Counterintelligence The Insider Threat An Enterprise Operations Counterintelligence






















- Slides: 24

Counterintelligence & The Insider Threat An Enterprise Operations Counterintelligence Presentation Presented by: Ralph Butler SSC Counterintelligence Lead 1

Overview • Understanding the Insider Threat • Insider Threat Trends • Insider Threat Program 2

Understanding the Insider Threat 3

Define the Insider • Authorized people using their trusted access to do unauthorized things • Threat actors vs. threats • Boils down to actors with some level of legitimate access, and with some level of organizational trust • Inadvertent or Malicious Insiders 4

Motivation Money Disgruntled Ego Paid $4. 6 million Felt CIA superiors failed to see his talent Felt the FBI didn't appreciate his brilliance, his ability and his skills Did not get promotions they felt they deserved Aldrich Ames – CIA Spied for KGB 1985 - 1994 Robert Hanssen – FBI Spied for Russian Intel 1979 - 2001 5

Glenn Shriver Recruited by China 2005 - 2011 Studied at East China Normal University in Shanghai Responds to an ad to write a political paper in for $120 Paid 10 k and 20 k for taking the Foreign Service Exam, and finally 40 k to apply with the CIA Lied on his security clearance paperwork and failed his preemployment polygraph 6

Pvt. Bradley Manning U. S. Army “I’m not a source for you…. I’m talking to you as someone who needs moral and emotional support” “I was actively involved in something that I was completely against” “Hopefully this will lead to worldwide discussion, debates, and reforms. If not, than we’re doomed as a species” 7

“I’m neither a traitor nor hero. I’m an American” Edward Snowden CIA/NSA “I have no intention of hiding who I am because I know I have done nothing wrong” “I don’t want to live in a society that does these sort of things” (Surveillance on its citizens) 8

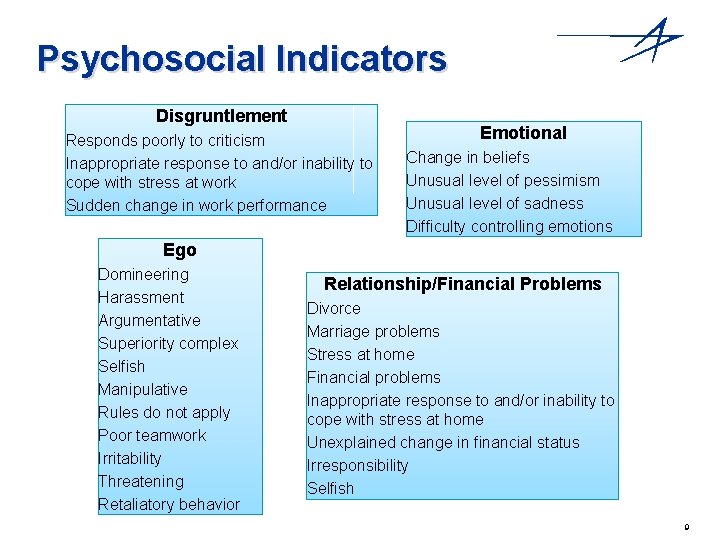
Psychosocial Indicators Disgruntlement Responds poorly to criticism Inappropriate response to and/or inability to cope with stress at work Sudden change in work performance Emotional Change in beliefs Unusual level of pessimism Unusual level of sadness Difficulty controlling emotions Ego Domineering Harassment Argumentative Superiority complex Selfish Manipulative Rules do not apply Poor teamwork Irritability Threatening Retaliatory behavior Relationship/Financial Problems Divorce Marriage problems Stress at home Financial problems Inappropriate response to and/or inability to cope with stress at home Unexplained change in financial status Irresponsibility Selfish 9

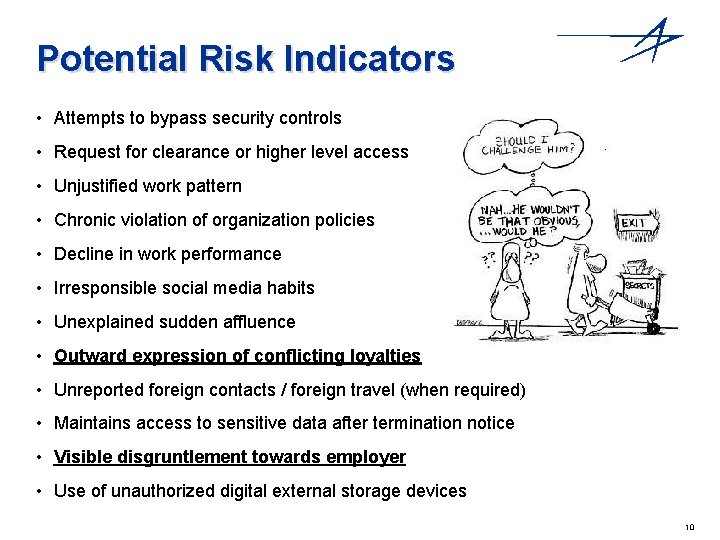
Potential Risk Indicators • Attempts to bypass security controls • Request for clearance or higher level access • Unjustified work pattern • Chronic violation of organization policies • Decline in work performance • Irresponsible social media habits • Unexplained sudden affluence • Outward expression of conflicting loyalties • Unreported foreign contacts / foreign travel (when required) • Maintains access to sensitive data after termination notice • Visible disgruntlement towards employer • Use of unauthorized digital external storage devices 10

Insider Threat Trends 11

Perspective Change Government Private Industry and Universities Classified Information Corporate Proprietary, Intellectual Property, Pre-Classified Research National Security US Technological Edge and Financial Prosperity Foreign Nations Industry Competition “Espionage used to be a problem for the FBI, CIA and military, but now it's a problem for corporations…” - Joel Brenner, National Counterintelligence Executive, 2008 Courtesy CI CENTRE & SPYpedia 12

Steady Upward Trend • 32% of all espionage arrests since 1945 have occurred in the last 5 years (FBI) • 54% of all individuals involved with compromise of classified or proprietary information were employed in Private Sector (FBI) • Industry SCRs up 600% from 2009 (DSS) – 76% increase in SCRs evaluated “of CI interest” by DSS from 2010 to 2012 • IIRs from Industry reporting up 500% from 2009 (DSS) • USG Investigations & Operations predicated on Industry reporting up over 1000% from 2009 (DSS) Courtesy: ; CI CENTRE & SPYPEDIA; CERT; DSS; www. whitehouse. gov 13

When Does it Happen? • 59% of employees leaving a company admit to taking proprietary information with them (FBI) • Out of 800 adjudicated insider threat cases, an overwhelming majority of subjects took the information within last 30 days of employment (CERT; Carnegie Mellon) • 60% of cases were individuals who had worked for the organization for less than 5 years (CPNI) • Majority of acts were carried out by staff (88%); 7% were contractors and 5% temporary staff (CPNI) Courtesy www. Whitehouse. gov 14

Insider Threat Program 15

How to Catch a Spy? • What is the most common way that spies within the U. S. Government and U. S. cleared defense contractors are detected and caught? A: B: C: D: Routine counterintelligence monitoring Tip from friend, family, co-worker Their own mistakes Reporting by U. S. sources within foreign intelligence services Answer: D – There is no loyalty in the spy business, and intelligence officers who have been recruited as sources by the U. S. Intelligence Community eagerly betray the U. S. persons who have given them information 16

Insider Threat Program Executive Order 13587 • All government agencies will have an insider threat detection and prevention program NISPOM Conforming Change 2 • Designate Insider Threat “Senior Official” – Training • Senior Official • Cleared Employee – Within first 30 -days (New Employee Orientation briefing) – Annually thereafter • System to maintain training records 17

What are we doing? • Invested in a dedicated CI program – Established Office of Counterintelligence Operations (OCIO) in 2011 – Designated CI Representatives in each business area • OCIO Representation at DSS – Full Time analyst support – Access to timely and relevant threat data • Increased CI emphasis within known target areas – CI in Contracts / Supply Chain • Risk Analysis and Mitigation System (RAMS) What is the single greatest factor? 18

CI Awareness The Employee • Mindset – Co-workers of former spies often knew something was “wrong, ” but didn’t report the behavior for many reasons • • People don’t like to “tattle” It is common to doubt yourself and your intuitions It is common to deflect responsibility It seems too personal - We don’t understand how certain behaviors are tied to espionage • Don’t miss the obvious signs!!! 19

What Can You Do? Help Me Justify My Paranoia 20

Our Challenging Equation “ 1 in 1, 000 persons in a position of trust are eligible targets for recruitment” Bruce Held, Director of Intelligence and Counterintelligence for the Department of Energy and 25 year CIA veteran Education: Consider the Operator 21

Summary • The insider threat is real and dramatically increasing • The threat has shifted from government to industry • Establish a solid CI program with emphasis on the insider threat • Detection of insider threats has to use behavioral based techniques • Employee’s are in the best position to observe potential risk indicators 22

Contact Info Ralph Butler Space Systems Company Counterintelligence Lead 408 -742 -6167 ralph. butler@lmco. com 23
