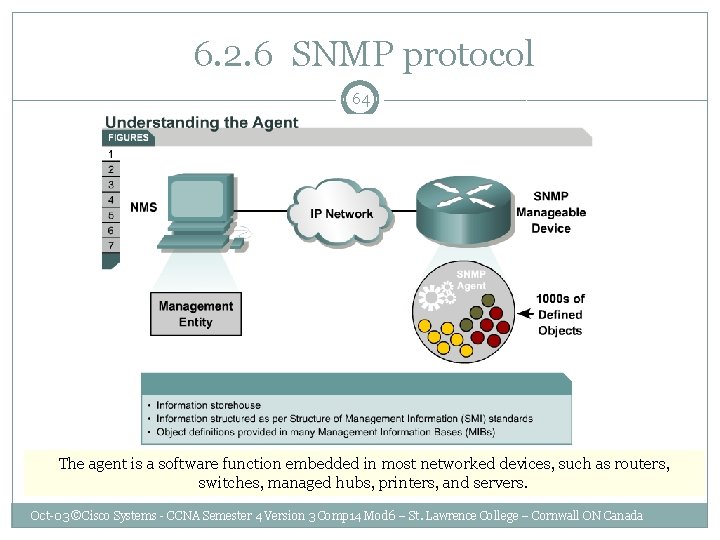
6. 2. 6 SNMP protocol 64 The agent is a software function embedded in most networked devices, such as routers, switches, managed hubs, printers, and servers. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

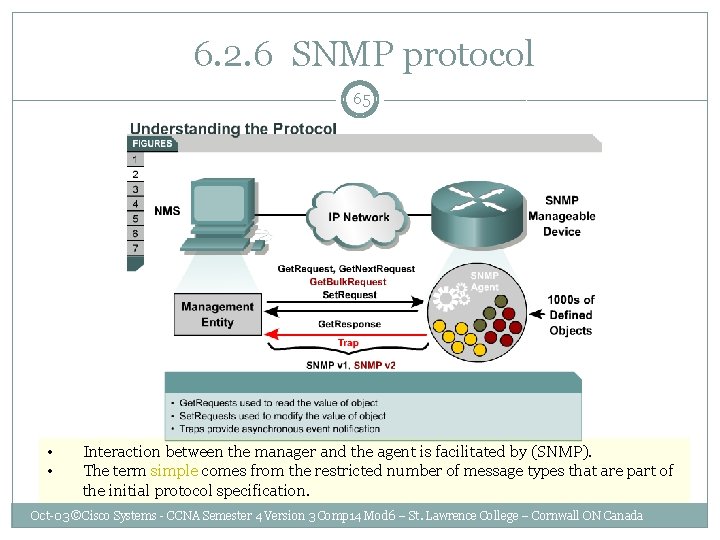
6. 2. 6 SNMP protocol 65 • • Interaction between the manager and the agent is facilitated by (SNMP). The term simple comes from the restricted number of message types that are part of the initial protocol specification. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

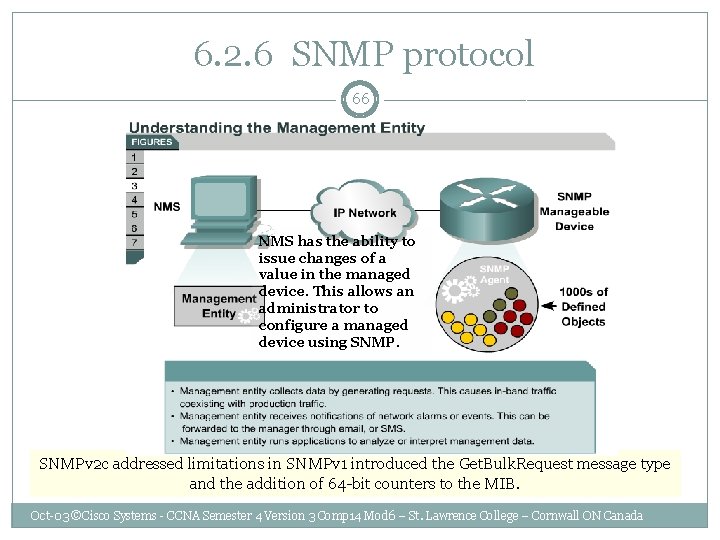
6. 2. 6 SNMP protocol 66 NMS has the ability to issue changes of a value in the managed device. This allows an administrator to configure a managed device using SNMPv 2 c addressed limitations in SNMPv 1 introduced the Get. Bulk. Request message type and the addition of 64 -bit counters to the MIB. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 6 SNMP protocol 67 • • The interaction between the manager and the managed device introduces traffic to the network. Aggressive monitoring strategies can negatively affect network performance. Bandwidth utilizations will go up, which may be an issue for WAN environments. Moreover, monitoring has a performance impact on the devices themselves being monitored, since they are required to process the manager requests. This processing should not take precedence over production services. A general rule is that a minimum amount of information should be polled as infrequently as possible. Determine which devices and links are most critical and what type of data is required. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

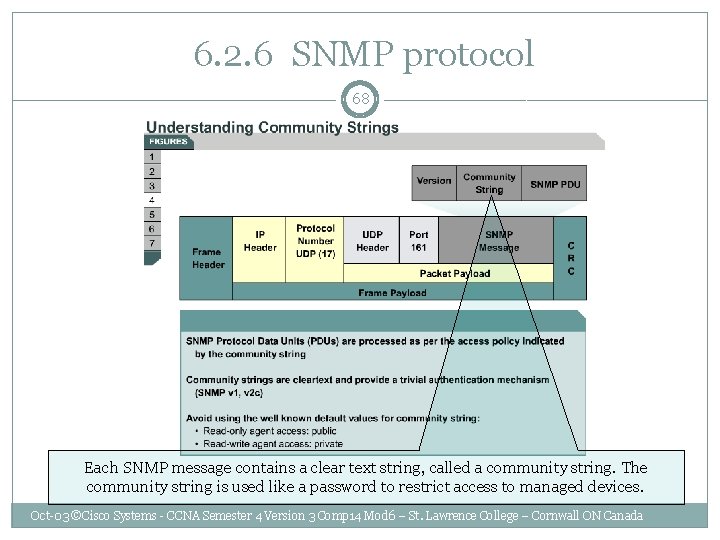
6. 2. 6 SNMP protocol 68 Each SNMP message contains a clear text string, called a community string. The community string is used like a password to restrict access to managed devices. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

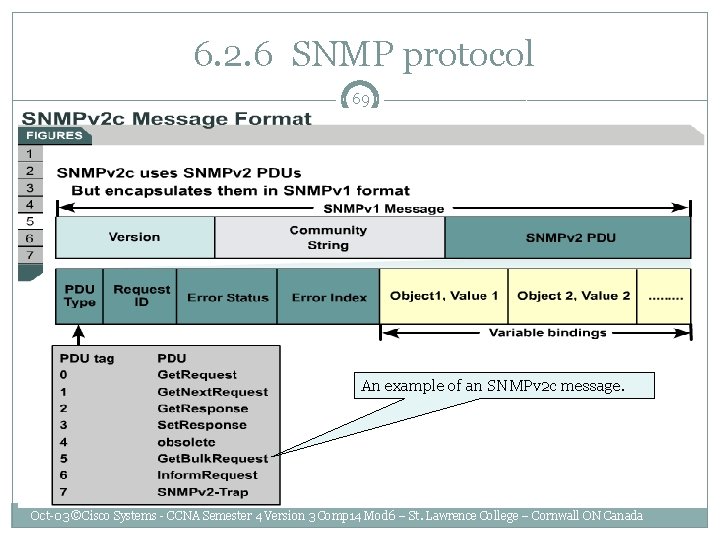
6. 2. 6 SNMP protocol 69 An example of an SNMPv 2 c message. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

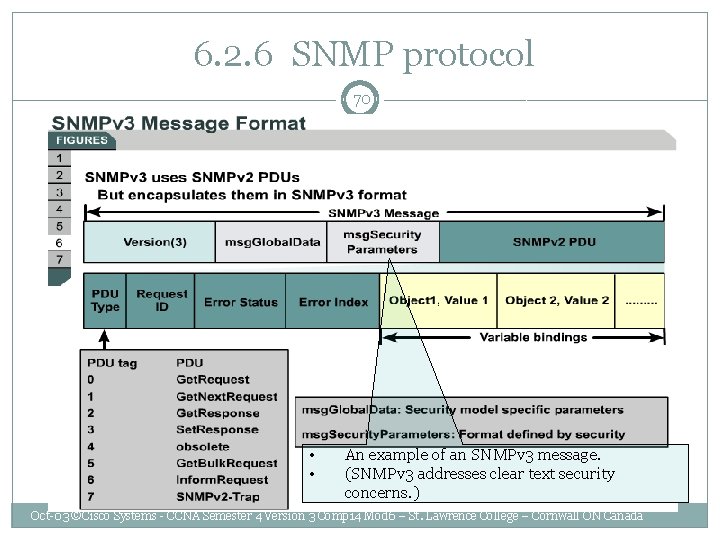
6. 2. 6 SNMP protocol 70 • • An example of an SNMPv 3 message. (SNMPv 3 addresses clear text security concerns. ) Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 6 SNMP protocol 71 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

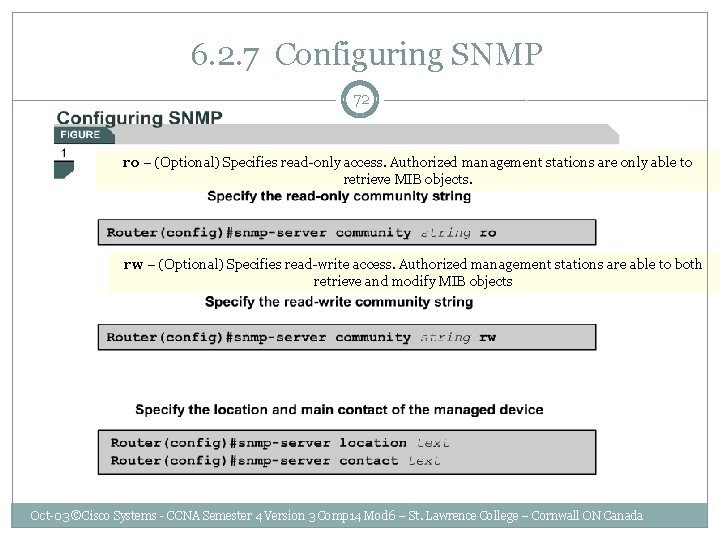
6. 2. 7 Configuring SNMP 72 ro – (Optional) Specifies read-only access. Authorized management stations are only able to retrieve MIB objects. rw – (Optional) Specifies read-write access. Authorized management stations are able to both retrieve and modify MIB objects Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 8 RMON 73 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

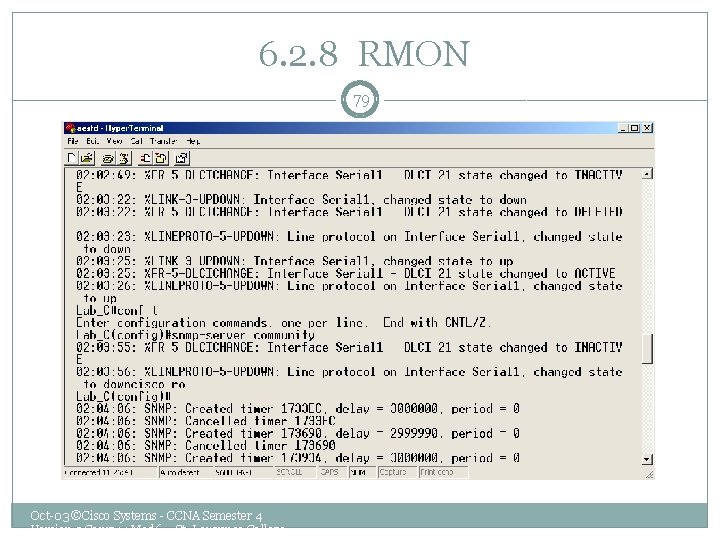
6. 2. 8 RMON 74 • RMON was developed to overcome limitations in the capabilities of SNMP can store only limited amounts of information (counters for overall traffic, number of errors, etc. ), and, as it is a polled system, network loading is high. • RMON on the other hand, provides much more detailed information and offers a simplified manner of data collection. • RMON makes use of a client (like a Network Management Console, a Protocol Analyzer, or a Network Analyzer like the new Fluke Networks Opti. View). The client then gathers the statistics from either one or more agents. These agents can be stand-alone RMON probes (located in strategic spots in the network) and/or embedded RMON agents in routers and switches. • In total RMON specifies 10 services called RMON Groups. Not all devices have to support all services as some of the RMON groups require extensive overhead (memory and processor power). Most stand-alone RMON probes will typically support all services, but embedded RMON may be limited to only a few groups. • The RMON client communicates directly to the RMON agent. RMON 1 only collects data at the MAC level, so you will only get information on the captured packets by decoding them with a Protocol Analyzer. A switch will limit your view of the network. • RMON 2 has been developed to provide data on higher level protocols such as IP and IPX, and up through the stack to the applications layer. • RMON 2 provides full information on which protocols are being used on the network and the mix between them, standard RMON host and matrix information also for the network an applications layers, and a customizable history function that can be used for base-lining. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

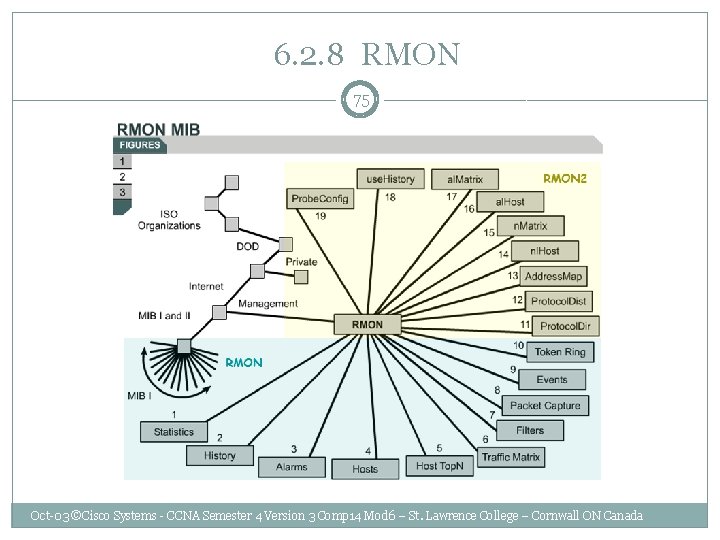
6. 2. 8 RMON 75 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 8 RMON 76 1. Statistics (OID: 1. 3. 6. 1. 2. 1. 16. 1) This group provides basic statistics for the given network interface type on the probe. For example, it will collect a breakdown of packet sizes on the segment over time. 2. History (OID: 1. 3. 6. 1. 2. 1. 16. 2) The history group is responsible for storing periodic samples of the segment for later analysis. 3. Alarm (OID: 1. 3. 6. 1. 2. 1. 16. 3) Using preconfigured thresholds on the probe, this group can generate alarm events when a parameter surpasses a threshold. 4. Hosts (OID: 1. 3. 6. 1. 2. 1. 16. 4) This group keeps track of the MAC addresses of the devices that are communicating on this segment. 5. Host. Top. N (OID: 1. 3. 6. 1. 2. 1. 16. 5) This group is used to store data regarding the top "talkers" based on some criteria provided by the management station. 6. Matrix (OID: 1. 3. 6. 1. 2. 1. 16. 6) This group holds a table that defines pairs of devices who are talking to one another. 7. Filter (OID: 1. 3. 6. 1. 2. 1. 16. 7) This group allows a Network Manager to define or more filters, based on a value and offset, for packets that want to be captured. The definition of that filter(s) exists in this group. 8. Capture Packets (OID: 1. 3. 6. 1. 2. 1. 16. 8) This group requires the presence of the Filter group and provides a means of capturing packet flowing through the network interface for later review. This group actually stores the contents of each packet flowing into the interface and meeting the filter criteria. 9. Event (OID: 1. 3. 6. 1. 2. 1. 16. 9) This group provides the mechanism for the device to generate events and alarms. It is basically the holding table for any events that occur on the device, either through configuration or exception. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

6. 2. 8 RMON 77 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

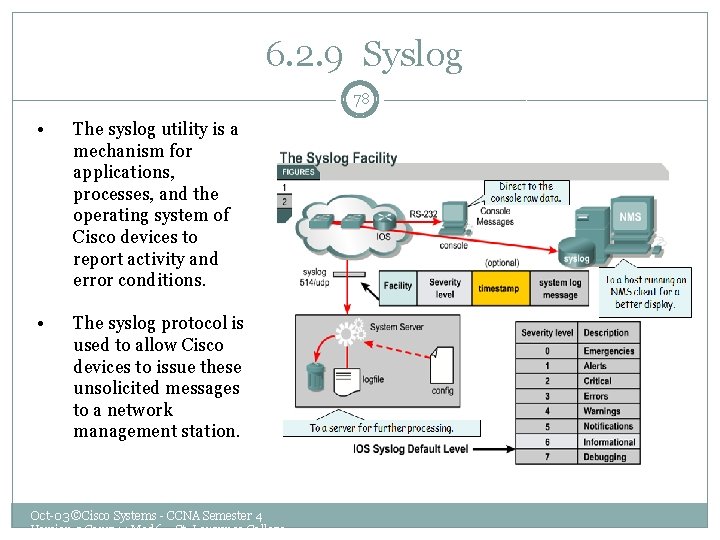
6. 2. 9 Syslog 78 • The syslog utility is a mechanism for applications, processes, and the operating system of Cisco devices to report activity and error conditions. • The syslog protocol is used to allow Cisco devices to issue these unsolicited messages to a network management station. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College –

6. 2. 8 RMON 79 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College –

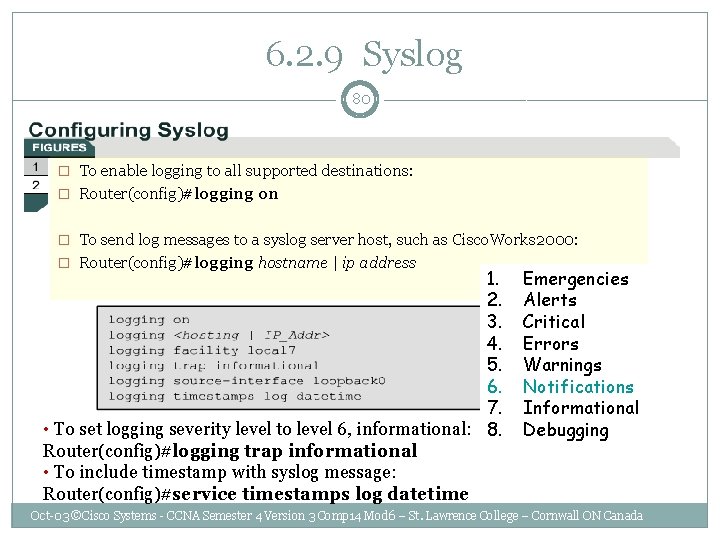
6. 2. 9 Syslog 80 � To enable logging to all supported destinations: � Router(config)#logging on � To send log messages to a syslog server host, such as Cisco. Works 2000: � Router(config)#logging hostname | ip address 1. 2. 3. 4. 5. 6. 7. • To set logging severity level to level 6, informational: 8. Router(config)#logging trap informational • To include timestamp with syslog message: Router(config)#service timestamps log datetime Emergencies Alerts Critical Errors Warnings Notifications Informational Debugging Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

Summary 81 The functions of a workstation and a server 2. The roles of various equipment in a client/server environment 3. The development of Networking Operating Systems (NOS) 4. An overview of the various Windows platforms 5. An overview of some of the alternatives to Windows operating systems 6. Reasons for network management 7. The layers of OSI and network management model 8. The type and application of network management tools 9. The role that SNMP and CMIP play in network monitoring 10. How management software gathers information and records problems 11. How to gather reports on network performance 1. Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada

FIN 82 Oct-03 ©Cisco Systems - CCNA Semester 4 Version 3 Comp 14 Mod 6 – St. Lawrence College – Cornwall ON Canada