Course Projects Examples Guidelines Suggestions Topics n Overview






















![An Example n E [Name, Rank, Salary, Department] n Two levels: Everything ok n An Example n E [Name, Rank, Salary, Department] n Two levels: Everything ok n](https://slidetodoc.com/presentation_image_h2/bb150262f3f9bf0aa5f4d13aa9f13669/image-32.jpg)




- Slides: 36

Course Projects Examples Guidelines Suggestions

Topics n Overview of project n Selected Fall 2003 projects n List of Fall 2004 projects n General comments

Course Projects n Undergraduate – group n Graduate – individual n Substantive investigation of some aspect of security n Approach may be experiment, data analysis, system comparison, algorithm analysis, etc. n First due date: Monday, October 24

Survey of Intrusion Detection Systems n Comparison of IDS n Different approaches n Different products n 27 pages, 7 references n Undergraduates

E-Commerce Security n Survey of client/server security issues in e-commerce n Firewalls, CGI, Databases n Privacy, Executable content n Unpaginated, 5 references n Undergraduates

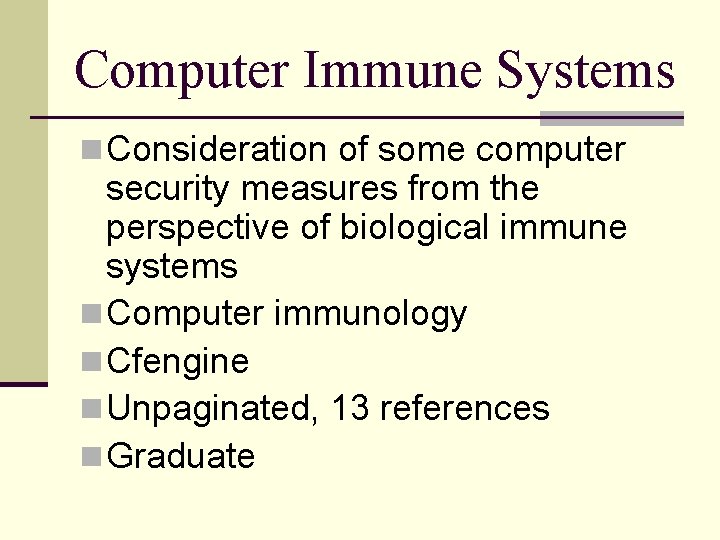
Computer Immune Systems n Consideration of some computer security measures from the perspective of biological immune systems n Computer immunology n Cfengine n Unpaginated, 13 references n Graduate

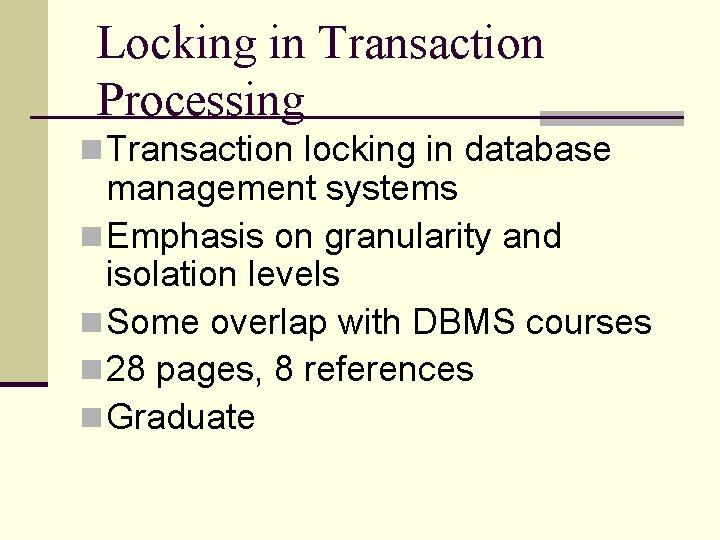
Locking in Transaction Processing n Transaction locking in database management systems n Emphasis on granularity and isolation levels n Some overlap with DBMS courses n 28 pages, 8 references n Graduate

Commit Protocols in Multilevel Secure Distributed Database Systems n 13 pages, 6 references n. Graduate

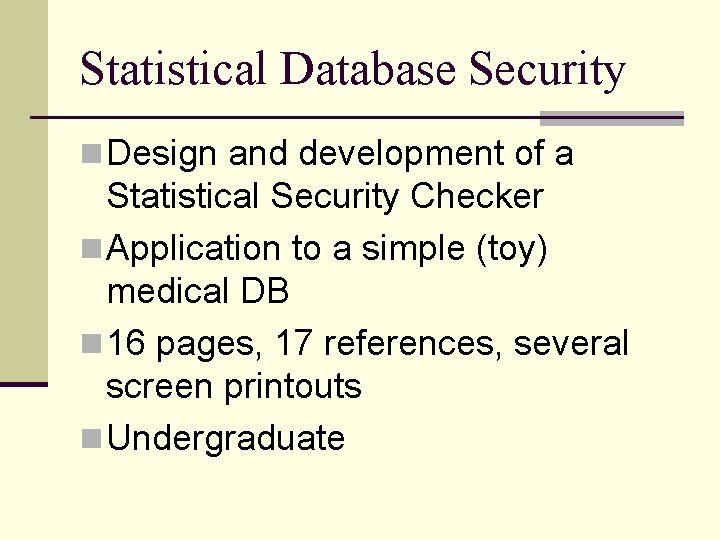
Statistical Database Security n Design and development of a Statistical Security Checker n Application to a simple (toy) medical DB n 16 pages, 17 references, several screen printouts n Undergraduate

Digital Watermarking n Use of digital watermarking for image authentication and copyright protection n Content-based watermarking n New approach to digital watermarking proposed n 18 pages, 5 references n Graduate

Video Watermarking n. Overview of video watermarking n. Unpaginated, 10 references n. Graduate ?

Specialized Hardware for Deep Network Packet Filtering n Design of hardware IDS n 13 pages text, 12 references, ~30 pages code n Graduate

Wireless Security n Overview of wireless security n Related to CSCE 313, 491, and other courses n Examines 802. 11 n 24 pages, 8 references n Undergraduate

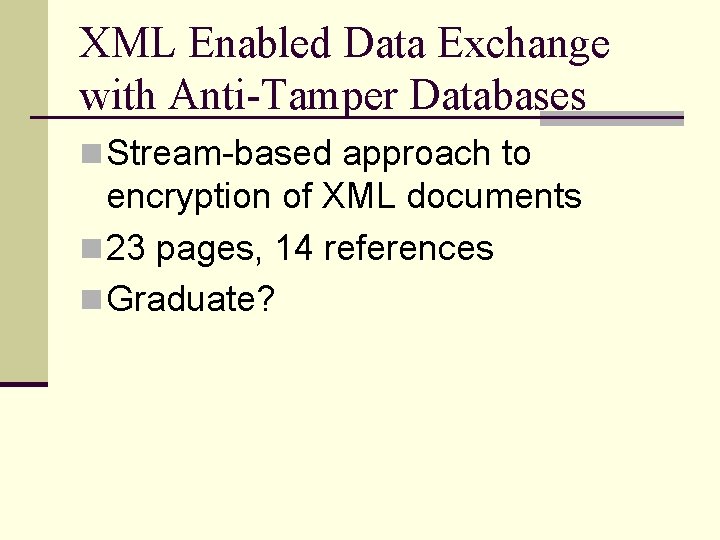
XML Enabled Data Exchange with Anti-Tamper Databases n Stream-based approach to encryption of XML documents n 23 pages, 14 references n Graduate?

Survey of Security for Home and Small Business Computer Users n Platform-independent methods to secure a host n Debian GNU/Linux n Windows XP n 18 pages, 16 references

Constraint Satisfaction Problem in Agent-based Distributed Architecture n Related to e-commerce n Security issues in an agent-based environment n 19 pages, 20 references

Defense of Network Attacks on Security n Overview of some managerial issues n 16 pages, 5 references, 1 attached article

Fall 2004 Projects n 5 undergraduate group (2 -4) projects n 6 graduate projects

Undergraduate Projects n Packet sniffing (4) n Firewalls and VPNs (3) n E-bay security (2) n On-line transaction security (4) n Steganography (4)

Graduate Projects n. Security in Java n. Passwords n. Web application security n. Wireless networks n. Ad hoc sensor networks n. PKI in e-commerce n. Wi-Fi security

Defense of Network Attacks on Security n Overview of some managerial issues n 16 pages, 5 references, 1 attached article

Some Approaches: Problems n Pick a real or potential problem. Try to find out how much of a problem it really is. n Pick a problem. Suggest a new or modified solution to it.

Some Approaches: Comparisons n Pick a class of objects (e. g. viruses, defense techniques, etc. ) and compare them in detail. n Pick a set of algorithms and compare their performance.

Some Suggestions n Credibility of web pages n Malicious code on the web n Privacy preserving web mining n Models of availability/confidentiality tradeoffs n Further work with AWARE

Web Pages Uncontrolled n Information on the web is uncontrolled n A Google search can produce n Useful information n Irrelevant information n Out-of-date information n Incorrect information n Malicious information/programs

Credibility of Web Pages n How can you tell if web information is credible? n Date, author, publisher, credentials n Human assessment n Appearance of web page n User assessment n Link patterns (hubs and spokes) n Automatic assessment

Web. Cred n System to assess credibility automatically using criteria usually considered by people n Evaluated in medical domain n Rank comparable to human ranking n Wall Street Journal n Stanford University study

Web. Cred Criteria n Credentials n Association with AMA accredited medical school or selected federal agency n Advertising n Check for doubleclick, ad. dom, adv. dom n Design n W 3 C’s online page validator

Malicious Code on the Web n Clicking on a link to a web page may allow malicious code to install itself on your computer n Using e-commerce sites may result in spyware installing itself on your computer n How likely is this? n How can you protect yourself?

Privacy Preserving Web Mining n Can privacy be preserved in the presence of web mining n Problem similar to that seen in statistical databases

Availability Tradeoffs n Security in MLS databases n MLS = Multilevel security n Mix of data at different security levels n Issue of granularity – how much information is protected n Small granules -> more availability n Large granules -> less availability
![An Example n E Name Rank Salary Department n Two levels Everything ok n An Example n E [Name, Rank, Salary, Department] n Two levels: Everything ok n](https://slidetodoc.com/presentation_image_h2/bb150262f3f9bf0aa5f4d13aa9f13669/image-32.jpg)
An Example n E [Name, Rank, Salary, Department] n Two levels: Everything ok n Can not associate specific name/salary n Easy solution: Restrict access to Salary n Reduced availability n More complex solution: Allow accesses that don’t allow inference of specific Name/Salary pair n More complex, higher availability n

AWARE n A Windows Attack Int. Rusion Emulator n Runs a simulated Windows environment on top of an actual Windows environment n Simulated attacks affect the emulation, not the underlying system

Major Components n Attack inventory n Attack generator n Attack simulator n Simulation evaluator

Attack Footprint n Rogue processes Files/directories n Registry modifications n Port openings n Firewall log entries n Change in services

Simulation Tools n Netstat n Internet Explorer n Registry Editor n Search n Services. msc n Task Manager n Windows Explorer