COURSE OUTLINE 1 IntroductionHistory Key functions Interface analysis











- Slides: 22


COURSE OUTLINE 1 Introduction(History) Key functions Interface analysis 2 Traffic Analysis/OSI Review Protocol Filtering 3 IP and port filtering Wireshark and Linux firewall interaction Demonstration of detecting unauthorized traffic 4 Tshark command line interface overview Demonstrate how credentials can be stolen Network card Modes: Monitoring/Remote Capture

Why is Wireshark relevant ? Network security Prevention Performance Troubleshooting

Brief History(What was happening in the 80’s? ) How did technicians troubleshoot networks ? ANY IDEAS ?

The Oscilloscope In the 1980’s to answer this question and thoroughly examine a network an oscilloscope was the main technology used.

What could the Oscilloscope do? An oscilloscope showed square-ish electrical pulses that bounced up and down observing the change of an electrical over time. Then the observed waveform could be analyzed. Ø Technicians could determine the time and voltage values of a signal. Ø Technicians could calculate the frequency of a signal. Ø Technicians could signal over time. observe the change of an electrical

Packet Switched Networks

Packets instead of pulses With the growth of packet-switched networks. Packet analysers such as Tcp dump combined with clever low-level programming (pcap) meant you could see what was in each message going across the network.

Enter Gerald Combs

Ethereal/Wireshark In the late 1990 s Gerald Combs a computer science graduate was working for a small internet service provider. He began writing Ethereal in 1998 which led to Riverbed Technology expanding the concept under Wireshark in 2010. Today Wireshark has won several industry awards and is today one of the best open source packet analyzers available today for UNIX and Windows.

What is Wireshark? Wireshark is a free and open source network protocol analyser(also known as a network sniffer) that enables users to interactively browse the data traffic on a computer network. q 500, 000 downloads a month. q The IT industry has embraced Wireshark as the go-to tool for network troubleshooting, optimization and security.

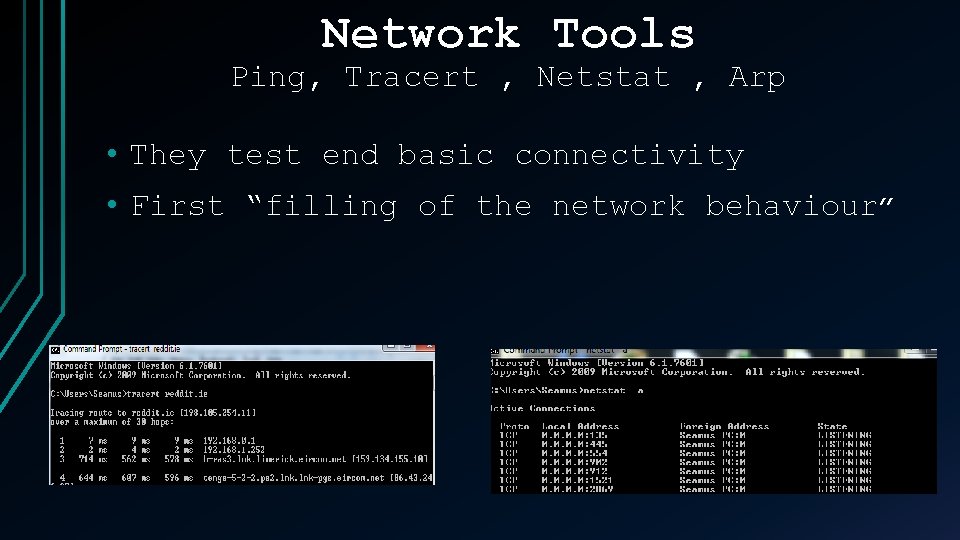
Network Tools Ping, Tracert , Netstat , Arp • They test end basic connectivity • First “filling of the network behaviour”

SNMP Tools • Continuous monitoring and mapping • Events and notifications • Map systems.

Where is Wireshark used ? Network administrators use it to • troubleshoot network problems • Hunt down unauthorized Network traffic • Troubleshoot slow network performance • Confirm Firewall settings • Determine whether a machine has malware • IT Security becoming a huge asset in the workplace • Knowledge of Wireshark is a huge plus in IT admin Jobs.

Where to Locate it? For Internet connectivity monitoring (Before or after the firewall? ) For WAN monitoring (Connect laptop to the LAN switch, with port mirror to the monitored router. For server monitoring(Connect the laptop to the LAN switch, with port mirror to the monitored server. )

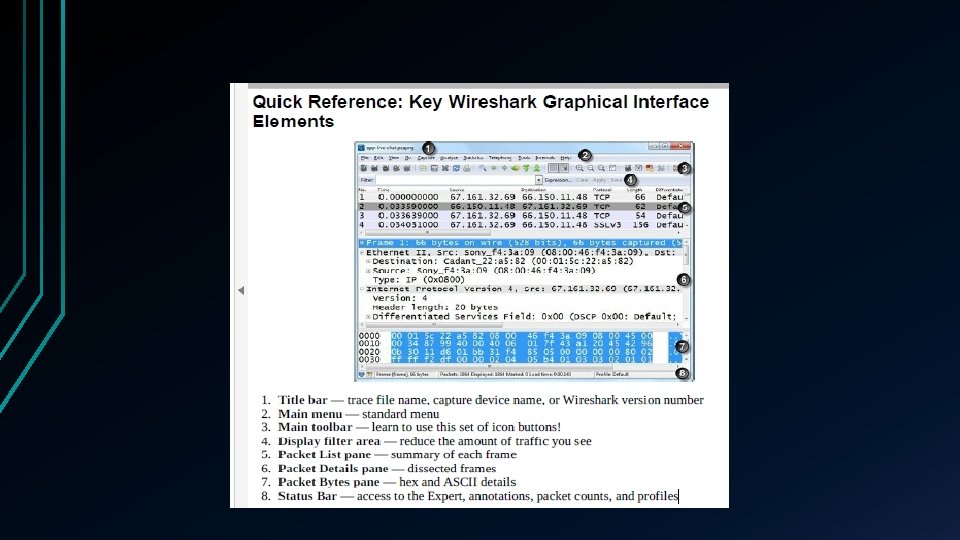
Welcome to the interface

Word. Press wireshark 01 site. wordpress. com

During installation main sure Win. Pcap is installed. Remember from earlier slide. Pcap is the (API) for capturing network traffic.


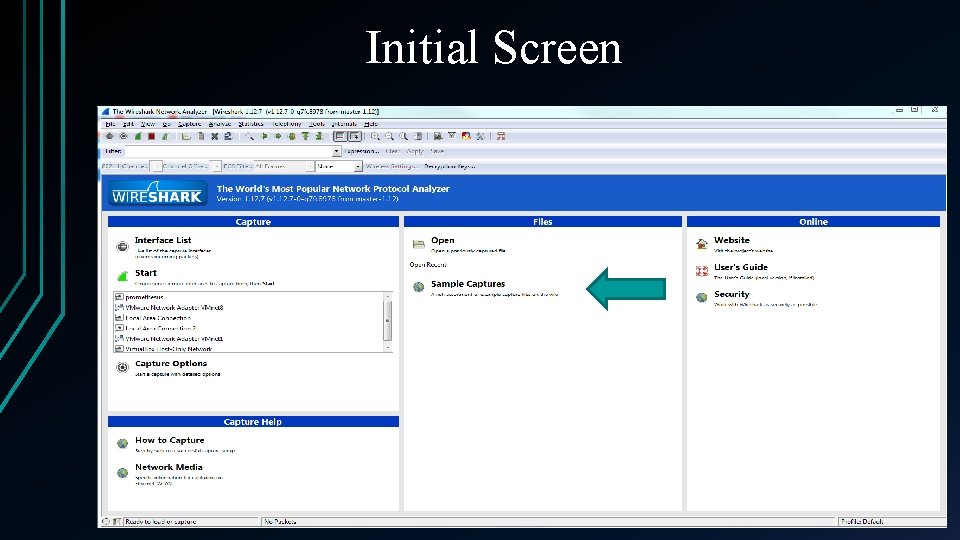
Initial Screen

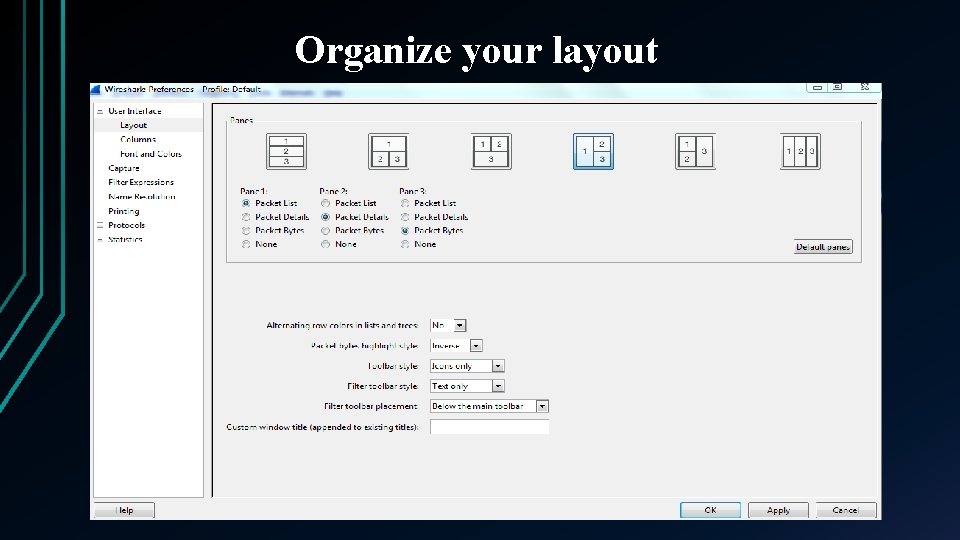
Organize your layout

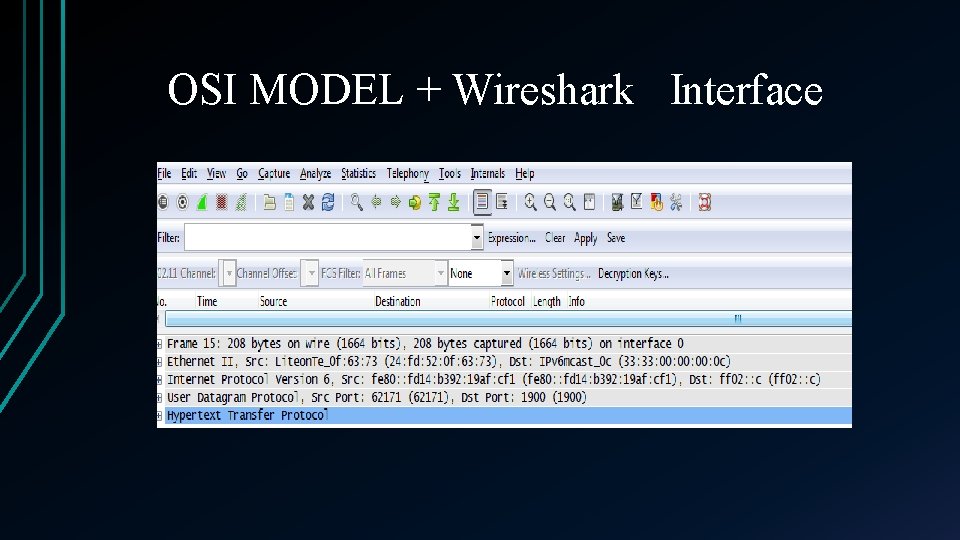
OSI MODEL + Wireshark Interface