Covert Communication via the QR Code Image by

Covert Communication via the QR Code Image by a Data Hiding Technique Based on Module Shape Adjustments Source: IEEE Open Journal of the Computer Society, vol. 1, pp. 12 -34, 2020. Authors: Da-Chun Wu, and Yuan-Ming Wu. Speaker: Huang Peng-Cheng Date: 10/18/2021 1

Outline • Introduction • Related works • Proposed scheme • Simulation results • Conclusions • Comments 2
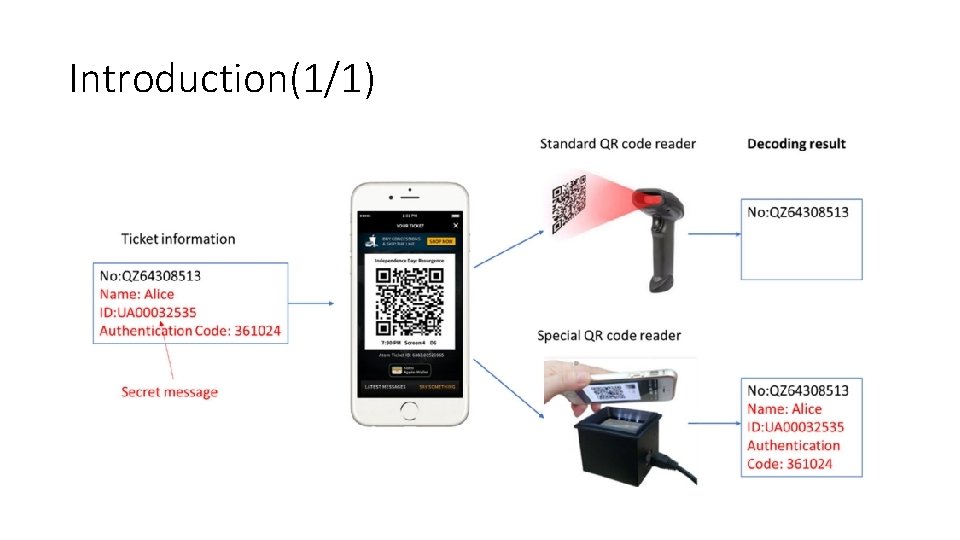
Introduction(1/1)
Related works(1/2) Data hiding mechanism based on QR code P. -C. Huang, Y. -H. Li, C. -C. Chang, and Y. Liu, "Efficient Scheme for Secret Hiding in QR Code by Improving Exploiting Modification Direction, " KSII Transactions on Internet & Information Systems, vol. 12, no. 5, pp. 2348 -2365, May 31 2018. P. -C. Huang, C. -C. Chang, Y. -H. Li, and Y. Liu, "High-payload secret hiding mechanism for QR codes, " Multimedia Tools and Applications, journal article vol. 78, no. 16, pp. 22331 -22350, August 01 2019. P. Huang, C. Chang, Y. Li and Y. Liu, "Efficient QR Code Secret Embedding Mechanism Based on Hamming Code, " in IEEE Access, vol. 8, pp. 86706 -86714, 2020, doi: 10. 1109/ACCESS. 2020. 2992694.
Related works(2/2) Data hiding mechanism based on QR code W. Erlangga and A. M. Barmawi, "Increasing Secret Data Hiding Capacity in QR Code Using 3 times 3 Subcells, " in International Workshop on Digital Watermarking, 2016, pp. 327 -342: Springer.
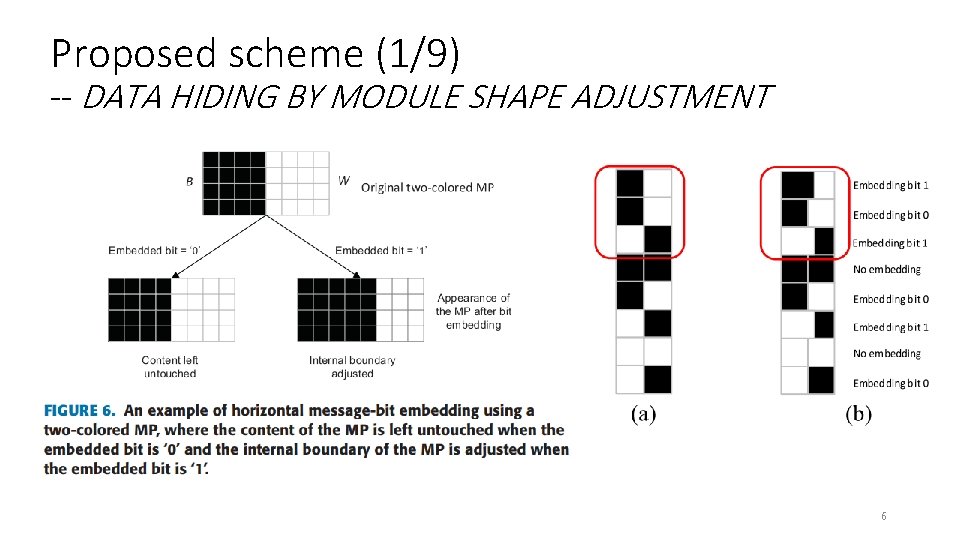
Proposed scheme (1/9) -- DATA HIDING BY MODULE SHAPE ADJUSTMENT 6
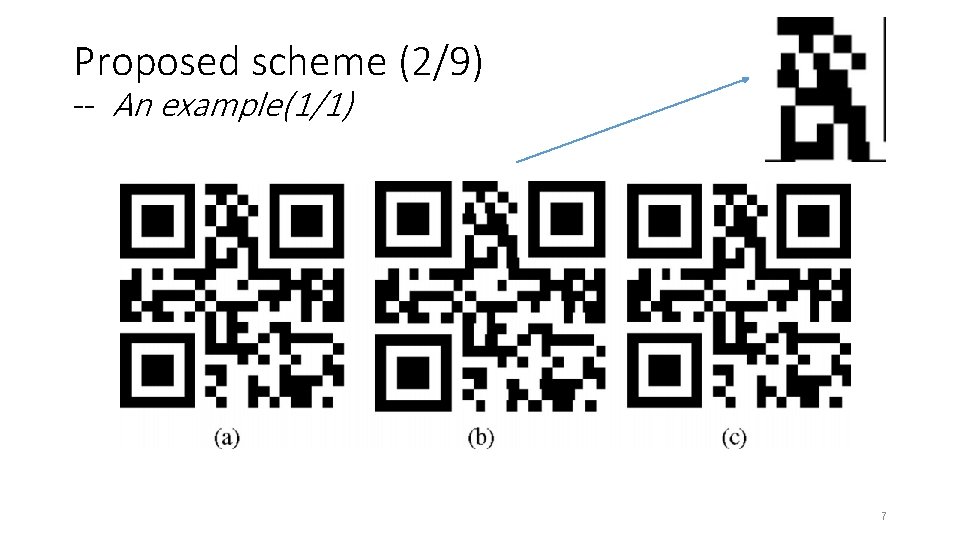
Proposed scheme (2/9) -- An example(1/1) 7
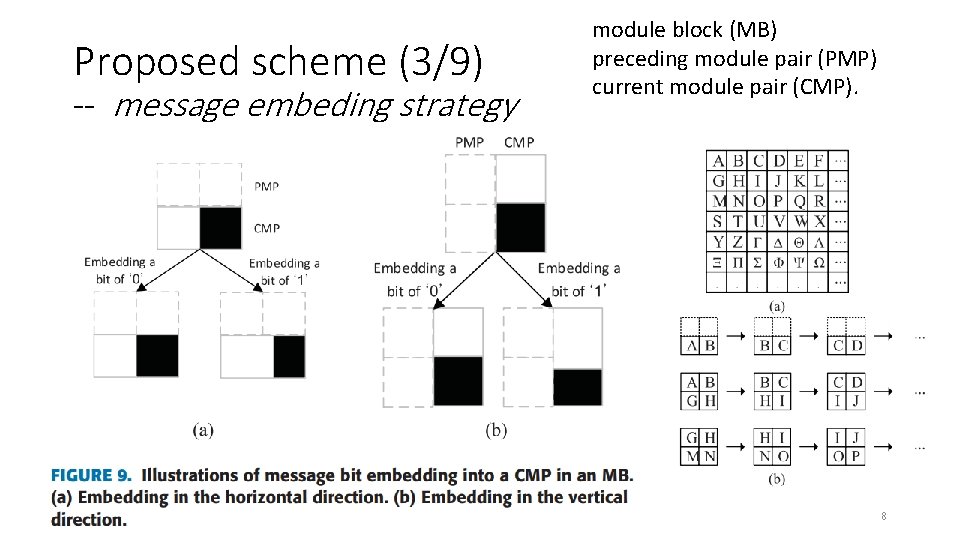
Proposed scheme (3/9) -- message embeding strategy module block (MB) preceding module pair (PMP) current module pair (CMP). 8
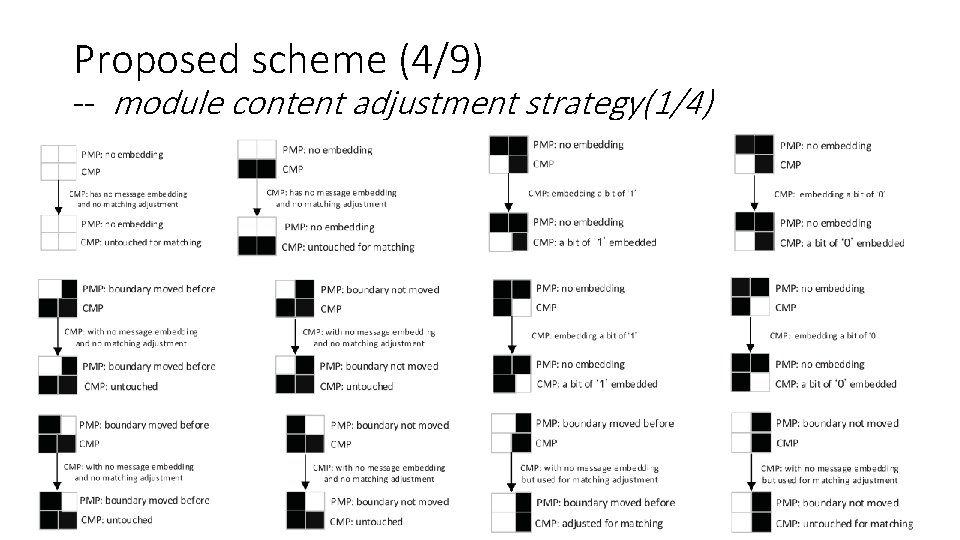
Proposed scheme (4/9) -- module content adjustment strategy(1/4) 9
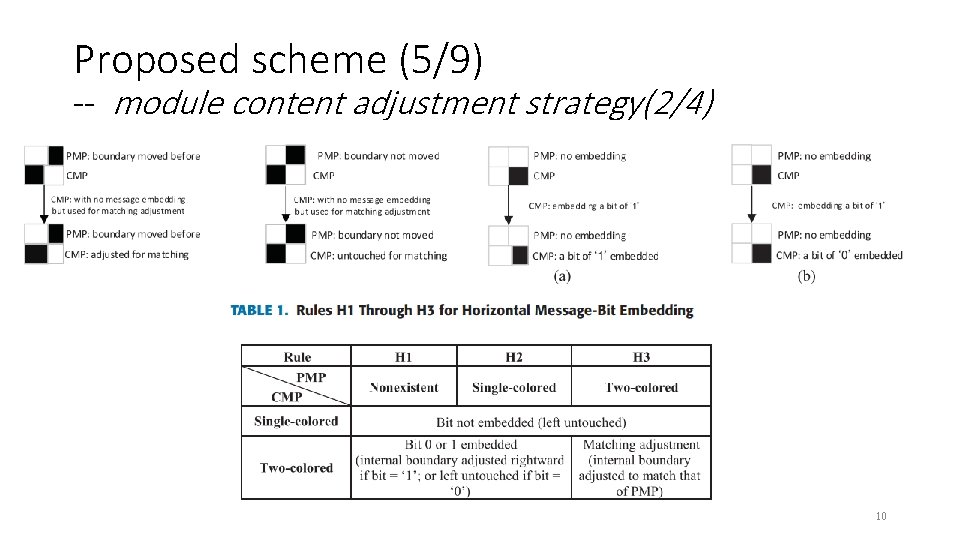
Proposed scheme (5/9) -- module content adjustment strategy(2/4) 10
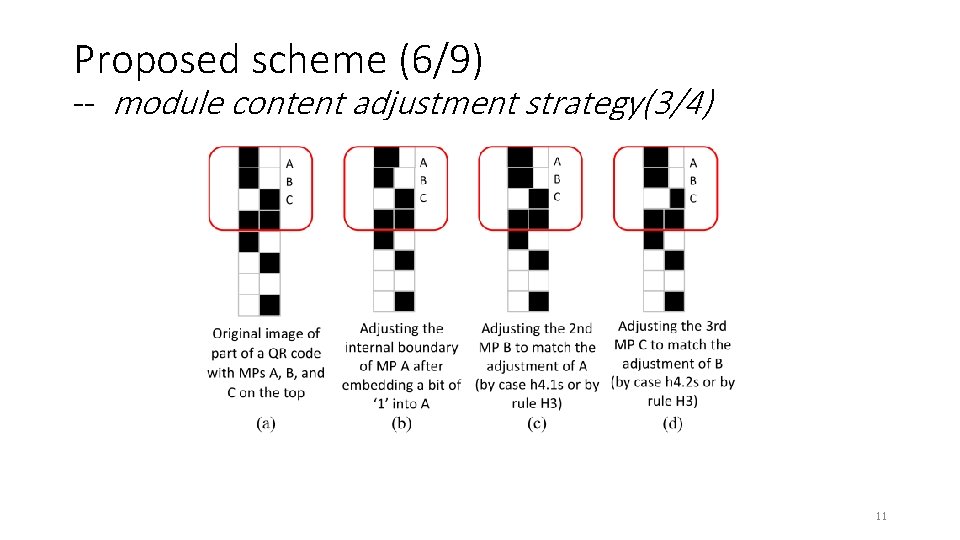
Proposed scheme (6/9) -- module content adjustment strategy(3/4) 11
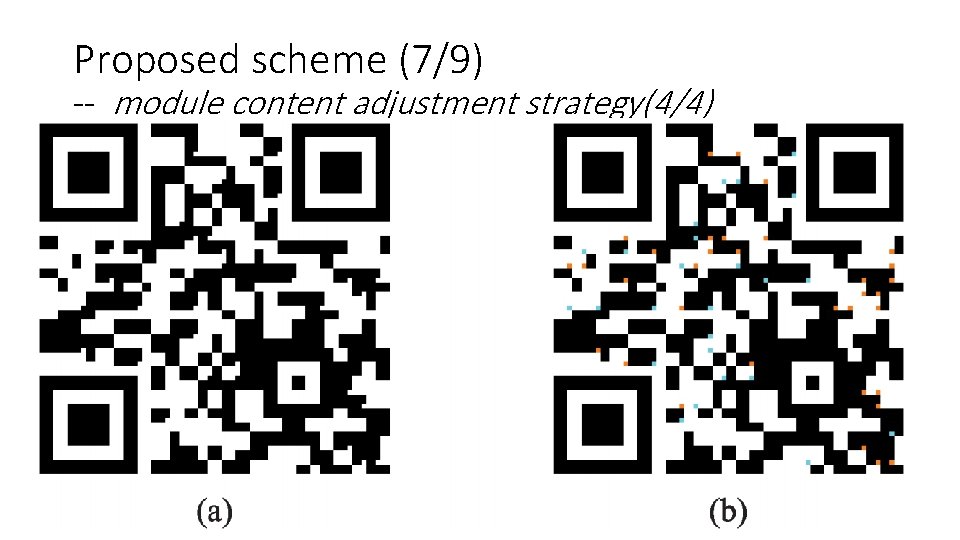
Proposed scheme (7/9) -- module content adjustment strategy(4/4) 12
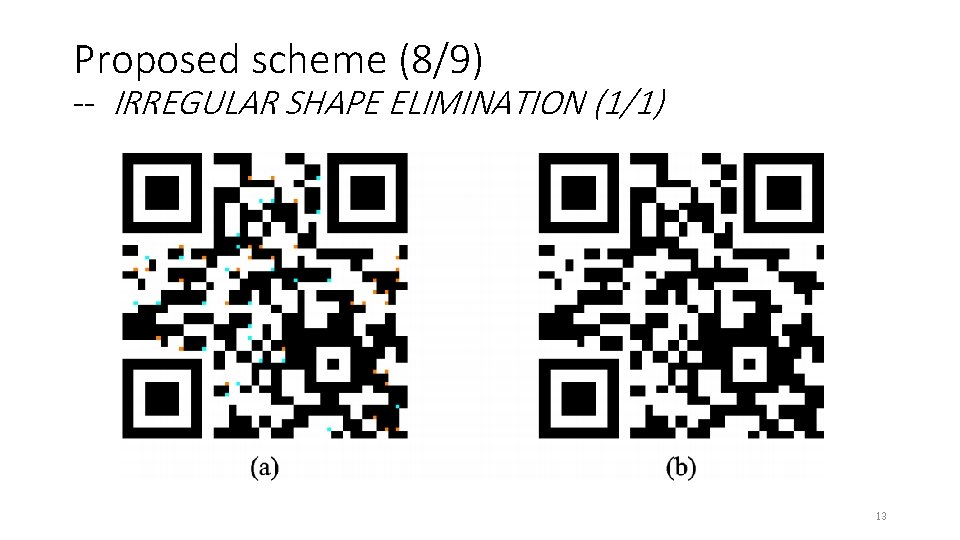
Proposed scheme (8/9) -- IRREGULAR SHAPE ELIMINATION (1/1) 13
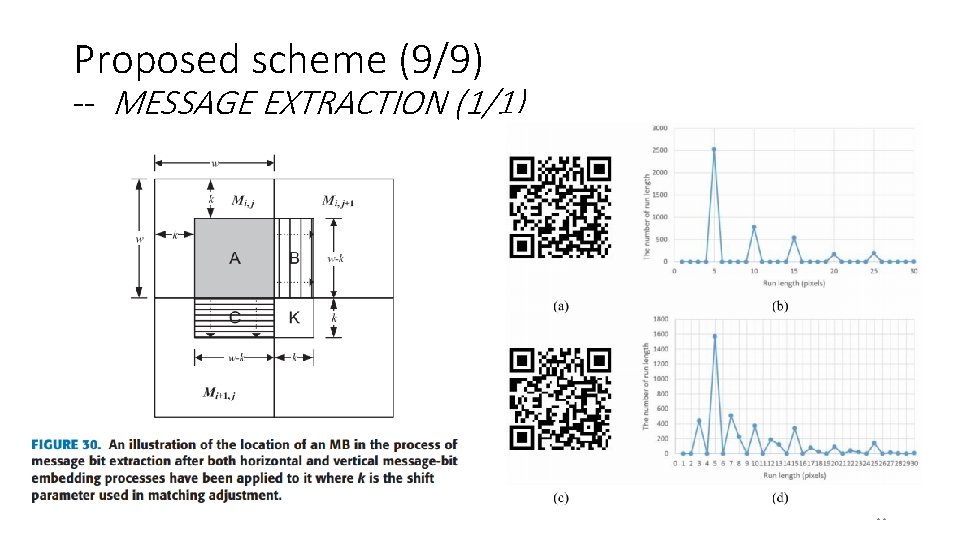
Proposed scheme (9/9) -- MESSAGE EXTRACTION (1/1) 14

Simulation results (1/5)—an example 15
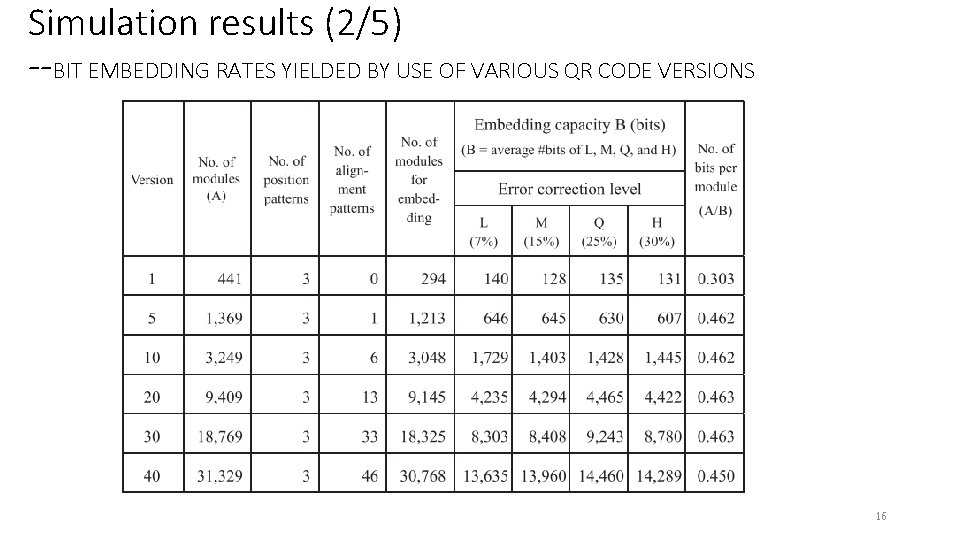
Simulation results (2/5) --BIT EMBEDDING RATES YIELDED BY USE OF VARIOUS QR CODE VERSIONS 16
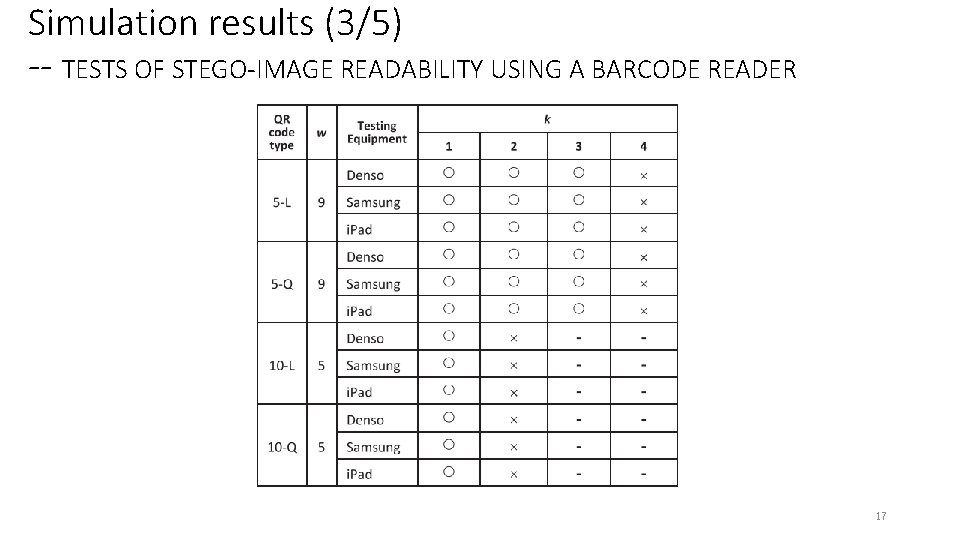
Simulation results (3/5) -- TESTS OF STEGO-IMAGE READABILITY USING A BARCODE READER 17
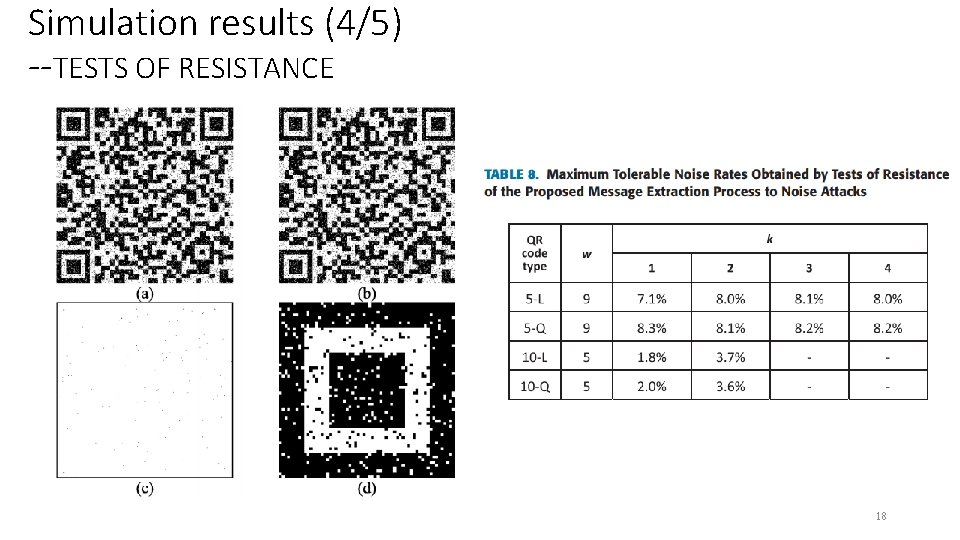
Simulation results (4/5) --TESTS OF RESISTANCE 18
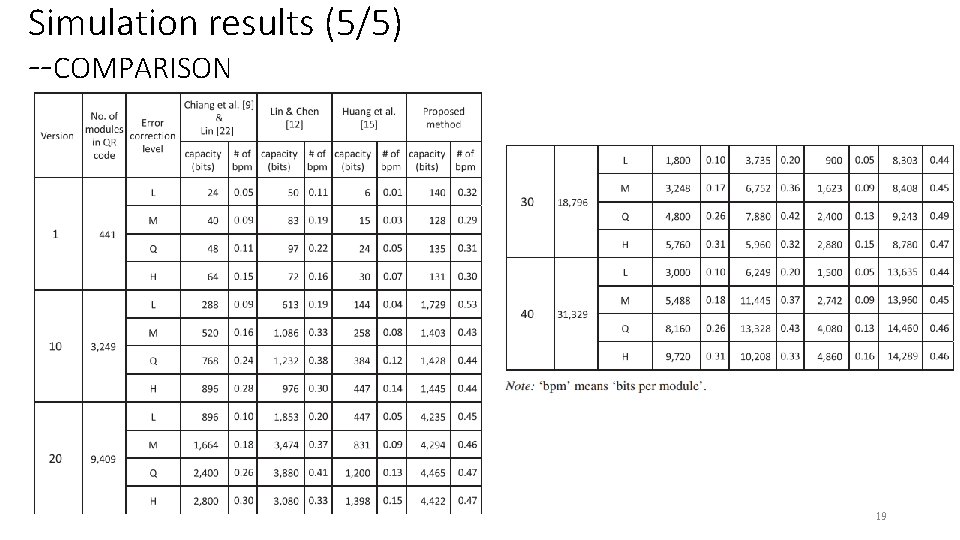
Simulation results (5/5) --COMPARISON 19

Conclusions • The first study. • High secret capacity. • Maintain fault tolerance. 20

Comments • Low practicability. • Resist print-and-camera attacks? • Module identification algorithm? • Secret payload is less than the methods based on module segmentation. 21
- Slides: 21